This guide explains how to use SUSE Linux Enterprise in public clouds.
Copyright © 2021–2026 SUSE LLC and contributors. All rights reserved.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”.
For SUSE trademarks, see https://www.suse.com/company/legal/. All third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof.
About this guide #
This chapter provides information about this guide itself and how to use it.
This guide explains how to use SUSE Linux Enterprise in public clouds.
This guide contains the following:
- Chapter 1, Getting started
SUSE—together with the cloud service providers—offers different products and plans to cater to a variety of use cases. Find out which works best for you.
- Chapter 2, Public cloud images
SUSE offers a variety of different product images for different use cases in partner cloud provider frameworks. Learn how to find the image that meets your use case.
- Chapter 3, Managing cloud instances
SUSE Linux Enterprise in public clouds is managed almost like on bare metal or in virtual environments. Learn about what is different in the cloud.
1 Available documentation #
- Online documentation
Our documentation is available online at https://documentation.suse.com. Browse or download the documentation in various formats.
Note: Latest updatesThe latest updates are usually available in the English-language version of this documentation.
- SUSE Knowledgebase
If you run into an issue, check out the Technical Information Documents (TIDs) that are available online at https://www.suse.com/support/kb/. Search the SUSE Knowledgebase for known solutions driven by customer need.
- Release notes
For release notes, see https://www.suse.com/releasenotes/.
- On your system
For offline use, the release notes are also available under
/usr/share/doc/release-noteson your system. The documentation for individual packages is available at/usr/share/doc/packages.Many commands are also described in their manual pages. To view them, run
man, followed by a specific command name. If themancommand is not installed on your system, install it withsudo zypper install man.
2 Improving the documentation #
Your feedback and contributions to this documentation are welcome. The following channels for giving feedback are available:
- Service requests and support
For services and support options available for your product, see https://www.suse.com/support/.
To open a service request, you need a SUSE subscription registered at SUSE Customer Center. Go to https://scc.suse.com/support/requests, log in and click .
- Bug reports
Report issues with the documentation at https://bugzilla.suse.com/.
To simplify this process, click the icon next to a headline in the HTML version of this document. This preselects the right product and category in Bugzilla and adds a link to the current section. You can start typing your bug report right away.
A Bugzilla account is required.
- Contributions
To contribute to this documentation, click the icon next to a headline in the HTML version of this document. This will take you to the source code on GitHub, where you can open a pull request.
A GitHub account is required.
Note: only available for EnglishThe icons are only available for the English version of each document. For all other languages, use the icons instead.
For more information about the documentation environment used for this documentation, see the repository's README.
You can also report errors and send feedback concerning the documentation to <doc-team@suse.com>. Include the document title, the product version, and the publication date of the document. Additionally, include the relevant section number and title (or provide the URL) and provide a concise description of the problem.
3 Documentation conventions #
The following notices and typographic conventions are used in this document:
/etc/passwd: Directory names and file namesPLACEHOLDER: Replace PLACEHOLDER with the actual value
PATH: An environment variablels,--help: Commands, options and parametersuser: The name of a user or grouppackage_name: The name of a software package
Alt, Alt–F1: A key to press or a key combination. Keys are shown in uppercase, as on a keyboard.
, › : Menu items, buttons
AMD/Intel This paragraph is only relevant for the AMD64/Intel 64 architectures. The arrows mark the beginning and the end of the text block.
IBM Z, POWER This paragraph is only relevant for the architectures
IBM ZandPOWER. The arrows mark the beginning and the end of the text block.Chapter 1, “Example chapter”: A cross-reference to another chapter in this guide.
Commands that must be run with
rootprivileges. You can also prefix these commands with thesudocommand to run them as a non-privileged user:#command>sudocommandCommands that can be run by non-privileged users:
>commandCommands can be split into two or multiple lines by a backslash character (
\) at the end of a line. The backslash informs the shell that the command invocation will continue after the end of the line:>echoa b \ c dA code block that shows both the command (preceded by a prompt) and the respective output returned by the shell:
>commandoutputNotices
Warning: Warning noticeVital information you must know before proceeding. Warns you about security issues, potential loss of data, damage to hardware, or physical hazards.
Important: Important noticeImportant information you should know before proceeding.
Note: Note noticeAdditional information, for example about differences in software versions.
Tip: Tip noticeHelpful information, like a guideline or a piece of practical advice.
Compact Notices
Additional information, for example, about differences in software versions.
Helpful information, like a guideline or a piece of practical advice.
1 Getting started #
SUSE—together with the cloud service providers—offers different products and plans to cater to a variety of use cases. Find out which works best for you.
1.1 Products #
The following SUSE products are available for public cloud:
To constantly adjust and improve SUSE's offerings, availability of products and versions is subject to change and may differ between cloud frameworks.
1.2 Cloud service providers #
SUSE publishes product images in the following cloud service provider (CSP) frameworks:
Amazon Web Services
Microsoft Azure
Google Cloud
SUSE images are also available in other providers' frameworks. These images are generally created and published by the provider.
Please note that this list may change. If you are interested in becoming a SUSE partner, visit https://www.suse.com/partners/cloud-service-providers/ for more information.
1.3 Plans #
SUSE—together with the cloud service providers—offers different plans to cater to a variety of use cases. While details differ depending on the cloud framework, usually there are two types of subscriptions.
- Bring your own subscription (BYOS)
Bring your own subscription(BYOS) images are useful if you already have a support contract with SUSE and want to move your workloads to the public cloud. An instance launched from a BYOS image is equivalent to a physical machine that just received a SUSE Linux Enterprise Server installation from the SLES installation image. After creation, useregistercloudguestto register the instance with the SUSE-operated update infrastructure in the cloud framework or use theSUSEConnectto register the system with SUSE Customer Center using the entitlements you already have. Connect your system to your own running RMT or SUSE Manager infrastructure in the same way you connect systems in your data center.BYOS instances make it easier to manage extensions such as LTSS or kernel live-patching. Extensions for PAYG instances can only be used in conjunction with SUSE Manager.
- Pay as you go (PAYG)
Pay as you go(PAYG) images are used to create on-demand instances. When an instance is first booted, it automatically registers with a local update server. Once the system finishes booting, it is ready to use.Create an instance when you need it and delete it when you are done. While in use, you have access to updates from SUSE through the automatically configured repositories. You only pay for the resources you use. Upcharges over the basic cloud prices may apply, depending on the image and framework.
PAYG instances include support through the cloud service provider or priority support from SUSE For details, refer to Section 1.4, “Support”.
In summary, if you already have a direct relationship with SUSE you generally want to start out with BYOS. You can still use PAYG for on-demand excess capacity.
|
Plan |
Bring your own subscription (BYOS) |
Pay as you go (PAYG) |
|---|---|---|
|
Customer relationship |
with CSP and SUSE |
with CSP |
|
Pricing |
per instance and license |
per use |
|
Registration |
with a local update server, your RMT or SUSE Manager infrastructure, or directly with the SUSE Customer Center |
with a local update server upon instance creation |
|
Support |
full support by SUSE |
by CSP; by SUSE only for SUSE Marketplace listings, meaning listings where the seller in the listing is SUSE |
|
Extended ESPOS1 or LTSS2 support |
available |
only if included in image base product |
|
Extensions |
no limitations |
only with SUSE Manager |
| 1 ESPOS: Extended Service Pack Overlay Support |
| 2 LTSS: Long-Term Service Pack Support |
Switching from BYOS to PAYG or vice-versa is possible on Microsoft Azure through the
Microsoft Azure Hybrid Benefit program and on Google Compute Engine through
Flexible Licenses. For all other cloud providers, you remain on the plan you
initially selected for as long as the instance is running. The only way to switch
plans is to start with the other image and rebuild your system.
For more information on how to switch plans on Microsoft Azure, refer to https://www.suse.com/c/upgrades-for-azure-hybrid-benefit/. For Google Compute Engine refer to https://www.suse.com/c/switching-licensing-models-on-google-cloud-for-sles-and-sles-for-sap-instances-flexible-licenses/.
Registering PAYG instances with the SUSE Customer Center or your own RMT server will create conflicts that are not easily solved. Only register BYOS instances. PAYG instances are automatically registered against the correct update server.
1.4 Support #
Regardless of the public cloud you use and the plan you choose, SUSE has you covered with support. Support is dependent on whether you "bring your own subscription" (BYOS) or you use SUSE Linux Enterprise "on-demand" (PAYG). For more information about BYOS and PAYG, refer to Section 1.3, “Plans”.
- BYOS
BYOS instances are supported by SUSE under the terms of your SUSE subscription. For an overview of SUSE's support subscriptions, refer to https://www.suse.com/support/.
- PAYG
Regular PAYG instances include support through the cloud service provider which in turn is supported by SUSE. If you have a problem, always contact your CSP for assistance. They provide first and second level support, and will work with SUSE for L3 support as required.
Note: Microsoft Azure basic imagesMicrosoft Azure also offers a basic PAYG image that only includes updates. Instances created from this image are not eligible for support.
- PAYG with SUSE Priority Support
SUSE offers 24x7 priority support for the PAYG versions of the following products:
SUSE Linux Enterprise Micro
SUSE Manager
Rancher Prime
You can transact priority support through the Amazon Web Services and Microsoft Azure marketplaces, where you will see two different listings: A global one and one for
EMEA Orders Only. Two listings are needed as there are different regulations to comply with, but the images and the support offering are identical. Select the correct listing for your organization's CSP account:For Amazon Web Services, it depends on the
tax addressof the account, see https://aws.amazon.com/tax-help/location.For Microsoft Azure, it depends on the
sold toaddress of the account, see https://learn.microsoft.com/azure/cost-management-billing/manage/change-azure-account-profile.For Google Cloud, it depends on the
billing countryof the account, see https://support.google.com/cloudidentity/answer/3530790.
For a complete list of countries that are eligble to transact priority support through the CSP's marketplaces, and the correct listing for each country, refer to Appendix B, Geographical availability.
Important: Other countriesIf the billing or tax address of your organization's CSP account is located in a country not listed in Appendix B, Geographical availability, you currently cannot transact priority support through the CSP's marketplaces.
SUSE is committed to making priority support available in more countries. In the meantime, you can still use SUSE PAYG products with regular support from the CSP. If you want support by SUSE, use a BYOS version.
For more information, refer to the SUSE Technical Support Policy and the support statement for SUSE Linux Enterprise in Appendix A, Support.
For information on how to contact the SUSE support team and report problems, refer to the SUSE Technical Support Guide.
1.5 Supported instance types #
To find out what types of instances are supported by each provider, refer to the SUSE Public Cloud Instance Support Matrix. Select your SUSE Linux Enterprise product and your cloud provider to see a list of supported instance types.
2 Public cloud images #
SUSE offers a variety of different product images for different use cases in partner cloud provider frameworks. Learn how to find the image that meets your use case.
2.1 Image lifecycle #
All SUSE public cloud images follow a refresh cycle up to the point of deletion. The refresh cycle follows a 'rolling' three month time frame. What this means:
Images in
activeandinactivestates are refreshed every three months. Replaced images are moved to thedeprecatedstate.If a critical security vulnerability occurs, images in
activeandinactivestates are updated as soon as possible once the fix for the affected code is available. For images inactiveandinactivestates the three month timer restarts with this forced replacement.SUSE is committed to address all security vulnerabilities disclosed through the
Common Vulnerabilities and Exposures process(CVE) and a score of 9.0 or greater in theCommon Vulnerability Scoring System(CVSS). For more information about the effects and rating of CVEs, refer to the SUSE CVE database.
The life cycle of an image consists of four different states:
- Active
Active images are fully supported and refreshed at least every three months. The duration lasts until the image is replaced by a newer image version.
- Inactive
Inactive images are supported following the rules of LTSS or ESPOS and will get refreshed at least every three months. The duration term is defined by the product. For more information, refer to https://www.suse.com/de-de/support/policy-products/#cloud
- Deprecated
Deprecated images may no longer be supported. The status of support depends on the support status of the product in the image. Deprecated images do not get refreshed and are not made available in regions added after an image has been set to
deprecated. At the end of the six month deprecation period, images are subject to deletion. It is strongly discouraged to use deprecated images to create new instances.- Deleted
Deleted images are no longer supported or available for instance creation.
active images for new instances
It is strongly recommended to only use active images to
launch instances for new deployments.
2.2 Naming scheme #
Names for SUSE's public cloud images consist of multiple parts that contain information about the product, its version, a time stamp indicating the release date of the image, and more. The general naming scheme for SUSE's public cloud images is as follows:
PRODUCT-FLAVOR-vVERSION-VIRTUALIZATION-STORAGE-ARCHITECTURE-TAXID-GEN
Not all components of this naming scheme are used in all frameworks.
PRODUCTAbbreviated name of the product in lower case letters, e.g.
suse-sles-15-sp3orsuse-manager-4-1-proxy. This part may also be “search-optimized” per cloud framework. For example the prefixsuse-helps when searching for SUSE in the general catalog in Amazon Web Services.FLAVORImages can have different flavors such as
chostorbyos. If it is the default image of a product, this part will be omitted. MultipleFLAVORattributes may be combined in an image name. For examplesles-15-sp3-chost-byosis an image build based on SUSE Linux Enterprise Server 15 SP3 build as a container host using a BYOS (Bring Your Own Subscription) billing model. Images withoutbyosin the name are set up the image is set up for PAYG (Pay As You Go) billing. For more information about the different billing models, refer to Section 1.3, “Plans”.SUSE Linux Enterprise flavors #byos: Bring your own subscription (BYOS) imagechost: Minimal container host imagehardened: Pre-hardened images, see Section 2.5, “Hardened Images”hpc: SUSE Linux Enterprise High Performance Computing imagesap: SUSE Linux Enterprise Server for SAP applications imagesapcal: SAP Cloud Application Library image
Not all flavors are available for all cloud frameworks; some are provider-specific.
Amazon Web Services flavors #ecs: Amazon Elastic Container Service image
Microsoft Azure flavors #basic: PAYG image that only includes updates but is not eligible for support (see Section 1.4, “Support”) or LTSS (see Section 3.3, “Enabling LTSS”).standard: Fully supported PAYG image
VERSIONUpload date of the image in the format
vYYYYMMDD(ISO 8601).VIRTUALIZATION(AWS-only)SUSE no longer supports or publishes para-virtualized images. The virtualization type was encoded as
pv(para-virtualized) orhvm(hardware-assisted virtual machine). Thehvmpart of the image name has been retained in an effort to not break backward compatibility.STORAGE(AWS-only)SUSE no longer publishes images that are based on hard disk (magnetic) backed storage. This used to be encoded as
mag. All published images are backed by SSD. Thessdpart of the image name has been retained in an effort to not break backward compatibility.ARCHITECTUREEither
x86_64orarm64. SUSE no longer supports or publishes 32 bitx86images. Images with thei386identifier are visible in Public Cloud Information Tracker data.TAXIDEither
llcorltd. Only for images with SUSE priority support. For more information, refer to Section 1.4, “Support”GENERATION(Microsoft Azure-only)appended as
gen2for 2nd Generation VMs.
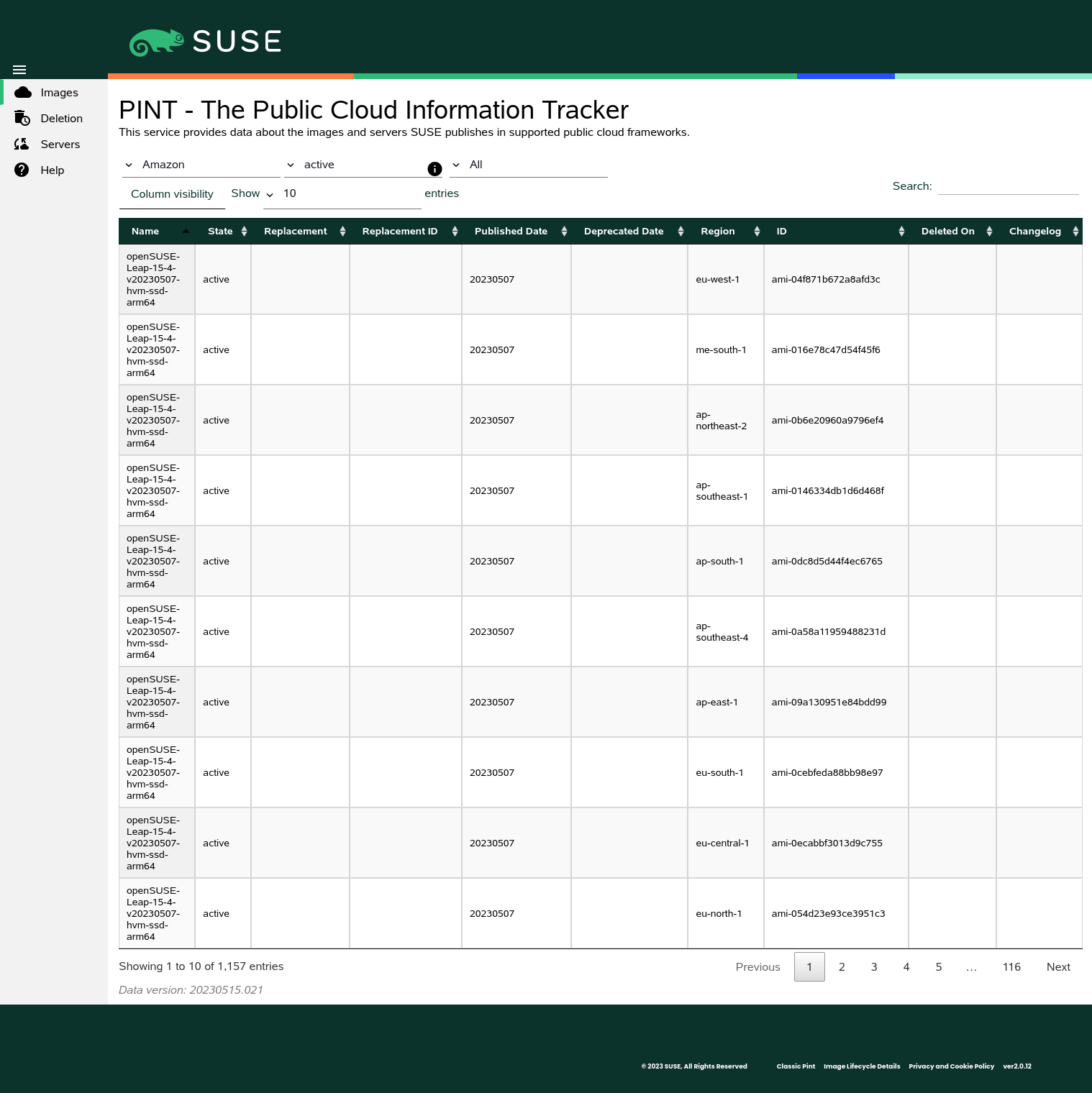
2.3 Public Cloud Information Tracker #
The Public Cloud Information Tracker (PINT) provides information about the images SUSE publishes
and servers that are part of the SUSE operated update infrastructure.
PINT is available at https://pint.suse.com/ and provided as an API
and command-line tool with the python3-susepubliccloudinfo
package from the Public Cloud Module repository.
Use the drop-down lists to view images, servers, or both, and filter by cloud framework, region, or image state. You can also search for strings and adjust the columns and the number of results per page.
2.3.1 Images view #
The following columns are shown in the Images view. Some columns depend on
the the cloud frameworks.
Images view #- Name
Name of the image. For more information about the image naming scheme, refer to Section 2.2, “Naming scheme”.
- State
State of the image. Can be one of
All states,active,inactive,deprecated, ordeleted. Note thatAll Statesexcludes images in thedeletedstate. Deleted images may be viewed by explicitly selectingdeletedas the image state. For more information information about image stated, refer to Section 2.1, “Image lifecycle”.- Replacement
Name of the image that replaces another.
- Replacement ID
ID of the image that replaces another. Only shown for Amazon, Oracle, and Alibaba; images on Google and Microsoft do not have IDs.
- Published Date
Publication date of the image. Displayed in the format
YYYYMMDD(ISO 8601).- Deprecated Date
Date the image was deprecated by a newer one. Displayed in the format
YYYYMMDD(ISO 8601). Only shown for deprecated or deleted images.- Project
Project of the image. Projects are used to organize Google Cloud Platform resources. Only shown for Google Cloud Platform.
- Region
Region of the image.
- Environment
Environment of the image. Only shown for Microsoft Azure.
- ID
Unique identifier of the image. While the
Nameof an image is the same across different regions, the is unique.- URN
Uniform Resource Name of an image. While the of an image is different across the environments, the
URNis the same. Only shown for Microsoft Azure.- Deleted on
Date the image was deleted in the format
YYYYMMDD(ISO 8601). Only shown for deleted images.- Changelog
Link to a detailed changelog and a software bill of materials (SBOM). For more information, refer to Section 2.4, “Change information”
Image changelogs are only available for images that replace others. For initial images of new product versions, refer to the product's release notes.
2.3.2 Servers view #
The following columns are shown in the Servers view:
Servers view #- Name
Host name of the server. Region servers do not have host names. Host names are not DNS resolvable.
- IP
IP address of the server.
- Region
Region of the server. For optimal performance SUSE provides servers in most regions of a cloud framework.
- Type
One of
regionserver-sles,regionserver-sap, orsmt. In every framework where SUSE operates an update infrastructure, theregionserversystems are randomly distributed across regions and thesmtservers are available in most regions. Every region hasupdateservers assigned.
2.4 Change information #
Whenever a new image gets released, you can review changes compared to the previously released image. Search for an image in PINT and click on its entry in the column.
Image change information is divided into different categories:
- Image configuration changes
This category describes changes in the image setup; for example, if a new service was enabled, kernel parameters were changed, or if packages were added or removed.
- CVE fixes
This category lists security fixes in the image. Entries are cross linked to the SUSE CVE database. For more information, refer to Section 2.1, “Image lifecycle”.
- Package version changes
This category lists all packages that had version changes compared to the previous image and the version in that image.
- Package change logs
This category shows a concatenated changelog of all packages that had changes.
- Software bill of materials (SPDX)
This category shows an SBOM in the
Software Package Data Exchangeformat.SPDXis an open standard backed by the Linux Foundation. For more information, refer to https://spdx.dev/.- Software bill of materials (CycloneDX)
This category shows an SBOM in the
CycloneDXformat. This format is backed by the Open Worldwide Application Security Project (OWASP) foundation. For more information, refer to https://cyclonedx.org/.
Please note that that image change information is only available for updated images, meaning for images that replace previous images of the same product version.
For initial images of new product versions, refer to the product's release notes at https://www.suse.com/releasenotes.
To allow for automatic retrieval of image change information, all URLs follow the schema:
https://publiccloudimagechangeinfo.suse.com/FRAMEWORK/IMAGE/CHANGES.html
FRAMEWORK is the cloud framework as used in the
pintcommand-line tool; i.e. one ofalibaba,amazon,google,microsoft, ororacle.IMAGE is the name of the image as shown by PINT, e.g.
suse-sles-15-sp3-byos-v20220127-hvm-ssd-x86_64.CHANGES is the category of the changes, i. e. one of
cve_fixes,image_changes,package_changelogs, orpackage_version_changes. Do not forget the.htmlextension to complete the URL.
2.5 Hardened Images #
To improve overall security, SUSE provides hardened images of some
products. The images are hardened using OpenSCAP, a collection of open source tools that
implement the Security Content Automation
Protocol (SCAP).
For more information and instructions on how to harden instances with OpenSCAP, refer to Section 3.4, “Hardening instances”.
3 Managing cloud instances #
SUSE Linux Enterprise in public clouds is managed almost like on bare metal or in virtual environments. Learn about what is different in the cloud.
3.1 Registering instances #
Like other SUSE products, SUSE Linux Enterprise in public clouds has to be registered to receive updates. There are different ways to register, depending on the image flavor chosen for the instance.
PAYG instances are registered automatically against the SUSE-operated update infrastructure in the cloud framework region, or a geographically close region. The
guestregister.servicemanages the registration on first boot.Important: Do not register PAYG instances with the SUSE Customer CenterRegistering PAYG instances with the SUSE Customer Center or your own RMT server will create conflicts that are not easily solved. Only register BYOS instances. PAYG instances are automatically registered against the correct update server.
BYOS instances have to be registered manually with your SUSE registration key. You can register with the cloud framework's SUSE update servers, the SUSE Customer Center, or your own SUSE Manager or RMT infrastructure.
There are two different ways to register BYOS instances:
Any BYOS instance can be registered with the SUSE Customer Center or your own SUSE Manager or RMT infrastructure using
SUSEConnect. Refer to Section 3.1.2, “Register withSUSEConnect” for instructions.BYOS instances with cloud-regionsrv-client version 9.3.0 or higher can be registered with the cloud framework's SUSE update servers using
registercloudguest. Using the cloud framework's update servers will result in faster package downloads. Registrations are forwarded from the update server to the SUSE Customer Center, so your cloud instances show up in your SUSE account and count against the system count of your subscription. Refer to Section 3.1.1, “Register withregistercloudguest” for instructions.Important:registercloudguestlimitationsNot all products and flavors can be registered with
registercloudguest.Container host (
chost) images are optimized for container workloads and contain only a few packages outside of the bare minimum to make containers run. These images do not containregistercloudguest, but you can register instances with the SUSE Customer Center first, install the necessary packages and then register with the SUSE-operated update infrastructure in the cloud framework region. Refer to Procedure 3.1, “Switching fromSUSEConnecttoregistercloudguest” for instructions.SUSE Linux Enterprise Micro (
sle-micro) 5.1 and 5.2 images do not containregistercloudguest. To register an instance, use the commandtransactional-update register. Refer to the SUSE Linux Enterprise Micro Administration Guide for more information. Images of SLE Micro 5.3 and later versions includeregistercloudguestand can be registered as described in Section 3.1.1, “Register withregistercloudguest”.SUSE Manager (
suse-manager) can only be registered with the SUSE Customer Center.
In summary, use registercloudguest to register with the
local cloud update infrastructure to benefit from faster downloads. Use
SUSEConnect to register with SUSE Customer Center or your own
SUSE Manager or RMT infrastructure.
3.1.1 Register with registercloudguest #
To register a BYOS instance with registercloudguest, run:
#registercloudguest-r REGISTRATION_CODE -e EMAIL_ADDRESS
Replace REGISTRATION_CODE with a valid registration code. Replace EMAIL_ADDRESS with the e-mail address associated with the SUSE account you or your organization uses to manage subscriptions.
BYOS instances created from images with a datestamp of
20220103 or later contain all
required packages. For BYOS instances created from images with a date stamp
prior to 20220103, perform the following steps:
SUSEConnect to registercloudguest #Check if the cloud-regionsrv-client package is installed:
#rpm-q cloud-regionsrv-clientIf the package is not installed or older than version 9.3.0, install or update it.
For instances created from images with a date stamp prior to
20220103, you first have to enable thePublic Cloud Module. For SUSE Linux Enterprise 15 SP4, run:#SUSEConnect-p sle-module-public-cloud/15.4/x86_64For other versions or a complete list of modules and their product identifiers, run
SUSEConnect --list-extensions.Install cloud-regionsrv-client. Depending on your cloud framework, you will need some additional packages.
For Amazon EC2 run:
#zypperin cloud-regionsrv-client cloud-regionsrv-client-plugin-ec2 \ regionServiceClientConfigEC2For Microsoft Azure run:
#zypperin cloud-regionsrv-client cloud-regionsrv-client-plugin-azure \ regionServiceClientConfigAzureFor Google Compute Engine run:
#zypperin cloud-regionsrv-client cloud-regionsrv-client-plugin-gce \ regionServiceClientConfigGCE
Disconnect your instance from the SUSE Customer Center:
#registercloudguest--cleanDo not use
SUSEConnect -d; it will no longer work.Connect the instance to the SUSE update infrastructure in the public cloud. Replace REGISTRATION_CODE with a valid registration code. Replace EMAIL_ADDRESS with the e-mail address associated with the SUSE account you or your organization uses to manage subscriptions.
#registercloudguest-r REGISTRATION_CODE -e EMAIL_ADDRESSThis will only register the base product and any recommended products. For instances created from images with a datestamp later than
20220103, it will also set up the repositories for thePublic Cloud Module.
3.1.2 Register with SUSEConnect #
To register a BYOS instance with SUSEConnect, run:
#SUSEConnect-r REGISTRATION_CODE -e EMAIL_ADDRESS
Replace REGISTRATION_CODE with a valid registration code. Replace EMAIL_ADDRESS with the e-mail address associated with the SUSE account you or your organization uses to manage subscriptions.
To register with your own registration server, also provide its URL:
#SUSEConnect-r REGISTRATION_CODE -e EMAIL_ADDRESS --url URL
If the instance was already registered with registercloudguest, perform the
following steps:
registercloudguest to SUSEConnect #Disconnect your instance from the SUSE-operated update infrastructure in the cloud framework:
#registercloudguest--cleanUninstall the cloud-regionsrv-client package and its dependencies:
#zypperrm -u cloud-regionsrv-clientClean up the registration status:
#SUSEConnect--cleanup --url https://scc.suse.comRegister the instance with
SUSEConnect.To connect the instance to the SUSE Customer Center, run:
#SUSEConnect-r REGISTRATION_CODE -e EMAIL_ADDRESSTo connect the instance to the your own registration server, run:
#SUSEConnect-r REGISTRATION_CODE -e EMAIL_ADDRESS --url URL
3.2 Deregister instances #
If you are to decommission an instance, remember to deregister it before termination. This will ensure that the system gets removed from the SUSE Customer Center and is no longer counted against your subscription.
Run
SUSEConnect --status-textto check the registration status.If the system is registered, check if the file
/var/log/cloudregisterexists. This usually indicates the system was registered withregistercloudguest.Deregister the system:
If a system was registered with
registercloudguest, run:#registercloudguest--cleanIf a system was registered with
SUSEConnect, run:#SUSEConnect-dIf this does not work, make sure the package cloud-regionsrv-client is not installed. It may have been installed after the system was registered.
3.3 Enabling LTSS #
Long Term Service Pack Support (LTSS) extends the lifecycle of
SUSE Linux Enterprise. It is available as an extension. For more information about LTSS, refer to
https://www.suse.com/products/long-term-service-pack-support/.
LTSS subscriptions are version-specific. If you have a subscription for SLES 15 SP4, you cannot use that registration code to register LTSS on a 15 SP3 image. Make sure to use the correct registration code for your instance and upgrade it if necessary.
Microsoft Azure also offers a basic PAYG image that only includes updates. Instances created from this image are not eligible for LTSS.
3.3.1 LTSS on BYOS #
If you do not have an LTSS subscription for your BYOS instance, contact a SUSE representative or visit https://www.suse.com/how-to-buy for purchase options.
To enable the LTSS extension, perform the following steps:
Log in to the SUSE Customer Center to look up your LTSS registration code.
Log in to your instance and make sure your system is registered:
>sudoSUSEConnect --status-textIf the system is not yet registered, register it (see Section 3.1, “Registering instances”).
Check if the LTSS extension is available for your system. For SUSE Linux Enterprise 15 SP3, it looks like this:
>sudoSUSEConnect --list-extensions | grep LTSSSUSE Linux Enterprise Server LTSS 15 SP3 x86_64 Activate with: SUSEConnect -p SLES-LTSS/15.3/x86_64 -r ADDITIONAL REGCODEActivate the module as instructed:
>sudoSUSEConnect -p SLES-LTSS/15.3/x86_64 -r LTSS_REGISTRATION_CODE
3.3.2 LTSS on PAYG #
LTSS subscriptions for PAYG can be transacted through a private offer on the CSPs market place or via direct transaction with SUSE. Reach out to cloudsales@suse.com to work out the commercial details. You will receive a subscription and access to the SUSE Customer Center). With your subscription, you can activate a registration code for LTSS.
If you already have an LTSS subscription that you are using in your data center, it will work in the cloud just fine. You can deregister a system in your data center and move that use of your LTSS subscription to an instance in the cloud.
To enable the LTSS extension, perform the following steps:
Log in to the SUSE Customer Center to activate a registration code. Note that LTSS subscriptions are version-specific. If you have a subscription for SLES 15 SP4, you cannot use that registration code to register LTSS on a 15 SP3 image. Make sure to activate the LTSS registration code for the correct version and service pack (SP) of your instance!
Log in to your instance and make sure your system is registered with a subscription that is eligible for LTSS. If the system is not yet registered, register it (see Section 3.1, “Registering instances”).
Update cloud-regionsrv-client:
>sudozypper up cloud-regionsrv-clientYou need at least version 10.3.4 of the package.
Register the LTSS extension with the registration code you activated in the SUSE Customer Center:
>sudoregistercloudguset -r LTSS_REGISTRATION_CODERunning LTSS registration...this takes a little longer LTSS registration succeeded
3.4 Hardening instances #
To improve overall security, SUSE provides hardened images of some products.
The images are hardened using OpenSCAP, a collection of open
source tools that implement the Security Content Automation
Protocol (SCAP) maintained by the National Institute
of Standards and Technology (NIST). OpenSCAP
supports automated configuration, vulnerability and patch checking, technical control
compliance activities, and security measurement.
To harden a system, OpenSCAP uses security rules that define certain security measures. Multiple rules can be combined into profiles. For more information, refer to the OpenSCAP documentation at https://www.open-scap.org/resources/documentation/.
3.4.1 Pre-hardening #
Hardened images are pre-hardened to the extent they can safely be hardened without causing problems in public cloud frameworks. Certain rules can only be applied after instance creation, for example:
Rules that require having passwords set up. Passwords would have to be public if configured during the image build. This would defeat the purpose of a secret password.
Rules that affect the network configuration. Networking is set up during instance creation, therefore it is not possible to limit access during image build.
Rules for custom partitioning. SUSE's public cloud images are partitioned to meet the requirements of the framework in which they are released. If your system needs to meet standards that require separate file systems for given directories, we recommend that you build your own images and use LVM or move those directories onto attached disks to get the strictest data separation possible.
Rules to remove packages. SUSE's public cloud images cater to a wide range of use cases. Even if the number of packages is limited, it is impossible to determine what packages an instance requires.
3.4.2 Available OpenSCAP profiles #
After instance creation, you can use the installed openscap packages to complete the hardening process using any of the following profiles:
- Standard (
standard.profile) Basic OpenSCAP system security standard.
- CIS Server Level 2 (
cis.profile) The
Center for Internet Security Server Level 2profile is considered to be “defense in depth” and is intended for environments where security is paramount. The recommendations associated with this profile can have an adverse effect on your organization if not implemented appropriately or without due care. For more information, refer to https://www.cisecurity.org.- Department of Defense STIG (
stig.profile) The Defense Information Systems Agency publishes Security Technical Implementation Guides (STIGs) for the Department of Defense. The STIG profile replaces the previous CIS Level 3 profile and provides all recommendations that are STIG-specific. Overlap of recommendations from other profiles, i.e. CIS Level 1 and Level 2, are present in the STIG profile as applicable. For more information, refer to https://public.cyber.mil/stigs/.
- HIPAA Security Rule (
hipaa.profile) In response to the Health Insurance Portability and Accountability Act (HIPAA) of 1996, the U.S. Department of Health and Human Services developed Security Standards for the Protection of Electronic Protected Health Information, commonly known as the
HIPAA Security Rule. It establishes national standards to protect individuals' electronic personal health information (e-PHI) that is created, received, used, or maintained by a covered entity. For more information, refer to https://www.hhs.gov/hipaa/for-professionals/security/index.html.- Payment Card Industry Data Security Standard (
pci-dss.profile) The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements to guide merchants to protect cardholder data. It is maintained by the PCI Security Standards Council (SSC) that was founded by all five major credit card brands Visa, MasterCard, American Express, Discover, and JCB. For more information, refer to https://www.pcisecuritystandards.org/document_library.
All profile files are available in the ComplianceAsCode repository.
For a complete list of rules that have been applied during pre-hardening, refer to pcs-hardening.profile.
This profile is a combination of the STIG and
CIS profiles minus rules that can only be applied
after instance creation.
Images of SUSE Linux Enterprise Server for SAP applications are hardened using a modified version of the profile
called pcs-hardening-sap.profile.
Users may need to make additional modifications to the system configuration
depending on individual application needs.
SUSE recommends using either the CIS or the
STIG profile. You can use other profiles at your own
discretion.
3.4.3 Hardening instances with OpenSCAP #
To evaluate an instance, you can run:
>sudooscapxccdf eval \ --profile stig1 \ --results /tmp/results.xml2 \ --report /tmp/report.html3 \ --stig-viewer /tmp/stigviewer.xml4 \ /usr/share/xml/scap/ssg/content/ssg-sle15-ds-1.2.xml5
Specifies the profile to use, e.g. | |
Saves the results of the evaluation to | |
Generates a HTML report called | |
Saves the results to | |
|
The evaluation process usually takes a few minutes, depending on the number of selected rules.
To remediate an instance, add the --remediate parameter:
>sudooscapxccdf eval --remediate\ --profile stig \ --results /tmp/results.xml \ --report /tmp/report.html \ --stig-viewer /tmp/stigviewer.xml \ /usr/share/xml/scap/ssg/content/ssg-sle15-ds-1.2.xml
3.4.4 More information #
For more information on how to harden your SUSE Linux Enterprise system with OpenSCAP, refer to the article Hardening SUSE Linux Enterprise with OpenSCAP. For general information on OpenSCAP, refer to the SCAP Security Guide.
A Support #
Find the support statement for SUSE Linux Enterprise and general information about technology previews below. For details about the product lifecycle, see https://www.suse.com/lifecycle.
If you are entitled to support, find details on how to collect information for a support ticket at https://documentation.suse.com/sles-15/html/SLES-all/cha-adm-support.html.
A1 Support statement for SUSE Linux Enterprise #
To receive support, you need an appropriate subscription with SUSE. To view the specific support offerings available to you, go to https://www.suse.com/support/ and select your product.
The support levels are defined as follows:
- L1
Problem determination, which means technical support designed to provide compatibility information, usage support, ongoing maintenance, information gathering and basic troubleshooting using available documentation.
- L2
Problem isolation, which means technical support designed to analyze data, reproduce customer problems, isolate problem area and provide a resolution for problems not resolved by Level 1 or prepare for Level 3.
- L3
Problem resolution, which means technical support designed to resolve problems by engaging engineering to resolve product defects which have been identified by Level 2 support.
For contracted customers and partners, SUSE Linux Enterprise is delivered with L3 support for all packages, except for the following:
Technology previews.
Sound, graphics, fonts, and artwork.
Packages that require an additional customer contract.
Some packages shipped as part of the module Workstation Extension are L2-supported only.
Packages with names ending in -devel (containing header files and similar developer resources) will only be supported together with their main packages.
SUSE will only support the usage of original packages. That is, packages that are unchanged and not recompiled.
A2 Technology previews #
Technology previews are packages, stacks, or features delivered by SUSE to provide glimpses into upcoming innovations. Technology previews are included for your convenience to give you a chance to test new technologies within your environment. We would appreciate your feedback! If you test a technology preview, please contact your SUSE representative and let them know about your experience and use cases. Your input is helpful for future development.
Technology previews have the following limitations:
Technology previews are still in development. Therefore, they may be functionally incomplete, unstable, or in other ways not suitable for production use.
Technology previews are not supported.
Technology previews may only be available for specific hardware architectures.
Details and functionality of technology previews are subject to change. As a result, upgrading to subsequent releases of a technology preview may be impossible and require a fresh installation.
SUSE may discover that a preview does not meet customer or market needs, or does not comply with enterprise standards. Technology previews can be removed from a product at any time. SUSE does not commit to providing a supported version of such technologies in the future.
For an overview of technology previews shipped with your product, see the release notes at https://www.suse.com/releasenotes/x86_64/public-cloud.
B Geographical availability #
SUSE offers 24x7 priority support for the PAYG versions of the following products:
SUSE Linux Enterprise Micro
SUSE Manager
Rancher Prime
You can transact priority support through the Amazon Web Services and Microsoft Azure marketplaces, where you
will see two different listings: A global one and one for EMEA Orders Only.
Two listings are needed as there are different regulations to comply
with, but the images and the support offering are identical. Select the correct listing for
your organization's CSP account:
For Amazon Web Services, it depends on the
tax addressof the account, see https://aws.amazon.com/tax-help/location.For Microsoft Azure, it depends on the
sold toaddress of the account, see https://learn.microsoft.com/azure/cost-management-billing/manage/change-azure-account-profile.For Google Cloud, it depends on the
billing countryof the account, see https://support.google.com/cloudidentity/answer/3530790.
|
Country (Code) |
AWS Marketplace |
Azure Marketplace |
Google Cloud Marketplace |
|---|---|---|---|
|
Afghanistan (AF) |
n/a |
n/a |
Global |
|
Åland Islands (AX) |
n/a |
n/a |
Global |
|
Albania (AL) |
n/a |
n/a |
Global |
|
Algeria (DZ) |
n/a |
n/a |
Global |
|
American Samoa (AS) |
n/a |
n/a |
Global |
|
Andorra (AD) |
n/a |
n/a |
Global |
|
Angola (AO) |
n/a |
n/a |
Global |
|
Anguilla (AI) |
n/a |
n/a |
Global |
|
Antarctica (AQ) |
n/a |
n/a |
Global |
|
Antigua and Barbuda (AG) |
n/a |
n/a |
Global |
|
Argentina (AR) |
n/a |
n/a |
Global |
|
Armenia (AM) |
n/a |
EMEA |
Global |
|
Aruba (AW) |
n/a |
n/a |
Global |
|
Australia (AU) |
Global |
Global |
Global |
|
Austria (AT) |
EMEA |
EMEA |
Global |
|
Azerbaijan (AZ) |
n/a |
n/a |
Global |
|
Bahamas (BS) |
n/a |
n/a |
Global |
|
Bahrain (BH) |
n/a |
n/a |
Global |
|
Bangladesh (BD) |
Global |
n/a |
Global |
|
Barbados (BB) |
Global |
n/a |
Global |
|
Belarus (BY) |
n/a |
EMEA |
Global |
|
Belgium (BE) |
EMEA |
EMEA |
Global |
|
Belize (BZ) |
n/a |
n/a |
Global |
|
Benin (BJ) |
n/a |
n/a |
Global |
|
Bermuda (BM) |
n/a |
n/a |
Global |
|
Bhutan (BT) |
n/a |
n/a |
Global |
|
Bolivia, Plurinational State of (BO) |
n/a |
n/a |
Global |
|
Bonaire (BQ) |
n/a |
n/a |
Global |
|
Bosnia and Herzegovina (BA) |
n/a |
n/a |
Global |
|
Botswana (BW) |
n/a |
n/a |
Global |
|
Bouvet Island (BV) |
n/a |
n/a |
Global |
|
Brazil (BR) |
n/a |
n/a |
Global |
|
British Indian Ocean Territory (IO) |
n/a |
n/a |
Global |
|
Brunei Darussalam (BN) |
n/a |
n/a |
Global |
|
Bulgaria (BG) |
EMEA |
EMEA |
Global |
|
Burkina Faso (BF) |
n/a |
n/a |
Global |
|
Burundi (BI) |
n/a |
n/a |
Global |
|
Cambodia (KH) |
n/a |
n/a |
Global |
|
Cameroon (CM) |
EMEA |
n/a |
Global |
|
Canada (CA) |
Global |
Global |
Global |
|
Cape Verde (CV) |
n/a |
n/a |
Global |
|
Cayman Islands (KY) |
n/a |
n/a |
Global |
|
Central African Republic (CF) |
n/a |
n/a |
Global |
|
Chad (TD) |
n/a |
n/a |
Global |
|
Chile (CL) |
Global |
Global |
Global |
|
China (CN) |
n/a |
n/a |
Global |
|
Christmas Island (CX) |
n/a |
n/a |
Global |
|
Cocos (Keeling) Islands (CC) |
n/a |
n/a |
Global |
|
Colombia (CO) |
n/a |
Global |
Global |
|
Comoros (KM) |
n/a |
n/a |
Global |
|
Congo (CG) |
n/a |
n/a |
Global |
|
Congo, the Democratic Republic of the (CD) |
n/a |
n/a |
Global |
|
Cook Islands (CK) |
n/a |
n/a |
Global |
|
Costa Rica (CR) |
n/a |
n/a |
Global |
|
Côte d'Ivoire (CI) |
n/a |
n/a |
Global |
|
Croatia (HR) |
EMEA |
EMEA |
Global |
|
Curaçao (CW) |
n/a |
n/a |
Global |
|
Cuba (CU) |
n/a |
n/a |
n/a |
|
Cyprus (CY) |
EMEA |
EMEA |
Global |
|
Czech Republic (CZ) |
EMEA |
EMEA |
Global |
|
Denmark (DK) |
EMEA |
EMEA |
Global |
|
Djibouti (DJ) |
n/a |
n/a |
Global |
|
Dominica (DM) |
n/a |
n/a |
Global |
|
Dominican Republic (DO) |
n/a |
n/a |
Global |
|
Ecuador (EC) |
n/a |
n/a |
Global |
|
Egypt (EG) |
EMEA |
EMEA |
Global |
|
El Salvador (SV) |
n/a |
n/a |
Global |
|
Equatorial Guinea (GQ) |
n/a |
n/a |
Global |
|
Eritrea (ER) |
n/a |
n/a |
Global |
|
Estonia (EE) |
EMEA |
EMEA |
Global |
|
Ethiopia (ET) |
n/a |
n/a |
Global |
|
Falkland Islands (Malvinas) (FK) |
n/a |
n/a |
Global |
|
Faroe Islands (FO) |
n/a |
n/a |
Global |
|
Fiji (FJ) |
n/a |
n/a |
Global |
|
Finland (FI) |
EMEA |
EMEA |
Global |
|
France (FR) |
EMEA |
EMEA |
Global |
|
French Guiana (GF) |
n/a |
n/a |
Global |
|
French Polynesia (PF) |
n/a |
n/a |
Global |
|
French Southern Territories (TF) |
n/a |
n/a |
Global |
|
Gabon (GA) |
n/a |
n/a |
Global |
|
Gambia (GM) |
n/a |
n/a |
Global |
|
Georgia (GE) |
n/a |
n/a |
Global |
|
Germany (DE) |
EMEA |
EMEA |
Global |
|
Ghana (GH) |
n/a |
n/a |
Global |
|
Gibraltar (GI) |
n/a |
n/a |
Global |
|
Greece (GR) |
EMEA |
EMEA |
Global |
|
Greenland (GL) |
n/a |
n/a |
Global |
|
Grenada (GD) |
n/a |
n/a |
Global |
|
Guadeloupe (GP) |
n/a |
n/a |
Global |
|
Guam (GU) |
n/a |
n/a |
Global |
|
Guatemala (GT) |
n/a |
n/a |
Global |
|
Guernsey (GG) |
n/a |
n/a |
Global |
|
Guinea (GN) |
n/a |
n/a |
Global |
|
Guinea-Bissau (GW) |
n/a |
n/a |
Global |
|
Guyana (GY) |
n/a |
n/a |
Global |
|
Haiti (HT) |
n/a |
n/a |
Global |
|
Heard Island and McDonald Islands (HM) |
n/a |
n/a |
Global |
|
Holy See (Vatican City State) (VA) |
n/a |
n/a |
Global |
|
Honduras (HN) |
n/a |
n/a |
Global |
|
Hong Kong (HK) |
n/a |
n/a |
Global |
|
Hungary (HU) |
EMEA |
EMEA |
Global |
|
Iceland (IS) |
n/a |
EMEA |
Global |
|
India (IN) |
Global |
Global |
Global |
|
Indonesia (ID) |
Global |
Global |
Global |
|
Ireland (IE) |
EMEA |
EMEA |
Global |
|
Iran (IR) |
n/a |
n/a |
n/a |
|
Iraq (IQ) |
n/a |
n/a |
Global |
|
Isle of Man (IM) |
n/a |
n/a |
Global |
|
Israel (IL) |
n/a |
n/a |
Global |
|
Italy (IT) |
EMEA |
EMEA |
Global |
|
Jamaica (JM) |
n/a |
n/a |
Global |
|
Japan (JP) |
n/a |
n/a |
Global |
|
Jersey (JE) |
n/a |
n/a |
Global |
|
Jordan (JO) |
n/a |
n/a |
Global |
|
Kazakhstan (KZ) |
n/a |
n/a |
Global |
|
Kenya (KE) |
EMEA |
EMEA |
Global |
|
Kingdom of Saudi Arabia (SA) |
EMEA |
EMEA |
Global |
|
Korea, Democratic People's Republic of (KP) |
n/a |
n/a |
n/a |
|
Korea, Republic of (KR) |
Global |
Global |
Global |
|
Kiribati (KI) |
n/a |
n/a |
Global |
|
Kuwait (KW) |
n/a |
n/a |
Global |
|
Kyrgyzstan (KG) |
n/a |
n/a |
Global |
|
Lao People's Democratic Republic (LA) |
n/a |
n/a |
Global |
|
Latvia (LV) |
EMEA |
EMEA |
Global |
|
Lebanon (LB) |
n/a |
n/a |
Global |
|
Lesotho (LS) |
n/a |
n/a |
Global |
|
Liberia (LR) |
n/a |
n/a |
Global |
|
Libyan Arab Jamahiriya (LY) |
n/a |
n/a |
Global |
|
Liechtenstein (LI) |
n/a |
EMEA |
Global |
|
Lithuania (LT) |
EMEA |
EMEA |
Global |
|
Luxembourg (LU) |
EMEA |
EMEA |
Global |
|
Macao (MO) |
n/a |
n/a |
Global |
|
Macedonia, the former Yugoslav Republic of (MK) |
n/a |
n/a |
Global |
|
Madagascar (MG) |
n/a |
n/a |
Global |
|
Malawi (MW) |
n/a |
n/a |
Global |
|
Malaysia (MY) |
Global |
Global |
Global |
|
Maldives (MV) |
n/a |
n/a |
Global |
|
Mali (ML) |
n/a |
n/a |
Global |
|
Malta (MT) |
EMEA |
EMEA |
Global |
|
Marshall Islands (MH) |
n/a |
n/a |
Global |
|
Martinique (MQ) |
n/a |
n/a |
Global |
|
Mauritania (MR) |
n/a |
n/a |
Global |
|
Mauritius (MU) |
n/a |
n/a |
Global |
|
Mayotte (YT) |
n/a |
n/a |
Global |
|
Mexico (MX) |
Global |
n/a |
Global |
|
Micronesia, Federated States of (FM) |
n/a |
n/a |
Global |
|
Moldova, Republic of (MD) |
n/a |
n/a |
Global |
|
Monaco (MC) |
n/a |
EMEA |
Global |
|
Mongolia (MN) |
n/a |
n/a |
Global |
|
Montenegro (ME) |
n/a |
n/a |
Global |
|
Montserrat (MS) |
n/a |
n/a |
Global |
|
Morocco (MA) |
n/a |
n/a |
Global |
|
Mozambique (MZ) |
n/a |
n/a |
Global |
|
Myanmar (MM) |
n/a |
n/a |
Global |
|
Namibia (NA) |
n/a |
n/a |
Global |
|
Nauru (NR) |
n/a |
n/a |
Global |
|
Nepal (NP) |
n/a |
n/a |
Global |
|
Netherlands (NL) |
EMEA |
EMEA |
Global |
|
New Caledonia (NC) |
n/a |
n/a |
Global |
|
New Zealand (NZ) |
Global |
Global |
Global |
|
Nicaragua (NI) |
n/a |
n/a |
Global |
|
Niger (NE) |
n/a |
n/a |
Global |
|
Nigeria (NG) |
n/a |
EMEA |
Global |
|
Niue (NU) |
n/a |
n/a |
Global |
|
Norfolk Island (NF) |
n/a |
n/a |
Global |
|
Northern Mariana Islands (MP) |
n/a |
n/a |
Global |
|
Norway (NO) |
EMEA |
EMEA |
Global |
|
Oman (OM) |
n/a |
n/a |
Global |
|
Pakistan (PK) |
n/a |
n/a |
Global |
|
Palau (PW) |
n/a |
n/a |
Global |
|
Palestinian Territory, Occupied (PS) |
n/a |
n/a |
Global |
|
Panama (PA) |
n/a |
n/a |
Global |
|
Papua New Guinea (PG) |
n/a |
n/a |
Global |
|
Paraguay (PY) |
n/a |
n/a |
Global |
|
Peru (PE) |
n/a |
n/a |
Global |
|
Philippines (PH) |
n/a |
n/a |
Global |
|
Pitcairn (PN) |
n/a |
n/a |
Global |
|
Poland (PL) |
EMEA |
EMEA |
Global |
|
Portugal (PT) |
EMEA |
EMEA |
Global |
|
Puerto Rico (PR) |
n/a |
Global |
Global |
|
Qatar (QA) |
n/a |
n/a |
Global |
|
Réunion (RE) |
n/a |
n/a |
Global |
|
Romania (RO) |
EMEA |
EMEA |
Global |
|
Russian Federation (RU) |
n/a |
n/a |
n/a |
|
Rwanda (RW) |
n/a |
n/a |
Global |
|
Saint Barthélemy (BL) |
n/a |
n/a |
Global |
|
Saint Helena, Ascension and Tristan da Cunha (SH) |
n/a |
n/a |
Global |
|
Saint Kitts and Nevis (KN) |
n/a |
n/a |
Global |
|
Saint Lucia (LC) |
n/a |
n/a |
Global |
|
Saint Martin (MF) |
n/a |
n/a |
Global |
|
Saint Pierre and Miquelon (PM) |
n/a |
n/a |
Global |
|
Saint Vincent and the Grenadines (VC) |
n/a |
n/a |
Global |
|
Samoa (WS) |
n/a |
n/a |
Global |
|
San Marino (SM) |
n/a |
n/a |
Global |
|
Sao Tome and Principe (ST) |
n/a |
n/a |
Global |
|
Senegal (SN) |
n/a |
n/a |
Global |
|
Serbia (RS) |
n/a |
EMEA |
Global |
|
Seychelles (SC) |
n/a |
n/a |
Global |
|
Sierra Leone (SL) |
n/a |
n/a |
Global |
|
Singapore (SG) |
Global |
Global |
Global |
|
Sint Maarten (SX) |
n/a |
n/a |
Global |
|
Slovakia (SK) |
EMEA |
EMEA |
Global |
|
Slovenia (SI) |
EMEA |
EMEA |
Global |
|
Solomon Islands (SB) |
n/a |
n/a |
Global |
|
Somalia (SO) |
n/a |
n/a |
Global |
|
South Africa (ZA) |
n/a |
EMEA |
Global |
|
South Georgia and the South Sandwich Islands (GS) |
n/a |
n/a |
Global |
|
South Sudan (SS) |
n/a |
n/a |
Global |
|
Spain (ES) |
EMEA |
EMEA |
Global |
|
Sri Lanka (LK) |
n/a |
n/a |
Global |
|
Suriname (SR) |
n/a |
n/a |
Global |
|
Svalbard and Jan Mayen (SJ) |
n/a |
n/a |
Global |
|
Swaziland (SZ) |
n/a |
n/a |
Global |
|
Sweden (SE) |
EMEA |
EMEA |
Global |
|
Switzerland (CH) |
n/a |
EMEA |
Global |
|
Syrian Arab Republic (SY) |
n/a |
n/a |
n/a |
|
Taiwan, Province of China (TW) |
Global |
Global |
Global |
|
Tajikistan (TJ) |
n/a |
n/a |
Global |
|
Tanzania, United Republic of (TZ) |
n/a |
n/a |
Global |
|
Thailand (TH) |
n/a |
Global |
Global |
|
Timor-Leste (TL) |
n/a |
n/a |
Global |
|
Togo (TG) |
n/a |
n/a |
Global |
|
Tokelau (TK) |
n/a |
n/a |
Global |
|
Tonga (TO) |
n/a |
n/a |
Global |
|
Trinidad and Tobago (TT) |
n/a |
n/a |
Global |
|
Tunisia (TN) |
n/a |
n/a |
Global |
|
Turkey (TR) |
EMEA |
EMEA |
Global |
|
Turkmenistan (TM) |
n/a |
n/a |
Global |
|
Turks and Caicos Islands (TC) |
n/a |
n/a |
Global |
|
Tuvalu (TV) |
n/a |
n/a |
Global |
|
Uganda (UG) |
n/a |
n/a |
Global |
|
Ukraine (UA) |
n/a |
n/a |
Global |
|
United Arab Emirates (AE) |
n/a |
EMEA |
Global |
|
United Kingdom (GB) |
EMEA |
EMEA |
Global |
|
United States (US) |
Global |
Global |
Global |
|
United States Minor Outlying Islands (UM) |
n/a |
n/a |
Global |
|
Uruguay (UY) |
n/a |
n/a |
Global |
|
Uzbekistan (UZ) |
n/a |
n/a |
Global |
|
Vanuatu (VU) |
n/a |
n/a |
Global |
|
Venezuela, Bolivarian Republic of (VE) |
n/a |
n/a |
Global |
|
Viet Nam (VN) |
n/a |
Global |
Global |
|
Virgin Islands, British (VG) |
n/a |
n/a |
Global |
|
Virgin Islands, U.S. (VI) |
n/a |
n/a |
Global |
|
Wallis and Futuna (WF) |
n/a |
n/a |
Global |
|
Western Sahara (EH) |
n/a |
n/a |
Global |
|
Yemen (YE) |
n/a |
n/a |
Global |
|
Zambia (ZM) |
n/a |
n/a |
Global |
|
Zimbabwe (ZW) |
n/a |
n/a |
Global |
If the billing or tax address of your organization's CSP account is located in a country listed as not available, you currently cannot transact priority support through the CSP's marketplaces.
SUSE is committed to making priority support available in more countries. In the meantime, you can still use SUSE PAYG products with regular support from the CSP. If you want support by SUSE, use a BYOS version.
C GNU licenses #
This appendix contains the GNU Free Documentation License version 1.2.
GNU Free Documentation License #
Copyright (C) 2000, 2001, 2002 Free Software Foundation, Inc. 51 Franklin St, Fifth Floor, Boston, MA 02110-1301 USA. Everyone is permitted to copy and distribute verbatim copies of this license document, but changing it is not allowed.
0. PREAMBLE #
The purpose of this License is to make a manual, textbook, or other functional and useful document "free" in the sense of freedom: to assure everyone the effective freedom to copy and redistribute it, with or without modifying it, either commercially or non-commercially. Secondarily, this License preserves for the author and publisher a way to get credit for their work, while not being considered responsible for modifications made by others.
This License is a kind of "copyleft", which means that derivative works of the document must themselves be free in the same sense. It complements the GNU General Public License, which is a copyleft license designed for free software.
We have designed this License to use it for manuals for free software, because free software needs free documentation: a free program should come with manuals providing the same freedoms that the software does. But this License is not limited to software manuals; it can be used for any textual work, regardless of subject matter or whether it is published as a printed book. We recommend this License principally for works whose purpose is instruction or reference.
1. APPLICABILITY AND DEFINITIONS #
This License applies to any manual or other work, in any medium, that contains a notice placed by the copyright holder saying it can be distributed under the terms of this License. Such a notice grants a world-wide, royalty-free license, unlimited in duration, to use that work under the conditions stated herein. The "Document", below, refers to any such manual or work. Any member of the public is a licensee, and is addressed as "you". You accept the license if you copy, modify or distribute the work in a way requiring permission under copyright law.
A "Modified Version" of the Document means any work containing the Document or a portion of it, either copied verbatim, or with modifications and/or translated into another language.
A "Secondary Section" is a named appendix or a front-matter section of the Document that deals exclusively with the relationship of the publishers or authors of the Document to the Document's overall subject (or to related matters) and contains nothing that could fall directly within that overall subject. (Thus, if the Document is in part a textbook of mathematics, a Secondary Section may not explain any mathematics.) The relationship could be a matter of historical connection with the subject or with related matters, or of legal, commercial, philosophical, ethical or political position regarding them.
The "Invariant Sections" are certain Secondary Sections whose titles are designated, as being those of Invariant Sections, in the notice that says that the Document is released under this License. If a section does not fit the above definition of Secondary then it is not allowed to be designated as Invariant. The Document may contain zero Invariant Sections. If the Document does not identify any Invariant Sections then there are none.
The "Cover Texts" are certain short passages of text that are listed, as Front-Cover Texts or Back-Cover Texts, in the notice that says that the Document is released under this License. A Front-Cover Text may be at most 5 words, and a Back-Cover Text may be at most 25 words.
A "Transparent" copy of the Document means a machine-readable copy, represented in a format whose specification is available to the general public, that is suitable for revising the document straightforwardly with generic text editors or (for images composed of pixels) generic paint programs or (for drawings) some widely available drawing editor, and that is suitable for input to text formatters or for automatic translation to a variety of formats suitable for input to text formatters. A copy made in an otherwise Transparent file format whose markup, or absence of markup, has been arranged to thwart or discourage subsequent modification by readers is not Transparent. An image format is not Transparent if used for any substantial amount of text. A copy that is not "Transparent" is called "Opaque".
Examples of suitable formats for Transparent copies include plain ASCII without markup, Texinfo input format, LaTeX input format, SGML or XML using a publicly available DTD, and standard-conforming simple HTML, PostScript or PDF designed for human modification. Examples of transparent image formats include PNG, XCF and JPG. Opaque formats include proprietary formats that can be read and edited only by proprietary word processors, SGML or XML for which the DTD and/or processing tools are not generally available, and the machine-generated HTML, PostScript or PDF produced by some word processors for output purposes only.
The "Title Page" means, for a printed book, the title page itself, plus such following pages as are needed to hold, legibly, the material this License requires to appear in the title page. For works in formats which do not have any title page as such, "Title Page" means the text near the most prominent appearance of the work's title, preceding the beginning of the body of the text.
A section "Entitled XYZ" means a named subunit of the Document whose title either is precisely XYZ or contains XYZ in parentheses following text that translates XYZ in another language. (Here XYZ stands for a specific section name mentioned below, such as "Acknowledgements", "Dedications", "Endorsements", or "History".) To "Preserve the Title" of such a section when you modify the Document means that it remains a section "Entitled XYZ" according to this definition.
The Document may include Warranty Disclaimers next to the notice which states that this License applies to the Document. These Warranty Disclaimers are considered to be included by reference in this License, but only as regards disclaiming warranties: any other implication that these Warranty Disclaimers may have is void and has no effect on the meaning of this License.
2. VERBATIM COPYING #
You may copy and distribute the Document in any medium, either commercially or non-commercially, provided that this License, the copyright notices, and the license notice saying this License applies to the Document are reproduced in all copies, and that you add no other conditions whatsoever to those of this License. You may not use technical measures to obstruct or control the reading or further copying of the copies you make or distribute. However, you may accept compensation in exchange for copies. If you distribute a large enough number of copies you must also follow the conditions in section 3.
You may also lend copies, under the same conditions stated above, and you may publicly display copies.
3. COPYING IN QUANTITY #
If you publish printed copies (or copies in media that commonly have printed covers) of the Document, numbering more than 100, and the Document's license notice requires Cover Texts, you must enclose the copies in covers that carry, clearly and legibly, all these Cover Texts: Front-Cover Texts on the front cover, and Back-Cover Texts on the back cover. Both covers must also clearly and legibly identify you as the publisher of these copies. The front cover must present the full title with all words of the title equally prominent and visible. You may add other material on the covers in addition. Copying with changes limited to the covers, as long as they preserve the title of the Document and satisfy these conditions, can be treated as verbatim copying in other respects.
If the required texts for either cover are too voluminous to fit legibly, you should put the first ones listed (as many as fit reasonably) on the actual cover, and continue the rest onto adjacent pages.
If you publish or distribute Opaque copies of the Document numbering more than 100, you must either include a machine-readable Transparent copy along with each Opaque copy, or state in or with each Opaque copy a computer-network location from which the general network-using public has access to download using public-standard network protocols a complete Transparent copy of the Document, free of added material. If you use the latter option, you must take reasonably prudent steps, when you begin distribution of Opaque copies in quantity, to ensure that this Transparent copy will remain thus accessible at the stated location until at least one year after the last time you distribute an Opaque copy (directly or through your agents or retailers) of that edition to the public.
It is requested, but not required, that you contact the authors of the Document well before redistributing any large number of copies, to give them a chance to provide you with an updated version of the Document.
4. MODIFICATIONS #
You may copy and distribute a Modified Version of the Document under the conditions of sections 2 and 3 above, provided that you release the Modified Version under precisely this License, with the Modified Version filling the role of the Document, thus licensing distribution and modification of the Modified Version to whoever possesses a copy of it. In addition, you must do these things in the Modified Version:
Use in the Title Page (and on the covers, if any) a title distinct from that of the Document, and from those of previous versions (which should, if there were any, be listed in the History section of the Document). You may use the same title as a previous version if the original publisher of that version gives permission.
List on the Title Page, as authors, one or more persons or entities responsible for authorship of the modifications in the Modified Version, together with at least five of the principal authors of the Document (all of its principal authors, if it has fewer than five), unless they release you from this requirement.
State on the Title page the name of the publisher of the Modified Version, as the publisher.
Preserve all the copyright notices of the Document.
Add an appropriate copyright notice for your modifications adjacent to the other copyright notices.
Include, immediately after the copyright notices, a license notice giving the public permission to use the Modified Version under the terms of this License, in the form shown in the Addendum below.
Preserve in that license notice the full lists of Invariant Sections and required Cover Texts given in the Document's license notice.
Include an unaltered copy of this License.
Preserve the section Entitled "History", Preserve its Title, and add to it an item stating at least the title, year, new authors, and publisher of the Modified Version as given on the Title Page. If there is no section Entitled "History" in the Document, create one stating the title, year, authors, and publisher of the Document as given on its Title Page, then add an item describing the Modified Version as stated in the previous sentence.
Preserve the network location, if any, given in the Document for public access to a Transparent copy of the Document, and likewise the network locations given in the Document for previous versions it was based on. These may be placed in the "History" section. You may omit a network location for a work that was published at least four years before the Document itself, or if the original publisher of the version it refers to gives permission.
For any section Entitled "Acknowledgements" or "Dedications", Preserve the Title of the section, and preserve in the section all the substance and tone of each of the contributor acknowledgements and/or dedications given therein.
Preserve all the Invariant Sections of the Document, unaltered in their text and in their titles. Section numbers or the equivalent are not considered part of the section titles.
Delete any section Entitled "Endorsements". Such a section may not be included in the Modified Version.
Do not retitle any existing section to be Entitled "Endorsements" or to conflict in title with any Invariant Section.
Preserve any Warranty Disclaimers.
If the Modified Version includes new front-matter sections or appendices that qualify as Secondary Sections and contain no material copied from the Document, you may at your option designate some or all of these sections as invariant. To do this, add their titles to the list of Invariant Sections in the Modified Version's license notice. These titles must be distinct from any other section titles.
You may add a section Entitled "Endorsements", provided it contains nothing but endorsements of your Modified Version by various parties--for example, statements of peer review or that the text has been approved by an organization as the authoritative definition of a standard.
You may add a passage of up to five words as a Front-Cover Text, and a passage of up to 25 words as a Back-Cover Text, to the end of the list of Cover Texts in the Modified Version. Only one passage of Front-Cover Text and one of Back-Cover Text may be added by (or through arrangements made by) any one entity. If the Document already includes a cover text for the same cover, previously added by you or by arrangement made by the same entity you are acting on behalf of, you may not add another; but you may replace the old one, on explicit permission from the previous publisher that added the old one.
The author(s) and publisher(s) of the Document do not by this License give permission to use their names for publicity for or to assert or imply endorsement of any Modified Version.
5. COMBINING DOCUMENTS #
You may combine the Document with other documents released under this License, under the terms defined in section 4 above for modified versions, provided that you include in the combination all of the Invariant Sections of all of the original documents, unmodified, and list them all as Invariant Sections of your combined work in its license notice, and that you preserve all their Warranty Disclaimers.
The combined work need only contain one copy of this License, and multiple identical Invariant Sections may be replaced with a single copy. If there are multiple Invariant Sections with the same name but different contents, make the title of each such section unique by adding at the end of it, in parentheses, the name of the original author or publisher of that section if known, or else a unique number. Make the same adjustment to the section titles in the list of Invariant Sections in the license notice of the combined work.
In the combination, you must combine any sections Entitled "History" in the various original documents, forming one section Entitled "History"; likewise combine any sections Entitled "Acknowledgements", and any sections Entitled "Dedications". You must delete all sections Entitled "Endorsements".
6. COLLECTIONS OF DOCUMENTS #
You may make a collection consisting of the Document and other documents released under this License, and replace the individual copies of this License in the various documents with a single copy that is included in the collection, provided that you follow the rules of this License for verbatim copying of each of the documents in all other respects.
You may extract a single document from such a collection, and distribute it individually under this License, provided you insert a copy of this License into the extracted document, and follow this License in all other respects regarding verbatim copying of that document.
7. AGGREGATION WITH INDEPENDENT WORKS #
A compilation of the Document or its derivatives with other separate and independent documents or works, in or on a volume of a storage or distribution medium, is called an "aggregate" if the copyright resulting from the compilation is not used to limit the legal rights of the compilation's users beyond what the individual works permit. When the Document is included in an aggregate, this License does not apply to the other works in the aggregate which are not themselves derivative works of the Document.
If the Cover Text requirement of section 3 is applicable to these copies of the Document, then if the Document is less than one half of the entire aggregate, the Document's Cover Texts may be placed on covers that bracket the Document within the aggregate, or the electronic equivalent of covers if the Document is in electronic form. Otherwise they must appear on printed covers that bracket the whole aggregate.
8. TRANSLATION #
Translation is considered a kind of modification, so you may distribute translations of the Document under the terms of section 4. Replacing Invariant Sections with translations requires special permission from their copyright holders, but you may include translations of some or all Invariant Sections in addition to the original versions of these Invariant Sections. You may include a translation of this License, and all the license notices in the Document, and any Warranty Disclaimers, provided that you also include the original English version of this License and the original versions of those notices and disclaimers. In case of a disagreement between the translation and the original version of this License or a notice or disclaimer, the original version will prevail.
If a section in the Document is Entitled "Acknowledgements", "Dedications", or "History", the requirement (section 4) to Preserve its Title (section 1) will typically require changing the actual title.
9. TERMINATION #
You may not copy, modify, sublicense, or distribute the Document except as expressly provided for under this License. Any other attempt to copy, modify, sublicense or distribute the Document is void, and will automatically terminate your rights under this License. However, parties who have received copies, or rights, from you under this License will not have their licenses terminated so long as such parties remain in full compliance.
10. FUTURE REVISIONS OF THIS LICENSE #
The Free Software Foundation may publish new, revised versions of the GNU Free Documentation License from time to time. Such new versions will be similar in spirit to the present version, but may differ in detail to address new problems or concerns. See https://www.gnu.org/copyleft/.
Each version of the License is given a distinguishing version number. If the Document specifies that a particular numbered version of this License "or any later version" applies to it, you have the option of following the terms and conditions either of that specified version or of any later version that has been published (not as a draft) by the Free Software Foundation. If the Document does not specify a version number of this License, you may choose any version ever published (not as a draft) by the Free Software Foundation.
ADDENDUM: How to use this License for your documents #
Copyright (c) YEAR YOUR NAME. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License”.
If you have Invariant Sections, Front-Cover Texts and Back-Cover Texts, replace the “with...Texts.” line with this:
with the Invariant Sections being LIST THEIR TITLES, with the Front-Cover Texts being LIST, and with the Back-Cover Texts being LIST.
If you have Invariant Sections without Cover Texts, or some other combination of the three, merge those two alternatives to suit the situation.
If your document contains nontrivial examples of program code, we recommend releasing these examples in parallel under your choice of free software license, such as the GNU General Public License, to permit their use in free software.