25 Building and Managing Profiles with YaST #
YaST provides a basic way to build profiles and manage AppArmor® profiles. It provides two interfaces: a graphical one and a text-based one. The text-based interface consumes less resources and bandwidth, making it a better choice for remote administration, or for times when a local graphical environment is inconvenient. Although the interfaces have differing appearances, they offer the same functionality in similar ways. Another alternative is to use AppArmor commands, which can control AppArmor from a terminal window or through remote connections. The command line tools are described in Chapter 26, Building Profiles from the Command Line.
Start YaST from the main menu and enter your root password
when prompted for it. Alternatively, start YaST by opening a terminal
window, logging in as root, and entering yast2
for the graphical mode or yast for the text-based mode.
In the section, there is an icon. Click it to launch the AppArmor YaST module.
25.1 Manually Adding a Profile #
AppArmor enables you to create an AppArmor profile by manually adding entries into the profile. Select the application for which to create a profile, then add entries.
Start YaST, select , and click in the main window.
Browse your system to find the application for which to create a profile.
When you find the application, select it and click . A basic, empty profile appears in the window.
In , add, edit, or delete AppArmor profile entries by clicking the corresponding buttons and referring to Section 25.2.1, “Adding an Entry”, Section 25.2.2, “Editing an Entry”, or Section 25.2.3, “Deleting an Entry”.
When finished, click .
25.2 Editing Profiles #
YaST offers basic manipulation for AppArmor profiles, such
as creating or editing. However, the most straightforward way
to edit an AppArmor
profile is to use a text editor such as vi:
root # vi /etc/apparmor.d/usr.sbin.httpd2-prefork
The vi editor also includes syntax (error)
highlighting and syntax error highlighting, which visually warns you
when the syntax of the edited AppArmor profile is wrong.
AppArmor enables you to edit AppArmor profiles manually by adding, editing, or deleting entries. To edit a profile, proceed as follows:
Start YaST, select , and click in the main window.
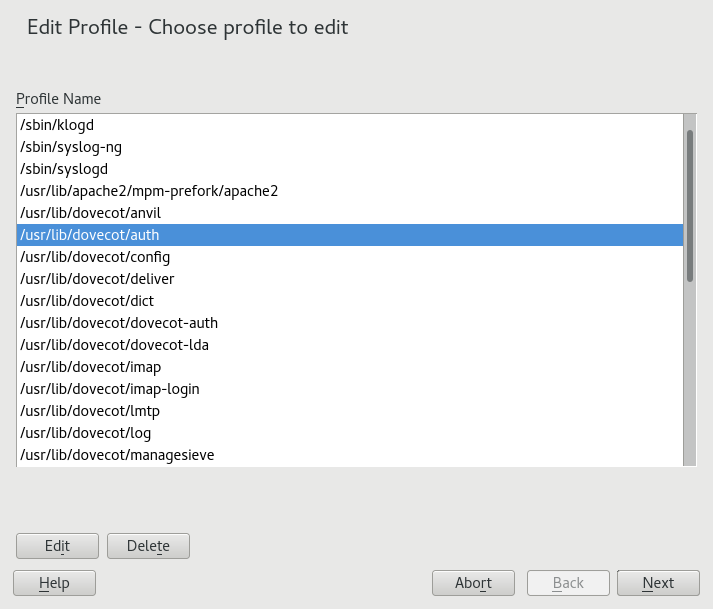
From the list of profiled applications, select the profile to edit.
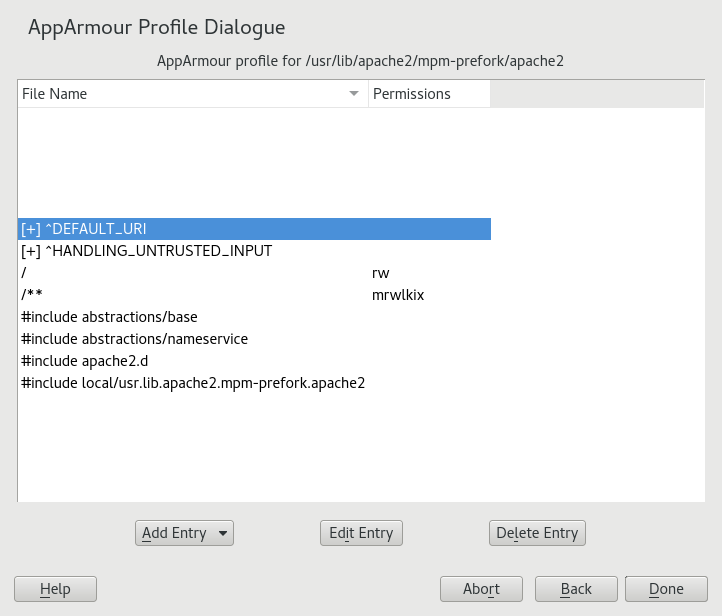
Click . The window displays the profile.
In the window, add, edit, or delete AppArmor profile entries by clicking the corresponding buttons and referring to Section 25.2.1, “Adding an Entry”, Section 25.2.2, “Editing an Entry”, or Section 25.2.3, “Deleting an Entry”.
When you are finished, click .
In the pop-up that appears, click to confirm your changes to the profile and reload the AppArmor profile set.
AppArmor contains a syntax check that notifies you of any syntax errors
in profiles you are trying to process with the YaST AppArmor tools.
If an error occurs, edit the profile manually as root and
reload the profile set with systemctl reload
apparmor.
25.2.1 Adding an Entry #
The button in the lists types of entries you can add to the AppArmor profile.
From the list, select one of the following:
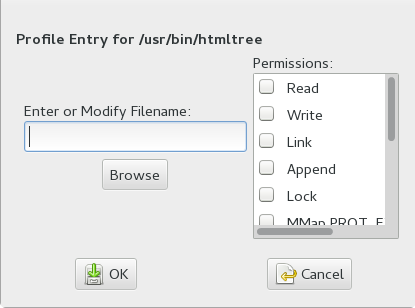
- File
In the pop-up window, specify the absolute path of a file, including the type of access permitted. When finished, click .
You can use globbing if necessary. For globbing information, refer to Section 23.6, “Profile Names, Flags, Paths, and Globbing”. For file access permission information, refer to Section 23.7, “File Permission Access Modes”.
- Directory
In the pop-up window, specify the absolute path of a directory, including the type of access permitted. You can use globbing if necessary. When finished, click .
For globbing information, refer to Section 23.6, “Profile Names, Flags, Paths, and Globbing”. For file access permission information, refer to Section 23.7, “File Permission Access Modes”.
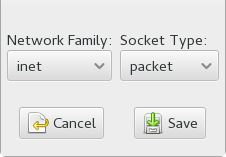
- Network Rule
In the pop-up window, select the appropriate network family and the socket type. For more information, refer to Section 23.5, “Network Access Control”.
- Capability
In the pop-up window, select the appropriate capabilities. These are statements that enable each of the 32 POSIX.1e capabilities. Refer to Section 23.4, “Capability Entries (POSIX.1e)” for more information about capabilities. When finished making your selections, click .
- Include File
In the pop-up window, browse to the files to use as includes. Includes are directives that pull in components of other AppArmor profiles to simplify profiles. For more information, refer to Section 23.3, “Include Statements”.
- Hat
In the pop-up window, specify the name of the subprofile (hat) to add to your current profile and click . For more information, refer to Chapter 27, Profiling Your Web Applications Using ChangeHat.
25.2.2 Editing an Entry #
When you select , a pop-up window opens. From here, edit the selected entry.
In the pop-up window, edit the entry you need to modify. You can use globbing if necessary. When finished, click .
For globbing information, refer to Section 23.6, “Profile Names, Flags, Paths, and Globbing”. For access permission information, refer to Section 23.7, “File Permission Access Modes”.
25.2.3 Deleting an Entry #
To delete an entry in a given profile, select . AppArmor removes the selected profile entry.
25.3 Deleting a Profile #
AppArmor enables you to delete an AppArmor profile manually. Simply select the application for which to delete a profile then delete it as follows:
Start YaST, select , and click in the main window.
Select the profile to delete.
Click .
In the pop-up that opens, click to delete the profile and reload the AppArmor profile set.
25.4 Managing AppArmor #
You can change the status of AppArmor by enabling or disabling it. Enabling AppArmor protects your system from potential program exploitation. Disabling AppArmor, even if your profiles have been set up, removes protection from your system. To change the status of AppArmor, start YaST, select , and click in the main window.
To change the status of AppArmor, continue as described in Section 25.4.1, “Changing AppArmor Status”. To change the mode of individual profiles, continue as described in Section 25.4.2, “Changing the Mode of Individual Profiles”.
25.4.1 Changing AppArmor Status #
When you change the status of AppArmor, set it to enabled or disabled. When AppArmor is enabled, it is installed, running, and enforcing the AppArmor security policies.
Start YaST, select , and click in the main window.
Enable AppArmor by checking or disable AppArmor by deselecting it.
Click in the window.
You always need to restart running programs to apply the profiles to them.
25.4.2 Changing the Mode of Individual Profiles #
AppArmor can apply profiles in two different modes. In
complain mode, violations of AppArmor profile rules,
such as the profiled program accessing files not permitted by the
profile, are detected. The violations are permitted, but also logged.
This mode is convenient for developing profiles and is used by the
AppArmor tools for generating profiles. Loading a profile in
enforce mode enforces the policy defined in the
profile, and reports policy violation attempts to
rsyslogd (or
auditd or
journalctl, depending on system
configuration).
The dialog allows you to view and edit the mode of currently loaded AppArmor profiles. This feature is useful for determining the status of your system during profile development. During systemic profiling (see Section 26.7.2, “Systemic Profiling”), you can use this tool to adjust and monitor the scope of the profiles for which you are learning behavior.
To edit an application's profile mode, proceed as follows:
Start YaST, select , and click in the main window.
In the section, select .
Select the profile for which to change the mode.
Select to set this profile to complain mode or to enforce mode.
Apply your settings and leave YaST with .
To change the mode of all profiles, use or .
By default, only active profiles are listed (any profile that has a matching application installed on your system). To set up a profile before installing the respective application, click and select the profile to configure from the list that appears.