An administrator's guide to Repository Mirroring Tool—a proxy system for SUSE Customer Center with repository and registration targets.
- Preface
- 1 Overview
- 2 RMT installation and configuration
- 3 Migrate from SMT to RMT
- 4 Mirroring repositories on the RMT server
- 5 Configuring clients to use RMT
- 5.1 Configuring clients with boot parameters
- 5.2 Configuring clients with AutoYaST profile
- 5.3 Configuring clients with
rmt-client-setup - 5.4 Configuring clients with YaST
- 5.5 Configuring clients for custom stand-alone repositories
- 5.6 Listing accessible repositories
- 5.7 Online migration of SUSE Linux Enterprise clients
- 6 RMT tools and configuration files
- 7 Backing up an RMT server
- 8 Managing TLS/SSL certificates
- 9 Deploying a SUSE Linux Enterprise Server instance to support RMT in the public cloud
- A GNU licenses
Copyright © 2006–2025 SUSE LLC and contributors. All rights reserved.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”.
For SUSE trademarks, see https://www.suse.com/company/legal/. All third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof.
1 Available documentation #
- Online documentation
Our documentation is available online at https://documentation.suse.com. Browse or download the documentation in various formats.
Note: Latest updatesThe latest updates are usually available in the English-language version of this documentation.
- SUSE Knowledgebase
If you run into an issue, check out the Technical Information Documents (TIDs) that are available online at https://www.suse.com/support/kb/. Search the SUSE Knowledgebase for known solutions driven by customer need.
- Release notes
For release notes, see https://www.suse.com/releasenotes/.
- In your system
For offline use, the release notes are also available under
/usr/share/doc/release-noteson your system. The documentation for individual packages is available at/usr/share/doc/packages.Many commands are also described in their manual pages. To view them, run
man, followed by a specific command name. If themancommand is not installed on your system, install it withsudo zypper install man.
2 Improving the documentation #
Your feedback and contributions to this documentation are welcome. The following channels for giving feedback are available:
- Service requests and support
For services and support options available for your product, see https://www.suse.com/support/.
To open a service request, you need a SUSE subscription registered at SUSE Customer Center. Go to https://scc.suse.com/support/requests, log in, and click .
- Bug reports
Report issues with the documentation at https://bugzilla.suse.com/.
To simplify this process, click the icon next to a headline in the HTML version of this document. This preselects the right product and category in Bugzilla and adds a link to the current section. You can start typing your bug report right away.
A Bugzilla account is required.
- Contributions
To contribute to this documentation, click the icon next to a headline in the HTML version of this document. This will take you to the source code on GitHub, where you can open a pull request.
A GitHub account is required.
Note: only available for EnglishThe icons are only available for the English version of each document. For all other languages, use the icons instead.
For more information about the documentation environment used for this documentation, see the repository's README.
You can also report errors and send feedback concerning the documentation to <doc-team@suse.com>. Include the document title, the product version, and the publication date of the document. Additionally, include the relevant section number and title (or provide the URL) and provide a concise description of the problem.
3 Documentation conventions #
The following notices and typographic conventions are used in this document:
/etc/passwd: Directory names and file namesPLACEHOLDER: Replace PLACEHOLDER with the actual value
PATH: An environment variablels,--help: Commands, options, and parametersuser: The name of a user or grouppackage_name: The name of a software package
Alt, Alt–F1: A key to press or a key combination. Keys are shown in uppercase as on a keyboard.
, › : menu items, buttons
AMD/Intel This paragraph is only relevant for the AMD64/Intel 64 architectures. The arrows mark the beginning and the end of the text block.
IBM Z, POWER This paragraph is only relevant for the architectures
IBM ZandPOWER. The arrows mark the beginning and the end of the text block.Chapter 1, “Example chapter”: A cross-reference to another chapter in this guide.
Commands that must be run with
rootprivileges. You can also prefix these commands with thesudocommand to run them as a non-privileged user:#command>sudocommandCommands that can be run by non-privileged users:
>commandCommands can be split into two or multiple lines by a backslash character (
\) at the end of a line. The backslash informs the shell that the command invocation will continue after the end of the line:>echoa b \ c dA code block that shows both the command (preceded by a prompt) and the respective output returned by the shell:
>commandoutputNotices
Warning: Warning noticeVital information you must be aware of before proceeding. Warns you about security issues, potential loss of data, damage to hardware, or physical hazards.
Important: Important noticeImportant information you should be aware of before proceeding.
Note: Note noticeAdditional information, for example about differences in software versions.
Tip: Tip noticeHelpful information, like a guideline or a piece of practical advice.
Compact Notices
Additional information, for example about differences in software versions.
Helpful information, like a guideline or a piece of practical advice.
4 Support #
Find the support statement for SUSE Linux Enterprise Server and general information about technology previews below. For details about the product lifecycle, see https://www.suse.com/lifecycle.
If you are entitled to support, find details on how to collect information for a support ticket at https://documentation.suse.com/sles-15/html/SLES-all/cha-adm-support.html.
4.1 Support statement for SUSE Linux Enterprise Server #
To receive support, you need an appropriate subscription with SUSE. To view the specific support offers available to you, go to https://www.suse.com/support/ and select your product.
The support levels are defined as follows:
- L1
Problem determination, which means technical support designed to provide compatibility information, usage support, ongoing maintenance, information gathering and basic troubleshooting using available documentation.
- L2
Problem isolation, which means technical support designed to analyze data, reproduce customer problems, isolate a problem area and provide a resolution for problems not resolved by Level 1 or prepare for Level 3.
- L3
Problem resolution, which means technical support designed to resolve problems by engaging engineering to resolve product defects which have been identified by Level 2 Support.
For contracted customers and partners, SUSE Linux Enterprise Server is delivered with L3 support for all packages, except for the following:
Technology previews.
Sound, graphics, fonts, and artwork.
Packages that require an additional customer contract.
Some packages shipped as part of the module Workstation Extension are L2-supported only.
Packages with names ending in -devel (containing header files and similar developer resources) will only be supported together with their main packages.
SUSE will only support the usage of original packages. That is, packages that are unchanged and not recompiled.
4.2 Technology previews #
Technology previews are packages, stacks, or features delivered by SUSE to provide glimpses into upcoming innovations. Technology previews are included for your convenience to give you a chance to test new technologies within your environment. We would appreciate your feedback. If you test a technology preview, please contact your SUSE representative and let them know about your experience and use cases. Your input is helpful for future development.
Technology previews have the following limitations:
Technology previews are still in development. Therefore, they may be functionally incomplete, unstable, or otherwise not suitable for production use.
Technology previews are not supported.
Technology previews may only be available for specific hardware architectures.
Details and functionality of technology previews are subject to change. As a result, upgrading to subsequent releases of a technology preview may be impossible and require a fresh installation.
SUSE may discover that a preview does not meet customer or market needs, or does not comply with enterprise standards. Technology previews can be removed from a product at any time. SUSE does not commit to providing a supported version of such technologies in the future.
For an overview of technology previews shipped with your product, see the release notes at https://www.suse.com/releasenotes.
The Repository Mirroring Tool (RMT) for SUSE Linux Enterprise 15 SP6 allows enterprise customers to optimize the management of SUSE Linux Enterprise software updates and subscription entitlements. It establishes a proxy system for SUSE® Customer Center with repositories and registration targets. This helps you to centrally manage software updates within a firewall on a per-system basis, while maintaining your corporate security policies and regulatory compliance.
RMT allows you to provision updates for all your devices running a product based on SUSE Linux Enterprise. By downloading these updates once and distributing them throughout the enterprise, you can set more restrictive firewall policies. This also reduces bandwidth usage, as there is no need to download the same updates for each device. RMT is fully supported and available as a download for customers with an active SUSE Linux Enterprise product subscription.
Repository Mirroring Tool provides functionality that can be useful in many situations, including the following:
You want to update SUSE Linux Enterprise servers.
Not all machines in your environment can be connected to SUSE Customer Center to register and retrieve updates for bandwidth or security reasons.
There are SUSE Linux Enterprise hosts that are restricted and difficult to update without putting in place a custom update management solution.
You need to integrate additional external or internal repositories.
RMT replaces SMT (Subscription Management Tool) which was used for SLE 11 and SLE 12. For a feature comparison between RMT and SMT, see Table 3.1, “Feature comparison”.
2 RMT installation and configuration #
RMT is included in SUSE Linux Enterprise Server starting with version 15. Install RMT directly during the installation of SUSE Linux Enterprise Server or install it on a running system. After the packages are installed, use YaST to do an initial configuration.
Configuring a server to be an RMT server installs and configures the NGINX Web server, listening on port 80.
However, configuring a machine to be an installation server automatically installs the Apache Web server and configures it to listen on port 80.
Do not try to enable both these functions on the same server. It is not possible for a single server to host both simultaneously.
2.1 Storage requirements #
Downloaded packages are stored in
/usr/share/rmt/public/repo, which is a symbolic link
to /var/lib/rmt/public/repo/.
The amount of storage your RMT server requires depends on several variables: the number of repositories and architectures that you mirror, and the number of products that are enabled. As a general guide, 1.5 times the total size of all enabled repositories should be sufficient. This is about 200 GB per SUSE Linux Enterprise release, including all extensions.
/tmp runs out of space
When RMT mirrors repositories from SUSE Customer Center, it writes large temporary files in /tmp.
If /tmp is too small, or is part of the /root files system, and
this file system is small in size, /tmp quickly runs out of space, resulting in a mirroring failure.
For more information, refer to https://support.scc.suse.com/s/kb/RMT-mirroring-fails-when-tmp-runs-out-of-disk-space?language=en_US.
2.2 Installation during system installation #
To install it during installation, select the rmt-server package. Package selection can be found in Installation Settings when selecting Software.
Check for available RMT updates immediately after installing SUSE Linux Enterprise Server
using the zypper patch command because SUSE
continuously releases maintenance updates for RMT.
2.3 Installation on an existing system #
To install RMT on a running SUSE Linux Enterprise Server installation, use
zypper:
>sudozypper in rmt-server
2.3.1 Installation on SLES Minimal VM #
SLES Minimal VM is a minimal customizable operating system that is designed for specific usage scenarios, for example, to be run as:
A container host
A virtual machine guest
An appliance base system
A small server image
SLES Minimal VM image is a good choice for being used as an RMT server. You can download SLES Minimal VM images for KVM, Xen, Microsoft Hyper-V, VMware, and OpenStack from the public SUSE Linux Enterprise Server download page at https://www.suse.com/download/sles/. Find more information on SLES Minimal VM at https://documentation.suse.com/smart/virtualization-cloud/html/minimal-vm/.
Installing RMT on SLES Minimal VM is the same as installing it on an
existing system (see Section 2.3, “Installation on an existing system”).
To install RMT on
SLES Minimal VM, run the following command from the SLES Minimal VM command line as
root:
# zypper install rmt-server yast2-rmt nginx mariadbWhen installing RMT on SLES Minimal VM, be aware that it requires a minimum of 100 GB disk space, depending on the products you select to mirror. Another requirement is a CPU with at least two cores and 2 GB of RAM.
2.4 Deploying RMT on top of the Kubernetes cluster #
This section describes how to deploy RMT on top of the Kubernetes cluster. It uses Helm as the package manager to interact with the Kubernetes cluster. Find more details about using Helm at https://helm.sh/docs/intro/using_helm/.
2.4.1 Prerequisites #
Running Kubernetes cluster
helmcommand configured to interact with the cluster
2.4.2 Application components #
Each component of the RMT application is deployed in its own container. RMT consists of the following components:
- RMT server
Containerized version of the RMT application server with the ability to pass its configuration via Helm values. Storage is done on a volume that is allocated to the Kubernetes cluster. You need to adjust the size of the storage depending on the number of repositories you need to mirror.
- MariaDB
The database back-end for RMT. No post-installation task is needed since RMT creates the required database and tables at start-up. If passwords are not specified in the
values.yamlfile, they are generated automatically.- Nginx
A Web server configured for RMT routes. Having a properly configured Web server allows you to target your Ingress traffic (for RMT) to this Nginx service directly. You do not need to configure Ingress for RMT specific paths handling, as Nginx is configured to take care of this itself.
2.4.3 The values.yaml file #
The RMT chart includes the values.yaml file
where all parameters are documented and their default values are
defined. You can override these values by providing your own values
file, for example:
> cat << EOF > rmt-config.yaml
---
app:
storage:
class: local-path1
scc:
enabled: false
username: "UXXXXXXX"
password: "PASSXXXX"
products_enable:
- SLES/15.3/x86_64
- sle-module-python2/15.3/x86_64
products_disable:
- sle-module-legacy/15.3/x86_64
- sle-module-cap-tools/15.3/x86_64
db:
storage:
class: local-path2
ingress:
enabled: true
hosts:
- host: chart-example.local
paths:
- path: "/"
pathType: Prefix
tls:
- secretName: rmt-cert
hosts:
- chart-example.local
EOF
The |
And to install RMT, run:
> helm install rmtsle oci://registry.suse.com/suse/rmt-helm -f rmt-config.yaml2.4.3.1 Required values #
- Key: app.scc.password
Type: string
Default:
nilDescription: SUSE Customer Center proxy password. The password string needs to be put inside quotes. If the quote character
"is part of the string, it has to be escaped with\.- Key: app.scc.username
Type: string
Default:
nilDescription: SUSE Customer Center proxy user name. The user name string needs to be put inside quotes. If the quote character
"is part of the string, it has to be escaped with\.- Key: app.scc.products_enable
Type: list
Default:
[]Description: list of products to enable for mirroring
- Key: app.scc.products_disable
Type: list
Default:
[]Description: list of products to disable for mirroring
- Key: app.storage.class
Type: string
Default:
""Description: Kubernetes
storageclass.- Key: db.storage.class
Type: string
Default:
""Description: Kubernetes
storageclass.- Key: ingress.enabled
Type: bool
Default:
falseDescription: Ingress Enabled
- Key: ingress.hosts[0]
Type: object
Default:
{"host":"chart-example.local","paths":[{"path":"/","pathType":"Prefix"}]}Description: DNS name at which the RMT service will be accessible from clients
- Key: ingress.tls[0].hosts[0]
Type: string
Default:
"chart-example.local"Description: DNS name at which the RMT service will be accessible from clients
- Key: ingress.tls[0].secretName
Type: string
Default:
"rmt-cert"Description: TLS Ingress Certificate
2.5 RMT configuration with YaST #
Configure RMT with YaST as described in the following procedure. It is assumed that this procedure is executed on a newly installed system.
Start YaST with the
rmtmodule.>sudoyast2 rmtAlternatively, start YaST and select › .
Enter your organization credentials. To retrieve your credentials, refer to Section 4.1, “Mirroring credentials”.
Enter credentials for a new MariaDB user and database name, and confirm with .
If a password for the MariaDB
rootuser is already set, you are required to enter it. If no password is set forroot, you are asked to enter a new one.Enter a common name for the SSL certificates. The common name should be the fully qualified domain name (FQDN) of the server. Enter all domain names and IP addresses with which you want to reach the RMT server as alternative common names.
When all common names are entered, select .
Tip: Certificate locations for RMT/etc/rmt/ssl/rmt-ca.crtThis is the CA certificate bundle that
yast2 rmtuses to certify the RMT server certificate.yast2 rmtonly creates this file if it does not already exist./etc/rmt/ssl/rmt-server.crtand/etc/rmt/ssl/rmt-server.keyyast2 rmtonly generates a new server certificate and private key if one does not already exist. To regenerate this certificate, refer to Section 8.1, “Regenerating HTTPS certificates”.
If
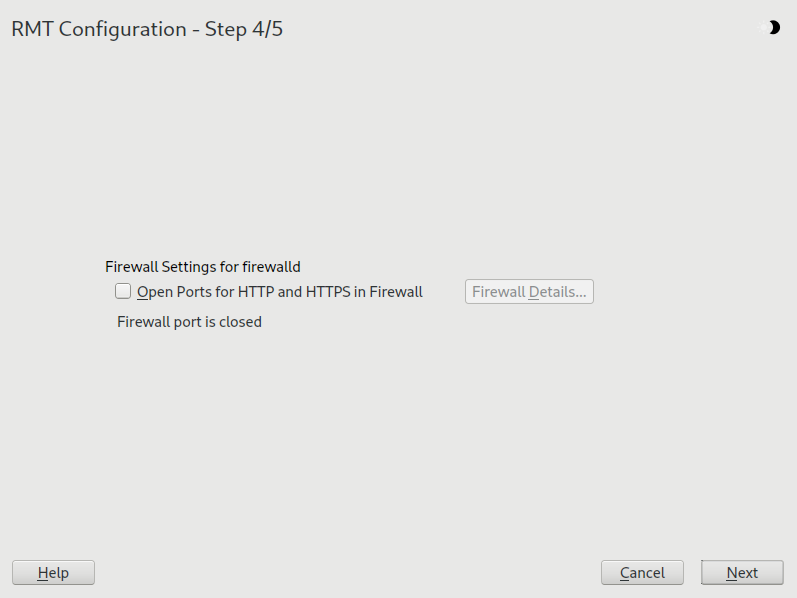
firewalldis enabled on this system, enable the check box to open the required ports.Figure 2.2: Enabling ports infirewalld#If
firewalldis not enabled now and you plan to enable it later, you can always open relevant ports by running theyast2 rmtmodule.Tip: Fine-tuningfirewalldsettingsBy clicking , you can open the relevant ports for specific network interfaces only.
Continue with .
To view the summary, click . Close YaST by clicking . YaST then enables and starts all
systemdservices and timers.
2.6 Enabling SLP announcements #
RMT includes the SLP service description file
/etc/slp.reg.d/rmt-server.reg. To enable SLP
announcements of the RMT service, follow these steps:
If
firewalldis running, open relevant ports and reload thefirewalldconfiguration:>sudofirewall-cmd --permanent --add-port=427/tcp success>sudofirewall-cmd --permanent --add-port=427/udp success>sudofirewall-cmd --reloadVerify that the SLP server is installed and install it if it is not:
>sudozypper install openslp-serverEnable and start the SLP service:
>sudosystemctl enable slpd.service>sudosystemctl restart slpd.service
2.7 Accessing SUSE Customer Center behind a firewall #
If the RMT server is behind a firewall and cannot access SUSE Customer Center directly, you need to allow connections to the following domains for both 80 and 443 ports on the firewall.
scc.suse.com
updates.suse.com
installer-updates.suse.com
If the firewall you are using does not support host name
allowlisting—such as firewalld—you need to allow connections
to the corresponding IP addresses as described in the following steps.
Resolve the IP address of the domain, for example,
installer-updates.suse.com.>nslookup installer-updates.suse.com[...] Address: 152.199.22.115Add firewall rules for ports 80 and 443 for each discovered IP address.
>sudofirewall-cmd --permanent --zone=public \ --add-rich-rule='rule family="ipv4" source address="152.199.22.115" \ port protocol="tcp" port="80" accept'>sudofirewall-cmd --permanent --zone=public \ --add-rich-rule='rule family="ipv4" source address="152.199.22.115" \ port protocol="tcp" port="443" accept'Reload the firewall configuration.
>sudofirewall-cmd --reload
3 Migrate from SMT to RMT #
This chapter describes the migration from SMT on SLES 11 or 12 to RMT on SLES 15.
3.1 Important notes #
Carefully read this section. It contains vital information about the migration process.
- Use a new host
We recommend that you install RMT on a newly installed SLES 15 host. RMT is not a complete replacement for SMT. It has a different workflow than SMT and only supports registering SUSE Linux Enterprise Server 12 systems and newer.
- Repository metadata and settings
The settings of staged repositories are not exported from SMT. Repositories that have been marked to be mirrored are exported.
- Custom repositories
It is only possible to export repositories that are marked for mirroring.
- Expired subscriptions
Products no longer available on the organization subscriptions will not be available on RMT.
- Client information
Systems and their activated products are exported. SMT client jobs and patch status are not exported from SMT.
|
Feature |
SMT |
RMT |
|---|---|---|
|
Available on SLES 11 |
yes |
no |
|
Available on SLES 12 |
yes |
no |
|
Available on SLES 15 |
no |
yes |
|
Synchronize products with SUSE Customer Center |
yes |
yes |
|
Mirror RPMs from repositories |
yes |
yes |
|
Selective mirroring (specifying products to mirror) |
yes |
yes |
|
Serve RPMs via HTTP |
yes |
yes |
|
Registration of SLE 15 systems |
yes |
yes |
|
Registration of SLE 12 systems |
yes |
yes |
|
Registration of SLE 11 systems |
yes |
no |
|
Red Hat 6 and earlier support |
yes 1 |
no |
|
Red Hat 7+ support |
yes 1 |
yes 1 |
|
Support for migrating SLE 12 to 15 |
yes 2 |
yes |
|
Support for migrating SLE 15 SPx to 15 SPx+1 |
yes 2 |
yes |
|
Staging repositories |
yes |
no 3 |
|
Offline mirroring |
yes |
yes |
|
NTLM Proxy support |
yes |
yes |
|
Custom repositories |
yes |
yes |
|
YaST installation wizard |
yes |
yes |
|
YaST management wizard |
yes |
no |
|
Client management |
yes |
no |
|
Files deduplication |
yes |
yes |
|
Data transfer from SMT to RMT |
n/a |
yes |
|
Transfer registration data to SUSE Customer Center |
yes |
yes |
|
Reporting |
yes |
no |
|
Custom TLS certificates for Web server |
yes |
yes |
|
Clean up data from repositories that are not used any longer |
yes |
yes |
|
Bash completion |
no |
yes |
|
Available on openSUSE Leap 15 |
no |
yes 4 |
|
Easy development setup + contribution guide |
no |
yes |
|
100% test coverage |
no |
yes |
|
no |
yes | |
|
Web server |
Apache2 |
Nginx |
|
Platform |
Perl |
Ruby |
|
Clean up data from repositories that are no longer used |
yes |
yes |
|
Bash completion |
no |
yes |
|
Option to deploy on Kubernetes |
no |
yes 5 |
Support via SUSE Liberty Linux—find more details in https://www.suse.com/products/suse-liberty-linux/.
SMT only partially supports migrating systems to SLE 15. SLE 15 is composed of multiple modules and extensions. Some modules are not required, as they provide additional functionality. RMT fully supports migrations into and within SLE 15, therefore it only adds the minimum of required modules. SMT does not fully support these migrations, and it enables all available modules on the system.
Functionality is offered by SUSE Manager.
Only available with self-support.
Find more details in Section 2.4, “Deploying RMT on top of the Kubernetes cluster”.
3.2 Exporting SMT data #
Update your SMT server installation by running
zypper up.To export your SSL certificates along with the rest of the data, run
smt-data-export. Remember to keep your certificates in a safe place.If you do not want to export the SSL certificates from SMT, run
smt-data-export --no-ssl-export.The exported configuration is now saved to
smt-data-export.TIMESTAMP.tar.gz. Copy the file to a location that the new RMT server can access.
3.3 Importing SMT data to RMT #
To make sure your RMT installation is up to date, run
zypper up.Copy the exported
.tar.gzfile to an empty directory and unpack it. Then enter the new directory:>mkdir EMPTY_DIR>cd EMPTY_DIR>tar xf /PATH/TO/smt-data-export.TIMESTAMP.tar.gz>cd smt-data-exportIf you chose to export the SSL certificates from SMT, copy the CA private key and certificate to
/etc/rmt/ssl/:>sudocp ssl/cacert.key /etc/rmt/ssl/rmt-ca.key>sudocp ssl/cacert.pem /etc/rmt/ssl/rmt-ca.crtRun the YaST RMT configuration module as described in Section 2.5, “RMT configuration with YaST”. If you imported the SMT CA certificate, add the domain of the SMT server to the common names of the new SSL certificate.
Run the RMT synchronization to get the products and repositories data from SUSE Customer Center.
>sudormt-cli syncImport the data from the SMT server.
>sudormt-data-import -d ./Optional: if the URL of the RMT server changed, change the URL parameter of clients in
/etc/SUSEConnectto point to the new RMT server. Alternatively, change the DNS records to re-assign the host name to the RMT server.Optional: move the mirrored repository data from SMT to RMT, and adjust the ownership of the copied data.
>sudocp -r /var/www/htdocs/repo/* /usr/share/rmt/public/repo/>sudochown -R _rmt:nginx /usr/share/rmt/public/repoTipThe path for storing custom repository data on the RMT server is different from that of SMT. With RMT, it replicates the directory structure of the source server's URL into a top level directory structure of the source server's URL into a top-level
http://download.opensuse.org/debug/distribution/leap/15.6/repo/oss
its path on the RMT server corresponds to
/usr/share/rmt/public/repo/debug/distribution/leap/15.6/repo/oss
Custom repositories on the SMT server are disabled by default. If you want to mirror them to the RMT, enable them before mirroring.
Check for custom repositories by running:
>sudormt-cli repos custom listThe command shows the table of all custom repositories. The first column contains the
IDof each repository and theMirror?column showsfalse.Enable each custom repository you want to mirror by running:
>sudormt-cli repos custom enable ID
Update the packages in the repositories by starting the mirroring process:
>sudormt-cli mirror
4 Mirroring repositories on the RMT server #
You can mirror the installation and update repositories on the RMT server. This way, you do not need to download updates on each machine, which saves time and capacity.
In its default configuration, RMT mirrors enabled product repositories automatically once every night.
By default, the mirrored repositories are stored in
/var/lib/rmt/public/repo.
To change the default location of the mirrored repositories, point the
/usr/share/rmt/public/repo symbolic link to the
desired directory. This can be done using the command:
ln -sfn TARGET
/usr/share/rmt/public/repo
(Replace TARGET with the desired destination). Make
sure that the target has read and write permissions for the
rmt user and nginx group.
When enabled repositories are fully mirrored, you can register your client
systems against RMT by running SUSEConnect --url
https://RMT_HOSTNAME on the client
machine. After successful registration, the repositories from the RMT
server are used by Zypper on the client machine.
RMT does not support clients with SUSE Linux Enterprise Server versions 11 and older.
4.1 Mirroring credentials #
You need organization credentials to create a local mirror of the SUSE Linux Enterprise repositories. You can obtain the credentials from SUSE Customer Center.
To get the credentials from SUSE Customer Center, follow these steps:
Visit SUSE Customer Center at https://scc.suse.com and log in.
If you are a member of multiple organizations, select the organization you want to work with from the sidebar on the left.
Select in the top menu.
The credentials are displayed in the top right corner.
The obtained credentials should be set with the YaST RMT Server
Configuration module or added directly to the
/etc/rmt.conf file. For more information about the
/etc/rmt.conf file, see
Section 6.3.1, “/etc/rmt.conf”.
4.2 Synchronizing repository metadata #
The local RMT database needs to be updated periodically with the information downloaded from SUSE Customer Center. This includes information about available products and repositories.
The synchronization is activated by the systemd timer
rmt-server-sync.timer. To view its status, for
example, the next running time, use systemctl status.
>sudosystemctl status rmt-server-sync.timer● rmt-server-sync.timer - RMT Sync timer Loaded: loaded (/usr/lib/systemd/system/rmt-server-sync.timer; enabled; vendor preset: disabled) Active: active (waiting) since Fri 2018-06-22 04:22:34 EDT; 2h 34min ago Trigger: Sat 2018-06-23 03:53:00 EDT; 20h left Jun 22 04:22:34 d31 systemd[1]: Started RMT Sync timer.
If the timer is not enabled or started, start it manually.
>sudosystemctl enable --now rmt-server-sync.timer
To update the RMT database manually, use the rmt-cli
sync command. For details, see
Section 6.1.2, “sync”.
4.3 Mirroring packages #
Packages for enabled repositories are mirrored on your RMT server. Packages are downloaded periodically once a day. But the download can also be triggered manually at any time.
The periodic mirroring is activated by the systemd timer
rmt-server-mirror.timer. To show its status, for
example, the next running time, use systemctl status.
#systemctl status rmt-server-mirror.timer● rmt-server-mirror.timer - RMT Mirror timer Loaded: loaded (/usr/lib/systemd/system/rmt-server-mirror.timer; enabled; vendor preset: disabled) Active: active (waiting) since Fri 2018-06-22 04:22:34 EDT; 2h 34min ago Trigger: Sat 2018-06-23 02:17:57 EDT; 19h left Jun 22 04:22:34 d31 systemd[1]: Started RMT Mirror timer.
If the timer is not enabled or started, start it manually.
>sudosystemctl enable --now rmt-server-mirror.timer
To update the mirrored packages manually, use the rmt-cli
mirror command. For details, see
Section 6.1.6, “mirror”.
4.4 Enabling and disabling mirroring of repositories #
You can enable or disable the mirroring of repositories individually or by product. You can specify one or more repositories or products at once. When repositories are enabled, their packages are downloaded and updated during the mirroring process. To enable or disable mirroring of repositories, you either need the product string or ID, or the repository name or ID. Enabling or disabling a product is desired, because this automatically enables or disables all repositories associated with the product.
4.4.1 Using products #
To enable or disable all repositories of a product, use the
rmt-cli products enable
ID and rmt-cli products
disable ID commands. To retrieve
an ID for an enabled product, use the rmt-cli products
list command. To get the ID of a disabled
product that is still available, run the rmt-cli products list --all
command.
Example:
>sudormt-cli products list --all+------+----------------------+---------+--------+--------------+--------------- | ID | Product | Version | Arch | Mirror? | Last mirrored +------+----------------------+---------+--------+--------------+--------------- [...] | 1743 | SUSE Package Hub | 15 | x86_64 | Don't Mirror | | | PackageHub/15/x86_64 | | | | [...]>sudormt-cli products enable 1743Found product by target 1743: SUSE Package Hub 15 x86_64. Enabling SUSE Package Hub 15 x86_64: SUSE Package Hub 15 x86_64: Enabled repository SLE-Module-Packagehub-Subpackages15-Pool. Enabled repository SLE-Module-Packagehub-Subpackages15-Updates. Enabled repository SUSE-PackageHub-15-Pool. Enabled repository SUSE-PackageHub-15-Standard-Pool..>sudormt-cli products disable 1743Found product by target 1743: SUSE Package Hub 15 x86_64. Disabling SUSE Package Hub 15 x86_64: SUSE Package Hub 15 x86_64: Disabled repository SLE-Module-Packagehub-Subpackages15-Pool. Disabled repository SLE-Module-Packagehub-Subpackages15-Updates. Disabled repository SUSE-PackageHub-15-Pool. Disabled repository SUSE-PackageHub-15-Standard-Pool. To clean up downloaded files, run 'rmt-cli repos clean'
To enable or disable multiple products at once, specify a space-delimited list of their IDs or product strings, for example:
>sudormt-cli products enable 1743 SLES/15/x86_64 SLES/12Found product by target 1743: SUSE Package Hub 15 x86_64. Enabling SUSE Package Hub 15 x86_64: SUSE Package Hub 15 x86_64: Enabled repository SLE-Module-Packagehub-Subpackages15-Pool. Enabled repository SLE-Module-Packagehub-Subpackages15-Updates. Enabled repository SUSE-PackageHub-15-Pool. Enabled repository SUSE-PackageHub-15-Standard-Pool. Found product by target SLES/15/x86_64: SUSE Linux Enterprise Server 15 x86_64. Enabling SUSE Linux Enterprise Server 15 x86_64: SUSE Linux Enterprise Server 15 x86_64: Enabled repository SLE-Product-SLES15-Pool. Enabled repository SLE-Product-SLES15-Updates. Enabled repository SLE15-Installer-Updates. Basesystem Module 15 x86_64: Enabled repository SLE-Module-Basesystem15-Pool. Enabled repository SLE-Module-Basesystem15-Updates. Server Applications Module 15 x86_64: Enabled repository SLE-Module-Server-Applications15-Pool. Enabled repository SLE-Module-Server-Applications15-Updates. Found product by target SLES/12: SUSE Linux Enterprise Server 12 x86_64. Enabling SUSE Linux Enterprise Server 12 x86_64: SUSE Linux Enterprise Server 12 x86_64: Enabled repository SLES12-Pool. Enabled repository SLES12-Updates.
4.4.2 Using repositories #
To enable or disable mirroring of specific repositories, use the
rmt-cli repos enable ID
and rmt-cli repos disable
ID commands. To retrieve an ID for
an enabled repository, use the rmt-cli repos
listcommand. If you need to get the ID of a disabled
but accessible repository, execute the command
rmt-cli repos list --all.
Example:
>sudormt-cli repos list --all+--------+-------------------------+-------------------------------------------+ | ID | Name | Description | +--------+-------------------------+-------------------------------------------+ [...] | 3061 | SUSE-PackageHub-15-Pool | SUSE-PackageHub-15-Pool for sle-15-x86_64 | [...] +--------+-------------------------+-------------------------------------------+>sudormt-cli repos enable 3061Repository by ID 3061 successfully enabled.>sudormt-cli repos disable 3061Repository by ID 3061 successfully disabled. To clean up downloaded files, please run 'rmt-cli repos clean'
To enable or disable multiple repositories at once, specify a space-delimited list of their IDs, for example:
>sudormt-cli repos enable 2526 3263Repository by ID 2526 successfully enabled. Repository by ID 3263 successfully enabled.>sudormt-cli repos disable 2526 3263Repository by ID 2526 successfully disabled. Repository by ID 3263 successfully disabled. To clean up downloaded files, run 'rmt-cli repos clean'
4.5 Deleting mirrored data #
After you disable the mirroring of a repository or product as described in Section 4.4, “Enabling and disabling mirroring of repositories”, the mirrored data remains on your local hard disk. This includes the mirrored RPM packages.
To delete disabled repository data, use the command rmt-cli
repos clean. With this command, RMT verifies that only enabled
repositories are mirrored and provides a way to delete invalid data.
Before removing any data, the command lists the affected repositories and
requires the user to input yes to continue.
>sudormt-cli repos cleanRMT found locally mirrored files from the following repositories which are not marked to be mirrored: SLE-Product-SLES15-Updates for sle-15-x86_64 SLE-Product-SLES15-Pool for sle-15-x86_64 SLE15-Installer-Updates for sle-15-x86_64 Would you like to continue and remove the locally mirrored files of these repositories? Only 'yes' will be accepted. Enter a value: yes Deleted locally mirrored files from repository 'SLE-Product-SLES15-Updates for sle-15-x86_64'. Deleted locally mirrored files from repository 'SLE-Product-SLES15-Pool for sle-15-x86_64'. Deleted locally mirrored files from repository 'SLE15-Installer-Updates for sle-15-x86_64'. Clean finished. An estimated 157 MB were removed.
To delete disabled repository data, manually remove its corresponding directory:
>sudorm -r /usr/share/rmt/public/repo/SUSE/Products/PRODUCT/VERSION/ARCHITECTURE/
4.6 Adding custom repositories #
You can mirror custom repositories with the RMT server. These
repositories are not provided by SUSE Customer Center. Repositories can be provided
by, for example, the Open Build Service, third-party vendors, or created with
createrepo.
Custom repositories can either be stand-alone, or you can attach them to products. This allows you to connect multiple repositories with one command on a client registered to the RMT server.
The following example procedure illustrates the mirroring of a third-party repository.
Add the remote repository to the RMT server. Replace URL with the URL to the repository. Replace NAME with a name of your choice for the repository.
#rmt-cli repos custom add URL NAMEList all custom repositories to get the ID of the new repository.
#rmt-cli repos custom listOptionally attach the new custom repository to a product. For example, if the new custom repository is required by all desktop clients, it can be attached to the
SUSE Linux Enterprise Desktopproduct.#rmt-cli repos custom attach REPOSITORY_ID PRODUCT_IDReplace REPOSITORY_ID with the ID of the new custom repository. Replace PRODUCT_ID with the ID of a product you want the repository to be attached to. If you need to retrieve the PRODUCT_ID, use the command
rmt-cli products list --all.ImportantWhen custom repositories are associated with a product, clients registering with that product see it as disabled. To enable the repository, find its ID with the command
zypper lrand run:#zypper mr -e REPO_IDEnable mirroring of the new custom repository.
#rmt-cli repos custom enable REPOSITORY_ID
To get a list of all available custom repositories commands, see
Section 6.1.4, “repos”.
4.7 Exporting and importing repositories #
RMT has built-in functions to import and export data about available repositories and the mirrored packages. For example, this can be used to speed up the setup of a new RMT server by locally copying already mirrored RPM packages.
Another use case is the offline mode. It allows the transfer of data to a disconnected RMT server, for example, to provide updates to computers in an air-gapped network.
The following procedure describes the transfer of data and mirrored RPMs
between two RMT servers with a USB drive. The server
sun is connected to SUSE Customer Center, while
sirius is a server in an air-gapped network.
Log in on the server
sun.root@sun #rmt-cli syncroot@sun #rmt-cli mirrorConnect a USB drive, assumed to be
/dev/sdband mount it, for example, in/mnt/external.root@sun #mount /dev/sdb1 /mnt/externalExport the data about available repositories and products.
root@sun #rmt-cli export data /mnt/external/Export the list of enabled repositories. The exported file is required for exporting the repositories in the next step.
root@sun #rmt-cli export settings /mnt/external/Export mirrored RPM packages. Depending on the size of mirrored repositories, this can take a long time.
root@sun #rmt-cli export repos /mnt/external/
Unmount and unplug the disk from
sunand go tosirius.root@sun #umount /mnt/externalIf not yet done, set up RMT on
siriusby running theyast2 rmt. In case of an offline RMT setup, select on the screen.Connect the USB drive to
siriusand mount it in/mnt/external.root@sirius #mount /dev/sdb1 /mnt/externalImport the metadata about available repositories and products.
root@sirius #rmt-cli import data /mnt/external/Import mirrored RPM packages. Depending on the size of mirrored repositories, this can take a long time.
root@sirius #rmt-cli import repos /mnt/external/
Enable repositories as required on the
sirius. For details, see Section 4.4, “Enabling and disabling mirroring of repositories”.
If your air-gapped server (sirius) has many enabled
repositories, or if the enabled repositories change frequently, we
recommend exporting the repository settings from this server.
The server connected to SUSE Customer Center (sun) can then
import the exported settings. This ensures that sun
downloads all data required by sirius.
5 Configuring clients to use RMT #
Any machine running SUSE Linux Enterprise 12 or newer can be configured to register against RMT and download software updates from there, instead of communicating directly with SUSE Customer Center.
We recommend registering with the RMT server over a secured HTTPS protocol (all examples in this documentation use it). However, you can also register with the RMT server over an insecure HTTP protocol. Use this approach only if your setup benefits from it and only in a trusted environment where security is not crucial.
To configure clients to use the RMT server, use one of the following methods:
Provide the required information with boot parameters. See Section 5.1, “Configuring clients with boot parameters”.
Configure the clients using an AutoYaST profile. See Section 5.2, “Configuring clients with AutoYaST profile”.
Use the
rmt-client-setupcommand. See Section 5.3, “Configuring clients withrmt-client-setup”.Use the YaST registration module during installation or later. See Section 5.4, “Configuring clients with YaST”.
If you need the CA certificate of the RMT server, find it at
/etc/rmt/ssl/rmt-ca.crt and
https://RMT_SERVER/rmt.crt.
5.1 Configuring clients with boot parameters #
Any client can be configured to use RMT by providing the
regurl parameter during machine boot.
The parameter needs to be entered as
regurl=RMT_SERVER_URL. The
URL needs to be in the following format:
https://FQDN, with
FQDN being the fully qualified host name of
the RMT server. It must be identical to the FQDN of the server
certificate used on the RMT server. Example:
regurl=https://rmt.example.com
Make sure the values you enter are correct. If regurl
has not been specified correctly, the registration of the update source
fails.
If the RMT server gets a new certificate from an untrusted CA, the clients need to retrieve the new CA certificate file. YaST displays a dialog for importing a new certificate. If you confirm importing the new certificate, the old one is replaced with the new one.
5.2 Configuring clients with AutoYaST profile #
Clients can be configured to register with the RMT server via an AutoYaST profile. To learn about creating AutoYaST profiles and preparing for automatic installation, refer to the AutoYaST Guide. In this section, only RMT specific configuration is described.
To configure RMT specific data using AutoYaST, follow the steps for the relevant version of the RMT client.
As
root, start YaST and select › to start the graphical AutoYaST front-end.From a command line, you can start the graphical AutoYaST front-end with the
yast2 autoyastcommand.Open an existing profile using › . Create a profile based on the current system's configuration using › , or work with an empty profile.
Select › . An overview of the current configuration is shown.
Click .
Check , set the URL of the RMT server in , and you can set the . The possible values for the server URL are the same as for the kernel parameter
regurl. For the SSL certificate location, you can use either HTTP or HTTPS based URLs.Perform all other configurations needed for the systems to be deployed, then click to return to the main screen.
Select › and enter a file name for the profile, such as
autoinst.xml.
5.3 Configuring clients with rmt-client-setup #
The /usr/share/rmt/public/tools/rmt-client-setup
script is provided in the package rmt-server. This
script allows you to configure a client machine to use an RMT server.
It can also be used to reconfigure an existing client to use a different
RMT server.
To configure a client machine to use RMT with
rmt-client-setup, follow these steps:
Download
rmt-client-setupfrom the RMT server:#curl http://RMT_SERVER/tools/rmt-client-setup --output rmt-client-setupRun the script with the URL of the RMT server as a parameter.
#sh rmt-client-setup https://RMT_SERVER/Executing this script imports the RMT CA's certificate into the trusted store.
Alternatively, you can specify the correct fingerprint or path to the server certificate. For details, see
sh rmt-client-setup --help.The script downloads the server's CA certificate. Accept it by pressing Y. The tool now performs all necessary modifications to the client.
Use
SUSEConnectto add more products. For details, runSUSEConnect --help.
5.4 Configuring clients with YaST #
To configure a client to perform the registration against an RMT server,
use the YaST module
yast2 registration.
On the client, the credentials are not necessary, and you may leave the relevant fields empty. Click and enter its URL. Then click until the exit from the module.
5.5 Configuring clients for custom stand-alone repositories #
If you created a custom stand-alone repository on the RMT server, it is
not registered on client machines with SUSEConnect
because it has no parent product.
To add the repository manually, follow these steps:
Point your Web browser to the following RMT server URL:
https://RMT_SERVER_HOSTNAME/repo/
Navigate the browser through the directory structure to your custom repository's
repodata/subdirectory.On the client machine, add the discovered repository URL:
>sudozypper ar CUSTOM_REPO_URL CUSTOM_REPO_NAME
5.6 Listing accessible repositories #
To list available modules and repositories, use SUSEConnect
--list-extensions. Alternatively, you can also browse the
directory listing of the RMT server by visiting
https://RMT_SERVER/repo/
and its subdirectories.
5.7 Online migration of SUSE Linux Enterprise clients #
SUSE Linux Enterprise clients registered to RMT can be migrated online to the latest service pack of the same major release the same way as clients registered to SUSE Customer Center. Before starting the migration, make sure that RMT has the required products available and mirrored.
For detailed information on the online migration, see Book “Upgrade Guide”, Chapter 2 “Upgrade paths and methods”.
6 RMT tools and configuration files #
This chapter describes the most important scripts, configuration files and certificates shipped with RMT.
The rmt-cli command and its sub-commands are used to
manage the mirroring of repositories, registration of clients, and
reporting. systemd is used for starting, stopping, restarting the RMT
service and for checking its status.
The basic configuration for RMT is stored in the
/etc/rmt.conf.
6.1 RMT command line interface (rmt-cli) #
6.1.1 Overview #
The key command to manage the RMT is rmt-cli
(/usr/bin/rmt-cli). The rmt-cli
command should be used together with the sub-commands described in this
section. If the rmt-cli command is used alone, it prints
a list of all available sub-commands. To get help for individual
sub-commands, use man rmt-cli or rmt-cli help
[subcommand].
The following sub-commands are available:
rmt-cli syncSynchronize database with SUSE Customer Center.
rmt-cli productsList and modify products.
rmt-cli reposList and modify repositories.
rmt-cli mirrorMirror repositories.
rmt-cli systemsList and modify systems.
rmt-cli importImport commands for offline mode.
rmt-cli exportExport commands for offline mode.
rmt-cli versionShow RMT version.
The following sections explain each sub-command in detail.
6.1.2 sync #
This command triggers synchronization with the SUSE Customer Center instantly. The command
has no further options. Synchronization is also triggered each night by the
systemd timer rmt-server-sync.timer.
During synchronization, no data is uploaded to the SUSE Customer Center. This command for example updates local product definitions and repository data.
6.1.3 products #
List and modify products.
rmt-cli products list [--all] [--csv]Lists the products that are enabled for mirroring. Use the
--allflag to list all available products. Use the--csvflag to output the list in CSV format.lscan be used as a shortcut forlist.rmt-cli products enable [id | string] [--all-modules]Enables mandatory repositories of a product by its ID or product string. The
--all-modulesflag enables all modules of a product instead of only the recommended ones.rmt-cli products disable [id | string]Disables all repositories of a product by its ID or product string.
6.1.4 repos #
rmt-cli repos list [--all] [--csv]Lists the repositories that are enabled for mirroring. Use the
--allflag to list all available repositories. Use the--csvflag to output the list in CSV format.lscan be used as a shortcut forlist.rmt-cli repos enable [id]Enables mirroring of a single repository by its ID.
rmt-cli repos disable [id]Disables mirroring of a single repository by its ID.
rmt-cli repos cleanRemoves locally mirrored files of repositories that are not marked to be mirrored.
6.1.5 repos custom #
rmt-cli repos custom list [--csv]Lists all your custom repositories. Use the
--csvflag to output the list in CSV format.lscan be used as a shortcut forlist.rmt-cli repos custom add [url] [name] [--id]Adds a new custom repository. Use the
--idflag to specify a custom alphanumeric ID.rmt-cli repos custom enable [id]Enables mirroring of a custom repository.
rmt-cli repos custom disable [id]Disables mirroring of a custom repository.
rmt-cli repos custom remove [id]Removes a custom repository.
rmt-cli repos custom products [id]Lists the products attached to the custom repository with the given ID.
rmt-cli repos custom attach [id] [product id]Attaches an existing custom repository to a product.
rmt-cli repos custom detach [id] [product id]Detaches an existing custom repository from a product.
6.1.6 mirror #
rmt-cli mirrorStarts the mirroring process manually.
rmt-cli mirror allMirrors all enabled repositories.
rmt-cli mirror repository [IDs]Mirrors enabled repositories by a list of IDs.
rmt-cli mirror product [IDs]Mirrors enabled repositories for a product by a list of IDs.
6.1.7 systems #
rmt-cli systems listThis command lists registered systems.
rmt-cli systems scc-syncThis command forwards registered systems' data to SCC.
rmt-cli systems remove [TARGET]This command removes a system from RMT as identified by the column of the output of the
rmt-cli systems listcommand.rmt-cli systems purgeThis command lists and provides the option to delete inactive systems. It has the following options:
--before DATE—lists systems that have been inactive since DATE until now. Default is the last 3 months.--no-confirmation—allows the administrator to delete matching systems without confirmation.
#rmt-cli systems purge --before 2021-06-16 +------------+----------+---------------------+---------------------+----------+ | Login | Hostname | Registration time | Last seen | Products | +------------+----------+---------------------+---------------------+----------+ | SCC_c5b0.. | 6e485e48b| 2021-06-11 13:38:07 | 2021-06-11 13:52:01 | SLES/15..| | SCC_5fcf.. | node52 | 2021-06-15 13:29:24 | 2021-06-15 13:31:25 | SLES/15..| +------------+----------+---------------------+---------------------+----------+ Do you want to delete these systems? (y/n) y Purged systems that have not contacted this RMT since 2021-06-16.
6.1.8 import #
This command is required for the offline mode. For details, see Section 4.7, “Exporting and importing repositories”.
rmt-cli import data [path]Run this on the offline RMT to read the JSON files from the given path and fill the local database with data.
rmt-cli import repos [path]Run this on the offline RMT to import RPM packages.
6.1.9 export #
This command is required for the offline mode. For details, see Section 4.7, “Exporting and importing repositories”.
rmt-cli export data [path]Run this on an online RMT to get the latest data from SUSE Customer Center and save the result as JSON files at the specified path.
rmt-cli export settings [path]Run this on the offline RMT to save the settings for enabled repositories at a given path as
repos.json.rmt-cli export repos [path]Run this regularly on the online RMT to mirror the set of repositories specified in the
repos.jsonat the given path. The mirrored repository files are stored in subdirectories of the same path.
6.1.10 clean packages #
The rmt-cli clean packages command removes locally
mirrored dangling files and their database entries. A file is
considered to be dangling if it matches all the following characteristics:
It exists in a repository directory with primary and metadata
repomd.xmlfiles.It is no longer referenced in the metadata files.
It is at least two days old.
You can pass the following options to the rmt-cli clean
packages command:
- --dry-run
Generates a report of all affected files without actually cleaning them or their database entries.
- --verbose
Prints detailed information about each cleaned file.
- --non-interactive
Skips confirmation before proceeding with the cleaning process.
6.1.11 version #
Display the version of rmt-cli.
6.2 RMT systemd commands #
You can manage RMT-related services with the standard systemd
commands. The RMT server has the following services and timers:
rmt-server.targetA
systemdtarget that starts all required RMT components.rmt-server.serviceThe RMT server.
rmt-server-migration.serviceThis service migrates the database to the newest schema, if required. There is no need to manually interact with this service.
rmt-server-sync.timerThis timer is responsible for periodically synchronizing all repository product data from the SUSE Customer Center.
rmt-server-mirror.timerThis timer is responsible for periodically synchronizing all RPMs from the SUSE Customer Center.
Use systemctl to manage the RMT services and timers.
6.3 RMT configuration files #
The main RMT configuration file is /etc/rmt.conf.
You can set most of the options with the YaST RMT Server module.
6.3.1 /etc/rmt.conf #
The only supported way of doing the initial configuration is with
yast2 rmt as described in Section 2.5, “RMT configuration with YaST”. Only the proxy
configuration needs to be entered manually. The other configuration
parameters are documented for reference.
All available configuration options can be found in the
/etc/rmt.conf file.
6.3.1.1 Mirroring settings #
The mirroring section lets you adjust mirroring
behavior.
mirror_srcDecides whether to mirror source RPM packages (architecture is
src).dedup_methodCreates hard links during mirroring when set to
hardlink. If the file system does not support hard links, it can be set tocopyinstead. Possible values:hardlink,copy.
6.3.1.2 HTTP client settings #
The http_client section defines the global HTTP
connection settings of RMT.
verboseEnables additional debug output to the
systemdjournal.proxyThe proxy server URL including the protocol and the port number. For example:
http://proxy_url:8080.noproxyA list of domains that should not go through the proxy, separated by commas. For example:
localhost.mylocaldomain.proxy_authThis setting determines the proxy authentication mechanism. Possible values are:
none,basic,digest,gssnegotiate,ntlm,digest_ie,ntlm_wb.proxy_userThe proxy server user name.
proxy_passwordThe proxy server password.
low_speed_limitLower speed limit when a download should be aborted in bytes/sec.
low_speed_timeTime until a download gets aborted, when download speed is below
low_speed_limit.
6.3.1.3 Settings for accessing SUSE repositories #
The scc section contains your mirroring
credentials for contacting the SUSE Customer Center. To obtain your mirroring
credentials, see Section 4.1, “Mirroring credentials”.
Valid configuration keys for the section are:
usernameMirroring credentials user name.
passwordMirroring credentials password.
6.3.1.4 Web server settings #
The web_server section lets you tune the performance of your RMT server.
min_threadsSpecifies the minimum number of threads that an RMT server worker should spawn.
Acceptable values: Integer greater than or equal to 1.
max_threadsSpecifies the maximum number of threads that an RMT server worker should spawn.
Acceptable values: Integer greater than or equal to 1.
workersSpecifies the number of Web workers for RMT.
Acceptable values: Integer greater than or equal to 1.
6.3.2 SSL certificates and HTTPS #
By default access to API endpoints consumed by
SUSEConnect is limited to HTTPS only. nginx is
configured to use an SSL certificate and a private key from the following
locations:
Certificate:
/etc/rmt/ssl/rmt-server.crtPrivate key:
/etc/rmt/ssl/rmt-server.key
The YaST RMT module generates a custom certificate authority which is used to sign HTTPS certificates. This means that to register, this certificate authority must be trusted by the client machines:
For registrations during installation from the media or with YaST Registration module, a message will appear, prompting to trust the server certificate.
For registering a client system on the command line, use the
rmt-client-setupscript. For details, see Section 5.3, “Configuring clients withrmt-client-setup”.
7 Backing up an RMT server #
This chapter explains how to create a backup of your RMT server and how to restore from it.
7.1 Creating a backup #
This procedure details how to create a full backup of your RMT server.
It is assumed that you have an external disk or network share mounted in
/mnt/backup that serves as a target for the backup.
Change to the backup directory.
#cd /mnt/backupCreate a file containing a dump of your SQL database. You need to provide the password you set for the
rmtdatabase user during the installation.#mysqldump -u rmt -p rmt > rmt_backup.sqlOptionally, create a copy of your mirrored data.
#mkdir repos#rmt-cli export repos ./repos/
7.2 Restoring a backup #
This procedure details how to restore your RMT server from a backup
created in Section 7.1, “Creating a backup”. It is assumed that
the backup is mounted in /mnt/backup. It is also
assumed that you are restoring the server on a newly installed SLES.
Install and configure the RMT server as described in Chapter 2, RMT installation and configuration.
Go to the backup directory.
#cd /mnt/backup/Use
mysqlto remove the newly created database and import the data.#mysql -u rmt -pEnter password: Welcome to the MariaDB monitor. Commands end with ; or \g. [...]MariaDB [(none)]>DROP DATABASE rmt;Query OK, 14 rows affected (0.84 sec)MariaDB [(none)]>CREATE DATABASE rmt;Query OK, 1 row affected (0.00 sec)MariaDB [(none)]>use rmt;Database changedMariaDB [rmt]>source rmt_backup.sql;[...]MariaDB [rmt]>quitOptionally, import the exported repositories.
#rmt-cli import repos ./repos/Synchronize your data and update your repositories.
#rmt-cli sync#rmt-cli mirror
8 Managing TLS/SSL certificates #
8.1 Regenerating HTTPS certificates #
HTTPS certificates should be regenerated before they expire or to include additional common alternative names. No additional actions are required on the client machines registered to the RMT server if only HTTPS certificates are regenerated.
Stop nginx and rmt-server services.
#systemctl stop nginx#systemctl stop rmt-serverRemove previously generated certificates.
#rm /etc/rmt/ssl/rmt-server.*Run the
yast rmtmodule as described in Section 2.5, “RMT configuration with YaST”.
8.2 Regenerating CA certificates and HTTPS certificates #
CA certificates can be regenerated after they have expired or in case of security issues.
The newly generated CA certificate must be imported on all clients
registered to the RMT server. This can be done by running the
rmt-client-setup script on the client machines as
described in Section 5.3, “Configuring clients with rmt-client-setup”.
Stop nginx and rmt-server services.
#systemctl stop nginx#systemctl stop rmt-serverRemove previously generated CA and HTTPS certificates.
#rm /etc/rmt/ssl/rmt-ca.*#rm /etc/rmt/ssl/rmt-server.*Run the
yast rmtmodule as described in Section 2.5, “RMT configuration with YaST”.
9 Deploying a SUSE Linux Enterprise Server instance to support RMT in the public cloud #
You can deploy a SUSE Linux Enterprise Server instance to support RMT in Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. RMT is included in SLES starting with version 15.
The following example shows a generic cloud architecture for the RMT deployment. Your deployment may look different based on your networking requirements.
9.1 Using a bring-your-own-subscription image #
SUSE provides images for SLES in Amazon Web Services, Google Cloud and Microsoft Azure. There are two types of images available: PAYG (Pay-As-You-Go) and BYOS (Bring-Your-Own-Subscription). These images are updated at regular intervals and it is suggested that you deploy new instances from the latest version of the image to ensure the most recent security updates are in place. To support RMT deployment, we recommend deploying an RMT instance from a BYOS image.
9.1.1 Finding images in the cloud marketplace #
The location of the relevant image in each of the cloud provider is shown below:
It is recommended to start with an instance type that has at least
two vCPUs and a minimum of 8 GB RAM to support the RMT deployment.
For example, on Amazon EC2, this could be a t3.large
instance type, and in Microsoft Azure, it could be a B2as_v2
The instance can be rightsized as needed and depends on the number of clients being managed and updated by the RMT server.
9.1.2 Registering the SLES instance #
After the SLES instance deployment, you must register the instance with the SUSE Customer Center.
Registering with the SUSE Customer Center requires a SUSE account. If you do not have a SUSE account yet, go to the SUSE Customer Center home page (https://scc.suse.com/) to create one.
To connect your instance:
AWS:
>ssh -i SSH_KEY EC2_USER_ID@SERVER_IP
Google Cloud:
>gcloud compute ssh GCE_INSTANCE_IP
Azure:
>ssh AZURE_USER_ID@SERVER_IP
To register the SLES instance with SCC:
>sudoSUSEConnect -e EMAIL_ADDRESS -r REGISTRATION_CODE
The registration code is available once you log in to SCC.
9.2 Considerations when using RMT #
You must consider the following requirements when you use RMT:
- Disk space
The RMT server requires sufficient disk space to mirror the repositories. Downloaded packages are available in
/var/lib/rmt/public/repo/. Disk space is dependent on the number of repositories you mirror. We recommend a minimum of 1.5 times the total size of all enabled repositories. It is a best practice to provision an additional disk volume to support this requirement. You can either mount the volume to/var/lib/rmt/public/repo/on instance creation or immediately after the launch. For Azure, this is an additional disk volume. For AWS, it is an Amazon EBS volume and for GCP, it is a persistent disk volume .- IP or DNS resolution
A static IP address or a DNS name is required in order for clients to connect to the RMT server. In Azure, AWS and GCP, a DNS provided by the Cloud Service Provider (CSP) is assigned when the instance is launched. This IP or DNS may change if the instance is re-created. For Azure, consider using a static IP address to provide a consistent connection point for your clients. In AWS, this would be an elastic IP or Route53. In GCP, this would be a cloud DNS record that uses a static IP address.
- Connectivity for the RMT server
The RMT server can connect to SCC on ports 80 and 443. There are many ways to provide connectivity. For example, in AWS, connectivity to SCC can be provided via an AWS Internet Gateway, an AWS NAT Gateway, or via a local data center (VPN/DX Connection) but this is depends on whether the RMT instance is in a public or private subnet. GCP provides direct access to the Internet via the VPC routes or Cloud NAT services. Azure offers similar services.
- Connectivity for clients
Clients can connect to RMT on ports 80 and 443. When launching the SLES instance to support RMT, check if network connectivity allows inbound access to the RMT server from your clients (HTTP/HTTPS). For AWS, when a SLES instance is launched to support RMT, it is possible to use an existing AWS security group or a new one. The security group must be configured to allow inbound access to the RMT server from your clients. For GCP, the firewall rules must be configured to allow inbound access to the RMT server from your clients.
9.3 More information #
https://documentation.suse.com/sles/15-SP6/html/SLES-all/cha-rmt-mirroring.html#sec-rmt-mirroring-credentials Organization credentials to create a local mirror of the SUSE Linux Enterprise repositories.
https://documentation.suse.com/sles/15-SP6/html/SLES-all/cha-register-sle.html#sec-register-sle-installation Register and activate SUSE Linux Enterprise Server with the SUSE Customer Center.
A GNU licenses #
This appendix contains the GNU Free Documentation License version 1.2.
GNU Free Documentation License #
Copyright (C) 2000, 2001, 2002 Free Software Foundation, Inc. 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA. Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
0. PREAMBLE #
The purpose of this License is to make a manual, textbook, or other functional and useful document "free" in the sense of freedom: to assure everyone the effective freedom to copy and redistribute it, with or without modifying it, either commercially or non-commercially. Secondarily, this License preserves for the author and publisher a way to get credit for their work, while not being considered responsible for modifications made by others.
This License is a kind of "copyleft", which means that derivative works of the document must themselves be free in the same sense. It complements the GNU General Public License, which is a copyleft license designed for free software.
We have designed this License to use it for manuals for free software, because free software needs free documentation: a free program should come with manuals providing the same freedoms that the software does. But this License is not limited to software manuals; it can be used for any textual work, regardless of subject matter or whether it is published as a printed book. We recommend this License principally for works whose purpose is instruction or reference.
1. APPLICABILITY AND DEFINITIONS #
This License applies to any manual or other work, in any medium, that contains a notice placed by the copyright holder saying it can be distributed under the terms of this License. Such a notice grants a world-wide, royalty-free license, unlimited in duration, to use that work under the conditions stated herein. The "Document", below, refers to any such manual or work. Any member of the public is a licensee, and is addressed as "you". You accept the license if you copy, modify or distribute the work in a way requiring permission under copyright law.
A "Modified Version" of the Document means any work containing the Document or a portion of it, either copied verbatim, or with modifications and/or translated into another language.
A "Secondary Section" is a named appendix or a front-matter section of the Document that deals exclusively with the relationship of the publishers or authors of the Document to the Document's overall subject (or to related matters) and contains nothing that could fall directly within that overall subject. (Thus, if the Document is in part a textbook of mathematics, a Secondary Section may not explain any mathematics.) The relationship could be a matter of historical connection with the subject or with related matters, or of legal, commercial, philosophical, ethical or political position regarding them.
The "Invariant Sections" are certain Secondary Sections whose titles are designated, as being those of Invariant Sections, in the notice that says that the Document is released under this License. If a section does not fit the above definition of Secondary then it is not allowed to be designated as Invariant. The Document may contain zero Invariant Sections. If the Document does not identify any Invariant Sections then there are none.
The "Cover Texts" are certain short passages of text that are listed, as Front-Cover Texts or Back-Cover Texts, in the notice that says that the Document is released under this License. A Front-Cover Text may be at most 5 words, and a Back-Cover Text may be at most 25 words.
A "Transparent" copy of the Document means a machine-readable copy, represented in a format whose specification is available to the general public, that is suitable for revising the document straightforwardly with generic text editors or (for images composed of pixels) generic paint programs or (for drawings) some widely available drawing editor, and that is suitable for input to text formatters or for automatic translation to a variety of formats suitable for input to text formatters. A copy made in an otherwise Transparent file format whose markup, or absence of markup, has been arranged to thwart or discourage subsequent modification by readers is not Transparent. An image format is not Transparent if used for any substantial amount of text. A copy that is not "Transparent" is called "Opaque".
Examples of suitable formats for Transparent copies include plain ASCII without markup, Texinfo input format, LaTeX input format, SGML or XML using a publicly available DTD, and standard-conforming simple HTML, PostScript or PDF designed for human modification. Examples of transparent image formats include PNG, XCF and JPG. Opaque formats include proprietary formats that can be read and edited only by proprietary word processors, SGML or XML for which the DTD and/or processing tools are not generally available, and the machine-generated HTML, PostScript or PDF produced by some word processors for output purposes only.
The "Title Page" means, for a printed book, the title page itself, plus such following pages as are needed to hold, legibly, the material this License requires to appear in the title page. For works in formats which do not have any title page as such, "Title Page" means the text near the most prominent appearance of the work's title, preceding the beginning of the body of the text.
A section "Entitled XYZ" means a named subunit of the Document whose title either is precisely XYZ or contains XYZ in parentheses following text that translates XYZ in another language. (Here XYZ stands for a specific section name mentioned below, such as "Acknowledgements", "Dedications", "Endorsements", or "History".) To "Preserve the Title" of such a section when you modify the Document means that it remains a section "Entitled XYZ" according to this definition.
The Document may include Warranty Disclaimers next to the notice which states that this License applies to the Document. These Warranty Disclaimers are considered to be included by reference in this License, but only as regards disclaiming warranties: any other implication that these Warranty Disclaimers may have is void and has no effect on the meaning of this License.
2. VERBATIM COPYING #
You may copy and distribute the Document in any medium, either commercially or non-commercially, provided that this License, the copyright notices, and the license notice saying this License applies to the Document are reproduced in all copies, and that you add no other conditions whatsoever to those of this License. You may not use technical measures to obstruct or control the reading or further copying of the copies you make or distribute. However, you may accept compensation in exchange for copies. If you distribute a large enough number of copies you must also follow the conditions in section 3.
You may also lend copies, under the same conditions stated above, and you may publicly display copies.
3. COPYING IN QUANTITY #
If you publish printed copies (or copies in media that commonly have printed covers) of the Document, numbering more than 100, and the Document's license notice requires Cover Texts, you must enclose the copies in covers that carry, clearly and legibly, all these Cover Texts: Front-Cover Texts on the front cover, and Back-Cover Texts on the back cover. Both covers must also clearly and legibly identify you as the publisher of these copies. The front cover must present the full title with all words of the title equally prominent and visible. You may add other material on the covers in addition. Copying with changes limited to the covers, as long as they preserve the title of the Document and satisfy these conditions, can be treated as verbatim copying in other respects.
If the required texts for either cover are too voluminous to fit legibly, you should put the first ones listed (as many as fit reasonably) on the actual cover, and continue the rest onto adjacent pages.
If you publish or distribute Opaque copies of the Document numbering more than 100, you must either include a machine-readable Transparent copy along with each Opaque copy, or state in or with each Opaque copy a computer-network location from which the general network-using public has access to download using public-standard network protocols a complete Transparent copy of the Document, free of added material. If you use the latter option, you must take reasonably prudent steps, when you begin distribution of Opaque copies in quantity, to ensure that this Transparent copy will remain thus accessible at the stated location until at least one year after the last time you distribute an Opaque copy (directly or through your agents or retailers) of that edition to the public.
It is requested, but not required, that you contact the authors of the Document well before redistributing any large number of copies, to give them a chance to provide you with an updated version of the Document.
4. MODIFICATIONS #
You may copy and distribute a Modified Version of the Document under the conditions of sections 2 and 3 above, provided that you release the Modified Version under precisely this License, with the Modified Version filling the role of the Document, thus licensing distribution and modification of the Modified Version to whoever possesses a copy of it. In addition, you must do these things in the Modified Version:
Use in the Title Page (and on the covers, if any) a title distinct from that of the Document, and from those of previous versions (which should, if there were any, be listed in the History section of the Document). You may use the same title as a previous version if the original publisher of that version gives permission.
List on the Title Page, as authors, one or more persons or entities responsible for authorship of the modifications in the Modified Version, together with at least five of the principal authors of the Document (all of its principal authors, if it has fewer than five), unless they release you from this requirement.
State on the Title page the name of the publisher of the Modified Version, as the publisher.
Preserve all the copyright notices of the Document.
Add an appropriate copyright notice for your modifications adjacent to the other copyright notices.
Include, immediately after the copyright notices, a license notice giving the public permission to use the Modified Version under the terms of this License, in the form shown in the Addendum below.
Preserve in that license notice the full lists of Invariant Sections and required Cover Texts given in the Document's license notice.
Include an unaltered copy of this License.
Preserve the section Entitled "History", Preserve its Title, and add to it an item stating at least the title, year, new authors, and publisher of the Modified Version as given on the Title Page. If there is no section Entitled "History" in the Document, create one stating the title, year, authors, and publisher of the Document as given on its Title Page, then add an item describing the Modified Version as stated in the previous sentence.
Preserve the network location, if any, given in the Document for public access to a Transparent copy of the Document, and likewise the network locations given in the Document for previous versions it was based on. These may be placed in the "History" section. You may omit a network location for a work that was published at least four years before the Document itself, or if the original publisher of the version it refers to gives permission.
For any section Entitled "Acknowledgements" or "Dedications", Preserve the Title of the section, and preserve in the section all the substance and tone of each of the contributor acknowledgements and/or dedications given therein.
Preserve all the Invariant Sections of the Document, unaltered in their text and in their titles. Section numbers or the equivalent are not considered part of the section titles.
Delete any section Entitled "Endorsements". Such a section may not be included in the Modified Version.
Do not retitle any existing section to be Entitled "Endorsements" or to conflict in title with any Invariant Section.
Preserve any Warranty Disclaimers.
If the Modified Version includes new front-matter sections or appendices that qualify as Secondary Sections and contain no material copied from the Document, you may at your option designate some or all of these sections as invariant. To do this, add their titles to the list of Invariant Sections in the Modified Version's license notice. These titles must be distinct from any other section titles.
You may add a section Entitled "Endorsements", provided it contains nothing but endorsements of your Modified Version by various parties--for example, statements of peer review or that the text has been approved by an organization as the authoritative definition of a standard.
You may add a passage of up to five words as a Front-Cover Text, and a passage of up to 25 words as a Back-Cover Text, to the end of the list of Cover Texts in the Modified Version. Only one passage of Front-Cover Text and one of Back-Cover Text may be added by (or through arrangements made by) any one entity. If the Document already includes a cover text for the same cover, previously added by you or by arrangement made by the same entity you are acting on behalf of, you may not add another; but you may replace the old one, on explicit permission from the previous publisher that added the old one.
The author(s) and publisher(s) of the Document do not by this License give permission to use their names for publicity for or to assert or imply endorsement of any Modified Version.
5. COMBINING DOCUMENTS #
You may combine the Document with other documents released under this License, under the terms defined in section 4 above for modified versions, provided that you include in the combination all of the Invariant Sections of all of the original documents, unmodified, and list them all as Invariant Sections of your combined work in its license notice, and that you preserve all their Warranty Disclaimers.
The combined work need only contain one copy of this License, and multiple identical Invariant Sections may be replaced with a single copy. If there are multiple Invariant Sections with the same name but different contents, make the title of each such section unique by adding at the end of it, in parentheses, the name of the original author or publisher of that section if known, or else a unique number. Make the same adjustment to the section titles in the list of Invariant Sections in the license notice of the combined work.
In the combination, you must combine any sections Entitled "History" in the various original documents, forming one section Entitled "History"; likewise combine any sections Entitled "Acknowledgements", and any sections Entitled "Dedications". You must delete all sections Entitled "Endorsements".
6. COLLECTIONS OF DOCUMENTS #
You may make a collection consisting of the Document and other documents released under this License, and replace the individual copies of this License in the various documents with a single copy that is included in the collection, provided that you follow the rules of this License for verbatim copying of each of the documents in all other respects.
You may extract a single document from such a collection, and distribute it individually under this License, provided you insert a copy of this License into the extracted document, and follow this License in all other respects regarding verbatim copying of that document.
7. AGGREGATION WITH INDEPENDENT WORKS #
A compilation of the Document or its derivatives with other separate and independent documents or works, in or on a volume of a storage or distribution medium, is called an "aggregate" if the copyright resulting from the compilation is not used to limit the legal rights of the compilation's users beyond what the individual works permit. When the Document is included in an aggregate, this License does not apply to the other works in the aggregate which are not themselves derivative works of the Document.
If the Cover Text requirement of section 3 is applicable to these copies of the Document, then if the Document is less than one half of the entire aggregate, the Document's Cover Texts may be placed on covers that bracket the Document within the aggregate, or the electronic equivalent of covers if the Document is in electronic form. Otherwise they must appear on printed covers that bracket the whole aggregate.
8. TRANSLATION #
Translation is considered a kind of modification, so you may distribute translations of the Document under the terms of section 4. Replacing Invariant Sections with translations requires special permission from their copyright holders, but you may include translations of some or all Invariant Sections in addition to the original versions of these Invariant Sections. You may include a translation of this License, and all the license notices in the Document, and any Warranty Disclaimers, provided that you also include the original English version of this License and the original versions of those notices and disclaimers. In case of a disagreement between the translation and the original version of this License or a notice or disclaimer, the original version will prevail.
If a section in the Document is Entitled "Acknowledgements", "Dedications", or "History", the requirement (section 4) to Preserve its Title (section 1) will typically require changing the actual title.
9. TERMINATION #
You may not copy, modify, sublicense, or distribute the Document except as expressly provided for under this License. Any other attempt to copy, modify, sublicense or distribute the Document is void, and will automatically terminate your rights under this License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated so long as such parties remain in full compliance.
10. FUTURE REVISIONS OF THIS LICENSE #
The Free Software Foundation may publish new, revised versions of the GNU Free Documentation License from time to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns. See https://www.gnu.org/copyleft/.
Each version of the License is given a distinguishing version number. If the Document specifies that a particular numbered version of this License "or any later version" applies to it, you have the option of following the terms and conditions either of that specified version or of any later version that has been published (not as a draft) by the Free Software Foundation. If the Document does not specify a version number of this License, you may choose any version ever published (not as a draft) by the Free Software Foundation.
ADDENDUM: How to use this License for your documents #
Copyright (c) YEAR YOUR NAME. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”.
If you have Invariant Sections, Front-Cover Texts and Back-Cover Texts, replace the “with...Texts.” line with this:
with the Invariant Sections being LIST THEIR TITLES, with the Front-Cover Texts being LIST, and with the Back-Cover Texts being LIST.
If you have Invariant Sections without Cover Texts, or some other combination of the three, merge those two alternatives to suit the situation.
If your document contains nontrivial examples of program code, we recommend releasing these examples in parallel under your choice of free software license, such as the GNU General Public License, to permit their use in free software.