Creating Customized Virtual Machines Using virt-scenario
- WHAT?
When deploying multiple virtual machines (VM), they often serve a similar purpose.
virt-scenariooffers a way to quickly create a VM following a predefined scenario. As an option, you can create a secure VM or override certain defaultvirt-scenariosettings.- WHY?
This article introduces the
virt-scenariotool and describes available predefined scenarios for creating VMs. It outlines steps to create a VM suitable for a selected scenario, as well as available commands for thevirt-scenariointeractive shell.- EFFORT
It takes up to 30 minutes to understand
virt-scenarioand use it to create a basic VM. To learn and try additional topics, for example, how to override default values or use interactive commands, you need additional time.- REQUIREMENTS
virt-scenariorequires KVM andlibvirtvirtualization environment configured and related daemons running.Secure virtual machines are supported only by an AMD processor that supports AMD SEV or SEV-ES technology. For more information about SUSE and AMD SEV, refer to https://documentation.suse.com/sles/html/SLES-amd-sev/article-amd-sev.html.
1 Introduction to virt-scenario #
virt-scenario is a tool that helps you create virtual machines (VM)
suitable for a specific scenario. It provides predefined
profiles that include optimal settings for each
scenario. You can override settings that are common to all profiles.
Although virt-scenario generally provides the best possible
configuration for a specific scenario, this cannot be guaranteed because
each environment may have specific requirements.
1.1 How does virt-scenario work? #
An interactive virt-scenario script creates a libvirt XML configuration
file for a VM based on the following:
selected basic profile
overridden values for common parameters
parameters that you specify interactively
After the configuration is validated, virt-scenario adjusts the
VM Host Server system and creates the image file for the VM Guest. You can
then operate the VM using standard libvirt commands.
1.2 Benefits of using virt-scenario #
Creating virtual machines is fast and simple.
virt-scenarioleaves all the virtualization complexity aside. You can focus on basic features only.Fine-tuned profiles already offer optimal settings for specified scenarios. You do not have to search and copy them to each virtual machine of the same type, just use the same profile.
The override mechanism lets you specify other values than the profile's default for selected options. This way, you can customize virtual machines to your needs.
2 Creating VMs #
The virt-scenario command presents an interactive shell where you
optionally specify configuration parameters and finally select the target
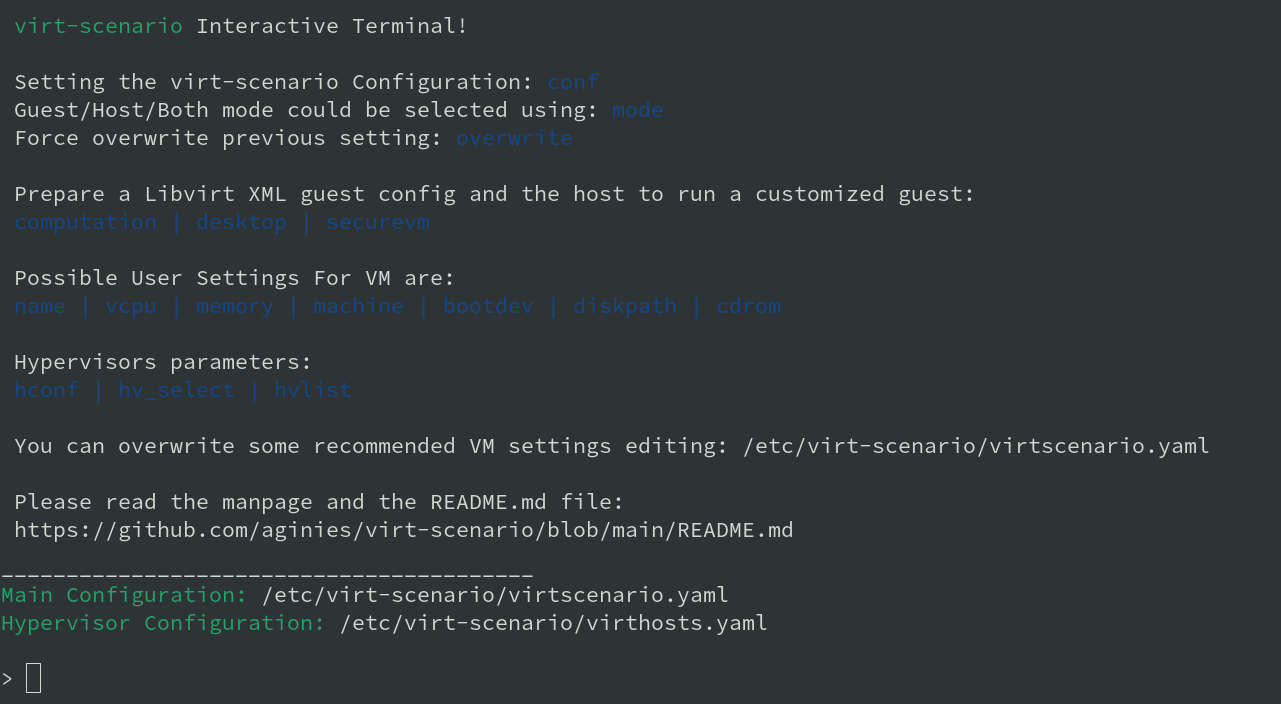
scenario. Its welcome screen shows categories with available commands.
virt-scenario welcome screen #
Each command has a built-in description of its usage. Enter help
COMMAND_NAME to view it on the
screen.
force_sev option
The force_sev option is only provided for
testing purposes. It forces the extraction of the
Platform Diffie-Hellman key (PDH) on the current AMD SEV system. The PDH
file is used to negotiate a master secret between the SEV firmware and
the external entities. This file must be stored in a secure place.
After you finish the optional configuration steps, enter the name of one of the
scenarios—computation, desktop
or securevm. virt-scenario then compiles all the
configuration, prepares the VM Host Server, and saves the libvirt XML file of the
new VM in ~/.local/virt-scenario/vmconfig.
2.1 Overriding default scenario settings #
On each run, virt-scenario reads settings for a new VM from the
/etc/virt-scenario/virtscenario.yaml file. Change
settings in this file to affect all VMs created by
virt-scenario.
The following is an example of
/etc/virt-scenario/virtscenario.yaml:
config: - path: /etc/virt-scenario - vm-config-store: ~/.local/virtscenario/ emulator: - emulator: /usr/bin/qemu-system-x86_64 input: - keyboard: virtio - mouse: virtio architecture: - arch: x86_64 STORAGE_DATA: # some options are only available with qcow2 format and # will be ignored in case of any other image format - disk_type: file - disk_cache: none - disk_target: vda - disk_bus: virtio - path: /var/livirt/images - format: qcow2 # host side: qemu-img creation options (-o), qemu-img --help - unit: G - capacity: 20 - cluster_size: 1024k - lazy_refcounts: on preallocation: full - preallocation: off - compression_type: zlib - encryption: off host_filesystem: - fmode: 644 - dmode: 755 - source_dir: /tmp - target_dir: /tmp/host
Back up
/etc/virt-scenario/virtscenario.yamlbefore modifying it as incorrect parameters may lead to an invalid VM configuration.Copy
/etc/virt-scenario/virtscenario.yamlto a different location and modify the settings that you need to override.Important: Include all settings and keep section namesIn the overriding
virtscenario.yamlfile, you need to include all available settings from the originalvirtscenario.yamlfile, not only the modified settings. Also, never change section names invirtscenario.yamlor its overriding copies. Doing so might causevirt-scenarioto misinterpret matching settings, leading to an invalid VM configuration.On the next
virt-scenariorun, specify the path to the new configuration file with theconfcommand, for example:> conf /home/tux/virt-scenarios/my-overriden-scenario.yaml
2.2 Specifying the virt-scenario mode #
By default, virt-scenario creates the libvirt XML configuration of
the new guest and adjusts the VM Host Server. You can instruct virt-scenario
to perform only part of the task. After entering the
mode command, you can specify one of the following options:
- guest
Creates only the
libvirtXML configuration of the guest. Useguestif you want to create an XML representation of a VM but not modify the host machine settings. Suitable for transferring the XML to another host.- host
Prepares the VM Host Server system only. When deploying multiple VMs with similar configuration, the host system may already have been adjusted appropriately, and it is useless to adjust it again.
- both
Creates the guest configuration and prepares the host. This is the default mode.
2.3 Interactive commands #
You can use the following commands when configuring a new VM
using the virt-scenario interactive shell.
Each command has a built-in description of its usage. Enter help
COMMAND_NAME to view it on the
screen.
- hvconf
Loads the hypervisor configuration.
- hvselect
Sets the hypervisor for which VMs are configured.
- hvlist
Lists the available hypervisors.
- overwrite
Forces overwriting the previous configuration.
- name
Defines the name of the VM.
- vcpu
Specifies the number of virtual CPUs.
- memory
Specifies the memory size (in GiB).
- machine
Selects the machine type.
- bootdev
Selects the boot device.
- diskpath
Specifies the directory where to store the VM disk image.
- conf
Specifies the path to the custom
virtscenario.yamlfile.- cdrom
Specifies the path to the CD/DVD installation media.
- computation
Creates a
libvirtXML configuration and VM Host Server adjustments for the computation scenario.- desktop
Creates a
libvirtXML configuration and VM Host Server adjustments for the desktop scenario.- securevm
Creates a
libvirtXML configuration and VM Host Server adjustments for the secure VM scenario.
3 Predefined scenarios #
When creating a VM, you can specify one of the following scenarios:
- securevm
Selecting this scenario results in an encrypted VM image with a high level of isolation and data security.
- computation
This scenario puts emphasis on the high performance of the resulting VM.
- desktop
The result of this scenario is a VM suitable for running desktop applications.
The following tables show default settings for each scenario:
|
Setting |
securevm |
computation |
desktop |
|---|---|---|---|
|
preallocation |
metadata |
off |
metadata |
|
encryption |
on |
off |
off |
|
disk_cache |
writethrough |
unsafe* |
none |
|
lazy_refcounts |
on |
on |
off |
|
format |
qcow2 |
raw |
qcow2 |
|
disk bus |
virtio |
virtio |
virtio |
|
capacity |
20G |
20G |
20G |
|
cluster_size |
1024k |
N/A |
1024k |
* the unsafe cache mode may cause data loss and, for example,
destroy a Btrfs file system after an unclean shutdown
|
Setting |
securevm |
computation |
desktop |
|---|---|---|---|
|
Transparent HugePages |
on |
on |
on |
|
KSM |
disable |
enable |
enable |
|
KSM merge across |
disable |
enable |
enable |
|
swappiness |
0 |
0 |
35 |
|
IO Scheduler |
bfq |
mq-deadline |
mq-deadline |
|
Setting |
securevm |
computation |
desktop |
|---|---|---|---|
|
CPU migratable |
off |
off |
on |
|
machine |
pc-q35-6.2 |
pc-q35-6.2 |
pc-q35-6.2 |
|
watchdog |
none |
i6300esb poweroff |
none |
|
boot UEFI |
auto |
auto |
auto |
|
vTPM |
tpm-crb 2.0 |
none |
none |
|
iothreads |
disable |
4 |
4 |
|
video |
qxl |
qxl |
virtio |
|
network |
e1000 |
virtio |
e1000 |
|
keyboard |
ps2 |
virtio |
virtio |
|
mouse |
disable |
virtio |
virtio |
|
on_poweroff |
destroy |
restart |
destroy |
|
on_reboot |
destroy |
restart |
restart |
|
on_crash |
destroy |
restart |
destroy |
|
suspend_to_mem |
off |
off |
on |
|
suspend_to_disk |
off |
off |
on |
|
features |
acpi apic pae |
acpi apic pae |
acpi apic pae |
|
host fs fmode, dmode, source_dir, target_dir |
N/A |
N/A |
644 755 /tmp/ /tmp/host |
|
Setting |
securevm |
computation |
desktop |
|---|---|---|---|
|
kvm SEV |
mem_encrypt=on kvm_amd sev=1 sev_es=1 |
N/A |
N/A |
|
sec cbitpos |
auto |
N/A |
N/A |
|
sec reducedPhysBits |
auto |
N/A |
N/A |
|
sec policy |
auto |
N/A |
N/A |
4 Managing VMs #
After you created a VM using the virt-scenario interactive shell, use the
virt-scenario-launch command to manage it. The command
identifies VMs by their name as displayed by the --list
option.
#virt-scenario-launch --listVersion: 2.1.2 Available VMs: ALP_OS desktop testing_vm SLE15_HPC
When the VM is identified, you can manage it by passing the following options to virt-scenario-launch.
--helpPrints short descriptions of available options.
--startStarts the VM and prints security attestation information, for example:
#virt-scenario-launch --start ALP_OSConnected to libvirtd socket; Version: 7001000 SEV(-ES) attestation passed! Validation successfull for domain ALPOS--statusShows the status of the VM, for example:
#virt-scenario-launch --status ALP_OSVersion: 2.1.2 Connecting to libvirt qemu:///system ... Connected to libvirtd socket; Version: 7001000 Domain SLE15SP5HPC state: Shutoff--offShuts a VM down.
#virt-scenario-launch --off ALP_OS--forceForces a VM off.
#virt-scenario-launch --force ALP_OS