Setting Up a FreeRADIUS Server
- WHAT?
FreeRADIUS is the open source RADIUS server implementation for AAA (Authentication, Authorization, and Accounting).
- WHY?
This article provides a complete overview of the FreeRADIUS server setup and basic FreeRADIUS configuration for testing.
- EFFORT
It takes 15 minutes to install and configure FreeRADIUS. You need up to an hour to fully understand the FreeRADIUS architecture and functionality.
- GOAL
Basic understanding of setting up and testing a FreeRADIUS server.
- REQUIREMENTS
A virtual machine or instance to install FreeRADIUS.
Another virtual machine on your network to test client functions.
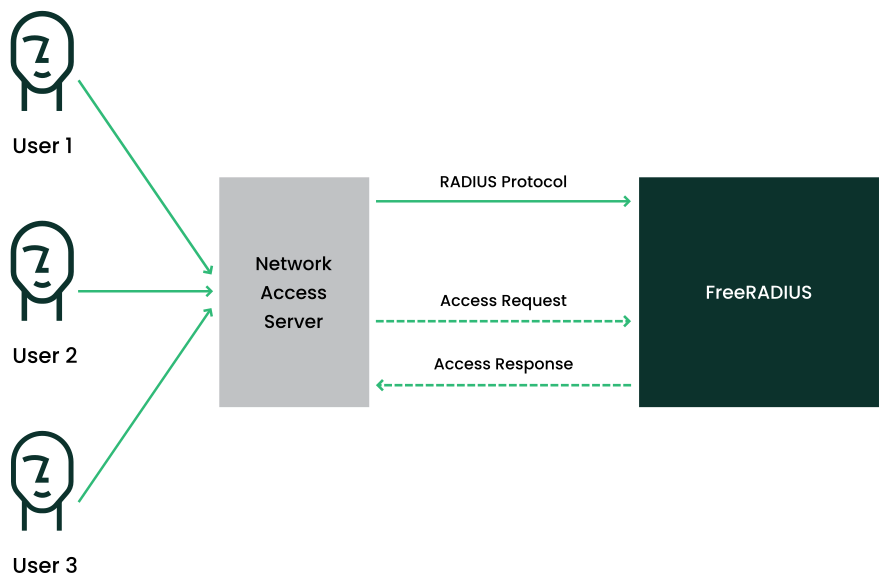
1 The FreeRADIUS concept #
The RADIUS (Remote Authentication Dial-In User Service) protocol is a standard service for managing network access. FreeRADIUS is the open source RADIUS server implementation and the most widely used RADIUS server.
FreeRADIUS verifies users and clients and manages network access and operations. FreeRADIUS ensures secure communication between network devices and user authentication servers.
FreeRADIUS performs authentication, authorization and accounting (AAA) for very large businesses such as Internet service providers and cellular network providers, and is also popular for small networks. It authenticates users and devices, authorizes those users and devices for certain network services, and tracks the use of services for billing and auditing. You do not have to use all three of the AAA protocols, use only the ones you need.
RADIUS operates over a distributed architecture and runs separately from the Network Access Server (NAS). User access data is stored on a central RADIUS server that is available to multiple NAS devices. The NAS provides physical access to the network, such as a managed Ethernet switch or a wireless access point. FreeRADIUS verifies and manages network access and operations. FreeRADIUS ensures secure communication between network devices and user authentication servers. To set up a FreeRADIUS server, you must install, configure and define user accounts, and define and determine authentication and authorization for FreeRADIUS. After installing FreeRADIUS, you must test the function by integrating FreeRADIUS with the devices to be managed.
This article includes an example that shows installing FreeRADIUS, creating a set of test certificates, starting the server, adding client server and user, testing authentication, and testing multiple clients.
2 Installing the FreeRADIUS server #
The following example shows how to install a FreeRADIUS server. Ensure that you install the freeradius-server and freeradius-server-utils packages on a separate machine from your Network Access Server (NAS).
Install freeradius-server and freeradius-server-utils.
>sudosudo zypper install freeradius-server and freeradius-server-utils
3 Creating test certificates on the server #
Certificates enable secure communication between the FreeRADIUS clients and the FreeRADIUS server.
To allow access to the server, certificate authentication is required. To test the authentication using FreeRADIUS, you can create test certificates. The following example shows how to create test certificates to test FreeRADIUS. Ensure that you remove the test certificates and use the correct certificates after testing FreeRADIUS.
The test certificates created are not suitable for production use.
Create a set of test certificates in /etc/raddb/certs.
> cd /etc/raddb/certs
./bootstrapWhen you are satisfied with your testing and ready to create a production configuration, remove all the test certificates in /etc/raddb/certs and replace them with your own certificates.
4 Starting FreeRADIUS on the server #
You must start FreeRADIUS on the server after installation.
After the bootstrap is complete, start the server in debugging mode as a root user.
To do this, run the following command:
NoteStart the FreeRADIUS server in debugging mode only for testing. Other than for testing, use
sudo systemctl start freeradius>sudoradiusd -X [...] Listening on auth address * port 1812 bound to server default Listening on acct address * port 1813 bound to server default Listening on auth address :: port 1812 bound to server default Listening on acct address :: port 1813 bound to server default Listening on auth address 127.0.0.1 port 18120 bound to server inner-tunnel Listening on proxy address * port 54435 Listening on proxy address :: port 58415 Ready to process requestsThe
ListeningandReady to process requestsappear when the server starts correctly.
5 Adding a test client with a user on the server #
You can add a client and a user to test authentication for the FreeRADIUS server. The client is a client of the RADIUS server, such as a wireless access point or switch. The users are added in the user configuration file and the clients are added in the client configuration file. These configuration files are stored on the server where FreeRADIUS is installed.
The machines that can use the devices of the FreeRADIUS server are defined in the client.conf file.
Add the machines that can use the devices of the FreeRADIUS server and the users by using the following example:
Configure users in the authorization file,
/etc/raddb/mods-config/files/authorize.To do this, open
/etc/raddb/mods-config/files/authorizeand uncomment the following lines:bob Cleartext-Password := "hello" Reply-Message := "Hello, %{User-Name}" "john" Cleartext-Password := "newpassword" Service-Type = New-User, Framed-IP-Address = 190.155.2.50Add a test client and user to test the authentication in
/etc/raddb/client.conf.vi /etc/raddb/client.conf
A test client, localhost, is provided in
/etc/raddb/client.conf, with the secrettesting123.client private-networks { ipaddr = 190.1.0/22 secret = testingabc-1 } client common-network { ipaddr = 191.1.0/27 secret = testingxyz }Add clients of the RADIUS server, such as a wireless access point, network switch, or another form of NAS.
Create a client configuration on your server by using the following example.
Uncomment the following entry in
/etc/raddb/client.confand use the IP address of your test client machine or access gateway instead of the given IP address.client private-network-1 { ipaddr = 192.0.2.0/24 secret = testing123-1 }You must also configure the client to talk to the RADIUS server by using the IP address of the machine running the RADIUS server. The client must use the same secret as configured above in the client section.
On the client machine, install
freeradius-server-utils.>sudosudo zypper install freeradius-server and freeradius-server-utils
You can now add more users and configure databases.
Run one more login test from a different computer on your network.
6 Starting the FreeRADIUS daemon on the server #
After adding client and user, you must start the FreeRADIUS daemon.
Start the FreeRADIUS daemon to provide authentication, authorization, and accounting (AAA) services in a network environment for network access control and network access management.
Start the FreeRADIUS daemon.
>sudosystemctl restart freeradiusEnable auto-start for FreeRADIUS on system boot up.
>sudosystemctl enable freeradius
7 Testing authentication on the client #
You can test the authentication for the newly added user in FreeRADIUS.
Test the authentication for the newly added user using the following example:
Open a new terminal, and as an unprivileged user, use the
radtestcommand to log in as the newly added userbob.>radtest bob hello 127.0.0.1 0 testing123 Sent Access-Request Id 241 from 0.0.0.0:35234 to 127.0.0.1:1812 length 73 User-Name = "bob" User-Password = "hello" NAS-IP-Address = 127.0.0.1 NAS-Port = 0 Message-Authenticator = 0x00 Cleartext-Password = "hello" Received Access-Accept Id 241 from 127.0.0.1:1812 to 0.0.0.0:0 length 20After the authentication is successful, a login message appears in the terminal in which you started FreeRADIUS, as shown below.
(3) pap: Login attempt with password (3) pap: Comparing with "known good" Cleartext-Password (3) pap: User authenticated successfully (3) [pap] = ok [...] (3) Sent Access-Accept Id 241 from 127.0.0.1:1812 to 127.0.0.1:35234 length 0 (3) Finished request Waking up in 4.9 seconds. (3) Cleaning up request packet ID 241 with timestamp +889The access request is successful and the authentication methods PAP, CHAP, MS-CHAPv1, MS-CHAPv2, PEAP, EAP-TTLS, EAP-GTC, EAP-MD5 work for the user
bob.
8 Troubleshooting FreeRADIUS #
There are several test users and test clients provided. Ensure that your server has the correct firewall settings. If your test logins fail, review all the output to understand the issues.
Possible troubleshooting methods are given below:
Check FreeRADIUS logs in
/var/log/freeradius/radius.logor/var/log/radius/radius.log.Check if FreeRADIUS is running.
systemctl status freeradius
If FreeRADIUS is not running, start FreeRADIUS.
systemctl start freeradius
If a FreeRADIUS server is already running, an error
Address already in useappears. Stop that server before running the server in debugging mode.If the server does not start, verify the output. The output includes the details about the errors. You can direct the output to a text file with
tee:radiusd -X | tee radiusd.text
Check if the ports for FreeRADIUS in the firewall are open for communication.
Check user authentication.
radtest username password localhost 0 testing123
Verify client configuration. Ensure that the secret and IP in the client and the FreeRADIUS server match.
Update FreeRADIUS software. Ensure that you use the latest stable version of FreeRADIUS.
When you are satisfied with your testing and ready to create a production configuration, remove all the test certificates in /etc/raddb/certs and replace them with your own certificates, comment out all the test users and clients, and stop radiusd by pressing Ctrl–C. Manage the radiusd.service with systemctl, just like any other service.
9 Legal Notice #
Copyright© 2006–2026 SUSE LLC and contributors. All rights reserved.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”.
For SUSE trademarks, see https://www.suse.com/company/legal/. All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors, nor the translators shall be held liable for possible errors or the consequences thereof.