- I Planning an Installation using Cloud Lifecycle Manager
- 1 Registering SLES
- 2 Hardware and Software Support Matrix
- 3 Recommended Hardware Minimums for the Example Configurations
- 3.1 Recommended Hardware Minimums for an Entry-scale KVM
- 3.2 Recommended Hardware Minimums for an Entry-scale ESX KVM Model
- 3.3 Recommended Hardware Minimums for an Entry-scale ESX, KVM with Dedicated Cluster for Metering, Monitoring, and Logging
- 3.4 Recommended Hardware Minimums for an Ironic Flat Network Model
- 3.5 Recommended Hardware Minimums for an Entry-scale Swift Model
- 4 High Availability
- 4.1 High Availability Concepts Overview
- 4.2 Highly Available Cloud Infrastructure
- 4.3 High Availability of Controllers
- 4.4 High Availability Routing - Centralized
- 4.5 Availability Zones
- 4.6 Compute with KVM
- 4.7 Nova Availability Zones
- 4.8 Compute with ESX Hypervisor
- 4.9 cinder Availability Zones
- 4.10 Object Storage with Swift
- 4.11 Highly Available Cloud Applications and Workloads
- 4.12 What is not Highly Available?
- 4.13 More Information
- II Cloud Lifecycle Manager Overview
- 5 Input Model
- 6 Configuration Objects
- 7 Other Topics
- 8 Configuration Processor Information Files
- 8.1 address_info.yml
- 8.2 firewall_info.yml
- 8.3 route_info.yml
- 8.4 server_info.yml
- 8.5 service_info.yml
- 8.6 control_plane_topology.yml
- 8.7 network_topology.yml
- 8.8 region_topology.yml
- 8.9 service_topology.yml
- 8.10 private_data_metadata_ccp.yml
- 8.11 password_change.yml
- 8.12 explain.txt
- 8.13 CloudDiagram.txt
- 8.14 HTML Representation
- 9 Example Configurations
- 10 Modifying Example Configurations for Compute Nodes
- 11 Modifying Example Configurations for Object Storage using Swift
- 11.1 Object Storage using swift Overview
- 11.2 Allocating Proxy, Account, and Container (PAC) Servers for Object Storage
- 11.3 Allocating Object Servers
- 11.4 Creating Roles for swift Nodes
- 11.5 Allocating Disk Drives for Object Storage
- 11.6 Swift Requirements for Device Group Drives
- 11.7 Creating a Swift Proxy, Account, and Container (PAC) Cluster
- 11.8 Creating Object Server Resource Nodes
- 11.9 Understanding Swift Network and Service Requirements
- 11.10 Understanding Swift Ring Specifications
- 11.11 Designing Storage Policies
- 11.12 Designing Swift Zones
- 11.13 Customizing Swift Service Configuration Files
- 12 Alternative Configurations
- III Pre-Installation
- IV Cloud Installation
- 19 Overview
- 20 Preparing for Stand-Alone Deployment
- 21 Installing with the Install UI
- 22 Using Git for Configuration Management
- 23 Installing a Stand-Alone Cloud Lifecycle Manager
- 24 Installing Mid-scale and Entry-scale KVM
- 24.1 Important Notes
- 24.2 Prepare for Cloud Installation
- 24.3 Configuring Your Environment
- 24.4 Provisioning Your Baremetal Nodes
- 24.5 Running the Configuration Processor
- 24.6 Configuring TLS
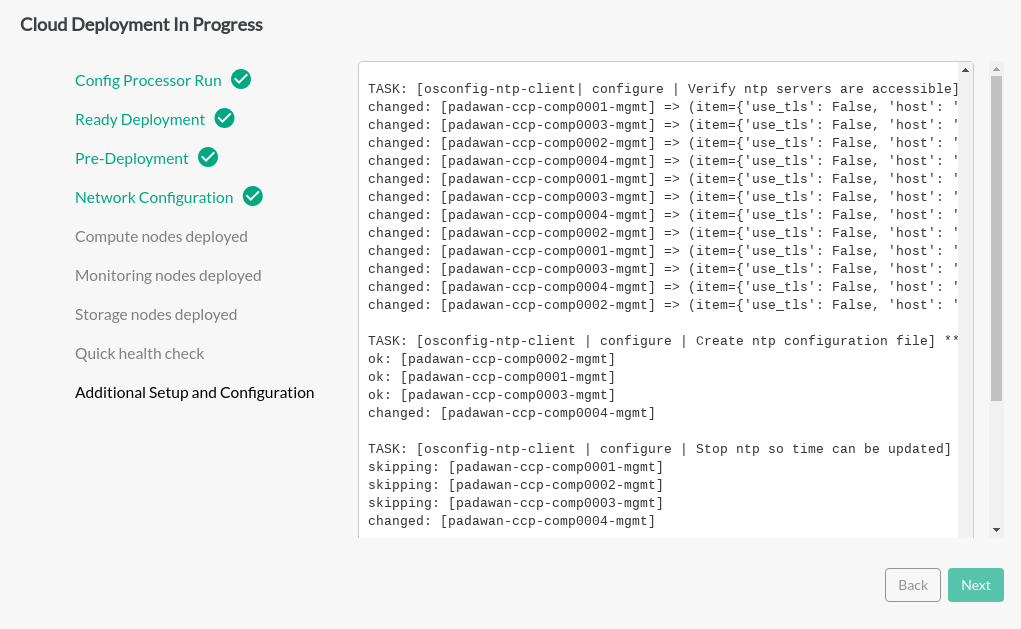
- 24.7 Deploying the Cloud
- 24.8 Configuring a Block Storage Backend
- 24.9 Post-Installation Verification and Administration
- 25 DNS Service Installation Overview
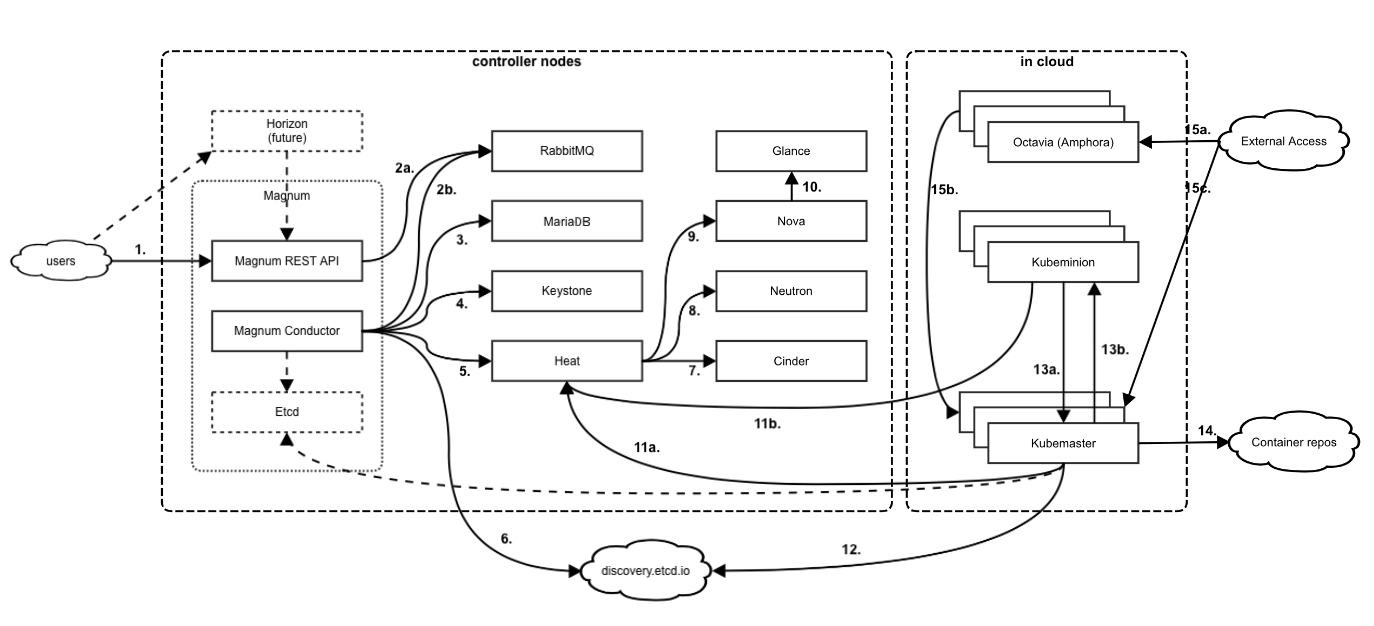
- 26 Magnum Overview
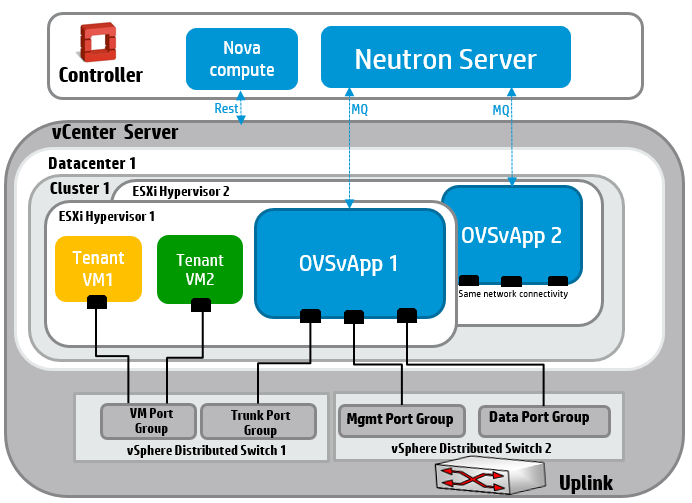
- 27 Installing ESX Computes and OVSvAPP
- 27.1 Prepare for Cloud Installation
- 27.2 Setting Up the Cloud Lifecycle Manager
- 27.3 Overview of ESXi and OVSvApp
- 27.4 VM Appliances Used in OVSvApp Implementation
- 27.5 Prerequisites for Installing ESXi and Managing with vCenter
- 27.6 ESXi/vCenter System Requirements
- 27.7 Creating an ESX Cluster
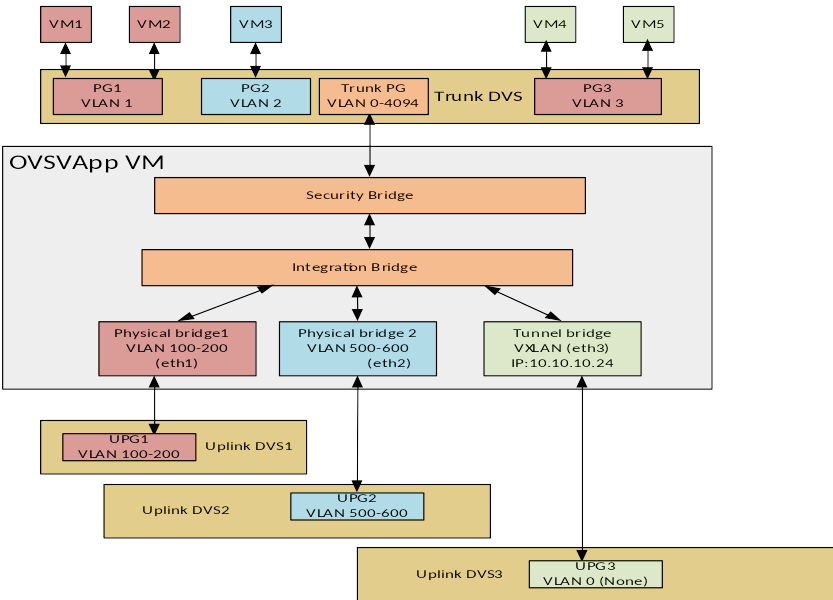
- 27.8 Configuring the Required Distributed vSwitches and Port Groups
- 27.9 Create a SUSE-based Virtual Appliance Template in vCenter
- 27.10 ESX Network Model Requirements
- 27.11 Creating and Configuring Virtual Machines Based on Virtual Appliance Template
- 27.12 Collect vCenter Credentials and UUID
- 27.13 Edit Input Models to Add and Configure Virtual Appliances
- 27.14 Running the Configuration Processor With Applied Changes
- 27.15 Test the ESX-OVSvApp Environment
- 28 Integrating NSX for vSphere
- 29 Installing Baremetal (Ironic)
- 29.1 Installation for SUSE OpenStack Cloud Entry-scale Cloud with Ironic Flat Network
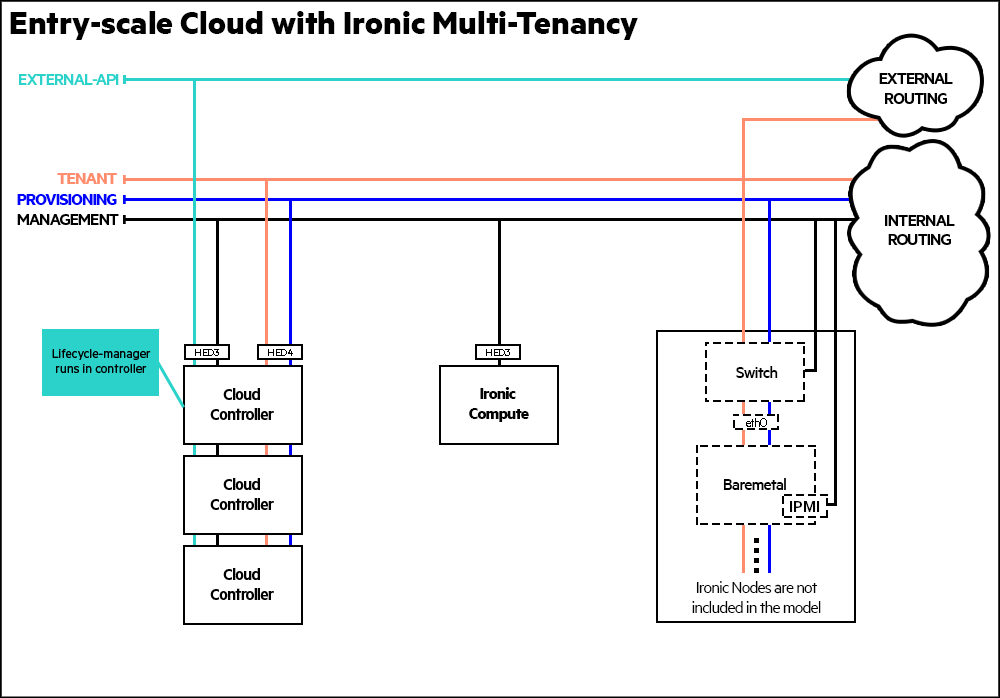
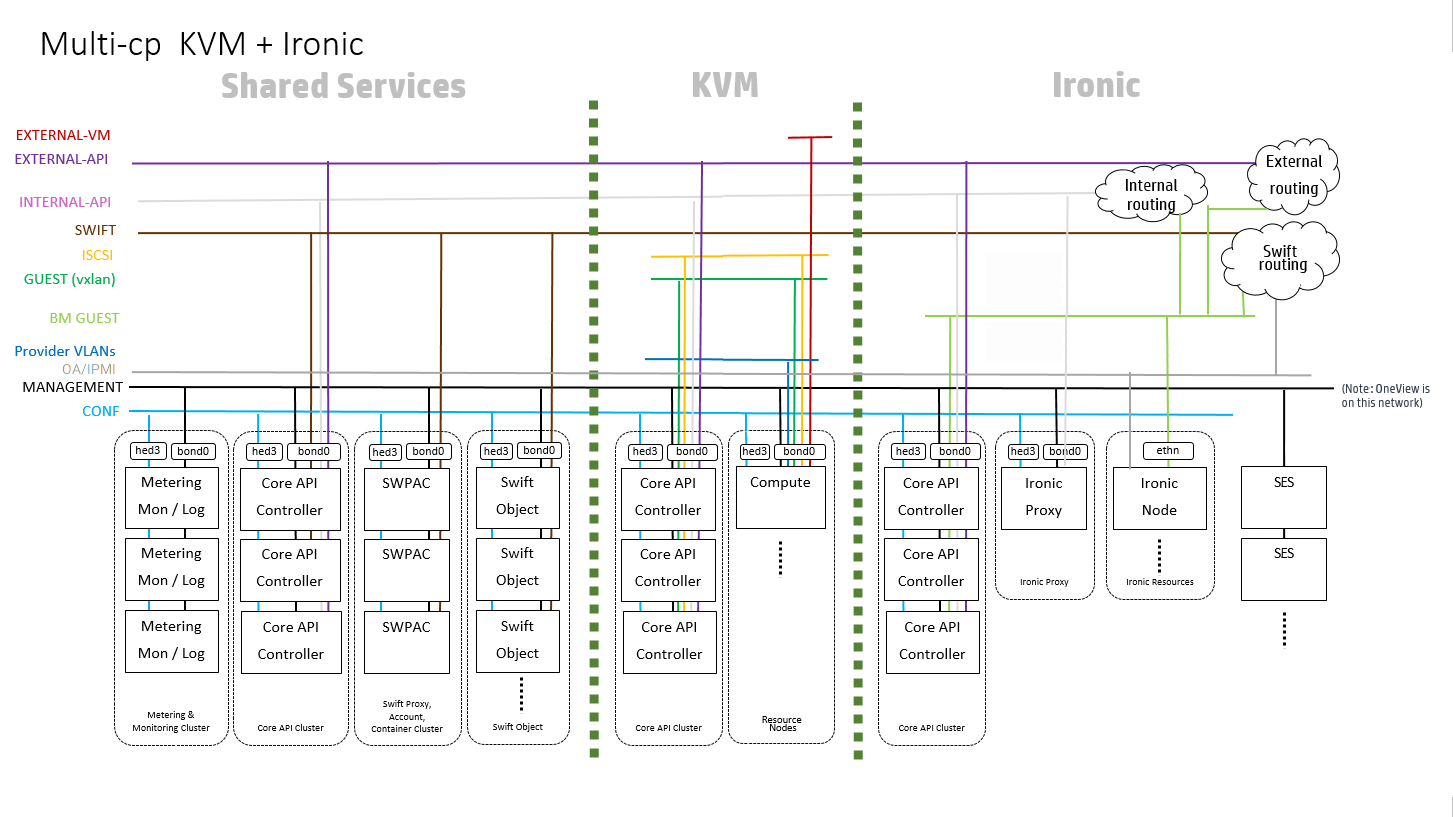
- 29.2 ironic in Multiple Control Plane
- 29.3 Provisioning Bare-Metal Nodes with Flat Network Model
- 29.4 Provisioning Baremetal Nodes with Multi-Tenancy
- 29.5 View Ironic System Details
- 29.6 Troubleshooting ironic Installation
- 29.7 Node Cleaning
- 29.8 Ironic and HPE OneView
- 29.9 RAID Configuration for Ironic
- 29.10 Audit Support for Ironic
- 30 Installation for SUSE OpenStack Cloud Entry-scale Cloud with Swift Only
- 31 Installing SLES Compute
- 32 Installing manila and Creating manila Shares
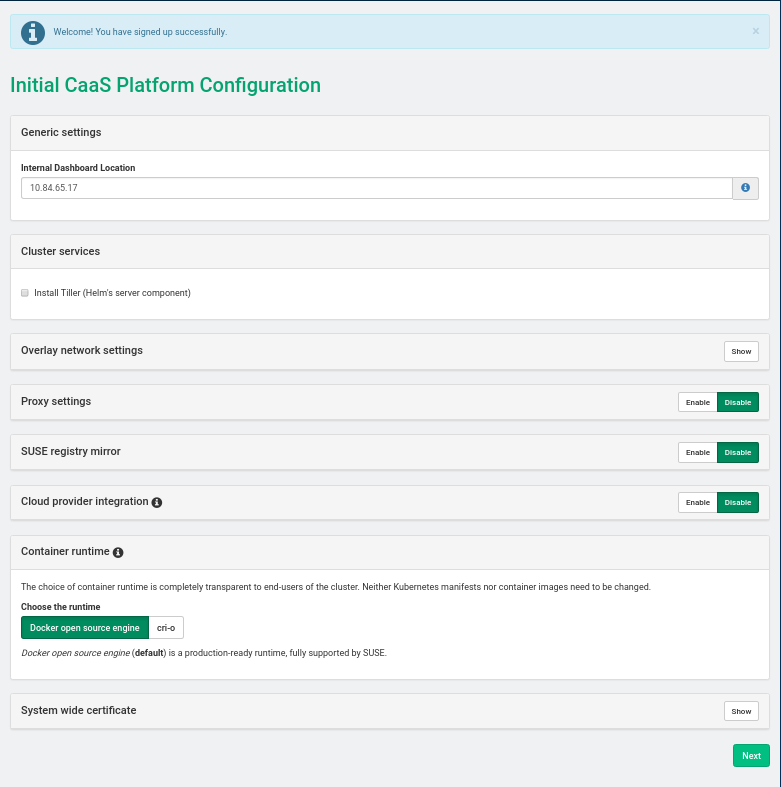
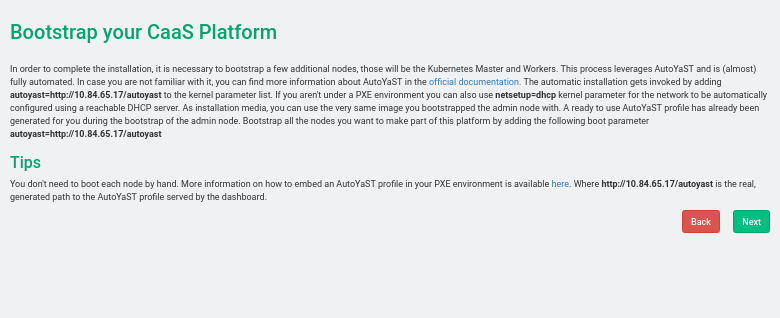
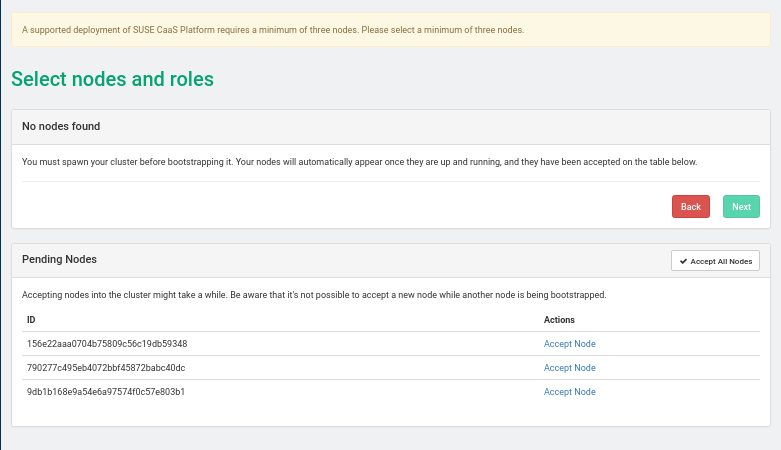
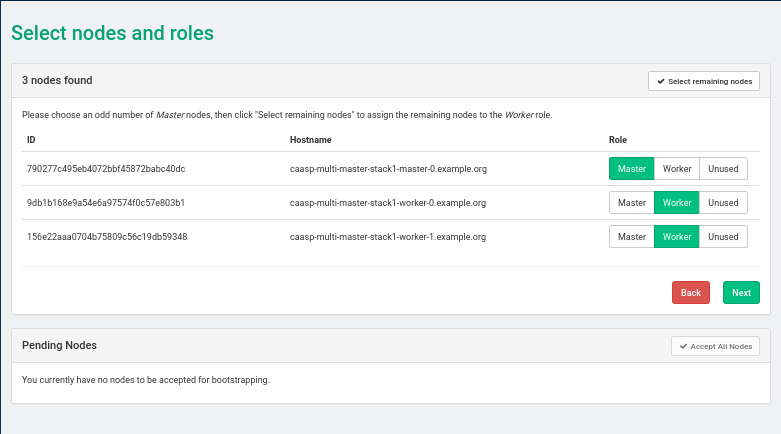
- 33 Installing SUSE CaaS Platform heat Templates
- 33.1 SUSE CaaS Platform heat Installation Procedure
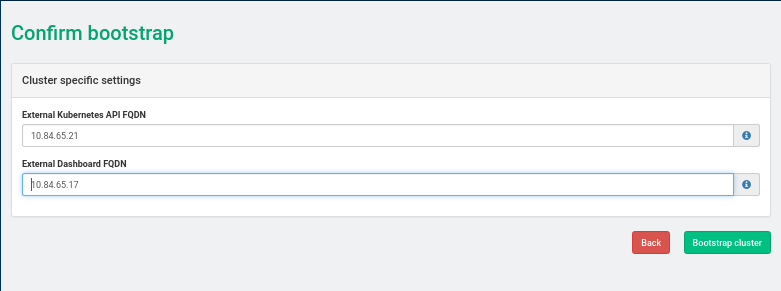
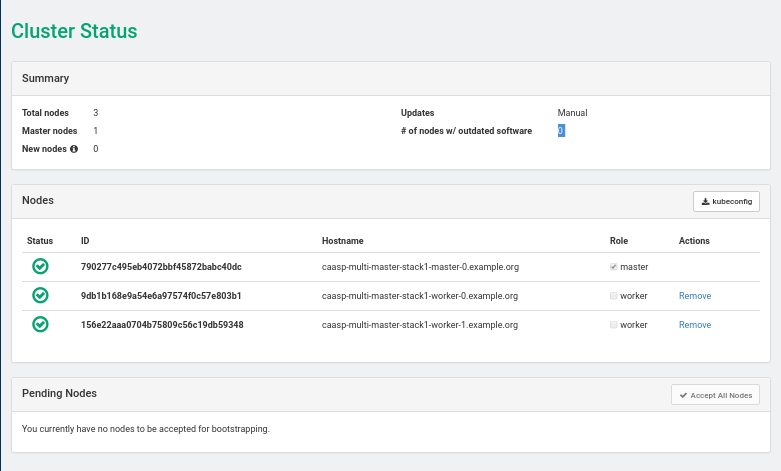
- 33.2 Installing SUSE CaaS Platform with Multiple Masters
- 33.3 Deploy SUSE CaaS Platform Stack Using heat SUSE CaaS Platform Playbook
- 33.4 Deploy SUSE CaaS Platform Cluster with Multiple Masters Using heat CaasP Playbook
- 33.5 SUSE CaaS Platform OpenStack Image for heat SUSE CaaS Platform Playbook
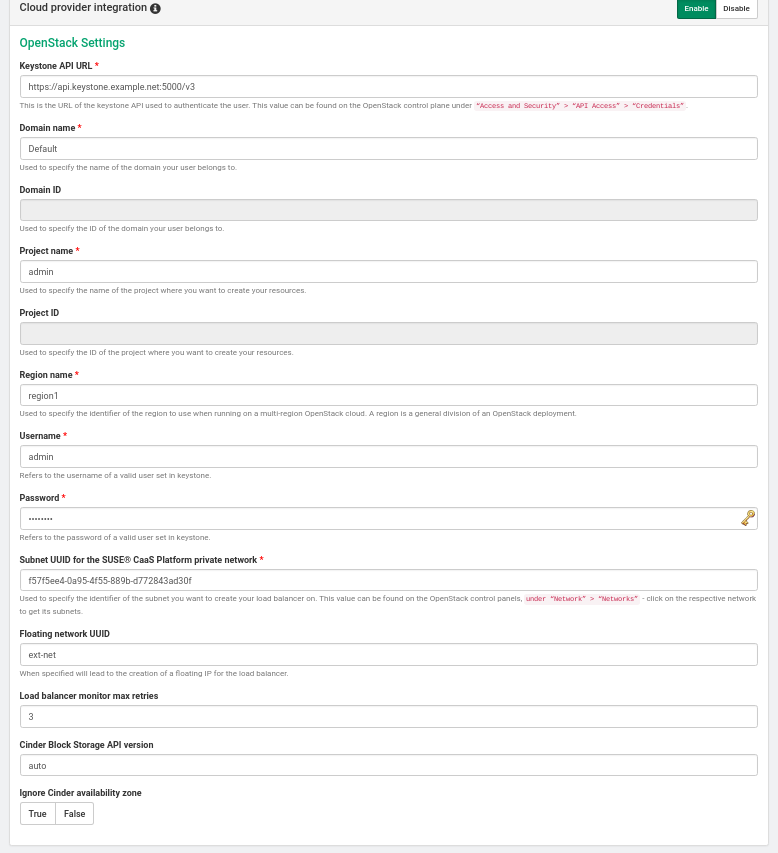
- 33.6 Enabling the Cloud Provider Integration (CPI) Feature
- 33.7 Register SUSE CaaS Platform Cluster for Software Updates
- 34 Installing SUSE CaaS Platform v4 using terraform
- 35 Integrations
- 36 Troubleshooting the Installation
- 37 Troubleshooting the ESX
- V Post-Installation
- 38 Post Installation Tasks
- 39 UI Verification
- 40 Installing OpenStack Clients
- 41 Configuring Transport Layer Security (TLS)
- 41.1 Configuring TLS in the input model
- 41.2 User-provided certificates and trust chains
- 41.3 Edit the input model to include your certificate files
- 41.4 Generate a self-signed CA
- 41.5 Generate a certificate signing request
- 41.6 Generate a server certificate
- 41.7 Upload to the Cloud Lifecycle Manager
- 41.8 Configuring the cipher suite
- 41.9 Testing
- 41.10 Verifying that the trust chain is correctly deployed
- 41.11 Turning TLS on or off
- 42 Configuring Availability Zones
- 43 Configuring Load Balancer as a Service
- 44 Other Common Post-Installation Tasks
- VI Support
- 6.1 neutron.networks.vxlan
- 6.2 neutron.networks.vlan
- 6.3 neutron.networks.flat
- 6.4 neutron.l3_agent.external_network_bridge
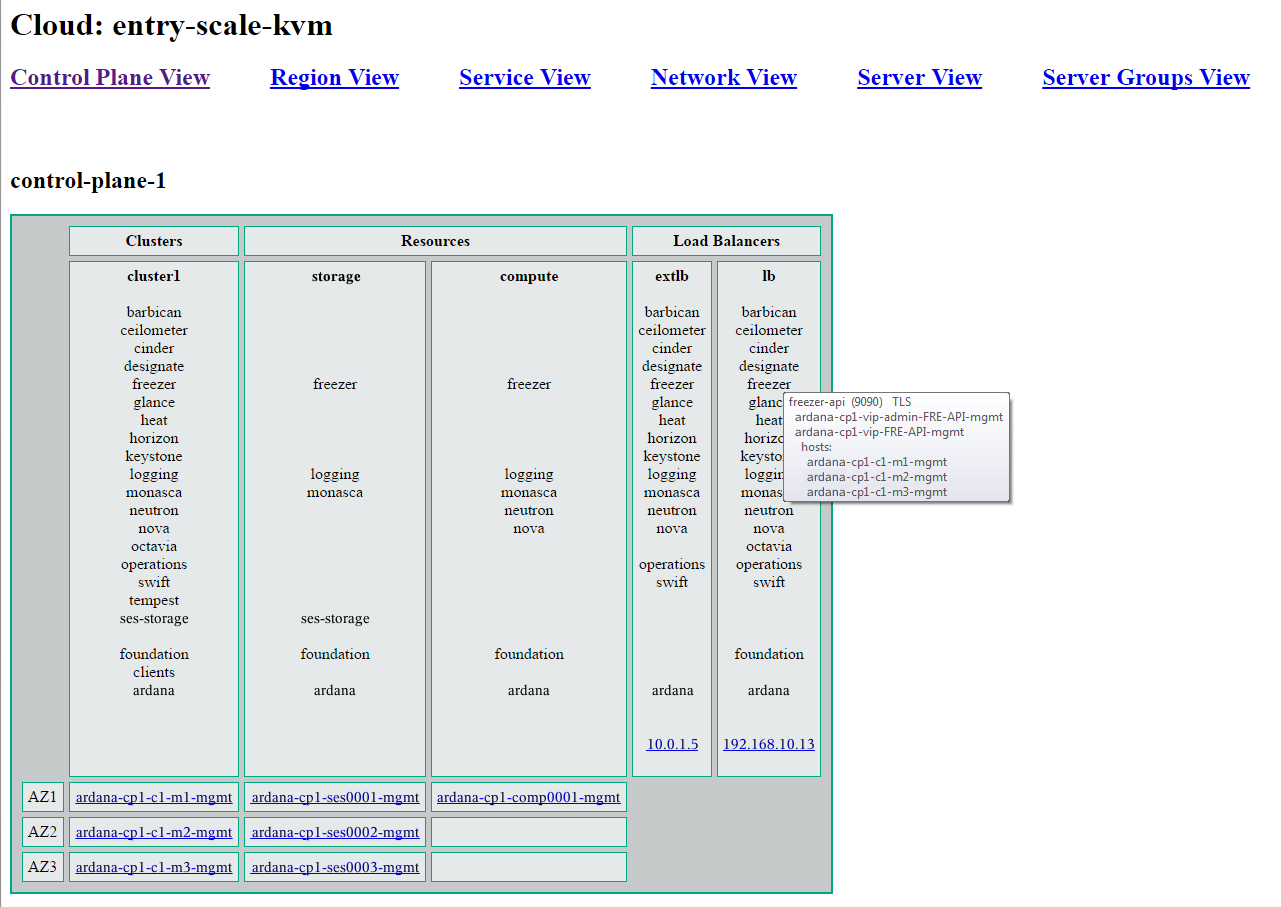
- 14.1 Control Plane 1
- 14.2 Control Plane 2
- 14.3 Control Plane 3
- 17.1 Local Product Repositories for SUSE OpenStack Cloud
- 17.2 SMT Repositories Hosted on the Cloud Lifecycle Manager
- 17.3 Repository Locations on the Cloud Lifecycle Manager server
- 25.1 DNS Backends
- 26.1 Data
- 26.2 Interfaces
- 26.3 Security Groups
- 26.4 Network Ports
- 28.1 NSX Hardware Requirements for Virtual Machine Integration
- 28.2 NSX Hardware Requirements for Baremetal Integration
- 28.3 NSX Interface Requirements
Copyright © 2006– 2024 SUSE LLC and contributors. All rights reserved.
Except where otherwise noted, this document is licensed under Creative Commons Attribution 3.0 License : https://creativecommons.org/licenses/by/3.0/legalcode.
For SUSE trademarks, see https://www.suse.com/company/legal/. All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof.
Part I Planning an Installation using Cloud Lifecycle Manager #
- 1 Registering SLES
To get technical support and product updates, you need to register and activate your SUSE product with the SUSE Customer Center. It is recommended to register during the installation, since this will enable you to install the system with the latest updates and patches available. However, if you are …
- 2 Hardware and Software Support Matrix
This document lists the details about the supported hardware and software for SUSE OpenStack Cloud 9
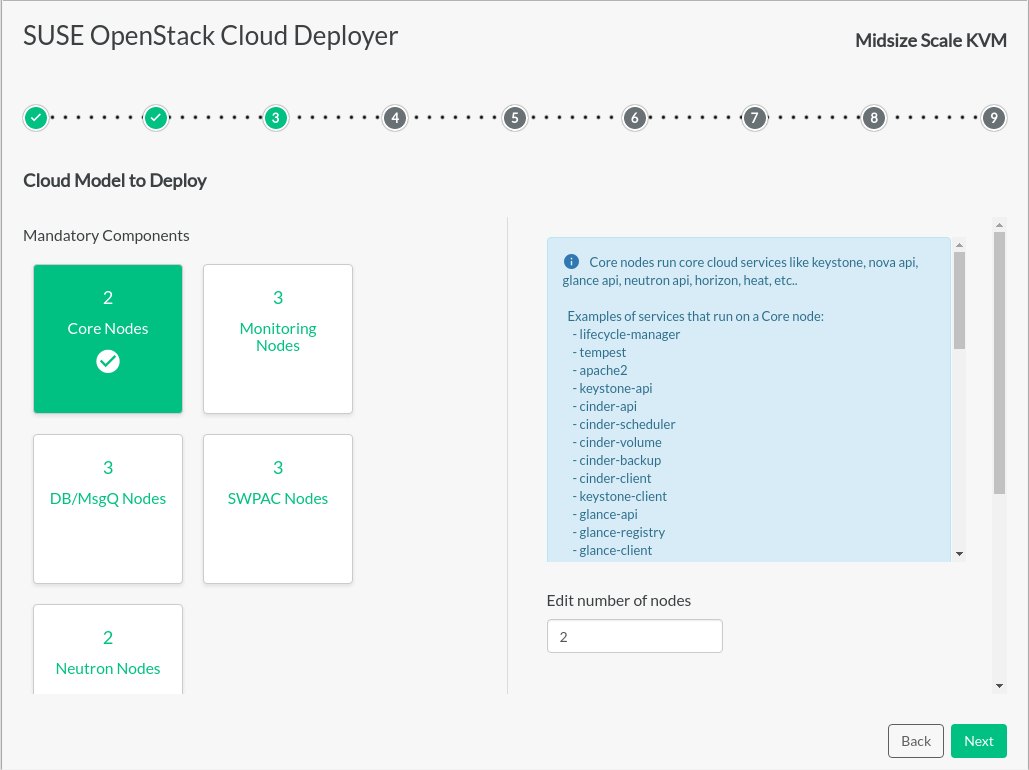
- 3 Recommended Hardware Minimums for the Example Configurations
These recommended minimums are based on example configurations included with the installation models (see Chapter 9, Example Configurations). They are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decision…
- 4 High Availability
This chapter covers High Availability concepts overview and cloud infrastructure.
1 Registering SLES #
To get technical support and product updates, you need to register and activate your SUSE product with the SUSE Customer Center. It is recommended to register during the installation, since this will enable you to install the system with the latest updates and patches available. However, if you are offline or want to skip the registration step, you can register at any time later from the installed system.
In case your organization does not provide a local registration server, registering SLES requires a SUSE account. In case you do not have a SUSE account yet, go to the SUSE Customer Center home page (https://scc.suse.com/) to create one.
1.1 Registering SLES during the Installation #
To register your system, provide the E-mail address associated with the SUSE account you or your organization uses to manage subscriptions. In case you do not have a SUSE account yet, go to the SUSE Customer Center home page (https://scc.suse.com/) to create one.
Enter the Registration Code you received with your copy of SUSE Linux Enterprise Server. Proceed with to start the registration process.
By default the system is registered with the SUSE Customer Center. However, if your
organization provides local registration servers you can either choose one
from the list of auto-detected servers or provide the URL at
Register System via local SMT Server. Proceed with
.
During the registration, the online update repositories will be added to your installation setup. When finished, you can choose whether to install the latest available package versions from the update repositories. This ensures that SUSE Linux Enterprise Server is installed with the latest security updates available. If you choose No, all packages will be installed from the installation media. Proceed with Next.
If the system was successfully registered during installation, YaST will disable repositories from local installation media such as CD/DVD or flash disks when the installation has been completed. This prevents problems if the installation source is no longer available and ensures that you always get the latest updates from the online repositories.
1.2 Registering SLES from the Installed System #
1.2.1 Registering from the Installed System #
If you have skipped the registration during the installation or want to
re-register your system, you can register the system at any time using the
YaST module or the command line
tool SUSEConnect.
Registering with YaST
To register the system start › › . Provide the E-mail address associated with the SUSE account you or your organization uses to manage subscriptions. In case you do not have a SUSE account yet, go to the SUSE Customer Center homepage (https://scc.suse.com/) to create one.
Enter the Registration Code you received with your copy of SUSE Linux Enterprise Server. Proceed with to start the registration process.
By default the system is registered with the SUSE Customer Center. However, if your organization provides local registration servers you can either choose one form the list of auto-detected servers or provide the URl at . Proceed with .
Registering with SUSEConnect
To register from the command line, use the command
tux > sudo SUSEConnect -r REGISTRATION_CODE -e EMAIL_ADDRESSReplace REGISTRATION_CODE with the Registration Code you received with your copy of SUSE Linux Enterprise Server. Replace EMAIL_ADDRESS with the E-mail address associated with the SUSE account you or your organization uses to manage subscriptions. To register with a local registration server, also provide the URL to the server:
tux > sudo SUSEConnect -r REGISTRATION_CODE -e EMAIL_ADDRESS \
--url "https://suse_register.example.com/"1.3 Registering SLES during Automated Deployment #
If you deploy your instances automatically using AutoYaST, you can register the system during the installation by providing the respective information in the AutoYaST control file. Refer to https://documentation.suse.com/sles/15-SP1/single-html/SLES-autoyast/#CreateProfile-Register for details.
2 Hardware and Software Support Matrix #
This document lists the details about the supported hardware and software for SUSE OpenStack Cloud 9
2.1 OpenStack Version Information #
SUSE OpenStack Cloud 9 services have been updated to the OpenStack Rocky release.
2.2 Supported Hardware Configurations #
SUSE OpenStack Cloud 9 supports hardware that is certified for SLES through the YES certification program. You will find a database of certified hardware at https://www.suse.com/yessearch/.
2.3 Support for Core and Non-Core OpenStack Features #
| OpenStack Service | Packages | Supported | OpenStack Service | Packages | Supported | |
| aodh | No | No | barbican | Yes | Yes | |
| ceilometer | Yes | Yes | cinder | Yes | Yes | |
| designate | Yes | Yes | glance | Yes | Yes | |
| heat | Yes | Yes | horizon | Yes | Yes | |
| ironic | Yes | Yes | keystone | Yes | Yes | |
| Magnum | Yes | Yes | manila | Yes | Yes | |
| monasca | Yes | Yes | monasca-ceilometer | Yes | Yes | |
| neutron | Yes | Yes | neutron(LBaaSv2) | No | No | |
| neutron(VPNaaS) | Yes | Yes | neutron(FWaaS) | Yes | Yes | |
| nova | Yes | Yes | Octavia | Yes | Yes | |
| swift | Yes | Yes |
nova
Supported | Not Supported |
|---|---|
SLES KVM Hypervisor | Xen hypervisor |
VMware ESX Hypervisor | Hyper-V |
Non-x86 Architectures |
neutron
Supported | Not Supported |
|---|---|
|
Tenant networks
|
Distributed Virtual Router (DVR) with any of the following:
|
VMware ESX Hypervisor | QoS |
glance Supported Features
swift and Ceph backends
cinder
Supported | Not Supported |
|---|---|
Encrypted & private volumes | VSA |
Incremental backup, backup attached volume, encrypted volume backup, backup snapshots |
swift
Supported | Not Supported |
|---|---|
Erasure coding | Geographically distributed clusters |
Dispersion report | |
swift zones |
keystone
Supported | Not Supported |
|---|---|
Domains | Web SSO |
Fernet tokens | Multi-Factor authentication |
| LDAP integration | Federation keystone to keystone |
Hierarchical multi-tenancy |
barbican Supported Features
Encryption for the following:
cinder
Hardware security model
Encrypted data volumes
Symmetric keys
Storage keys
CADF format auditing events
ceilometer
Supported | Not Supported |
|---|---|
keystone v3 support | Gnocchi |
glance v2 API | IPMI and SNMP |
ceilometer Compute Agent |
heat Features Not Supported
Multi-region stack
ironic
The table below shows supported node configurations. UEFI
secure is not supported.
| Hardware Type | Interface | ||||
|---|---|---|---|---|---|
| Boot | Deploy | Inspect | Management | Power | |
| ilo | ilo-virtual-media | direct | ilo | ilo | ilo |
| ilo | ilo-pxe | iscsi | ilo | ilo | ilo |
| ipmi | pxe | direct | no-inspect | ipmitool | ipmitool |
| ipmi | pxe | iscsi | no-inspect | ipmitool | ipmitool |
| redfish | pxe | iscsi | no-inspect | redfish | redfish |
2.4 Cloud Scaling #
SUSE OpenStack Cloud 9 has been tested and qualified with a total of 200 total compute nodes in a single region (Region0).
SUSE OpenStack Cloud 9 has been tested and qualified with a total of 12,000 virtual machines across a total of 200 compute nodes.
Larger configurations are possible, but SUSE has tested and qualified this configuration size. Typically larger configurations are enabled with services and engineering engagements.
2.5 Supported Software #
Supported ESXi versions
SUSE OpenStack Cloud 9 currently supports the following ESXi versions:
ESXi version 6.0
ESXi version 6.0 (Update 1b)
ESXi version 6.5
The following are the requirements for your vCenter server:
Software: vCenter (It is recommended to run the same server version as the ESXi hosts.)
License Requirements: vSphere Enterprise Plus license
2.6 Notes About Performance #
We have the following recommendations to ensure good performance of your cloud environment:
On the control plane nodes, you will want good I/O performance. Your array controllers must have cache controllers and we advise against the use of RAID-5.
On compute nodes, the I/O performance will influence the virtual machine start-up performance. We also recommend the use of cache controllers in your storage arrays.
If you are using dedicated object storage (swift) nodes, in particular the account, container, and object servers, we recommend that your storage arrays have cache controllers.
For best performance on, set the servers power management setting in the iLO to OS Control Mode. This power mode setting is only available on servers that include the HP Power Regulator.
2.7 KVM Guest OS Support #
For a list of the supported VM guests, see https://documentation.suse.com/sles/15-SP1/single-html/SLES-virtualization/#virt-support-guests
2.8 ESX Guest OS Support #
For ESX, refer to the VMware Compatibility Guide. The information for SUSE OpenStack Cloud is below the search form.
2.9 Ironic Guest OS Support #
A Verified Guest OS has been tested by SUSE and appears to function properly as a bare metal instance on SUSE OpenStack Cloud 9.
A Certified Guest OS has been officially tested by the operating system vendor, or by SUSE under the vendor's authorized program, and will be supported by the operating system vendor as a bare metal instance on SUSE OpenStack Cloud 9.
| ironic Guest Operating System | Verified | Certified |
|---|---|---|
| SUSE Linux Enterprise Server 12 SP4 | Yes | Yes |
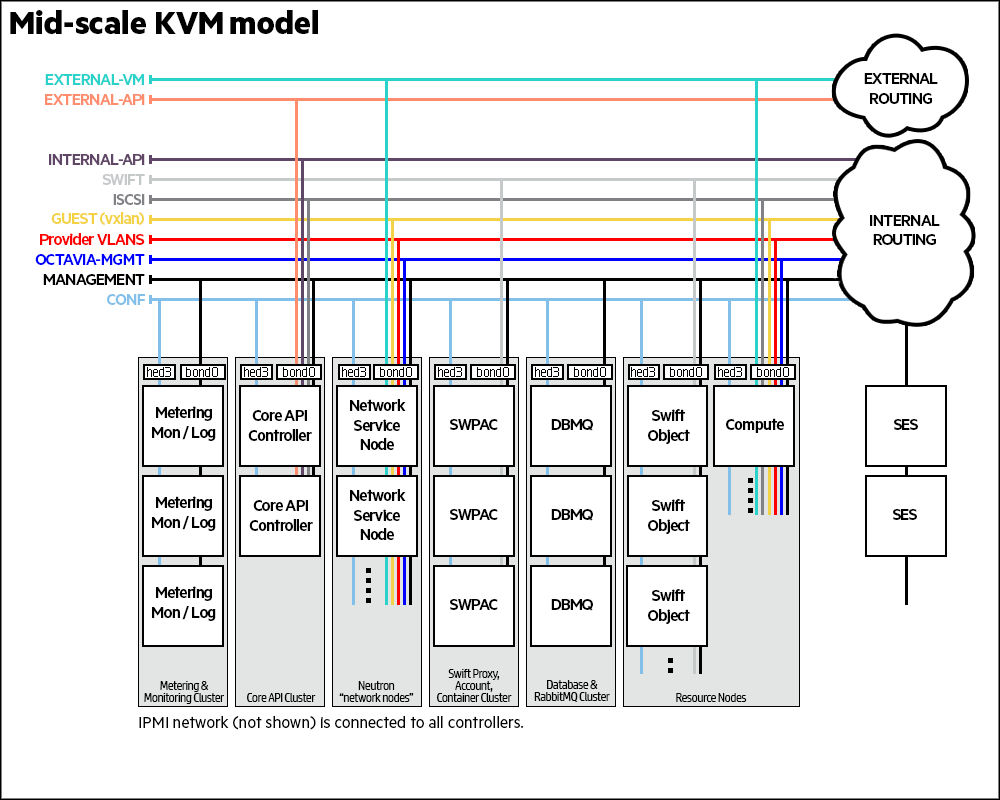
3 Recommended Hardware Minimums for the Example Configurations #
3.1 Recommended Hardware Minimums for an Entry-scale KVM #
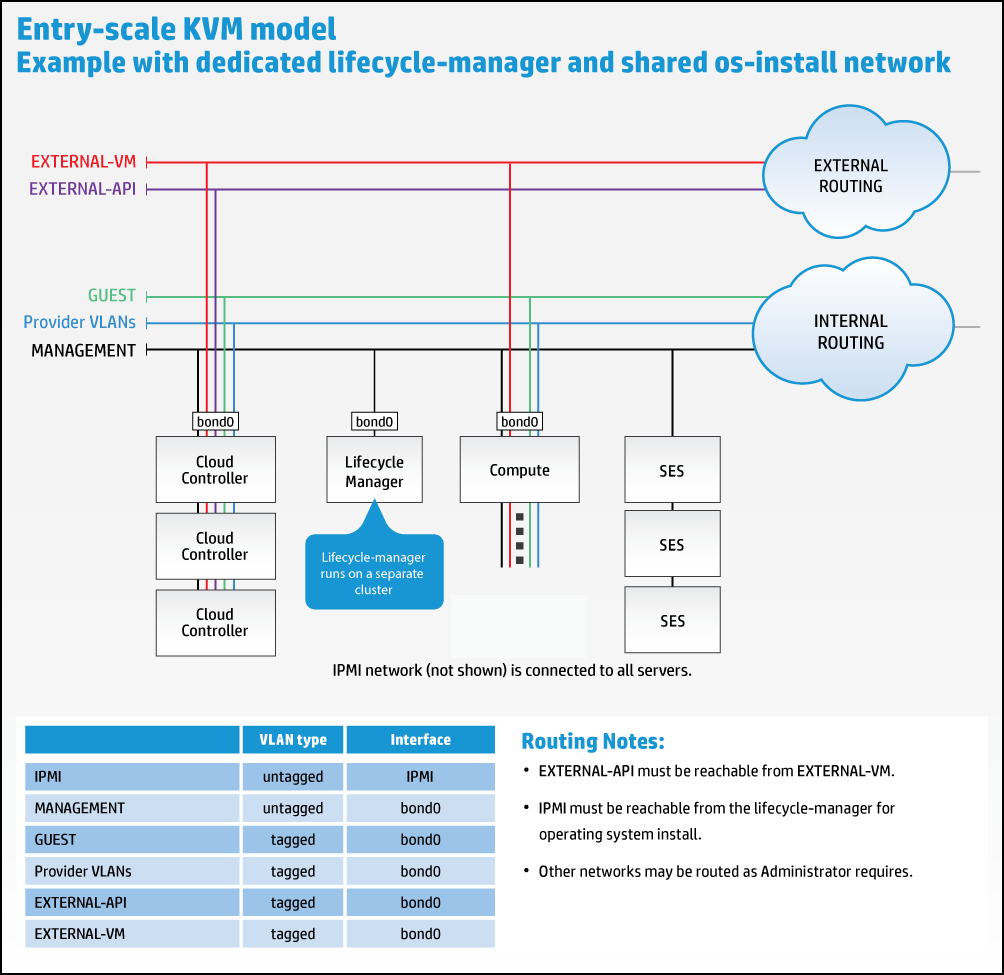
These recommended minimums are based on example configurations included with the installation models (see Chapter 9, Example Configurations). They are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
The disk requirements detailed below can be met with logical drives, logical volumes, or external storage such as a 3PAR array.
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Controller | 3 |
| 128 GB | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| Compute | Compute | 1-3 | 2 x 600 GB (minimum) | 32 GB (memory must be sized based on the virtual machine instances hosted on the Compute node) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) with hardware virtualization support. The CPU cores must be sized based on the VM instances hosted by the Compute node. |
For more details about the supported network requirements, see Chapter 9, Example Configurations.
3.2 Recommended Hardware Minimums for an Entry-scale ESX KVM Model #
These recommended minimums are based on example configurations included with the installation models (see Chapter 9, Example Configurations). They are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
SUSE OpenStack Cloud currently supports the following ESXi versions:
ESXi version 6.0
ESXi version 6.0 (Update 1b)
ESXi version 6.5
The following are the requirements for your vCenter server:
Software: vCenter (It is recommended to run the same server version as the ESXi hosts.)
License Requirements: vSphere Enterprise Plus license
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Controller | 3 |
| 128 GB | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| Compute (ESXi hypervisor) | 2 | 2 x 1 TB (minimum, shared across all nodes) | 128 GB (minimum) | 2 x 10 Gbit/s +1 NIC (for DC access) | 16 CPU (64-bit) cores total (Intel x86_64) | |
| Compute (KVM hypervisor) | kvm-compute | 1-3 | 2 x 600 GB (minimum) | 32 GB (memory must be sized based on the virtual machine instances hosted on the Compute node) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) with hardware virtualization support. The CPU cores must be sized based on the VM instances hosted by the Compute node. |
| OVSvApp VM | on VMWare cluster | 1 | 80 GB | 4 GB | 3 VMXNET Virtual Network Adapters | 2 vCPU |
| nova proxy VM | on VMWare cluster | 1 per cluster | 80 GB | 4 GB | 3 VMXNET Virtual Network Adapters | 2 vCPU |
3.3 Recommended Hardware Minimums for an Entry-scale ESX, KVM with Dedicated Cluster for Metering, Monitoring, and Logging #
These recommended minimums are based on example configurations included with the installation models (see Chapter 9, Example Configurations). They are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
SUSE OpenStack Cloud currently supports the following ESXi versions:
ESXi version 6.0
ESXi version 6.0 (Update 1b)
ESXi version 6.5
The following are the requirements for your vCenter server:
Software: vCenter (It is recommended to run the same server version as the ESXi hosts.)
License Requirements: vSphere Enterprise Plus license
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Core-API Controller | 2 |
| 128 GB | 2 x 10 Gbit/s with PXE Support | 24 CPU (64-bit) cores total (Intel x86_64) |
| DBMQ Cluster | 3 |
| 96 GB | 2 x 10 Gbit/s with PXE Support | 24 CPU (64-bit) cores total (Intel x86_64) | |
| Metering Mon/Log Cluster | 3 |
| 128 GB | 2 x 10 Gbit/s with one PXE enabled port | 24 CPU (64-bit) cores total (Intel x86_64) | |
| Compute (ESXi hypervisor) | 2 (minimum) | 2 X 1 TB (minimum, shared across all nodes) | 64 GB (memory must be sized based on the virtual machine instances hosted on the Compute node) | 2 x 10 Gbit/s +1 NIC (for Data Center access) | 16 CPU (64-bit) cores total (Intel x86_64) | |
| Compute (KVM hypervisor) | kvm-compute | 1-3 | 2 X 600 GB (minimum) | 32 GB (memory must be sized based on the virtual machine instances hosted on the Compute node) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) with hardware virtualization support. The CPU cores must be sized based on the VM instances hosted by the Compute node. |
| OVSvApp VM | on VMWare cluster | 1 | 80 GB | 4 GB | 3 VMXNET Virtual Network Adapters | 2 vCPU |
| nova proxy VM | on VMWare cluster | 1 per cluster | 80 GB | 4 GB | 3 VMXNET Virtual Network Adapters | 2 vCPU |
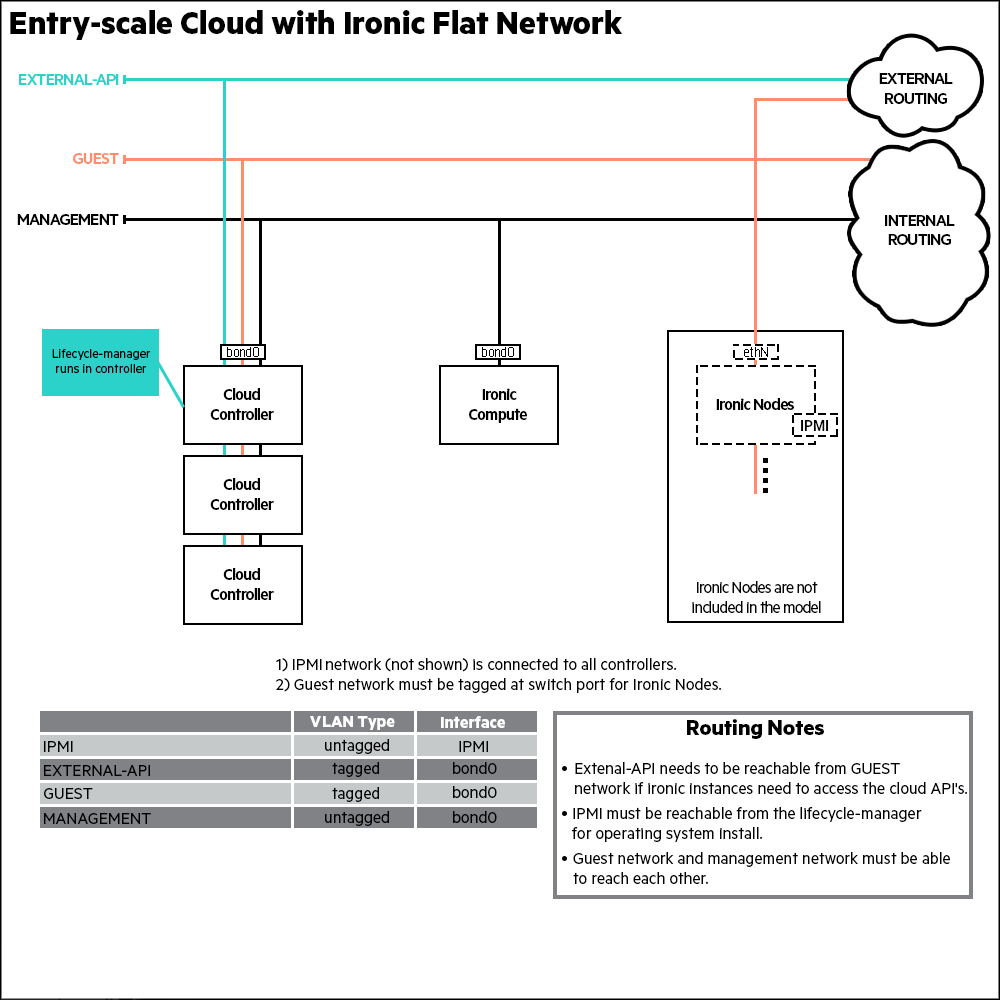
3.4 Recommended Hardware Minimums for an Ironic Flat Network Model #
When using the agent_ilo driver, you should ensure that
the most recent iLO controller firmware is installed. A recommended minimum
for the iLO4 controller is version 2.30.
The recommended minimum hardware requirements are based on the Chapter 9, Example Configurations included with the base installation and are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Controller | 3 |
| 128 GB | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| Compute | Compute | 1 | 1 x 600 GB (minimum) | 16 GB | 2 x 10 Gbit/s with one PXE enabled port | 16 CPU (64-bit) cores total (Intel x86_64) |
For more details about the supported network requirements, see Chapter 9, Example Configurations.
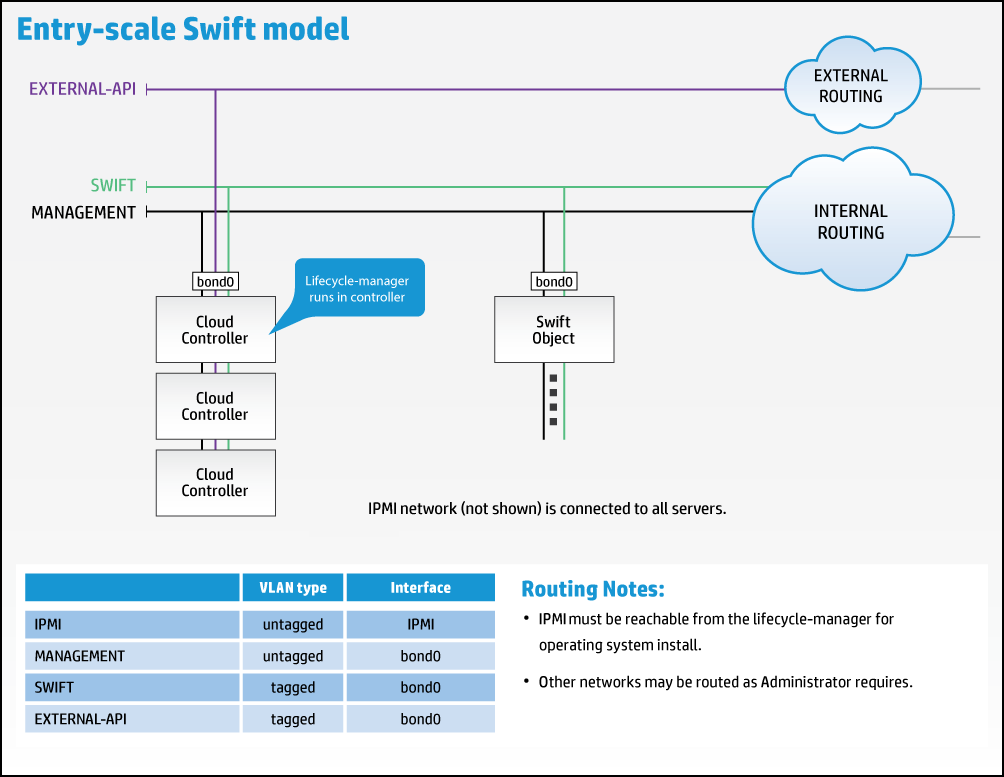
3.5 Recommended Hardware Minimums for an Entry-scale Swift Model #
These recommended minimums are based on the included Chapter 9, Example Configurations included with the base installation and are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
The entry-scale-swift example runs the swift proxy,
account and container services on the three controller servers. However, it
is possible to extend the model to include the swift proxy, account and
container services on dedicated servers (typically referred to as the swift
proxy servers). If you are using this model, we have included the recommended
swift proxy servers specs in the table below.
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Controller | 3 |
| 128 GB | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| swift Object | swobj | 3 |
If using x3 replication only:
If using Erasure Codes only or a mix of x3 replication and Erasure Codes:
| 32 GB (see considerations at bottom of page for more details) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| swift Proxy, Account, and Container | swpac | 3 | 2 x 600 GB (minimum, see considerations at bottom of page for more details) | 64 GB (see considerations at bottom of page for more details) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
The disk speeds (RPM) chosen should be consistent within the same ring or storage policy. It is best to not use disks with mixed disk speeds within the same swift ring.
Considerations for your swift object and proxy, account, container servers RAM and disk capacity needs
swift can have a diverse number of hardware configurations. For example, a swift object server may have just a few disks (minimum of 6 for erasure codes) or up to 70 and beyond. The memory requirement needs to be increased as more disks are added. The general rule of thumb for memory needed is 0.5 GB per TB of storage. For example, a system with 24 hard drives at 8TB each, giving a total capacity of 192TB, should use 96GB of RAM. However, this does not work well for a system with a small number of small hard drives or a very large number of very large drives. So, if after calculating the memory given this guideline, if the answer is less than 32GB then go with 32GB of memory minimum and if the answer is over 256GB then use 256GB maximum, no need to use more memory than that.
When considering the capacity needs for the swift proxy, account, and container (PAC) servers, you should calculate 2% of the total raw storage size of your object servers to specify the storage required for the PAC servers. So, for example, if you were using the example we provided earlier and you had an object server setup of 24 hard drives with 8TB each for a total of 192TB and you had a total of 6 object servers, that would give a raw total of 1152TB. So you would take 2% of that, which is 23TB, and ensure that much storage capacity was available on your swift proxy, account, and container (PAC) server cluster. If you had a cluster of three swift PAC servers, that would be ~8TB each.
Another general rule of thumb is that if you are expecting to have more than a million objects in a container then you should consider using SSDs on the swift PAC servers rather than HDDs.
4 High Availability #
This chapter covers High Availability concepts overview and cloud infrastructure.
4.1 High Availability Concepts Overview #
A highly available (HA) cloud ensures that a minimum level of cloud resources are always available on request, which results in uninterrupted operations for users.
In order to achieve this high availability of infrastructure and workloads, we define the scope of HA to be limited to protecting these only against single points of failure (SPOF). Single points of failure include:
Hardware SPOFs: Hardware failures can take the form of server failures, memory going bad, power failures, hypervisors crashing, hard disks dying, NIC cards breaking, switch ports failing, network cables loosening, and so forth.
Software SPOFs: Server processes can crash due to software defects, out-of-memory conditions, operating system kernel panic, and so forth.
By design, SUSE OpenStack Cloud strives to create a system architecture resilient to SPOFs, and does not attempt to automatically protect the system against multiple cascading levels of failures; such cascading failures will result in an unpredictable state. The cloud operator is encouraged to recover and restore any failed component as soon as the first level of failure occurs.
4.2 Highly Available Cloud Infrastructure #
The highly available cloud infrastructure consists of the following:
High Availability of Controllers
Availability Zones
Compute with KVM
nova Availability Zones
Compute with ESX
Object Storage with swift
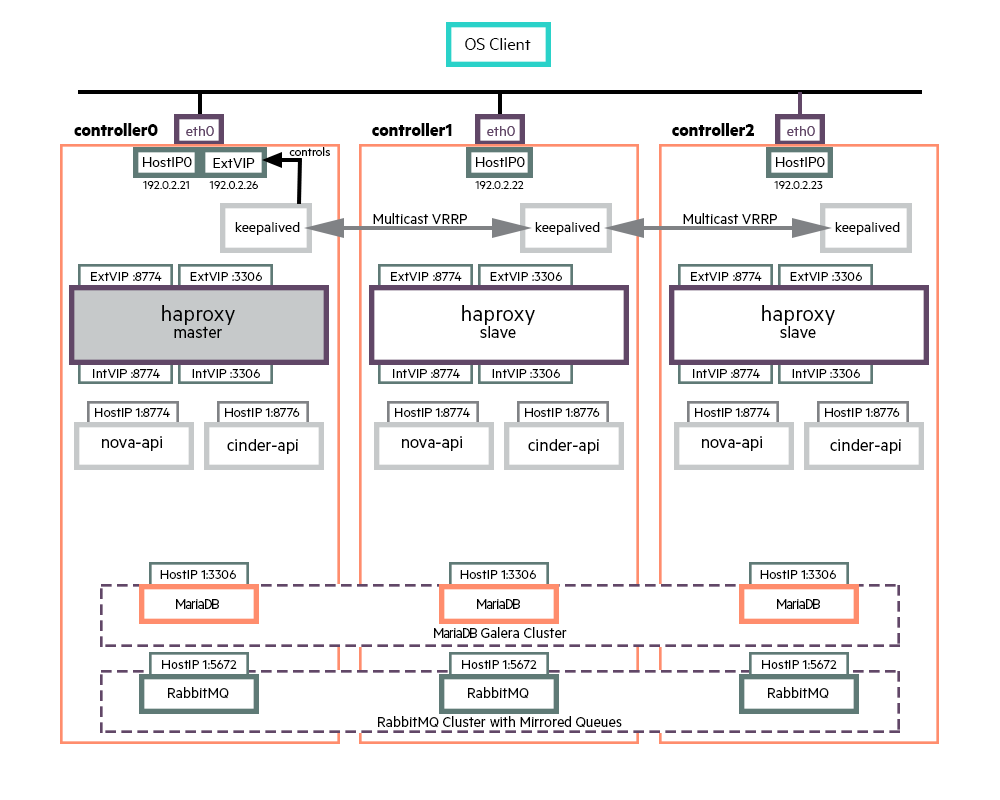
4.3 High Availability of Controllers #
The SUSE OpenStack Cloud installer deploys highly available configurations of OpenStack cloud services, resilient against single points of failure.
The high availability of the controller components comes in two main forms.
Many services are stateless and multiple instances are run across the control plane in active-active mode. The API services (nova-api, cinder-api, etc.) are accessed through the HA proxy load balancer whereas the internal services (nova-scheduler, cinder-scheduler, etc.), are accessed through the message broker. These services use the database cluster to persist any data.
NoteThe HA proxy load balancer is also run in active-active mode and keepalived (used for Virtual IP (VIP) Management) is run in active-active mode, with only one keepalived instance holding the VIP at any one point in time.
The high availability of the message queue service and the database service is achieved by running these in a clustered mode across the three nodes of the control plane: RabbitMQ cluster with Mirrored Queues and MariaDB Galera cluster.
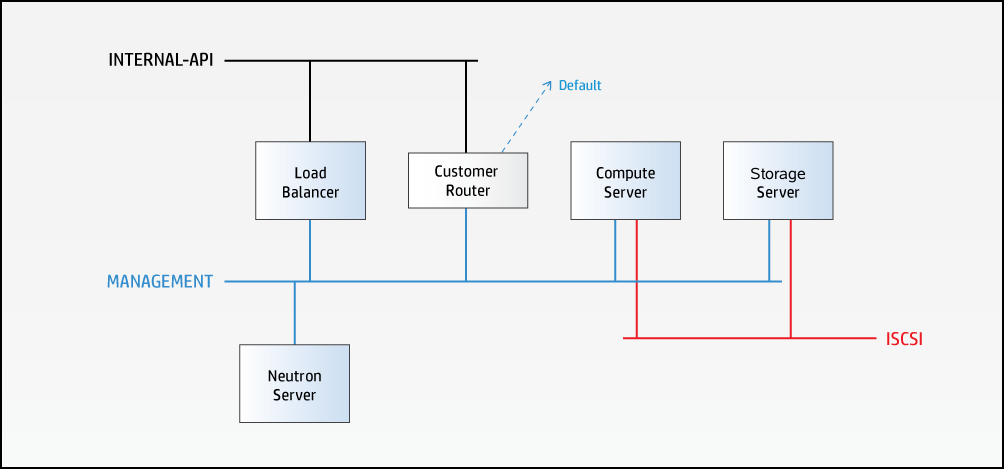
The above diagram illustrates the HA architecture with the focus on VIP management and load balancing. It only shows a subset of active-active API instances and does not show examples of other services such as nova-scheduler, cinder-scheduler, etc.
In the above diagram, requests from an OpenStack client to the API services are sent to VIP and port combination; for example, 192.0.2.26:8774 for a nova request. The load balancer listens for requests on that VIP and port. When it receives a request, it selects one of the controller nodes configured for handling nova requests, in this particular case, and then forwards the request to the IP of the selected controller node on the same port.
The nova-api service, which is listening for requests on the IP of its host machine, then receives the request and deals with it accordingly. The database service is also accessed through the load balancer. RabbitMQ, on the other hand, is not currently accessed through VIP/HA proxy as the clients are configured with the set of nodes in the RabbitMQ cluster and failover between cluster nodes is automatically handled by the clients.
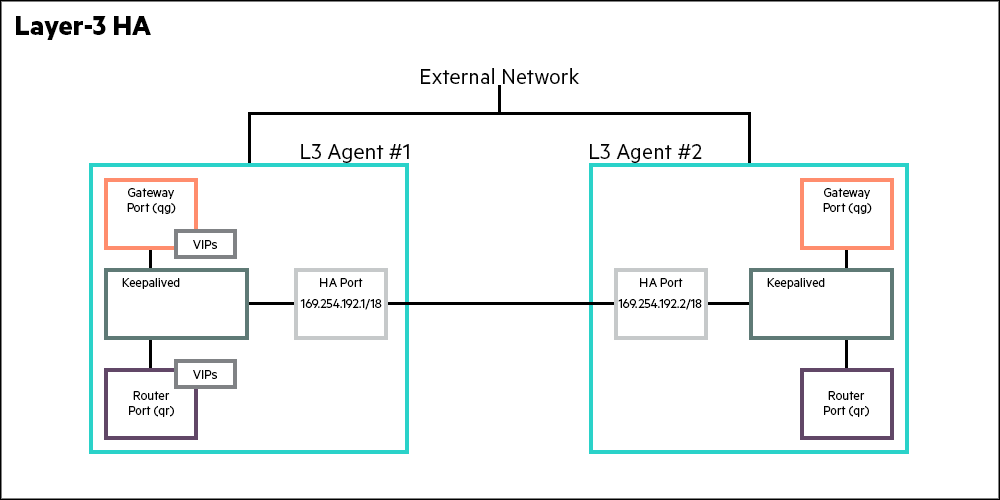
4.4 High Availability Routing - Centralized #
Incorporating High Availability into a system involves implementing redundancies in the component that is being made highly available. In Centralized Virtual Router (CVR), that element is the Layer 3 agent (L3 agent). By making L3 agent highly available, upon failure all HA routers are migrated from the primary L3 agent to a secondary L3 agent. The implementation efficiency of an HA subsystem is measured by the number of packets that are lost when the secondary L3 agent is made the master.
In SUSE OpenStack Cloud, the primary and secondary L3 agents run continuously, and failover involves a rapid switchover of mastership to the secondary agent (IEFT RFC 5798). The failover essentially involves a switchover from an already running master to an already running slave. This substantially reduces the latency of the HA. The mechanism used by the master and the slave to implement a failover is implemented using Linux’s pacemaker HA resource manager. This CRM (Cluster resource manager) uses VRRP (Virtual Router Redundancy Protocol) to implement the HA mechanism. VRRP is a industry standard protocol and defined in RFC 5798.
L3 HA uses of VRRP comes with several benefits.
The primary benefit is that the failover mechanism does not involve interprocess communication overhead. Such overhead would be in the order of 10s of seconds. By not using an RPC mechanism to invoke the secondary agent to assume the primary agents role enables VRRP to achieve failover within 1-2 seconds.
In VRRP, the primary and secondary routers are all active. As the routers are running, it is a matter of making the router aware of its primary/master status. This switchover takes less than 2 seconds instead of 60+ seconds it would have taken to start a backup router and failover.
The failover depends upon a heartbeat link between the primary and secondary. That link in SUSE OpenStack Cloud uses keepalived package of the pacemaker resource manager. The heartbeats are sent at a 2 second intervals between the primary and secondary. As per the VRRP protocol, if the secondary does not hear from the master after 3 intervals, it assumes the function of the primary.
Further, all the routable IP addresses, that is the VIPs (virtual IPs) are assigned to the primary agent.
4.5 Availability Zones #
While planning your OpenStack deployment, you should decide on how to zone various types of nodes - such as compute, block storage, and object storage. For example, you may decide to place all servers in the same rack in the same zone. For larger deployments, you may plan more elaborate redundancy schemes for redundant power, network ISP connection, and even physical firewalling between zones (this aspect is outside the scope of this document).
SUSE OpenStack Cloud offers APIs, CLIs and horizon UIs for the administrator to define and user to consume, availability zones for nova, cinder and swift services. This section outlines the process to deploy specific types of nodes to specific physical servers, and makes a statement of available support for these types of availability zones in the current release.
By default, SUSE OpenStack Cloud is deployed in a single availability zone upon installation. Multiple availability zones can be configured by an administrator post-install, if required. Refer to OpenStack Documentation
4.6 Compute with KVM #
You can deploy your KVM nova-compute nodes either during initial installation or by adding compute nodes post initial installation.
While adding compute nodes post initial installation, you can specify the target physical servers for deploying the compute nodes.
Learn more about adding compute nodes in Book “Operations Guide CLM”, Chapter 15 “System Maintenance”, Section 15.1 “Planned System Maintenance”, Section 15.1.3 “Planned Compute Maintenance”, Section 15.1.3.4 “Adding Compute Node”.
4.7 Nova Availability Zones #
nova host aggregates and nova availability zones can be used to segregate nova compute nodes across different failure zones.
4.8 Compute with ESX Hypervisor #
Compute nodes deployed on ESX Hypervisor can be made highly available using the HA feature of VMware ESX Clusters. For more information on VMware HA, please refer to your VMware ESX documentation.
4.9 cinder Availability Zones #
cinder availability zones are not supported for general consumption in the current release.
4.10 Object Storage with Swift #
High availability in swift is achieved at two levels.
Control Plane
The swift API is served by multiple swift proxy nodes. Client requests are directed to all swift proxy nodes by the HA Proxy load balancer in round-robin fashion. The HA Proxy load balancer regularly checks the node is responding, so that if it fails, traffic is directed to the remaining nodes. The swift service will continue to operate and respond to client requests as long as at least one swift proxy server is running.
If a swift proxy node fails in the middle of a transaction, the transaction fails. However it is standard practice for swift clients to retry operations. This is transparent to applications that use the python-swiftclient library.
The entry-scale example cloud models contain three swift proxy nodes. However, it is possible to add additional clusters with additional swift proxy nodes to handle a larger workload or to provide additional resiliency.
Data
Multiple replicas of all data is stored. This happens for account, container and object data. The example cloud models recommend a replica count of three. However, you may change this to a higher value if needed.
When swift stores different replicas of the same item on disk, it ensures that as far as possible, each replica is stored in a different zone, server or drive. This means that if a single server of disk drives fails, there should be two copies of the item on other servers or disk drives.
If a disk drive is failed, swift will continue to store three replicas. The replicas that would normally be stored on the failed drive are “handed off” to another drive on the system. When the failed drive is replaced, the data on that drive is reconstructed by the replication process. The replication process re-creates the “missing” replicas by copying them to the drive using one of the other remaining replicas. While this is happening, swift can continue to store and retrieve data.
4.11 Highly Available Cloud Applications and Workloads #
Projects writing applications to be deployed in the cloud must be aware of the cloud architecture and potential points of failure and architect their applications accordingly for high availability.
Some guidelines for consideration:
Assume intermittent failures and plan for retries
OpenStack Service APIs: invocations can fail - you should carefully evaluate the response of each invocation, and retry in case of failures.
Compute: VMs can die - monitor and restart them
Network: Network calls can fail - retry should be successful
Storage: Storage connection can hiccup - retry should be successful
Build redundancy into your application tiers
Replicate VMs containing stateless services such as Web application tier or Web service API tier and put them behind load balancers. You must implement your own HA Proxy type load balancer in your application VMs.
Boot the replicated VMs into different nova availability zones.
If your VM stores state information on its local disk (Ephemeral Storage), and you cannot afford to lose it, then boot the VM off a cinder volume.
Take periodic snapshots of the VM which will back it up to swift through glance.
Your data on ephemeral may get corrupted (but not your backup data in swift and not your data on cinder volumes).
Take regular snapshots of cinder volumes and also back up cinder volumes or your data exports into swift.
Instead of rolling your own highly available stateful services, use readily available SUSE OpenStack Cloud platform services such as designate, the DNS service.
4.12 What is not Highly Available? #
- Cloud Lifecycle Manager
The Cloud Lifecycle Manager in SUSE OpenStack Cloud is not highly available.
- Control Plane
High availability (HA) is supported for the Network Service FWaaS. HA is not supported for VPNaaS.
- cinder Volume and Backup Services
cinder Volume and Backup Services are not high availability and started on one controller node at a time. More information on cinder Volume and Backup Services can be found in Book “Operations Guide CLM”, Chapter 8 “Managing Block Storage”, Section 8.1 “Managing Block Storage using Cinder”, Section 8.1.3 “Managing cinder Volume and Backup Services”.
- keystone Cron Jobs
The keystone cron job is a singleton service, which can only run on a single node at a time. A manual setup process for this job will be required in case of a node failure. More information on enabling the cron job for keystone on the other nodes can be found in Book “Operations Guide CLM”, Chapter 5 “Managing Identity”, Section 5.12 “Identity Service Notes and Limitations”, Section 5.12.4 “System cron jobs need setup”.
4.13 More Information #
Part II Cloud Lifecycle Manager Overview #
This section contains information on the Input Model and the Example Configurations.
- 5 Input Model
This document describes how SUSE OpenStack Cloud input models can be used to define and configure the cloud.
- 6 Configuration Objects
The top-level cloud configuration file,
cloudConfig.yml, defines some global values for SUSE OpenStack Cloud, as described in the table below.- 7 Other Topics
Names are generated by the configuration processor for all allocated IP addresses. A server connected to multiple networks will have multiple names associated with it. One of these may be assigned as the hostname for a server via the network-group configuration (see Section 6.12, “NIC Mappings”). Na…
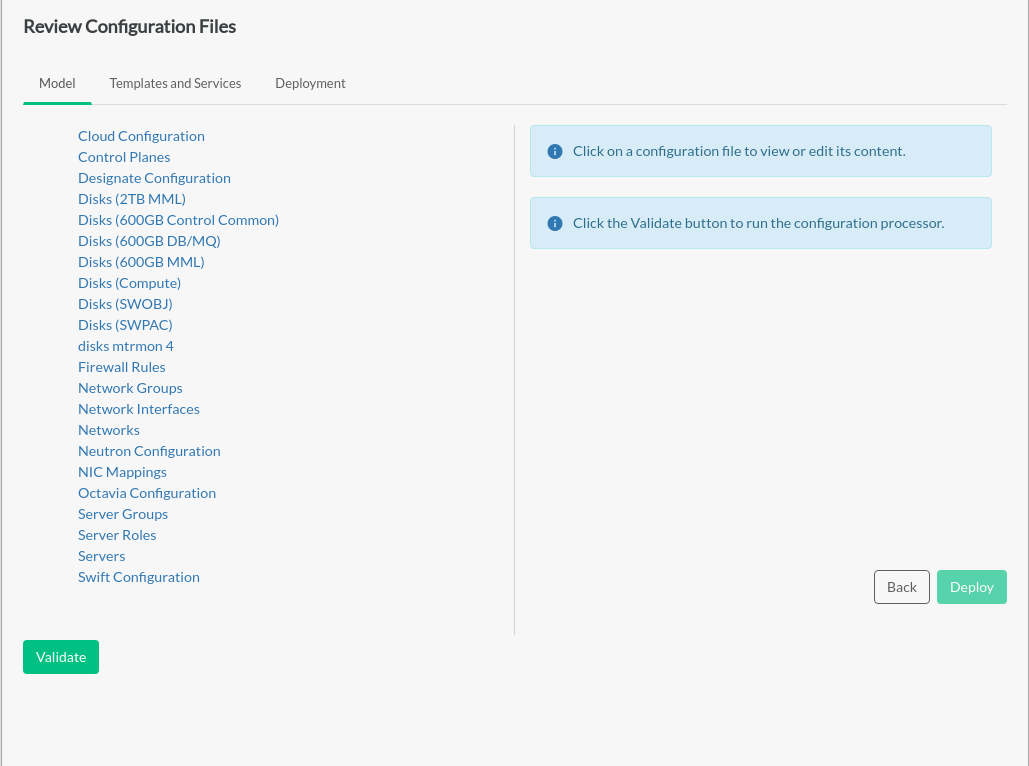
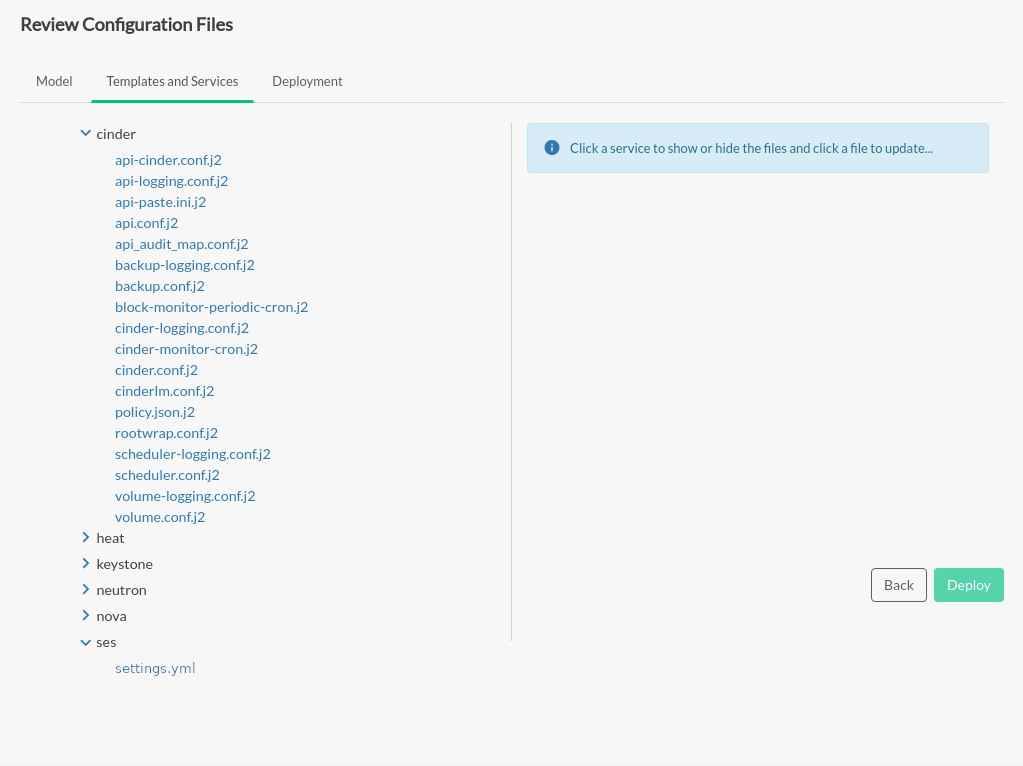
- 8 Configuration Processor Information Files
In addition to producing all of the data needed to deploy and configure the cloud, the configuration processor also creates a number of information files that provide details of the resulting configuration.
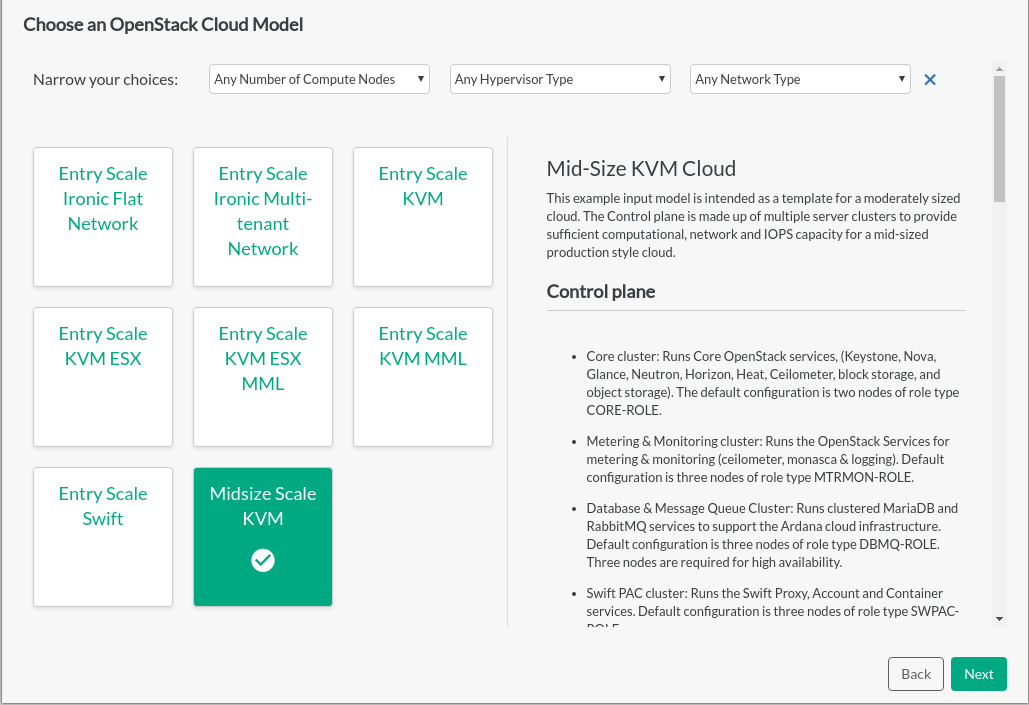
- 9 Example Configurations
The SUSE OpenStack Cloud 9 system ships with a collection of pre-qualified example configurations. These are designed to help you to get up and running quickly with a minimum number of configuration changes.
- 10 Modifying Example Configurations for Compute Nodes
This section contains detailed information about the Compute Node parts of the input model. For example input models, see Chapter 9, Example Configurations. For general descriptions of the input model, see Section 6.14, “Networks”.
- 11 Modifying Example Configurations for Object Storage using Swift
This section contains detailed descriptions about the swift-specific parts of the input model. For example input models, see Chapter 9, Example Configurations. For general descriptions of the input model, see Section 6.14, “Networks”. In addition, the swift ring specifications are available in the ~…
- 12 Alternative Configurations
In SUSE OpenStack Cloud 9 there are alternative configurations that we recommend for specific purposes.
5 Input Model #
5.1 Introduction to the Input Model #
This document describes how SUSE OpenStack Cloud input models can be used to define and configure the cloud.
SUSE OpenStack Cloud ships with a set of example input models that can be used as starting points for defining a custom cloud. An input model allows you, the cloud administrator, to describe the cloud configuration in terms of:
Which OpenStack services run on which server nodes
How individual servers are configured in terms of disk and network adapters
The overall network configuration of the cloud
Network traffic separation
CIDR and VLAN assignments
The input model is consumed by the configuration processor which parses and validates the input model and outputs the effective configuration that will be deployed to each server that makes up your cloud.
The document is structured as follows:
- This explains the ideas behind the declarative model approach used in SUSE OpenStack Cloud 9 and the core concepts used in describing that model
- This section provides a description of each of the configuration entities in the input model
- In this section we provide samples and definitions of some of the more important configuration entities
5.2 Concepts #
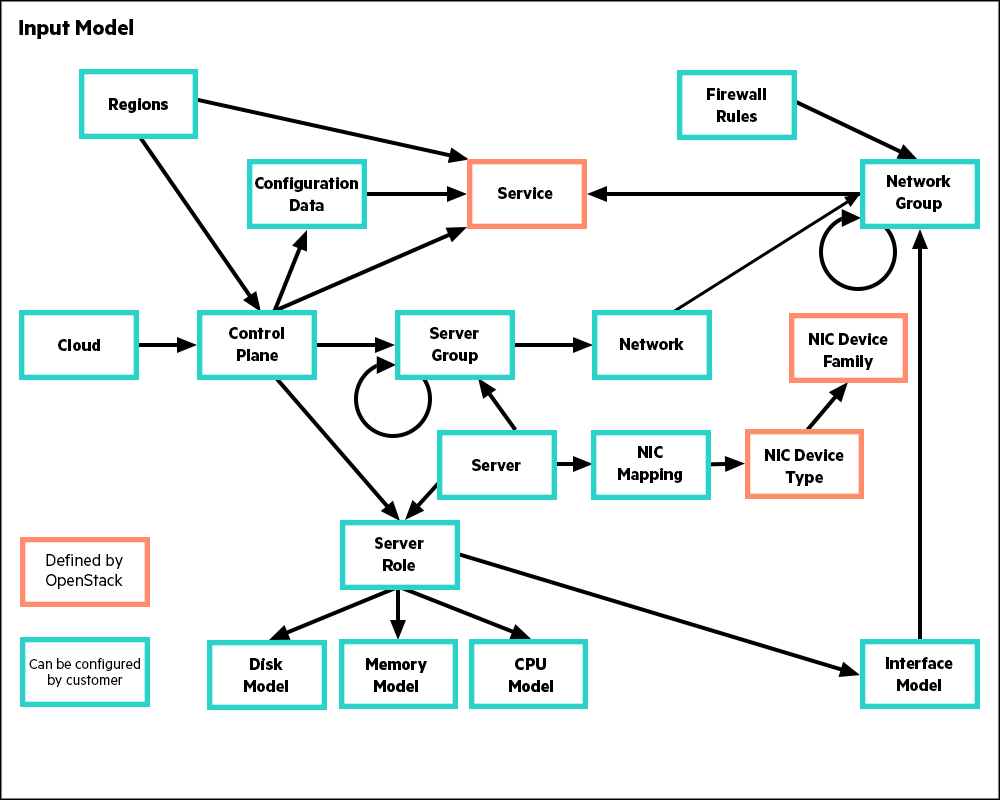
An SUSE OpenStack Cloud 9 cloud is defined by a declarative model that is described in a series of configuration objects. These configuration objects are represented in YAML files which together constitute the various example configurations provided as templates with this release. These examples can be used nearly unchanged, with the exception of necessary changes to IP addresses and other site and hardware-specific identifiers. Alternatively, the examples may be customized to meet site requirements.
The following diagram shows the set of configuration objects and their relationships. All objects have a name that you may set to be something meaningful for your context. In the examples these names are provided in capital letters as a convention. These names have no significance to SUSE OpenStack Cloud, rather it is the relationships between them that define the configuration.
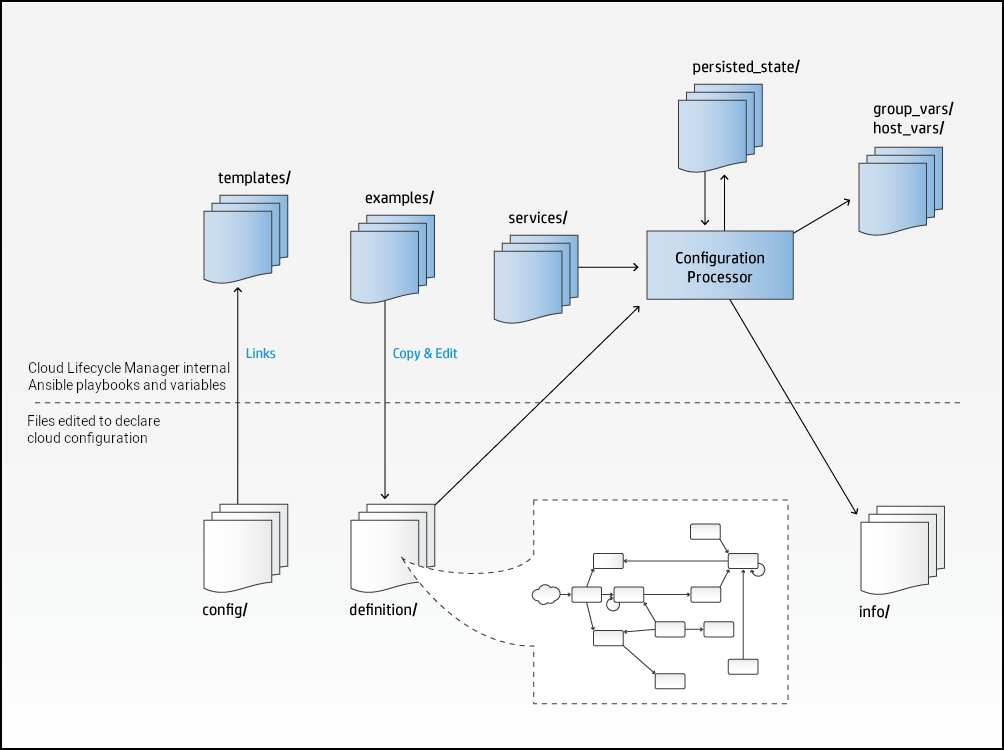
The configuration processor reads and validates the input model described in the YAML files discussed above, combines it with the service definitions provided by SUSE OpenStack Cloud and any persisted state information about the current deployment to produce a set of Ansible variables that can be used to deploy the cloud. It also produces a set of information files that provide details about the configuration.
The relationship between the file systems on the SUSE OpenStack Cloud deployment server and the configuration processor is shown in the following diagram. Below the line are the directories that you, the cloud administrator, edit to declare the cloud configuration. Above the line are the directories that are internal to the Cloud Lifecycle Manager such as Ansible playbooks and variables.
The input model is read from the
~/openstack/my_cloud/definition directory. Although the
supplied examples use separate files for each type of object in the model,
the names and layout of the files have no significance to the configuration
processor, it simply reads all of the .yml files in this directory. Cloud
administrators are therefore free to use whatever structure is best for their
context. For example, you may decide to maintain separate files or
sub-directories for each physical rack of servers.
As mentioned, the examples use the conventional upper casing for object names, but these strings are used only to define the relationship between objects. They have no specific significance to the configuration processor.
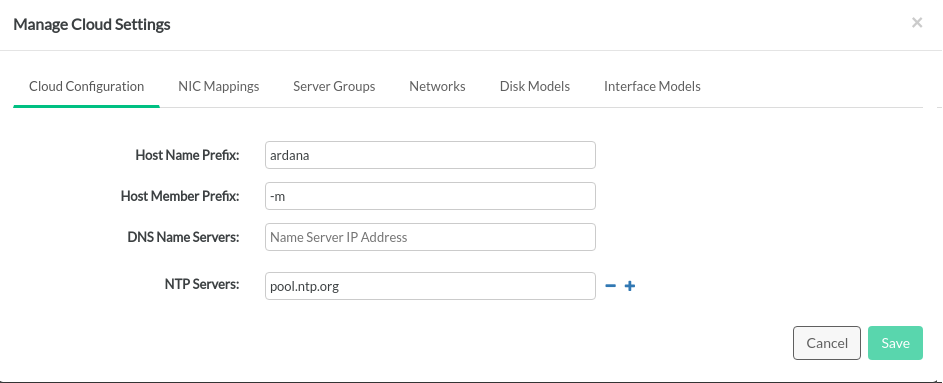
5.2.1 Cloud #
The Cloud definition includes a few top-level configuration values such as the name of the cloud, the host prefix, details of external services (NTP, DNS, SMTP) and the firewall settings.
The location of the cloud configuration file also tells the configuration processor where to look for the files that define all of the other objects in the input model.
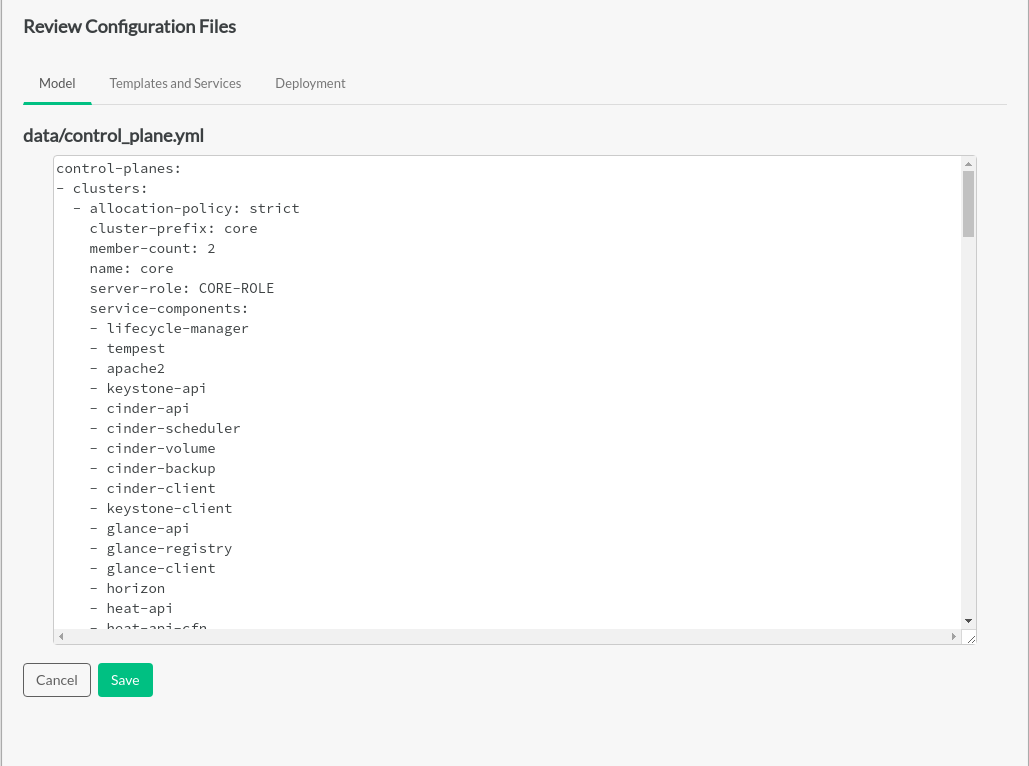
5.2.2 Control Planes #
A control-plane runs one or more distributed across and .
A control-plane uses servers with a particular .
A provides the operating environment for a set of ; normally consisting of a set of shared services (MariaDB, RabbitMQ, HA Proxy, Apache, etc.), OpenStack control services (API, schedulers, etc.) and the they are managing (compute, storage, etc.).
A simple cloud may have a single which runs all of the . A more complex cloud may have multiple to allow for more than one instance of some services. Services that need to consume (use) another service (such as neutron consuming MariaDB, nova consuming neutron) always use the service within the same . In addition a control-plane can describe which services can be consumed from other control-planes. It is one of the functions of the configuration processor to resolve these relationships and make sure that each consumer/service is provided with the configuration details to connect to the appropriate provider/service.
Each is structured as and . The are typically used to host the OpenStack services that manage the cloud such as API servers, database servers, neutron agents, and swift proxies, while the are used to host the scale-out OpenStack services such as nova-Compute or swift-Object services. This is a representation convenience rather than a strict rule, for example it is possible to run the swift-Object service in the management cluster in a smaller-scale cloud that is not designed for scale-out object serving.
A cluster can contain one or more and you can have one or more depending on the capacity and scalability needs of the cloud that you are building. Spreading services across multiple provides greater scalability, but it requires a greater number of physical servers. A common pattern for a large cloud is to run high data volume services such as monitoring and logging in a separate cluster. A cloud with a high object storage requirement will typically also run the swift service in its own cluster.
Clusters in this context are a mechanism for grouping service components in physical servers, but all instances of a component in a work collectively. For example, if HA Proxy is configured to run on multiple clusters within the same then all of those instances will work as a single instance of the ha-proxy service.
Both and define the type (via a list of ) and number of servers (min and max or count) they require.
The can also define a list of failure-zones () from which to allocate servers.
5.2.2.1 Control Planes and Regions #
A region in OpenStack terms is a collection of URLs that together provide a
consistent set of services (nova, neutron, swift, etc). Regions are
represented in the keystone identity service catalog. In SUSE OpenStack Cloud,
multiple regions are not supported. Only Region0 is valid.
In a simple single control-plane cloud, there is no need for a separate region definition and the control-plane itself can define the region name.
5.2.3 Services #
A runs one or more .
A service is the collection of that provide a particular feature; for example, nova provides the compute service and consists of the following service-components: nova-api, nova-scheduler, nova-conductor, nova-novncproxy, and nova-compute. Some services, like the authentication/identity service keystone, only consist of a single service-component.
To define your cloud, all you need to know about a service are the names of the . The details of the services themselves and how they interact with each other is captured in service definition files provided by SUSE OpenStack Cloud.
When specifying your SUSE OpenStack Cloud cloud you have to decide where components will run and how they connect to the networks. For example, should they all run in one sharing common services or be distributed across multiple to provide separate instances of some services? The SUSE OpenStack Cloud supplied examples provide solutions for some typical configurations.
Where services run is defined in the . How they connect to networks is defined in the .
5.2.4 Server Roles #
and use with a particular set of s.
You are going to be running the services on physical , and you are going to need a way to specify which type of servers you want to use where. This is defined via the . Each describes how to configure the physical aspects of a server to fulfill the needs of a particular role. You will generally use a different role whenever the servers are physically different (have different disks or network interfaces) or if you want to use some specific servers in a particular role (for example to choose which of a set of identical servers are to be used in the control plane).
Each has a relationship to four other entities:
The specifies how to configure and use a server's local storage and it specifies disk sizing information for virtual machine servers. The disk model is described in the next section.
The describes how a server's network interfaces are to be configured and used. This is covered in more details in the networking section.
An optional specifies how to configure and use huge pages. The memory-model specifies memory sizing information for virtual machine servers.
An optional specifies how the CPUs will be used by nova and by DPDK. The cpu-model specifies CPU sizing information for virtual machine servers.
5.2.5 Disk Model #
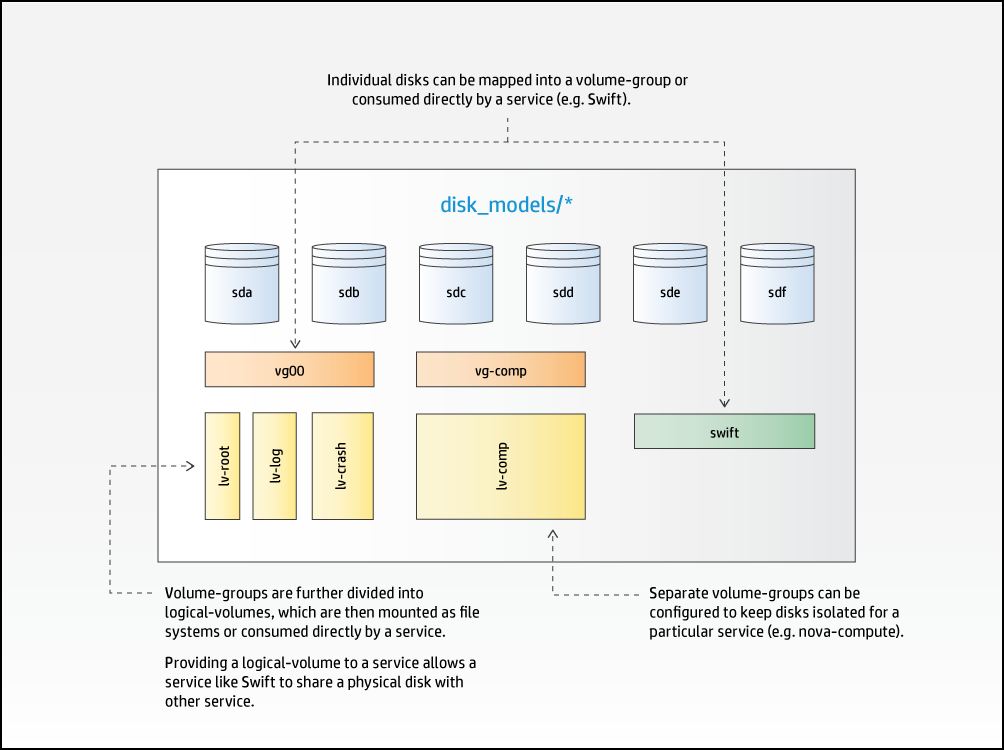
Each physical disk device is associated with a or a .
are consumed by .
are divided into .
are mounted as file systems or consumed by services.
Disk-models define how local storage is to be configured and presented to . Disk-models are identified by a name, which you will specify. The SUSE OpenStack Cloud examples provide some typical configurations. As this is an area that varies with respect to the services that are hosted on a server and the number of disks available, it is impossible to cover all possible permutations you may need to express via modifications to the examples.
Within a , disk devices are assigned to either a or a .
A is a set of one or more disks that are to be consumed directly by a service. For example, a set of disks to be used by swift. The device-group identifies the list of disk devices, the service, and a few service-specific attributes that tell the service about the intended use (for example, in the case of swift this is the ring names). When a device is assigned to a device-group, the associated service is responsible for the management of the disks. This management includes the creation and mounting of file systems. (swift can provide additional data integrity when it has full control over the file systems and mount points.)
A is used to present disk devices in a LVM volume group. It also contains details of the logical volumes to be created including the file system type and mount point. Logical volume sizes are expressed as a percentage of the total capacity of the volume group. A can also be consumed by a service in the same way as a . This allows services to manage their own devices on configurations that have limited numbers of disk drives.
Disk models also provide disk sizing information for virtual machine servers.
5.2.6 Memory Model #
Memory models define how the memory of a server should be configured to meet the needs of a particular role. It allows a number of HugePages to be defined at both the server and numa-node level.
Memory models also provide memory sizing information for virtual machine servers.
Memory models are optional - it is valid to have a server role without a memory model.
5.2.7 CPU Model #
CPU models define how CPUs of a server will be used. The model allows CPUs to be assigned for use by components such as nova (for VMs) and Open vSwitch (for DPDK). It also allows those CPUs to be isolated from the general kernel SMP balancing and scheduling algorithms.
CPU models also provide CPU sizing information for virtual machine servers.
CPU models are optional - it is valid to have a server role without a cpu model.
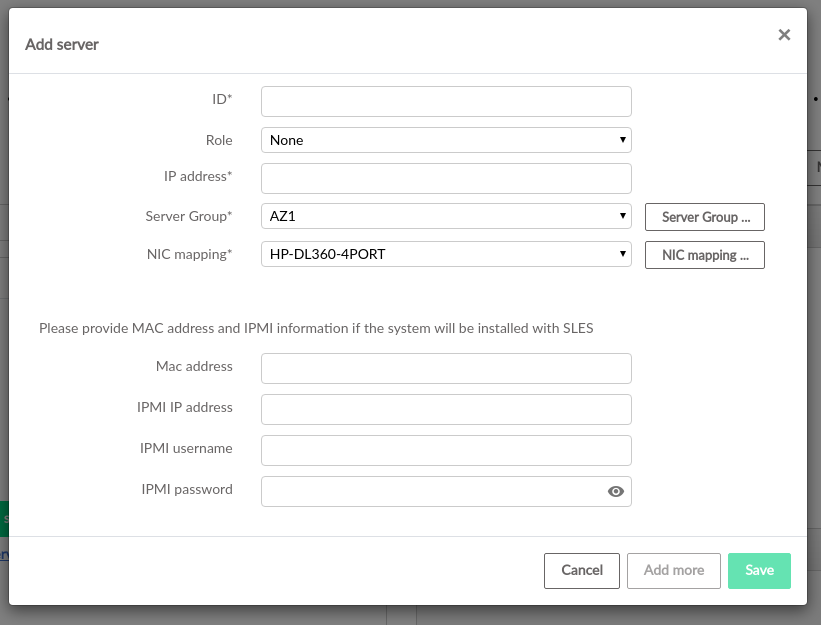
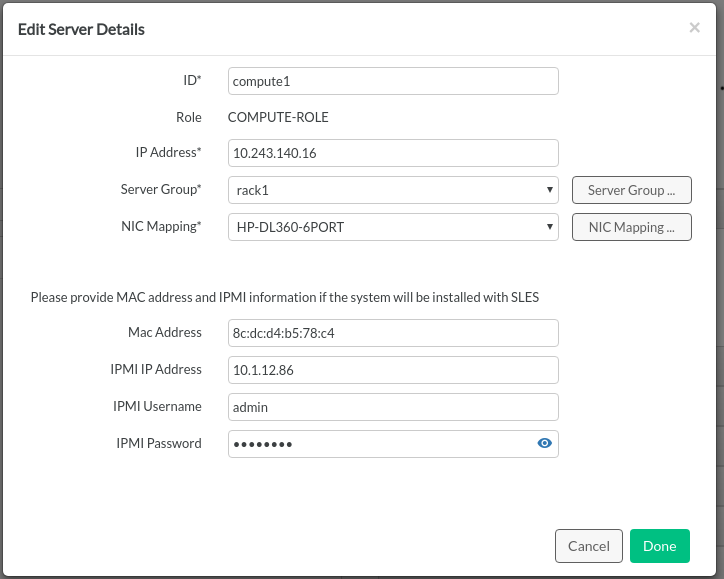
5.2.8 Servers #
have a which determines how they will be used in the cloud.
(in the input model) enumerate the resources available for your cloud. In addition, in this definition file you can either provide SUSE OpenStack Cloud with all of the details it needs to PXE boot and install an operating system onto the server, or, if you prefer to use your own operating system installation tooling you can simply provide the details needed to be able to SSH into the servers and start the deployment.
The address specified for the server will be the one used by SUSE OpenStack Cloud for lifecycle management and must be part of a network which is in the input model. If you are using SUSE OpenStack Cloud to install the operating system this network must be an untagged VLAN. The first server must be installed manually from the SUSE OpenStack Cloud ISO and this server must be included in the input model as well.
In addition to the network details used to install or connect to the server, each server defines what its is and to which it belongs.
5.2.9 Server Groups #
A is associated with a .
A can use as failure zones for server allocation.
A may be associated with a list of .
A can contain other .
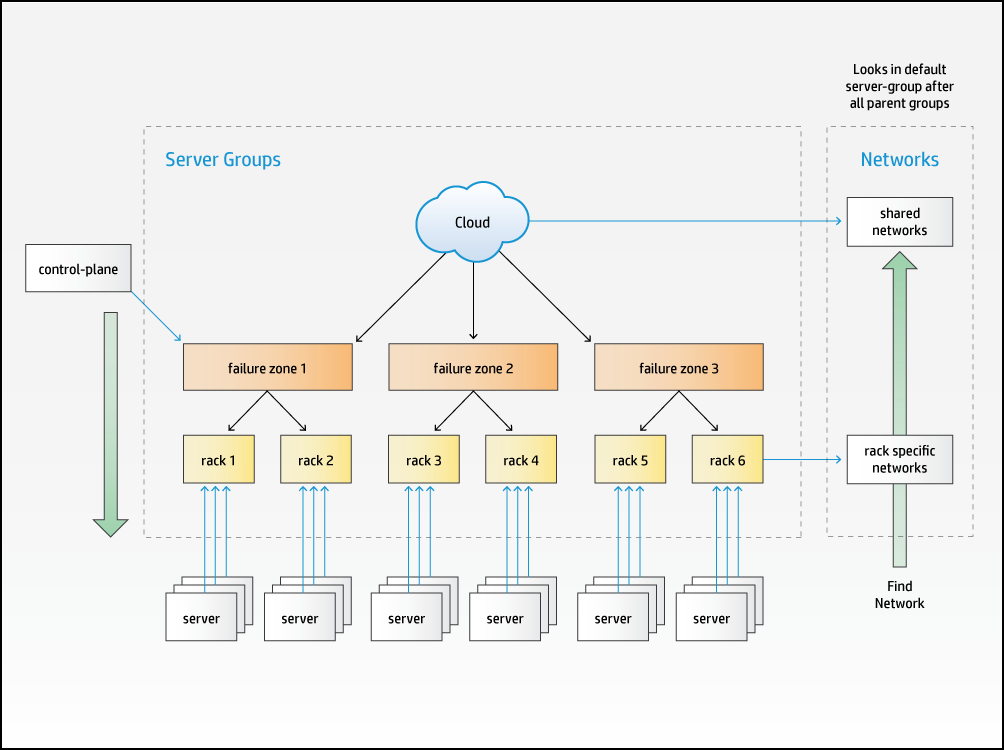
The practice of locating physical servers in a number of racks or enclosures in a data center is common. Such racks generally provide a degree of physical isolation that allows for separate power and/or network connectivity.
In the SUSE OpenStack Cloud model we support this configuration by allowing you to define a hierarchy of . Each is associated with one , normally at the bottom of the hierarchy.
are an optional part of the input model - if you do not define any, then all and will be allocated as if they are part of the same .
5.2.9.1 Server Groups and Failure Zones #
A defines a list of as the failure zones from which it wants to use servers. All servers in a listed as a failure zone in the and any they contain are considered part of that failure zone for allocation purposes. The following example shows how three levels of can be used to model a failure zone consisting of multiple racks, each of which in turn contains a number of .
When allocating , the configuration processor will traverse down the hierarchy of listed as failure zones until it can find an available server with the required . If the allocation policy is defined to be strict, it will allocate equally across each of the failure zones. A or can also independently specify the failure zones it wants to use if needed.
5.2.9.2 Server Groups and Networks #
Each L3 in a cloud must be associated with all or some of the , typically following a physical pattern (such as having separate networks for each rack or set of racks). This is also represented in the SUSE OpenStack Cloud model via , each group lists zero or more networks to which associated with at or below this point in the hierarchy are connected.
When the configuration processor needs to resolve the specific a should be configured to use, it traverses up the hierarchy of , starting with the group the server is directly associated with, until it finds a server-group that lists a network in the required network group.
The level in the hierarchy at which a is associated will depend on the span of connectivity it must provide. In the above example there might be networks in some which are per rack (that is Rack 1 and Rack 2 list different networks from the same ) and in a different that span failure zones (the network used to provide floating IP addresses to virtual machines for example).
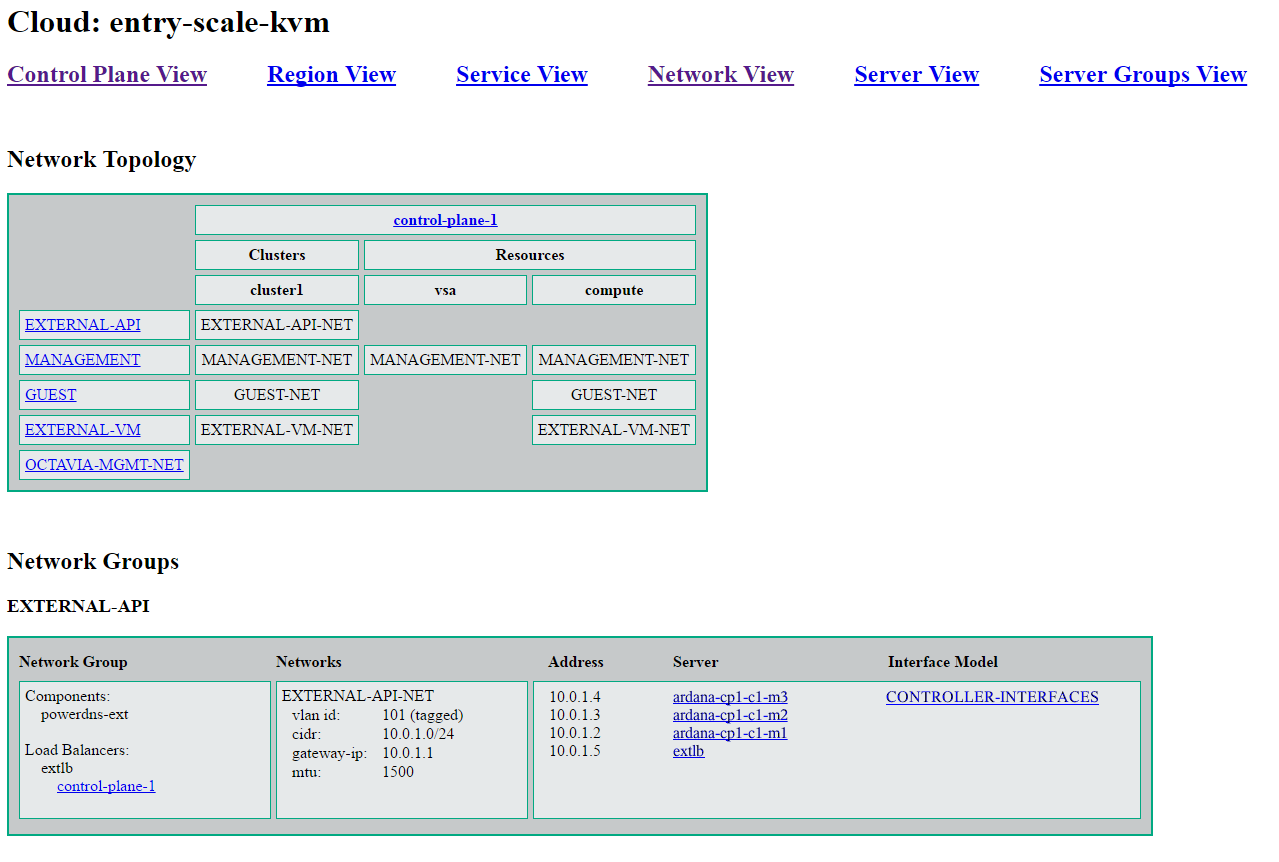
5.2.10 Networking #
In addition to the mapping of to specific and we must also be able to define how the connect to one or more .
In a simple cloud there may be a single L3 network but more typically there are functional and physical layers of network separation that need to be expressed.
Functional network separation provides different networks for different types of traffic; for example, it is common practice in even small clouds to separate the External APIs that users will use to access the cloud and the external IP addresses that users will use to access their virtual machines. In more complex clouds it is common to also separate out virtual networking between virtual machines, block storage traffic, and volume traffic onto their own sets of networks. In the input model, this level of separation is represented by .
Physical separation is required when there are separate L3 network segments providing the same type of traffic; for example, where each rack uses a different subnet. This level of separation is represented in the input model by the within each .
5.2.10.1 Network Groups #
Service endpoints attach to in a specific .
can define routes to other .
encapsulate the configuration for via
A defines the traffic separation model and all of the properties that are common to the set of L3 networks that carry each type of traffic. They define where services are attached to the network model and the routing within that model.
In terms of connectivity, all that has to be captured in the definition are the same service-component names that are used when defining . SUSE OpenStack Cloud also allows a default attachment to be used to specify "all service-components" that are not explicitly connected to another . So, for example, to isolate swift traffic, the swift-account, swift-container, and swift-object service components are attached to an "Object" and all other services are connected to "MANAGEMENT" via the default relationship.
The name of the "MANAGEMENT" cannot be changed. It must be upper case. Every SUSE OpenStack Cloud requires this network group in order to be valid.
The details of how each service connects, such as what port it uses, if it should be behind a load balancer, if and how it should be registered in keystone, and so forth, are defined in the service definition files provided by SUSE OpenStack Cloud.
In any configuration with multiple networks, controlling the routing is a major consideration. In SUSE OpenStack Cloud, routing is controlled at the level. First, all are configured to provide the route to any other in the same . In addition, a may be configured to provide the route any other in the same ; for example, if the internal APIs are in a dedicated (a common configuration in a complex network because a network group with load balancers cannot be segmented) then other may need to include a route to the internal API so that services can access the internal API endpoints. Routes may also be required to define how to access an external storage network or to define a general default route.
As part of the SUSE OpenStack Cloud deployment, networks are configured to act as the default route for all traffic that was received via that network (so that response packets always return via the network the request came from).
Note that SUSE OpenStack Cloud will configure the routing rules on the servers it deploys and will validate that the routes between services exist in the model, but ensuring that gateways can provide the required routes is the responsibility of your network configuration. The configuration processor provides information about the routes it is expecting to be configured.
For a detailed description of how the configuration processor validates routes, refer to Section 7.6, “Network Route Validation”.
5.2.10.1.1 Load Balancers #
provide a specific type of routing and are defined as a relationship between the virtual IP address (VIP) on a network in one and a set of service endpoints (which may be on in the same or a different ).
As each is defined providing a virtual IP on a , it follows that those s can each only have one associated to them.
The definition includes a list of and endpoint roles it will provide a virtual IP for. This model allows service-specific to be defined on different . A "default" value is used to express "all service-components" which require a virtual IP address and are not explicitly configured in another configuration. The details of how the should be configured for each service, such as which ports to use, how to check for service liveness, etc., are provided in the SUSE OpenStack Cloud supplied service definition files.
Where there are multiple instances of a service (for example, in a cloud with multiple control-planes), each control-plane needs its own set of virtual IP address and different values for some properties such as the external name and security certificate. To accommodate this in SUSE OpenStack Cloud 9, load-balancers are defined as part of the control-plane, with the network groups defining just which load-balancers are attached to them.
Load balancers are always implemented by an ha-proxy service in the same control-plane as the services.
5.2.10.1.2 Separation of Public, Admin, and Internal Endpoints #
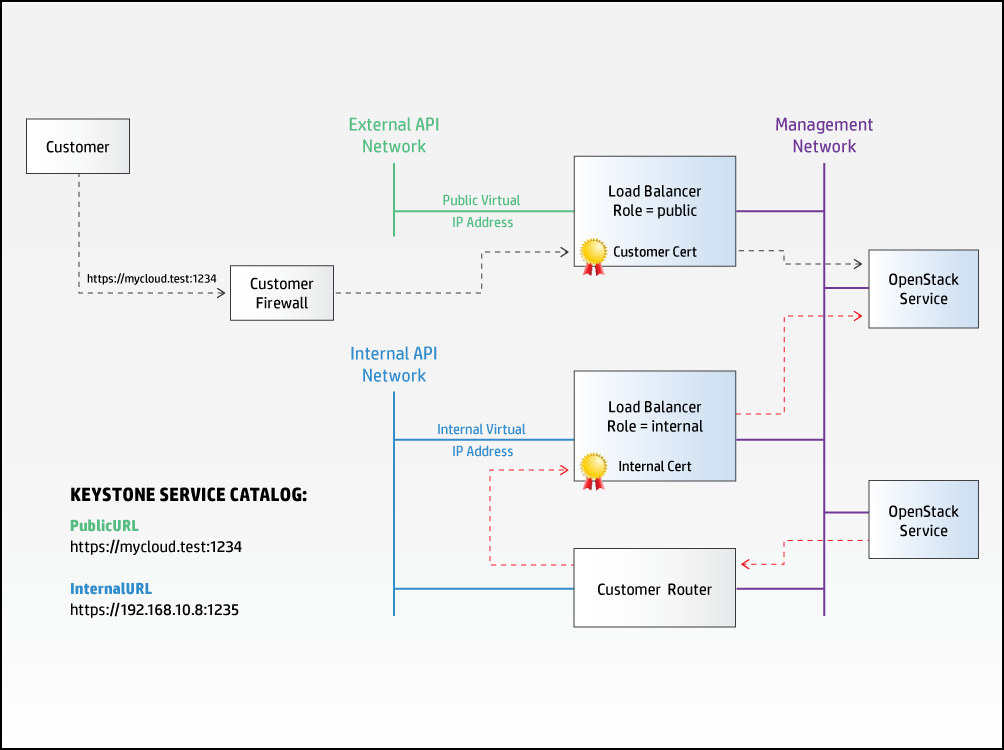
The list of endpoint roles for a make it possible to configure separate for public and internal access to services, and the configuration processor uses this information to both ensure the correct registrations in keystone and to make sure the internal traffic is routed to the correct endpoint. SUSE OpenStack Cloud services are configured to only connect to other services via internal virtual IP addresses and endpoints, allowing the name and security certificate of public endpoints to be controlled by the customer and set to values that may not be resolvable/accessible from the servers making up the cloud.
Note that each defined in the input model will be allocated a separate virtual IP address even when the load-balancers are part of the same . Because of the need to be able to separate both public and internal access, SUSE OpenStack Cloud will not allow a single to provide both public and internal access. in this context are logical entities (sets of rules to transfer traffic from a virtual IP address to one or more endpoints).
The following diagram shows a possible configuration in which the hostname associated with the public URL has been configured to resolve to a firewall controlling external access to the cloud. Within the cloud, SUSE OpenStack Cloud services are configured to use the internal URL to access a separate virtual IP address.
5.2.10.1.3 Network Tags #
Network tags are defined by some SUSE OpenStack Cloud and are used to convey information between the network model and the service, allowing the dependent aspects of the service to be automatically configured.
Network tags also convey requirements a service may have for aspects of the server network configuration, for example, that a bridge is required on the corresponding network device on a server where that service-component is installed.
See Section 6.13.2, “Network Tags” for more information on specific tags and their usage.
5.2.10.2 Networks #
A is part of a .
are fairly simple definitions. Each defines the details of its VLAN, optional address details (CIDR, start and end address, gateway address), and which it is a member of.
5.2.10.3 Interface Model #
A identifies an that describes how its network interfaces are to be configured and used.
Network groups are mapped onto specific network interfaces via an , which describes the network devices that need to be created (bonds, ovs-bridges, etc.) and their properties.
An acts like a template; it can define how some or all of the are to be mapped for a particular combination of physical NICs. However, it is the on each server that determine which are required and hence which interfaces and will be configured. This means that can be shared between different . For example, an API role and a database role may share an interface model even though they may have different disk models and they will require a different subset of the .
Within an , physical ports are identified by a device name, which in turn is resolved to a physical port on a server basis via a . To allow different physical servers to share an , the is defined as a property of each .
The interface-model can also used to describe how network
devices are to be configured for use with DPDK, SR-IOV, and PCI Passthrough.
5.2.10.4 NIC Mapping #
When a has more than a single physical network
port, a is required to unambiguously identify
each port. Standard Linux mapping of ports to interface names at the time of
initial discovery (for example, eth0,
eth1, eth2, ...) is not uniformly
consistent
from server to server, so a mapping of PCI bus address to interface name is
instead.
NIC mappings are also used to specify the device type for interfaces that are to be used for SR-IOV or PCI Passthrough. Each SUSE OpenStack Cloud release includes the data for the supported device types.
5.2.10.5 Firewall Configuration #
The configuration processor uses the details it has about which networks and ports use to create a set of firewall rules for each server. The model allows additional user-defined rules on a per basis.
5.2.11 Configuration Data #
Configuration Data is used to provide settings which have to be applied in a specific context, or where the data needs to be verified against or merged with other values in the input model.
For example, when defining a neutron provider network to be used by Octavia, the network needs to be included in the routing configuration generated by the Configuration Processor.
6 Configuration Objects #
6.1 Cloud Configuration #
The top-level cloud configuration file, cloudConfig.yml,
defines some global values for SUSE OpenStack Cloud, as described in the table below.
The snippet below shows the start of the control plane definition file.
---
product:
version: 2
cloud:
name: entry-scale-kvm
hostname-data:
host-prefix: ardana
member-prefix: -m
ntp-servers:
- "ntp-server1"
# dns resolving configuration for your site
dns-settings:
nameservers:
- name-server1
firewall-settings:
enable: true
# log dropped packets
logging: true
audit-settings:
audit-dir: /var/audit
default: disabled
enabled-services:
- keystone| Key | Value Description |
|---|---|
| name | An administrator-defined name for the cloud |
| hostname-data (optional) |
Provides control over some parts of the generated names (see ) Consists of two values:
|
| ntp-servers (optional) |
A list of external NTP servers your cloud has access to. If specified by name then the names need to be resolvable via the external DNS nameservers you specify in the next section. All servers running the "ntp-server" component will be configured to use these external NTP servers. |
| dns-settings (optional) |
DNS configuration data that will be applied to all servers. See example configuration for a full list of values. |
| smtp-settings (optional) |
SMTP client configuration data that will be applied to all servers. See example configurations for a full list of values. |
| firewall-settings (optional) |
Used to enable/disable the firewall feature and to enable/disable logging of dropped packets. The default is to have the firewall enabled. |
| audit-settings (optional) |
Used to enable/disable the production of audit data from services. The default is to have audit disabled for all services. |
6.2 Control Plane #
The snippet below shows the start of the control plane definition file.
---
product:
version: 2
control-planes:
- name: control-plane-1
control-plane-prefix: cp1
region-name: region0
failure-zones:
- AZ1
- AZ2
- AZ3
configuration-data:
- NEUTRON-CONFIG-CP1
- OCTAVIA-CONFIG-CP1
common-service-components:
- logging-producer
- monasca-agent
- stunnel
- lifecycle-manager-target
clusters:
- name: cluster1
cluster-prefix: c1
server-role: CONTROLLER-ROLE
member-count: 3
allocation-policy: strict
service-components:
- lifecycle-manager
- ntp-server
- swift-ring-builder
- mysql
- ip-cluster
...
resources:
- name: compute
resource-prefix: comp
server-role: COMPUTE-ROLE
allocation-policy: any
min-count: 0
service-components:
- ntp-client
- nova-compute
- nova-compute-kvm
- neutron-l3-agent
...| Key | Value Description |
|---|---|
| name |
This name identifies the control plane. This value is used to persist server allocations Section 7.3, “Persisted Data” and cannot be changed once servers have been allocated. |
| control-plane-prefix (optional) |
The control-plane-prefix is used as part of the hostname (see Section 7.2, “Name Generation”). If not specified, the control plane name is used. |
| region-name |
This name identifies the keystone region within which services in the
control plane will be registered. In SUSE OpenStack Cloud, multiple regions are
not supported. Only
For clouds consisting of multiple control planes, this attribute should
be omitted and the regions object should be used to set the region
name ( |
| uses (optional) |
Identifies the services this control will consume from other control planes (see Section 6.2.3, “Multiple Control Planes”). |
| load-balancers (optional) |
A list of load balancer definitions for this control plane (see Section 6.2.4, “Load Balancer Definitions in Control Planes”). For a multi control-plane cloud load balancers must be defined in each control-plane. For a single control-plane cloud they may be defined either in the control plane or as part of a network group. |
| common-service-components (optional) |
This lists a set of service components that run on all servers in the control plane (clusters and resource pools). |
| failure-zones (optional) |
A list of names that servers for this control plane will be allocated from. If no failure-zones are specified, only servers not associated with a will be used. (See Section 5.2.9.1, “Server Groups and Failure Zones” for a description of server-groups as failure zones.) |
| configuration-data (optional) |
A list of configuration data settings to be used for services in this control plane (see Section 5.2.11, “Configuration Data”). |
| clusters |
A list of clusters for this control plane (see Section 6.2.1, “ Clusters”). |
| resources |
A list of resource groups for this control plane (see Section 6.2.2, “Resources”). |
6.2.1 Clusters #
| Key | Value Description |
|---|---|
| name |
Cluster and resource names must be unique within a control plane. This value is used to persist server allocations (see Section 7.3, “Persisted Data”) and cannot be changed once servers have been allocated. |
| cluster-prefix (optional) |
The cluster prefix is used in the hostname (see Section 7.2, “Name Generation”). If not supplied then the cluster name is used. |
| server-role |
This can either be a string (for a single role) or a list of roles. Only servers matching one of the specified will be allocated to this cluster. (see Section 5.2.4, “Server Roles” for a description of server roles) |
| service-components |
The list of to be deployed on the servers allocated for the cluster. (The common-service-components for the control plane are also deployed.) |
|
member-count min-count max-count (all optional) |
Defines the number of servers to add to the cluster. The number of servers that can be supported in a cluster depends on the services it is running. For example MariaDB and RabbitMQ can only be deployed on clusters on 1 (non-HA) or 3 (HA) servers. Other services may support different sizes of cluster. If min-count is specified, then at least that number of servers will be allocated to the cluster. If min-count is not specified it defaults to a value of 1. If max-count is specified, then the cluster will be limited to that number of servers. If max-count is not specified then all servers matching the required role and failure-zones will be allocated to the cluster. Specifying member-count is equivalent to specifying min-count and max-count with the same value. |
| failure-zones (optional) |
A list of that servers will be allocated from. If specified, it overrides the list of values specified for the control-plane. If not specified, the control-plane value is used. (see Section 5.2.9.1, “Server Groups and Failure Zones” for a description of server groups as failure zones). |
| allocation-policy (optional) |
Defines how failure zones will be used when allocating servers. strict: Server allocations will be distributed across all specified failure zones. (if max-count is not a whole number, an exact multiple of the number of zones, then some zones may provide one more server than other zones) any: Server allocations will be made from any combination of failure zones. The default allocation-policy for a cluster is strict. |
| configuration-data (optional) |
A list of configuration-data settings that will be applied to the services in this cluster. The values for each service will be combined with any values defined as part of the configuration-data list for the control-plane. If a value is specified by settings in both lists, the value defined here takes precedence. |
6.2.2 Resources #
| Key | Value Description |
|---|---|
| name |
The name of this group of resources. Cluster names and resource-node names must be unique within a control plane. Additionally, clusters and resources cannot share names within a control-plane. This value is used to persist server allocations (see Section 7.3, “Persisted Data”) and cannot be changed once servers have been allocated. |
| resource-prefix | The resource-prefix is used in the name generation. (see Section 7.2, “Name Generation”) |
| server-role | This can either be a string (for a single role) or a list of roles. Only servers matching one of the specified will be allocated to this resource group. (see Section 5.2.4, “Server Roles” for a description of server roles). |
| service-components | The list of to be deployed on the servers in this resource group. (The common-service-components for the control plane are also deployed.) |
|
member-count min-count max-count (all optional) |
Defines the number of servers to add to the cluster. The number of servers that can be supported in a cluster depends on the services it is running. For example MariaDB and RabbitMQ can only be deployed on clusters on 1 (non-HA) or 3 (HA) servers. Other services may support different sizes of cluster. If min-count is specified, then at least that number of servers will be allocated to the cluster. If min-count is not specified it defaults to a value of 1. If max-count is specified, then the cluster will be limited to that number of servers. If max-count is not specified then all servers matching the required role and failure-zones will be allocated to the cluster. Specifying member-count is equivalent to specifying min-count and max-count with the same value. |
| failure-zones (optional) | A list of that servers will be allocated from. If specified, it overrides the list of values specified for the control-plane. If not specified, the control-plane value is used. (see Section 5.2.9.1, “Server Groups and Failure Zones” for a description of server groups as failure zones). |
| allocation-policy (optional) |
Defines how failure zones will be used when allocating servers. strict: Server allocations will be distributed across all specified failure zones. (if max-count is not a whole number, an exact multiple of the number of zones, then some zones may provide one more server than other zones) any: Server allocations will be made from any combination of failure zones. The default allocation-policy for resources is any. |
| configuration-data (optional) | A list of configuration-data settings that will be applied to the services in this cluster. The values for each service will be combined with any values defined as part of the configuration-data list for the control-plane. If a value is specified by settings in both lists, the value defined here takes precedence. |
6.2.3 Multiple Control Planes #
The dependencies between service components (for example, nova needs
MariaDB and keystone API) is defined as part of the service definitions
provide by SUSE OpenStack Cloud, the control-planes define how those dependencies will
be met. For clouds consisting of multiple control-planes, the relationship
between services in different control planes is defined by a
uses attribute in its control-plane object. Services
will always use other services in the same control-plane before looking to
see if the required service can be provided from another control-plane.
For example, a service component in control-plane
cp-2 (for example, nova-api) might use service
components from control-plane cp-shared (for example,
keystone-api).
control-planes:
- name: cp-2
uses:
- from: cp-shared
service-components:
- any| Key | Value Description |
|---|---|
| from | The name of the control-plane providing services which may be consumed by this control-plane. |
| service-components |
A list of service components from the specified control-plane which may
be consumed by services in this control-plane. The reserved keyword
any indicates that any service component from the
specified control-plane may be consumed by services in this
control-plane.
|
6.2.4 Load Balancer Definitions in Control Planes #
Starting in SUSE OpenStack Cloud 9, a load-balancer may be defined within a
control-plane object, and referenced by name from a network-groups object.
The following example shows load balancer extlb defined in
control-plane cp1 and referenced from the EXTERNAL-API
network group. See section Load balancers for a complete description of load
balance attributes.
network-groups:
- name: EXTERNAL-API
load-balancers:
- extlb
control-planes:
- name: cp1
load-balancers:
- provider: ip-cluster
name: extlb
external-name:
tls-components:
- default
roles:
- public
cert-file: cp1-extlb-cert6.3 Load Balancers #
Load balancers may be defined as part of a network-group object, or as part of a control-plane object. When a load-balancer is defined in a control-plane, it must be referenced by name only from the associated network-group object.
For clouds consisting of multiple control planes, load balancers must be defined as part of a control-plane object. This allows different load balancer configurations for each control plane.
In either case, a load-balancer definition has the following attributes:
load-balancers:
- provider: ip-cluster
name: extlb
external-name:
tls-components:
- default
roles:
- public
cert-file: cp1-extlb-cert| Key | Value Description |
|---|---|
| name | An administrator defined name for the load balancer. This name is used to make the association from a network-group. |
| provider |
The service component that implements the load balancer. Currently only
ip-cluster (ha-proxy) is supported. Future releases
will provide support for external load balancers.
|
| roles |
The list of endpoint roles that this load balancer provides (see
below).
Valid roles are
public, internal, and
admin. To ensure separation of concerns, the role
public cannot be combined with any other role. See
Load Balancers for an example of how the role provides endpoint
separation.
|
| components (optional) | The list of service-components for which the load balancer provides a non-encrypted virtual IP address for. |
| tls-components (optional) | The list of service-components for which the load balancer provides TLS-terminated virtual IP addresses for. |
| external-name (optional) | The name to be registered in keystone for the publicURL. If not specified, the virtual IP address will be registered. Note that this value cannot be changed after the initial deployment. |
| cert-file (optional) |
The name of the certificate file to be used for tls endpoints. If not
specified, a file name will be constructed using the format
CP-NAME-LB-NAME-cert,
where CP-NAME is the
control-plane name and
LB-NAME is the
load-balancer name.
|
6.4 Regions #
The regions configuration object is used to define how a set of services from
one or more control-planes are mapped into Openstack regions (entries within
the keystone catalog). In SUSE OpenStack Cloud, multiple regions are not
supported. Only Region0 is valid.
Within each region a given service is provided by one control plane, but the set of services in the region may be provided by multiple control planes.
| Key | Value Description |
|---|---|
| name | The name of the region in the keystone service catalog. |
| includes | A list of services to include in this region, broken down by the control planes providing the services. |
| Key | Value Description |
|---|---|
| control-plane | A control-plane name. |
| services |
A list of service names. This list specifies the services from this
control-plane to be included in this region. The reserved keyword
all may be used when all services from the
control-plane are to be included.
|
6.5 Servers #
The configuration object is used to list the available servers for deploying the cloud.
Optionally, it can be used as an input file to the operating system installation process, in which case some additional fields (identified below) will be necessary.
---
product:
version: 2
baremetal:
subnet: 192.168.10.0
netmask: 255.255.255.0
servers:
- id: controller1
ip-addr: 192.168.10.3
role: CONTROLLER-ROLE
server-group: RACK1
nic-mapping: HP-DL360-4PORT
mac-addr: b2:72:8d:ac:7c:6f
ilo-ip: 192.168.9.3
ilo-password: password
ilo-user: admin
- id: controller2
ip-addr: 192.168.10.4
role: CONTROLLER-ROLE
server-group: RACK2
nic-mapping: HP-DL360-4PORT
mac-addr: 8a:8e:64:55:43:76
ilo-ip: 192.168.9.4
ilo-password: password
ilo-user: admin| Key | Value Description |
|---|---|
| id | An administrator-defined identifier for the server. IDs must be unique and are used to track server allocations. (see Section 7.3, “Persisted Data”). |
| ip-addr |
The IP address is used by the configuration processor to install and configure the service components on this server. This IP address must be within the range of a defined in this model. When the servers file is being used for operating system installation, this IP address will be assigned to the node by the installation process, and the associated must be an untagged VLAN. |
| hostname (optional) | The value to use for the hostname of the server. If specified this will be used to set the hostname value of the server which will in turn be reflected in systems such as nova, monasca, etc. If not specified the hostname will be derived based on where the server is used and the network defined to provide hostnames. |
| role | Identifies the of the server. |
| nic-mapping | Name of the entry to apply to this server. (See Section 6.12, “NIC Mappings”.) |
| server-group (optional) | Identifies the entry that this server belongs to. (see Section 5.2.9, “Server Groups”) |
| boot-from-san (optional) | Must be set to true is the server needs to be configured to boot from SAN storage. Default is False |
| fcoe-interfaces (optional) | A list of network devices that will be used for accessing FCoE storage. This is only needed for devices that present as native FCoE, not devices such as Emulex which present as a FC device. |
| ansible-options (optional) |
A string of additional variables to be set when defining the server as
a host in Ansible. For example, ansible_ssh_port=5986
|
| mac-addr (optional) | Needed when the servers file is being used for operating system installation. This identifies the MAC address on the server that will be used to network install the operating system. |
| kopt-extras (optional) |
Provides additional command line arguments to be passed to the booting
network kernel. For example, vga=769 sets the video
mode for the install to low resolution which can be useful for remote
console users.
|
| ilo-ip (optional) | Needed when the servers file is being used for operating system installation. This provides the IP address of the power management (for example, IPMI, iLO) subsystem. |
| ilo-user (optional) | Needed when the servers file is being used for operating system installation. This provides the user name of the power management (for example, IPMI, iLO) subsystem. |
| ilo-password (optional) | Needed when the servers file is being used for operating system installation. This provides the user password of the power management (for example, IPMI, iLO) subsystem. |
| ilo-extras (optional) | Needed when the servers file is being used for operating system installation. Additional options to pass to ipmitool. For example, this may be required if the servers require additional IPMI addressing parameters. |
| moonshot (optional) |
Provides the node identifier for HPE Moonshot servers, for example,
c4n1 where c4 is the cartridge and n1 is node.
|
| hypervisor-id (optional) | This attribute serves two purposes: it indicates that this server is a virtual machine (VM), and it specifies the server id of the Cloud Lifecycle Manager hypervisor that will host the VM. |
| ardana-hypervisor (optional) |
When set to True, this attribute identifies a server as a Cloud Lifecycle Manager
hypervisor. A Cloud Lifecycle Manager hypervisor is a server that may be used to host
other servers that are themselves virtual machines. Default value is
False.
|
6.6 Server Groups #
The server-groups configuration object provides a mechanism for organizing servers and networks into a hierarchy that can be used for allocation and network resolution.
---
product:
version: 2
- name: CLOUD
server-groups:
- AZ1
- AZ2
- AZ3
networks:
- EXTERNAL-API-NET
- EXTERNAL-VM-NET
- GUEST-NET
- MANAGEMENT-NET
#
# Create a group for each failure zone
#
- name: AZ1
server-groups:
- RACK1
- name: AZ2
server-groups:
- RACK2
- name: AZ3
server-groups:
- RACK3
#
# Create a group for each rack
#
- name: RACK1
- name: RACK2
- name: RACK3| Key | Value Description |
|---|---|
| name | An administrator-defined name for the server group. The name is used to link server-groups together and to identify server-groups to be used as failure zones in a . (see Section 6.2, “Control Plane”) |
| server-groups (optional) | A list of server-group names that are nested below this group in the hierarchy. Each server group can only be listed in one other server group (that is in a strict tree topology). |
| networks (optional) | A list of network names (see Section 5.2.10.2, “Networks”). See Section 5.2.9.2, “Server Groups and Networks” for a description of how networks are matched to servers via server groups. |
6.7 Server Roles #
The server-roles configuration object is a list of the various server roles that you can use in your cloud. Each server role is linked to other configuration objects:
Disk model (Section 6.8, “ Disk Models”)
Interface model (Section 6.11, “Interface Models”)
Memory model (Section 6.9, “Memory Models”)
CPU model (Section 6.10, “ CPU Models”)
Server roles are referenced in the servers (see Section 6.7, “Server Roles”) configuration object above.
---
product:
version: 2
server-roles:
- name: CONTROLLER-ROLE
interface-model: CONTROLLER-INTERFACES
disk-model: CONTROLLER-DISKS
- name: COMPUTE-ROLE
interface-model: COMPUTE-INTERFACES
disk-model: COMPUTE-DISKS
memory-model: COMPUTE-MEMORY
cpu-model: COMPUTE-CPU| Key | Value Description |
|---|---|
| name | An administrator-defined name for the role. |
| interface-model |
The name of the to be used for this server-role. Different server-roles can use the same interface-model. |
| disk-model |
The name of the to use for this server-role. Different server-roles can use the same disk-model. |
| memory-model (optional) |
The name of the to use for this server-role. Different server-roles can use the same memory-model. |
| cpu-model (optional) |
The name of the to use for this server-role. Different server-roles can use the same cpu-model. |
6.8 Disk Models #
The disk-models configuration object is used to specify how the directly attached disks on the server should be configured. It can also identify which service or service component consumes the disk, for example, swift object server, and provide service-specific information associated with the disk. It is also used to specify disk sizing information for virtual machine servers.
Disks can be used as raw devices or as logical volumes and the disk model provides a configuration item for each.
If the operating system has been installed by the SUSE OpenStack Cloud installation
process then the root disk will already have been set up as a volume-group
with a single logical-volume. This logical-volume will have been created on a
partition identified, symbolically, in the configuration files as
/dev/sda_root. This is due to the fact that different
BIOS systems (UEFI, Legacy) will result in different partition numbers on the
root disk.
---
product:
version: 2
disk-models:
- name: SES-DISKS
volume-groups:
- ...
device-groups:
- ...
vm-size:
...| Key | Value Description |
|---|---|
| name | The name of the disk-model that is referenced from one or more server-roles. |
| volume-groups | A list of volume-groups to be configured (see below). There must be at least one volume-group describing the root file system. |
| device-groups (optional) | A list of device-groups (see below) |
6.8.1 Volume Groups #
The configuration object is used to define volume groups and their constituent logical volumes.
Note that volume-groups are not exact analogs of device-groups. A volume-group specifies a set of physical volumes used to make up a volume-group that is then subdivided into multiple logical volumes.
The SUSE OpenStack Cloud operating system installation automatically creates a volume-group name "ardana-vg" on the first drive in the system. It creates a "root" logical volume there. The volume-group can be expanded by adding more physical-volumes (see examples). In addition, it is possible to create more logical-volumes on this volume-group to provide dedicated capacity for different services or file system mounts.
volume-groups:
- name: ardana-vg
physical-volumes:
- /dev/sda_root
logical-volumes:
- name: root
size: 35%
fstype: ext4
mount: /
- name: log
size: 50%
mount: /var/log
fstype: ext4
mkfs-opts: -O large_file
- ...
- name: vg-comp
physical-volumes:
- /dev/sdb
logical-volumes:
- name: compute
size: 95%
mount: /var/lib/nova
fstype: ext4
mkfs-opts: -O large_file| Key | Value Descriptions |
|---|---|
| name | The name that will be assigned to the volume-group |
| physical-volumes |
A list of physical disks that make up the volume group. As installed by the SUSE OpenStack Cloud operating system install process, the volume group "ardana-vg" will use a large partition (sda_root) on the first disk. This can be expanded by adding additional disk(s). |
| logical-volumes | A list of logical volume devices to create from the above named volume group. |
| name | The name to assign to the logical volume. |
| size | The size, expressed as a percentage of the entire volume group capacity, to assign to the logical volume. |
| fstype (optional) | The file system type to create on the logical volume. If none specified, the volume is not formatted. |
| mkfs-opts (optional) |
Options, for example, -O large_file to pass to the
mkfs command.
|
| mode (optional) |
The mode changes the root file system mode bits,
which can be either a symbolic representation or an octal number
representing the bit pattern for the new mode bits.
|
| mount (optional) | Mount point for the file system. |
| consumer attributes (optional, consumer dependent) |
These will vary according to the service consuming the device group. The examples section provides sample content for the different services. |
Multipath storage should be listed as the corresponding
/dev/mapper/mpathX
6.8.2 Device Groups #
The device-groups configuration object provides the mechanism to make the whole of a physical disk available to a service.
| Key | Value Descriptions |
|---|---|
| name | An administrator-defined name for the device group. |
| devices |
A list of named devices to be assigned to this group. There must be at least one device in the group.
Multipath storage should be listed as the corresponding
|
| consumer |
Identifies the name of one of the storage services (for example, one of the following: swift, cinder, etc.) that will consume the disks in this device group. |
| consumer attributes |
These will vary according to the service consuming the device group. The examples section provides sample content for the different services. |
6.9 Memory Models #
The memory-models configuration object describes details of the optional configuration of Huge Pages. It also describes the amount of memory to be allocated for virtual machine servers.
The memory-model allows the number of pages of a particular size to be configured at the server level or at the numa-node level.
The following example would configure:
five 2 MB pages in each of numa nodes 0 and 1
three 1 GB pages (distributed across all numa nodes)
six 2 MB pages (distributed across all numa nodes)
memory-models:
- name: COMPUTE-MEMORY-NUMA
default-huge-page-size: 2M
huge-pages:
- size: 2M
count: 5
numa-node: 0
- size: 2M
count: 5
numa-node: 1
- size: 1G
count: 3
- size: 2M
count: 6
- name: VIRTUAL-CONTROLLER-MEMORY
vm-size:
ram: 6G| Key | Value Description |
|---|---|
| name | The name of the memory-model that is referenced from one or more server-roles. |
| default-huge-page-size (optional) |
The default page size that will be used is specified when allocating huge pages. If not specified, the default is set by the operating system. |
| huge-pages | A list of huge page definitions (see below). |
6.9.1 Huge Pages #
| Key | Value Description |
|---|---|
| size |
The page size in kilobytes, megabytes, or gigabytes specified as nX where:
|
| count | The number of pages of this size to create (must be greater than zero). |
| numa-node (optional) |
If specified the pages will be created in the memory associated with this numa node. If not specified the pages are distributed across numa nodes by the operating system. |
6.10 CPU Models #
The cpu-models configuration object describes how CPUs are
assigned for use by service components such as nova (for VMs) and Open
vSwitch (for DPDK), and whether or not those CPUs are isolated from the
general kernel SMP balancing and scheduling algorithms.
It also describes the number of vCPUs for virtual machine servers.
---
product:
version: 2
cpu-models:
- name: COMPUTE-CPU
assignments:
- components:
- nova-compute-kvm
cpu:
- processor-ids: 0-1,3,5-7
role: vm
- components:
- openvswitch
cpu:
- processor-ids: 4,12
isolate: False
role: eal
- processor-ids: 2,10
role: pmd
- name: VIRTUAL-CONTROLLER-CPU
vm-size:
vcpus: 4cpu-models
| Key | Value Description |
|---|---|
| name | An administrator-defined name for the cpu model. |
| assignments | A list of CPU assignments . |
6.10.1 CPU Assignments #
assignments
| Key | Value Description |
|---|---|
| components | A list of components to which the CPUs will be assigned. |
| cpu | A list of CPU usage objects (see Section 6.10.2, “CPU Usage” below). |
6.10.2 CPU Usage #
cpu
| Key | Value Description |
|---|---|
| processor-ids | A list of CPU IDs as seen by the operating system. |
| isolate (optional) |
A Boolean value which indicates if the CPUs are to be isolated from the general kernel SMP balancing and scheduling algorithms. The specified processor IDs will be configured in the Linux kernel isolcpus parameter. The default value is True. |
| role | A role within the component for which the CPUs will be used. |
6.10.3 Components and Roles in the CPU Model #
| Component | Role | Description |
|---|---|---|
| nova-compute-kvm | vm |
The specified processor IDs will be configured in the nova vcpu_pin_set option. |
| openvswitch | eal |
The specified processor IDs will be configured in the Open vSwitch DPDK EAL -c (coremask) option. Refer to the DPDK documentation for details. |
| pmd |
The specified processor IDs will be configured in the Open vSwitch pmd-cpu-mask option. Refer to the Open vSwitch documentation and the ovs-vswitchd.conf.db man page for details. |
6.11 Interface Models #
The interface-models configuration object describes how network interfaces are bonded and the mapping of network groups onto interfaces. Interface devices are identified by name and mapped to a particular physical port by the (see Section 5.2.10.4, “NIC Mapping”).
---
product:
version: 2
interface-models:
- name: INTERFACE_SET_CONTROLLER
network-interfaces:
- name: BONDED_INTERFACE
device:
name: bond0
bond-data:
provider: linux
devices:
- name: hed3
- name: hed4
options:
mode: active-backup
miimon: 200
primary: hed3
network-groups:
- EXTERNAL_API
- EXTERNAL_VM
- GUEST
- name: UNBONDED_INTERFACE
device:
name: hed0
network-groups:
- MGMT
fcoe-interfaces:
- name: FCOE_DEVICES
devices:
- eth7
- eth8
- name: INTERFACE_SET_DPDK
network-interfaces:
- name: BONDED_DPDK_INTERFACE
device:
name: bond0
bond-data:
provider: openvswitch
devices:
- name: dpdk0
- name: dpdk1
options:
mode: active-backup
network-groups:
- GUEST
- name: UNBONDED_DPDK_INTERFACE
device:
name: dpdk2
network-groups:
- PHYSNET2
dpdk-devices:
- devices:
- name: dpdk0
- name: dpdk1
- name: dpdk2
driver: igb_uio
components:
- openvswitch
eal-options:
- name: socket-mem
value: 1024,0
- name: n
value: 2
component-options:
- name: n-dpdk-rxqs
value: 64| Key | Value Description |
|---|---|
| name | An administrator-defined name for the interface model. |
| network-interfaces | A list of network interface definitions. |
| fcoe-interfaces (optional): Section 6.11.2, “fcoe-interfaces” |
A list of network interfaces that will be used for Fibre Channel over Ethernet (FCoE). This is only needed for devices that present as a native FCoE device, not cards such as Emulex which present FCoE as a FC device. |
| dpdk-devices (optional) | A list of DPDK device definitions. |
The devices must be “raw” device names, not names controlled via a nic-mapping.
6.11.1 network-interfaces #
The network-interfaces configuration object has the following attributes:
| Key | Value Description |
|---|---|
| name | An administrator-defined name for the interface |
| device |
A dictionary containing the network device name (as seen on the associated server) and associated properties (see Section 6.11.1.1, “network-interfaces device” for details). |
| network-groups (optional if forced-network-groups is defined) | A list of one or more (see Section 6.13, “Network Groups”) containing (see Section 6.14, “Networks”) that can be accessed via this interface. Networks in these groups will only be configured if there is at least one on the server which matches the list of component-endpoints defined in the . |
| forced-network-groups (optional if network-groups is defined) | A list of one or more (see Section 6.13, “Network Groups”) containing (see Section 6.14, “Networks”) that can be accessed via this interface. Networks in these groups are always configured on the server. |
| passthrough-network-groups (optional) |
A list of one or more network-groups (see
Section 6.13, “Network Groups”) containing networks (see
Section 6.14, “Networks”) that can be accessed by servers
running as virtual machines on an Cloud Lifecycle Manager hypervisor server. Networks in
these groups are not configured on the Cloud Lifecycle Manager hypervisor server unless
they also are specified in the network-groups or
forced-network-groups attributes.
|
6.11.1.1 network-interfaces device #
network-interfaces device
The network-interfaces device configuration object has the following attributes:
| Key | Value Description |
|---|---|
| name |
When configuring a bond, this is used as the bond device name - the names of the devices to be bonded are specified in the bond-data section. If the interface is not bonded, this must be the name of the device specified by the nic-mapping (see NIC Mapping). |
| vf-count (optional) |
Indicates that the interface is to be used for SR-IOV. The value is the number of virtual functions to be created. The associated device specified by the nic-mapping must have a valid nice-device-type. vf-count cannot be specified on bonded interfaces
Interfaces used for SR-IOV must be associated with a network with
|
| sriov-only (optional) |
Only valid when vf-count is specified. If set to true then the interface is to be used for virtual functions only and the physical function will not be used. The default value is False. |
| pci-pt (optional) |
If set to true then the interface is used for PCI passthrough. The default value is False. |
6.11.2 fcoe-interfaces #
The fcoe-interfaces configuration object has the following attributes:
| Key | Value Description |
|---|---|
| name | An administrator-defined name for the group of FCOE interfaces |
| devices |
A list of network devices that will be configured for FCOE Entries in this must be the name of a device specified by the nic-mapping (see Section 6.12, “NIC Mappings”). |
6.11.3 dpdk-devices #
The dpdk-devices configuration object has the following attributes:
| Key | Value Descriptions |
|---|---|
| devices |
A list of network devices to be configured for DPDK. See Section 6.11.3.1, “ dpdk-devices devices”. |
| eal-options |
A list of key-value pairs that may be used to set DPDK Environmental Abstraction Layer (EAL) options. Refer to the DPDK documentation for details.
Note that the cpu-model should be used to specify the processor IDs to
be used by EAL for this component. The EAL coremask
( |
| component-options |
A list of key-value pairs that may be used to set component-specific configuration options. |
6.11.3.1 dpdk-devices devices #
The devices configuration object within dpdk-devices has the following attributes:
| Key | Value Descriptions |
|---|---|
| name | The name of a network device to be used with DPDK. The device names must be the logical-name specified by the nic-mapping (see Section 6.12, “NIC Mappings”). |
| driver (optional) |
Defines the userspace I/O driver to be used for network devices where the native device driver does not provide userspace I/O capabilities.
The default value is |
6.11.3.2 DPDK component-options for the openvswitch component #
The following options are supported for use with the openvswitch component:
| Name | Value Descriptions |
|---|---|
| n-dpdk-rxqs |
Number of rx queues for each DPDK interface. Refer to the Open vSwitch
documentation and the |
Note that the cpu-model should be used to define the CPU affinity of the Open vSwitch
PMD (Poll Mode Driver) threads. The Open vSwitch
pmd-cpu-mask option will be set automatically based on the
information in the cpu-model. See Section 6.10, “
CPU Models”.
6.12 NIC Mappings #
The configuration object is used to ensure
that the network device name used by the operating system always maps to the
same physical device. A is associated to a
in the server definition file. Devices should be named hedN to
avoid name clashes with any other devices configured during the operating
system install as well as any interfaces that are not being managed by
SUSE OpenStack Cloud, ensuring that all devices on a baremetal machine are specified in
the file. An excerpt from nic_mappings.yml illustrates:
---
product:
version: 2
nic-mappings:
- name: HP-DL360-4PORT
physical-ports:
- logical-name: hed1
type: simple-port
bus-address: "0000:07:00.0"
- logical-name: hed2
type: simple-port
bus-address: "0000:08:00.0"
nic-device-type: '8086:10fb'
- logical-name: hed3
type: multi-port
bus-address: "0000:09:00.0"
port-attributes:
port-num: 0
- logical-name: hed4
type: multi-port
bus-address: "0000:09:00.0"
port-attributes:
port-num: 1Each entry in the list has the following attributes:
| Key | Value Description |
|---|---|
| name | An administrator-defined name for the mapping. This name may be used in a server definition (see Section 6.5, “Servers”) to apply the mapping to that server. |
| physical-ports | A list containing device name to address mapping information. |
Each entry in the list has the following attributes:
| Key | Value Description |
|---|---|
| logical-name | The network device name that will be associated with the device at the specified bus-address. The logical-name specified here can be used as a device name in network interface model definitions. (See Section 6.11, “Interface Models”.) |
| type |
The type of port. SUSE OpenStack Cloud 9 supports "simple-port" and "multi-port". Use "simple-port" if your device has a unique bus-address. Use "multi-port" if your hardware requires a "port-num" attribute to identify a single port on a multi-port device. An examples of such a device is:
|
| bus-address |
PCI bus address of the port. Enclose the bus address in quotation marks
so yaml does not misinterpret the embedded colon
(:) characters. See
Chapter 14, Pre-Installation Checklist for details on how to determine
this value. |
port-attributes (required if type is
multi-port)
| Provides a list of attributes for the physical port. The current implementation supports only one attribute, "port-num". Multi-port devices share a bus-address. Use the "port-num" attribute to identify which physical port on the multi-port device to map. See Chapter 14, Pre-Installation Checklist for details on how to determine this value. |
| nic-device-type (optional) |
Specifies the PCI vendor ID and device ID of the port in the format of
VENDOR_ID:DEVICE_ID, for example,
8086:10fb.
|
6.13 Network Groups #
Network-groups define the overall network topology, including where service-components connect, what load balancers are to be deployed, which connections use TLS, and network routing. They also provide the data needed to map neutron's network configuration to the physical networking.
The name of the "MANAGEMENT" cannot be changed. It must be upper case. Every SUSE OpenStack Cloud requires this network group in order to be valid.
---
product:
version: 2
network-groups:
- name: EXTERNAL-API
hostname-suffix: extapi
load-balancers:
- provider: ip-cluster
name: extlb
external-name:
tls-components:
- default
roles:
- public
cert-file: my-public-entry-scale-kvm-cert
- name: EXTERNAL-VM
tags:
- neutron.l3_agent.external_network_bridge
- name: GUEST
hostname-suffix: guest
tags:
- neutron.networks.vxlan
- name: MANAGEMENT
hostname-suffix: mgmt
hostname: true
component-endpoints:
- default
routes:
- default
load-balancers:
- provider: ip-cluster
name: lb
components:
- default
roles:
- internal
- admin
tags:
- neutron.networks.vlan:
provider-physical-network: physnet1| Key | Value Description |
|---|---|
| name | An administrator-defined name for the network group. The name is used to make references from other parts of the input model. |
| component-endpoints (optional) | The list of that will bind to or need direct access to networks in this network-group. |
| hostname (optional) |
If set to true, the name of the address associated with a network in this group will be used to set the hostname of the server. |
| hostname-suffix (optional) | If supplied, this string will be used in the name generation (see Section 7.2, “Name Generation”). If not specified, the name of the network-group will be used. |
| load-balancers (optional) |
A list of load balancers to be configured on networks in this network-group. Because load balances need a virtual IP address, any network group that contains a load balancer can only have one network associated with it.
For clouds consisting of a single control plane, a load balancer may be
fully defined within a
Starting in SUSE OpenStack Cloud 9, a load balancer may be defined within a
|
| routes (optional) |
A list of that networks in this group
provide access to via their gateway. This can include the value
A network group with no services attached to it can be used to define routes to external networks. The name of a neutron provide network defined via configuration-data (see Section 6.16.2.1, “neutron-provider-networks”) can also be included in this list. |
| tags (optional) |
A list of network tags. Tags provide the linkage between the physical network configuration and the neutron network configuration.
Starting in SUSE OpenStack Cloud 9, network tags may be defined as part of a
neutron |
| mtu (optional) |
Specifies the MTU value required for networks in this network group If not specified a default value of 1500 is used. See Section 6.13.3, “MTU (Maximum Transmission Unit)” on how MTU settings are applied to interfaces when there are multiple tagged networks on the same interface. |
hostnamemust be set to
true for one, and only one, of your network groups.
A load balancer definition has the following attributes:
| Key | Value Description |
|---|---|
| name | An administrator-defined name for the load balancer. |
| provider |
The service component that implements the load balancer. Currently only
ip-cluster (ha-proxy) is supported. Future releases
will provide support for external load balancers.
|
| roles | The list of endpoint roles that this load balancer provides (see below). Valid roles are "public", "internal", and "admin'. To ensure separation of concerns, the role "public" cannot be combined with any other role. See Section 5.2.10.1.1, “Load Balancers” for an example of how the role provides endpoint separation. |
| components (optional) | The list of for which the load balancer provides a non-encrypted virtual IP address for. |
| tls-components (optional) | The list of for which the load balancer provides TLS-terminated virtual IP addresses for. In SUSE OpenStack Cloud, TLS is supported both for internal and public endpoints. |
| external-name (optional) | The name to be registered in keystone for the publicURL. If not specified, the virtual IP address will be registered. Note that this value cannot be changed after the initial deployment. |
| cert-file (optional) | The name of the certificate file to be used for TLS endpoints. |
6.13.1 Load Balancer Definitions in Network Groups #
In a cloud consisting of a single control-plane, a
load-balancer may be fully defined within a
network-groups object as shown in the examples above. See
section Section 6.3, “Load Balancers” for a complete description
of load balancer attributes.
Starting in SUSE OpenStack Cloud 9, a load-balancer may be
defined within a control-plane object in which case the
network-group provides just a list of load balancer names as shown below. See
section Section 6.3, “Load Balancers” definitions in control
planes.
network-groups:
- name: EXTERNAL-API
hostname-suffix: extapi
load-balancers:
- lb-cp1
- lb-cp2The same load balancer name can be used in multiple control-planes to make the above list simpler.
6.13.2 Network Tags #
SUSE OpenStack Cloud supports a small number of network tags which may be used to convey information between the input model and the service components (currently only neutron uses network tags). A network tag consists minimally of a tag name; but some network tags have additional attributes.
| Tag | Value Description |
|---|---|
| neutron.networks.vxlan | This tag causes neutron to be configured to use VxLAN as the underlay for tenant networks. The associated network group will carry the VxLAN traffic. |
| tenant-vxlan-id-range (optional) | Used to specify the VxLAN identifier range in the format “MIN-ID:MAX-ID”. The default range is “1001:65535”. Enclose the range in quotation marks. Multiple ranges can be specified as a comma-separated list. |
Example using the default ID range:
tags:
- neutron.networks.vxlanExample using a user-defined ID range:
tags:
- neutron.networks.vxlan:
tenant-vxlan-id-range: “1:20000”Example using multiple user-defined ID range:
tags:
- neutron.networks.vxlan:
tenant-vxlan-id-range: “1:2000,3000:4000,5000:6000”| Tag | Value Description |
|---|---|
| neutron.networks.vlan |
This tag causes neutron to be configured for provider VLAN networks, and optionally to use VLAN as the underlay for tenant networks. The associated network group will carry the VLAN traffic. This tag can be specified on multiple network groups. However, this tag does not cause any neutron networks to be created, that must be done in neutron after the cloud is deployed. |
| provider-physical-network | The provider network name. This is the name to be used in the neutron API for the provider:physical_network parameter of network objects. |
| tenant-vlan-id-range (optional) | This attribute causes neutron to use VLAN for tenant networks; omit this attribute if you are using provider VLANs only. It specifies the VLAN ID range for tenant networks, in the format “MIN-ID:MAX-ID”. Enclose the range in quotation marks. Multiple ranges can be specified as a comma-separated list. |
Example using a provider vlan only (may be used with tenant VxLAN):
tags:
- neutron.networks.vlan:
provider-physical-network: physnet1Example using a tenant and provider VLAN:
tags:
- neutron.networks.vlan:
provider-physical-network: physnet1
tenant-vlan-id-range: “30:50,100:200”| Tag | Value Description |
|---|---|
| neutron.networks.flat |
This tag causes neutron to be configured for provider flat networks. The associated network group will carry the traffic. This tag can be specified on multiple network groups. However, this tag does not cause any neutron networks to be created, that must be done in neutron after the cloud is deployed. |
| provider-physical-network | The provider network name. This is the name to be used in the neutron API for the provider:physical_network parameter of network objects. When specified on multiple network groups, the name must be unique for each network group. |
Example using a provider flat network:
tags:
- neutron.networks.flat:
provider-physical-network: flatnet1| Tag | Value Description |
|---|---|
| neutron.l3_agent.external_network_bridge |
This tag causes the neutron L3 Agent to be configured to use the associated network group as the neutron external network for floating IP addresses. A CIDR should not be defined for the associated physical network, as that will cause addresses from that network to be configured in the hypervisor. When this tag is used, provider networks cannot be used as external networks. However, this tag does not cause a neutron external networks to be created, that must be done in neutron after the cloud is deployed. |
Example using neutron.l3_agent.external_network_bridge:
tags:
- neutron.l3_agent.external_network_bridge6.13.3 MTU (Maximum Transmission Unit) #
A network group may optionally specify an MTU for its networks to use. Because a network-interface in the interface-model may have a mix of one untagged-vlan network group and one or more tagged-vlan network groups, there are some special requirements when specifying an MTU on a network group.
If the network group consists of untagged-vlan network(s) then its specified MTU must be greater than or equal to the MTU of any tagged-vlan network groups which are co-located on the same network-interface.
For example consider a network group with untagged VLANs, NET-GROUP-1, which is going to share (via a Network Interface definition) a device (eth0) with two network groups with tagged VLANs: NET-GROUP-2 (ID=201, MTU=1550) and NET-GROUP-3 (ID=301, MTU=9000).
The device (eth0) must have an MTU which is large enough to accommodate the VLAN in NET-GROUP-3. Since NET-GROUP-1 has untagged VLANS it will also be using this device and so it must also have an MTU of 9000, which results in the following configuration.
+eth0 (9000) <------ this MTU comes from NET-GROUP-1
| |
| |----+ vlan201@eth0 (1550)
\------+ vlan301@eth0 (9000)Where an interface is used only by network groups with tagged VLANs the MTU of the device or bond will be set to the highest MTU value in those groups.
For example if bond0 is configured to be used by three network groups: NET-GROUP-1 (ID=101, MTU=3000), NET-GROUP-2 (ID=201, MTU=1550) and NET-GROUP-3 (ID=301, MTU=9000).
Then the resulting configuration would be:
+bond0 (9000) <------ because of NET-GROUP-3
| | |
| | |--+vlan101@bond0 (3000)
| |----+vlan201@bond0 (1550)
|------+vlan301@bond0 (9000)6.14 Networks #
A network definition represents a physical L3 network used by the cloud infrastructure. Note that these are different from the network definitions that are created/configured in neutron, although some of the networks may be used by neutron.
---
product:
version: 2
networks:
- name: NET_EXTERNAL_VM
vlanid: 102
tagged-vlan: true
network-group: EXTERNAL_VM
- name: NET_GUEST
vlanid: 103
tagged-vlan: true
cidr: 10.1.1.0/24
gateway-ip: 10.1.1.1
network-group: GUEST
- name: NET_MGMT
vlanid: 100
tagged-vlan: false
cidr: 10.2.1.0/24
addresses:
- 10.2.1.10-10.2.1.20
- 10.2.1.24
- 10.2.1.30-10.2.1.36
gateway-ip: 10.2.1.1
network-group: MGMT| Key | Value Description |
|---|---|
| name | The name of this network. The network name may be used in a server-group definition (see Section 6.6, “Server Groups”) to specify a particular network from within a network-group to be associated with a set of servers. |
| network-group | The name of the associated network group. |
| vlanid (optional) | The IEEE 802.1Q VLAN Identifier, a value in the range 1 through 4094. A vlanid must be specified when tagged-vlan is true. |
| tagged-vlan (optional) |
May be set to true or false. If
true, packets for this network carry the
vlanid in the packet header; such packets are
referred to as VLAN-tagged frames in IEEE 1Q.
|
| cidr (optional) | The IP subnet associated with this network. |
| addresses (optional) |
A list of IP addresses or IP address ranges (specified as
The |
| start-address (optional) (deprecated) |
An IP address within the CIDR which will be used as the start of the range of IP addresses from which server addresses may be allocated. The default value is the first host address within the CIDR (for example, the .1 address). |
| end-address (optional) (deprecated) |
An IP address within the CIDR which will be used as
the end of the range of IP addresses from which server addresses may be
allocated. The default value is the last host address within the
CIDR (for example, the .254 address of a /24). This
parameter is deprecated in favor of the new |
| gateway-ip (optional) | The IP address of the gateway for this network. Gateway addresses must be specified if the associated provides routes. |
6.15 Firewall Rules #
The configuration processor will automatically generate "allow" firewall rules for each server based on the services deployed and block all other ports. The firewall rules in the input model allow the customer to define additional rules for each network group.
Administrator-defined rules are applied after all rules generated by the Configuration Processor.
---
product:
version: 2
firewall-rules:
- name: PING
network-groups:
- MANAGEMENT
- GUEST
- EXTERNAL-API
rules:
# open ICMP echo request (ping)
- type: allow
remote-ip-prefix: 0.0.0.0/0
# icmp type
port-range-min: 8
# icmp code
port-range-max: 0
protocol: icmp| Key | Value Description |
|---|---|
| name | An administrator-defined name for the group of rules. |
| network-groups |
A list of names that the rules apply to. A value of "all" matches all network-groups. |
| rules |
A list of rules. Rules are applied in the order in which they appear in the list, apart from the control provided by the "final" option (see above). The order between sets of rules is indeterminate. |
6.15.1 Rule #
Each rule in the list takes the following parameters (which match the parameters of a neutron security group rule):
| Key | Value Description |
|---|---|
| type | Must allow
|
| remote-ip-prefix | Range of remote addresses in CIDR format that this rule applies to. |
|
port-range-min port-range-max |
Defines the range of ports covered by the rule. Note that if the
protocol is icmp then port-range-min is the ICMP
type and port-range-max is the ICMP code.
|
| protocol |
Must be one of tcp, udp, or
icmp. |
6.16 Configuration Data #
Configuration data allows values to be passed into the model to be used in the context of a specific control plane or cluster. The content and format of the data is service specific.
---
product:
version: 2
configuration-data:
- name: NEUTRON-CONFIG-CP1
services:
- neutron
data:
neutron_provider_networks:
- name: OCTAVIA-MGMT-NET
provider:
- network_type: vlan
physical_network: physnet1
segmentation_id: 106
cidr: 172.30.1.0/24
no_gateway: True
enable_dhcp: True
allocation_pools:
- start: 172.30.1.10
end: 172.30.1.250
host_routes:
# route to MANAGEMENT-NET-1
- destination: 192.168.245.0/24
nexthop: 172.30.1.1
neutron_external_networks:
- name: ext-net
cidr: 172.31.0.0/24
gateway: 172.31.0.1
provider:
- network_type: vlan
physical_network: physnet1
segmentation_id: 107
allocation_pools:
- start: 172.31.0.2
end: 172.31.0.254
network-tags:
- network-group: MANAGEMENT
tags:
- neutron.networks.vxlan
- neutron.networks.vlan:
provider-physical-network: physnet1
- network-group: EXTERNAL-VM
tags:
- neutron.l3_agent.external_network_bridge| Key | Value Description |
|---|---|
| name | An administrator-defined name for the set of configuration data. |
| services |
A list of services that the data applies to. Note that these are
service names (for example,
|
| data | A service specific data structure (see below). |
| network-tags (optional, neutron-only) |
A list of network tags. Tags provide the linkage between the physical network configuration and the neutron network configuration.
Starting in SUSE OpenStack Cloud 9, network tags may be defined as part of a
neutron |
6.16.1 neutron network-tags #
| Key | Value Description |
|---|---|
| network-group | The name of the network-group with which the tags are associated. |
| tags | A list of network tags. Tags provide the linkage between the physical network configuration and the neutron network configuration. See section Network Tags. |
6.16.2 Neutron Configuration Data #
| Key | Value Description |
|---|---|
| neutron-provider-networks | A list of provider networks that will be created in neutron. |
| neutron-external-networks | A list of external networks that will be created in neutron. These networks will have the “router:external” attribute set to True. |
6.16.2.1 neutron-provider-networks #
| Key | Value Description |
|---|---|
| name |
The name for this network in neutron. This name must be distinct from the names of any Network Groups in the model to enable it to be included in the “routes” value of a network group. |
| provider |
Details of network to be created
These values are passed as |
| cidr |
The CIDR to use for the network. This is passed to the
|
| shared (optional) |
A Boolean value that specifies if the network can be shared.
This value is passed to the |
| allocation_pools (optional) |
A list of start and end address pairs that limit the set of IP addresses that can be allocated for this network.
These values are passed to the |
| host_routes (optional) |
A list of routes to be defined for the network. Each route consists of a
These values are passed to the |
| gateway_ip (optional) |
A gateway address for the network.
This value is passed to the |
| no_gateway (optional) |
A Boolean value indicating that the gateway should not be distributed on this network.
This is translated into the |
| enable_dhcp (optional) |
A Boolean value indicating that DHCP should be enabled. The default if not specified is to not enable DHCP.
This value is passed to the |
6.16.2.2 neutron-external-networks #
| Key | Value Description |
|---|---|
| name |
The name for this network in neutron. This name must be distinct from the names of any Network Groups in the model to enable it to be included in the “routes” value of a network group. |
| provider (optional) |
The provider attributes are specified when using neutron provider
networks as external networks. Provider attributes should not be
specified when the external network is configured with the
Standard provider network attributes may be specified:
These values are passed as |
| cidr |
The CIDR to use for the network. This is passed to the
|
| allocation_pools (optional) |
A list of start and end address pairs that limit the set of IP addresses that can be allocated for this network.
These values are passed to the |
| gateway (optional) |
A gateway address for the network.
This value is passed to the |
6.16.3 Octavia Configuration Data #
---
product:
version: 2
configuration-data:
- name: OCTAVIA-CONFIG-CP1
services:
- octavia
data:
amp_network_name: OCTAVIA-MGMT-NET| Key | Value Description |
|---|---|
| amp_network_name | The name of the neutron provider network that Octavia will use for management access to load balancers. |
6.16.4 Ironic Configuration Data #
---
product:
version: 2
configuration-data:
- name: IRONIC-CONFIG-CP1
services:
- ironic
data:
cleaning_network: guest-network
enable_node_cleaning: true
enable_oneview: false
oneview_manager_url:
oneview_username:
oneview_encrypted_password:
oneview_allow_insecure_connections:
tls_cacert_file:
enable_agent_drivers: trueRefer to the documentation on configuring ironic for details of the above attributes.
6.16.5 Swift Configuration Data #
---
product:
version: 2
configuration-data:
- name: SWIFT-CONFIG-CP1
services:
- swift
data:
control_plane_rings:
swift-zones:
- id: 1
server-groups:
- AZ1
- id: 2
server-groups:
- AZ2
- id: 3
server-groups:
- AZ3
rings:
- name: account
display-name: Account Ring
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
- name: container
display-name: Container Ring
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
- name: object-0
display-name: General
default: yes
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3Refer to the documentation on Section 11.10, “Understanding Swift Ring Specifications” for details of the above attributes.
6.17 Pass Through #
Through pass_through definitions, certain configuration values can be assigned and used.
product:
version: 2
pass-through:
global:
esx_cloud: true
servers:
data:
vmware:
cert_check: false
vcenter_cluster: Cluster1
vcenter_id: BC9DED4E-1639-481D-B190-2B54A2BF5674
vcenter_ip: 10.1.200.41
vcenter_port: 443
vcenter_username: administrator@vsphere.local
id: 7d8c415b541ca9ecf9608b35b32261e6c0bf275a| Key | Value Description |
|---|---|
| global | These values will be used at the cloud level. |
| servers | These values will be assigned to a specific server(s) using the server-id. |
7 Other Topics #
7.1 Services and Service Components #
| Type | Service | Service Components |
|---|---|---|
| Compute | ||
| Virtual Machine Provisioning | nova |
nova-api nova-compute nova-compute-hyperv nova-compute-ironic nova-compute-kvm nova-conductor nova-console-auth nova-esx-compute-proxy nova-metadata nova-novncproxy nova-scheduler nova-scheduler-ironic nova-placement-api |
| Bare Metal Provisioning | ironic |
ironic-api ironic-conductor |
| Networking | ||
| Networking | neutron |
infoblox-ipam-agent neutron-dhcp-agent neutron-l2gateway-agent neutron-l3-agent neutron-metadata-agent neutron-ml2-plugin neutron-openvswitch-agent neutron-ovsvapp-agent neutron-server neutron-sriov-nic-agent neutron-vpn-agent |
| Network Load Balancer | octavia |
octavia-api octavia-health-manager |
| Domain Name Service (DNS) | designate |
designate-api designate-central designate-mdns designate-mdns-external designate-pool-manager designate-zone-manager |
| Storage | ||
| Block Storage | cinder |
cinder-api cinder-backup cinder-scheduler cinder-volume |
| Object Storage | swift |
swift-account swift-common swift-container swift-object swift-proxy swift-ring-builder swift-rsync |
| Image | ||
| Image Management | glance |
glance-api glance-registry |
| Security | ||
| Key Management | barbican |
barbican-api barbican-worker |
| Identity and Authentication | keystone |
keystone-api |
| Orchestration | ||
| Orchestration | heat |
heat-api heat-api-cfn heat-api-cloudwatch heat-engine |
| Operations | ||
| Telemetry | ceilometer |
ceilometer-agent-notification ceilometer-common ceilometer-polling |
| Cloud Lifecycle Manager | ardana |
ardana-ux-services lifecycle-manager lifecycle-manager-target |
| Dashboard | horizon |
horizon |
| Centralized Logging | logging |
logging-api logging-producer logging-rotate logging-server |
| Monitoring | monasca |
monasca-agent monasca-api monasca-dashboard monasca-liveness-check monasca-notifier monasca-persister monasca-threshold monasca-transform |
| Operations Console | operations |
ops-console-web |
| Openstack Functional Test Suite | tempest |
tempest |
| Foundation | ||
| OpenStack Clients | clients |
barbican-client cinder-client designate-client glance-client heat-client ironic-client keystone-client monasca-client neutron-client nova-client openstack-client swift-client |
| Supporting Services | foundation |
apache2 bind bind-ext influxdb ip-cluster kafka memcached mysql ntp-client ntp-server openvswitch rabbitmq spark storm cassandra zookeeper |
7.2 Name Generation #
Names are generated by the configuration processor for all allocated IP addresses. A server connected to multiple networks will have multiple names associated with it. One of these may be assigned as the hostname for a server via the network-group configuration (see Section 6.12, “NIC Mappings”). Names are generated from data taken from various parts of the input model as described in the following sections.
Clusters#
Names generated for servers in a cluster have the following form:
CLOUD-CONTROL-PLANE-CLUSTERMEMBER-PREFIXMEMBER_ID-NETWORK
Example: ardana-cp1-core-m1-mgmt
| Name | Description |
|---|---|
| CLOUD | Comes from the hostname-data section of the object (see Section 6.1, “Cloud Configuration”) |
| CONTROL-PLANE | is the prefix or name (see Section 6.2, “Control Plane”) |
| CLUSTER | is the name (see Section 6.2.1, “ Clusters”) |
| member-prefix | comes from the hostname-data section of the object (see Section 6.1, “Cloud Configuration”) |
| member_id | is the ordinal within the cluster, generated by the configuration processor as servers are allocated to the cluster |
| network | comes from the of the network group to which the network belongs (see Section 6.12, “NIC Mappings”). |
Resource Nodes#
Names generated for servers in a resource group have the following form:
CLOUD-CONTROL-PLANE-RESOURCE-PREFIXMEMBER_ID-NETWORK
Example: ardana-cp1-comp0001-mgmt
| Name | Description |
|---|---|
| CLOUD | comes from the hostname-data section of the object (see Section 6.1, “Cloud Configuration”). |
| CONTROL-PLANE | is the prefix or name (see Section 6.2, “Control Plane”). |
| RESOURCE-PREFIX | is the value name (see Section 6.2.2, “Resources”). |
| MEMBER_ID | is the ordinal within the cluster, generated by the configuration processor as servers are allocated to the cluster, padded with leading zeroes to four digits. |
| NETWORK | comes from the of the network group to which the network belongs to (see Section 6.12, “NIC Mappings”) |
7.3 Persisted Data #
The configuration processor makes allocation decisions on servers and IP addresses which it needs to remember between successive runs so that if new servers are added to the input model they do not disrupt the previously deployed allocations.
To allow users to make multiple iterations of the input model before deployment SUSE OpenStack Cloud will only persist data when the administrator confirms that they are about to deploy the results via the "ready-deployment" operation. To understand this better, consider the following example:
Imagine you have completed your SUSE OpenStack Cloud deployment with servers A, B, and C and you want to add two new compute nodes by adding servers D and E to the input model.
When you add these to the input model and re-run the configuration processor it will read the persisted data for A, B, and C and allocate D and E as new servers. The configuration processor now has allocation data for A, B, C, D, and E -- which it keeps in a staging area (actually a special branch in Git) until we get confirmation that the configuration processor has done what you intended and you are ready to deploy the revised configuration.
If you notice that the role of E is wrong and it became a swift node instead of a nova node you need to be able to change the input model and re-run the configuration processor. This is fine because the allocations of D and E have not been confirmed, and so the configuration processor will re-read the data about A, B, C and re-allocate D and E now to the correct clusters, updating the persisted data in the staging area.
You can loop though this as many times as needed. Each time, the
configuration processor is processing the deltas to what is deployed, not the
results of the previous run. When you are ready to use the results of the
configuration processor, you run ready-deployment.yml
which commits the data in the staging area into the persisted data. The next
run of the configuration processor will then start from the persisted data
for A, B, C, D, and E.
7.3.1 Persisted Server Allocations #
Server allocations are persisted by the administrator-defined server ID (see Section 6.5, “Servers”), and include the control plane, cluster/resource name, and ordinal within the cluster or resource group.
To guard against data loss, the configuration processor persists server allocations even when the server ID no longer exists in the input model -- for example, if a server was removed accidentally and the configuration processor allocated a new server to the same ordinal, then it would be very difficult to recover from that situation.
The following example illustrates the behavior:
A cloud is deployed with four servers with IDs of A, B, C, and D that can
all be used in a resource group with min-size=0 and
max-size=3. At the end of this deployment they persisted
state is as follows:
| ID | Control Plane | Resource Group | Ordinal | State | Deployed As |
|---|---|---|---|---|---|
| A | ccp | compute | 1 | Allocated | mycloud-ccp-comp0001 |
| B | ccp | compute | 2 | Allocated | mycloud-ccp-comp0002 |
| C | ccp | compute | 3 | Allocated | mycloud-ccp-comp0003 |
| D | Available |
(In this example server D has not been allocated because the group is at its max size, and there are no other groups that required this server)
If server B is removed from the input model and the configuration processor is re-run, the state is changed to:
| ID | Control Plane | Resource Group | Ordinal | State | Deployed As |
|---|---|---|---|---|---|
| A | ccp | compute | 1 | Allocated | mycloud-ccp-comp0001 |
| B | ccp | compute | 2 | Deleted | |
| C | ccp | compute | 3 | Allocated | mycloud-ccp-comp0003 |
| D | ccp | compute | 4 | Allocated | mycloud-ccp-comp0004 |
The details associated with server B are still retained, but the configuration processor will not generate any deployment data for this server. Server D has been added to the group to meet the minimum size requirement but has been given a different ordinal and hence will get different names and IP addresses than were given to server B.
If server B is added back into the input model the resulting state will be:
| ID | Control Plane | Resource Group | Ordinal | State | Deployed As |
|---|---|---|---|---|---|
| A | ccp | compute | 1 | Allocated | mycloud-ccp-comp0001 |
| B | ccp | compute | 2 | Deleted | |
| C | ccp | compute | 3 | Allocated | mycloud-ccp-comp0003 |
| D | ccp | compute | 4 | Allocated | mycloud-ccp-comp0004 |
The configuration processor will issue a warning that server B cannot be returned to the compute group because it would exceed the max-size constraint. However, because the configuration processor knows that server B is associated with this group it will not allocate it to any other group that could use it, since that might lead to data loss on that server.
If the max-size value of the group was increased, then server B would be
allocated back to the group, with its previous name and addresses
(mycloud-cp1-compute0002).
Note that the configuration processor relies on the server ID to identify a physical server. If the ID value of a server is changed the configuration processor will treat it as a new server. Conversely, if a different physical server is added with the same ID as a deleted server the configuration processor will assume that it is the original server being returned to the model.
You can force the removal of persisted data for servers that are no longer
in the input model by running the configuration processor with the
remove_deleted_servers option, like below:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml \ -e remove_deleted_servers="y"
7.3.2 Persisted Address Allocations #
The configuration processor persists IP address allocations by the generated name (see Section 7.2, “Name Generation” for how names are generated). As with servers. once an address has been allocated that address will remain allocated until the configuration processor is explicitly told that it is no longer required. The configuration processor will generate warnings for addresses that are persisted but no longer used.
You can remove persisted address allocations that are no longer used in the
input model by running the configuration processor with the
free_unused_addresses option, like below:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml \ -e free_unused_addresses="y"
7.4 Server Allocation #
The configuration processor allocates servers to a cluster or resource group in the following sequence:
Any that are persisted with a state of "allocated" are first returned to the or . Such servers are always allocated even if this contradicts the cluster size, failure-zones, or list of server roles since it is assumed that these servers are actively deployed.
If the or is still below its minimum size, then any that are persisted with a state of "deleted", but where the server is now listed in the input model (that is, the server was removed but is now back), are added to the group providing they meet the and criteria. If they do not meet the criteria then a warning is given and the remains in a deleted state (that is, it is still not allocated to any other cluster or group). These are not part of the current deployment, and so you must resolve any conflicts before they can be redeployed.
If the or is still below its minimum size, the configuration processor will allocate additional that meet the and criteria. If the allocation policy is set to "strict" then the failure zones of servers already in the cluster or resource group are not considered until an equal number of servers has been allocated from each zone.
7.5 Server Network Selection #
Once the configuration processor has allocated a to a or it uses the information in the associated to determine which need to be configured. It does this by:
Looking at the that are to run on the server (from the definition)
Looking to see which each of those components is attached to (from the definition)
Looking to see if there are any related to a running on this server, and if so, adding those to the list (also from the definition)
Looking to see if there are any that the says should be forced onto the server
It then searches the hierarchy (as described in Section 5.2.9.2, “Server Groups and Networks”) to find a in each of the it needs to attach to
If there is no available to a server, either because the does not include the required , or there is no from that group in the appropriate part of the hierarchy, then the configuration processor will generate an error.
The configuration processor will also generate an error if the address does not match any of the networks it will be connected to.
7.6 Network Route Validation #
Once the configuration processor has allocated all of the required and matched them to the appropriate , it validates that all have the required network routes to other .
It does this by using the data in the services section of the input model which provides details of which need to connect to each other. This data is not configurable by the administrator; however, it is provided as part of the SUSE OpenStack Cloud release.
For each , the configuration processor looks at the list of it runs and determines the network addresses of every other it needs to connect to (depending on the service, this might be a virtual IP address on a load balancer or a set of addresses for the service).
If the target address is on a that this is connected to, then there is no routing required. If the target address is on a different , then the Configuration Processor looks at each the server is connected to and looks at the routes defined in the corresponding . If the provides a route to the of the target address, then that route is considered valid.
within the same
are always considered as routed to each other;
from different must have an explicit entry
in the routes stanza of the
definition. Routes to a named
are always considered before a "default"
route.
A warning is given for any routes which are using the "default" route since it is possible that the user did not intend to route this traffic. Such warning can be removed by adding the appropriate to the list of routes.
The configuration processor provides details of all routes between networks
that it is expecting to be configured in the
info/route_info.yml file.
To illustrate how network routing is defined in the input model, consider the following example:
A compute server is configured to run nova-compute which requires access to
the neutron API servers and a block storage service. The neutron API
servers have a virtual IP address provided by a load balancer in the
INTERNAL-API network-group and the storage service is connected to the ISCSI
network-group. nova-compute itself is part of the set of components attached
by default to the MANAGEMENT network-group. The intention is to have virtual
machines on the compute server connect to the block storage via the ISCSI
network.
The physical network is shown below:
The corresponding entries in the are:
- name: INTERNAL-API
hostname-suffix: intapi
load-balancers:
- provider: ip-cluster
name: lb
components:
- default
roles:
- internal
- admin
- name: MANAGEMENT
hostname-suffix: mgmt
hostname: true
component-endpoints:
- default
routes:
- INTERNAL-API
- default
- name: ISCSI
hostname-suffix: iscsi
component-endpoints:
- storage serviceAnd the for the compute server looks like this:
- name: INTERFACE_SET_COMPUTE
network-interfaces:
- name: BOND0
device:
name: bond0
bond-data:
options:
mode: active-backup
miimon: 200
primary: hed5
provider: linux
devices:
- name: hed4
- name: hed5
network-groups:
- MANAGEMENT
- ISCSI
When validating the route from nova-compute to the neutron API, the
configuration processor will detect that the target address is on a network
in the INTERNAL-API network group, and that the MANAGEMENT network (which is
connected to the compute server) provides a route to this network, and thus
considers this route valid.
When validating the route from nova-compute to a storage service, the
configuration processor will detect that the target address is on a network
in the ISCSInetwork group. However, because there is no service component on
the compute server connected to the ISCSI network (according to the
network-group definition) the ISCSI network will not have been configured on
the compute server (see Section 7.5, “Server Network Selection”. The
configuration processor will detect that the MANAGEMENT network-group provides
a "default" route and thus considers the route as valid (it is, of course,
valid to route ISCSI traffic). However, because this is using the default
route, a warning will be issued:
# route-generator-2.0 WRN: Default routing used between networks
The following networks are using a 'default' route rule. To remove this warning
either add an explicit route in the source network group or force the network to
attach in the interface model used by the servers.
MANAGEMENT-NET-RACK1 to ISCSI-NET
ardana-ccp-comp0001
MANAGEMENT-NET-RACK 2 to ISCSI-NET
ardana-ccp-comp0002
MANAGEMENT-NET-RACK 3 to SCSI-NET
ardana-ccp-comp0003To remove this warning, you can either add ISCSI to the list of routes in the MANAGEMENT network group (routed ISCSI traffic is still a valid configuration) or force the compute server to attach to the ISCSI network-group by adding it as a forced-network-group in the interface-model, like this:
- name: INTERFACE_SET_COMPUTE
network-interfaces:
- name: BOND0
device:
name: bond0
bond-data:
options:
mode: active-backup
miimon: 200
primary: hed5
provider: linux
devices:
- name: hed4
- name: hed5
network-groups:
- MANAGEMENT
forced-network-groups:
- ISCSIWith the attachment to the ISCSI network group forced, the configuration processor will attach the compute server to a network in that group and validate the route as either being direct or between networks in the same network-group.
The generated route_info.yml file will include entries
such as the following, showing the routes that are still expected to be
configured between networks in the MANAGEMENT network group and the
INTERNAL-API network group.
MANAGEMENT-NET-RACK1:
INTERNAL-API-NET:
default: false
used_by:
nova-compute:
neutron-server:
- ardana-ccp-comp0001
MANAGEMENT-NET-RACK2:
INTERNAL-API-NET:
default: false
used_by:
nova-compute:
neutron-server:
- ardana-ccp-comp00037.7 Configuring neutron Provider VLANs #
neutron provider VLANs are networks that map directly to an 802.1Q VLAN in the cloud provider’s physical network infrastructure. There are four aspects to a provider VLAN configuration:
Network infrastructure configuration (for example, the top-of-rack switch)
Server networking configuration (for compute nodes and neutron network nodes)
neutron configuration file settings
Creation of the corresponding network objects in neutron
The physical network infrastructure must be configured to convey the provider VLAN traffic as tagged VLANs to the cloud compute nodes and neutron network nodes. Configuration of the physical network infrastructure is outside the scope of the SUSE OpenStack Cloud 9 software.
SUSE OpenStack Cloud 9 automates the server networking configuration and the neutron
configuration based on information in the cloud definition. To configure the
system for provider VLANs, specify the
neutron.networks.vlan tag with a
provider-physical-network attribute on one or more
as described in
Section 6.13.2, “Network Tags”. For example (some
attributes omitted for brevity):
network-groups:
- name: NET_GROUP_A
tags:
- neutron.networks.vlan:
provider-physical-network: physnet1
- name: NET_GROUP_B
tags:
- neutron.networks.vlan:
provider-physical-network: physnet2A is associated with a server network interface via an as described in Section 6.11, “Interface Models”. For example (some attributes omitted for brevity):
interface-models:
- name: INTERFACE_SET_X
network-interfaces:
- device:
name: bond0
network-groups:
- NET_GROUP_A
- device:
name: hed3
network-groups:
- NET_GROUP_B
A used for provider VLANs may contain only a
single SUSE OpenStack Cloud , because that VLAN must span all
compute nodes and any neutron network nodes/controllers (that is, it is a single
L2 segment). The SUSE OpenStack Cloud must be defined with
tagged-vlan: false, otherwise a Linux VLAN network
interface will be created. For example:
networks:
- name: NET_A
tagged-vlan: false
network-group: NET_GROUP_A
- name: NET_B
tagged-vlan: false
network-group: NET_GROUP_BWhen the cloud is deployed, SUSE OpenStack Cloud 9 will create the appropriate bridges on the servers, and set the appropriate attributes in the neutron configuration files (for example, bridge_mappings).
After the cloud has been deployed, create neutron network objects for each provider VLAN using the OpenStackClient CLI:
tux > sudo openstack network create --provider:network_type vlan \
--provider:physical_network PHYSNET1 --provider:segmentation_id 101 MYNET101tux > sudo openstack network create --provider:network_type vlan \
--provider:physical_network PHYSNET2 --provider:segmentation_id 234 MYNET2347.8 Standalone Cloud Lifecycle Manager #
All the example configurations use a “deployer-in-the-cloud”
scenario where the first controller is also the deployer/Cloud Lifecycle Manager. If you want
to use a standalone Cloud Lifecycle Manager, you need to add the relevant details in
control_plane.yml, servers.yml and
related configuration files. Detailed instructions are available at Section 12.1, “Using a Dedicated Cloud Lifecycle Manager Node”.
8 Configuration Processor Information Files #
In addition to producing all of the data needed to deploy and configure the cloud, the configuration processor also creates a number of information files that provide details of the resulting configuration.
These files can be found in ~/openstack/my_cloud/info
after the first configuration processor run. This directory is also rebuilt
each time the Configuration Processor is run.
Most of the files are in YAML format, allowing them to be used in further automation tasks if required.
| File | Provides details of |
|---|---|
address_info.yml
| IP address assignments on each network. See Section 8.1, “address_info.yml” |
firewall_info.yml
| All ports that are open on each network by the firewall configuration. Can be used if you want to configure an additional firewall in front of the API network, for example. See Section 8.2, “firewall_info.yml” |
route_info.yml
| Routes that need to be configured between networks. See Section 8.3, “route_info.yml” |
server_info.yml
| How servers have been allocated, including their network configuration. Allows details of a server to be found from its ID. See Section 8.4, “server_info.yml” |
service_info.yml
| Details of where components of each service are deployed. See Section 8.5, “service_info.yml” |
control_plane_topology.yml
| Details the structure of the cloud from the perspective of each control-plane. See Section 8.6, “control_plane_topology.yml” |
network_topology.yml
| Details the structure of the cloud from the perspective of each control-plane. See Section 8.7, “network_topology.yml” |
region_topology.yml
| Details the structure of the cloud from the perspective of each region. See Section 8.8, “region_topology.yml” |
service_topology.yml
| Details the structure of the cloud from the perspective of each service. See Section 8.9, “service_topology.yml” |
private_data_metadata_ccp.yml
| Details the secrets that are generated by the configuration processor – the names of the secrets, along with the service(s) that use each secret and a list of the clusters on which the service that consumes the secret is deployed. See Section 8.10, “private_data_metadata_ccp.yml” |
password_change.yml
|
Details the secrets that have been changed by the configuration
processor – information for each secret is the same as for
private_data_metadata_ccp.yml. See
Section 8.11, “password_change.yml”
|
explain.txt
| An explanation of the decisions the configuration processor has made when allocating servers and networks. See Section 8.12, “explain.txt” |
CloudDiagram.txt
| A pictorial representation of the cloud. See Section 8.13, “CloudDiagram.txt” |
The examples are taken from the entry-scale-kvm
example configuration.
8.1 address_info.yml #
This file provides details of all the IP addresses allocated by the Configuration Processor:
NETWORK GROUPS
LIST OF NETWORKS
IP ADDRESS
LIST OF ALIASESExample:
EXTERNAL-API:
EXTERNAL-API-NET:
10.0.1.2:
- ardana-cp1-c1-m1-extapi
10.0.1.3:
- ardana-cp1-c1-m2-extapi
10.0.1.4:
- ardana-cp1-c1-m3-extapi
10.0.1.5:
- ardana-cp1-vip-public-SWF-PRX-extapi
- ardana-cp1-vip-public-FRE-API-extapi
- ardana-cp1-vip-public-GLA-API-extapi
- ardana-cp1-vip-public-HEA-ACW-extapi
- ardana-cp1-vip-public-HEA-ACF-extapi
- ardana-cp1-vip-public-NEU-SVR-extapi
- ardana-cp1-vip-public-KEY-API-extapi
- ardana-cp1-vip-public-MON-API-extapi
- ardana-cp1-vip-public-HEA-API-extapi
- ardana-cp1-vip-public-NOV-API-extapi
- ardana-cp1-vip-public-CND-API-extapi
- ardana-cp1-vip-public-CEI-API-extapi
- ardana-cp1-vip-public-SHP-API-extapi
- ardana-cp1-vip-public-OPS-WEB-extapi
- ardana-cp1-vip-public-HZN-WEB-extapi
- ardana-cp1-vip-public-NOV-VNC-extapi
EXTERNAL-VM:
EXTERNAL-VM-NET: {}
GUEST:
GUEST-NET:
10.1.1.2:
- ardana-cp1-c1-m1-guest
10.1.1.3:
- ardana-cp1-c1-m2-guest
10.1.1.4:
- ardana-cp1-c1-m3-guest
10.1.1.5:
- ardana-cp1-comp0001-guest
MANAGEMENT:
...8.2 firewall_info.yml #
This file provides details of all the network ports that will be opened on the deployed cloud. Data is ordered by network. If you want to configure an external firewall in front of the External API network, then you would need to open the ports listed in that section.
NETWORK NAME
List of:
PORT
PROTOCOL
LIST OF IP ADDRESSES
LIST OF COMPONENTSExample:
EXTERNAL-API:
- addresses:
- 10.0.1.5
components:
- horizon
port: '443'
protocol: tcp
- addresses:
- 10.0.1.5
components:
- keystone-api
port: '5000'
protocol: tcpPort 443 (tcp) is open on network EXTERNAL-API for address 10.0.1.5 because it is used by horizon
Port 5000 (tcp) is open on network EXTERNAL-API for address 10.0.1.5 because it is used by keystone API
8.3 route_info.yml #
This file provides details of routes between networks that need to be configured. Available routes are defined in the input model as part of the data; this file shows which routes will actually be used. SUSE OpenStack Cloud will reconfigure routing rules on the servers, you must configure the corresponding routes within your physical network. Routes must be configured to be symmetrical -- only the direction in which a connection is initiated is captured in this file.
Note that simple models may not require any routes, with all servers being
attached to common L3 networks. The following example is taken from the
tech-preview/mid-scale-kvm example.
SOURCE-NETWORK-NAME
TARGET-NETWORK-NAME
default: TRUE IF THIS IS THIS THE RESULT OF A "DEFAULT" ROUTE RULE
used_by:
SOURCE-SERVICE
TARGET-SERVICE
LIST OF HOSTS USING THIS ROUTEExample:
MANAGEMENT-NET-RACK1:
INTERNAL-API-NET:
default: false
used_by:
- ardana-cp1-mtrmon-m1
keystone-api:
- ardana-cp1-mtrmon-m1
MANAGEMENT-NET-RACK2:
default: false
used_by:
cinder-backup:
rabbitmq:
- ardana-cp1-core-m1A route is required from network MANAGEMENT-NET-RACK1 to network MANAGEMENT-NET-RACK2 so that cinder-backup can connect to rabbitmq from server ardana-cp1-core-m1
8.4 server_info.yml #
This file provides details of how servers have been allocated by the
Configuration Processor. This provides the easiest way to find where a
specific physical server (identified by server-id) is
being used.
SERVER-ID
failure-zone: FAILURE ZONE THAT THE SERVER WAS ALLOCATED FROM
hostname: HOSTNAME OF THE SERVER
net_data: NETWORK CONFIGURATION
state: "allocated" | "available" Example:
controller1:
failure-zone: AZ1
hostname: ardana-cp1-c1-m1-mgmt
net_data:
BOND0:
EXTERNAL-API-NET:
addr: 10.0.1.2
tagged-vlan: true
vlan-id: 101
EXTERNAL-VM-NET:
addr: null
tagged-vlan: true
vlan-id: 102
GUEST-NET:
addr: 10.1.1.2
tagged-vlan: true
vlan-id: 103
MANAGEMENT-NET:
addr: 192.168.10.3
tagged-vlan: false
vlan-id: 100
state: allocated8.5 service_info.yml #
This file provides details of how services are distributed across the cloud.
CONTROL-PLANE
SERVICE
SERVICE COMPONENT
LIST OF HOSTSExample:
control-plane-1:
neutron:
neutron-client:
- ardana-cp1-c1-m1-mgmt
- ardana-cp1-c1-m2-mgmt
- ardana-cp1-c1-m3-mgmt
neutron-dhcp-agent:
- ardana-cp1-c1-m1-mgmt
- ardana-cp1-c1-m2-mgmt
- ardana-cp1-c1-m3-mgmt
neutron-l3-agent:
- ardana-cp1-comp0001-mgmt
...8.6 control_plane_topology.yml #
This file provides details of the topology of the cloud from the perspective of each control plane:
control_planes:
CONTROL-PLANE-NAME
load-balancers:
LOAD-BALANCER-NAME:
address: IP ADDRESS OF VIP
cert-file: NAME OF CERT FILE
external-name: NAME TO USED FOR ENDPOINTS
network: NAME OF THE NETWORK THIS LB IS CONNECTED TO
network_group: NAME OF THE NETWORK GROUP THIS LB IS CONNECT TO
provider: SERVICE COMPONENT PROVIDING THE LB
roles: LIST OF ROLES OF THIS LB
services:
SERVICE-NAME:
COMPONENT-NAME:
aliases:
ROLE: NAME IN /etc/hosts
host-tls: BOOLEAN, TRUE IF CONNECTION FROM LB USES TLS
hosts: LIST OF HOSTS FOR THIS SERVICE
port: PORT USED FOR THIS COMPONENT
vip-tls: BOOLEAN, TRUE IF THE VIP TERMINATES TLS
clusters:
CLUSTER-NAME
failure-zones:
FAILURE-ZONE-NAME:
LIST OF HOSTS
services:
SERVICE NAME:
components:
LIST OF SERVICE COMPONENTS
regions:
LIST OF REGION NAMES
resources:
RESOURCE-NAME:
AS FOR CLUSTERS ABOVEExample:
control_planes:
control-plane-1:
clusters:
cluster1:
failure_zones:
AZ1:
- ardana-cp1-c1-m1-mgmt
AZ2:
- ardana-cp1-c1-m2-mgmt
AZ3:
- ardana-cp1-c1-m3-mgmt
services:
barbican:
components:
- barbican-api
- barbican-worker
regions:
- region1
…
load-balancers:
extlb:
address: 10.0.1.5
cert-file: my-public-entry-scale-kvm-cert
external-name: ''
network: EXTERNAL-API-NET
network-group: EXTERNAL-API
provider: ip-cluster
roles:
- public
services:
barbican:
barbican-api:
aliases:
public: ardana-cp1-vip-public-KEYMGR-API-extapi
host-tls: true
hosts:
- ardana-cp1-c1-m1-mgmt
- ardana-cp1-c1-m2-mgmt
- ardana-cp1-c1-m3-mgmt
port: '9311'
vip-tls: true8.7 network_topology.yml #
This file provides details of the topology of the cloud from the perspective of each network_group:
network-groups:
NETWORK-GROUP-NAME:
NETWORK-NAME:
control-planes:
CONTROL-PLANE-NAME:
clusters:
CLUSTER-NAME:
servers:
ARDANA-SERVER-NAME: ip address
vips:
IP ADDRESS: load balancer name
resources:
RESOURCE-GROUP-NAME:
servers:
ARDANA-SERVER-NAME: ip addressExample:
network_groups:
EXTERNAL-API:
EXTERNAL-API-NET:
control_planes:
control-plane-1:
clusters:
cluster1:
servers:
ardana-cp1-c1-m1: 10.0.1.2
ardana-cp1-c1-m2: 10.0.1.3
ardana-cp1-c1-m3: 10.0.1.4
vips:
10.0.1.5: extlb
EXTERNAL-VM:
EXTERNAL-VM-NET:
control_planes:
control-plane-1:
clusters:
cluster1:
servers:
ardana-cp1-c1-m1: null
ardana-cp1-c1-m2: null
ardana-cp1-c1-m3: null
resources:
compute:
servers:
ardana-cp1-comp0001: null8.8 region_topology.yml #
This file provides details of the topology of the cloud from the perspective
of each region. In SUSE OpenStack Cloud, multiple regions are not supported. Only
Region0 is valid.
regions:
REGION-NAME:
control-planes:
CONTROL-PLANE-NAME:
services:
SERVICE-NAME:
LIST OF SERVICE COMPONENTSExample:
regions:
region0:
control-planes:
control-plane-1:
services:
barbican:
- barbican-api
- barbican-worker
ceilometer:
- ceilometer-common
- ceilometer-agent-notification
- ceilometer-polling
cinder:
- cinder-api
- cinder-volume
- cinder-scheduler
- cinder-backup8.9 service_topology.yml #
This file provides details of the topology of the cloud from the perspective of each service:
services:
SERVICE-NAME:
components:
COMPONENT-NAME:
control-planes:
CONTROL-PLANE-NAME:
clusters:
CLUSTER-NAME:
LIST OF SERVERS
resources:
RESOURCE-GROUP-NAME:
LIST OF SERVERS
regions:
LIST OF REGIONS8.10 private_data_metadata_ccp.yml #
This file provide details of the secrets that are generated by the configuration processor. The details include:
The names of each secret
Metadata about each secret. This is a list where each element contains details about each
componentservice that uses the secret.The
componentservice that uses the secret, and if applicable the service that this component "consumes" when using the secretThe list of clusters on which the
componentservice is deployedThe control plane
cpon which the services are deployed
A version number (the model version number)
SECRET
METADATA
LIST OF METADATA
CLUSTERS
LIST OF CLUSTERS
COMPONENT
CONSUMES
CONTROL-PLANE
VERSIONFor example:
barbican_admin_password:
metadata:
- clusters:
- cluster1
component: barbican-api
cp: ccp
version: '2.0'
keystone_swift_password:
metadata:
- clusters:
- cluster1
component: swift-proxy
consumes: keystone-api
cp: ccp
version: '2.0'
metadata_proxy_shared_secret:
metadata:
- clusters:
- cluster1
component: nova-metadata
cp: ccp
- clusters:
- cluster1
- compute
component: neutron-metadata-agent
cp: ccp
version: '2.0'
…8.11 password_change.yml #
This file provides details equivalent to those in private_data_metadata_ccp.yml for passwords which have been changed from their original values, using the procedure outlined in the SUSE OpenStack Cloud documentation
8.12 explain.txt #
This file provides details of the server allocation and network configuration decisions the configuration processor has made. The sequence of information recorded is:
Any service components that are automatically added
Allocation of servers to clusters and resource groups
Resolution of the network configuration for each server
Resolution of the network configuration of each load balancer
Example:
Add required services to control plane control-plane-1
======================================================
control-plane-1: Added nova-metadata required by nova-api
control-plane-1: Added swift-common required by swift-proxy
control-plane-1: Added swift-rsync required by swift-account
Allocate Servers for control plane control-plane-1
==================================================
cluster: cluster1
-----------------
Persisted allocation for server 'controller1' (AZ1)
Persisted allocation for server 'controller2' (AZ2)
Searching for server with role ['CONTROLLER-ROLE'] in zones: set(['AZ3'])
Allocated server 'controller3' (AZ3)
resource: compute
-----------------
Persisted allocation for server 'compute1' (AZ1)
Searching for server with role ['COMPUTE-ROLE'] in zones: set(['AZ1', 'AZ2', 'AZ3'])
Resolve Networks for Servers
============================
server: ardana-cp1-c1-m1
------------------------
add EXTERNAL-API for component ip-cluster
add MANAGEMENT for component ip-cluster
add MANAGEMENT for lifecycle-manager (default)
add MANAGEMENT for ntp-server (default)
...
add MANAGEMENT for swift-rsync (default)
add GUEST for tag neutron.networks.vxlan (neutron-openvswitch-agent)
add EXTERNAL-VM for tag neutron.l3_agent.external_network_bridge (neutron-vpn-agent)
Using persisted address 10.0.1.2 for server ardana-cp1-c1-m1 on network EXTERNAL-API-NET
Using address 192.168.10.3 for server ardana-cp1-c1-m1 on network MANAGEMENT-NET
Using persisted address 10.1.1.2 for server ardana-cp1-c1-m1 on network GUEST-NET
…
Define load balancers
=====================
Load balancer: extlb
--------------------
Using persisted address 10.0.1.5 for vip extlb ardana-cp1-vip-extlb-extapi on network EXTERNAL-API-NET
Add nova-api for roles ['public'] due to 'default'
Add glance-api for roles ['public'] due to 'default'
...
Map load balancers to providers
===============================
Network EXTERNAL-API-NET
------------------------
10.0.1.5: ip-cluster nova-api roles: ['public'] vip-port: 8774 host-port: 8774
10.0.1.5: ip-cluster glance-api roles: ['public'] vip-port: 9292 host-port: 9292
10.0.1.5: ip-cluster keystone-api roles: ['public'] vip-port: 5000 host-port: 5000
10.0.1.5: ip-cluster swift-proxy roles: ['public'] vip-port: 8080 host-port: 8080
10.0.1.5: ip-cluster monasca-api roles: ['public'] vip-port: 8070 host-port: 8070
10.0.1.5: ip-cluster heat-api-cfn roles: ['public'] vip-port: 8000 host-port: 8000
10.0.1.5: ip-cluster ops-console-web roles: ['public'] vip-port: 9095 host-port: 9095
10.0.1.5: ip-cluster heat-api roles: ['public'] vip-port: 8004 host-port: 8004
10.0.1.5: ip-cluster nova-novncproxy roles: ['public'] vip-port: 6080 host-port: 6080
10.0.1.5: ip-cluster neutron-server roles: ['public'] vip-port: 9696 host-port: 9696
10.0.1.5: ip-cluster heat-api-cloudwatch roles: ['public'] vip-port: 8003 host-port: 8003
10.0.1.5: ip-cluster horizon roles: ['public'] vip-port: 443 host-port: 80
10.0.1.5: ip-cluster cinder-api roles: ['public'] vip-port: 8776 host-port: 87768.13 CloudDiagram.txt #
This file provides a pictorial representation of the cloud. Although this file is still produced, it is superseded by the HTML output described in the following section.
8.14 HTML Representation #
An HTML representation of the cloud can be found in
~/openstack/my_cloud/html after the first Configuration
Processor run. This directory is also rebuilt each time the Configuration
Processor is run. These files combine the data in the input model with
allocation decisions made by the Configuration processor to allow the
configured cloud to be viewed from a number of different perspectives.
Most of the entries on the HTML pages provide either links to other parts of the HTML output or additional details via hover text.
9 Example Configurations #
The SUSE OpenStack Cloud 9 system ships with a collection of pre-qualified example configurations. These are designed to help you to get up and running quickly with a minimum number of configuration changes.
The SUSE OpenStack Cloud input model allows a wide variety of configuration parameters that can, at first glance, appear daunting. The example configurations are designed to simplify this process by providing pre-built and pre-qualified examples that need only a minimum number of modifications to get started.
9.1 SUSE OpenStack Cloud Example Configurations #
This section briefly describes the various example configurations and their capabilities. It also describes in detail, for the entry-scale-kvm example, how you can adapt the input model to work in your environment.
The following pre-qualified examples are shipped with SUSE OpenStack Cloud 9:
| Name | Location |
|---|---|
| Section 9.3.1, “Entry-Scale Cloud” |
~/openstack/examples/entry-scale-kvm
|
| Section 9.3.2, “Entry Scale Cloud with Metering and Monitoring Services” |
~/openstack/examples/entry-scale-kvm-mml
|
| Section 9.4.1, “Single-Region Entry-Scale Cloud with a Mix of KVM and ESX Hypervisors” | ~/openstack/examples/entry-scale-kvm-esx
|
| Section 9.4.2, “Single-Region Entry-Scale Cloud with Metering and Monitoring Services, and a Mix of KVM and ESX Hypervisors” |
~/openstack/examples/entry-scale-kvm-esx-mml
|
| Section 9.5.1, “Entry-scale swift Model” |
~/openstack/examples/entry-scale-swift
|
| Section 9.6.1, “Entry-Scale Cloud with Ironic Flat Network” |
~/openstack/examples/entry-scale-ironic-flat-network
|
| Section 9.6.2, “Entry-Scale Cloud with Ironic Multi-Tenancy” |
~/openstack/examples/entry-scale-ironic-multi-tenancy
|
| Section 9.3.3, “Single-Region Mid-Size Model” |
~/openstack/examples/mid-scale-kvm
|
The entry-scale systems are designed to provide an entry-level solution that can be scaled from a small number of nodes to a moderately high node count (approximately 100 compute nodes, for example).
In the mid-scale model, the cloud control plane is subdivided into a number of dedicated service clusters to provide more processing power for individual control plane elements. This enables a greater number of resources to be supported (compute nodes, swift object servers). This model also shows how a segmented network can be expressed in the SUSE OpenStack Cloud model.
9.2 Alternative Configurations #
In SUSE OpenStack Cloud 9 there are alternative configurations that we recommend for specific purposes and this section we will outline them.
The ironic multi-tenancy feature uses neutron to manage the tenant networks. The interaction between neutron and the physical switch is facilitated by neutron's Modular Layer 2 (ML2) plugin. The neutron ML2 plugin supports drivers to interact with various networks, as each vendor may have their own extensions. Those drivers are referred to as neutron ML2 mechanism drivers, or simply mechanism drivers.
The ironic multi-tenancy feature has been validated using OpenStack
genericswitch mechanism driver. However, if the given physical switch
requires a different mechanism driver, you must update the input model
accordingly. To update the input model with a custom ML2 mechanism driver,
specify the relevant information in the
multi_tenancy_switch_config: section of the
data/ironic/ironic_config.yml file.
9.3 KVM Examples #
9.3.1 Entry-Scale Cloud #
This example deploys an entry-scale cloud.
- Control Plane
Cluster1 3 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
Compute One node of type
COMPUTE-ROLEruns nova Compute and associated services.Object Storage Minimal swift resources are provided by the control plane.
Additional resource nodes can be added to the configuration.
- Networking
This example requires the following networks:
IPMI network connected to the lifecycle-manager and the IPMI ports of all servers.
Nodes require a pair of bonded NICs which are used by the following networks:
External API The network for making requests to the cloud.
External VM This network provides access to VMs via floating IP addresses.
Cloud Management This network is used for all internal traffic between the cloud services. It is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest The network that carries traffic between VMs on private networks within the cloud.
The
EXTERNAL APInetwork must be reachable from theEXTERNAL VMnetwork for VMs to be able to make API calls to the cloud.An example set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be edited to match your system.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB in capacity. In addition the example configures one additional disk depending on the role of the server:
Controllers
/dev/sdband/dev/sdcare configured to be used by swift.Compute Servers
/dev/sdbis configured as an additional Volume Group to be used for VM storage
Additional disks can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile
9.3.2 Entry Scale Cloud with Metering and Monitoring Services #
This example deploys an entry-scale cloud that provides metering and monitoring services and runs the database and messaging services in their own cluster.
- Control Plane
Cluster1 2 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.Cluster2 3 nodes of type
MTRMON-ROLE, run the OpenStack services for metering and monitoring (for example, ceilometer, monasca and Logging).Cluster3 3 nodes of type
DBMQ-ROLEthat run clustered database and RabbitMQ services to support the cloud infrastructure. 3 nodes are required for high availability.
- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
Compute 1 node of type
COMPUTE-ROLEruns nova Compute and associated services.Object Storage Minimal swift resources are provided by the control plane.
Additional resource nodes can be added to the configuration.
- Networking
This example requires the following networks:
IPMI network connected to the lifecycle-manager and the IPMI ports of all servers.
Nodes require a pair of bonded NICs which are used by the following networks:
External API The network for making requests to the cloud.
External VM The network that provides access to VMs via floating IP addresses.
Cloud Management This is the network that is used for all internal traffic between the cloud services. It is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest The network that carries traffic between VMs on private networks within the cloud.
The
EXTERNAL APInetwork must be reachable from theEXTERNAL VMnetwork for VMs to be able to make API calls to the cloud.An example set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be edited to match your system.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB of capacity. In addition, the example configures one additional disk depending on the role of the server:
Core Controllers
/dev/sdband/dev/sdcis configured to be used by swift.DBMQ Controllers
/dev/sdbis configured as an additional Volume Group to be used by the database and RabbitMQ.Compute Servers
/dev/sdbis configured as an additional Volume Group to be used for VM storage.
Additional disks can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile.
9.3.3 Single-Region Mid-Size Model #
The mid-size model is intended as a template for a moderate sized cloud. The Control plane is made up of multiple server clusters to provide sufficient computational, network and IOPS capacity for a mid-size production style cloud.
- Control Plane
Core Cluster runs core OpenStack Services, such as keystone, nova API, glance API, neutron API, horizon, and heat API. Default configuration is two nodes of role type
CORE-ROLE.Metering and Monitoring Cluster runs the OpenStack Services for metering and monitoring (for example, ceilometer, monasca and logging). Default configuration is three nodes of role type
MTRMON-ROLE.Database and Message Queue Cluster runs clustered MariaDB and RabbitMQ services to support the Ardana cloud infrastructure. Default configuration is three nodes of role type
DBMQ-ROLE. Three nodes are required for high availability.swift PAC Cluster runs the swift Proxy, Account and Container services. Default configuration is three nodes of role type
SWPAC-ROLE.neutron Agent Cluster Runs neutron VPN (L3), DHCP, Metadata and OpenVswitch agents. Default configuration is two nodes of role type
NEUTRON-ROLE.
- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
Compute runs nova Compute and associated services. Runs on nodes of role type
COMPUTE-ROLE. This model lists 3 nodes. 1 node is the minimum requirement.Object Storage 3 nodes of type
SOWBJ-ROLErun the swift Object service. The minimum node count should match your swift replica count.
The minimum node count required to run this model unmodified is 19 nodes. This can be reduced by consolidating services on the control plane clusters.
- Networking
This example requires the following networks:
IPMI network connected to the lifecycle-manager and the IPMI ports of all servers.
Nodes require a pair of bonded NICs which are used by the following networks:
External API The network for making requests to the cloud.
Internal API This network is used within the cloud for API access between services.
External VM This network provides access to VMs via floating IP addresses.
Cloud Management This network is used for all internal traffic between the cloud services. It is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest The network that carries traffic between VMs on private networks within the cloud.
SWIFT This network is used for internal swift communications between the swift nodes.
The
EXTERNAL APInetwork must be reachable from theEXTERNAL VMnetwork for VMs to be able to make API calls to the cloud.An example set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be edited to match your system.
9.3.3.1 Adapting the Mid-Size Model to Fit Your Environment #
The minimum set of changes you need to make to adapt the model for your environment are:
Update
servers.ymlto list the details of your baremetal servers.Update the
networks.ymlfile to replace network CIDRs and VLANs with site specific values.Update the
nic_mappings.ymlfile to ensure that network devices are mapped to the correct physical port(s).Review the disk models (
disks_*.yml) and confirm that the associated servers have the number of disks required by the disk model. The device names in the disk models might need to be adjusted to match the probe order of your servers. The default number of disks for the swift nodes (3 disks) is set low on purpose to facilitate deployment on generic hardware. For production scale swift the servers should have more disks. For example, 6 on SWPAC nodes and 12 on SWOBJ nodes. If you allocate more swift disks then you should review the ring power in the swift ring configuration. This is documented in the swift section. Disk models are provided as follows:DISK SET CONTROLLER: Minimum 1 disk
DISK SET DBMQ: Minimum 3 disks
DISK SET COMPUTE: Minimum 2 disks
DISK SET SWPAC: Minimum 3 disks
DISK SET SWOBJ: Minimum 3 disks
Update the
netinterfaces.ymlfile to match the server NICs used in your configuration. This file has a separate interface model definition for each of the following:INTERFACE SET CONTROLLER
INTERFACE SET DBMQ
INTERFACE SET SWPAC
INTERFACE SET SWOBJ
INTERFACE SET COMPUTE
9.4 ESX Examples #
9.4.1 Single-Region Entry-Scale Cloud with a Mix of KVM and ESX Hypervisors #
This example deploys a cloud which mixes KVM and ESX hypervisors.
- Control Plane
Cluster1 3 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
Compute:
KVM runs nova Computes and associated services. It runs on nodes of role type
COMPUTE-ROLE.ESX provides ESX Compute services. OS and software on this node is installed by user.
- ESX Resource Requirements
User needs to supply vSphere server
User needs to deploy the ovsvapp network resources using the vSphere GUI (Section 27.8.2, “Creating ESXi MGMT DVS and Required Portgroup”) by running the
neutron-create-ovsvapp-resources.ymlplaybook (Section 27.8.3, “Configuring OVSvApp Network Resources Using Ansible-Playbook”) or via Python-Networking-vSphere (Section 27.8.4, “Configuring OVSVAPP Using Python-Networking-vSphere”)The following DVS and DVPGs need to be created and configured for each cluster in each ESX hypervisor that will host an OvsVapp appliance. The settings for each DVS and DVPG are specific to your system and network policies. A JSON file example is provided in the documentation, but it needs to be edited to match your requirements.
DVS Port Groups assigned to DVS MGMT MGMT-PG, ESX-CONF-PG, GUEST-PG TRUNK TRUNK-PG User needs to deploy ovsvapp appliance (
OVSVAPP-ROLE) and nova-proxy appliance (ESX-COMPUTE-ROLE)User needs to add required information related to compute proxy and OVSvApp Nodes
- Networking
This example requires the following networks:
IPMInetwork connected to the lifecycle-manager and the IPMI ports of all nodes, except the ESX hypervisors.
Nodes require a pair of bonded NICs which are used by the following networks:
External API The network for making requests to the cloud.
External VM The network that provides access to VMs via floating IP addresses.
Cloud Management The network used for all internal traffic between the cloud services. It is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest This network carries traffic between VMs on private networks within the cloud.
SES This is the network that control-plane and compute-node clients use to talk to the external SUSE Enterprise Storage.
TRUNK is the network that is used to apply security group rules on tenant traffic. It is managed by the cloud admin and is restricted to the vCenter environment.
ESX-CONF-NET network is used only to configure the ESX compute nodes in the cloud. This network should be different from the network used with PXE to stand up the cloud control-plane.
This example's set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be edited to match your system.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB in capacity. In addition, the example configures additional disk depending on the node's role:
Controllers
/dev/sdband/dev/sdcare configured to be used by swiftCompute Servers
/dev/sdbis configured as an additional Volume Group to be used for VM storage
Additional disks can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile.
9.4.2 Single-Region Entry-Scale Cloud with Metering and Monitoring Services, and a Mix of KVM and ESX Hypervisors #
This example deploys a cloud which mixes KVM and ESX hypervisors, provides metering and monitoring services, and runs the database and messaging services in their own cluster.
- Control Plane
Cluster1 2 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.Cluster2 3 nodes of type
MTRMON-ROLE, run the OpenStack services for metering and monitoring (for example, ceilometer, monasca and Logging).Cluster3 3 nodes of type
DBMQ-ROLE, run clustered database and RabbitMQ services to support the cloud infrastructure. 3 nodes are required for high availability.
- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
Compute:
KVM runs nova Computes and associated services. It runs on nodes of role type
COMPUTE-ROLE.ESX provides ESX Compute services. OS and software on this node is installed by user.
- ESX Resource Requirements
User needs to supply vSphere server
User needs to deploy the ovsvapp network resources using the vSphere GUI or by running the
neutron-create-ovsvapp-resources.ymlplaybookThe following DVS and DVPGs need to be created and configured for each cluster in each ESX hypervisor that will host an OvsVapp appliance. The settings for each DVS and DVPG are specific to your system and network policies. A JSON file example is provided in the documentation, but it needs to be edited to match your requirements.
ESX-CONF (DVS and DVPG) connected to ovsvapp eth0 and compute-proxy eth0
MANAGEMENT (DVS and DVPG) connected to ovsvapp eth1, eth2, eth3 and compute-proxy eth1
User needs to deploy ovsvapp appliance (
OVSVAPP-ROLE) and nova-proxy appliance (ESX-COMPUTE-ROLE)User needs to add required information related to compute proxy and OVSvApp Nodes
- Networking
This example requires the following networks:
IPMInetwork connected to the lifecycle-manager and the IPMI ports of all nodes, except the ESX hypervisors.
Nodes require a pair of bonded NICs which are used by the following networks:
External API The network for making requests to the cloud.
External VM The network that provides access to VMs (via floating IP addresses).
Cloud Management This network is used for all internal traffic between the cloud services. It is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest This is the network that will carry traffic between VMs on private networks within the cloud.
TRUNK is the network that will be used to apply security group rules on tenant traffic. It is managed by the cloud admin and is restricted to the vCenter environment.
ESX-CONF-NET network is used only to configure the ESX compute nodes in the cloud. This network should be different from the network used with PXE to stand up the cloud control-plane.
This example's set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be edited to match your system.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB in capacity. In addition, the example configures additional disk depending on the node's role:
Controllers
/dev/sdband/dev/sdcare configured to be used by swift.Compute Servers
/dev/sdbis configured as an additional Volume Group to be used for VM storage
Additional disks can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile
9.5 Swift Examples #
9.5.1 Entry-scale swift Model #
This example shows how SUSE OpenStack Cloud can be configured to provide a swift-only configuration, consisting of three controllers and one or more swift object servers.
The example requires the following networks:
External API - The network for making requests to the cloud.
swift - The network for all data traffic between the swift services.
Management - This network that is used for all internal traffic between the cloud services, including node provisioning. This network must be on an untagged VLAN.
All of these networks are configured to be presented via a pair of bonded NICs. The example also enables provider VLANs to be configured in neutron on this interface.
In the diagram "External Routing" refers to whatever routing you want to provide to allow users to access the External API. "Internal Routing" refers to whatever routing you want to provide to allow administrators to access the Management network.
If you are using SUSE OpenStack Cloud to install the operating system, then an IPMI network connected to the IPMI ports of all servers and routable from the Cloud Lifecycle Manager is also required for BIOS and power management of the node during the operating system installation process.
In the example the controllers use one disk for the operating system and two disks for swift proxy and account storage. The swift object servers use one disk for the operating system and four disks for swift storage. These values can be modified to suit your environment.
These recommended minimums are based on the included with the base installation and are suitable only for demo environments. For production systems you will want to consider your capacity and performance requirements when making decisions about your hardware.
The entry-scale-swift example runs the swift proxy,
account and container services on the three controller servers. However, it
is possible to extend the model to include the swift proxy, account and
container services on dedicated servers (typically referred to as the swift
proxy servers). If you are using this model, we have included the recommended
swift proxy servers specs in the table below.
| Node Type | Role Name | Required Number | Server Hardware - Minimum Requirements and Recommendations | |||
|---|---|---|---|---|---|---|
| Disk | Memory | Network | CPU | |||
| Dedicated Cloud Lifecycle Manager (optional) | Lifecycle-manager | 1 | 300 GB | 8 GB | 1 x 10 Gbit/s with PXE Support | 8 CPU (64-bit) cores total (Intel x86_64) |
| Control Plane | Controller | 3 |
| 64 GB | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| swift Object | swobj | 3 |
If using x3 replication only:
If using Erasure Codes only or a mix of x3 replication and Erasure Codes:
| 32 GB (see considerations at bottom of page for more details) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
| swift Proxy, Account, and Container | swpac | 3 | 2 x 600 GB (minimum, see considerations at bottom of page for more details) | 64 GB (see considerations at bottom of page for more details) | 2 x 10 Gbit/s with one PXE enabled port | 8 CPU (64-bit) cores total (Intel x86_64) |
The disk speeds (RPM) chosen should be consistent within the same ring or storage policy. It is best to not use disks with mixed disk speeds within the same swift ring.
Considerations for your swift object and proxy, account, container servers RAM and disk capacity needs
swift can have a diverse number of hardware configurations. For example, a swift object server may have just a few disks (minimum of 6 for erasure codes) or up to 70 and beyond. The memory requirement needs to be increased as more disks are added. The general rule of thumb for memory needed is 0.5 GB per TB of storage. For example, a system with 24 hard drives at 8TB each, giving a total capacity of 192TB, should use 96GB of RAM. However, this does not work well for a system with a small number of small hard drives or a very large number of very large drives. So, if after calculating the memory given this guideline, if the answer is less than 32GB then go with 32GB of memory minimum and if the answer is over 256GB then use 256GB maximum, no need to use more memory than that.
When considering the capacity needs for the swift proxy, account, and container (PAC) servers, you should calculate 2% of the total raw storage size of your object servers to specify the storage required for the PAC servers. So, for example, if you were using the example we provided earlier and you had an object server setup of 24 hard drives with 8TB each for a total of 192TB and you had a total of 6 object servers, that would give a raw total of 1152TB. So you would take 2% of that, which is 23TB, and ensure that much storage capacity was available on your swift proxy, account, and container (PAC) server cluster. If you had a cluster of three swift PAC servers, that would be ~8TB each.
Another general rule of thumb is that if you are expecting to have more than a million objects in a container then you should consider using SSDs on the swift PAC servers rather than HDDs.
9.6 Ironic Examples #
9.6.1 Entry-Scale Cloud with Ironic Flat Network #
This example deploys an entry scale cloud that uses the ironic service to provision physical machines through the Compute services API.
- Control Plane
Cluster1 3 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
ironic Compute One node of type
IRONIC-COMPUTE-ROLEruns nova-compute, nova-compute-ironic, and other supporting services.Object Storage Minimal swift resources are provided by the control plane.
- Networking
This example requires the following networks:
IPMI network connected to the lifecycle-manager and the IPMI ports of all servers.
Nodes require a pair of bonded NICs which are used by the following networks:
External API This is the network that users will use to make requests to the cloud.
Cloud Management This is the network that will be used for all internal traffic between the cloud services. This network is also used to install and configure the nodes. The network needs to be on an untagged VLAN.
Guest This is the flat network that will carry traffic between bare metal instances within the cloud. It is also used to PXE boot said bare metal instances and install the operating system selected by tenants.
The
EXTERNAL APInetwork must be reachable from theGUESTnetwork for the bare metal instances to make API calls to the cloud.An example set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses the devices
hed3andhed4as a bonded network interface for all services. The name given to a network interface by the system is configured in the filedata/net_interfaces.yml. That file needs to be modified to match your system.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB in capacity. In addition the example configures one additional disk depending on the role of the server:
Controllers
/dev/sdband/dev/sdcconfigured to be used by swift.
Additional discs can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile.
9.6.2 Entry-Scale Cloud with Ironic Multi-Tenancy #
This example deploys an entry scale cloud that uses the ironic service to provision physical machines through the Compute services API and supports multi tenancy.
- Control Plane
Cluster1 3 nodes of type
CONTROLLER-ROLErun the core OpenStack services, such as keystone, nova API, glance API, neutron API, horizon, and heat API.- Cloud Lifecycle Manager
The Cloud Lifecycle Manager runs on one of the control-plane nodes of type
CONTROLLER-ROLE. The IP address of the node that will run the Cloud Lifecycle Manager needs to be included in thedata/servers.ymlfile.- Resource Nodes
ironic Compute One node of type
IRONIC-COMPUTE-ROLEruns nova-compute, nova-compute-ironic, and other supporting services.Object Storage Minimal swift Resources are provided by the control plane.
- Networking
This example requires the following networks:
IPMI network connected to the deployer and the IPMI ports of all nodes.
External API network is used to make requests to the cloud.
Cloud Management This is the network that will be used for all internal traffic between the cloud services. This network is also used to install and configure the controller nodes. The network needs to be on an untagged VLAN.
Provisioning is the network used to PXE boot the ironic nodes and install the operating system selected by tenants. This network needs to be tagged on the switch for control plane/ironic compute nodes. For ironic bare metal nodes, VLAN configuration on the switch will be set by neutron driver.
Tenant VLANs The range of VLAN IDs should be reserved for use by ironic and set in the cloud configuration. It is configured as untagged on control plane nodes, therefore it cannot be combined with management network on the same network interface.
The following access should be allowed by routing/firewall:
Access from Management network to IPMI. Used during cloud installation and during ironic bare metal node provisioning.
Access from Management network to switch management network. Used by neutron driver.
The
EXTERNAL APInetwork must be reachable from the tenant networks if you want bare metal nodes to be able to make API calls to the cloud.
An example set of networks is defined in
data/networks.yml. The file needs to be modified to reflect your environment.The example uses
hed3for Management and External API traffic, andhed4for provisioning and tenant network traffic. If you need to modify these assignments for your environment, they are defined indata/net_interfaces.yml.- Local Storage
All servers should present a single OS disk, protected by a RAID controller. This disk needs to be at least 512 GB in capacity. In addition the example configures one additional disk depending on the role of the server:
Controllers
/dev/sdband/dev/sdcconfigured to be used by swift.
Additional disks can be configured for any of these roles by editing the corresponding
data/disks_*.ymlfile.
10 Modifying Example Configurations for Compute Nodes #
This section contains detailed information about the Compute Node parts of the input model. For example input models, see Chapter 9, Example Configurations. For general descriptions of the input model, see Section 6.14, “Networks”.
Usually, the example models provide most of the data that is required to create a valid input model. However, before you start to deploy, you may want to customize an input model using the following information about Compute Nodes.
10.1 SLES Compute Nodes #
net_interfaces.yml- name: SLES-COMPUTE-INTERFACES network-interfaces: - name: BOND0 device: name: bond0 bond-data: options: mode: active-backup miimon: 200 primary: hed1 provider: linux devices: - name: hed1 - name: hed2 network-groups: - EXTERNAL-VM - GUEST - MANAGEMENTservers.yml- id: compute1 ip-addr: 10.13.111.15 role: SLES-COMPUTE-ROLE server-group: RACK1 nic-mapping: DL360p_G8_2Port mac-addr: ec:b1:d7:77:d0:b0 ilo-ip: 10.12.13.14 ilo-password: ********* ilo-user: Administrator distro-id: sles12sp4-x86_64server_roles.yml- name: SLES-COMPUTE-ROLE interface-model: SLES-COMPUTE-INTERFACES disk-model: SLES-COMPUTE-DISKS
disk_compute.yml- name: SLES-COMPUTE-DISKS volume-groups: - name: ardana-vg physical-volumes: - /dev/sda_root logical-volumes: # The policy is not to consume 100% of the space of each volume group. # 5% should be left free for snapshots and to allow for some flexibility. - name: root size: 35% fstype: ext4 mount: / - name: log size: 50% mount: /var/log fstype: ext4 mkfs-opts: -O large_file - name: crash size: 10% mount: /var/crash fstype: ext4 mkfs-opts: -O large_file - name: vg-comp # this VG is dedicated to nova Compute to keep VM IOPS off the OS disk physical-volumes: - /dev/sdb logical-volumes: - name: compute size: 95% mount: /var/lib/nova fstype: ext4 mkfs-opts: -O large_filecontrol_plane.ymlcontrol-planes: - name: control-plane-1 control-plane-prefix: cp1 region-name: region0 .... resources: - name: sles-compute resource-prefix: sles-comp server-role: SLES-COMPUTE-ROLE allocation-policy: any min-count: 1 service-components: - ntp-client - nova-compute - nova-compute-kvm - neutron-l3-agent - neutron-metadata-agent - neutron-openvswitch-agent
11 Modifying Example Configurations for Object Storage using Swift #
This section contains detailed descriptions about the swift-specific parts of
the input model. For example input models, see
Chapter 9, Example Configurations. For general descriptions of the
input model, see Section 6.14, “Networks”. In addition, the swift
ring specifications are available in the
~/openstack/my_cloud/definition/data/swift/swift_config.yml
file.
Usually, the example models provide most of the data that is required to create a valid input model. However, before you start to deploy, you must do the following:
Check the disk model used by your nodes and that all disk drives are correctly named and used as described in Section 11.6, “Swift Requirements for Device Group Drives”.
Select an appropriate partition power for your rings. For more information, see Section 11.10, “Understanding Swift Ring Specifications”.
For further information, read these related pages:
11.1 Object Storage using swift Overview #
11.1.1 What is the Object Storage (swift) Service? #
The SUSE OpenStack Cloud Object Storage using swift service leverages swift which uses software-defined storage (SDS) layered on top of industry-standard servers using native storage devices. swift presents an object paradigm, using an underlying set of disk drives. The disk drives are managed by a data structure called a "ring" and you can store, retrieve, and delete objects in containers using RESTful APIs.
SUSE OpenStack Cloud Object Storage using swift provides a highly-available, resilient, and scalable storage pool for unstructured data. It has a highly-durable architecture, with no single point of failure. In addition, SUSE OpenStack Cloud includes the concept of cloud models, where the user can modify the cloud input model to provide the configuration required for their environment.
11.1.2 Object Storage (swift) Services #
A swift system consists of a number of services:
swift-proxy provides the API for all requests to the swift system.
Account and container services provide storage management of the accounts and containers.
Object services provide storage management for object storage.
These services can be co-located in a number of ways. The following general pattern exists in the example cloud models distributed in SUSE OpenStack Cloud:
The swift-proxy, account, container, and object services run on the same (PACO) node type in the control plane. This is used for smaller clouds or where swift is a minor element in a larger cloud. This is the model seen in most of the entry-scale models.
The swift-proxy, account, and container services run on one (PAC) node type in a cluster in a control plane and the object services run on another (OBJ) node type in a resource pool. This deployment model, known as the Entry-Scale swift model, is used in larger clouds or where a larger swift system is in use or planned. See Section 9.5.1, “Entry-scale swift Model” for more details.
The swift storage service can be scaled both vertically (nodes with larger or more disks) and horizontally (more swift storage nodes) to handle an increased number of simultaneous user connections and provide larger storage space.
swift is configured through a number of YAML files in the SUSE OpenStack Cloud implementation of the OpenStack Object Storage (swift) service. For more details on the configuration of the YAML files, see Chapter 11, Modifying Example Configurations for Object Storage using Swift.
11.2 Allocating Proxy, Account, and Container (PAC) Servers for Object Storage #
A swift proxy, account, and container (PAC) server is a node that runs the swift-proxy, swift-account and swift-container services. It is used to respond to API requests and to store account and container data. The PAC node does not store object data.
This section describes the procedure to allocate PAC servers during the initial deployment of the system.
11.2.1 To Allocate Swift PAC Servers #
Perform the following steps to allocate PAC servers:
Verify if the example input model already contains a suitable server role. The server roles are usually described in the
data/server_roles.ymlfile. If the server role is not described, you must add a suitable server role and allocate drives to store object data. For instructions, see Section 11.4, “Creating Roles for swift Nodes” and Section 11.5, “Allocating Disk Drives for Object Storage”.Verify if the example input model has assigned a cluster to swift proxy, account, container servers. It is usually mentioned in the
data/control_plane.ymlfile. If the cluster is not assigned, then add a suitable cluster. For instructions, see Section 11.7, “Creating a Swift Proxy, Account, and Container (PAC) Cluster”.Identify the physical servers and their IP address and other detailed information.
You add these details to the servers list (usually in the
data/servers.ymlfile).As with all servers, you must also verify and/or modify the server-groups information (usually in
data/server_groups.yml)
The only part of this process that is unique to swift is the allocation of disk drives for use by the account and container rings. For instructions, see Section 11.5, “Allocating Disk Drives for Object Storage”.
11.3 Allocating Object Servers #
A swift object server is a node that runs the swift-object service (only) and is used to store object data. It does not run the swift-proxy, swift-account, or swift-container services.
This section describes the procedure to allocate a swift object server during the initial deployment of the system.
11.3.1 To Allocate a Swift Object Server #
Perform the following steps to allocate one or more swift object servers:
Verify if the example input model already contains a suitable server role. The server roles are usually described in the
data/server_roles.ymlfile. If the server role is not described, you must add a suitable server role. For instructions, see Section 11.4, “Creating Roles for swift Nodes”. While adding a server role for the swift object server, you will also allocate drives to store object data. For instructions, see Section 11.5, “Allocating Disk Drives for Object Storage”.Verify if the example input model has a resource node assigned to swift object servers. The resource nodes are usually assigned in the
data/control_plane.ymlfile. If it is not assigned, you must add a suitable resource node. For instructions, see Section 11.8, “Creating Object Server Resource Nodes”.Identify the physical servers and their IP address and other detailed information. Add the details for the servers in either of the following YAML files and verify the server-groups information:
Add details in the servers list (usually in the
data/servers.ymlfile).As with all servers, you must also verify and/or modify the server-groups information (usually in the
data/server_groups.ymlfile).
The only part of this process that is unique to swift is the allocation of disk drives for use by the object ring. For instructions, see Section 11.5, “Allocating Disk Drives for Object Storage”.
11.4 Creating Roles for swift Nodes #
To create roles for swift nodes, you must edit the
data/server_roles.yml file and add an entry to the
server-roles list using the following syntax:
server-roles: - name: PICK-A-NAME interface-model: SPECIFY-A-NAME disk-model: SPECIFY-A-NAME
The fields for server roles are defined as follows:
name
| Specifies a name assigned for the role. In the following example, SWOBJ-ROLE is the role name. |
interface-model
| You can either select an existing interface model or create one specifically for swift object servers. In the following example SWOBJ-INTERFACES is used. For more information, see Section 11.9, “Understanding Swift Network and Service Requirements”. |
disk-model
| You can either select an existing model or create one specifically for swift object servers. In the following example SWOBJ-DISKS is used. For more information, see Section 11.5, “Allocating Disk Drives for Object Storage”. |
server-roles: - name: SWOBJ-ROLE interface-model: SWOBJ-INTERFACES disk-model: SWOBJ-DISKS
11.5 Allocating Disk Drives for Object Storage #
The disk model describes the configuration of disk drives and their usage. The examples include several disk models. You must always review the disk devices before making any changes to the existing the disk model.
11.5.1 Making Changes to a Swift Disk Model #
There are several reasons for changing the disk model:
If you have additional drives available, you can add them to the devices list.
If the disk devices listed in the example disk model have different names on your servers. This may be due to different hardware drives. Edit the disk model and change the device names to the correct names.
If you prefer a different disk drive than the one listed in the model. For example, if
/dev/sdband/dev/sdcare slow hard drives and you have SDD drives available in/dev/sddand/dev/sde. In this case, delete/dev/sdband/dev/sdcand replace them with/dev/sddand/dev/sde.NoteDisk drives must not contain labels or file systems from a prior usage. For more information, see Section 11.6, “Swift Requirements for Device Group Drives”.
TipThe terms add and delete in the document means editing the respective YAML files to add or delete the configurations/values.
Swift Consumer Syntax#
The consumer field determines the usage of a disk drive or logical volume by swift. The syntax of the consumer field is as follows:
consumer:
name: swift
attrs:
rings:
- name: RING-NAME
- name: RING-NAME
- etc...The fields for consumer are defined as follows:
name
|
Specifies the service that uses the device group. A
name field containing
swift indicates that the drives or
logical volumes are used by swift.
|
attrs
|
Lists the rings that the devices are allocated to. It must contain a
rings item.
|
rings
|
Contains a list of ring names. In the rings list,
the name field is optional.
|
The following are the different configurations (patterns) of the proxy, account, container, and object services:
Proxy, account, container, and object (PACO) run on same node type.
Proxy, account, and container run on a node type (PAC) and the object services run on a dedicated object server (OBJ).
The proxy service does not have any rings associated with it.
consumer:
name: swift
attrs:
rings:
- name: account
- name: container
- name: object-0consumer:
name: swift
attrs:
rings:
- name: account
- name: containerThe following example shows two Storage Policies (object-0 and object-1). For more information, see Section 11.11, “Designing Storage Policies”.
consumer:
name: swift
attrs:
rings:
- name: object-0
- name: object-1Swift Device Groups#
You may have several device groups if you have several different uses for different sets of drives.
The following example shows a configuration where one drive is used for account and container rings and the other drives are used by the object-0 ring:
device-groups:
- name: swiftpac
devices:
- name: /dev/sdb
consumer:
name: swift
attrs:
- name: account
- name: container
- name: swiftobj
devices:
- name: /dev/sdc
- name: /dev/sde
- name: /dev/sdf
consumer:
name: swift
attrs:
rings:
- name: object-0Swift Logical Volumes#
Be careful while using logical volumes to store swift data. The data remains intact during an upgrade, but will be lost if the server is reimaged. If you use logical volumes you must ensure that you only reimage one server at a time. This is to allow the data from the other replicas to be replicated back to the logical volume once the reimage is complete.
swift can use a logical volume. To do this, ensure you meet the requirements listed in the table below:
| Do not specify these attributes. |
| Specify both of these attributes. |
|
This attribute must have a name field set to
swift.
|
When setting up swift as a logical volume, the configuration processor will give a warning. This warning is normal and does not affect the configuration.
Following is an example of swift logical volumes:
...
- name: swift
size: 50%
consumer:
name: swift
attrs:
rings:
- name: object-0
- name: object-111.6 Swift Requirements for Device Group Drives #
To install and deploy, swift requires that the disk drives listed in the devices list of the device-groups item in a disk model meet the following criteria (if not, the deployment will fail):
The disk device must exist on the server. For example, if you add
/dev/sdXto a server with only three devices, then the deploy process will fail.The disk device must be unpartitioned or have a single partition that uses the whole drive.
The partition must not be labeled.
The XFS file system must not contain a file system label.
If the disk drive is already labeled as described above, the
swiftlm-drive-provisionprocess will assume that the drive has valuable data and will not use or modify the drive.
11.7 Creating a Swift Proxy, Account, and Container (PAC) Cluster #
If you already have a cluster with the server-role
SWPAC-ROLE there is no need to proceed through these
steps.
11.7.1 Steps to Create a swift Proxy, Account, and Container (PAC) Cluster #
To create a cluster for swift proxy, account, and container (PAC) servers, you must identify the control plane and node type/role:
In the
~/openstack/my_cloud/definition/data/control_plane.ymlfile, identify the control plane that the PAC servers are associated with.Next, identify the node type/role used by the swift PAC servers. In the following example,
server-roleis set to SWPAC-ROLE.Add an entry to the
clustersitem in thecontrol-planesection.Example:
control-planes: - name: control-plane-1 control-plane-prefix: cp1 . . . clusters: . . . - name: swpac cluster-prefix: swpac server-role: SWPAC-ROLE member-count: 3 allocation-policy: strict service-components: - ntp-client - swift-ring-builder - swift-proxy - swift-account - swift-container - swift-clientImportantDo not change the name of the cluster
swpacto ensure that it remains unique among clusters. Use names for its servers such asswpac1,swpac2, andswpac3.If you have more than three servers available that have the
SWPAC-ROLEassigned to them, you must changemember-countto match the number of servers.For example, if you have four servers with a role of
SWPAC-ROLE, then themember-countshould be 4.
11.7.2 Service Components #
A swift PAC server requires the following service components:
ntp-client
swift-proxy
swift-account
swift-container
swift-ring-builder
swift-client
11.8 Creating Object Server Resource Nodes #
To create a resource node for swift object servers, you must identify the control plane and node type/role:
In the
data/control_plane.ymlfile, identify the control plane that the object servers are associated with.Next, identify the node type/role used by the swift object servers. In the following example,
server-roleis set to SWOBJ-ROLE:Add an entry to the
resourcesitem in the control-plane:control-planes: - name: control-plane-1 control-plane-prefix: cp1 region-name: region1 . . . resources: . . . - name: swobj resource-prefix: swobj server-role: SWOBJ-ROLE allocation-policy: strict min-count: 0 service-components: - ntp-client - swift-object
Service Components
A swift object server requires the following service components:
ntp-clientswift-objectswift-clientis optional; installs thepython-swiftclientpackage on the server.
Resource nodes do not have a member count attribute. So the number of servers
allocated with the SWOBJ-ROLE is the number
of servers in the data/servers.yml file with a server role
of SWOBJ-ROLE.
11.9 Understanding Swift Network and Service Requirements #
This topic describes swift’s requirements for which service components must exist in the input model and how these relate to the network model. This information is useful if you are creating a cluster or resource node, or when defining the networks used by swift. The network model allows many options and configurations. For smooth swift operation, the following must be true:
The following services must have a direct connection to the same network:
swift-proxyswift-accountswift-containerswift-objectswift-ring-builder
The
swift-proxyservice must have a direct connection to the same network as thecluster-ipservice.The memcached service must be configured on a cluster of the control plane. In small deployments, it is convenient to run it on the same cluster as the horizon service. For larger deployments, with many nodes running the
swift-proxyservice, it is better to co-locate theswift-proxyandmemcachedservices. Theswift-proxyandswift-containerservices must have a direct connection to the same network as thememcachedservice.The
swift-proxyandswift-ring-builderservice must be co-located in the same cluster of the control plane.The
ntp-clientservice must be present on all swift nodes.
11.10 Understanding Swift Ring Specifications #
In swift, the ring is responsible for mapping data on particular disks. There
is a separate ring for account databases, container databases, and each
object storage policy, but each ring works similarly. The
swift-ring-builder utility is used to build and manage
rings. This utility uses a builder file to contain ring information and
additional data required to build future rings. In SUSE OpenStack Cloud 9, you will
use the cloud model to specify how the rings are configured and used. This
model is used to automatically invoke the
swift-ring-builder utility as part of the deploy process.
(Normally, you will not run the swift-ring-builder utility
directly.)
The rings are specified in the input model using the
configuration-data key. The
configuration-data in the
control-planes definition is given a name that you will
then use in the swift_config.yml file. If you have several
control planes hosting swift services, the ring specifications can use a
shared configuration-data object, however it is considered
best practice to give each swift instance its own
configuration-data object.
11.10.1 Ring Specifications in the Input Model #
In most models, the ring-specification is mentioned in the
~/openstack/my_cloud/definition/data/swift/swift_config.yml
file. For example:
configuration-data:
- name: SWIFT-CONFIG-CP1
services:
- swift
data:
control_plane_rings:
swift-zones:
- id: 1
server-groups:
- AZ1
- id: 2
server-groups:
- AZ2
- id: 3
server-groups:
- AZ3
rings:
- name: account
display-name: Account Ring
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
- name: container
display-name: Container Ring
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
- name: object-0
display-name: General
default: yes
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
The above sample file shows that the rings are specified using the
configuration-data object
SWIFT-CONFIG-CP1 and has three
rings as follows:
Account ring: You must always specify a ring called account. The account ring is used by swift to store metadata about the projects in your system. In swift, a keystone project maps to a swift account. The
display-nameis informational and not used.Container ring:You must always specify a ring called container. The
display-nameis informational and not used.Object ring: This ring is also known as a storage policy. You must always specify a ring called object-0. It is possible to have multiple object rings, which is known as storage policies. The
display-nameis the name of the storage policy and can be used by users of the swift system when they create containers. It allows them to specify the storage policy that the container uses. In the example, the storage policy is called General. There are also two aliases for the storage policy name:GeneralPolicyandAnotherAliasForGeneral. In this example, you can useGeneral,GeneralPolicy, orAnotherAliasForGeneralto refer to this storage policy. The aliases item is optional. Thedisplay-nameis required.Min-part-hours, partition-power, replication-policy and replica-count are described in the following section.
11.10.2 Replication Ring Parameters #
The ring parameters for traditional replication rings are defined as follows:
| Parameter | Description |
|---|---|
replica-count
|
Defines the number of copies of object created.
Use this to control the degree of resiliency or availability. The
|
min-part-hours
|
Changes the value used to decide when a given partition can be moved.
This is the number of hours that the
In the example above, the
A value of
In prior releases, this parameter was called
|
partition-power
| The optimal value for this parameter is related to the number of disk drives that
you allocate to swift storage. As a best practice, you should use the same drives for
both the account and container rings. In this case, the
partition-power value should be the same. For more information,
see Section 11.10.4, “Selecting a Partition Power”. |
replication-policy
| Specifies that a ring uses replicated storage. The duplicate copies of the object are created and stored on different disk drives. All replicas are identical. If one is lost or corrupted, the system automatically copies one of the remaining replicas to restore the missing replica. |
default
| The default value in the above sample file of ring-specification is set to yes, which means that the storage policy is enabled to store objects. For more information, see Section 11.11, “Designing Storage Policies”. |
11.10.3 Erasure Coded Rings #
In the cloud model, a ring-specification is mentioned in
the ~/openstack/my_cloud/definition/data/swift/swift_config.yml
file. A typical erasure coded ring in this file looks like this:
- name: object-1
display-name: EC_ring
default: no
min-part-hours: 16
partition-power: 12
erasure-coding-policy:
ec-type: jerasure_rs_vand
ec-num-data-fragments: 10
ec-num-parity-fragments: 4
ec-object-segment-size: 1048576The additional parameters are defined as follows:
| Parameter | Description |
|---|---|
| ec-type |
This is the particular erasure policy scheme that is being used. The supported ec_types in SUSE OpenStack Cloud 9 are:
|
| erasure-coding-policy | This line indicates that the object ring will be of type "erasure coding" |
| ec-num-data-fragments | This indicated the number of data fragments for an object in the ring. |
| ec-num-parity-fragments | This indicated the number of parity fragments for an object in the ring. |
| ec-object-segment-size | The amount of data that will be buffered up before feeding a segment into the encoder/decoder. The default value is 1048576. |
When using an erasure coded ring, the number of devices in the ring must be greater than or equal to the total number of fragments of an object. For example, if you define an erasure coded ring with 10 data fragments and 4 parity fragments, there must be at least 14 (10+4) devices added to the ring.
When using erasure codes, for a PUT object to be successful it must store
ec_ndata + 1 fragment to achieve quorum. Where the number
of data fragments (ec_ndata) is 10 then at least 11
fragments must be saved for the object PUT to be successful. The 11
fragments must be saved to different drives. To tolerate a single object
server going down, say in a system with 3 object servers, each object server
must have at least 6 drives assigned to the erasure coded storage policy. So
with a single object server down, 12 drives are available between the
remaining object servers. This allows an object PUT to save 12 fragments,
one more than the minimum to achieve quorum.
Unlike replication rings, none of the erasure coded parameters may be edited after the initial creation. Otherwise there is potential for permanent loss of access to the data.
On the face of it, you would expect that an erasure coded configuration that uses a data to parity ratio of 10:4, that the data consumed storing the object is 1.4 times the size of the object just like the x3 replication takes x3 times the size of the data when storing the object. However, for erasure coding, this 10:4 ratio is not correct. The efficiency (that is how much storage is needed to store the object) is very poor for small objects and improves as the object size grows. However, the improvement is not linear. If all of your files are less than 32K in size, erasure coding will take more space to store than the x3 replication.
11.10.4 Selecting a Partition Power #
When storing an object, the object storage system hashes the name. This hash results in a hit on a partition (so a number of different object names result in the same partition number). Generally, the partition is mapped to available disk drives. With a replica count of 3, each partition is mapped to three different disk drives. The hashing algorithm used hashes over a fixed number of partitions. The partition-power attribute determines the number of partitions you have.
Partition power is used to distribute the data uniformly across drives in a swift nodes. It also defines the storage cluster capacity. You must set the partition power value based on the total amount of storage you expect your entire ring to use.
You should select a partition power for a given ring that is appropriate to the number of disk drives you allocate to the ring for the following reasons:
If you use a high partition power and have a few disk drives, each disk drive will have thousands of partitions. With too many partitions, audit and other processes in the Object Storage system cannot walk the partitions in a reasonable time and updates will not occur in a timely manner.
If you use a low partition power and have many disk drives, you will have tens (or maybe only one) partition on a drive. The Object Storage system does not use size when hashing to a partition - it hashes the name.
With many partitions on a drive, a large partition is cancelled out by a smaller partition so the overall drive usage is similar. However, with very small numbers of partitions, the uneven distribution of sizes can be reflected in uneven disk drive usage (so one drive becomes full while a neighboring drive is empty).
An ideal number of partitions per drive is 100. If you know the number of drives, select a partition power that will give you approximately 100 partitions per drive. Usually, you install a system with a specific number of drives and add drives as needed. However, you cannot change the value of the partition power. Hence you must select a value that is a compromise between current and planned capacity.
If you are installing a small capacity system and you need to grow to a very large capacity but you cannot fit within any of the ranges in the table, please seek help from Sales Engineering to plan your system.
There are additional factors that can help mitigate the fixed nature of the partition power:
Account and container storage represents a small fraction (typically 1 percent) of your object storage needs. Hence, you can select a smaller partition power (relative to object ring partition power) for the account and container rings.
For object storage, you can add additional storage policies (that is, another object ring). When you have reached capacity in an existing storage policy, you can add a new storage policy with a higher partition power (because you now have more disk drives in your system). This means that you can install your system using a small partition power appropriate to a small number of initial disk drives. Later, when you have many disk drives, the new storage policy can have a higher value appropriate to the larger number of drives.
However, when you continue to add storage capacity, existing containers will continue to use their original storage policy. Hence, the additional objects must be added to new containers to take advantage of the new storage policy.
Use the following table to select an appropriate partition power for each ring. The partition power of a ring cannot be changed, so it is important to select an appropriate value. This table is based on a replica count of 3. If your replica count is different, or you are unable to find your system in the table, then see Section 11.10.4, “Selecting a Partition Power” for information of selecting a partition power.
The table assumes that when you first deploy swift, you have a small number of drives (the minimum column in the table), and later you add drives.
Use the total number of drives. For example, if you have three servers, each with two drives, the total number of drives is six.
The lookup should be done separately for each of the account, container and object rings. Since account and containers represent approximately 1 to 2 percent of object storage, you will probably use fewer drives for the account and container rings (that is, you will have fewer proxy, account, and container (PAC) servers) so that your object rings may have a higher partition power.
The largest anticipated number of drives imposes a limit in the minimum drives you can have. (For more information, see Section 11.10.4, “Selecting a Partition Power”.) This means that, if you anticipate significant growth, your initial system can be small, but under a certain limit. For example, if you determine that the maximum number of drives the system will grow to is 40,000, then use a partition power of 17 as listed in the table below. In addition, a minimum of 36 drives is required to build the smallest system with this partition power.
The table assumes that disk drives are the same size. The actual size of a drive is not significant.
11.11 Designing Storage Policies #
Storage policies enable you to differentiate the way objects are stored.
Reasons to use storage policies include the following:
Different types or classes of disk drive
You can use different drives to store various type of data. For example, you can use 7.5K RPM high-capacity drives for one type of data and fast SSD drives for another type of data.
Different redundancy or availability needs
You can define the redundancy and availability based on your requirement. You can use a replica count of 3 for "normal" data and a replica count of 4 for "critical" data.
Growing of cluster capacity
If the storage cluster capacity grows beyond the recommended partition power as described in Section 11.10, “Understanding Swift Ring Specifications”.
Erasure-coded storage and replicated storage
If you use erasure-coded storage for some objects and replicated storage for other objects.
Storage policies are implemented on a per-container basis. If you want a non-default storage policy to be used for a new container, you can explicitly specify the storage policy to use when you create the container. You can change which storage policy is the default. However, this does not affect existing containers. Once the storage policy of a container is set, the policy for that container cannot be changed.
The disk drives used by storage policies can overlap or be distinct. If the storage policies overlap (that is, have disks in common between two storage policies), it is recommended to use the same set of disk drives for both policies. But in the case where there is a partial overlap in disk drives, because one storage policy receives many objects, the drives that are common to both policies must store more objects than drives that are only allocated to one storage policy. This can be appropriate for a situation where the overlapped disk drives are larger than the non-overlapped drives.
11.11.1 Specifying Storage Policies #
There are two places where storage policies are specified in the input model:
The attribute of the storage policy is specified in ring-specification in the
data/swift/swift_config.ymlfile.When associating disk drives with specific rings in a disk model. This specifies which drives and nodes use the storage policy. In other word words, where data associated with a storage policy is stored.
A storage policy is specified similar to other rings. However, the following features are unique to storage policies:
Storage policies are applicable to object rings only. The account or container rings cannot have storage policies.
There is a format for the ring name: object-index, where index is a number in the range 0 to 9 (in this release). For example: object-0.
The object-0 ring must always be specified.
Once a storage policy is deployed, it should never be deleted. You can remove all disk drives for the storage policy, however the ring specification itself cannot be deleted.
You can use the
display-nameattribute when creating a container to indicate which storage policy you want to use for that container.One of the storage policies can be the default policy. If you do not specify the storage policy then the object created in new container uses the default storage policy.
If you change the default, only containers created later will have that changed default policy.
The following example shows three storage policies in use. Note that the third storage policy example is an erasure coded ring.
rings:
. . .
- name: object-0
display-name: General
default: no
min-part-hours: 16
partition-power: 12
replication-policy:
replica-count: 3
- name: object-1
display-name: Data
default: yes
min-part-hours: 16
partition-power: 20
replication-policy:
replica-count: 3
- name: object-2
display-name: Archive
default: no
min-part-hours: 16
partition-power: 20
erasure-coded-policy:
ec-type: jerasure_rs_vand
ec-num-data-fragments: 10
ec-num-parity-fragments: 4
ec-object-segment-size: 104857611.12 Designing Swift Zones #
The concept of swift zones allows you to control the placement of replicas on different groups of servers. When constructing rings and allocating replicas to specific disk drives, swift will, where possible, allocate replicas using the following hierarchy so that the greatest amount of resiliency is achieved by avoiding single points of failure:
swift will place each replica on a different disk drive within the same server.
swift will place each replica on a different server.
swift will place each replica in a different swift zone.
If you have three servers and a replica count of three, it is easy for swift to place each replica on a different server. If you only have two servers though, swift will place two replicas on one server (different drives on the server) and one copy on the other server.
With only three servers there is no need to use the swift zone concept. However, if you have more servers than your replica count, the swift zone concept can be used to control the degree of resiliency. The following table shows how data is placed and explains what happens under various failure scenarios. In all cases, a replica count of three is assumed and that there are a total of six servers.
| Number of swift Zones | Replica Placement | Failure Scenarios | Details |
|---|---|---|---|
| One (all servers in the same zone) | Replicas are placed on different servers. For any given object, you have no control over which servers the replicas are placed on. | One server fails | You are guaranteed that there are two other replicas. |
| Two servers fail | You are guaranteed that there is one remaining replica. | ||
| Three servers fail | 1/3 of the objects cannot be accessed. 2/3 of the objects have three replicas. | ||
| Two (three servers in each swift zone) | Half the objects have two replicas in swift zone 1 with one replica in swift zone The other objects are reversed, with one replica in swift zone 1 and two replicas in swift zone 2. | One swift zone fails | You are guaranteed to have at least one replica. Half the objects have two remaining replicas and the other half have a single replica. |
| Three (two servers in each swift zone) | Each zone contains a replica. For any given object, there is a replica in each swift zone. | One swift zone fails | You are guaranteed to have two replicas of every object. |
| Two swift zones fail | You are guaranteed to have one replica of every object. |
The following sections show examples of how to specify the swift zones in your input model.
11.12.1 Using Server Groups to Specify swift Zones #
swift zones are specified in the ring specifications using the server group concept. To define a swift zone, you specify:
An id - this is the swift zone number
A list of associated server groups
Server groups are defined in your input model. The example input models typically define a number of server groups. You can use these pre-defined server groups or create your own.
For example, the following three models use the example server groups
CLOUD, AZ1, AZ2 and
AZ3. Each of these examples achieves the same effect –
creating a single swift zone.
ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- CLOUD
rings:
…ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- AZ1
- AZ2
- AZ3
rings:
…server-groups:
- name: ZONE_ONE
server-groups:
- AZ1
- AZ2
- AZ3
ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- ZONE_ONE
rings:
…
Alternatively, if you omit the swift-zones specification,
a single swift zone is used by default for all servers.
In the following example, three swift zones are specified and mapped to the same availability zones that nova uses (assuming you are using one of the example input models):
ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- AZ1
- id: 2
server-groups:
- AZ2
- id: 3
server-groups:
- AZ3In this example, it shows a datacenter with four availability zones which are mapped to two swift zones. This type of setup may be used if you had two buildings where each building has a duplicated network infrastructure:
ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- AZ1
- AZ2
- id: 2
server-groups:
- AZ3
- AZ411.12.2 Specifying Swift Zones at Ring Level #
Usually, you would use the same swift zone layout for all rings in your system. However, it is possible to specify a different layout for a given ring. The following example shows that the account, container and object-0 rings have two zones, but the object-1 ring has a single zone.
ring-specifications:
- region: region1
swift-zones:
- id: 1
server-groups:
- AZ1
- id: 2
server-groups:
- AZ2
rings
- name: account
…
- name: container
…
- name: object-0
…
- name: object-1
swift-zones:
- id: 1
server-groups:
- CLOUD
…11.13 Customizing Swift Service Configuration Files #
SUSE OpenStack Cloud 9 enables you to modify various swift service configuration
files. The following swift service configuration files are located on the
Cloud Lifecycle Manager in the ~/openstack/my_cloud/config/swift/ directory:
account-server.conf.j2container-reconciler.conf.j2container-server.conf.j2container-sync-realms.conf.j2object-expirer.conf.j2object-server.conf.j2proxy-server.conf.j2rsyncd.conf.j2swift.conf.j2swift-recon.j2
There are many configuration options that can be set or changed, including container rate limit and logging level:
11.13.1 Configuring Swift Container Rate Limit #
The swift container rate limit allows you to limit the number of
PUT and DELETE requests of an object
based on the number of objects in a container. For example, suppose the
container_ratelimit_x = r . It means that for containers
of size x, limit requests per second to
r.
To enable container rate limiting:
Log in to the Cloud Lifecycle Manager.
Edit the
DEFAULTsection of~/openstack/my_cloud/config/swift/proxy-server.conf.j2:container_ratelimit_0 = 100 container_ratelimit_1000000 = 100 container_ratelimit_5000000 = 50
This will set the
PUTandDELETEobject rate limit to 100 requests per second for containers with up to 1,000,000 objects. Also, thePUTandDELETErate for containers with between 1,000,000 and 5,000,000 objects will vary linearly from between 100 and 50 requests per second as the container object count increases.Commit your changes to git:
ardana >cd ~/openstack/ardana/ansibleardana >git commit -m "COMMIT_MESSAGE" \ ~/openstack/my_cloud/config/swift/proxy-server.conf.j2Run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun the
swift-reconfigure.ymlplaybook to reconfigure the swift servers:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts swift-reconfigure.yml
11.13.2 Configuring swift Account Server Logging Level #
By default the swift logging level is set to INFO. As a
best practice, do not set the log level to DEBUG for a long period of time.
Use it for troubleshooting issues and then change it back to INFO.
Perform the following steps to set the logging level of the
account-server to DEBUG:
Log in to the Cloud Lifecycle Manager.
Edit the
DEFAULTsection of~/openstack/my_cloud/config/swift/account-server.conf.j2:[DEFAULT] . . log_level = DEBUG
Commit your changes to git:
ardana >cd ~/openstack/ardana/ansibleardana >git commit -m "COMMIT_MESSAGE" \ ~/openstack/my_cloud/config/swift/account-server.conf.j2Run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun the
swift-reconfigure.ymlplaybook to reconfigure the swift servers:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts swift-reconfigure.yml
11.13.3 For More Information #
For more information, see:
Book “Operations Guide CLM”, Chapter 13 “Managing Monitoring, Logging, and Usage Reporting”, Section 13.2 “Centralized Logging Service”, Section 13.2.5 “Configuring Centralized Logging”
Book “Operations Guide CLM”, Chapter 13 “Managing Monitoring, Logging, and Usage Reporting”, Section 13.2 “Centralized Logging Service”
12 Alternative Configurations #
In SUSE OpenStack Cloud 9 there are alternative configurations that we recommend for specific purposes.
12.1 Using a Dedicated Cloud Lifecycle Manager Node #
All of the example configurations included host the Cloud Lifecycle Manager on the first Control Node. It is also possible to deploy this service on a dedicated node. One use case for wanting to run the dedicated Cloud Lifecycle Manager is to be able to test the deployment of different configurations without having to re-install the first server. Some administrators prefer the additional security of keeping all of the configuration data on a separate server from those that users of the cloud connect to (although all of the data can be encrypted and SSH keys can be password protected).
Here is a graphical representation of this setup:
12.1.1 Specifying a dedicated Cloud Lifecycle Manager in your input model #
To specify a dedicated Cloud Lifecycle Manager in your input model, make the following edits to your configuration files.
The indentation of each of the input files is important and will cause errors if not done correctly. Use the existing content in each of these files as a reference when adding additional content for your Cloud Lifecycle Manager.
Update
control_plane.ymlto add the Cloud Lifecycle Manager.Update
server_roles.ymlto add the Cloud Lifecycle Manager role.Update
net_interfaces.ymlto add the interface definition for the Cloud Lifecycle Manager.Create a
disks_lifecycle_manager.ymlfile to define the disk layout for the Cloud Lifecycle Manager.Update
servers.ymlto add the dedicated Cloud Lifecycle Manager node.
Control_plane.yml: The snippet below shows the addition
of a single node cluster into the control plane to host the Cloud Lifecycle Manager service.
Note that, in addition to adding the new cluster, you also have to remove
the Cloud Lifecycle Manager component from the cluster1 in the examples:
clusters:
- name: cluster0
cluster-prefix: c0
server-role: LIFECYCLE-MANAGER-ROLE
member-count: 1
allocation-policy: strict
service-components:
- lifecycle-manager
- ntp-client
- name: cluster1
cluster-prefix: c1
server-role: CONTROLLER-ROLE
member-count: 3
allocation-policy: strict
service-components:
- lifecycle-manager
- ntp-server
- tempest
This specifies a single node of role
LIFECYCLE-MANAGER-ROLE hosting the Cloud Lifecycle Manager.
Server_roles.yml: The snippet below shows the insertion
of the new server roles definition:
server-roles:
- name: LIFECYCLE-MANAGER-ROLE
interface-model: LIFECYCLE-MANAGER-INTERFACES
disk-model: LIFECYCLE-MANAGER-DISKS
- name: CONTROLLER-ROLEThis defines a new server role which references a new interface-model and disk-model to be used when configuring the server.
net-interfaces.yml: The snippet below shows the
insertion of the network-interface info:
- name: LIFECYCLE-MANAGER-INTERFACES
network-interfaces:
- name: BOND0
device:
name: bond0
bond-data:
options:
mode: active-backup
miimon: 200
primary: hed3
provider: linux
devices:
- name: hed3
- name: hed4
network-groups:
- MANAGEMENTThis assumes that the server uses the same physical networking layout as the other servers in the example.
disks_lifecycle_manager.yml: In the examples,
disk-models are provided as separate files (this is just a convention, not a
limitation) so the following should be added as a new file named
disks_lifecycle_manager.yml:
---
product:
version: 2
disk-models:
- name: LIFECYCLE-MANAGER-DISKS
# Disk model to be used for Cloud Lifecycle Managers nodes
# /dev/sda_root is used as a volume group for /, /var/log and /var/crash
# sda_root is a templated value to align with whatever partition is really used
# This value is checked in os config and replaced by the partition actually used
# on sda e.g. sda1 or sda5
volume-groups:
- name: ardana-vg
physical-volumes:
- /dev/sda_root
logical-volumes:
# The policy is not to consume 100% of the space of each volume group.
# 5% should be left free for snapshots and to allow for some flexibility.
- name: root
size: 80%
fstype: ext4
mount: /
- name: crash
size: 15%
mount: /var/crash
fstype: ext4
mkfs-opts: -O large_file
consumer:
name: os
Servers.yml: The snippet below shows the insertion of an
additional server used for hosting the Cloud Lifecycle Manager. Provide the address
information here for the server you are running on, that is, the node where
you have installed the SUSE OpenStack Cloud ISO.
servers:
# NOTE: Addresses of servers need to be changed to match your environment.
#
# Add additional servers as required
#Lifecycle-manager
- id: lifecycle-manager
ip-addr: YOUR IP ADDRESS HERE
role: LIFECYCLE-MANAGER-ROLE
server-group: RACK1
nic-mapping: HP-SL230-4PORT
mac-addr: 8c:dc:d4:b5:c9:e0
# ipmi information is not needed
# Controllers
- id: controller1
ip-addr: 192.168.10.3
role: CONTROLLER-ROLEWith a stand-alone deployer, the OpenStack CLI and other clients will not be installed automatically. You need to install OpenStack clients to get the desired OpenStack capabilities. For more information and installation instructions, consult Chapter 40, Installing OpenStack Clients.
12.2 Configuring SUSE OpenStack Cloud without DVR #
By default in the KVM model, the neutron service utilizes distributed routing (DVR). This is the recommended setup because it allows for high availability. However, if you would like to disable this feature, here are the steps to achieve this.
On your Cloud Lifecycle Manager, make the following changes:
In the
~/openstack/my_cloud/config/neutron/neutron.conf.j2file, change the line below from:router_distributed = {{ router_distributed }}to:
router_distributed = False
In the
~/openstack/my_cloud/config/neutron/ml2_conf.ini.j2file, change the line below from:enable_distributed_routing = {{ enable_distributed_routing }}to:
enable_distributed_routing = False
In the
~/openstack/my_cloud/config/neutron/l3_agent.ini.j2file, change the line below from:agent_mode = {{ neutron_l3_agent_mode }}to:
agent_mode = legacy
In the
~/openstack/my_cloud/definition/data/control_plane.ymlfile, remove the following values from the Compute resourceservice-componentslist:- neutron-l3-agent - neutron-metadata-agent
WarningIf you fail to remove the above values from the Compute resource service-components list from file
~/openstack/my_cloud/definition/data/control_plane.yml, you will end up with routers (non_DVR routers) being deployed in the compute host, even though the lifecycle manager is configured for non_distributed routers.Commit your changes to your local git repository:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"Run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlRun the ready deployment playbook:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlContinue installation. More information on cloud deployments are available in the Chapter 19, Overview
12.3 Configuring SUSE OpenStack Cloud with Provider VLANs and Physical Routers Only #
Another option for configuring neutron is to use provider VLANs and physical routers only, here are the steps to achieve this.
On your Cloud Lifecycle Manager, make the following changes:
In the
~/openstack/my_cloud/config/neutron/neutron.conf.j2file, change the line below from:router_distributed = {{ router_distributed }}to:
router_distributed = False
In the
~/openstack/my_cloud/config/neutron/ml2_conf.ini.j2file, change the line below from:enable_distributed_routing = {{ enable_distributed_routing }}to:
enable_distributed_routing = False
In the
~/openstack/my_cloud/config/neutron/dhcp_agent.ini.j2file, change the line below from:enable_isolated_metadata = {{ neutron_enable_isolated_metadata }}to:
enable_isolated_metadata = True
In the
~/openstack/my_cloud/definition/data/control_plane.ymlfile, remove the following values from the Compute resourceservice-componentslist:- neutron-l3-agent - neutron-metadata-agent
12.4 Considerations When Installing Two Systems on One Subnet #
If you wish to install two separate SUSE OpenStack Cloud 9 systems using a single subnet, you will need to consider the following notes.
The ip_cluster service includes the
keepalived daemon which maintains virtual IPs (VIPs) on
cluster nodes. In order to maintain VIPs, it communicates between cluster
nodes over the VRRP protocol.
A VRRP virtual routerid identifies a particular VRRP cluster and must be
unique for a subnet. If you have two VRRP clusters with the same virtual
routerid, causing a clash of VRRP traffic, the VIPs are unlikely to be up or
pingable and you are likely to get the following signature in your
/etc/keepalived/keepalived.log:
Dec 16 15:43:43 ardana-cp1-c1-m1-mgmt Keepalived_vrrp[2218]: ip address associated with VRID not present in received packet : 10.2.1.11 Dec 16 15:43:43 ardana-cp1-c1-m1-mgmt Keepalived_vrrp[2218]: one or more VIP associated with VRID mismatch actual MASTER advert Dec 16 15:43:43 ardana-cp1-c1-m1-mgmt Keepalived_vrrp[2218]: bogus VRRP packet received on br-bond0 !!! Dec 16 15:43:43 ardana-cp1-c1-m1-mgmt Keepalived_vrrp[2218]: VRRP_Instance(VI_2) ignoring received advertisment...
To resolve this issue, our recommendation is to install your separate SUSE OpenStack Cloud 9 systems with VRRP traffic on different subnets.
If this is not possible, you may also assign a unique routerid to your
separate SUSE OpenStack Cloud 9 system by changing the
keepalived_vrrp_offset service configurable. The routerid
is currently derived using the keepalived_vrrp_index which
comes from a configuration processor variable and the
keepalived_vrrp_offset.
For example,
Log in to your Cloud Lifecycle Manager.
Edit your
~/openstack/my_cloud/config/keepalived/defaults.ymlfile and change the value of the following line:keepalived_vrrp_offset: 0
Change the off value to a number that uniquely identifies a separate vrrp cluster. For example:
keepalived_vrrp_offset: 0for the 1st vrrp cluster on this subnet.keepalived_vrrp_offset: 1for the 2nd vrrp cluster on this subnet.keepalived_vrrp_offset: 2for the 3rd vrrp cluster on this subnet.ImportantYou should be aware that the files in the
~/openstack/my_cloud/config/directory are symlinks to the~/openstack/ardana/ansible/directory. For example:ardana >ls -al ~/openstack/my_cloud/config/keepalived/defaults.yml lrwxrwxrwx 1 stack stack 55 May 24 20:38 /var/lib/ardana/openstack/my_cloud/config/keepalived/defaults.yml -> ../../../ardana/ansible/roles/keepalived/defaults/main.ymlIf you are using a tool like
sedto make edits to files in this directory, you might break the symbolic link and create a new copy of the file. To maintain the link, you will need to forcesedto follow the link:ardana >sed -i --follow-symlinks \ 's$keepalived_vrrp_offset: 0$keepalived_vrrp_offset: 2$' \ ~/openstack/my_cloud/config/keepalived/defaults.ymlAlternatively, directly edit the target of the link
~/openstack/ardana/ansible/roles/keepalived/defaults/main.yml.Commit your configuration to the Git repository (see Chapter 22, Using Git for Configuration Management), as follows:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "changing Admin password"Run the configuration processor with this command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlUse the playbook below to create a deployment directory:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlIf you are making this change after your initial install, run the following reconfigure playbook to make this change in your environment:
ardana >cd ~/scratch/ansible/next/ardana/ansible/ardana >ansible-playbook -i hosts/verb_hosts FND-CLU-reconfigure.yml
Part III Pre-Installation #
- 13 Overview
To ensure that your environment meets the requirements of the cloud model you choose, see the check list in Chapter 14, Pre-Installation Checklist.
- 14 Pre-Installation Checklist
The formatting of this page facilitates printing it out and using it to record details of your setup.
- 15 Installing the Cloud Lifecycle Manager server
This chapter will show how to install the Cloud Lifecycle Manager from scratch. It will run on SUSE Linux Enterprise Server 12 SP4, include the SUSE OpenStack Cloud extension, and, optionally, the Subscription Management Tool (SMT) server.
- 16 Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional)
One way to provide the repositories needed to set up the nodes in SUSE OpenStack Cloud is to install a Subscription Management Tool (SMT) server on the Cloud Lifecycle Manager server, and then mirror all repositories from SUSE Customer Center via this server. Installing an SMT server on the Cloud Lifecycle Manager server is optional. If your organization already provides an SMT server or a SUSE Manager server that can be accessed from the Cloud Lifecycle Manager server, skip this step.
- 17 Software Repository Setup
Software repositories containing products, extensions, and the respective updates for all software need to be available to all nodes in SUSE OpenStack Cloud in order to complete the deployment. These can be managed manually, or they can be hosted on the Cloud Lifecycle Manager server. In this config…
- 18 Boot from SAN and Multipath Configuration
For information about supported hardware for multipathing, see Section 2.2, “Supported Hardware Configurations”.
13 Overview #
To ensure that your environment meets the requirements of the cloud model you choose, see the check list in Chapter 14, Pre-Installation Checklist.
After you have decided on a configuration to choose for your cloud and you have gone through the pre-installation steps, you will have two options for installation:
You can use a graphical user interface (GUI) that runs in your Web browser.
You can install via the command line that gives you the flexibility and full control of SUSE OpenStack Cloud 9.
Using the GUI
You should use the GUI if:
You are not planning to deploy availability zones or use L3 segmentation in your initial deployment.
You are satisfied with the tuned SUSE-default OpenStack configuration.
Instructions for GUI installation are in Chapter 21, Installing with the Install UI.
Reconfiguring your cloud can only be done via the command line. The GUI installer is for initial installation only.
Using the Command Line
You should use the command line if:
You are installing a complex or large-scale cloud.
You need to use availability zones or the server groups functionality of the cloud model. For more information, see the Chapter 5, Input Model.
You want to customize the cloud configuration beyond the tuned defaults that SUSE provides out of the box.
You need more extensive customizations than are possible using the GUI.
Instructions for installing via the command line are in Chapter 24, Installing Mid-scale and Entry-scale KVM.
Ardana is an open-source project and a generalized lifecycle management framework. Cloud Lifecycle Manager is based on Ardana, and delivers the lifecycle management functionality required by SUSE OpenStack Cloud 9. Due to this relationship, some Cloud Lifecycle Manager commands refer to Ardana.
14 Pre-Installation Checklist #
The formatting of this page facilitates printing it out and using it to record details of your setup.
This checklist is focused on the Entry-scale KVM model but you can alter it to fit the example configuration you choose for your cloud.
14.1 BIOS and IPMI Settings #
Ensure that the following BIOS and IPMI settings are applied to each bare-metal server:
| ☐ | Item |
|---|---|
| Choose either UEFI or Legacy BIOS in the BIOS settings | |
|
Verify the Date and Time settings in the BIOS. Note SUSE OpenStack Cloud installs and runs with UTC, not local time. | |
| Ensure that Wake-on-LAN is disabled in the BIOS | |
| Ensure that the NIC port to be used for PXE installation has PXE enabled in the BIOS | |
| Ensure that all other NIC ports have PXE disabled in the BIOS | |
| Ensure all hardware in the server not directly used by SUSE OpenStack Cloud is disabled |
14.2 Network Setup and Configuration #
Before installing SUSE OpenStack Cloud, the following networks must be provisioned and tested. The networks are not installed or managed by the Cloud. You must install and manage the networks as documented in Chapter 9, Example Configurations.
Note that if you want a pluggable IPAM driver, it must be specified at install time. Only with a clean install of SUSE OpenStack Cloud 9 can you specify a different IPAM driver. If upgrading, you must use the default driver. More information can be found in Book “Operations Guide CLM”, Chapter 10 “Managing Networking”, Section 10.4 “Networking Service Overview”, Section 10.4.7 “Using IPAM Drivers in the Networking Service”.
Use these checklists to confirm and record your network configuration information.
Router
The IP router used with SUSE OpenStack Cloud must support the updated of its ARP table through gratuitous ARP packets.
PXE Installation Network
When provisioning the IP range, allocate sufficient IP addresses to cover both the current number of servers and any planned expansion. Use the following table to help calculate the requirements:
| Instance | Description | IPs |
|---|---|---|
| Deployer O/S | 1 | |
| Controller server O/S (x3) | 3 | |
| Compute servers (2nd thru 100th) | single IP per server | |
| block storage host servers | single IP per server |
| ☐ | Item | Value |
|---|---|---|
| Network is untagged | ||
| No DHCP servers other than SUSE OpenStack Cloud are on the network | ||
| Switch PVID used to map any "internal" VLANs to untagged | ||
| Routable to the IPMI network | ||
| IP CIDR | ||
| IP Range (Usable IPs) |
begin: end: | |
| Default IP Gateway |
Management Network
The management network is the backbone used for the majority of SUSE OpenStack Cloud management communications. Control messages are exchanged between the Controllers, Compute hosts, and cinder backends through this network. In addition to the control flows, the management network is also used to transport swift and iSCSI based cinder block storage traffic between servers.
When provisioning the IP Range, allocate sufficient IP addresses to cover both the current number of servers and any planned expansion. Use the following table to help calculate the requirements:
| Instance | Description | IPs |
|---|---|---|
| Controller server O/S (x3) | 3 | |
| Controller VIP | 1 | |
| Compute servers (2nd through 100th) | single IP per server | |
| VM servers | single IP per server | |
| VIP per cluster |
| ☐ | Item | Value |
|---|---|---|
| Network is untagged | ||
| No DHCP servers other than SUSE OpenStack Cloud are on the network | ||
| Switch PVID used to map any "internal" VLANs to untagged | ||
| IP CIDR | ||
| IP Range (Usable IPs) |
begin: end: | |
| Default IP Gateway | ||
| VLAN ID |
IPMI Network
The IPMI network is used to connect the IPMI interfaces on the servers that are assigned for use with implementing the cloud. This network is used by Cobbler to control the state of the servers during baremetal deployments.
| ☐ | Item | Value |
|---|---|---|
| Network is untagged | ||
| Routable to the Management Network | ||
| IP Subnet | ||
| Default IP Gateway |
External API Network
The External network is used to connect OpenStack endpoints to an external public network such as a company’s intranet or the public internet in the case of a public cloud provider.
When provisioning the IP Range, allocate sufficient IP addresses to cover both the current number of servers and any planned expansion. Use the following table to help calculate the requirements.
| Instance | Description | IPs |
|---|---|---|
| Controller server O/S (x3) | 3 | |
| Controller VIP | 1 |
| ☐ | Item | Value |
|---|---|---|
| VLAN Tag assigned: | ||
| IP CIDR | ||
| IP Range (Usable IPs) |
begin: end: | |
| Default IP Gateway | ||
| VLAN ID |
External VM Network
The External VM network is used to connect cloud instances to an external public network such as a company’s intranet or the public internet in the case of a public cloud provider. The external network has a predefined range of Floating IPs which are assigned to individual instances to enable communications to and from the instance to the assigned corporate intranet/internet. There should be a route between the External VM and External API networks so that instances provisioned in the cloud, may access the Cloud API endpoints, using the instance floating IPs.
| ☐ | Item | Value |
|---|---|---|
| VLAN Tag assigned: | ||
| IP CIDR | ||
| IP Range (Usable IPs) |
begin: end: | |
| Default IP Gateway | ||
| VLAN ID |
14.3 Cloud Lifecycle Manager #
This server contains the SUSE OpenStack Cloud installer, which is based on Git, Ansible, and Cobbler.
| ☐ | Item | Value |
|---|---|---|
| Disk Requirement: Single 8GB disk needed per the Chapter 2, Hardware and Software Support Matrix | ||
| Section 15.5.2, “Installing the SUSE OpenStack Cloud Extension” | ||
Ensure your local DNS nameserver is placed into your
/etc/resolv.conf file
| ||
| Install and configure NTP for your environment | ||
Ensure your NTP server(s) is placed into your
/etc/ntp.conf file
| ||
| NTP time source: | ||
14.4 Information for the nic_mappings.yml Input File #
Log on to each type of physical server you have and issue platform-appropriate
commands to identify the bus-address and
port-num values that may be required. For example, run the
following command:
sudo lspci -D | grep -i net
and enter this information in the space below. Use this information for the
bus-address value in your
nic_mappings.yml file.
| NIC Adapter PCI Bus Address Output |
|---|
|
|
To find the port-num use:
cat /sys/class/net/<device name>/dev_port
where the 'device-name' is the name of the device currently mapped to this address, not necessarily the name of the device to be mapped. Enter the information for your system in the space below.
| Network Device Port Number Output |
|---|
|
|
14.5 Control Plane #
The Control Plane consists of at least three servers in a highly available cluster that host the core SUSE OpenStack Cloud services including nova, keystone, glance, cinder, heat, neutron, swift, ceilometer, and horizon. Additional services include mariadb, ip-cluster, apache2, rabbitmq, memcached, zookeeper, kafka, storm, monasca, logging, and cmc.
To mitigate the “split-brain” situation described in Book “Operations Guide CLM”, Chapter 18 “Troubleshooting Issues”, Section 18.4 “Network Service Troubleshooting” it is recommended that you have HA network configuration with Multi-Chassis Link Aggregation (MLAG) and NIC bonding configured for all the controllers to deliver system-level redundancy as well network-level resiliency. Also reducing the ARP timeout on the TOR switches will help.
| ☐ | Item | Value |
|---|---|---|
| Disk Requirement: 3x 512 GB disks (or enough space to create three logical drives with that amount of space) | ||
| Ensure the disks are wiped | ||
| MAC address of first NIC | ||
| A second NIC, or a set of bonded NICs are required | ||
| IPMI IP address | ||
| IPMI Username/Password |
| ☐ | Item | Value |
|---|---|---|
| Disk Requirement: 3x 512 GB disks (or enough space to create three logical drives with that amount of space) | ||
| Ensure the disks are wiped | ||
| MAC address of first NIC | ||
| A second NIC, or a set of bonded NICs are required | ||
| IPMI IP address | ||
| IPMI Username/Password |
| ☐ | Item | Value |
|---|---|---|
| Disk Requirement: 3x 512 GB disks (or enough space to create three logical drives with that amount of space) | ||
| Ensure the disks are wiped | ||
| MAC address of first NIC | ||
| A second NIC, or a set of bonded NICs are required | ||
| IPMI IP address | ||
| IPMI Username/Password |
14.6 Compute Hosts #
One or more KVM Compute servers will be used as the compute host targets for instances.
| ☐ | Item |
|---|---|
| Disk Requirement: 2x 512 GB disks (or enough space to create three logical drives with that amount of space) | |
| A NIC for PXE boot and a second NIC, or a NIC for PXE and a set of bonded NICs are required | |
| Ensure the disks are wiped |
Table to record your Compute host details:
| ID | NIC MAC Address | IPMI Username/Password | IMPI IP Address | CPU/Mem/Disk |
|---|---|---|---|---|
14.7 Storage Hosts #
Three or more servers with local disk volumes to provide cinder block storage resources.
The cluster created from block storage nodes must allow for quorum. In other words, the node count of the cluster must be 3, 5, 7, or another odd number.
| ☐ | Item |
|---|---|
|
Disk Requirement: 3x 512 GB disks (or enough space to create three logical drives with that amount of space) The block storage appliance deployed on a host is expected to consume ~40 GB of disk space from the host root disk for ephemeral storage to run the block storage virtual machine. | |
| A NIC for PXE boot and a second NIC, or a NIC for PXE and a set of bonded NICs are required | |
| Ensure the disks are wiped |
Table to record your block storage host details:
| ID | NIC MAC Address | IPMI Username/Password | IPMI IP Address | CPU/Mem/Disk | Data Volume |
|---|---|---|---|---|---|
14.8 Additional Comments #
This section is for any additional information that you deem necessary.
15 Installing the Cloud Lifecycle Manager server #
This chapter will show how to install the Cloud Lifecycle Manager from scratch. It will run on SUSE Linux Enterprise Server 12 SP4, include the SUSE OpenStack Cloud extension, and, optionally, the Subscription Management Tool (SMT) server.
15.1 Registration and Online Updates #
Registering SUSE Linux Enterprise Server 12 SP4 during the installation process is required for getting product updates and for installing the SUSE OpenStack Cloud extension.
After a successful registration you will be asked whether to add the update repositories. If you agree, the latest updates will automatically be installed, ensuring that your system is on the latest patch level after the initial installation. We strongly recommend adding the update repositories immediately. If you choose to skip this step you need to perform an online update later, before starting the installation.
To register a product, you need to have a SUSE login. If you do not have such a login, create it at http://www.suse.com/.
15.2 Starting the Operating System Installation #
Installing SUSE Linux Enterprise Server for SUSE OpenStack Cloud requires the following steps, which are different from the default SUSE Linux Enterprise Server installation process.
For an overview of a default SUSE Linux Enterprise Server installation, refer to https://documentation.suse.com/sles/12-SP5/single-html/SLES-installquick/#art-sle-installquick.
Start the installation by booting into the SUSE Linux Enterprise Server 12 SP4 installation system.
15.3 Partitioning #
Create a custom partition setup using the . The following setup is required:
Two partitions are needed: one for boot, EFI or UEFI, and one for everything else.
If the system is using a UEFI BIOS, there must be a UEFI boot partition.
An LVM setup with no encryption is recommended, Btrfs will work. The file system must contain:
a volume group named
ardana-vgon the first disk (/dev/sda)a volume named
rootwith a size of 50GB and an ext4 filesystem
no separate mount point for
/homeno swap partition or file (No swap is a general OpenStack recommendation. Some services such as rabbit and cassandra do not perform well with swapping.)
15.4 Creating a User #
Setting up Cloud Lifecycle Manager requires a regular user which you can set up during the
installation. You are free to choose any available user name except for
ardana, because the ardana user is reserved by SUSE OpenStack Cloud.
15.5 Installation Settings #
With , you need to adjust the software selection for your Cloud Lifecycle Manager setup. For more information refer to the https://documentation.suse.com/sles/15-SP1/single-html/SLES-deployment/#sec-yast-install-perform.
The default firewall must be disabled, as SUSE OpenStack Cloud enables its own firewall during deployment.
SSH must be enabled.
Set text as the .
15.5.1 Software Selection #
Installing a minimal base system is sufficient to set up the Cloud Lifecycle Manager. The following patterns are the minimum required:
(in case you have chosen to install the SUSE OpenStack Cloud Extension)
(optional, also see Tip: Installing a Local SMT Server (Optional))
If you do not have a SUSE Manager or SMT server in your organization, or are planning to manually update the repositories required for deployment of the SUSE OpenStack Cloud nodes, you need to set up an SMT server on the Cloud Lifecycle Manager. Choose the pattern in addition to the patterns listed above to install the SMT server software.
15.5.2 Installing the SUSE OpenStack Cloud Extension #
SUSE OpenStack Cloud is an extension to SUSE Linux Enterprise Server. Installing it during the SUSE Linux Enterprise Server installation is the easiest and recommended way to set up the Cloud Lifecycle Manager. To get access to the extension selection dialog, you need to register SUSE Linux Enterprise Server 12 SP4 during the installation. After a successful registration, the SUSE Linux Enterprise Server 12 SP4 installation continues with the . Choose and provide the registration key you obtained by purchasing SUSE OpenStack Cloud. The registration and the extension installation require an Internet connection.
If you do not have Internet access or are not able to register during installation, then once Internet access is available for the Cloud Lifecycle Manager do the following steps:
tux >sudo SUSEConnect -r SLES_REGISTRATION_CODEList repositories to verify:
ardana >zypper lrRefresh the repositories:
tux >sudo zypper ref
Alternatively, install the SUSE OpenStack Cloud after the SUSE Linux Enterprise Server 12 SP4 installation via › › . For details, refer to https://documentation.suse.com/sles/15-SP1/single-html/SLES-deployment/#sec-add-ons-extensions.
16 Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) #
One way to provide the repositories needed to set up the nodes in SUSE OpenStack Cloud is to install a Subscription Management Tool (SMT) server on the Cloud Lifecycle Manager server, and then mirror all repositories from SUSE Customer Center via this server. Installing an SMT server on the Cloud Lifecycle Manager server is optional. If your organization already provides an SMT server or a SUSE Manager server that can be accessed from the Cloud Lifecycle Manager server, skip this step.
When installing an SMT server on the Cloud Lifecycle Manager server, use it exclusively for SUSE OpenStack Cloud. To use the SMT server for other products, run it outside of SUSE OpenStack Cloud. Make sure it can be accessed from the Cloud Lifecycle Manager for mirroring the repositories needed for SUSE OpenStack Cloud.
When the SMT server is installed on the Cloud Lifecycle Manager server, Cloud Lifecycle Manager
provides the mirrored repositories on port 79.
16.1 SMT Installation #
If you have not installed the SMT server during the initial Cloud Lifecycle Manager server installation as suggested in Section 15.5.1, “Software Selection”, run the following command to install it:
sudo zypper in -t pattern smt
16.2 SMT Configuration #
No matter whether the SMT server was installed during the initial installation or in the running system, it needs to be configured with the following steps.
To configure the SMT server, a SUSE account is required. If you do not have such an account, register at http://www.suse.com/. All products and extensions for which you want to mirror updates with the SMT server should be registered at the SUSE Customer Center (http://scc.suse.com/).
If you did not register with the SUSE Customer Center during installation, then at this point you will need to register in order to proceed. Ensure that the Cloud Lifecycle Manager has external network access and then run the following command:
tux > sudo SUSEConnect -r
SLES_REGISTRATION_CODEConfiguring the SMT server requires you to have your mirroring credentials (user name and password) and your registration e-mail address at hand. To access them, proceed as follows:
Open a Web browser and log in to the SUSE Customer Center at http://scc.suse.com/.
Click your name to see the e-mail address which you have registered.
Click › to obtain your mirroring credentials (user name and password).
Start › › .
Activate .
Enter the data as follows:
: Do not activate this option : The user name you retrieved from the SUSE Customer Center : The password you retrieved from the SUSE Customer Center Check your input with . If the test does not return
success, check the credentials you entered.Enter the e-mail address you retrieved from the SUSE Customer Center at .
shows the HTTP address of your server. Usually it should not be necessary to change it.
Select to proceed to step two of the .
Enter a and confirm it by entering it once again.
Enter one or more e-mail addresses to which SMT status reports are sent by selecting .
Select to save your SMT configuration. When setting up the database you will be prompted for the MariaDB root password. If you have not already created one then create it in this step. Note that this is the global MariaDB root password, not the database password for the SMT user you specified before.
The SMT server requires a server certificate at
/etc/pki/trust/anchors/YaST-CA.pem. Choose , provide a password and choose to create such a certificate. If your organization already provides a CA certificate, this step and import the certificate via › › after the SMT configuration is done. See https://documentation.suse.com/sles/15-SP1/single-html/SLES-security/#cha-security-yast-security for more information.After you complete your configuration a synchronization check with the SUSE Customer Center will run, which may take several minutes.
16.3 Setting up Repository Mirroring on the SMT Server #
The final step in setting up the SMT server is configuring it to mirror the repositories needed for SUSE OpenStack Cloud. The SMT server mirrors the repositories from the SUSE Customer Center. Make sure to have the appropriate subscriptions registered in SUSE Customer Center with the same e-mail address you specified when configuring SMT.
16.3.1 Adding Mandatory Repositories #
Mirroring the SUSE Linux Enterprise Server 12 SP4 and SUSE OpenStack Cloud 9
repositories is mandatory. Run the following commands as user
root to add them to the list of mirrored repositories:
for REPO in SLES12-SP4-{Pool,Updates} SUSE-OpenStack-Cloud-9-{Pool,Updates}; do
smt-repos $REPO sle-12-x86_64 -e
done16.3.2 Updating the Repositories #
New repositories added to SMT must be updated immediately by running the following command as user root:
smt-mirror -L /var/log/smt/smt-mirror.log
This command will download several GB of patches. This process may last
up to several hours. A log file is written to
/var/log/smt/smt-mirror.log. After this first manual update the repositories are updated automatically via cron
job. A list of all
repositories and their location in the file system on the Cloud Lifecycle Manager server can be
found at Table 17.2, “SMT Repositories Hosted on the Cloud Lifecycle Manager”.
16.4 For More Information #
For detailed information about SMT refer to the Subscription Management Tool manual at https://documentation.suse.com/sles/12-SP5/single-html/SLES-smt/.
17 Software Repository Setup #
Software repositories containing products, extensions, and the respective updates for all software need to be available to all nodes in SUSE OpenStack Cloud in order to complete the deployment. These can be managed manually, or they can be hosted on the Cloud Lifecycle Manager server. In this configuration step, these repositories are made available on the Cloud Lifecycle Manager server. There are two types of repositories:
Product Media Repositories: Product media repositories are copies of the installation media. They need to be directly copied to the Cloud Lifecycle Manager server, “loop-mounted” from an iso image, or mounted from a remote server via NFS. Affected are SUSE Linux Enterprise Server 12 SP4 and SUSE OpenStack Cloud 9. These are static repositories; they do not change or receive updates. See Section 17.1, “Copying the Product Media Repositories” for setup instructions.
Update and Pool Repositories: Update and Pool repositories are provided by the SUSE Customer Center. They contain all updates and patches for the products and extensions. To make them available for SUSE OpenStack Cloud they need to be mirrored from the SUSE Customer Center. Their content is regularly updated, so they must be kept in synchronization with SUSE Customer Center. For these purposes, SUSE provides the Subscription Management Tool (SMT). See Section 17.2, “Update and Pool Repositories” for setup instructions.
17.1 Copying the Product Media Repositories #
The files in the product repositories for SUSE OpenStack Cloud do not
change, therefore they do not need to be synchronized with a remote
source. If you have installed the product media from a downloaded ISO image,
the product repositories will automatically be made available to the client
nodes and these steps can be skipped. These steps can also be skipped if you
prefer to install from the Pool repositories provided by SUSE Customer Center. Otherwise,
it is sufficient to either copy the data (from a remote host or the
installation media), to mount the product repository from a remote server
via NFS, or to loop mount a copy of the installation
images.
If you choose to install from the product media rather than from the SUSE Customer Center repositories, the following product media needs to reside in the specified directories:
|
Repository |
Directory |
|---|---|
|
SUSE OpenStack Cloud 9 DVD #1 |
|
The data can be copied by a variety of methods:
- Copying from the Installation Media
We recommend using
rsyncfor copying. If the installation data is located on a removable device, make sure to mount it first (for example, after inserting the DVD1 in the Cloud Lifecycle Manager and waiting for the device to become ready):SUSE OpenStack Cloud 9 DVD#1 #
mkdir -p /srv/www/suse-12.4/x86_64/repos/Cloud mount /dev/dvd /mnt rsync -avP /mnt/ /srv/www/suse-12.4/x86_64/repos/Cloud/ umount /mnt
- Copying from a Remote Host
If the data is provided by a remote machine, log in to that machine and push the data to the Cloud Lifecycle Manager (which has the IP address
192.168.245.10in the following example):SUSE OpenStack Cloud 9 DVD#1 #
mkdir -p /srv/www/suse-12.4/x86_64/repos/Cloud rsync -avPz /data/SUSE-OPENSTACK-CLOUD//DVD1/ 192.168.245.10:/srv/www/suse-12.4/x86_64/repos/Cloud/
- Mounting from an NFS Server
If the installation data is provided via NFS by a remote machine, mount the respective shares as follows. To automatically mount these directories either create entries in
/etc/fstabor set up the automounter.SUSE OpenStack Cloud 9 DVD#1 #
mkdir -p /srv/www/suse-12.4/x86_64/repos/Cloud/ mount -t nfs nfs.example.com:/exports/SUSE-OPENSTACK-CLOUD/DVD1/ /srv/www/suse-12.4/x86_64/repos/Cloud
17.2 Update and Pool Repositories #
Update and Pool Repositories are required on the Cloud Lifecycle Manager server to set up and maintain the SUSE OpenStack Cloud nodes. They are provided by SUSE Customer Center and contain all software packages needed to install SUSE Linux Enterprise Server 12 SP4 and the extensions (pool repositories). In addition, they contain all updates and patches (update repositories).
The repositories can be made available on the Cloud Lifecycle Manager server using one or more of the following methods:
17.2.1 Repositories Hosted on an SMT Server Installed on the Cloud Lifecycle Manager #
When all update and pool repositories are managed by an SMT server installed on the Cloud Lifecycle Manager server (see Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional)), the Cloud Lifecycle Manager automatically detects all available repositories. No further action is required.
17.2.2 Alternative Ways to Make the Repositories Available #
If you want to keep your SUSE OpenStack Cloud network as isolated from the company network as possible, or your infrastructure does not allow accessing a SUSE Manager or an SMT server, you can alternatively provide access to the required repositories by one of the following methods:
Mount the repositories from a remote server.
Synchronize the repositories from a remote server (for example via
rsyncand cron).Manually synchronize the update repositories from removable media.
The repositories must be made available at the default locations on the Cloud Lifecycle Manager server as listed in Table 17.3, “Repository Locations on the Cloud Lifecycle Manager server”.
17.3 Repository Locations #
The following tables show the locations of all repositories that can be used for SUSE OpenStack Cloud.
|
Repository |
Directory |
|---|---|
|
Mandatory Repositories | |
|
SLES12-SP4-Pool |
|
|
SLES12-SP4-Updates |
|
|
SUSE-OpenStack-Cloud-9-Pool |
|
|
SUSE-OpenStack-Cloud-9-Updates |
|
The following table shows the required repository locations to use when manually copying, synchronizing, or mounting the repositories.
|
Channel |
Directory on the Cloud Lifecycle Manager |
|---|---|
|
Mandatory Repositories | |
|
SLES12-SP4-Pool |
|
|
SLES12-SP4-Updates |
|
|
SUSE-OpenStack-Cloud-9-Pool |
|
|
SUSE-OpenStack-Cloud-9-Updates |
|
18 Boot from SAN and Multipath Configuration #
18.1 Introduction #
For information about supported hardware for multipathing, see Section 2.2, “Supported Hardware Configurations”.
When exporting a LUN to a node for boot from SAN, you should ensure that LUN 0 is assigned to the LUN and configure any setup dialog that is necessary in the firmware to consume this LUN 0 for OS boot.
Any hosts that are connected to 3PAR storage must have a host
persona of 2-generic-alua set on the 3PAR.
Refer to the 3PAR documentation for the steps necessary to check this and
change if necessary.
iSCSI boot from SAN is not supported. For more information on the use of cinder with multipath, see Section 35.1.3, “Multipath Support”.
To allow SUSE OpenStack Cloud 9 to use volumes from a SAN, you have to specify configuration options for both the installation and the OS configuration phase. In all cases, the devices that are utilized are devices for which multipath is configured.
18.2 Install Phase Configuration #
For FC connected nodes and for FCoE nodes where the network processor used is from the Emulex family such as for the 650FLB, the following changes are required.
Instead of using Cobbler, you need to provision a baremetal node manually using the following procedure.
During manual installation of SUSE Linux Enterprise Server 12 SP4, select the desired SAN disk and create an LVM partitioning scheme that meets SUSE OpenStack Cloud requirements: it has an
ardana-vgvolume group and anardana-vg-rootlogical volume. For more information on partitioning, see Section 15.3, “Partitioning”.Open the
/etc/multipath/bindingsfile and map the expected device name to the SAN disk selected during installation. In SUSE OpenStack Cloud, the naming convention is mpatha, mpathb, and so on. For example:mpatha-part1 360000000030349030-part1 mpatha-part2 360000000030349030-part2 mpatha-part3 360000000030349030-part3 mpathb-part1 360000000030349000-part1 mpathb-part2 360000000030349000-part2
Reboot to enable the changes.
Assign a static IP to the node:
Use the
ip addrcommand to list active network interfaces on your system:1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000 link/ether f0:92:1c:05:89:70 brd ff:ff:ff:ff:ff:ff inet 10.13.111.178/26 brd 10.13.111.191 scope global eno1 valid_lft forever preferred_lft forever inet6 fe80::f292:1cff:fe05:8970/64 scope link valid_lft forever preferred_lft forever 3: eno2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000 link/ether f0:92:1c:05:89:74 brd ff:ff:ff:ff:ff:ffIdentify the network interface that matches the MAC address of your server and edit the corresponding configuration file in
/etc/sysconfig/network-scripts. For example, for theeno1interface, open the/etc/sysconfig/network-scripts/ifcfg-eno1file and edit IPADDR and NETMASK values to match your environment. The IPADDR is used in the corresponding stanza inservers.yml. You may also need to setBOOTPROTOtonone:TYPE=Ethernet BOOTPROTO=none DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_PEERDNS=yes IPV6_PEERROUTES=yes IPV6_FAILURE_FATAL=no NAME=eno1 UUID=360360aa-12aa-444a-a1aa-ee777a3a1a7a DEVICE=eno1 ONBOOT=yes NETMASK=255.255.255.192 IPADDR=10.10.100.10
Reboot the SLES node and ensure that it can be accessed from the Cloud Lifecycle Manager.
Add the
ardanauser and home directory:root #useradd -m -d /var/lib/ardana -U ardanaAllow the user
ardanato runsudowithout a password by creating the/etc/sudoers.d/ardanafile with the following configuration:ardana ALL=(ALL) NOPASSWD:ALL
When you start installation using the Cloud Lifecycle Manager, or if you are adding a SLES node to an existing cloud, copy the Cloud Lifecycle Manager public key to the SLES node to enable passwordless SSH access. One way of doing this is to copy the file
~/.ssh/authorized_keysfrom another node in the cloud to the same location on the SLES node. If you are installing a new cloud, this file will be available on the nodes after running thebm-reimage.ymlplaybook. Ensure that there is global read access to the file/var/lib/ardana/.ssh/authorized_keys.Use the following command to test passwordless SSH from the deployer and check the ability to remotely execute sudo commands:
ssh stack@SLES_NODE_IP "sudo tail -5 /var/log/messages"
18.2.1 Deploying the Cloud #
In
openstack/my_cloud/config/multipath/multipath_settings.yml, setmanual_multipath_conftoTrueso thatmultipath.confon manually installed nodes is not overwritten.Commit the changes.
tux >cd ~/openstacktux >git add -Atux >git commit -m "multipath config"Run
config-processorandready-deployment.tux >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymltux >ansible-playbook -i hosts/localhost ready-deployment.ymlEnsure that all existing non-OS partitions on the nodes are wiped prior to installation by running the
wipe_disks.ymlplaybook.NoteConfirm that your root partition disk is not listed in disks to be wiped.
tux >cd ~/scratch/ansible/next/ardana/ansibletux >ansible-playbook -i hosts/verb_hosts wipe_disks.ymlRun the
site.ymlplaybook:tux >cd ~/scratch/ansible/next/ardana/ansibletux >ansible-playbook -i hosts/verb_hosts site.yml
Part IV Cloud Installation #
- 19 Overview
Before starting the installation, review the sample configurations offered by SUSE OpenStack Cloud in Chapter 9, Example Configurations. SUSE OpenStack Cloud ships with highly tuned example configurations for each of these cloud models:
- 20 Preparing for Stand-Alone Deployment
The Cloud Lifecycle Manager can be installed on a Control Plane or on a stand-alone server.
- 21 Installing with the Install UI
- 22 Using Git for Configuration Management
In SUSE OpenStack Cloud 9, a local git repository is used to track configuration changes; the Configuration Processor (CP) uses this repository. Use of a git workflow means that your configuration history is maintained, making rollbacks easier and keeping a record of previous configuration settings.…
- 23 Installing a Stand-Alone Cloud Lifecycle Manager
For information about when to use the GUI installer and when to use the command line (CLI), see Chapter 13, Overview.
- 24 Installing Mid-scale and Entry-scale KVM
For information about when to use the GUI installer and when to use the command line (CLI), see Chapter 13, Overview.
- 25 DNS Service Installation Overview
The SUSE OpenStack Cloud DNS Service supports several different backends for domain name service. The choice of backend must be included in the deployment model before the SUSE OpenStack Cloud install is completed.
- 26 Magnum Overview
The SUSE OpenStack Cloud Magnum Service provides container orchestration engines such as Docker Swarm, Kubernetes, and Apache Mesos available as first class resources. SUSE OpenStack Cloud Magnum uses heat to orchestrate an OS image which contains Docker and Kubernetes and runs that image in either …
- 27 Installing ESX Computes and OVSvAPP
This section describes the installation step requirements for ESX Computes (nova-proxy) and OVSvAPP.
- 28 Integrating NSX for vSphere
This section describes the installation and integration of NSX-v, a Software Defined Networking (SDN) network virtualization and security platform for VMware's vSphere.
- 29 Installing Baremetal (Ironic)
Bare Metal as a Service is enabled in this release for deployment of nova instances on bare metal nodes using flat networking.
- 30 Installation for SUSE OpenStack Cloud Entry-scale Cloud with Swift Only
This page describes the installation step requirements for the SUSE OpenStack Cloud Entry-scale Cloud with swift Only model.
- 31 Installing SLES Compute
SUSE OpenStack Cloud 9 supports SLES compute nodes, specifically SUSE Linux Enterprise Server 12 SP4. SUSE does not ship a SLES ISO with SUSE OpenStack Cloud so you will need to download a copy of the SLES ISO (SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.iso) from SUSE. You can use the following link to do…
- 32 Installing manila and Creating manila Shares
The OpenStack Shared File Systems service (manila) provides file storage to a virtual machine. The Shared File Systems service provides a storage provisioning control plane for shared or distributed file systems. The service enables management of share types and share snapshots if you have a driver …
- 33 Installing SUSE CaaS Platform heat Templates
This chapter describes how to install SUSE CaaS Platform v3 using heat template on SUSE OpenStack Cloud.
- 34 Installing SUSE CaaS Platform v4 using terraform
More information about the SUSE CaaS Platform v4 is available at https://documentation.suse.com/suse-caasp/4.0/html/caasp-deployment/_deployment_instructions.html#_deployment_on_suse_openstack_cloud
- 35 Integrations
Once you have completed your cloud installation, these are some of the common integrations you may want to perform.
- 36 Troubleshooting the Installation
We have gathered some of the common issues that occur during installation and organized them by when they occur during the installation. These sections will coincide with the steps labeled in the installation instructions.
- 37 Troubleshooting the ESX
This section contains troubleshooting tasks for your SUSE® OpenStack Cloud 9 for ESX.
19 Overview #
Before starting the installation, review the sample configurations offered by SUSE OpenStack Cloud in Chapter 9, Example Configurations. SUSE OpenStack Cloud ships with highly tuned example configurations for each of these cloud models:
| Name | Location |
|---|---|
| Section 9.3.1, “Entry-Scale Cloud” |
~/openstack/examples/entry-scale-kvm
|
| Section 9.3.2, “Entry Scale Cloud with Metering and Monitoring Services” |
~/openstack/examples/entry-scale-kvm-mml
|
| Section 9.4.1, “Single-Region Entry-Scale Cloud with a Mix of KVM and ESX Hypervisors” | ~/openstack/examples/entry-scale-kvm-esx
|
| Section 9.4.2, “Single-Region Entry-Scale Cloud with Metering and Monitoring Services, and a Mix of KVM and ESX Hypervisors” |
~/openstack/examples/entry-scale-kvm-esx-mml
|
| Section 9.5.1, “Entry-scale swift Model” |
~/openstack/examples/entry-scale-swift
|
| Section 9.6.1, “Entry-Scale Cloud with Ironic Flat Network” |
~/openstack/examples/entry-scale-ironic-flat-network
|
| Section 9.6.2, “Entry-Scale Cloud with Ironic Multi-Tenancy” |
~/openstack/examples/entry-scale-ironic-multi-tenancy
|
| Section 9.3.3, “Single-Region Mid-Size Model” |
~/openstack/examples/mid-scale-kvm
|
There are two methods for installation to choose from:
You can use a GUI that runs in your Web browser.
You can install via the command line that gives you the flexibility and full control of SUSE OpenStack Cloud 9.
Using the GUI
You should use the GUI if:
You are not planning to deploy availability zones, L3 segmentation, or server groups functionality in your initial deployment.
You are satisfied with the tuned SUSE-default OpenStack configuration.
Instructions for GUI installation are in Chapter 21, Installing with the Install UI.
Reconfiguring your cloud can only be done via the command line. The GUI installer is for initial installation only.
Using the Command Line
You should use the command line if:
You are installing a complex or large-scale cloud.
You are planning to deploy availability zones, L3 segmentation, or server groups functionality. For more information, see the Chapter 5, Input Model.
You want to customize the cloud configuration beyond the tuned defaults that SUSE provides out of the box.
You need more extensive customizations than are possible using the GUI.
Instructions for installing via the command line are in Chapter 24, Installing Mid-scale and Entry-scale KVM.
20 Preparing for Stand-Alone Deployment #
20.1 Cloud Lifecycle Manager Installation Alternatives #
The Cloud Lifecycle Manager can be installed on a Control Plane or on a stand-alone server.
Installing the Cloud Lifecycle Manager on a Control Plane is done during the process of deploying your Cloud. Your Cloud and the Cloud Lifecycle Manager are deployed together.
With a standalone Cloud Lifecycle Manager, you install the deployer first and then deploy your Cloud in a separate process. Either the Install UI or command line can be used to deploy a stand-alone Cloud Lifecycle Manager.
Each method is suited for particular needs. The best choice depends on your situation.
Stand-alone Deployer
+ Compared to a Control Plane deployer, a stand-alone deployer is easier to backup and redeploy in case of disaster
+ Separates cloud management from components being managed
+ Does not use Control Plane resources
- Another server is required (less of a disadvantage if using a VM)
- Installation may be more complex than a Control Plane Cloud Lifecycle Manager
Control Plane Deployer
+ Installation is usually simpler than installing a stand-alone deployer
+ Requires fewer servers or VMs
- Could contend with workloads for resources
- Harder to redeploy in case of failure compared to stand-alone deployer
- There is a risk to the Cloud Lifecycle Manager when updating or modifying controllers
- Runs on one of the servers that is deploying or managing your Cloud
Summary
A Control Plane Cloud Lifecycle Manager is best for small, simple Cloud deployments.
With a larger, more complex cloud, a stand-alone deployer provides better recoverability and the separation of manager from managed components.
20.2 Installing a Stand-Alone Deployer #
If you do not intend to install a stand-alone deployer, proceed to installing the Cloud Lifecycle Manager on a Control Plane.
Instructions for GUI installation are in Chapter 21, Installing with the Install UI.
Instructions for installing via the command line are in Chapter 24, Installing Mid-scale and Entry-scale KVM.
20.2.1 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
20.2.2 Configuring for a Stand-Alone Deployer #
The following steps are necessary to set up a stand-alone deployer whether you will be using the Install UI or command line.
Copy the SUSE OpenStack Cloud Entry-scale KVM example input model to a stand-alone input model. This new input model will be edited so that it can be used as a stand-alone Cloud Lifecycle Manager installation.
tux >cp -r ~/openstack/examples/entry-scale-kvm/* \ ~/openstack/examples/entry-scale-kvm-stand-alone-deployerChange to the new directory
tux >cd ~/openstack/examples/entry-scale-kvm-stand-alone-deployerEdit the cloudConfig.yml file to change the name of the input model. This will make the model available both to the Install UI and to the command line installation process.
Change
name: entry-scale-kvmtoname: entry-scale-kvm-stand-alone-deployerChange to the
datadirectory.Make the following edits to your configuration files.
ImportantThe indentation of each of the input files is important and will cause errors if not done correctly. Use the existing content in each of these files as a reference when adding additional content for your Cloud Lifecycle Manager.
Update
control_plane.ymlto add the Cloud Lifecycle Manager.Update
server_roles.ymlto add the Cloud Lifecycle Manager role.Update
net_interfaces.ymlto add the interface definition for the Cloud Lifecycle Manager.Create a
disks_lifecycle_manager.ymlfile to define the disk layout for the Cloud Lifecycle Manager.Update
servers.ymlto add the dedicated Cloud Lifecycle Manager node.
Control_plane.yml: The snippet below shows the addition of a single node cluster into the control plane to host the Cloud Lifecycle Manager service.ImportantIn addition to adding the new cluster, you also have to remove the Cloud Lifecycle Manager component from the
cluster1in the examples.clusters: - name: cluster0 cluster-prefix: c0 server-role: LIFECYCLE-MANAGER-ROLE member-count: 1 allocation-policy: strict service-components: - lifecycle-manager - ntp-client - name: cluster1 cluster-prefix: c1 server-role: CONTROLLER-ROLE member-count: 3 allocation-policy: strict service-components: - ntp-serverThis specifies a single node of role
LIFECYCLE-MANAGER-ROLEhosting the Cloud Lifecycle Manager.Server_roles.yml: The snippet below shows the insertion of the new server roles definition:server-roles: - name: LIFECYCLE-MANAGER-ROLE interface-model: LIFECYCLE-MANAGER-INTERFACES disk-model: LIFECYCLE-MANAGER-DISKS - name: CONTROLLER-ROLEThis defines a new server role which references a new interface-model and disk-model to be used when configuring the server.
net-interfaces.yml: The snippet below shows the insertion of the network-interface info:- name: LIFECYCLE-MANAGER-INTERFACES network-interfaces: - name: BOND0 device: name: bond0 bond-data: options: mode: active-backup miimon: 200 primary: hed3 provider: linux devices: - name: hed3 - name: hed4 network-groups: - MANAGEMENTThis assumes that the server uses the same physical networking layout as the other servers in the example.
disks_lifecycle_manager.yml: In the examples, disk-models are provided as separate files (this is just a convention, not a limitation) so the following should be added as a new file nameddisks_lifecycle_manager.yml:--- product: version: 2 disk-models: - name: LIFECYCLE-MANAGER-DISKS # Disk model to be used for Cloud Lifecycle Managers nodes # /dev/sda_root is used as a volume group for /, /var/log and /var/crash # sda_root is a templated value to align with whatever partition is really used # This value is checked in os config and replaced by the partition actually used # on sda e.g. sda1 or sda5 volume-groups: - name: ardana-vg physical-volumes: - /dev/sda_root logical-volumes: # The policy is not to consume 100% of the space of each volume group. # 5% should be left free for snapshots and to allow for some flexibility. - name: root size: 80% fstype: ext4 mount: / - name: crash size: 15% mount: /var/crash fstype: ext4 mkfs-opts: -O large_file consumer: name: osServers.yml: The snippet below shows the insertion of an additional server used for hosting the Cloud Lifecycle Manager. Provide the address information here for the server you are running on, that is, the node where you have installed the SUSE OpenStack Cloud ISO.servers: # NOTE: Addresses of servers need to be changed to match your environment. # # Add additional servers as required #Lifecycle-manager - id: lifecycle-manager ip-addr: YOUR IP ADDRESS HERE role: LIFECYCLE-MANAGER-ROLE server-group: RACK1 nic-mapping: HP-SL230-4PORT mac-addr: 8c:dc:d4:b5:c9:e0 # ipmi information is not needed # Controllers - id: controller1 ip-addr: 192.168.10.3 role: CONTROLLER-ROLE
With the stand-alone input model complete, you are ready to proceed to installing the stand-alone deployer with either the Install UI or the command line.
21 Installing with the Install UI #
SUSE OpenStack Cloud comes with a GUI-based installation wizard for first-time cloud installations. It will guide you through the configuration process and deploy your cloud based on the custom configuration you provide. The Install UI will start with a set of example cloud configurations for you to choose from. Based on your cloud choice, you can refine your configuration to match your needs using Install UI widgets. You can also directly edit your model configuration files.
The Install UI is only for initial deployments. It will not function properly after your cloud has been deployed successfully, whether it was from the CLI or with the Install UI.
When you are satisfied with your configuration and the Install UI has validated your configuration successfully, you can then deploy the cloud into your environment. Deploying the cloud will version-control your configuration into a git repository and provide you with live progress of your deployment.
With the Install UI, you have the option of provisioning SLES12-SP4 to IPMI-capable machines described in your configuration files. Provisioning machines with the Install UI will also properly configure them for Ansible access.
The Install UI is designed to make the initial installation process simpler, more accurate, and faster than manual installation.
21.1 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
21.2 Preparing to Run the Install UI #
Before you launch the Install UI to install your cloud, do the following:
Gather the following details from the servers that will make up your cloud:
Server names
IP addresses
Server roles
PXE MAC addresses
PXE IP addresses
PXE interfaces
IPMI IP address, username, password
Choose an input model from Chapter 9, Example Configurations. No action other than an understanding of your needs is necessary at this point. In the Install UI you will indicate which input model you wish to deploy.
Before you use the Install UI to install your cloud, you may install the operating system, SLES, on your nodes (servers) if you choose. Otherwise, the Install UI will install it for you.
If you are installing the operating system on all nodes yourself, you must do so using the SLES image included in the SUSE OpenStack Cloud 9 package.
In SUSE OpenStack Cloud 9, a local git repository is used to track configuration changes; the Configuration Processor (CP) uses this repository. Use of a git workflow means that your configuration history is maintained, making rollbacks easier and keeping a record of previous configuration settings. The git repository also provides a way for you to merge changes that you pull down as “upstream” updates (that is, updates from SUSE). It also allows you to manage your own configuration changes.
The git repository is installed by the Cloud Lifecycle Manager on the Cloud Lifecycle Manager node.
Using the Install UI does not require the use of the git repository. After the installation, it may be useful to know more about Chapter 22, Using Git for Configuration Management.
21.3 Optional: Creating a CSV File to Import Server Data #
Before beginning the installation, you can create a CSV file with your server information to import directly into the Install UI to avoid entering it manually on the page.
The following table shows the fields needed for your CSV file.
| Field | Required | Required for OS Provisioning | Aliases |
| Server ID | Yes | Yes | server_id, id |
| IP Address | Yes | Yes | ip, ip_address, ip_addr |
| MAC Address | Yes | Yes | mac, mac_address, mac_addr |
| IPMI IP Address | No | Yes | ipmi_ip, ipmi_ip_address |
| IPMI User | No | Yes | ipmi_user, user |
| IPMI Password | No | Yes | ipmi_password, password |
| Server Role | No | No | server_role, role |
| Server Group | No | No | server_group, group |
| NIC Mapping | No | No | server_nic_map, nic_map, nic_mapping |
The aliases are all the valid names that can be used in the CSV file for the
column header for a given field. Field names are not case sensitive. You can
use either (space) or - (hyphen) in
place of underscore for a field name.
An example CSV file could be:
id,ip-addr,mac-address,server-group,nic-mapping,server-role,ipmi-ip,ipmi-user controller1,192.168.110.3,b2:72:8d:ac:7c:6f,RACK1,HP-DL360-4PORT,CONTROLLER-ROLE,192.168.109.3,admin myserver4,10.2.10.24,00:14:22:01:23:44,AZ1,,,,
21.4 Optional: Importing Certificates for SUSE Manager and HPE OneView #
If you intend to use SUSE Manager or HPE OneView to add servers, certificates for those services must be accessible to the Install UI.
Use the following steps to import a SUSE Manager certificate.
Retrieve the
.pemfile from the SUSE Manager.curl -k https://SUSE_MANAGER_IP:PORT/pub/RHN-ORG-TRUSTED-SSL-CERT > PEM_NAME.pem
Copy the
.pemfile to the proper location on the Cloud Lifecycle Manager.cd /etc/pki/trust/anchors sudo cp ~/PEM_NAME.pem .
Install the certificate.
sudo update-ca-certificates
Add SUSE Manager host IP address if SUSE Manager.test.domain is not reachable by DNS.
sudo vi /etc/hosts
Add SUSE Manager host IP address SUSE Manager.test.domain. For example:
10.10.10.10 SUSE Manager.test.domain
Use the following steps to import an HPE OneView certificate.
Retrieve the
sessionID.curl -k -H "X-Api-Version:500" -H "Content-Type: application/json" \ -d '{"userName":ONEVIEW_USER, "password":ONEVIEW_PASSWORD, \ "loginMsgAck":"true"}' https://ONEVIEW_MANAGER_URL:PORT/rest/login-sessionsThe response will be similar to:
{"partnerData":{},"sessionID":"LTYxNjA1O1NjkxMHcI1b2ypaGPscErUOHrl7At3-odHPmR"}Retrieve a Certificate Signing Request (CSR) using the sessionID from Step 1.
curl -k -i -H "X-Api-Version:500" -H sessionID \ ONEVIEW_MANAGER_URL/rest/certificates/ca \ > CA_NAME.csr
Follow instructions in the HPE OneView User Guide to validate the CSR and obtain a signed certificate (CA_NAME
.crt).Copy the
.crtfile to the proper location on the Cloud Lifecycle Manager.cd /etc/pki/trust/anchors sudo cp ~/data/CA_NAME.crt .
Install the certificate.
sudo update-ca-certificates
Follow instructions in your HPE OneView User Guide to import the CA_NAME.crt certificate into HPE OneView.
Add HPE OneView host IP address if HPE OneView.test.domain is not reachable by DNS.
sudo vi /etc/hosts
Add HPE OneView host IP address HPE OneView.test.domain For example:
10.84.84.84 HPE OneView.test.domain
21.5 Running the Install UI #
The Install UI must run continuously without stopping for authentication at any step. When using the Install UI it is required to launch the Cloud Lifecycle Manager with the following command:
ARDANA_INIT_AUTO=1 /usr/bin/ardana-init
Deploying the cloud to your servers will reconfigure networking and firewall
rules on your cloud servers. To avoid problems with these networking changes
when using the Install UI, we recommend you run a browser directly on your
Cloud Lifecycle Manager node and point it to http://localhost:9085.
If you cannot run a browser on the Cloud Lifecycle Manager node to perform the install, you can run a browser from a Linux-based computer in your MANAGEMENT network. However, firewall rules applied during cloud deployment will block access to the Install UI. To avoid blocking the connection, you can use the Install UI via an SSH tunnel to the Cloud Lifecycle Manager server. This will allow SSH connections through the MANAGEMENT network when you reach the "Review Configuration Files" step of the install process.
To open an SSH tunnel from your Linux-based computer in your MANAGEMENT network to the Cloud Lifecycle Manager:
Open a new terminal and enter the following command:
ssh -N -L 8080:localhost:9085 ardana@MANAGEMENT IP address of Cloud Lifecycle Manager
The user name and password should be what was set in Section 15.5.2, “Installing the SUSE OpenStack Cloud Extension”. There will be no prompt after you have logged in.
Leave this terminal session open to keep the SSH tunnel open and running. This SSH tunnel will forward connections from your Linux-based computer directly to the Cloud Lifecycle Manager, bypassing firewall restrictions.
On your local computer (the one you are tunneling from), point your browser to
http://localhost:8080.If the connection is interrupted, refresh your browser.
If you use an SSH tunnel to connect to the Install UI, there is an
important note in the "Review Configuration Files" step about modifying
firewall_rules.yml to allow SSH connections on the
MANAGEMENT network.
Overview#
The first page of the Install UI shows the general installation process and a reminder to gather some information before beginning. Clicking the button brings up the page.
Choose an OpenStack Cloud Model#
The input model choices are displayed on this page. Details of each model can be seen on the right by clicking the model name on the left. If you have already decided some aspects of your cloud environment, models can be filtered using the dropdown selections. Narrowing a parameter affects the range of choices of models and changes other dropdown choices to only those that are compatible.
Selecting a model will determine the base template from which the cloud will be deployed. Models can be adjusted later in the process, though selecting the closest match to your requirements reduces the effort required to deploy your cloud.
If you select any ESX model, extra manual steps are required to avoid configuration failures. While installing an ESX model with the Install UI, you will be asked for interfaces related to ESX and OVSvApp. Those interfaces must be defined before being entered in the Install UI. Instructions are available at Section 27.3, “Overview of ESXi and OVSvApp”.
Installing a Stand-alone Deployer
If you are using the Install UI to install a stand-alone deployer, select that model, which was created previously in Chapter 20, Preparing for Stand-Alone Deployment.
Continue with the remaining Install UI steps to finish installing the stand-alone deployer.
Cloud Model to Deploy#
Based on the cloud example selected on the previous page, more detail is shown about that cloud configuration and the components that will be deployed. If you go back and select a different model, the deployment process restarts from the beginning. Any configuration changes you have made will be deleted.
Mandatory components have assigned quantities. We strongly suggest not changing those quantities to avoid potential problems later in the installation process.
Additional components can be adjusted within the parameters shown.
The number of nodes (servers) dedicated to each server role can be adjusted. Most input models are designed to support High Availability and to distribute OpenStack services appropriately.
Adding Servers and Assigning Server Roles#
This page provides more detail about the number and assignment of each type of node based on the information from the previous page (any changes must be made there).
Components that do not meet the required parameters will be shown in red in the accordion bar. Missing required fields and duplicate server names will also be red, as will the accordion bar. The button will be disabled.
Servers may be discovered using SUSE Manager, HPE OneView, or both. Ensure that the certificates are accessible, as described in Section 21.4, “Optional: Importing Certificates for SUSE Manager and HPE OneView”. Clicking the button will prompt for access credentials to the system management software to be used for discovery. Certificates can be verified by checking . After validating credentials, Discovery will retrieve a list of known servers from SUSE Manager and/or HPE OneView and allow access to server details on those management platforms.
You can drag and drop to move servers from the left to the right in order to assign server roles, from right to left, or up and down in the accordion bar.
Server information may also be entered manually or imported via CSV in the tab. The format for CSV entry is described in Section 21.3, “Optional: Creating a CSV File to Import Server Data”. The server assignment list includes placeholder server details that can be edited to reflect real hardware, or can be removed and replaced with discovered or manually added systems.
For more information about server roles, see Section 5.2.4, “Server Roles”.
Subnet and netmask values should be set on this page as they may impact the IP addresses being assigned to various servers.
Choose servers on which SLES will be installed#
If an OS has not previously been installed on the servers that make up the cloud configuration, the OS installation page allows for Cobbler to deploy SLES on servers in the cloud configuration. Enter password, select servers and click to deploy SLES to these servers. An installation log and progress indicators will be displayed.
Server and Role Summary#
When the OS installation is complete, a Server and Server Role Summary page is displayed. It shows which servers have been assigned to each role, and provides an opportunity to edit the server configurations. Various cloud components can be configured by clicking on the button. Incorrect information will be shown in red.
Below is the list of what can be changed within the Install UI, followed by a list of customizations that can only be changed by directly editing the files on the page. Anything changed directly in the files themselves during the Install UI process will be overwritten by values you have entered with the Install UI.
Changes to the following items can be made:
servers (including SLES installation configuration)
networks
disk models
interface models
NIC mappings
NTP servers
name servers
tags in network groups
Changes to the following items can only be made by manually editing the
associated .yml files on the page of the Install UI:
server groups
server roles
network groups
firewall rules
DNS, SMTP, firewall settings (
cloudConfig.yml)control planes
Directly changing files may cause the configuration to fail validation. During the process of installing with the Install UI, any changes should be made with the tools provided within the Install UI.
Review Configuration Files#
Advanced editing of the cloud configuration can be done on the
Review Configuration Files page. Individual
.yml and .j2 files can be edited
directly with the embedded editor in the and
tabs. The
tab contains the items , and .
This page also provides the ability to set up SUSE Enterprise Storage Integration during initial deployment.
If you are using an SSH tunnel to connect to the Install UI, you will need to make an extra modification here to allow SSH connections through the firewall:
While on the Review Configuration Files page, click on the tab.
Click .
Uncomment the
SSHsection (remove the#at the beginning of the line for the- name: SSHsection).If you do not have such a
- name: SSHsection, manually add the following under thefirewall-rules:section:name: SSH network-groups: - MANAGEMENT rules: - type: allow remote-ip-prefix: 0.0.0.0/0 port-range-min: 22 port-range-max: 22 protocol: tcp
Configure SUSE Enterprise Storage During Initial Deployment
A link to the settings.yml file is available under the
ses selection on the tab.
To set up SUSE Enterprise Storage Integration:
Click on the link to edit the
settings.ymlfile.Uncomment the
ses_config_pathparameter, specify the location on the deployer host containing theses_config.ymlfile, and save thesettings.ymlfile.If the
ses_config.ymlfile does not yet exist in that location on the deployer host, a new link will appear for uploading a file from your local workstation.When
ses_config.ymlis present on the deployer host, it will appear in thesessection of the tab and can be edited directly there.
Manual edits to your configuration files outside of the Install UI may not be reflected in the Install UI. If you make changes to any files directly, refresh the browser to make sure changes are seen by the Install UI.
Before performing the deployment, the configuration must be validated by clicking the button below the list of configuration files on the tab. This ensures the configuration will be successful before the actual configuration process runs and possibly fails. The button also commits any changes. If there are issues with the validation, the configuration processor will provide detailed information about the causes. When validation completes successfully, a message will be displayed that the model is valid. If either validation or commit fail, the button is disabled.
Clicking the button starts the actual deployment process.
Cloud Deployment in Progress#
General progress steps are shown on the left. Detailed activity is shown on the right.
To start the deployment process, the Install UI runs scripts and playbooks based on the actual final configuration. Completed operations are green, black means in process, gray items are not started yet.
The log stream on the right shows finished states. If there are any failures, the log stream will show the errors and the button will be disabled. The and buttons are disabled during the deployment process.
The log files in ~/ardana/.ansible/ansible.log and
/var/cache/ardana_installer/ have debugging
information.
/var/cache/ardana_installer/log/ardana-service/ardana-service.logis created and used during the deployment step.Each of the time-stamped files in
/var/cache/ardana_installer/log/ardana-service/logs/*.logshows the output of a single Ansible playbook run invoked during the UI installation process and the log output for each of those runs.The
~/ardana/.ansible/ansible.logfile is the output of all Ansible playbook runs. This includes the logs from/var/cache/ardana_installer/log/ardana-service/logs/*.log.
When the deployment process is complete, all items on the left will be green. Some deployments will not include all steps shown if they do not apply to the selected input model. In such a situation, those unneeded steps will remain gray.
The button will be enabled when deployment is successful.
Clicking will display the Cloud Deployment
Successful page with information about the deployment, including
the chosen input model and links to cloud management tools.
After installation is complete, shutdown the Install UI by logging into the Cloud Lifecycle Manager and running the following commands:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost installui-stop.yml
After deployment, continue to Chapter 38, Post Installation Tasks and Chapter 44, Other Common Post-Installation Tasks.
To understand cloud configuration more thoroughly and to learn how to make changes later, see:
22 Using Git for Configuration Management #
In SUSE OpenStack Cloud 9, a local git repository is used to track configuration changes; the Configuration Processor (CP) uses this repository. Use of a git workflow means that your configuration history is maintained, making rollbacks easier and keeping a record of previous configuration settings. The git repository also provides a way for you to merge changes that you pull down as “upstream” updates (that is, updates from SUSE). It also allows you to manage your own configuration changes.
The git repository is installed by the Cloud Lifecycle Manager on the Cloud Lifecycle Manager node.
22.1 Initialization on a new deployment #
On a system new to SUSE OpenStack Cloud 9, the Cloud Lifecycle Manager will prepare a git repository
under ~/openstack. The Cloud Lifecycle Manager provisioning runs the
ardana-init-deployer script automatically. This calls
ansible-playbook -i hosts/localhost git-00-initialise.yml.
As a result, the ~/openstack directory is initialized as
a git repo (if it is empty). It is initialized with four empty branches:
- ardana
This holds the upstream source code corresponding to the contents of the
~/openstackdirectory on a pristine installation. Every source code release that is downloaded from SUSE is applied as a fresh commit to this branch. This branch contains no customization by the end user.- site
This branch begins life as a copy of the first
ardanadrop. It is onto this branch that you commit your configuration changes. It is the branch most visible to the end user.- ansible
This branch contains the variable definitions generated by the CP that our main ansible playbooks need. This includes the
verb_hostsfile that describes to ansible what servers are playing what roles. Theready-deploymentplaybook takes this output and assembles a~/scratchdirectory containing the ansible playbooks together with the variable definitions in this branch. The result is a working ansible directory~/scratch/ansible/next/ardana/ansiblefrom which the main deployment playbooks may be successfully run.- cp-persistent
This branch contains the persistent state that the CP needs to maintain. That state is mostly the assignment of IP addresses and roles to particular servers. Some operational procedures may involve editing the contents of this branch: for example, retiring a machine from service or repurposing it.
Two temporary branches are created and populated at run time:
- staging-ansible
This branch hosts the most recent commit that will be appended to the Ansible branch.
- staging-cp-persistent
This branch hosts the most recent commit that will be appended to the cp-persistent branch.
The information above provides insight into the workings of the configuration processor and the git repository. However, in practice you can simply follow the steps below to make configuration changes.
22.2 Updating any configuration, including the default configuration #
When you need to make updates to a configuration you must:
Check out the
sitebranch. You may already be on that branch. If so, git will tell you that and the command will leave you there.git checkout site
Edit the YAML file or files that contain the configuration you want to change.
Commit the changes to the
sitebranch.git add -A git commit -m "your commit message goes here in quotes"
If you want to add a single file to your git repository, you can use the command below, as opposed to using
git add -A.git add PATH_TO_FILE
For example, if you made a change to your
servers.ymlfile and wanted to only commit that change, you would use this command:git add ~/openstack/my_cloud/definition/data/servers.yml
To produce the required configuration processor output from those changes. Review the output files manually if required, run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
Ready the deployment area
ansible-playbook -i hosts/localhost ready-deployment.yml
Run the deployment playbooks from the resulting scratch directory.
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts site.yml
22.3 Resolving Git merge conflicts #
When you make changes, SUSE OpenStack Cloud attempts to incorporate new or updated
configuration information on top of your existing environment. However, with
some changes to your environment, SUSE OpenStack Cloud cannot automatically
determine whether to keep your changes or drop them in favor of the new or
updated configurations. This will result in merge
conflicts, and it will be up to you to manually resolve the
conflicts before you can proceed. This is common, but it can be
confusing. Git provides a way to resolve these situations.
This section gives an overview of how to approach the issue of merge conflicts, showing general procedures for determining where the conflict is occurring, alternative methods for resolution, and a fallback procedure for the case where the resolution goes wrong and you need to start changes from the beginning.
For a general overview of how SUSE OpenStack Cloud uses Git, see the introductory
article Chapter 22, Using Git for Configuration Management. In particular, note how the
site branch is the one most used by the end-user, while
the ardana branch contains the "upstream" source code
corresponding to the contents of the ~/openstack
directory on a pristine fresh installation.
22.3.1 Identifying the occurrence of a merge conflict #
If you get a merge conflict, you will observe output
similar to the following on the console:
Auto-merging ardana/ansible/roles/nova-compute-esx/defaults/main.yml
Auto-merging ardana/ansible/roles/nova-common/templates/nova.conf.j2
CONFLICT (content): Merge conflict in ardana/ansible/roles/nova-common/templates/nova.conf.j2
Auto-merging ardana/ansible/roles/nova-cli/tasks/availability_zones.yml
Auto-merging ardana/ansible/roles/nova-api/templates/api-paste.ini.j222.3.2 Examining Conflicts #
Use git status to discover the source of the problem:
...
new file: tech-preview/entry-scale-kvm-mml/data/swift/swift_config.yml
modified: tech-preview/mid-scale/README.md
modified: tech-preview/mid-scale/data/control_plane.yml
Unmerged paths:
(use "git add/rm <file>..." as appropriate to mark resolution)
both modified: ardana/ansible/roles/nova-common/templates/nova.conf.j2
Edit the file
ardana/ansible/roles/nova-common/templates/nova.conf.j2
to see the conflict markers:
[neutron]
admin_auth_url = {{ neutron_admin_auth_url }}
admin_password = {{ neutron_admin_password }}
admin_tenant_name = {{ neutron_admin_tenant_name }}
admin_username = {{ neutron_admin_username }}
<<<<<<<HEAD
metadata_proxy_shared_secret = top_secret_password111
=======
metadata_proxy_shared_secret = {{ neutron_metadata_proxy_shared_secret }}
>>>>>>> ardana
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
service_metadata_proxy = True
This indicates that SUSE OpenStack Cloud 9is trying to set the value of
metadata_proxy_shared_secret to be {{
neutron_metadata_proxy_shared_secret }} whereas previously you
have set its value to top_secret_password111.
22.3.3 Examining differences between your current version and the previous upstream version #
Typically, the previous upstream version will be the last-but-one commit on
the ardana branch. This version will have been created
during the initial installation of your cloud (or perhaps during a previous
upgrade or configuration change). So in total, there are three significant
versions of the file:
The previous "upstream" version on the
ardanabranch.Your current version on the
sitebranch.The new "upstream" version on the
ardanabranch.
You can identify the commit number of the previous "upstream" version using
git merge-base.
tux > git merge-base ardana site
2eda1df48e2822533c50f80f5bfd7a9d788bdf73
And then use git log to see where this commit occurs in
the history of the ardana branch.
tux > git log ardana --
commit 22cfa83f3526baf30b3697e971a712930f86f611
Author: Openstack git user <openstack@example.com>
Date: Mon Jan 18 00:30:33 2018 +0000
New drop
commit 2eda1df48e2822533c50f80f5bfd7a9d788bdf73
Author: Openstack git user <openstack@example.com>
Date: Sun Jan 17 19:14:01 2018 +0000
New drop
In this instance, we can see that the relevant commit is in fact the
last-but-one commit. We can use the simplified name
ardana^1 to identify that commit.
tux > git diff ardana^1 HEAD -- ardana/ansible/roles/nova-common/templates/nova.conf.j2
In the diff output, you should be able to see how you changed the value for
metadata_proxy_shared_secret from
unset to top_secret_password111:
tux > diff --git a/ardana/ansible/roles/nova-common/templates/nova.conf.j2 b/ardana/ansible/roles/nova-common/templates/nova.conf.j2
index 597a982..05cb07c 100644
--- a/ardana/ansible/roles/nova-common/templates/nova.conf.j2
+++ b/ardana/ansible/roles/nova-common/templates/nova.conf.j2
@@ -132,7 +132,7 @@ admin_auth_url = {{ neutron_admin_auth_url }}
admin_password = {{ neutron_admin_password }}
admin_tenant_name = {{ neutron_admin_tenant_name }}
admin_username = {{ neutron_admin_username }}
-metadata_proxy_shared_secret = unset
+metadata_proxy_shared_secret = top_secret_password111
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
service_metadata_proxy = True22.3.4 Examining differences between your current version and the new upstream version #
To compare your change with the new upstream version from SUSE OpenStack Cloud 9 on
the ardana branch you can use git diff HEAD
ardana -- <<path/to/file>>:
tux > git diff HEAD ardana -- ardana/ansible/roles/nova-common/templates/nova.conf.j2
In the extract of output below, you can see your value
top_secret_password111 and the new value {{
neutron_metadata_proxy_shared_secret }} that SUSE OpenStack Cloud 9 wants
to set.
..
admin_username = {{ neutron_admin_username }}
-metadata_proxy_shared_secret = top_secret_password111
+metadata_proxy_shared_secret = {{ neutron_metadata_proxy_shared_secret }}
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt22.3.5 Examining differences between the new upstream version and the previous upstream version #
To compare the new upstream version from SUSE OpenStack Cloud 9 with the previous upstream version from your initial install (or previous change):
tux > git diff $(git merge-base ardana HEAD) ardana -- ardana/ansible/roles/nova-common/templates/nova.conf.j2
In the extract of output below, you can see the new upstream value
{{ neutron_metadata_proxy_shared_secret }} that
SUSE OpenStack Cloud 9 wants to set and the previous upstream value
unset.
admin_password = {{ neutron_admin_password }}
admin_tenant_name = {{ neutron_admin_tenant_name }}
admin_username = {{ neutron_admin_username }}
-metadata_proxy_shared_secret = unset
+metadata_proxy_shared_secret = {{ neutron_metadata_proxy_shared_secret }}
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt22.3.6 Using stage markers to view clean versions of files (without conflict markers) #
You can use the git show command with stage markers to
view files without having conflict markers embedded in them. Stage 1 is the
previous upstream version (:1), stage 2 is
your current version (:2) while stage 3 is
the new upstream version (:3).
Stage 1
tux > git show :1:ardana/ansible/roles/nova-common/templates/nova.conf.j2...
admin_username = {{ neutron_admin_username }}
metadata_proxy_shared_secret = unset
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
...Stage 2
tux > git show :2:ardana/ansible/roles/nova-common/templates/nova.conf.j2...
admin_username = {{ neutron_admin_username }}
metadata_proxy_shared_secret = top_secret_password111
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
...Stage 3
tux > git show :3:ardana/ansible/roles/nova-common/templates/nova.conf.j2...
admin_username = {{ neutron_admin_username }}
metadata_proxy_shared_secret = {{ neutron_metadata_proxy_shared_secret }}
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
...22.3.7 Resolving the conflict #
There are two approaches to resolving the conflict:
Edit the merged file containing the conflict markers, keeping the change you want to preserve and removing the conflict markers and any changes you want to discard.
Take the new upstream version of the file and re-apply any changes you would like to keep from your current version.
22.3.8 Resolving the conflict - editing the file containing the conflict markers #
Edit the file
ardana/ansible/roles/nova-common/templates/nova.conf.j2
and if you want to maintain your change, then delete the lines in bold
below:
[neutron]
admin_auth_url = {{ neutron_admin_auth_url }}
admin_password = {{ neutron_admin_password }}
admin_tenant_name = {{ neutron_admin_tenant_name }}
admin_username = {{ neutron_admin_username }}
<<<<<<<HEAD
metadata_proxy_shared_secret = top_secret_password111
=======
metadata_proxy_shared_secret = {{ neutron_metadata_proxy_shared_secret }}
>>>>>>> ardana
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
service_metadata_proxy = TrueYour file should now look like this:
[neutron]
admin_auth_url = {{ neutron_admin_auth_url }}
admin_password = {{ neutron_admin_password }}
admin_tenant_name = {{ neutron_admin_tenant_name }}
admin_username = {{ neutron_admin_username }}
metadata_proxy_shared_secret = top_secret_password111
neutron_auth_strategy = keystone
neutron_ca_certificates_file = /etc/ssl/certs/ca-certificates.crt
service_metadata_proxy = True22.3.9 Resolving the conflict - re-applying your changes to new upstream version #
Create a copy of the new upstream version (see Stage 3 above) in your working directory:
tux > git show :3:ardana/ansible/roles/nova-common/templates/nova.conf.j2 > \
ardana/ansible/roles/nova-common/templates/nova.conf.j2
Now edit the file
ardana/ansible/roles/nova-common/templates/nova.conf.j2
and manually re-apply the changes you want.
22.3.10 Completing the merge procedure #
You may want to check that the changes you have applied are correct. Compare the new upstream version with the version in your working directory:
tux > git diff ardana -- ardana/ansible/roles/nova-common/templates/nova.conf.j2If you are happy with the resolution, you can stage your changes using:
tux > git add ardana/ansible/roles/nova-common/templates/nova.conf.j2Apply the above steps to all the merge conflicts you encounter, and when you have them resolved to your satisfaction, complete the merge:
git commit -m "complete merge"
22.3.11 Recovering from Errors #
If you make a mistake during the resolution process, you can return your
working directory to a clean copy of the site branch
using:
tux > git reset --hard
If the new upstream version contains files that did not exist in the previous
version, these files will be left behind - you can see them using
git status. To clean up these files, remove them and then
reset:
tux >git rm -rf ardanatux >git reset --hard
Alternatively, you can use git stash to save these files
to a transient stash queue.
23 Installing a Stand-Alone Cloud Lifecycle Manager #
23.1 Important Notes #
For information about when to use the GUI installer and when to use the command line (CLI), see Chapter 13, Overview.
Review the Chapter 2, Hardware and Software Support Matrix that we have listed.
Review the release notes to make yourself aware of any known issues and limitations.
The installation process can occur in different phases. For example, you can install the control plane only and then add Compute nodes afterwards if you would like.
If you run into issues during installation, we have put together a list of Chapter 36, Troubleshooting the Installation you can reference.
Make sure all disks on the system(s) are wiped before you begin the install. (For swift, refer to Section 11.6, “Swift Requirements for Device Group Drives”.)
There is no requirement to have a dedicated network for OS-install and system deployment, this can be shared with the management network. More information can be found in Chapter 9, Example Configurations.
The terms deployer and Cloud Lifecycle Manager are used interchangeably. They refer to the same nodes in your cloud environment.
When running the Ansible playbook in this installation guide, if a runbook fails you will see in the error response to use the
--limitswitch when retrying a playbook. This should be avoided. You can simply re-run any playbook without this switch.DVR is not supported with ESX compute.
When you attach a cinder volume to the VM running on the ESXi host, the volume will not get detected automatically. Make sure to set the image metadata vmware_adaptertype=lsiLogicsas for image before launching the instance. This will help to discover the volume change appropriately.
The installation process will create several OpenStack roles. Not all roles will be relevant for a cloud with swift only, but they will not cause problems.
23.2 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
23.3 Configuring Your Environment #
You have already configured an input model for a stand-alone deployer in a previous step (Chapter 20, Preparing for Stand-Alone Deployment). Now that input model needs to be moved into the setup directory.
ardana >cp -r ~/openstack/examples/entry-scale-kvm-stand-alone-deployer/* \ ~/openstack/my_cloud/definition/(Optional) You can use the
ardanaencrypt.pyscript to encrypt your IPMI passwords. This script uses OpenSSL.Change to the Ansible directory:
ardana >cd ~/openstack/ardana/ansibleEnter the encryption key into the following environment variable:
ardana >export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>Run the python script below and follow the instructions. Enter a password that you want to encrypt.
ardana >./ardanaencrypt.pyTake the string generated and place it in the
ilo-passwordfield in your~/openstack/my_cloud/definition/data/servers.ymlfile, remembering to enclose it in quotes.Repeat the above for each server.
NoteBefore you run any playbooks, remember that you need to export the encryption key in the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"ImportantThis step needs to be repeated any time you make changes to your configuration files before you move on to the following steps. See Chapter 22, Using Git for Configuration Management for more information.
23.4 Running the Configuration Processor #
Once you have your configuration files setup, you need to run the configuration processor to complete your configuration.
When you run the configuration processor, you will be prompted for two
passwords. Enter the first password to make the configuration processor
encrypt its sensitive data, which consists of the random inter-service
passwords that it generates and the ansible group_vars
and host_vars that it produces for subsequent deploy
runs. You will need this password for subsequent Ansible deploy and
configuration processor runs. If you wish to change an encryption password
that you have already used when running the configuration processor then
enter the new password at the second prompt, otherwise just press
Enter to bypass this.
Run the configuration processor with this command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml
For automated installation (for example CI), you can specify the required passwords on the ansible command line. For example, the command below will disable encryption by the configuration processor:
ardana > ansible-playbook -i hosts/localhost config-processor-run.yml \
-e encrypt="" -e rekey=""If you receive an error during this step, there is probably an issue with one or more of your configuration files. Verify that all information in each of your configuration files is correct for your environment. Then commit those changes to Git using the instructions in the previous section before re-running the configuration processor again.
For any troubleshooting information regarding these steps, see Section 36.2, “Issues while Updating Configuration Files”.
23.5 Configuring TLS #
This section is optional, but recommended, for a SUSE OpenStack Cloud installation.
After you run the configuration processor the first time, the IP addresses
for your environment will be generated and populated in the
~/openstack/my_cloud/info/address_info.yml file. At
this point, consider whether to configure TLS and set up an SSL certificate
for your environment. Please read Chapter 41, Configuring Transport Layer Security (TLS) before proceeding
for how to achieve this.
23.6 Deploying the Cloud #
Use the playbook below to create a deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
[OPTIONAL] - Run the
wipe_disks.ymlplaybook to ensure all of your non-OS partitions on your nodes are completely wiped before continuing with the installation. Thewipe_disks.ymlplaybook is only meant to be run on systems immediately after runningbm-reimage.yml. If used for any other case, it may not wipe all of the expected partitions.If you are using fresh machines this step may not be necessary.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts wipe_disks.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts wipe_disks.yml --ask-vault-passRun the
site.ymlplaybook below:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts site.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts site.yml --ask-vault-passNoteThe step above runs
osconfigto configure the cloud andardana-deployto deploy the cloud. Therefore, this step may run for a while, perhaps 45 minutes or more, depending on the number of nodes in your environment.Verify that the network is working correctly. Ping each IP in the
/etc/hostsfile from one of the controller nodes.
For any troubleshooting information regarding these steps, see Section 36.3, “Issues while Deploying the Cloud”.
23.7 Installing OpenStack Assets on the Stand-alone Deployer #
The OpenStack CLI and OpenStack clients will not be installed automatically. If you require access to these clients, you will need to follow the procedure below to add the appropriate software.
[OPTIONAL] To confirm that OpenStack clients have not been installed, connect to your stand-alone deployer and try to use the OpenStack CLI:
ardana >source ~/keystone.osrcardana >openstack project list -bash: openstack: command not foundEdit the configuration file containing details of your Control Plane,
~/openstack/my_cloud/definition/data/control_plane.ymlLocate the stanza for the cluster where you want to install the client(s). This will look like the following extract:
clusters: - name: cluster0 cluster-prefix: c0 server-role: LIFECYCLE-MANAGER-ROLE member-count: 1 allocation-policy: strict service-components: - ntp-server - lifecycle-managerChoose the client(s) you wish to install from the following list of available clients:
- barbican-client - ceilometer-client - cinder-client - designate-client - glance-client - heat-client - ironic-client - keystone-client - magnum-client - manila-client - monasca-client - neutron-client - nova-client - ntp-client - octavia-client - openstack-client - swift-client
Add the client(s) to the list of
service-components- in the following example, several OpenStack clients are added to the stand-alone deployer:clusters: - name: cluster0 cluster-prefix: c0 server-role: LIFECYCLE-MANAGER-ROLE member-count: 1 allocation-policy: strict service-components: - ntp-server - lifecycle-manager - openstack-client - cinder-client - designate-client - glance-client - heat-client - ironic-client - keystone-client - neutron-client - nova-client - swift-client - monasca-client - barbican-clientCommit the configuration changes:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "Add explicit client service deployment"Run the configuration processor, followed by the
ready-deploymentplaybook:ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml -e encrypt="" \ -e rekey=""ardana >ansible-playbook -i hosts/localhost ready-deployment.ymlAdd the software for the clients using the following command:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts clients-upgrade.ymlCheck that the software has been installed correctly. Using the same test that was unsuccessful before, connect to your stand-alone deployer and try to use the OpenStack CLI:
ardana >source ~/keystone.osrcardana >openstack project listYou should now see a list of projects returned:
ardana >openstack project list +----------------------------------+------------------+ | ID | Name | +----------------------------------+------------------+ | 076b6e879f324183bbd28b46a7ee7826 | kronos | | 0b81c3a9e59c47cab0e208ea1bb7f827 | backup | | 143891c2a6094e2988358afc99043643 | octavia | | 1d3972a674434f3c95a1d5ed19e0008f | glance-swift | | 2e372dc57cac4915bf06bbee059fc547 | glance-check | | 383abda56aa2482b95fb9da0b9dd91f4 | monitor | | 606dd3b1fa6146668d468713413fb9a6 | swift-monitor | | 87db9d1b30044ea199f0293f63d84652 | admin | | 9fbb7494956a483ca731748126f50919 | demo | | a59d0c682474434a9ddc240ddfe71871 | services | | a69398f0f66a41b2872bcf45d55311a7 | swift-dispersion | | f5ec48d0328d400992c1c5fb44ec238f | cinderinternal | +----------------------------------+------------------+
23.8 Post-Installation Verification and Administration #
We recommend verifying the installation using the instructions in Chapter 38, Post Installation Tasks.
There are also a list of other common post-installation administrative tasks listed in the Chapter 44, Other Common Post-Installation Tasks list.
24 Installing Mid-scale and Entry-scale KVM #
24.1 Important Notes #
For information about when to use the GUI installer and when to use the command line (CLI), see Chapter 13, Overview.
Review the Chapter 2, Hardware and Software Support Matrix that we have listed.
Review the release notes to make yourself aware of any known issues and limitations.
The installation process can occur in different phases. For example, you can install the control plane only and then add Compute nodes afterwards if you would like.
If you run into issues during installation, we have put together a list of Chapter 36, Troubleshooting the Installation you can reference.
Make sure all disks on the system(s) are wiped before you begin the install. (For swift, refer to Section 11.6, “Swift Requirements for Device Group Drives”.)
There is no requirement to have a dedicated network for OS-install and system deployment, this can be shared with the management network. More information can be found in Chapter 9, Example Configurations.
The terms deployer and Cloud Lifecycle Manager are used interchangeably. They refer to the same nodes in your cloud environment.
When running the Ansible playbook in this installation guide, if a runbook fails you will see in the error response to use the
--limitswitch when retrying a playbook. This should be avoided. You can simply re-run any playbook without this switch.DVR is not supported with ESX compute.
When you attach a cinder volume to the VM running on the ESXi host, the volume will not get detected automatically. Make sure to set the image metadata vmware_adaptertype=lsiLogicsas for image before launching the instance. This will help to discover the volume change appropriately.
The installation process will create several OpenStack roles. Not all roles will be relevant for a cloud with swift only, but they will not cause problems.
24.2 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
24.3 Configuring Your Environment #
During the configuration phase of the installation you will be making
modifications to the example configuration input files to match your cloud
environment. You should use the Chapter 9, Example Configurations
documentation for detailed information on how to do this. There is also a
README.md file included in each of the example
directories on the Cloud Lifecycle Manager that has useful information about the models.
In the steps below we show how to set up the directory structure with the example input files as well as use the optional encryption methods for your sensitive data.
Set up your configuration files, as follows:
Copy the example configuration files into the required setup directory and edit them to contain the details of your environment.
For example, if you want to use the SUSE OpenStack Cloud Mid-scale KVM model, you can use this command to copy the files to your cloud definition directory:
ardana >cp -r ~/openstack/examples/mid-scale-kvm/* \ ~/openstack/my_cloud/definition/If you want to use the SUSE OpenStack Cloud Entry-scale KVM model, you can use this command to copy the files to your cloud definition directory:
ardana >cp -r ~/openstack/examples/entry-scale-kvm/* \ ~/openstack/my_cloud/definition/Begin inputting your environment information into the configuration files in the
~/openstack/my_cloud/definitiondirectory.
(Optional) You can use the
ardanaencrypt.pyscript to encrypt your IPMI passwords. This script uses OpenSSL.Change to the Ansible directory:
ardana >cd ~/openstack/ardana/ansiblePut the encryption key into the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Run the python script below and follow the instructions. Enter a password that you want to encrypt.
ardana >./ardanaencrypt.pyTake the string generated and place it in the
ilo-passwordfield in your~/openstack/my_cloud/definition/data/servers.ymlfile, remembering to enclose it in quotes.Repeat the above for each server.
NoteBefore you run any playbooks, remember that you need to export the encryption key in the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"ImportantThis step needs to be repeated any time you make changes to your configuration files before you move on to the following steps. See Chapter 22, Using Git for Configuration Management for more information.
24.4 Provisioning Your Baremetal Nodes #
To provision the baremetal nodes in your cloud deployment you can either use the automated operating system installation process provided by SUSE OpenStack Cloud or you can use the 3rd party installation tooling of your choice. We will outline both methods below:
24.4.1 Using Third Party Baremetal Installers #
If you do not wish to use the automated operating system installation tooling included with SUSE OpenStack Cloud then the requirements that have to be met using the installation tooling of your choice are:
The operating system must be installed via the SLES ISO provided on the SUSE Customer Center.
Each node must have SSH keys in place that allows the same user from the Cloud Lifecycle Manager node who will be doing the deployment to SSH to each node without a password.
Passwordless sudo needs to be enabled for the user.
There should be a LVM logical volume as
/rooton each node.If the LVM volume group name for the volume group holding the
rootLVM logical volume isardana-vg, then it will align with the disk input models in the examples.Ensure that
openssh-server,python,python-apt, andrsyncare installed.
If you chose this method for installing your baremetal hardware, skip forward to the step Running the Configuration Processor.
24.4.2 Using the Automated Operating System Installation Provided by SUSE OpenStack Cloud #
If you would like to use the automated operating system installation tools provided by SUSE OpenStack Cloud, complete the steps below.
24.4.2.1 Deploying Cobbler #
This phase of the install process takes the baremetal information that was
provided in servers.yml and installs the Cobbler
provisioning tool and loads this information into Cobbler. This sets each
node to netboot-enabled: true in Cobbler. Each node
will be automatically marked as netboot-enabled: false
when it completes its operating system install successfully. Even if the
node tries to PXE boot subsequently, Cobbler will not serve it. This is
deliberate so that you cannot reimage a live node by accident.
The cobbler-deploy.yml playbook prompts for a password
- this is the password that will be encrypted and stored in Cobbler, which
is associated with the user running the command on the Cloud Lifecycle Manager, that you
will use to log in to the nodes via their consoles after install. The
username is the same as the user set up in the initial dialogue when
installing the Cloud Lifecycle Manager from the ISO, and is the same user that is running
the cobbler-deploy play.
When imaging servers with your own tooling, it is still necessary to have
ILO/IPMI settings for all nodes. Even if you are not using Cobbler, the
username and password fields in servers.yml need to
be filled in with dummy settings. For example, add the following to
servers.yml:
ilo-user: manual ilo-password: deployment
Run the following playbook which confirms that there is IPMI connectivity for each of your nodes so that they are accessible to be re-imaged in a later step:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-power-status.ymlRun the following playbook to deploy Cobbler:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.yml
24.4.2.2 Imaging the Nodes #
This phase of the install process goes through a number of distinct steps:
Powers down the nodes to be installed
Sets the nodes hardware boot order so that the first option is a network boot.
Powers on the nodes. (The nodes will then boot from the network and be installed using infrastructure set up in the previous phase)
Waits for the nodes to power themselves down (this indicates a successful install). This can take some time.
Sets the boot order to hard disk and powers on the nodes.
Waits for the nodes to be reachable by SSH and verifies that they have the signature expected.
Deploying nodes has been automated in the Cloud Lifecycle Manager and requires the following:
All of your nodes using SLES must already be installed, either manually or via Cobbler.
Your input model should be configured for your SLES nodes.
You should have run the configuration processor and the
ready-deployment.ymlplaybook.
Execute the following steps to re-image one or more nodes after you have
run the ready-deployment.yml playbook.
Run the following playbook, specifying your SLES nodes using the nodelist. This playbook will reconfigure Cobbler for the nodes listed.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook prepare-sles-grub2.yml -e \ nodelist=node1[,node2,node3]Re-image the node(s) with the following command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml \ -e nodelist=node1[,node2,node3]
If a nodelist is not specified then the set of nodes in Cobbler with
netboot-enabled: True is selected. The playbook pauses
at the start to give you a chance to review the set of nodes that it is
targeting and to confirm that it is correct.
You can use the command below which will list all of your nodes with the
netboot-enabled: True flag set:
sudo cobbler system find --netboot-enabled=1
24.5 Running the Configuration Processor #
Once you have your configuration files setup, you need to run the configuration processor to complete your configuration.
When you run the configuration processor, you will be prompted for two
passwords. Enter the first password to make the configuration processor
encrypt its sensitive data, which consists of the random inter-service
passwords that it generates and the ansible group_vars
and host_vars that it produces for subsequent deploy
runs. You will need this password for subsequent Ansible deploy and
configuration processor runs. If you wish to change an encryption password
that you have already used when running the configuration processor then
enter the new password at the second prompt, otherwise just press
Enter to bypass this.
Run the configuration processor with this command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml
For automated installation (for example CI), you can specify the required passwords on the ansible command line. For example, the command below will disable encryption by the configuration processor:
ardana > ansible-playbook -i hosts/localhost config-processor-run.yml \
-e encrypt="" -e rekey=""If you receive an error during this step, there is probably an issue with one or more of your configuration files. Verify that all information in each of your configuration files is correct for your environment. Then commit those changes to Git using the instructions in the previous section before re-running the configuration processor again.
For any troubleshooting information regarding these steps, see Section 36.2, “Issues while Updating Configuration Files”.
24.6 Configuring TLS #
This section is optional, but recommended, for a SUSE OpenStack Cloud installation.
After you run the configuration processor the first time, the IP addresses
for your environment will be generated and populated in the
~/openstack/my_cloud/info/address_info.yml file. At
this point, consider whether to configure TLS and set up an SSL certificate
for your environment. Please read Chapter 41, Configuring Transport Layer Security (TLS) before proceeding
for how to achieve this.
24.7 Deploying the Cloud #
Use the playbook below to create a deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
[OPTIONAL] - Run the
wipe_disks.ymlplaybook to ensure all of your non-OS partitions on your nodes are completely wiped before continuing with the installation. Thewipe_disks.ymlplaybook is only meant to be run on systems immediately after runningbm-reimage.yml. If used for any other case, it may not wipe all of the expected partitions.If you are using fresh machines this step may not be necessary.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts wipe_disks.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts wipe_disks.yml --ask-vault-passRun the
site.ymlplaybook below:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts site.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts site.yml --ask-vault-passNoteThe step above runs
osconfigto configure the cloud andardana-deployto deploy the cloud. Therefore, this step may run for a while, perhaps 45 minutes or more, depending on the number of nodes in your environment.Verify that the network is working correctly. Ping each IP in the
/etc/hostsfile from one of the controller nodes.
For any troubleshooting information regarding these steps, see Section 36.3, “Issues while Deploying the Cloud”.
24.8 Configuring a Block Storage Backend #
SUSE OpenStack Cloud supports multiple Block Storage backend options. You can use one or more of these for setting up multiple Block Storage backends. Multiple volume types are also supported. For more information on configuring backends, see Configure multiple-storage back ends
default_volume_type #Create a volume type:
openstack volume type create --public NAME
Volume types do not have to be tied to a backend. They can contain attributes that can be applied to a volume during creation, these are referred to as extra specs. One of those attributes is the
volume_backend_name. By setting the value to the same as thevolume_backend_nameof a specific backend as defined incinder.conf, then volumes created with that type will always land on that backend. For example, if thecinder.confhas an LVM volume backend defined as:[lvmdriver-1] image_volume_cache_enabled = True volume_clear = zero lvm_type = auto target_helper = lioadm volume_group = stack-volumes-lvmdriver-1 volume_driver = cinder.volume.drivers.lvm.LVMVolumeDriver volume_backend_name = lvmdriver-1You can tie a volume type to that specific backend by doing:
$ openstack volume type create --public my_lvm_type $ openstack volume type set --property volume_backend_name=lvmdriver-1 my_lvm_type $ openstack volume type show my_lvm_type +--------------------+--------------------------------------+ | Field | Value | +--------------------+--------------------------------------+ | access_project_ids | None | | description | None | | id | a2049509-7789-4949-95e2-89cf7fd5792f | | is_public | True | | name | my_lvm_type | | properties | volume_backend_name='lvmdriver-1' | | qos_specs_id | None | +--------------------+--------------------------------------+
24.9 Post-Installation Verification and Administration #
We recommend verifying the installation using the instructions in Chapter 38, Post Installation Tasks.
There are also a list of other common post-installation administrative tasks listed in the Chapter 44, Other Common Post-Installation Tasks list.
25 DNS Service Installation Overview #
The SUSE OpenStack Cloud DNS Service supports several different backends for domain name service. The choice of backend must be included in the deployment model before the SUSE OpenStack Cloud install is completed.
By default any user in the project is allowed to manage a DNS domain. This can be changed by updating the Policy.json file for designate.
The backends that are available within the DNS Service are separated into two categories, self-contained and external.
| Category | Backend | Description | Recommended For |
|---|---|---|---|
| Self-contained | BIND 9.x | All components necessary will be installed and configured as part of the SUSE OpenStack Cloud install. | POCs and customers who wish to keep cloud and traditional DNS separated. |
| External | InfoBlox | The authoritative DNS server itself is external to SUSE OpenStack Cloud. Management and configuration is out of scope for the Cloud Lifecycle Manager but remains the responsibility of the customer. | Customers who wish to integrate with their existing DNS infrastructure. |
25.1 Installing the DNS Service with BIND #
SUSE OpenStack Cloud DNS Service defaults to the BIND back-end if another back-end is not configured for domain name service. BIND will be deployed to one or more control planes clusters. The following configuration example shows how the BIND service is installed.
25.1.1 Configuring the Back-end #
Ensure the DNS Service components and the BIND component have been placed on a cluster. BIND can be placed on a cluster separate from the other DNS service components.
control-planes:
- name: control-plane-1
region-name: region1
clusters:
- name: cluster1
service-components:
- lifecycle-manager
- mariadb
- ip-cluster
- apache2
- ...
- designate-api
- designate-central
- designate-pool-manager
- designate-zone-manager
- designate-mdns
- designate-client
- bindUpdating the Input Model
When the back-end is configured, add bind-ext to the file
network_groups.yml.
Edit
~/openstack/my_cloud/definition/data/network_groups.ymlto addbind-extto component-endpoints.name: EXTERNAL-API hostname-suffix: extapi component-endpoints: - bind-ext
Save the file.
25.2 Install the DNS Service with PowerDNS #
25.2.1 Installing DNS Service with PowerDNS #
SUSE OpenStack Cloud DNS Service and PowerDNS can be installed together instead of the default BIND backend. PowerDNS will be deployed to one or more control planes clusters. The following configuration example shows how the PowerDNS service is installed.
25.2.2 Configure the Backend #
To configure the backend for PowerDNS, follow these steps.
Ensure the DNS Service components and the PowerDNS component have been placed on a cluster. PowerDNS may be placed on a separate cluster to the other DNS Service components. Ensure the default bind component has been removed.
control-planes: - name: control-plane-1 region-name: region1 clusters: - name: cluster1 service-components: - lifecycle-manager - mariadb - ip-cluster - apache2 - ... - designate-api - designate-central - designate-pool-manager - designate-zone-manager - designate-mdns - designate-client - powerdnsEdit the
~/openstack/my_cloud/definitions/data/network_groups.ymlfile to include the powerdns-ext.- name: EXTERNAL-API hostname-suffix: extapi component-endpoints: - powerdns-ext load-balancers: - provider: ip-cluster
Edit the
~/openstack/my_cloud/definitions/data/firewall_rules.ymlto allow UDP/TCP access.- name: DNSudp # network-groups lists the network group names that the rules apply to network-groups: - EXTERNAL-API rules: - type: allow # range of remote addresses in CIDR format that this rule applies to remote-ip-prefix: 0.0.0.0/0 port-range-min: 53 port-range-max: 53 protocol: udp - name: DNStcp # network-groups lists the network group names that the rules apply to network-groups: - EXTERNAL-API rules: - type: allow # range of remote addresses in CIDR format that this rule applies to remote-ip-prefix: 0.0.0.0/0 port-range-min: 53 port-range-max: 53 protocol: tcp
Please see Book “Operations Guide CLM”, Chapter 10 “Managing Networking”, Section 10.3 “DNS Service Overview”, Section 10.3.2 “designate Initial Configuration” for post-installation DNS Service configuration.
25.3 Configure DNS Domain and NS Records #
To configure the default DNS domain and Name Server records for the default pool, follow these steps.
Ensure that
designate_config.ymlfile is present in the~/openstack/my_cloud/definition/data/designatefolder. If the file or folder is not present, create the folder and copydesignate_config.ymlfile from one of the example input models (for example,~/openstack/examples/entry-scale-kvm/data/designate/designate_config.yml).Modify the dns_domain and/or ns_records entries in the
designate_config.ymlfile.data: dns_domain: example.org. ns_records: hostname: ns1.example.org. priority: 1 hostname: ns2.example.org. priority: 2Edit your input model's
control_plane.ymlfile to include DESIGNATE-CONFIG-CP1 in configuration-data section.control-planes: - name: control-plane-1 region-name: region1 lifecycle-manager-target configuration-data: - DESIGNATE-CONFIG-CP1 - NEUTRON-CONFIG-CP1Continue your cloud deployment by reviewing and committing your changes.
$ git add ~/openstack/my_cloud/definition/data/designate/designate_config.yml $ git commit -m "Adding DNS Domain and NS Records"
In an entry-scale model (Section 9.3.1, “Entry-Scale Cloud”), you will have 3 ns_records since the DNS service runs on all three control planes.
In a mid-scale model (Section 9.3.3, “Single-Region Mid-Size Model”) or dedicated metering, monitoring and logging model (Section 9.3.2, “Entry Scale Cloud with Metering and Monitoring Services”), the above example would be correct since there are only two controller nodes.
25.4 Migrate Zone/Pool to Worker/Producer after Upgrade #
After upgrade, the following steps may be used to migrate the zone/pool scheme to the worker/producer scheme:
Log in to the Cloud Lifecycle Manager.
Edit the file
~/openstack/my_cloud/definitions/data/control_plane.ymlto replacedesignate-pool-managertodesignate-workeranddesignate-zone-managertodesignate-producercontrol-planes: - name: control-plane-1 region-name: region1 clusters: - name: cluster1 service-components: - lifecycle-manager - mariadb - ip-cluster - apache2 - ... - designate-api - designate-central - designate-worker - designate-producer - designate-mdns - designate-client - powerdnsCommit your changes to git:
ardana >cd ~/openstack/ardana/ansibleardana >git commit -m "COMMIT_MESSAGE"Run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun the
designate-migrate.ymlplaybook to migrate the designate services:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts designate-migrate.yml
26 Magnum Overview #
The SUSE OpenStack Cloud Magnum Service provides container orchestration engines such as Docker Swarm, Kubernetes, and Apache Mesos available as first class resources. SUSE OpenStack Cloud Magnum uses heat to orchestrate an OS image which contains Docker and Kubernetes and runs that image in either virtual machines or bare metal in a cluster configuration.
26.1 Magnum Architecture #
As an OpenStack API service, Magnum provides Container as a Service (CaaS) functionality. Magnum is capable of working with container orchestration engines (COE) such as Kubernetes, Docker Swarm, and Apache Mesos. Some operations work with a User CRUD (Create, Read, Update, Delete) filter.
Components
Magnum API: RESTful API for cluster and cluster template operations.
Magnum Conductor: Performs operations on clusters requested by Magnum API in an asynchronous manner.
Magnum CLI: Command-line interface to the Magnum API.
Etcd (planned, currently using public service): Remote key/value storage for distributed cluster bootstrap and discovery.
Kubemaster (in case of Kubernetes COE): One or more VM(s) or baremetal server(s), representing a control plane for Kubernetes cluster.
Kubeminion (in case of Kubernetes COE): One or more VM(s) or baremetal server(s), representing a workload node for Kubernetes cluster.
| Data Name | Confidentiality | Integrity | Availability | Backup? | Description |
|---|---|---|---|---|---|
| Session Tokens | Confidential | High | Medium | No | Session tokens not stored. |
| System Request | Confidential | High | Medium | No | Data in motion or in MQ not stored. |
| MariaDB Database "Magnum" | Confidential | High | High | Yes | Contains user preferences. Backed up to swift daily. |
| etcd data | Confidential | High | Low | No | Kubemaster IPs and cluster info. Only used during cluster bootstrap. |
| Interface | Network | Request | Response | Operation Description |
|---|---|---|---|---|
| 1 |
Name: External-API Protocol: HTTPS |
Request: Manage clusters Requester: User Credentials: keystone token Authorization: Manage objects that belong to current project Listener: Magnum API |
Operation status with or without data Credentials: TLS certificate |
CRUD operations on cluster templates and clusters |
| 2a |
Name: Internal-API Protocol: AMQP over HTTPS |
Request: Enqueue messages Requester: Magnum API Credentials: RabbitMQ username, password Authorization: RabbitMQ queue read/write operations Listener: RabbitMQ |
Operation status Credentials: TLS certificate |
Notifications issued when cluster CRUD operations requested |
| 2b |
Name: Internal-API Protocol: AMQP over HTTPS |
Request: Read queued messages Requester: Magnum Conductor Credentials: RabbitMQ username, password Authorization: RabbitMQ queue read/write operations Listener: RabbitMQ |
Operation status Credentials: TLS certificate |
Notifications issued when cluster CRUD operations requested |
| 3 |
Name: Internal-API Protocol: MariaDB over HTTPS |
Request: Persist data in MariaDB Requester: Magnum Conductor Credentials: MariaDB username, password Authorization: Magnum database Listener: MariaDB |
Operation status with or without data Credentials: TLS certificate |
Persist cluster/cluster template data, read persisted data |
| 4 |
Name: Internal-API Protocol: HTTPS |
Request: Create per-cluster user in dedicated domain, no role assignments initially Requester: Magnum Conductor Credentials: Trustee domain admin username, password Authorization: Manage users in dedicated Magnum domain Listener: keystone |
Operation status with or without data Credentials: TLS certificate |
Magnum generates user record in a dedicated keystone domain for each cluster |
| 5 |
Name: Internal-API Protocol: HTTPS |
Request: Create per-cluster user stack Requester: Magnum Conductor Credentials: keystone token Authorization: Limited to scope of authorized user Listener: heat |
Operation status with or without data Credentials: TLS certificate |
Magnum creates heat stack for each cluster |
| 6 |
Name: External Network Protocol: HTTPS |
Request: Bootstrap a cluster in public discovery https://discovery.etcd.io/ Requester: Magnum Conductor Credentials: Unguessable URL over HTTPS. URL is only available to software processes needing it. Authorization: Read and update Listener: Public discovery service |
Cluster discovery URL Credentials: TLS certificate |
Create key/value registry of specified size in public storage. This is used to stand up a cluster of kubernetes master nodes (refer to interface call #12). |
| 7 |
Name: Internal-API Protocol: HTTPS |
Request: Create cinder volumes Requester: heat Engine Credentials: keystone token Authorization: Limited to scope of authorized user Listener: cinder API |
Operation status with or without data Credentials: TLS certificate |
heat creates cinder volumes as part of stack. |
| 8 |
Name: Internal-API Protocol: HTTPS |
Request: Create networks, routers, load balancers Requester: heat Engine Credentials: keystone token Authorization: Limited to scope of authorized user Listener: neutron API |
Operation status with or without data Credentials: TLS certificate |
heat creates networks, routers, load balancers as part of the stack. |
| 9 |
Name: Internal-API Protocol: HTTPS |
Request: Create nova VMs, attach volumes Requester: heat Engine Credentials: keystone token Authorization: Limited to scope of authorized user Listener: nova API |
Operation status with or without data Credentials: TLS certificate |
heat creates nova VMs as part of the stack. |
| 10 |
Name: Internal-API Protocol: HTTPS |
Request: Read pre-configured glance image Requester: nova Credentials: keystone token Authorization: Limited to scope of authorized user Listener: glance API |
Operation status with or without data Credentials: TLS certificate |
nova uses pre-configured image in glance to bootstrap VMs. |
| 11a |
Name: External-API Protocol: HTTPS |
Request: heat notification Requester: Cluster member (VM or ironic node) Credentials: keystone token Authorization: Limited to scope of authorized user Listener: heat API |
Operation status with or without data Credentials: TLS certificate |
heat uses OS::heat::WaitCondition resource. VM is expected to call heat notification URL upon completion of certain bootstrap operation. |
| 11b |
Name: External-API Protocol: HTTPS |
Request: heat notification Requester: Cluster member (VM or ironic node) Credentials: keystone token Authorization: Limited to scope of authorized user Listener: heat API |
Operation status with or without data Credentials: TLS certificate |
heat uses OS::heat::WaitCondition resource. VM is expected to call heat notification URL upon completion of certain bootstrap operation. |
| 12 |
Name: External-API Protocol: HTTPS |
Request: Update cluster member state in a public registry at https://discovery.etcd.io Requester: Cluster member (VM or ironic node) Credentials: Unguessable URL over HTTPS only available to software processes needing it. Authorization: Read and update Listener: Public discovery service |
Operation status Credentials: TLS certificate |
Update key/value pair in a registry created by interface call #6. |
| 13a |
Name: VxLAN encapsulated private network on the Guest network Protocol: HTTPS |
Request: Various communications inside Kubernetes cluster Requester: Cluster member (VM or ironic node) Credentials: Tenant specific Authorization: Tenant specific Listener: Cluster member (VM or ironic node) |
Tenant specific Credentials: TLS certificate |
Various calls performed to build Kubernetes clusters, deploy applications and put workload |
| 13b |
Name: VxLAN encapsulated private network on the Guest network Protocol: HTTPS |
Request: Various communications inside Kubernetes cluster Requester: Cluster member (VM or ironic node) Credentials: Tenant specific Authorization: Tenant specific Listener: Cluster member (VM or ironic node) |
Tenant specific Credentials: TLS certificate |
Various calls performed to build Kubernetes clusters, deploy applications and put workload |
| 14 |
Name: Guest/External Protocol: HTTPS |
Request: Download container images Requester: Cluster member (VM or ironic node) Credentials: None Authorization: None Listener: External |
Container image data Credentials: TLS certificate |
Kubernetes makes calls to external repositories to download pre-packed container images |
| 15a |
Name: External/EXT_VM (Floating IP) Protocol: HTTPS |
Request: Tenant specific Requester: Tenant specific Credentials: Tenant specific Authorization: Tenant specific Listener: Octavia load balancer |
Tenant specific Credentials: Tenant specific |
External workload handled by container applications |
| 15b |
Name: Guest Protocol: HTTPS |
Request: Tenant specific Requester: Tenant specific Credentials: Tenant specific Authorization: Tenant specific Listener: Cluster member (VM or ironic node) |
Tenant specific Credentials: Tenant specific |
External workload handled by container applications |
| 15c |
Name: External/EXT_VM (Floating IP) Protocol: HTTPS |
Request: Tenant specific Requester: Tenant specific Credentials: Tenant specific Authorization: Tenant specific Listener: Cluster member (VM or ironic node) |
Tenant specific Credentials: Tenant specific |
External workload handled by container applications |
Dependencies
keystone
RabbitMQ
MariaDB
heat
glance
nova
cinder
neutron
barbican
swift
Implementation
Magnum API and Magnum Conductor are run on the SUSE OpenStack Cloud controllers (or core nodes in case of mid-scale deployments).
| Source CIDR/Security Group | Port/Range | Protocol | Notes |
|---|---|---|---|
| Any IP | 22 | SSH | Tenant Admin access |
| Any IP/Kubernetes Security Group | 2379-2380 | HTTPS | Etcd Traffic |
| Any IP/Kubernetes Security Group | 6443 | HTTPS | kube-apiserver |
| Any IP/Kubernetes Security Group | 7080 | HTTPS | kube-apiserver |
| Any IP/Kubernetes Security Group | 8080 | HTTPS | kube-apiserver |
| Any IP/Kubernetes Security Group | 30000-32767 | HTTPS | kube-apiserver |
| Any IP/Kubernetes Security Group | any | tenant app specific | tenant app specific |
| Port/Range | Protocol | Notes |
|---|---|---|
| 22 | SSH | Admin Access |
| 9511 | HTTPS | Magnum API Access |
| 2379-2380 | HTTPS | Etcd (planned) |
Summary of controls spanning multiple components and interfaces:
Audit: Magnum performs logging. Logs are collected by the centralized logging service.
Authentication: Authentication via keystone tokens at APIs. Password authentication to MQ and DB using specific users with randomly-generated passwords.
Authorization: OpenStack provides admin and non-admin roles that are indicated in session tokens. Processes run at minimum privilege. Processes run as unique user/group definitions (magnum/magnum). Appropriate filesystem controls prevent other processes from accessing service’s files. Magnum config file is mode 600. Logs written using group adm, user magnum, mode 640. IPtables ensure that no unneeded ports are open. Security Groups provide authorization controls between in-cloud components.
Availability: Redundant hosts, clustered DB, and fail-over provide high availability.
Confidentiality: Network connections over TLS. Network separation via VLANs. Data and config files protected via filesystem controls. Unencrypted local traffic is bound to localhost. Separation of customer traffic on the TUL network via Open Flow (VxLANs).
Integrity: Network connections over TLS. Network separation via VLANs. DB API integrity protected by SQL Alchemy. Data and config files are protected by filesystem controls. Unencrypted traffic is bound to localhost.
26.2 Install the Magnum Service #
Installing the Magnum Service can be performed as part of a new SUSE OpenStack Cloud 9 environment or can be added to an existing SUSE OpenStack Cloud 9 environment. Both installations require container management services, running in Magnum cluster VMs with access to specific Openstack API endpoints. The following TCP ports need to be open in your firewall to allow access from VMs to external (public) SUSE OpenStack Cloud endpoints.
| TCP Port | Service |
|---|---|
| 5000 | Identity |
| 8004 | heat |
| 9511 | Magnum |
Magnum is dependent on the following OpenStack services.
keystone
heat
nova KVM
neutron
glance
cinder
swift
barbican
Magnum relies on the public discovery service
https://discovery.etcd.io during cluster bootstrapping
and update. This service does not perform authentication checks. Although
running a cluster cannot be harmed by unauthorized changes in the public
discovery registry, it can be compromised during a cluster update operation.
To avoid this, it is recommended that you keep your cluster discovery URL
(that is,
https://discovery.etc.io/SOME_RANDOM_ID)
secret.
26.2.1 Installing Magnum as part of new SUSE OpenStack Cloud 9 environment #
Magnum components are already included in example SUSE OpenStack Cloud models based on nova KVM, such as entry-scale-kvm, entry-scale-kvm-mml and mid-scale. These models contain the Magnum dependencies (see above). You can follow generic installation instruction for Mid-Scale and Entry-Scale KM model by using this guide: Chapter 24, Installing Mid-scale and Entry-scale KVM.
If you modify the cloud model to utilize a dedicated Cloud Lifecycle Manager, add
magnum-clientitem to the list of service components for the Cloud Lifecycle Manager cluster.Magnum needs a properly configured external endpoint. While preparing the cloud model, ensure that
external-namesetting indata/network_groups.ymlis set to valid hostname, which can be resolved on DNS server, and a valid TLS certificate is installed for your external endpoint. For non-production test installations, you can omitexternal-name. In test installations, the SUSE OpenStack Cloud installer will use an IP address as a public endpoint hostname, and automatically generate a new certificate, signed by the internal CA. Please refer to Chapter 41, Configuring Transport Layer Security (TLS) for more details.
26.2.2 Adding Magnum to an Existing SUSE OpenStack Cloud Environment #
Adding Magnum to an already deployed SUSE OpenStack Cloud 9 installation or during an upgrade can be achieved by performing the following steps.
Add items listed below to the list of service components in
~/openstack/my_cloud/definition/data/control_plane.yml. Add them to clusters which haveserver-roleset toCONTROLLER-ROLE(entry-scale models) orCORE_ROLE(mid-scale model).- magnum-api - magnum-conductor
If your environment utilizes a dedicated Cloud Lifecycle Manager, add
magnum-clientto the list of service components for the Cloud Lifecycle Manager.Commit your changes to the local git repository. Run the following playbooks as described in Chapter 22, Using Git for Configuration Management for your installation.
config-processor-run.ymlready-deployment.ymlsite.yml
Ensure that your external endpoint is configured correctly. The current public endpoint configuration can be verified by running the following commands on the Cloud Lifecycle Manager.
$ source service.osrc $ openstack endpoint list --interface=public --service=identity +-----------+---------+--------------+----------+---------+-----------+------------------------+ | ID | Region | Service Name | Service | Enabled | Interface | URL | | | | | Type | | | | +-----------+---------+--------------+----------+---------+-----------+------------------------+ | d83...aa3 | region0 | keystone | identity | True | public | https://10.245.41.168: | | | | | | | | 5000/v2.0 | +-----------+---------+--------------+----------+---------+-----------+------------------------+
Ensure that the endpoint URL is using either an IP address, or a valid hostname, which can be resolved on the DNS server. If the URL is using an invalid hostname (for example,
myardana.test), follow the steps in Chapter 41, Configuring Transport Layer Security (TLS) to configure a valid external endpoint. You will need to update theexternal-namesetting in thedata/network_groups.ymlto a valid hostname, which can be resolved on DNS server, and provide a valid TLS certificate for the external endpoint. For non-production test installations, you can omit theexternal-name. The SUSE OpenStack Cloud installer will use an IP address as public endpoint hostname, and automatically generate a new certificate, signed by the internal CA. For more information, see Chapter 41, Configuring Transport Layer Security (TLS).
By default SUSE OpenStack Cloud stores the private key used by Magnum and its passphrase in barbican which provides a secure place to store such information. You can change this such that this sensitive information is stored on the file system or in the database without encryption. Making such a change exposes you to the risk of this information being exposed to others. If stored in the database then any database backups, or a database breach, could lead to the disclosure of the sensitive information. Similarly, if stored unencrypted on the file system this information is exposed more broadly than if stored in barbican.
26.3 Integrate Magnum with the DNS Service #
Integration with DNSaaS may be needed if:
The external endpoint is configured to use
myardana.testas host name and SUSE OpenStack Cloud front-end certificate is issued for this host name.Minions are registered using nova VM names as hostnames Kubernetes API server. Most kubectl commands will not work if the VM name (for example,
cl-mu3eevqizh-1-b3vifun6qtuh-kube-minion-ff4cqjgsuzhy) is not getting resolved at the provided DNS server.
Follow these steps to integrate the Magnum Service with the DNS Service.
Allow connections from VMs to EXT-API
sudo modprobe 8021q sudo ip link add link virbr5 name vlan108 type vlan id 108 sudo ip link set dev vlan108 up sudo ip addr add 192.168.14.200/24 dev vlan108 sudo iptables -t nat -A POSTROUTING -o vlan108 -j MASQUERADE
Run the designate reconfigure playbook.
$ cd ~/scratch/ansible/next/ardana/ansible/ $ ansible-playbook -i hosts/verb_hosts designate-reconfigure.yml
Set up designate to resolve myardana.test correctly.
$ openstack zone create --email hostmaster@myardana.test myardana.test. # wait for status to become active $ EXTERNAL_VIP=$(grep HZN-WEB-extapi /etc/hosts | awk '{ print $1 }') $ openstack recordset create --records $EXTERNAL_VIP --type A myardana.test. myardana.test. # wait for status to become active $ LOCAL_MGMT_IP=$(grep `hostname` /etc/hosts | awk '{ print $1 }') $ nslookup myardana.test $LOCAL_MGMT_IP Server: 192.168.14.2 Address: 192.168.14.2#53 Name: myardana.test Address: 192.168.14.5If you need to add/override a top level domain record, the following example should be used, substituting proxy.example.org with your own real address:
$ openstack tld create --name net $ openstack zone create --email hostmaster@proxy.example.org proxy.example.org. $ openstack recordset create --records 16.85.88.10 --type A proxy.example.org. proxy.example.org. $ nslookup proxy.example.org. 192.168.14.2 Server: 192.168.14.2 Address: 192.168.14.2#53 Name: proxy.example.org Address: 16.85.88.10
Enable propagation of dns_assignment and dns_name attributes to neutron ports, as per https://docs.openstack.org/neutron/rocky/admin/config-dns-int.html
# optionally add 'dns_domain = <some domain name>.' to [DEFAULT] section # of ardana/ansible/roles/neutron-common/templates/neutron.conf.j2 stack@ksperf2-cp1-c1-m1-mgmt:~/openstack$ cat <<-EOF >>ardana/services/designate/api.yml provides-data: - to: - name: neutron-ml2-plugin data: - option: extension_drivers values: - dns EOF $ git commit -a -m "Enable DNS support for neutron ports" $ cd ardana/ansible $ ansible-playbook -i hosts/localhost config-processor-run.yml $ ansible-playbook -i hosts/localhost ready-deployment.ymlEnable DNSaaS registration of created VMs by editing the
~/openstack/ardana/ansible/roles/neutron-common/templates/neutron.conf.j2file. You will need to addexternal_dns_driver = designateto the [DEFAULT] section and create a new [designate] section for the designate specific configurations.... advertise_mtu = False dns_domain = ksperf. external_dns_driver = designate {{ neutron_api_extensions_path|trim }} {{ neutron_vlan_transparent|trim }} # Add additional options here [designate] url = https://10.240.48.45:9001 admin_auth_url = https://10.240.48.45:35357/v3 admin_username = designate admin_password = P8lZ9FdHuoW admin_tenant_name = services allow_reverse_dns_lookup = True ipv4_ptr_zone_prefix_size = 24 ipv6_ptr_zone_prefix_size = 116 ca_cert = /etc/ssl/certs/ca-certificates.crtCommit your changes.
$ git commit -a -m "Enable DNSaaS registration of nova VMs" [site f4755c0] Enable DNSaaS registration of nova VMs 1 file changed, 11 insertions(+)
27 Installing ESX Computes and OVSvAPP #
This section describes the installation step requirements for ESX Computes (nova-proxy) and OVSvAPP.
27.1 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
27.2 Setting Up the Cloud Lifecycle Manager #
27.2.1 Installing the Cloud Lifecycle Manager #
Running the ARDANA_INIT_AUTO=1 command is optional to
avoid stopping for authentication at any step. You can also run
ardana-initto launch the Cloud Lifecycle Manager. You will be prompted to
enter an optional SSH passphrase, which is used to protect the key used by
Ansible when connecting to its client nodes. If you do not want to use a
passphrase, press Enter at the prompt.
If you have protected the SSH key with a passphrase, you can avoid having to enter the passphrase on every attempt by Ansible to connect to its client nodes with the following commands:
ardana >eval $(ssh-agent)ardana >ssh-add ~/.ssh/id_rsa
The Cloud Lifecycle Manager will contain the installation scripts and configuration files to deploy your cloud. You can set up the Cloud Lifecycle Manager on a dedicated node or you do so on your first controller node. The default choice is to use the first controller node as the Cloud Lifecycle Manager.
Download the product from:
Boot your Cloud Lifecycle Manager from the SLES ISO contained in the download.
Enter
install(all lower-case, exactly as spelled out here) to start installation.Select the language. Note that only the English language selection is currently supported.
Select the location.
Select the keyboard layout.
Select the primary network interface, if prompted:
Assign IP address, subnet mask, and default gateway
Create new account:
Enter a username.
Enter a password.
Enter time zone.
Once the initial installation is finished, complete the Cloud Lifecycle Manager setup with these steps:
Ensure your Cloud Lifecycle Manager has a valid DNS nameserver specified in
/etc/resolv.conf.Set the environment variable LC_ALL:
export LC_ALL=C
NoteThis can be added to
~/.bashrcor/etc/bash.bashrc.
The node should now have a working SLES setup.
27.3 Overview of ESXi and OVSvApp #
ESXi is a hypervisor developed by VMware for deploying and serving virtual computers. OVSvApp is a service VM that allows for leveraging advanced networking capabilities that OpenStack neutron provides. As a result, OpenStack features can be added quickly with minimum effort where ESXi is used. OVSvApp allows for hosting VMs on ESXi hypervisors together with the flexibility of creating port groups dynamically on Distributed Virtual Switches (DVS). Network traffic can then be steered through the OVSvApp VM which provides VLAN and VXLAN underlying infrastructure for VM communication and security features based on OpenStack. More information is available at the OpenStack wiki.
The diagram below illustrates the OVSvApp architecture.
27.4 VM Appliances Used in OVSvApp Implementation #
The default configuration deployed with the Cloud Lifecycle Manager for VMware ESX hosts uses service appliances that run as VMs on the VMware hypervisor. There is one OVSvApp VM per VMware ESX host and one nova Compute Proxy per VMware cluster or VMware vCenter Server. Instructions for how to create a template for the Nova Compute Proxy or ovsvapp can be found at Section 27.9, “Create a SUSE-based Virtual Appliance Template in vCenter”.
27.4.1 OVSvApp VM #
OVSvApp implementation is comprised of:
a service VM called OVSvApp VM hosted on each ESXi hypervisor within a cluster, and
two vSphere Distributed vSwitches (DVS).
OVSvApp VMs run SUSE Linux Enterprise and have Open vSwitch installed with an agent called
OVSvApp agent. The OVSvApp VM routes network traffic to
the various VMware tenants and cooperates with the OpenStack deployment to
configure the appropriate port and network settings for VMware tenants.
27.4.2 nova Compute Proxy VM #
The nova compute proxy is the nova-compute service
for VMware ESX. Only one instance of this service is required for each ESX
cluster that is deployed and is communicating with a single VMware vCenter
server. (This is not like KVM where the nova-compute
service must run on every KVM Host.) The single instance of
nova-compute service can run in the OpenStack controller
node or any other service node in your cloud. The main component of the
nova-compute VM is the OVSvApp nova VCDriver that talks
to the VMware vCenter server to perform VM operations such as VM creation
and deletion.
27.5 Prerequisites for Installing ESXi and Managing with vCenter #
ESX/vCenter integration is not fully automatic. vCenter administrators are responsible for taking steps to ensure secure operation.
The VMware administrator is responsible for administration of the vCenter servers and the ESX nodes using the VMware administration tools. These responsibilities include:
Installing and configuring vCenter server
Installing and configuring ESX server and ESX cluster
Installing and configuring shared datastores
Establishing network connectivity between the ESX network and the Cloud Lifecycle Manager OpenStack management network
The VMware administration staff is responsible for the review of vCenter logs. These logs are not automatically included in Cloud Lifecycle Manager OpenStack centralized logging.
The VMware administrator is responsible for administration of the vCenter servers and the ESX nodes using the VMware administration tools.
Logging levels for vCenter should be set appropriately to prevent logging of the password for the Cloud Lifecycle Manager OpenStack message queue.
The vCenter cluster and ESX Compute nodes must be appropriately backed up.
Backup procedures for vCenter should ensure that the file containing the Cloud Lifecycle Manager OpenStack configuration as part of nova and cinder volume services is backed up and the backups are protected appropriately.
Since the file containing the Cloud Lifecycle Manager OpenStack message queue password could appear in the swap area of a vCenter server, appropriate controls should be applied to the vCenter cluster to prevent discovery of the password via snooping of the swap area or memory dumps.
It is recommended to have a common shared storage for all the ESXi hosts in a particular cluster.
Ensure that you have enabled HA (High Availability) and DRS (Distributed Resource Scheduler) settings in a cluster configuration before running the installation. DRS and HA are disabled only for OVSvApp. This is done so that it does not move to a different host. If you do not enable DRS and HA prior to installation then you will not be able to disable it only for OVSvApp. As a result DRS or HA could migrate OVSvApp to a different host, which would create a network loop.
No two clusters should have the same name across datacenters in a given vCenter.
27.6 ESXi/vCenter System Requirements #
For information about recommended hardware minimums, consult Section 3.2, “Recommended Hardware Minimums for an Entry-scale ESX KVM Model”.
27.7 Creating an ESX Cluster #
Steps to create an ESX Cluster:
Download the ESXi Hypervisor and vCenter Appliance from the VMware website.
Install the ESXi Hypervisor.
Configure the Management Interface.
Enable the CLI and Shell access.
Set the password and login credentials.
Extract the vCenter Appliance files.
The vCenter Appliance offers two ways to install the vCenter. The directory
vcsa-ui-installercontains the graphical installer. Thevcsa-cli-installerdirectory contains the command line installer. The remaining steps demonstrate using thevcsa-ui-installerinstaller.In the
vcsa-ui-installer, click the to start installing the vCenter Appliance in the ESXi Hypervisor.Note the MANAGEMENT IP, USER ID, and PASSWORD of the ESXi Hypervisor.
Assign an IP ADDRESS, USER ID, and PASSWORD to the vCenter server.
Complete the installation.
When the installation is finished, point your Web browser to the IP ADDRESS of the vCenter. Connect to the vCenter by clicking on link in the browser.
Enter the information for the vCenter you just created: IP ADDRESS, USER ID, and PASSWORD.
When connected, configure the following:
DatacenterGo to
Home>Inventory>Hosts and ClustersSelect File > New > Datacenter
Rename the datacenter
Cluster
Right-click a datacenter or directory in the vSphere Client and select .
Enter a name for the cluster.
Choose cluster features.
Add a Host to Cluster
In the vSphere Web Client, navigate to a datacenter, cluster, or directory within a datacenter.
Right-click the datacenter, cluster, or directory and select .
Type the IP address or the name of the host and click .
Enter the administrator credentials and click .
Review the host summary and click .
Assign a license key to the host.
27.8 Configuring the Required Distributed vSwitches and Port Groups #
The required Distributed vSwitches (DVS) and port groups can be created by
using the vCenter graphical user interface (GUI) or by using the command line
tool provided by python-networking-vsphere. The vCenter
GUI is recommended.
OVSvApp virtual machines (VMs) give ESX installations the ability to leverage some of the advanced networking capabilities and other benefits OpenStack provides. In particular, OVSvApp allows for hosting VMs on ESX/ESXi hypervisors together with the flexibility of creating port groups dynamically on Distributed Virtual Switch.
A port group is a management object for aggregation of multiple ports (on a virtual switch) under a common configuration. A VMware port group is used to group together a list of ports in a virtual switch (DVS in this section) so that they can be configured all at once. The member ports of a port group inherit their configuration from the port group, allowing for configuration of a port by simply dropping it into a predefined port group.
The following sections cover configuring OVSvApp switches on ESX. More information about OVSvApp is available at https://wiki.openstack.org/wiki/Neutron/Networking-vSphere
The diagram below illustrates a typical configuration that uses OVSvApp and Distributed vSwitches.
Detailed instructions are shown in the following sections for four example installations and two command line procedures.
27.8.1 Creating ESXi TRUNK DVS and Required Portgroup #
The process of creating an ESXi Trunk Distributed vSwitch (DVS) consists of three steps: create a switch, add host and physical adapters, and add a port group. Use the following detailed instructions to create a trunk DVS and a required portgroup. These instructions use a graphical user interface (GUI). The GUI menu options may vary slightly depending on the specific version of vSphere installed. Command line interface (CLI) instructions are below the GUI instructions.
27.8.1.1 Creating ESXi Trunk DVS with vSphere Web Client #
Create the switch.
Using vSphere webclient, connect to the vCenter server.
Under , right-click on the appropriate datacenter. Select > .
Name the switch
TRUNK. Click .Select version 6.0.0 or larger. Click .
Under , lower the number of uplink ports to the lowest possible number (0 or 1). Uncheck . Click .
Under , verify the settings are correct and click .
Add host and physical adapters.
Under find the DVS named
TRUNKyou just created. Right-click on it and select .Under , select . Click .
Click .
Select the
CURRENT ESXI HOSTand select . Click .Under , select and UNCHECK all other boxes. Click .
Under , check that the
Maximum Number of Portsreads(auto). There is nothing else to do. Click .Under , verify that one and only one host is being added and click .
Add port group.
Right-click on the TRUNK DVS that was just created (or modified) and select > .
Name the port group
TRUNK-PG. Click .Under select:
port binding>Static bindingport allocation>Elasticvlan type>VLAN trunkingwith range of 1–4094.
Check
Customized default policies configuration. Click .Under use the following values:
Setting
Value
promiscuous mode
accept
MAC address changes
reject
Forged transmits
accept
Set to
true(port count growing).Skip and click .
Skip and click .
Skip and click .
Under there is nothing to be done. Click .
Under add a description if desired. Click .
Under verify everything is as expected and click .
27.8.2 Creating ESXi MGMT DVS and Required Portgroup #
The process of creating an ESXi Mgmt Distributed vSwitch (DVS) consists of three steps: create a switch, add host and physical adapters, and add a port group. Use the following detailed instructions to create a mgmt DVS and a required portgroup.
Create the switch.
Using the vSphere webclient, connect to the vCenter server.
Under , right-click on the appropriate datacenter, and select
Distributed Switch>New Distributed SwitchName the switch
MGMT. Click .Select version 6.0.0 or higher. Click .
Under , select the appropriate number of uplinks. The
MGMTDVS is what connects the ESXi host to the OpenStack management network. UncheckCreate a default port group. Click .Under , verify the settings are correct. Click .
Add host and physical adapters to Distributed Virtual Switch.
Under
Networking, find theMGMTDVS you just created. Right-click on it and select .Under , select . Click .
Click .
Select the current ESXi host and select . Click .
Under , select and UNCHECK all other boxes. Click .
Under , click on the interface you are using to connect the ESXi to the OpenStack management network. The name is of the form
vmnic#(for example,vmnic0,vmnic1, etc.). When the interface is highlighted, select then select the uplink name to assign or auto assign. Repeat the process for each uplink physical NIC you will be using to connect to the OpenStack data network. Click .Verify that you understand and accept the impact shown by . Click .
Verify that everything is correct and click on .
Add MGMT port group to switch.
Right-click on the
MGMTDVS and select > .Name the port group
MGMT-PG. Click .Under , select:
port binding>Static bindingport allocation>Elasticvlan type>None
Click .
Under , verify that everything is as expected and click .
Add GUEST port group to the switch.
Right-click on the DVS (MGMT) that was just created (or modified). Select > .
Name the port group
GUEST-PG. Click .Under , select:
port binding>Static bindingport allocation>Elasticvlan type>VLAN trunkingThe VLAN range corresponds to the VLAN ids being used by the OpenStack underlay. This is the same VLAN range as configured in theneutron.confconfiguration file for the neutron server.
Select . Click .
Under , use the following settings:
setting
value
promiscuous mode
accept
MAC address changes
reject
Forged transmits
accept
Skip and click .
Under , make changes appropriate for your network and deployment.
Skip and click .
Skip and click .
Under , add a description if desired. Click .
Under , verify everything is as expected. Click .
Add ESX-CONF port group.
Right-click on the DVS (MGMT) that was just created (or modified). Select > .
Name the port group
ESX-CONF-PG. Click .Under , select:
port binding>Static bindingport allocation>Elasticvlan type>None
Click .
port binding>Static bindingport allocation>Elasticvlan type>None
Click .
Under , verify that everything is as expected and click .
27.8.3 Configuring OVSvApp Network Resources Using Ansible-Playbook #
The Ardana ansible playbook
neutron-create-ovsvapp-resources.yml can be used to
create Distributed Virtual Switches and Port Groups on a vCenter cluster.
The playbook requires the following inputs:
vcenter_usernamevcenter_encrypted_passwordvcenter_ipvcenter_port(default 443)vc_net_resources_locationThis is the path to a file which contains the definition of the resources to be created. The definition is in JSON format.
The neutron-create-ovsvapp-resources.yml playbook is
not set up by default. In order to execute the playbook from the Cloud Lifecycle Manager, the
python-networking-vsphere package must be installed.
Install the
python-networking-vspherepackage:tux >sudo zypper install python-networking-vsphereRun the playbook:
ardana >ansible-playbook neutron-create-ovsvapp-resources.yml \ -i hosts/verb_hosts -vvv -e 'variable_host=localhost vcenter_username=USERNAME vcenter_encrypted_password=ENCRYPTED_PASSWORD vcenter_ip=IP_ADDRESS vcenter_port=443 vc_net_resources_location=LOCATION_TO_RESOURCE_DEFINITION_FILE
The RESOURCE_DEFINITION_FILE is in JSON format and
contains the resources to be created.
Sample file contents:
{
"datacenter_name": "DC1",
"host_names": [
"192.168.100.21",
"192.168.100.222"
],
"network_properties": {
"switches": [
{
"type": "dvSwitch",
"name": "TRUNK",
"pnic_devices": [],
"max_mtu": "1500",
"description": "TRUNK DVS for ovsvapp.",
"max_ports": 30000
},
{
"type": "dvSwitch",
"name": "MGMT",
"pnic_devices": [
"vmnic1"
],
"max_mtu": "1500",
"description": "MGMT DVS for ovsvapp. Uses 'vmnic0' to connect to OpenStack Management network",
"max_ports": 30000
}
],
"portGroups": [
{
"name": "TRUNK-PG",
"vlan_type": "trunk",
"vlan_range_start": "1",
"vlan_range_end": "4094",
"dvs_name": "TRUNK",
"nic_teaming": null,
"allow_promiscuous": true,
"forged_transmits": true,
"auto_expand": true,
"description": "TRUNK port group. Configure as trunk for vlans 1-4094. Default nic_teaming selected."
},
{
"name": "MGMT-PG",
"dvs_name": "MGMT",
"nic_teaming": null,
"description": "MGMT port group. Configured as type 'access' (vlan with vlan_id = 0, default). Default nic_teaming. Promiscuous false, forged_transmits default"
},
{
"name": "GUEST-PG",
"dvs_name": "GUEST",
"vlan_type": "MGMT",
"vlan_range_start": 100,
"vlan_range_end": 200,
"nic_teaming": null,
"allow_promiscuous": true,
"forged_transmits": true,
"auto_expand": true,
"description": "GUEST port group. Configure for vlans 100 through 200."
},
{
"name": "ESX-CONF-PG",
"dvs_name": "MGMT",
"nic_teaming": null,
"description": "ESX-CONF port group. Configured as type 'access' (vlan with vlan_id = 0, default)."
}
]
}
}27.8.4 Configuring OVSVAPP Using Python-Networking-vSphere #
Scripts can be used with the Networking-vSphere Project. The scripts automate some of the process of configuring OVSvAPP from the command line. The following are help entries for two of the scripts:
tux >cd /opt/repos/networking-vspheretux >ovsvapp-manage-dvs -h usage: ovsvapp-manage-dvs [-h] [--tcp tcp_port] [--pnic_devices pnic_devices [pnic_devices ...]] [--max_mtu max_mtu] [--host_names host_names [host_names ...]] [--description description] [--max_ports max_ports] [--cluster_name cluster_name] [--create] [--display_spec] [-v] dvs_name vcenter_user vcenter_password vcenter_ip datacenter_name positional arguments: dvs_name Name to use for creating the DVS vcenter_user Username to be used for connecting to vCenter vcenter_password Password to be used for connecting to vCenter vcenter_ip IP address to be used for connecting to vCenter datacenter_name Name of data center where the DVS will be created optional arguments: -h, --help show this help message and exit --tcp tcp_port TCP port to be used for connecting to vCenter --pnic_devices pnic_devices [pnic_devices ...] Space separated list of PNIC devices for DVS --max_mtu max_mtu MTU to be used by the DVS --host_names host_names [host_names ...] Space separated list of ESX hosts to add to DVS --description description DVS description --max_ports max_ports Maximum number of ports allowed on DVS --cluster_name cluster_name Cluster name to use for DVS --create Create DVS on vCenter --display_spec Print create spec of DVS -v Verbose output
tux >cd /opt/repos/networking-vspheretux >ovsvapp-manage-dvpg -h usage: ovsvapp-manage-dvpg [-h] [--tcp tcp_port] [--vlan_type vlan_type] [--vlan_id vlan_id] [--vlan_range_start vlan_range_start] [--vlan_range_stop vlan_range_stop] [--description description] [--allow_promiscuous] [--allow_forged_transmits] [--notify_switches] [--network_failover_detection] [--load_balancing {loadbalance_srcid,loadbalance_ip,loadbalance_srcmac,loadbalance_loadbased,failover_explicit}] [--create] [--display_spec] [--active_nics ACTIVE_NICS [ACTIVE_NICS ...]] [-v] dvpg_name vcenter_user vcenter_password vcenter_ip dvs_name positional arguments: dvpg_name Name to use for creating theDistributed Virtual Port Group (DVPG) vcenter_user Username to be used for connecting to vCenter vcenter_password Password to be used for connecting to vCenter vcenter_ip IP address to be used for connecting to vCenter dvs_name Name of the Distributed Virtual Switch (DVS) to create the DVPG in optional arguments: -h, --help show this help message and exit --tcp tcp_port TCP port to be used for connecting to vCenter --vlan_type vlan_type Vlan type to use for the DVPG --vlan_id vlan_id Vlan id to use for vlan_type='vlan' --vlan_range_start vlan_range_start Start of vlan id range for vlan_type='trunk' --vlan_range_stop vlan_range_stop End of vlan id range for vlan_type='trunk' --description description DVPG description --allow_promiscuous Sets promiscuous mode of DVPG --allow_forged_transmits Sets forge transmit mode of DVPG --notify_switches Set nic teaming 'notify switches' to True. --network_failover_detection Set nic teaming 'network failover detection' to True --load_balancing {loadbalance_srcid,loadbalance_ip,loadbalance_srcmac,loadbalance_loadbased,failover_explicit} Set nic teaming load balancing algorithm. Default=loadbalance_srcid --create Create DVPG on vCenter --display_spec Send DVPG's create spec to OUTPUT --active_nics ACTIVE_NICS [ACTIVE_NICS ...] Space separated list of active nics to use in DVPG nic teaming -v Verbose output
27.9 Create a SUSE-based Virtual Appliance Template in vCenter #
Download the SLES12-SP4 ISO image (
SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.iso) from https://www.suse.com/products/server/download/. You need to sign in or create a SUSE customer service account before downloading.Create a new Virtual Machine in vCenter Resource Pool.
Configure the Storage selection.
Configure the Guest Operating System.
Create a Disk.
Ready to Complete.
Edit Settings before booting the VM with additional Memory, typically 16GB or 32GB, though large scale environments may require larger memory allocations.
Edit Settings before booting the VM with additional Network Settings. Ensure there are four network adapters, one each for TRUNK, MGMT, ESX-CONF, and GUEST.
Attach the ISO image to the DataStore.
Configure the 'disk.enableUUID=TRUE' flag in the General - Advanced Settings.
After attaching the CD/DVD drive with the ISO image and completing the initial VM configuration, power on the VM by clicking the Play button on the VM's summary page.
Click when the VM boots from the console window.
Accept the License agreement, language and Keyboard selection.
Select the System Role to Xen Virtualization Host.
Select the 'Proposed Partitions' in the Suggested Partition screen.
Edit the Partitions to select the 'LVM' Mode and then select the 'ext4' filesystem type.
Increase the size of the root partition from 10GB to 60GB.
Create an additional logical volume to accommodate the LV_CRASH volume (15GB). Do not mount the volume at this time, it will be used later.
Configure the Admin User/Password and User name.
Installation Settings (Disable Firewall and enable SSH).
The operating system successfully installs and the VM reboots.
Check that the contents of the ISO files are copied to the locations shown below on your Cloud Lifecycle Manager. This may already be completed on the Cloud Lifecycle Manager.
Mount or copy the contents of
SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.isoto/opt/ardana_packager/ardana/sles12/zypper/OS/(create the directory if it is missing).
Log in to the VM with the configured user credentials.
The VM must be set up before a template can be created with it. The IP addresses configured here are temporary and will need to be reconfigured as VMs are created using this template. The temporary IP address should not overlap with the network range for the MGMT network.
The VM should now have four network interfaces. Configure them as follows:
ardana >cd /etc/sysconfig/networktux >sudo lsThe directory will contain the files:
ifcfg-br0,ifcfg-br1,ifcfg-br2,ifcfg-br3,ifcfg-eth0,ifcfg-eth1,ifcfg-eth2, andifcfg-eth3.If you have configured a default route while installing the VM, then there will be a
routesfile.Note the IP addresses configured for MGMT.
Configure the temporary IP for the MGMT network. Edit the
ifcfg-eth1file.tux >sudo vi /etc/sysconfig/network/ifcfg-eth1 BOOTPROTO='static' BROADCAST='' ETHTOOL_OPTIONS='' IPADDR='192.168.24.132/24' (Configure the IP address of the MGMT Interface) MTU='' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto'
Edit the
ifcfg-eth0,ifcfg-eth2, andifcfg-eth3files.tux >sudo vi /etc/sysconfig/network/ifcfg-eth0 BOOTPROTO='static' BROADCAST='' ETHTOOL_OPTIONS='' IPADDR='' MTU='' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto'tux >sudo vi /etc/sysconfig/network/ifcfg-eth2 BOOTPROTO='' BROADCAST='' ETHTOOL_OPTIONS='' IPADDR='' MTU='' NAME='VMXNET3 Ethernet Controller' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto'tux >sudo vi /etc/sysconfig/network/ifcfg-eth3 BOOTPROTO='' BROADCAST='' ETHTOOL_OPTIONS='' IPADDR='' MTU='' NAME='VMXNET3 Ethernet Controller' NETWORK='' REMOTE_IPADDR='' STARTMODE='auto'If the default route is not configured, add a default route file manually.
Create a file
routesin/etc/sysconfig/network.Edit the file to add your default route.
tux >sudo sudo vi routes default 192.168.24.140 - -
Delete all the bridge configuration files, which are not required:
ifcfg-br0,ifcfg-br1,ifcfg-br2, andifcfg-br3.
Add
ardanauser and home directory if that is not your defaultuser. The username and password should beardana/ardana.tux >sudo useradd -m ardanatux >sudo passwd ardanaCreate a
ardanausergroup in the VM if it does not exist.Check for an existing
ardanagroup.tux >sudo groups ardanaAdd
ardanagroup if necessary.tux >sudo groupadd ardanaAdd
ardanauser to theardanagroup.tux >sudo gpasswd -a ardana ardana
Allow the
ardanauser tosudowithout password. Setting upsudoon SLES is covered in the SUSE documentation at https://documentation.suse.com/sles/15-SP1/single-html/SLES-admin/#sec-sudo-conf. We recommend creating user specific sudo config files in the/etc/sudoers.ddirectory. Create an/etc/sudoers.d/ardanaconfig file with the following content to allow sudo commands without the requirement of a password.ardana ALL=(ALL) NOPASSWD:ALL
Add the Zypper repositories using the ISO-based repositories created previously. Change the value of
deployer_ipif necessary.tux >sudo DEPLOYER_IP=192.168.24.140tux >sudo zypper addrepo --no-gpgcheck --refresh \ http://$deployer_ip:79/ardana/sles12/zypper/OS SLES-OStux >sudo zypper addrepo --no-gpgcheck --refresh \ http://$deployer_ip:79/ardana/sles12/zypper/SDK SLES-SDKVerify that the repositories have been added.
tux >zypper repos --detailSet up SSH access that does not require a password to the temporary IP address that was configured for
eth1.When you have started the installation using the Cloud Lifecycle Manager or if you are adding a SLES node to an existing cloud, the Cloud Lifecycle Manager public key needs to be copied to the SLES node. You can do this by copying
~/.ssh/authorized_keysfrom another node in the cloud to the same location on the SLES node. If you are installing a new cloud, this file will be available on the nodes after running thebm-reimage.ymlplaybook.ImportantEnsure that there is global read access to the file
~/.ssh/authorized_keys.Test passwordless ssh from the Cloud Lifecycle Manager and check your ability to remotely execute sudo commands.
tux >ssh ardana@IP_OF_SLES_NODE_eth1 "sudo tail -5 /var/log/messages"
Shutdown the VM and create a template out of the VM appliance for future use.
The VM Template will be saved in your vCenter Datacenter and you can view it from menu. Note that menu options will vary slightly depending on the version of vSphere that is deployed.
27.10 ESX Network Model Requirements #
For this model the following networks are needed:
MANAGEMENT-NET: This is an untagged network this is used for the control plane as well as the esx-compute proxy and ovsvapp VMware instance. It is tied to the MGMT DVS/PG in vSphere.EXTERNAL-API_NET: This is a tagged network for the external/public API. There is no difference in this model from those without ESX and there is no additional setup needed in vSphere for this network.EXTERNAL-VM-NET: This is a tagged network used for Floating IP (FIP) assignment to running instances. There is no difference in this model from those without ESX and there is no additional setup needed in vSphere for this network.GUEST-NET: This is a tagged network used internally for neutron. It is tied to the GUEST PG in vSphere.ESX-CONF-NET: This is a separate configuration network for ESX that must be reachable via the MANAGEMENT-NET. It is tied to the ESX-CONF PG in vSphere.TRUNK-NET: This is an untagged network used internally for ESX. It is tied to the TRUNC DVS/PG in vSphere.
27.11 Creating and Configuring Virtual Machines Based on Virtual Appliance Template #
The following process for creating and configuring VMs from the vApp template
should be repeated for every cluster in the DataCenter. Each cluster should
host a nova Proxy VM, and each host in a cluster should have an OVSvApp
VM running. The following method uses the vSphere Client
Management Tool to deploy saved templates from the vCenter.
Identify the cluster that you want nova Proxy to manage.
Create a VM from the template on a chosen cluster.
The first VM deployed is the
nova-compute-proxyVM. This VM can reside on anyHOSTinside a cluster. There should be only one instance of this VM in a cluster.The
nova-compute-proxyonly uses two of the four interfaces configured previously (ESX_CONFandMANAGEMENT).NoteDo not swap the interfaces. They must be in the specified order (
ESX_CONFiseth0,MGMTiseth1).After the VM has been deployed, log in to it with
ardana/ardanacredentials. Log in to the VM with SSH using theMGMTIP address. Make sure that all root level commands work withsudo. This is required for the Cloud Lifecycle Manager to configure the appliance for services and networking.Install another VM from the template and name it
OVSvApp-VM1-HOST1. (You can add a suffix with the host name to identify the host it is associated with).NoteThe VM must have four interfaces configured in the right order. The VM must be accessible from the Management Network through SSH from the Cloud Lifecycle Manager.
/etc/sysconfig/network/ifcfg-eth0isESX_CONF./etc/sysconfig/network/ifcfg-eth1isMGMT./etc/sysconfig/network/ifcfg-eth2isTRUNK./etc/sysconfig/network/ifcfg-eth3isGUEST.
If there is more than one
HOSTin the cluster, deploy another VM from the Template and name itOVSvApp-VM2-HOST2.If the OVSvApp VMs end up on the same
HOST, then manually separate the VMs and follow the instructions below to add rules for High Availability (HA) and Distributed Resource Scheduler (DRS).NoteHA seeks to minimize system downtime and data loss. See also Chapter 4, High Availability. DRS is a utility that balances computing workloads with available resources in a virtualized environment.
When installed from a template to a cluster, the VM will not be bound to a particular host if you have more than one Hypervisor. The requirement for the OVSvApp is that there be only one OVSvApp Appliance per host and that it should be constantly bound to the same host. DRS or VMotion should not be allowed to migrate the VMs from the existing HOST. This would cause major network interruption. In order to achieve this we need to configure rules in the cluster HA and DRS settings.
NoteVMotion enables the live migration of running virtual machines from one physical server to another with zero downtime, continuous service availability, and complete transaction integrity.
Configure rules for OVSvApp VMs.
Configure .
must be disabled.
VM should be
Power-On.
Configure .
Configure .
Create a DRS Group for the OVSvApp VMs.
Add VMs to the DRS Group.
Add appropriate to the DRS Groups.
All three VMs are up and running. Following the preceding process, there is one nova Compute Proxy VM per cluster, and
OVSvAppVM1andOVSvAppVM2on each HOST in the cluster.Record the configuration attributes of the VMs.
nova Compute Proxy VM:
Cluster Namewhere this VM is locatedManagement IP AddressVM NameThe actual name given to the VM to identify it.
OVSvAppVM1
Cluster Namewhere this VM is locatedManagement IP Addressesx_hostnamethat this OVSvApp is bound tocluster_dvs_mappingThe Distributed vSwitch name created in the datacenter for this particular cluster.Example format:
DATA_CENTER/host/CLUSTERNAME: DVS-NAME Do not substitute for
host'. It is a constant.
OVSvAppVM2:
Cluster Namewhere this VM is locatedManagement IP Addressesx_hostnamethat this OVSvApp is bound tocluster_dvs_mappingThe Distributed vSwitch name created in the datacenter for this particular cluster.Example format:
DATA_CENTER/host/CLUSTERNAME: DVS-NAME Do not substitute for
host'. It is a constant.
27.12 Collect vCenter Credentials and UUID #
Obtain the vCenter UUID from vSphere with the URL shown below:
https://VCENTER-IP/mob/?moid=ServiceInstance&doPath=content.about
Select the field
instanceUUID. Copy and paste the value of# field instanceUUID.Record the
UUIDRecord the
vCenter PasswordRecord the
vCenter Management IPRecord the
DataCenter NameRecord the
Cluster NameRecord the
DVS (Distributed vSwitch) Name
27.13 Edit Input Models to Add and Configure Virtual Appliances #
The following steps should be used to edit the Ardana input model data to add and configure the Virtual Appliances that were just created. The process assumes that the SUSE OpenStack Cloud is deployed and a valid Cloud Lifecycle Manager is in place.
Edit the following files in
~/openstack/my_cloud/definition/data/:servers.yml,disks_app_vm.yml, andpass_through.yml. Fill in attribute values recorded in the previous step.Follow the instructions in
pass_through.ymlto encrypt your vCenter password using an encryption key.Export an environment variable for the encryption key.
ARDANA_USER_PASSWORD_ENCRYPT_KEY=ENCRYPTION_KEY
Run
~ardana/openstack/ardana/ansible/ardanaencrypt.pyscript. It will prompt forunencrypted value?. Enter the unencrypted vCenter password and it will return an encrypted string.Copy and paste the encrypted password string in the
pass_through.ymlfile as a value for thepasswordfield enclosed in double quotes.Enter the
username,ip, andidof the vCenter server in the Global section of thepass_through.ymlfile. Use the values recorded in the previous step.In the
serverssection of thepass_through.ymlfile, add the details about the nova Compute Proxy and OVSvApp VMs that was recorded in the previous step.# Here the 'id' refers to the name of the node running the # esx-compute-proxy. This is identical to the 'servers.id' in # servers.yml. # NOTE: There should be one esx-compute-proxy node per ESX # resource pool or cluster. # cluster_dvs_mapping in the format # 'Datacenter-name/host/Cluster-Name:Trunk-DVS-Name' # Here 'host' is a string and should not be changed or # substituted. # vcenter_id is same as the 'vcenter-uuid' obtained in the global # section. # 'id': is the name of the appliance manually installed # 'vcenter_cluster': Name of the vcenter target cluster # esx_hostname: Name of the esx host hosting the ovsvapp # NOTE: For every esx host in a cluster there should be an ovsvapp # instance running. id: esx-compute1 data: vmware: vcenter_cluster: <vmware cluster1 name> vcenter_id: <vcenter-uuid> - id: ovsvapp1 data: vmware: vcenter_cluster: <vmware cluster1 name> cluster_dvs_mapping: <cluster dvs mapping> esx_hostname: <esx hostname hosting the ovsvapp> vcenter_id: <vcenter-uuid> - id: ovsvapp2 data: vmware: vcenter_cluster: <vmware cluster1 name> cluster_dvs_mapping: <cluster dvs mapping> esx_hostname: <esx hostname hosting the ovsvapp> vcenter_id: <vcenter-uuid>The VM
idstring should match exactly with the data written in theservers.ymlfile.Edit the
servers.ymlfile, adding the nova Proxy VM and OVSvApp information recorded in the previous step.# Below entries shall be added by the user # for entry-scale-kvm-esx after following # the doc instructions in creating the # esx-compute-proxy VM Appliance and the # esx-ovsvapp VM Appliance. # Added just for the reference # NOTE: There should be one esx-compute per # Cluster and one ovsvapp per Hypervisor in # the Cluster. # id - is the name of the virtual appliance # ip-addr - is the Mgmt ip address of the appliance # The values shown below are examples and has to be # substituted based on your setup. # Nova Compute proxy node - id: esx-compute1 server-group: RACK1 ip-addr: 192.168.24.129 role: ESX-COMPUTE-ROLE # OVSVAPP node - id: ovsvapp1 server-group: RACK1 ip-addr: 192.168.24.130 role: OVSVAPP-ROLE - id: ovsvapp2 server-group: RACK1 ip-addr: 192.168.24.131 role: OVSVAPP-ROLEExamples of
pass_through.ymlandservers.ymlfiles:pass_through.yml product: version: 2 pass-through: global: vmware: - username: administrator@vsphere.local ip: 10.84.79.3 port: '443' cert_check: false password: @hos@U2FsdGVkX19aqGOUYGgcAIMQSN2lZ1X+gyNoytAGCTI= id: a0742a39-860f-4177-9f38-e8db82ad59c6 servers: - data: vmware: vcenter_cluster: QE vcenter_id: a0742a39-860f-4177-9f38-e8db82ad59c6 id: lvm-nova-compute1-esx01-qe - data: vmware: vcenter_cluster: QE cluster_dvs_mapping: 'PROVO/host/QE:TRUNK-DVS-QE' esx_hostname: esx01.qe.provo vcenter_id: a0742a39-860f-4177-9f38-e8db82ad59c6 id: lvm-ovsvapp1-esx01-qe - data: vmware: vcenter_cluster: QE cluster_dvs_mapping: 'PROVO/host/QE:TRUNK-DVS-QE' esx_hostname: esx02.qe.provo vcenter_id: a0742a39-860f-4177-9f38-e8db82ad59c6 id: lvm-ovsvapp2-esx02-qeservers.yml product: version: 2 servers: - id: deployer ilo-ip: 192.168.10.129 ilo-password: 8hAcPMne ilo-user: CLM004 ip-addr: 192.168.24.125 is-deployer: true mac-addr: '8c:dc:d4:b4:c5:4c' nic-mapping: MY-2PORT-SERVER role: DEPLOYER-ROLE server-group: RACK1 - id: controller3 ilo-ip: 192.168.11.52 ilo-password: 8hAcPMne ilo-user: HLM004 ip-addr: 192.168.24.128 mac-addr: '8c:dc:d4:b5:ed:b8' nic-mapping: MY-2PORT-SERVER role: CONTROLLER-ROLE server-group: RACK1 - id: controller2 ilo-ip: 192.168.10.204 ilo-password: 8hAcPMne ilo-user: HLM004 ip-addr: 192.168.24.127 mac-addr: '8c:dc:d4:b5:ca:c8' nic-mapping: MY-2PORT-SERVER role: CONTROLLER-ROLE server-group: RACK2 - id: controller1 ilo-ip: 192.168.11.57 ilo-password: 8hAcPMne ilo-user: CLM004 ip-addr: 192.168.24.126 mac-addr: '5c:b9:01:89:c6:d8' nic-mapping: MY-2PORT-SERVER role: CONTROLLER-ROLE server-group: RACK3 # Nova compute proxy for QE cluster added manually - id: lvm-nova-compute1-esx01-qe server-group: RACK1 ip-addr: 192.168.24.129 role: ESX-COMPUTE-ROLE # OVSvApp VM for QE cluster added manually # First ovsvapp vm in esx01 node - id: lvm-ovsvapp1-esx01-qe server-group: RACK1 ip-addr: 192.168.24.132 role: OVSVAPP-ROLE # Second ovsvapp vm in esx02 node - id: lvm-ovsvapp2-esx02-qe server-group: RACK1 ip-addr: 192.168.24.131 role: OVSVAPP-ROLE baremetal: subnet: 192.168.24.0 netmask: 255.255.255.0Edit the
disks_app_vm.ymlfile based on yourlvmconfiguration. The attributes ofVolume Group,Physical Volume, andLogical Volumesmust be edited based on theLVMconfiguration of the VM.When you partitioned
LVMduring installation, you receivedVolume Groupname,Physical Volumename andLogical Volumeswith their partition sizes.This information can be retrieved from any of the VMs (nova Proxy VM or the OVSvApp VM):
tux >sudo pvdisplay# — Physical volume — # PV Name /dev/sda1 # VG Name system # PV Size 80.00 GiB / not usable 3.00 MiB # Allocatable yes # PE Size 4.00 MiB # Total PE 20479 # Free PE 511 # Allocated PE 19968 # PV UUID 7Xn7sm-FdB4-REev-63Z3-uNdM-TF3H-S3ZrIZThe Physical Volume Name is
/dev/sda1. And the Volume Group Name issystem.To find
Logical Volumes:tux >sudo fdisk -l# Disk /dev/sda: 80 GiB, 85899345920 bytes, 167772160 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disklabel type: dos # Disk identifier: 0x0002dc70 # Device Boot Start End Sectors Size Id Type # /dev/sda1 * 2048 167772159 167770112 80G 8e Linux LVM # Disk /dev/mapper/system-root: 60 GiB, 64424509440 bytes, # 125829120 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disk /dev/mapper/system-swap: 2 GiB, 2147483648 bytes, 4194304 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disk /dev/mapper/system-LV_CRASH: 16 GiB, 17179869184 bytes, # 33554432 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # NOTE: Even though we have configured the SWAP partition, it is # not required to be configured in here. Just configure the root # and the LV_CRASH partitionThe line with
/dev/mapper/system-root: 60 GiB, 64424509440 bytesindicates that the first logical partition isroot.The line with
/dev/mapper/system-LV_CRASH: 16 GiB, 17179869184 bytesindicates that the second logical partition isLV_CRASH.The line with
/dev/mapper/system-swap: 2 GiB, 2147483648 bytes, 4194304 sectorsindicates that the third logical partition isswap.
Edit the
disks_app_vm.ymlfile. It is not necessary to configure theswappartition.volume-groups: - name: system (Volume Group Name) physical-volumes: - /dev/sda1 (Physical Volume Name) logical-volumes: - name: root ( Logical Volume 1) size: 75% (Size in percentage) fstype: ext4 ( filesystem type) mount: / ( Mount point) - name: LV_CRASH (Logical Volume 2) size: 20% (Size in percentage) mount: /var/crash (Mount point) fstype: ext4 (filesystem type) mkfs-opts: -O large_fileAn example
disks_app_vm.ymlfile:disks_app_vm.yml --- product: version: 2 disk-models: - name: APP-VM-DISKS # Disk model to be used for application vms such as nova-proxy and ovsvapp # /dev/sda1 is used as a volume group for /, /var/log and /var/crash # Additional disks can be added to either volume group # # NOTE: This is just an example file and has to filled in by the user # based on the lvm partition map for their virtual appliance # While installing the operating system opt for the LVM partition and # create three partitions as shown below # Here is an example partition map # In this example we have three logical partitions # root partition (75%) # swap (5%) and # LV_CRASH (20%) # Run this command 'sudo pvdisplay' on the virtual appliance to see the # output as shown below # # — Physical volume — # PV Name /dev/sda1 # VG Name system # PV Size 80.00 GiB / not usable 3.00 MiB # Allocatable yes # PE Size 4.00 MiB # Total PE 20479 # Free PE 511 # Allocated PE 19968 # PV UUID 7Xn7sm-FdB4-REev-63Z3-uNdM-TF3H-S3ZrIZ # # Next run the following command on the virtual appliance # # sudo fdisk -l # The output will be as shown below # # Disk /dev/sda: 80 GiB, 85899345920 bytes, 167772160 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disklabel type: dos # Disk identifier: 0x0002dc70 # Device Boot Start End Sectors Size Id Type # /dev/sda1 * 2048 167772159 167770112 80G 8e Linux LVM # Disk /dev/mapper/system-root: 60 GiB, 64424509440 bytes, # 125829120 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disk /dev/mapper/system-swap: 2 GiB, 2147483648 bytes, 4194304 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # Disk /dev/mapper/system-LV_CRASH: 16 GiB, 17179869184 bytes, # 33554432 sectors # Units: sectors of 1 * 512 = 512 bytes # Sector size (logical/physical): 512 bytes / 512 bytes # I/O size (minimum/optimal): 512 bytes / 512 bytes # NOTE: Even though we have configured the SWAP partition, it is # not required to be configured in here. Just configure the root # and the LV_CRASH partition volume-groups: - name: system physical-volumes: - /dev/sda1 logical-volumes: - name: root size: 75% fstype: ext4 mount: / - name: LV_CRASH size: 20% mount: /var/crash fstype: ext4 mkfs-opts: -O large_file
27.14 Running the Configuration Processor With Applied Changes #
If the changes are being applied to a previously deployed cloud, then after the previous section is completed, the Configuration Processor should be run with the changes that were applied.
If nodes have been added after deployment, run the
site.ymlplaybook withgenerate_hosts_file.ardana >cd ~/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts site.yml --tag "generate_hosts_file"Run the Configuration Processor
ardana >cd ~/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml \ -e remove_deleted_servers="y" -e free_unused_addresses="y"ardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun the
site.ymlplaybook against only the VMs that were added.ardana >cd ~/scratch/ansible/next/ardana/ansible/ardana >ansible-playbook -i hosts/verb_hosts site.yml --limit hlm004-cp1-esx-comp0001-mgmt, \ hlm004-cp1-esx-ovsvapp0001-mgmt,hlm004-cp1-esx-ovsvapp0002-mgmtAdd nodes to monitoring by running the following playbook on those nodes:
ardana >ansible-playbook -i hosts/verb_hosts monasca-deploy.yml --tags "active_ping_checks"
If the changes are being applied ahead of deploying a new (greenfield) cloud, then after the previous section is completed, the following steps should be run.
Run the Configuration Processor
ardana >cd ~/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun the
site.ymlplaybook against only the VMs that were added.ardana >cd ~/scratch/ansible/next/ardana/ansible/ardana >ansible-playbook -i hosts/verb_hosts site.yml
27.15 Test the ESX-OVSvApp Environment #
When all of the preceding installation steps have been completed, test the ESX-OVSvApp environment with the following steps:
SSH to the Controller
Source the
service.osrcfileCreate a Network
Create a Subnet
Create a VMware-based glance image if there is not one available in the glance repo. The following instructions can be used to create an image that can be used by nova to to create a VM in vCenter.
Download a
vmdkimage file for the corresponding distro that you want for a VM.Create a nova image for VMware Hypervisor
ardana >openstack image create --name DISTRO \ --container-format bare --disk-format vmdk --property vmware_disktype="sparse" \ --property vmware_adaptertype="ide" --property hypervisor_type=vmware < SERVER_CLOUDIMG.VMDK+--------------------+--------------------------------------+ | Property | Value | +--------------------+--------------------------------------+ | checksum | 45a4a06997e64f7120795c68beeb0e3c | | container_format | bare | | created_at | 2018-02-17T10:42:14Z | | disk_format | vmdk | | hypervisor_type | vmware | | id | 17e4915a-ada0-4b95-bacf-ba67133f39a7 | | min_disk | 0 | | min_ram | 0 | | name | leap | | owner | 821b7bb8148f439191d108764301af64 | | protected | False | | size | 372047872 | | status | active | | tags | [] | | updated_at | 2018-02-17T10:42:23Z | | virtual_size | None | | visibility | shared | | vmware_adaptertype | ide | | vmware_disktype | sparse | +--------------------+--------------------------------------+
The image you created needs to be uploaded or saved. Otherwise the size will still be
0.Upload/save the image
ardana >openstack image save --file \ ./SERVER_CLOUDIMG.VMDK 17e4915...133f39a7After saving the image, check that it is active and has a valid size.
ardana >openstack image list+--------------------------------------+------------------------+--------+ | ID | Name | Status | +--------------------------------------+------------------------+--------+ | c48a9349-8e5c-4ca7-81ac-9ed8e2cab3aa | cirros-0.3.2-i386-disk | active | | 17e4915a-ada0-4b95-bacf-ba67133f39a7 | leap | active | +--------------------------------------+------------------------+--------+
Check the details of the image
ardana >openstack image show 17e4915...133f39a7+------------------+------------------------------------------------------------------------------+ | Field | Value | +------------------+------------------------------------------------------------------------------+ | checksum | 45a4a06997e64f7120795c68beeb0e3c | | container_format | bare | | created_at | 2018-02-17T10:42:14Z | | disk_format | vmdk | | file | /v2/images/40aa877c-2b7a-44d6-9b6d-f635dcbafc77/file | | id | 17e4915a-ada0-4b95-bacf-ba67133f39a7 | | min_disk | 0 | | min_ram | 0 | | name | leap | | owner | 821b7bb8148f439191d108764301af64 | | properties | hypervisor_type='vmware', vmware_adaptertype='ide', vmware_disktype='sparse' | | protected | False | | schema | /v2/schemas/image | | size | 372047872 | | status | active | | tags | | | updated_at | 2018-02-17T10:42:23Z | | virtual_size | None | | visibility | shared | +------------------+------------------------------------------------------------------------------+
Create security rules. All security rules must be created before any VMs are created. Otherwise the security rules will have no impact. Rebooting or restarting
neutron-ovsvapp-agentwill have no effect. The following example shows creating a security rule for ICMP:ardana >openstack security group rule create default --protocol icmpCreate a nova instance with the VMware VMDK-based image and target it to the new cluster in the vCenter.
The new VM will appear in the vCenter.
The respective PortGroups for the OVSvApp on the Trunk-DVS will be created and connected.
Test the VM for connectivity and service.
28 Integrating NSX for vSphere #
This section describes the installation and integration of NSX-v, a Software Defined Networking (SDN) network virtualization and security platform for VMware's vSphere.
VMware's NSX embeds networking and security functionality, normally handled by hardware, directly into the hypervisor. NSX can reproduce, in software, an entire networking environment, and provides a complete set of logical networking elements and services including logical switching, routing, firewalling, load balancing, VPN, QoS, and monitoring. Virtual networks are programmatically provisioned and managed independent of the underlying hardware.
VMware's neutron plugin called NSX for vSphere (NSX-v) has been tested under the following scenarios:
Virtual SUSE OpenStack Cloud deployment
Baremetal SUSE OpenStack Cloud deployment
Installation instructions are provided for both scenarios. This documentation is meant as an example of how to integrate VMware's NSX-v neutron plugin with SUSE OpenStack Cloud. The examples in this documentation are not suitable for all environments. To configure this for your specific environment, use the design guide Reference Design: VMware® NSX for vSphere (NSX) Network Virtualization Design Guide.
This section includes instructions for:
Integrating with NSX for vSphere on Baremetal
Integrating with NSX for vSphere on virtual machines with changes necessary for Baremetal integration
Verifying NSX-v functionality
28.1 Integrating with NSX for vSphere #
This section describes the installation steps and requirements for integrating with NSX for vSphere on virtual machines and baremetal hardware.
28.1.1 Pre-Integration Checklist #
The following installation and integration instructions assumes an understanding of VMware's ESXI and vSphere products for setting up virtual environments.
Please review the following requirements for the VMware vSphere environment.
Software Requirements
Before you install or upgrade NSX, verify your software versions. The following are the required versions.
Software | Version |
|---|---|
SUSE OpenStack Cloud | 8 |
VMware NSX-v Manager | 6.3.4 or higher |
VMWare NSX-v neutron Plugin | Pike Release (TAG=11.0.0) |
VMWare ESXi and vSphere Appliance (vSphere web Client) | 6.0 or higher |
A vCenter server (appliance) is required to manage the vSphere environment. It is recommended that you install a vCenter appliance as an ESX virtual machine.
Each ESXi compute cluster is required to have shared storage between the hosts in the cluster, otherwise attempts to create instances through nova-compute will fail.
28.1.2 Installing OpenStack #
OpenStack can be deployed in two ways: on baremetal (physical hardware) or in an ESXi virtual environment on virtual machines. The following instructions describe how to install OpenStack.
Changes for installation on baremetal hardware are noted in each section.
This deployment example will consist of two ESXi clusters at minimum: a
control-plane cluster and a compute
cluster. The control-plane cluster must have 3 ESXi hosts minimum (due to
VMware's recommendation that each NSX controller virtual machine is on a
separate host). The compute cluster must have 2 ESXi hosts minimum. There
can be multiple compute clusters. The following table outlines the virtual
machine specifications to be built in the control-plane cluster:
Virtual Machine Role | Required Number | Disk | Memory | Network | CPU |
|---|---|---|---|---|---|
|
Dedicated lifecycle manager Baremetal - not needed | 1 | 100GB | 8GB | 3 VMXNET Virtual Network Adapters | 4 vCPU |
|
Controller virtual machines Baremetal - not needed | 3 | 3 x 300GB | 32GB | 3 VMXNET Virtual Network Adapters | 8 vCPU |
Compute virtual machines | 1 per compute cluster | 80GB | 4GB | 3 VMXNET Virtual Network Adapters | 2 vCPU |
NSX Edge Gateway/DLR/Metadata-proxy appliances | Autogenerated by NSXv | Autogenerated by NSXv | Autogenerated by NSXv | Autogenerated by NSXv |
Baremetal: In addition to the ESXi hosts, it is recommended to have one physical host for the Cloud Lifecycle Manager node and three physical hosts for the controller nodes.
28.1.2.1 Network Requirements #
NSX-v requires the following for networking:
The ESXi hosts, vCenter, and the NSX Manager appliance must resolve DNS lookup.
The ESXi host must have the NTP service configured and enabled.
Jumbo frames must be enabled on the switch ports that the ESXi hosts are connected to.
The ESXi hosts must have at least 2 physical network cards each.
28.1.2.2 Network Model #
The model in these instructions requires the following networks:
- ESXi Hosts and vCenter
This is the network that the ESXi hosts and vCenter use to route traffic with.
- NSX Management
The network which the NSX controllers and NSX Manager will use.
- NSX VTEP Pool
The network that NSX uses to create endpoints for VxLAN tunnels.
- Management
The network that OpenStack uses for deployment and maintenance of the cloud.
- Internal API (optional)
The network group that will be used for management (private API) traffic within the cloud.
- External API
This is the network that users will use to make requests to the cloud.
- External VM
VLAN-backed provider network for external access to guest VMs (floating IPs).
28.1.2.3 vSphere port security settings #
Baremetal: Even though the OpenStack deployment is on baremetal, it is still necessary to define each VLAN within a vSphere Distributed Switch for the nova compute proxy virtual machine.
The vSphere port security settings for both VMs and baremetal are shown in the table below.
Network Group | VLAN Type | Interface | vSphere Port Group Security Settings |
|---|---|---|---|
ESXi Hosts and vCenter | Tagged | N/A | Defaults |
NSX Manager Must be able to reach ESXi Hosts and vCenter | Tagged | N/A | Defaults |
NSX VTEP Pool | Tagged | N/A | Defaults |
Management | Tagged or Untagged | eth0 |
Promiscuous Mode: Accept MAC Address Changes: Reject Forged Transmits:Reject |
|
Internal API (Optional, may be combined with the Management Network. If network segregation is required for security reasons, you can keep this as a separate network.) | Tagged | eth2 |
Promiscuous Mode: Accept MAC Address Changes: Reject Forged Transmits: Accept |
External API (Public) | Tagged | eth1 |
Promiscuous Mode: Accept MAC Address Changes: Reject Forged Transmits: Accept |
External VM | Tagged | N/A |
Promiscuous Mode: Accept MAC Address Changes: Reject Forged Transmits: Accept |
Baremetal Only: IPMI | Untagged | N/A | N/A |
28.1.2.4 Configuring the vSphere Environment #
Before deploying OpenStack with NSX-v, the VMware vSphere environment must be properly configured, including setting up vSphere distributed switches and port groups. For detailed instructions, see Chapter 27, Installing ESX Computes and OVSvAPP.
Installing and configuring the VMware NSX Manager and creating the NSX network within the vSphere environment is covered below.
Before proceeding with the installation, ensure that the following are configured in the vSphere environment.
The vSphere datacenter is configured with at least two clusters, one control-plane cluster and one compute cluster.
Verify that all software, hardware, and networking requirements have been met.
Ensure the vSphere distributed virtual switches (DVS) are configured for each cluster.
The MTU setting for each DVS should be set to 1600. NSX should automatically apply this setting to each DVS during the setup process. Alternatively, the setting can be manually applied to each DVS before setup if desired.
Make sure there is a copy of the SUSE Linux Enterprise Server 12 SP4 .iso in the
ardana home directory,
var/lib/ardana, and that it is called
sles12sp4.iso.
Install the open-vm-tools package.
tux > sudo zypper install open-vm-tools28.1.2.4.1 Install NSX Manager #
The NSX Manager is the centralized network management component of NSX. It provides a single point of configuration and REST API entry-points.
The NSX Manager is installed as a virtual appliance on one of the ESXi hosts within the vSphere environment. This guide will cover installing the appliance on one of the ESXi hosts within the control-plane cluster. For more detailed information, refer to VMware's NSX Installation Guide.
To install the NSX Manager, download the virtual appliance from VMware and deploy the appliance within vCenter onto one of the ESXi hosts. For information on deploying appliances within vCenter, refer to VMware's documentation for ESXi 5.5 or 6.0.
During the deployment of the NSX Manager appliance, be aware of the following:
When prompted, select . This will present options for configuring IPv4 and IPv6 addresses, the default gateway, DNS, NTP, and SSH properties during the installation, rather than configuring these settings manually after the installation.
Choose an ESXi host that resides within the control-plane cluster.
Ensure that the network mapped port group is the DVS port group that represents the VLAN the NSX Manager will use for its networking (in this example it is labeled as the
NSX Managementnetwork).
The IP address assigned to the NSX Manager must be able to resolve reverse DNS.
Power on the NSX Manager virtual machine after it finishes deploying and wait for the operating system to fully load. When ready, carry out the following steps to have the NSX Manager use single sign-on (SSO) and to register the NSX Manager with vCenter:
Open a web browser and enter the hostname or IP address that was assigned to the NSX Manager during setup.
Log in with the username
adminand the password set during the deployment.After logging in, click on .
Configure the NSX Manager to connect to the vCenter server.
Configure NSX manager for single sign on (SSO) under the section.
When configuring SSO, use Lookup Service Port 443 for
vCenter version 6.0. Use Lookup Service Port 7444 for
vCenter version 5.5.
SSO makes vSphere and NSX more secure by allowing the various components to communicate with each other through a secure token exchange mechanism, instead of requiring each component to authenticate a user separately. For more details, refer to VMware's documentation on Configure Single Sign-On.
Both the Lookup Service URL and the vCenter
Server sections should have a status of
connected when configured properly.
Log into the vSphere Web Client (log out and and back in if already logged in). The NSX Manager will appear under the section of the client.
The section will not appear under the vSphere desktop client. Use of the web client is required for the rest of this process.
28.1.2.4.2 Add NSX Controllers #
The NSX controllers serve as the central control point for all logical switches within the vSphere environment's network, and they maintain information about all hosts, logical switches (VXLANs), and distributed logical routers.
NSX controllers will each be deployed as a virtual appliance on the ESXi hosts within the control-plane cluster to form the NSX Controller cluster. For details about NSX controllers and the NSX control plane in general, refer to VMware's NSX documentation.
Whatever the size of the NSX deployment, the following conditions must be met:
Each NSX Controller cluster must contain three controller nodes. Having a different number of controller nodes is not supported.
Before deploying NSX Controllers, you must deploy an NSX Manager appliance and register vCenter with NSX Manager.
Determine the IP pool settings for your controller cluster, including the gateway and IP address range. DNS settings are optional.
The NSX Controller IP network must have connectivity to the NSX Manager and to the management interfaces on the ESXi hosts.
Log in to the vSphere web client and do the following steps to add the NSX controllers:
In vCenter, navigate to , select › , and then select the tab.
In the section, click the icon represented by a green plus sign.
Enter the NSX Controller settings appropriate to your environment. If you are following this example, use the control-plane clustered ESXi hosts and control-plane DVS port group for the controller settings.
If it has not already been done, create an IP pool for the NSX Controller cluster with at least three IP addressess by clicking . Individual controllers can be in separate IP subnets, if necessary.
Click to deploy the controller. After the first controller is completely deployed, deploy two additional controllers.
Three NSX controllers is mandatory. VMware recommends configuring a DRS anti-affinity rule to prevent the controllers from residing on the same ESXi host. See more information about DRS Affinity Rules.
28.1.2.4.3 Prepare Clusters for NSX Management #
During , the NSX Manager:
Installs the NSX kernel modules on ESXi hosts that are members of vSphere clusters
Builds the NSX control-plane and management-plane infrastructure
The NSX kernel modules are packaged in VIB
(vSphere Installation Bundle) files. They run within the hypervisor kernel and
provide services such as distributed routing, distributed firewall, and VXLAN
bridging capabilities. These files are installed on a per-cluster level, and
the setup process deploys the required software on all ESXi hosts in the
target cluster. When a new ESXi host is added to the cluster, the required
software is automatically installed on the newly added host.
Before beginning the NSX host preparation process, make sure of the following in your environment:
Register vCenter with NSX Manager and deploy the NSX controllers.
Verify that DNS reverse lookup returns a fully qualified domain name when queried with the IP address of NSX Manager.
Verify that the ESXi hosts can resolve the DNS name of vCenter server.
Verify that the ESXi hosts can connect to vCenter Server on port 80.
Verify that the network time on vCenter Server and the ESXi hosts is synchronized.
For each vSphere cluster that will participate in NSX, verify that the ESXi hosts within each respective cluster are attached to a common VDS.
For example, given a deployment with two clusters named Host1 and Host2. Host1 is attached to VDS1 and VDS2. Host2 is attached to VDS1 and VDS3. When you prepare a cluster for NSX, you can only associate NSX with VDS1 on the cluster. If you add another host (Host3) to the cluster and Host3 is not attached to VDS1, it is an invalid configuration, and Host3 will not be ready for NSX functionality.
If you have vSphere Update Manager (VUM) in your environment, you must disable it before preparing clusters for network virtualization. For information on how to check if VUM is enabled and how to disable it if necessary, see the VMware knowledge base.
In the vSphere web client, ensure that the cluster is in the resolved state (listed under the tab). If the Resolve option does not appear in the cluster's Actions list, then it is in a resolved state.
To prepare the vSphere clusters for NSX:
In vCenter, select › › , and then select the tab.
Continuing with the example in these instructions, click on the button (gear icon) and select for both the control-plane cluster and compute cluster (if you are using something other than this example, then only install on the clusters that require NSX logical switching, routing, and firewalls).
Monitor the installation until the
Installation Statuscolumn displays a green check mark.ImportantWhile installation is in progress, do not deploy, upgrade, or uninstall any service or component.
ImportantIf the
Installation Statuscolumn displays a red warning icon and saysNot Ready, click . Clicking might result in a reboot of the host. If the installation is still not successful, click the warning icon. All errors will be displayed. Take the required action and click again.To verify the VIBs (
esx-vsipandesx-vxlan) are installed and registered, SSH into an ESXi host within the prepared cluster. List the names and versions of the VIBs installed by running the following command:tux >esxcli software vib list | grep esx... esx-vsip 6.0.0-0.0.2732470 VMware VMwareCertified 2015-05-29 esx-vxlan 6.0.0-0.0.2732470 VMware VMwareCertified 2015-05-29 ...
After host preparation:
A host reboot is not required
If you add a host to a prepared cluster, the NSX VIBs are automatically installed on the host.
If you move a host to an unprepared cluster, the NSX VIBs are automatically uninstalled from the host. In this case, a host reboot is required to complete the uninstall process.
28.1.2.4.4 Configure VXLAN Transport Parameters #
VXLAN is configured on a per-cluster basis, where each vSphere cluster that is to participate in NSX is mapped to a vSphere Distributed Virtual Switch (DVS). When mapping a vSphere cluster to a DVS, each ESXi host in that cluster is enabled for logical switches. The settings chosen in this section will be used in creating the VMkernel interface.
Configuring transport parameters involves selecting a DVS, a VLAN ID, an MTU size, an IP addressing mechanism, and a NIC teaming policy. The MTU for each switch must be set to 1550 or higher. By default, it is set to 1600 by NSX. This is also the recommended setting for integration with OpenStack.
To configure the VXLAN transport parameters:
In the vSphere web client, navigate to › › .
Select the tab.
Click the link in the VXLAN column.
Enter the required information.
If you have not already done so, create an IP pool for the VXLAN tunnel end points (VTEP) by clicking :
Click to create the VXLAN network.
When configuring the VXLAN transport network, consider the following:
Use a NIC teaming policy that best suits the environment being built.
Load Balance - SRCIDas the VMKNic teaming policy is usually the most flexible out of all the available options. This allows each host to have a VTEP vmkernel interface for each dvuplink on the selected distributed switch (two dvuplinks gives two VTEP interfaces per ESXi host).Do not mix different teaming policies for different portgroups on a VDS where some use Etherchannel or Link Aggregation Control Protocol (LACPv1 or LACPv2) and others use a different teaming policy. If uplinks are shared in these different teaming policies, traffic will be interrupted. If logical routers are present, there will be routing problems. Such a configuration is not supported and should be avoided.
For larger environments it may be better to use DHCP for the VMKNic IP Addressing.
For more information and further guidance, see the VMware NSX for vSphere Network Virtualization Design Guide.
28.1.2.4.5 Assign Segment ID Pool #
Each VXLAN tunnel will need a segment ID to isolate its network traffic. Therefore, it is necessary to configure a segment ID pool for the NSX VXLAN network to use. If an NSX controller is not deployed within the vSphere environment, a multicast address range must be added to spread traffic across the network and avoid overloading a single multicast address.
For the purposes of the example in these instructions, do the following steps to assign a segment ID pool. Otherwise, follow best practices as outlined in VMware's documentation.
In the vSphere web client, navigate to › › .
Select the tab.
Click , and then .
Click to save your changes.
28.1.2.4.6 Create a Transport Zone #
A transport zone controls which hosts a logical switch can reach and has the following characteristics.
It can span one or more vSphere clusters.
Transport zones dictate which clusters can participate in the use of a particular network. Therefore they dictate which VMs can participate in the use of a particular network.
A vSphere NSX environment can contain one or more transport zones based on the environment's requirements.
A host cluster can belong to multiple transport zones.
A logical switch can belong to only one transport zone.
OpenStack has only been verified to work with a single transport zone within a vSphere NSX-v environment. Other configurations are currently not supported.
For more information on transport zones, refer to VMware's Add A Transport Zone.
To create a transport zone:
In the vSphere web client, navigate to › › .
Select the tab.
Click , and then click the (New Logical Switch) icon.
In the dialog box, type a name and an optional description for the transport zone.
For these example instructions, select the control plane mode as
Unicast.NoteWhether there is a controller in the environment or if the environment is going to use multicast addresses will determine the control plane mode to select:
Unicast(what this set of instructions uses): The control plane is handled by an NSX controller. All unicast traffic leverages optimized headend replication. No multicast IP addresses or special network configuration is required.Multicast: Multicast IP addresses in the physical network are used for the control plane. This mode is recommended only when upgrading from older VXLAN deployments. Requires PIM/IGMP in the physical network.Hybrid: Offloads local traffic replication to the physical network (L2 multicast). This requires IGMP snooping on the first-hop switch and access to an IGMP querier in each VTEP subnet, but does not require PIM. The first-hop switch handles traffic replication for the subnet.
Select the clusters to be added to the transport zone.
Click to save your changes.
28.1.2.4.7 Deploying SUSE OpenStack Cloud #
With vSphere environment setup completed, the OpenStack can be deployed. The following sections will cover creating virtual machines within the vSphere environment, configuring the cloud model and integrating NSX-v neutron core plugin into the OpenStack:
Create the virtual machines
Deploy the Cloud Lifecycle Manager
Configure the neutron environment with NSX-v
Modify the cloud input model
Set up the parameters
Deploy the Operating System with Cobbler
Deploy the cloud
28.1.2.5 Deploying SUSE OpenStack Cloud #
Within the vSphere environment, create the OpenStack virtual machines. At minimum, there must be the following:
One Cloud Lifecycle Manager deployer
Three OpenStack controllers
One OpenStack neutron compute proxy
For the minimum NSX hardware requirements, refer to Table 28.1, “NSX Hardware Requirements for Virtual Machine Integration”.
If ESX VMs are to be used as nova compute proxy nodes, set up three LAN interfaces in each virtual machine as shown in the networking model table below. There must be at least one nova compute proxy node per cluster.
Network Group | Interface |
|---|---|
Management |
|
External API |
|
Internal API |
|
28.1.2.5.1 Advanced Configuration Option #
Within vSphere for each in the virtual machine:
In the section, under , ensure that
disk.EnableUUIDoptionis set totrue.If the option does not exist, it must be added. This option is required for the OpenStack deployment.
If the option is not specified, then the deployment will fail when attempting to configure the disks of each virtual machine.
28.1.2.5.2 Setting Up the Cloud Lifecycle Manager #
28.1.2.5.2.1 Installing the Cloud Lifecycle Manager #
Running the ARDANA_INIT_AUTO=1 command is optional to
avoid stopping for authentication at any step. You can also run
ardana-initto launch the Cloud Lifecycle Manager. You will be prompted to
enter an optional SSH passphrase, which is used to protect the key used by
Ansible when connecting to its client nodes. If you do not want to use a
passphrase, press Enter at the prompt.
If you have protected the SSH key with a passphrase, you can avoid having to enter the passphrase on every attempt by Ansible to connect to its client nodes with the following commands:
ardana >eval $(ssh-agent)ardana >ssh-add ~/.ssh/id_rsa
The Cloud Lifecycle Manager will contain the installation scripts and configuration files to deploy your cloud. You can set up the Cloud Lifecycle Manager on a dedicated node or you do so on your first controller node. The default choice is to use the first controller node as the Cloud Lifecycle Manager.
Download the product from:
Boot your Cloud Lifecycle Manager from the SLES ISO contained in the download.
Enter
install(all lower-case, exactly as spelled out here) to start installation.Select the language. Note that only the English language selection is currently supported.
Select the location.
Select the keyboard layout.
Select the primary network interface, if prompted:
Assign IP address, subnet mask, and default gateway
Create new account:
Enter a username.
Enter a password.
Enter time zone.
Once the initial installation is finished, complete the Cloud Lifecycle Manager setup with these steps:
Ensure your Cloud Lifecycle Manager has a valid DNS nameserver specified in
/etc/resolv.conf.Set the environment variable LC_ALL:
export LC_ALL=C
NoteThis can be added to
~/.bashrcor/etc/bash.bashrc.
The node should now have a working SLES setup.
28.1.2.5.3 Configure the Neutron Environment with NSX-v #
In summary, integrating NSX with vSphere has four major steps:
Modify the input model to define the server roles, servers, network roles and networks. Section 28.1.2.5.3.2, “Modify the Input Model”
Set up the parameters needed for neutron and nova to communicate with the ESX and NSX Manager. Section 28.1.2.5.3.3, “Deploying the Operating System with Cobbler”
Do the steps to deploy the cloud. Section 28.1.2.5.3.4, “Deploying the Cloud”
28.1.2.5.3.1 Third-Party Import of VMware NSX-v Into neutron and python-neutronclient #
To import the NSX-v neutron core-plugin into Cloud Lifecycle Manager, run the third-party import playbook.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost third-party-import.yml
28.1.2.5.3.2 Modify the Input Model #
After the third-party import has completed successfully, modify the input model:
Prepare for input model changes
Define the servers and server roles needed for a NSX-v cloud.
Define the necessary networks and network groups
Specify the services needed to be deployed on the Cloud Lifecycle Manager controllers and the nova ESX compute proxy nodes.
Commit the changes and run the configuration processor.
28.1.2.5.3.2.1 Prepare for Input Model Changes #
The previous steps created a modified SUSE OpenStack Cloud tarball with the NSX-v
core plugin in the neutron and neutronclient venvs. The
tar file can now be extracted and the
ardana-init.bash script can be run to set up the
deployment files and directories. If a modified tar file
was not created, then extract the tar from the /media/cdrom/ardana location.
To run the ardana-init.bash script which is included in
the build, use this commands:
ardana > ~/ardana/hos-init.bash28.1.2.5.3.2.2 Create the Input Model #
Copy the example input model to
~/openstack/my_cloud/definition/ directory:
ardana >cd ~/ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsxardana >cp -R entry-scale-nsx ~/openstack/my_cloud/definition
Refer to the reference input model in
ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsx/
for details about how these definitions should be made. The main differences
between this model and the standard Cloud Lifecycle Manager input models are:
Only the neutron-server is deployed. No other neutron agents are deployed.
Additional parameters need to be set in
pass_through.ymlandnsx/nsx_config.yml.nova ESX compute proxy nodes may be ESX virtual machines.
28.1.2.5.3.2.2.1 Set up the Parameters #
The special parameters needed for the NSX-v integrations are set in the
files pass_through.yml and
nsx/nsx_config.yml. They are in the
~/openstack/my_cloud/definition/data directory.
Parameters in pass_through.yml are in the sample input
model in the
ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsx/
directory. The comments in the sample input model file describe how to
locate the values of the required parameters.
#
# (c) Copyright 2017 SUSE LLC
#
# Licensed under the Apache License, Version 2.0 (the "License"); you may
# not use this file except in compliance with the License. You may obtain
# a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
# WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
# License for the specific language governing permissions and limitations
# under the License.
#
---
product:
version: 2
pass-through:
global:
vmware:
- username: VCENTER_ADMIN_USERNAME
ip: VCENTER_IP
port: 443
cert_check: false
# The password needs to be encrypted using the script
# openstack/ardana/ansible/ardanaencrypt.py on the deployer:
#
# $ cd ~/openstack/ardana/ansible
# $ export ARDANA_USER_PASSWORD_ENCRYPT_KEY=ENCRYPTION_KEY
# $ ./ardanaencrypt.py
#
# The script will prompt for the vCenter password. The string
# generated is the encrypted password. Enter the string
# enclosed by double-quotes below.
password: "ENCRYPTED_PASSWD_FROM_ARDANAENCRYPT"
# The id is is obtained by the URL
# https://VCENTER_IP/mob/?moid=ServiceInstance&doPath=content%2eabout,
# field instanceUUID.
id: VCENTER_UUID
servers:
-
# Here the 'id' refers to the name of the node running the
# esx-compute-proxy. This is identical to the 'servers.id' in
# servers.yml. There should be one esx-compute-proxy node per ESX
# resource pool.
id: esx-compute1
data:
vmware:
vcenter_cluster: VMWARE_CLUSTER1_NAME
vcenter_id: VCENTER_UUID
-
id: esx-compute2
data:
vmware:
vcenter_cluster: VMWARE_CLUSTER2_NAME
vcenter_id: VCENTER_UUID
There are parameters in nsx/nsx_config.yml. The
comments describes how to retrieve the values.
# (c) Copyright 2017 SUSE LLC
#
# Licensed under the Apache License, Version 2.0 (the "License"); you may
# not use this file except in compliance with the License. You may obtain
# a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
# WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
# License for the specific language governing permissions and limitations
# under the License.
#
---
product:
version: 2
configuration-data:
- name: NSX-CONFIG-CP1
services:
- nsx
data:
# (Required) URL for NSXv manager (e.g - https://management_ip).
manager_uri: 'https://NSX_MGR_IP
# (Required) NSXv username.
user: 'admin'
# (Required) Encrypted NSX Manager password.
# Password encryption is done by the script
# ~/openstack/ardana/ansible/ardanaencrypt.py on the deployer:
#
# $ cd ~/openstack/ardana/ansible
# $ export ARDANA_USER_PASSWORD_ENCRYPT_KEY=ENCRYPTION_KEY
# $ ./ardanaencrypt.py
#
# NOTE: Make sure that the NSX Manager password is encrypted with the same key
# used to encrypt the VCenter password.
#
# The script will prompt for the NSX Manager password. The string
# generated is the encrypted password. Enter the string enclosed
# by double-quotes below.
password: "ENCRYPTED_NSX_MGR_PASSWD_FROM_ARDANAENCRYPT"
# (Required) datacenter id for edge deployment.
# Retrieved using
# http://VCENTER_IP_ADDR/mob/?moid=ServiceInstance&doPath=content
# click on the value from the rootFolder property. The datacenter_moid is
# the value of the childEntity property.
# The vCenter-ip-address comes from the file pass_through.yml in the
# input model under "pass-through.global.vmware.ip".
datacenter_moid: 'datacenter-21'
# (Required) id of logic switch for physical network connectivity.
# How to retrieve
# 1. Get to the same page where the datacenter_moid is found.
# 2. Click on the value of the rootFolder property.
# 3. Click on the value of the childEntity property
# 4. Look at the network property. The external network is
# network associated with EXTERNAL VM in VCenter.
external_network: 'dvportgroup-74'
# (Required) clusters ids containing OpenStack hosts.
# Retrieved using http://VCENTER_IP_ADDR/mob, click on the value
# from the rootFolder property. Then click on the value of the
# hostFolder property. Cluster_moids are the values under childEntity
# property of the compute clusters.
cluster_moid: 'domain-c33,domain-c35'
# (Required) resource-pool id for edge deployment.
resource_pool_id: 'resgroup-67'
# (Optional) datastore id for edge deployment. If not needed,
# do not declare it.
# datastore_id: 'datastore-117'
# (Required) network scope id of the transport zone.
# To get the vdn_scope_id, in the vSphere web client from the Home
# menu:
# 1. click on Networking & Security
# 2. click on installation
# 3. click on the Logical Netowrk Preparation tab.
# 4. click on the Transport Zones button.
# 5. Double click on the transport zone being configure.
# 6. Select Manage tab.
# 7. The vdn_scope_id will appear at the end of the URL.
vdn_scope_id: 'vdnscope-1'
# (Optional) Dvs id for VLAN based networks. If not needed,
# do not declare it.
# dvs_id: 'dvs-68'
# (Required) backup_edge_pool: backup edge pools management range,
# - edge_type>[edge_size]:MINIMUM_POOLED_EDGES:MAXIMUM_POOLED_EDGES
# - edge_type: service (service edge) or vdr (distributed edge)
# - edge_size: compact , large (by default), xlarge or quadlarge
backup_edge_pool: 'service:compact:4:10,vdr:compact:4:10'
# (Optional) mgt_net_proxy_ips: management network IP address for
# metadata proxy. If not needed, do not declare it.
# mgt_net_proxy_ips: '10.142.14.251,10.142.14.252'
# (Optional) mgt_net_proxy_netmask: management network netmask for
# metadata proxy. If not needed, do not declare it.
# mgt_net_proxy_netmask: '255.255.255.0'
# (Optional) mgt_net_moid: Network ID for management network connectivity
# Do not declare if not used.
# mgt_net_moid: 'dvportgroup-73'
# ca_file: Name of the certificate file. If insecure is set to True,
# then this parameter is ignored. If insecure is set to False and this
# parameter is not defined, then the system root CAs will be used
# to verify the server certificate.
ca_file: a/nsx/certificate/file
# insecure:
# If true (default), the NSXv server certificate is not verified.
# If false, then the default CA truststore is used for verification.
# This option is ignored if "ca_file" is set
insecure: True
# (Optional) edge_ha: if true, will duplicate any edge pool resources
# Default to False if undeclared.
# edge_ha: False
# (Optional) spoofguard_enabled:
# If True (default), indicates NSXV spoofguard component is used to
# implement port-security feature.
# spoofguard_enabled: True
# (Optional) exclusive_router_appliance_size:
# Edge appliance size to be used for creating exclusive router.
# Valid values: 'compact', 'large', 'xlarge', 'quadlarge'
# Defaults to 'compact' if not declared. # exclusive_router_appliance_size:
'compact'28.1.2.5.3.2.3 Commit Changes and Run the Configuration Processor #
Commit your changes with the input model and the required configuration
values added to the pass_through.yml and
nsx/nsx_config.yml files.
ardana >cd ~/openstack/my_cloud/definitionardana >git commit -A -m "Configuration changes for NSX deployment"ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml \ -e \encrypt="" -e rekey=""
If the playbook config-processor-run.yml fails, there is
an error in the input model. Fix the error and repeat the above steps.
28.1.2.5.3.3 Deploying the Operating System with Cobbler #
From the Cloud Lifecycle Manager, run Cobbler to install the operating system on the nodes after it has to be deployed:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.ymlVerify the nodes that will have an operating system installed by Cobbler by running this command:
tux >sudo cobbler system find --netboot-enabled=1Reimage the nodes using Cobbler. Do not use Cobbler to reimage the nodes running as ESX virtual machines. The command below is run on a setup where the nova ESX compute proxies are VMs. Controllers 1, 2, and 3 are running on physical servers.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml -e \ nodelist=controller1,controller2,controller3When the playbook has completed, each controller node should have an operating system installed with an IP address configured on
eth0.After your controller nodes have been completed, you should install the operating system on your nova compute proxy virtual machines. Each configured virtual machine should be able to PXE boot into the operating system installer.
From within the vSphere environment, power on each nova compute proxy virtual machine and watch for it to PXE boot into the OS installer via its console.
If successful, the virtual machine will have the operating system automatically installed and will then automatically power off.
When the virtual machine has powered off, power it on and let it boot into the operating system.
Verify network settings after deploying the operating system to each node.
Verify that the NIC bus mapping specified in the cloud model input file (
~/ardana/my_cloud/definition/data/nic_mappings.yml) matches the NIC bus mapping on each OpenStack node.Check the NIC bus mapping with this command:
tux >sudo cobbler system listAfter the playbook has completed, each controller node should have an operating system installed with an IP address configured on eth0.
When the ESX compute proxy nodes are VMs, install the operating system if you have not already done so.
28.1.2.5.3.4 Deploying the Cloud #
When the configuration processor has completed successfully, the cloud can be
deployed. Set the ARDANA_USER_PASSWORD_ENCRYPT_KEY environment
variable before running site.yml.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >export ARDANA_USER_PASSWORD_ENCRYPT_KEY=PASSWORD_KEYardana >ansible-playbook -i hosts/verb_hosts site.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-cloud-configure.yml
PASSWORD_KEY in the export
command is the key used to encrypt the passwords for vCenter and NSX Manager.
28.2 Integrating with NSX for vSphere on Baremetal #
This section describes the installation steps and requirements for integrating with NSX for vSphere on baremetal physical hardware.
28.2.1 Pre-Integration Checklist #
The following installation and integration instructions assumes an understanding of VMware's ESXI and vSphere products for setting up virtual environments.
Please review the following requirements for the VMware vSphere environment.
Software Requirements
Before you install or upgrade NSX, verify your software versions. The following are the required versions.
|
Software |
Version |
|---|---|
|
SUSE OpenStack Cloud |
8 |
|
VMware NSX-v Manager |
6.3.4 or higher |
|
VMWare NSX-v neutron Plugin |
Pike Release (TAG=11.0.0) |
|
VMWare ESXi and vSphere Appliance (vSphere web Client) |
6.0 or higher |
A vCenter server (appliance) is required to manage the vSphere environment. It is recommended that you install a vCenter appliance as an ESX virtual machine.
Each ESXi compute cluster is required to have shared storage between the hosts in the cluster, otherwise attempts to create instances through nova-compute will fail.
28.2.2 Installing on Baremetal #
OpenStack can be deployed in two ways: on baremetal (physical hardware) or in an ESXi virtual environment on virtual machines. The following instructions describe how to install OpenStack on baremetal nodes with vCenter and NSX Manager running as virtual machines. For instructions on virtual machine installation, see Section 28.1, “Integrating with NSX for vSphere”.
This deployment example will consist of two ESXi clusters at minimum: a
control-plane cluster and a compute
cluster. The control-plane cluster must have 3 ESXi hosts minimum (due to
VMware's recommendation that each NSX controller virtual machine is on a
separate host). The compute cluster must have 2 ESXi hosts minimum. There
can be multiple compute clusters. The following table outlines the virtual
machine specifications to be built in the control-plane cluster:
|
Virtual Machine Role |
Required Number |
Disk |
Memory |
Network |
CPU |
|---|---|---|---|---|---|
|
Compute virtual machines |
1 per compute cluster |
80GB |
4GB |
3 VMXNET Virtual Network Adapters |
2 vCPU |
|
NSX Edge Gateway/DLR/Metadata-proxy appliances |
Autogenerated by NSXv |
Autogenerated by NSXv |
Autogenerated by NSXv |
Autogenerated by NSXv |
In addition to the ESXi hosts, it is recommended that there is one physical host for the Cloud Lifecycle Manager node and three physical hosts for the controller nodes.
28.2.2.1 Network Requirements #
NSX-v requires the following for networking:
The ESXi hosts, vCenter, and the NSX Manager appliance must resolve DNS lookup.
The ESXi host must have the NTP service configured and enabled.
Jumbo frames must be enabled on the switch ports that the ESXi hosts are connected to.
The ESXi hosts must have at least 2 physical network cards each.
28.2.2.2 Network Model #
The model in these instructions requires the following networks:
- ESXi Hosts and vCenter
This is the network that the ESXi hosts and vCenter use to route traffic with.
- NSX Management
The network which the NSX controllers and NSX Manager will use.
- NSX VTEP Pool
The network that NSX uses to create endpoints for VxLAN tunnels.
- Management
The network that OpenStack uses for deployment and maintenance of the cloud.
- Internal API (optional)
The network group that will be used for management (private API) traffic within the cloud.
- External API
This is the network that users will use to make requests to the cloud.
- External VM
VLAN-backed provider network for external access to guest VMs (floating IPs).
28.2.2.3 vSphere port security settings #
Even though the OpenStack deployment is on baremetal, it is still necessary to define each VLAN within a vSphere Distributed Switch for the nova compute proxy virtual machine. Therefore, the vSphere port security settings are shown in the table below.
|
Network Group |
VLAN Type |
Interface |
vSphere Port Group Security Settings |
|---|---|---|---|
|
IPMI |
Untagged |
N/A |
N/A |
|
ESXi Hosts and vCenter |
Tagged |
N/A |
Defaults |
|
NSX Manager Must be able to reach ESXi Hosts and vCenter |
Tagged |
N/A |
Defaults |
|
NSX VTEP Pool |
Tagged |
N/A |
Defaults |
|
Management |
Tagged or Untagged |
bond0 |
|
|
Internal API (Optional, may be combined with the Management Network. If network segregation is required for security reasons, you can keep this as a separate network.) |
Tagged |
bond0 |
|
|
External API (Public) |
Tagged |
N/A |
|
|
External VM |
Tagged |
N/A |
|
28.2.2.4 Configuring the vSphere Environment #
Before deploying OpenStack with NSX-v, the VMware vSphere environment must be properly configured, including setting up vSphere distributed switches and port groups. For detailed instructions, see Chapter 27, Installing ESX Computes and OVSvAPP.
Installing and configuring the VMware NSX Manager and creating the NSX network within the vSphere environment is covered below.
Before proceeding with the installation, ensure that the following are configured in the vSphere environment.
The vSphere datacenter is configured with at least two clusters, one control-plane cluster and one compute cluster.
Verify that all software, hardware, and networking requirements have been met.
Ensure the vSphere distributed virtual switches (DVS) are configured for each cluster.
The MTU setting for each DVS should be set to 1600. NSX should automatically apply this setting to each DVS during the setup process. Alternatively, the setting can be manually applied to each DVS before setup if desired.
Make sure there is a copy of the SUSE Linux Enterprise Server 12 SP4 .iso in the
ardana home directory,
var/lib/ardana, and that it is called
sles12sp4.iso.
Install the open-vm-tools package.
tux > sudo zypper install open-vm-tools28.2.2.4.1 Install NSX Manager #
The NSX Manager is the centralized network management component of NSX. It provides a single point of configuration and REST API entry-points.
The NSX Manager is installed as a virtual appliance on one of the ESXi hosts within the vSphere environment. This guide will cover installing the appliance on one of the ESXi hosts within the control-plane cluster. For more detailed information, refer to VMware's NSX Installation Guide.
To install the NSX Manager, download the virtual appliance from VMware and deploy the appliance within vCenter onto one of the ESXi hosts. For information on deploying appliances within vCenter, refer to VMware's documentation for ESXi 5.5 or 6.0.
During the deployment of the NSX Manager appliance, be aware of the following:
When prompted, select . This will present options for configuring IPv4 and IPv6 addresses, the default gateway, DNS, NTP, and SSH properties during the installation, rather than configuring these settings manually after the installation.
Choose an ESXi host that resides within the control-plane cluster.
Ensure that the network mapped port group is the DVS port group that represents the VLAN the NSX Manager will use for its networking (in this example it is labeled as the
NSX Managementnetwork).
The IP address assigned to the NSX Manager must be able to resolve reverse DNS.
Power on the NSX Manager virtual machine after it finishes deploying and wait for the operating system to fully load. When ready, carry out the following steps to have the NSX Manager use single sign-on (SSO) and to register the NSX Manager with vCenter:
Open a web browser and enter the hostname or IP address that was assigned to the NSX Manager during setup.
Log in with the username
adminand the password set during the deployment.After logging in, click on .
Configure the NSX Manager to connect to the vCenter server.
Configure NSX manager for single sign on (SSO) under the section.
When configuring SSO, use Lookup Service Port 443 for
vCenter version 6.0. Use Lookup Service Port 7444 for
vCenter version 5.5.
SSO makes vSphere and NSX more secure by allowing the various components to communicate with each other through a secure token exchange mechanism, instead of requiring each component to authenticate a user separately. For more details, refer to VMware's documentation on Configure Single Sign-On.
Both the Lookup Service URL and the vCenter
Server sections should have a status of
connected when configured properly.
Log into the vSphere Web Client (log out and and back in if already logged in). The NSX Manager will appear under the section of the client.
The section will not appear under the vSphere desktop client. Use of the web client is required for the rest of this process.
28.2.2.4.2 Add NSX Controllers #
The NSX controllers serve as the central control point for all logical switches within the vSphere environment's network, and they maintain information about all hosts, logical switches (VXLANs), and distributed logical routers.
NSX controllers will each be deployed as a virtual appliance on the ESXi hosts within the control-plane cluster to form the NSX Controller cluster. For details about NSX controllers and the NSX control plane in general, refer to VMware's NSX documentation.
Whatever the size of the NSX deployment, the following conditions must be met:
Each NSX Controller cluster must contain three controller nodes. Having a different number of controller nodes is not supported.
Before deploying NSX Controllers, you must deploy an NSX Manager appliance and register vCenter with NSX Manager.
Determine the IP pool settings for your controller cluster, including the gateway and IP address range. DNS settings are optional.
The NSX Controller IP network must have connectivity to the NSX Manager and to the management interfaces on the ESXi hosts.
Log in to the vSphere web client and do the following steps to add the NSX controllers:
In vCenter, navigate to , select › , and then select the tab.
In the section, click the icon represented by a green plus sign.
Enter the NSX Controller settings appropriate to your environment. If you are following this example, use the control-plane clustered ESXi hosts and control-plane DVS port group for the controller settings.
If it has not already been done, create an IP pool for the NSX Controller cluster with at least three IP addressess by clicking . Individual controllers can be in separate IP subnets, if necessary.
Click to deploy the controller. After the first controller is completely deployed, deploy two additional controllers.
Three NSX controllers is mandatory. VMware recommends configuring a DRS anti-affinity rule to prevent the controllers from residing on the same ESXi host. See more information about DRS Affinity Rules.
28.2.2.4.3 Prepare Clusters for NSX Management #
During , the NSX Manager:
Installs the NSX kernel modules on ESXi hosts that are members of vSphere clusters
Builds the NSX control-plane and management-plane infrastructure
The NSX kernel modules are packaged in VIB (vSphere
Installation Bundle) files. They run within the hypervisor kernel and
provide services such as distributed routing, distributed firewall, and
VXLAN bridging capabilities. These files are installed on a per-cluster
level, and the setup process deploys the required software on all ESXi
hosts in the target cluster. When a new ESXi host is added to the cluster,
the required software is automatically installed on the newly added host.
Before beginning the NSX host preparation process, make sure of the following in your environment:
Register vCenter with NSX Manager and deploy the NSX controllers.
Verify that DNS reverse lookup returns a fully qualified domain name when queried with the IP address of NSX Manager.
Verify that the ESXi hosts can resolve the DNS name of vCenter server.
Verify that the ESXi hosts can connect to vCenter Server on port 80.
Verify that the network time on vCenter Server and the ESXi hosts is synchronized.
For each vSphere cluster that will participate in NSX, verify that the ESXi hosts within each respective cluster are attached to a common VDS.
For example, given a deployment with two clusters named Host1 and Host2. Host1 is attached to VDS1 and VDS2. Host2 is attached to VDS1 and VDS3. When you prepare a cluster for NSX, you can only associate NSX with VDS1 on the cluster. If you add another host (Host3) to the cluster and Host3 is not attached to VDS1, it is an invalid configuration, and Host3 will not be ready for NSX functionality.
If you have vSphere Update Manager (VUM) in your environment, you must disable it before preparing clusters for network virtualization. For information on how to check if VUM is enabled and how to disable it if necessary, see the VMware knowledge base.
In the vSphere web client, ensure that the cluster is in the resolved state (listed under the tab). If the Resolve option does not appear in the cluster's Actions list, then it is in a resolved state.
To prepare the vSphere clusters for NSX:
In vCenter, select › › , and then select the tab.
Continuing with the example in these instructions, click on the button (gear icon) and select for both the control-plane cluster and compute cluster (if you are using something other than this example, then only install on the clusters that require NSX logical switching, routing, and firewalls).
Monitor the installation until the
Installation Statuscolumn displays a green check mark.ImportantWhile installation is in progress, do not deploy, upgrade, or uninstall any service or component.
ImportantIf the
Installation Statuscolumn displays a red warning icon and saysNot Ready, click . Clicking might result in a reboot of the host. If the installation is still not successful, click the warning icon. All errors will be displayed. Take the required action and click again.To verify the VIBs (
esx-vsipandesx-vxlan) are installed and registered, SSH into an ESXi host within the prepared cluster. List the names and versions of the VIBs installed by running the following command:tux >esxcli software vib list | grep esx... esx-vsip 6.0.0-0.0.2732470 VMware VMwareCertified 2015-05-29 esx-vxlan 6.0.0-0.0.2732470 VMware VMwareCertified 2015-05-29 ...
After host preparation:
A host reboot is not required
If you add a host to a prepared cluster, the NSX VIBs are automatically installed on the host.
If you move a host to an unprepared cluster, the NSX VIBs are automatically uninstalled from the host. In this case, a host reboot is required to complete the uninstall process.
28.2.2.4.4 Configure VXLAN Transport Parameters #
VXLAN is configured on a per-cluster basis, where each vSphere cluster that is to participate in NSX is mapped to a vSphere Distributed Virtual Switch (DVS). When mapping a vSphere cluster to a DVS, each ESXi host in that cluster is enabled for logical switches. The settings chosen in this section will be used in creating the VMkernel interface.
Configuring transport parameters involves selecting a DVS, a VLAN ID, an MTU size, an IP addressing mechanism, and a NIC teaming policy. The MTU for each switch must be set to 1550 or higher. By default, it is set to 1600 by NSX. This is also the recommended setting for integration with OpenStack.
To configure the VXLAN transport parameters:
In the vSphere web client, navigate to › › .
Select the tab.
Click the link in the VXLAN column.
Enter the required information.
If you have not already done so, create an IP pool for the VXLAN tunnel end points (VTEP) by clicking :
Click to create the VXLAN network.
When configuring the VXLAN transport network, consider the following:
Use a NIC teaming policy that best suits the environment being built.
Load Balance - SRCIDas the VMKNic teaming policy is usually the most flexible out of all the available options. This allows each host to have a VTEP vmkernel interface for each dvuplink on the selected distributed switch (two dvuplinks gives two VTEP interfaces per ESXi host).Do not mix different teaming policies for different portgroups on a VDS where some use Etherchannel or Link Aggregation Control Protocol (LACPv1 or LACPv2) and others use a different teaming policy. If uplinks are shared in these different teaming policies, traffic will be interrupted. If logical routers are present, there will be routing problems. Such a configuration is not supported and should be avoided.
For larger environments it may be better to use DHCP for the VMKNic IP Addressing.
For more information and further guidance, see the VMware NSX for vSphere Network Virtualization Design Guide.
28.2.2.4.5 Assign Segment ID Pool #
Each VXLAN tunnel will need a segment ID to isolate its network traffic. Therefore, it is necessary to configure a segment ID pool for the NSX VXLAN network to use. If an NSX controller is not deployed within the vSphere environment, a multicast address range must be added to spread traffic across the network and avoid overloading a single multicast address.
For the purposes of the example in these instructions, do the following steps to assign a segment ID pool. Otherwise, follow best practices as outlined in VMware's documentation.
In the vSphere web client, navigate to › › .
Select the tab.
Click , and then .
Click to save your changes.
28.2.2.4.6 Assign Segment ID Pool #
Each VXLAN tunnel will need a segment ID to isolate its network traffic. Therefore, it is necessary to configure a segment ID pool for the NSX VXLAN network to use. If an NSX controller is not deployed within the vSphere environment, a multicast address range must be added to spread traffic across the network and avoid overloading a single multicast address.
For the purposes of the example in these instructions, do the following steps to assign a segment ID pool. Otherwise, follow best practices as outlined in VMware's documentation.
In the vSphere web client, navigate to › › .
Select the tab.
Click , and then .
Click to save your changes.
28.2.2.4.7 Create a Transport Zone #
A transport zone controls which hosts a logical switch can reach and has the following characteristics.
It can span one or more vSphere clusters.
Transport zones dictate which clusters can participate in the use of a particular network. Therefore they dictate which VMs can participate in the use of a particular network.
A vSphere NSX environment can contain one or more transport zones based on the environment's requirements.
A host cluster can belong to multiple transport zones.
A logical switch can belong to only one transport zone.
OpenStack has only been verified to work with a single transport zone within a vSphere NSX-v environment. Other configurations are currently not supported.
For more information on transport zones, refer to VMware's Add A Transport Zone.
To create a transport zone:
In the vSphere web client, navigate to › › .
Select the tab.
Click , and then click the (New Logical Switch) icon.
In the dialog box, type a name and an optional description for the transport zone.
For these example instructions, select the control plane mode as
Unicast.NoteWhether there is a controller in the environment or if the environment is going to use multicast addresses will determine the control plane mode to select:
Unicast(what this set of instructions uses): The control plane is handled by an NSX controller. All unicast traffic leverages optimized headend replication. No multicast IP addresses or special network configuration is required.Multicast: Multicast IP addresses in the physical network are used for the control plane. This mode is recommended only when upgrading from older VXLAN deployments. Requires PIM/IGMP in the physical network.Hybrid: Offloads local traffic replication to the physical network (L2 multicast). This requires IGMP snooping on the first-hop switch and access to an IGMP querier in each VTEP subnet, but does not require PIM. The first-hop switch handles traffic replication for the subnet.
Select the clusters to be added to the transport zone.
Click to save your changes.
28.2.2.4.8 Deploying SUSE OpenStack Cloud #
With vSphere environment setup completed, the OpenStack can be deployed. The following sections will cover creating virtual machines within the vSphere environment, configuring the cloud model and integrating NSX-v neutron core plugin into the OpenStack:
Create the virtual machines
Deploy the Cloud Lifecycle Manager
Configure the neutron environment with NSX-v
Modify the cloud input model
Set up the parameters
Deploy the Operating System with Cobbler
Deploy the cloud
28.2.2.4.9 Deploying SUSE OpenStack Cloud on Baremetal #
Within the vSphere environment, create the OpenStack compute proxy virtual machines. There needs to be one neutron compute proxy virtual machine per ESXi compute cluster.
For the minimum NSX hardware requirements, refer to Table 28.2, “NSX Hardware Requirements for Baremetal Integration”. Also be aware of the networking model to use for the VM network interfaces, see Table 28.3, “NSX Interface Requirements”:
If ESX VMs are to be used as nova compute proxy nodes, set up three LAN interfaces in each virtual machine as shown in the table below. There is at least one nova compute proxy node per cluster.
|
Network Group |
Interface |
|---|---|
|
Management |
|
|
External API |
|
|
Internal API |
|
28.2.2.4.9.1 Advanced Configuration Option #
Within vSphere for each in the virtual machine:
In the section, under , ensure that
disk.EnableUUIDoptionis set totrue.If the option does not exist, it must be added. This option is required for the OpenStack deployment.
If the option is not specified, then the deployment will fail when attempting to configure the disks of each virtual machine.
28.2.2.4.9.2 Setting Up the Cloud Lifecycle Manager #
28.2.2.4.9.2.1 Installing the Cloud Lifecycle Manager #
Running the ARDANA_INIT_AUTO=1 command is optional to
avoid stopping for authentication at any step. You can also run
ardana-initto launch the Cloud Lifecycle Manager. You will be prompted to
enter an optional SSH passphrase, which is used to protect the key used by
Ansible when connecting to its client nodes. If you do not want to use a
passphrase, press Enter at the prompt.
If you have protected the SSH key with a passphrase, you can avoid having to enter the passphrase on every attempt by Ansible to connect to its client nodes with the following commands:
ardana >eval $(ssh-agent)ardana >ssh-add ~/.ssh/id_rsa
The Cloud Lifecycle Manager will contain the installation scripts and configuration files to deploy your cloud. You can set up the Cloud Lifecycle Manager on a dedicated node or you do so on your first controller node. The default choice is to use the first controller node as the Cloud Lifecycle Manager.
Download the product from:
Boot your Cloud Lifecycle Manager from the SLES ISO contained in the download.
Enter
install(all lower-case, exactly as spelled out here) to start installation.Select the language. Note that only the English language selection is currently supported.
Select the location.
Select the keyboard layout.
Select the primary network interface, if prompted:
Assign IP address, subnet mask, and default gateway
Create new account:
Enter a username.
Enter a password.
Enter time zone.
Once the initial installation is finished, complete the Cloud Lifecycle Manager setup with these steps:
Ensure your Cloud Lifecycle Manager has a valid DNS nameserver specified in
/etc/resolv.conf.Set the environment variable LC_ALL:
export LC_ALL=C
NoteThis can be added to
~/.bashrcor/etc/bash.bashrc.
The node should now have a working SLES setup.
28.2.2.4.9.3 Configure the Neutron Environment with NSX-v #
In summary, integrating NSX with vSphere has four major steps:
Modify the input model to define the server roles, servers, network roles and networks. Section 28.1.2.5.3.2, “Modify the Input Model”
Set up the parameters needed for neutron and nova to communicate with the ESX and NSX Manager. Section 28.1.2.5.3.3, “Deploying the Operating System with Cobbler”
Do the steps to deploy the cloud. Section 28.1.2.5.3.4, “Deploying the Cloud”
28.2.2.4.9.3.1 Third-Party Import of VMware NSX-v Into neutron and python-neutronclient #
To import the NSX-v neutron core-plugin into Cloud Lifecycle Manager, run the third-party import playbook.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost third-party-import.yml
28.2.2.4.9.3.2 Modify the Input Model #
After the third-party import has completed successfully, modify the input model:
Prepare for input model changes
Define the servers and server roles needed for a NSX-v cloud.
Define the necessary networks and network groups
Specify the services needed to be deployed on the Cloud Lifecycle Manager controllers and the nova ESX compute proxy nodes.
Commit the changes and run the configuration processor.
28.2.2.4.9.3.2.1 Prepare for Input Model Changes #
The previous steps created a modified SUSE OpenStack Cloud tarball with the
NSX-v core plugin in the neutron and neutronclient
venvs. The tar file can now be extracted and the
ardana-init.bash script can be run to set up the
deployment files and directories. If a modified
tar file was not created, then extract the tar
from the /media/cdrom/ardana location.
To run the ardana-init.bash script which is
included in the build, use this commands:
ardana > ~/ardana/hos-init.bash28.2.2.4.9.3.2.2 Create the Input Model #
Copy the example input model to
~/openstack/my_cloud/definition/ directory:
ardana >cd ~/ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsxardana >cp -R entry-scale-nsx ~/openstack/my_cloud/definition
Refer to the reference input model in
ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsx/
for details about how these definitions should be made. The main
differences between this model and the standard Cloud Lifecycle Manager input models are:
Only the neutron-server is deployed. No other neutron agents are deployed.
Additional parameters need to be set in
pass_through.ymlandnsx/nsx_config.yml.nova ESX compute proxy nodes may be ESX virtual machines.
28.2.2.4.9.3.2.2.1 Set up the Parameters #
The special parameters needed for the NSX-v integrations are set in
the files pass_through.yml and
nsx/nsx_config.yml. They are in the
~/openstack/my_cloud/definition/data directory.
Parameters in pass_through.yml are in the sample
input model in the
ardana-extensions/ardana-extensions-nsx/vmware/examples/models/entry-scale-nsx/
directory. The comments in the sample input model file describe how to
locate the values of the required parameters.
#
# (c) Copyright 2017 SUSE LLC
#
# Licensed under the Apache License, Version 2.0 (the "License"); you may
# not use this file except in compliance with the License. You may obtain
# a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
# WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
# License for the specific language governing permissions and limitations
# under the License.
#
---
product:
version: 2
pass-through:
global:
vmware:
- username: VCENTER_ADMIN_USERNAME
ip: VCENTER_IP
port: 443
cert_check: false
# The password needs to be encrypted using the script
# openstack/ardana/ansible/ardanaencrypt.py on the deployer:
#
# $ cd ~/openstack/ardana/ansible
# $ export ARDANA_USER_PASSWORD_ENCRYPT_KEY=ENCRYPTION_KEY
# $ ./ardanaencrypt.py
#
# The script will prompt for the vCenter password. The string
# generated is the encrypted password. Enter the string
# enclosed by double-quotes below.
password: "ENCRYPTED_PASSWD_FROM_ARDANAENCRYPT"
# The id is is obtained by the URL
# https://VCENTER_IP/mob/?moid=ServiceInstance&doPath=content%2eabout,
# field instanceUUID.
id: VCENTER_UUID
servers:
-
# Here the 'id' refers to the name of the node running the
# esx-compute-proxy. This is identical to the 'servers.id' in
# servers.yml. There should be one esx-compute-proxy node per ESX
# resource pool.
id: esx-compute1
data:
vmware:
vcenter_cluster: VMWARE_CLUSTER1_NAME
vcenter_id: VCENTER_UUID
-
id: esx-compute2
data:
vmware:
vcenter_cluster: VMWARE_CLUSTER2_NAME
vcenter_id: VCENTER_UUID
There are parameters in nsx/nsx_config.yml. The
comments describes how to retrieve the values.
# (c) Copyright 2017 SUSE LLC
#
# Licensed under the Apache License, Version 2.0 (the "License"); you may
# not use this file except in compliance with the License. You may obtain
# a copy of the License at
#
# http://www.apache.org/licenses/LICENSE-2.0
#
# Unless required by applicable law or agreed to in writing, software
# distributed under the License is distributed on an "AS IS" BASIS, WITHOUT
# WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the
# License for the specific language governing permissions and limitations
# under the License.
#
---
product:
version: 2
configuration-data:
- name: NSX-CONFIG-CP1
services:
- nsx
data:
# (Required) URL for NSXv manager (e.g - https://management_ip).
manager_uri: 'https://NSX_MGR_IP
# (Required) NSXv username.
user: 'admin'
# (Required) Encrypted NSX Manager password.
# Password encryption is done by the script
# ~/openstack/ardana/ansible/ardanaencrypt.py on the deployer:
#
# $ cd ~/openstack/ardana/ansible
# $ export ARDANA_USER_PASSWORD_ENCRYPT_KEY=ENCRYPTION_KEY
# $ ./ardanaencrypt.py
#
# NOTE: Make sure that the NSX Manager password is encrypted with the same key
# used to encrypt the VCenter password.
#
# The script will prompt for the NSX Manager password. The string
# generated is the encrypted password. Enter the string enclosed
# by double-quotes below.
password: "ENCRYPTED_NSX_MGR_PASSWD_FROM_ARDANAENCRYPT"
# (Required) datacenter id for edge deployment.
# Retrieved using
# http://VCENTER_IP_ADDR/mob/?moid=ServiceInstance&doPath=content
# click on the value from the rootFolder property. The datacenter_moid is
# the value of the childEntity property.
# The vCenter-ip-address comes from the file pass_through.yml in the
# input model under "pass-through.global.vmware.ip".
datacenter_moid: 'datacenter-21'
# (Required) id of logic switch for physical network connectivity.
# How to retrieve
# 1. Get to the same page where the datacenter_moid is found.
# 2. Click on the value of the rootFolder property.
# 3. Click on the value of the childEntity property
# 4. Look at the network property. The external network is
# network associated with EXTERNAL VM in VCenter.
external_network: 'dvportgroup-74'
# (Required) clusters ids containing OpenStack hosts.
# Retrieved using http://VCENTER_IP_ADDR/mob, click on the value
# from the rootFolder property. Then click on the value of the
# hostFolder property. Cluster_moids are the values under childEntity
# property of the compute clusters.
cluster_moid: 'domain-c33,domain-c35'
# (Required) resource-pool id for edge deployment.
resource_pool_id: 'resgroup-67'
# (Optional) datastore id for edge deployment. If not needed,
# do not declare it.
# datastore_id: 'datastore-117'
# (Required) network scope id of the transport zone.
# To get the vdn_scope_id, in the vSphere web client from the Home
# menu:
# 1. click on Networking & Security
# 2. click on installation
# 3. click on the Logical Netowrk Preparation tab.
# 4. click on the Transport Zones button.
# 5. Double click on the transport zone being configure.
# 6. Select Manage tab.
# 7. The vdn_scope_id will appear at the end of the URL.
vdn_scope_id: 'vdnscope-1'
# (Optional) Dvs id for VLAN based networks. If not needed,
# do not declare it.
# dvs_id: 'dvs-68'
# (Required) backup_edge_pool: backup edge pools management range,
# - edge_type>[edge_size]:MINIMUM_POOLED_EDGES:MAXIMUM_POOLED_EDGES
# - edge_type: service (service edge) or vdr (distributed edge)
# - edge_size: compact , large (by default), xlarge or quadlarge
backup_edge_pool: 'service:compact:4:10,vdr:compact:4:10'
# (Optional) mgt_net_proxy_ips: management network IP address for
# metadata proxy. If not needed, do not declare it.
# mgt_net_proxy_ips: '10.142.14.251,10.142.14.252'
# (Optional) mgt_net_proxy_netmask: management network netmask for
# metadata proxy. If not needed, do not declare it.
# mgt_net_proxy_netmask: '255.255.255.0'
# (Optional) mgt_net_moid: Network ID for management network connectivity
# Do not declare if not used.
# mgt_net_moid: 'dvportgroup-73'
# ca_file: Name of the certificate file. If insecure is set to True,
# then this parameter is ignored. If insecure is set to False and this
# parameter is not defined, then the system root CAs will be used
# to verify the server certificate.
ca_file: a/nsx/certificate/file
# insecure:
# If true (default), the NSXv server certificate is not verified.
# If false, then the default CA truststore is used for verification.
# This option is ignored if "ca_file" is set
insecure: True
# (Optional) edge_ha: if true, will duplicate any edge pool resources
# Default to False if undeclared.
# edge_ha: False
# (Optional) spoofguard_enabled:
# If True (default), indicates NSXV spoofguard component is used to
# implement port-security feature.
# spoofguard_enabled: True
# (Optional) exclusive_router_appliance_size:
# Edge appliance size to be used for creating exclusive router.
# Valid values: 'compact', 'large', 'xlarge', 'quadlarge'
# Defaults to 'compact' if not declared. # exclusive_router_appliance_size:
'compact'28.2.2.4.9.3.2.3 Commit Changes and Run the Configuration Processor #
Commit your changes with the input model and the required configuration
values added to the pass_through.yml and
nsx/nsx_config.yml files.
ardana >cd ~/openstack/my_cloud/definitionardana >git commit -A -m "Configuration changes for NSX deployment"ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml \ -e \encrypt="" -e rekey=""
If the playbook config-processor-run.yml fails,
there is an error in the input model. Fix the error and repeat the
above steps.
28.2.2.4.9.3.3 Deploying the Operating System with Cobbler #
From the Cloud Lifecycle Manager, run Cobbler to install the operating system on the nodes after it has to be deployed:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.ymlVerify the nodes that will have an operating system installed by Cobbler by running this command:
tux >sudo cobbler system find --netboot-enabled=1Reimage the nodes using Cobbler. Do not use Cobbler to reimage the nodes running as ESX virtual machines. The command below is run on a setup where the nova ESX compute proxies are VMs. Controllers 1, 2, and 3 are running on physical servers.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml -e \ nodelist=controller1,controller2,controller3When the playbook has completed, each controller node should have an operating system installed with an IP address configured on
eth0.After your controller nodes have been completed, you should install the operating system on your nova compute proxy virtual machines. Each configured virtual machine should be able to PXE boot into the operating system installer.
From within the vSphere environment, power on each nova compute proxy virtual machine and watch for it to PXE boot into the OS installer via its console.
If successful, the virtual machine will have the operating system automatically installed and will then automatically power off.
When the virtual machine has powered off, power it on and let it boot into the operating system.
Verify network settings after deploying the operating system to each node.
Verify that the NIC bus mapping specified in the cloud model input file (
~/ardana/my_cloud/definition/data/nic_mappings.yml) matches the NIC bus mapping on each OpenStack node.Check the NIC bus mapping with this command:
tux >sudo cobbler system listAfter the playbook has completed, each controller node should have an operating system installed with an IP address configured on eth0.
When the ESX compute proxy nodes are VMs, install the operating system if you have not already done so.
28.2.2.4.9.3.4 Deploying the Cloud #
When the configuration processor has completed successfully, the cloud
can be deployed. Set the ARDANA_USER_PASSWORD_ENCRYPT_KEY environment
variable before running site.yml.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >export ARDANA_USER_PASSWORD_ENCRYPT_KEY=PASSWORD_KEYardana >ansible-playbook -i hosts/verb_hosts site.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-cloud-configure.yml
PASSWORD_KEY in the export
command is the key used to encrypt the passwords for vCenter and NSX
Manager.
28.3 Verifying the NSX-v Functionality After Integration #
After you have completed your OpenStack deployment and integrated the NSX-v neutron plugin, you can use these steps to verify that NSX-v is enabled and working in the environment.
Validating neutron from the Cloud Lifecycle Manager. All of these commands require that you authenticate by
service.osrcfile.ardana >source ~/service.osrcList your neutron networks:
ardana >openstack network list +--------------------------------------+----------------+-------------------------------------------------------+ | id | name | subnets | +--------------------------------------+----------------+-------------------------------------------------------+ | 574d5f6c-871e-47f8-86d2-4b7c33d91002 | inter-edge-net | c5e35e22-0c1c-4886-b7f3-9ce3a6ab1512 169.254.128.0/17 | +--------------------------------------+----------------+-------------------------------------------------------+List your neutron subnets:
ardana >openstack subnet list +--------------------------------------+-------------------+------------------+------------------------------------------------------+ | id | name | cidr | allocation_pools | +--------------------------------------+-------------------+------------------+------------------------------------------------------+ | c5e35e22-0c1c-4886-b7f3-9ce3a6ab1512 | inter-edge-subnet | 169.254.128.0/17 | {"start": "169.254.128.2", "end": "169.254.255.254"} | +--------------------------------------+-------------------+------------------+------------------------------------------------------+List your neutron routers:
ardana >openstack router list +--------------------------------------+-----------------------+-----------------------+-------------+ | id | name | external_gateway_info | distributed | +--------------------------------------+-----------------------+-----------------------+-------------+ | 1c5bf781-5120-4b7e-938b-856e23e9f156 | metadata_proxy_router | null | False | | 8b5d03bf-6f77-4ea9-bb27-87dd2097eb5c | metadata_proxy_router | null | False | +--------------------------------------+-----------------------+-----------------------+-------------+List your neutron ports:
ardana >openstack port list +--------------------------------------+------+-------------------+------------------------------------------------------+ | id | name | mac_address | fixed_ips | +--------------------------------------+------+-------------------+------------------------------------------------------+ | 7f5f0461-0db4-4b9a-a0c6-faa0010b9be2 | | fa:16:3e:e5:50:d4 | {"subnet_id": | | | | | "c5e35e22-0c1c-4886-b7f3-9ce3a6ab1512", | | | | | "ip_address": "169.254.128.2"} | | 89f27dff-f38d-4084-b9b0-ded495255dcb | | fa:16:3e:96:a0:28 | {"subnet_id": | | | | | "c5e35e22-0c1c-4886-b7f3-9ce3a6ab1512", | | | | | "ip_address": "169.254.128.3"} | +--------------------------------------+------+-------------------+------------------------------------------------------+List your neutron security group rules:
ardana >openstack security group rule list +--------------------------------------+----------------+-----------+-----------+---------------+-----------------+ | id | security_group | direction | ethertype | protocol/port | remote | +--------------------------------------+----------------+-----------+-----------+---------------+-----------------+ | 0385bd3a-1050-4bc2-a212-22ddab00c488 | default | egress | IPv6 | any | any | | 19f6f841-1a9a-4b4b-bc45-7e8501953d8f | default | ingress | IPv6 | any | default (group) | | 1b3b5925-7aa6-4b74-9df0-f417ee6218f1 | default | egress | IPv4 | any | any | | 256953cc-23d7-404d-b140-2600d55e44a2 | default | ingress | IPv4 | any | default (group) | | 314c4e25-5822-44b4-9d82-4658ae87d93f | default | egress | IPv6 | any | any | | 59d4a71e-9f99-4b3b-b75b-7c9ad34081e0 | default | ingress | IPv6 | any | default (group) | | 887e25ef-64b7-4b69-b301-e053f88efa6c | default | ingress | IPv4 | any | default (group) | | 949e9744-75cd-4ae2-8cc6-6c0f578162d7 | default | ingress | IPv4 | any | default (group) | | 9a83027e-d6d6-4b6b-94fa-7c0ced2eba37 | default | egress | IPv4 | any | any | | abf63b79-35ad-428a-8829-8e8d796a9917 | default | egress | IPv4 | any | any | | be34b72b-66b6-4019-b782-7d91674ca01d | default | ingress | IPv6 | any | default (group) | | bf3d87ce-05c8-400d-88d9-a940e43760ca | default | egress | IPv6 | any | any | +--------------------------------------+----------------+-----------+-----------+---------------+-----------------+
Verify metadata proxy functionality
To test that the metadata proxy virtual machines are working as intended, verify that there are at least two metadata proxy virtual machines from within vSphere (there will be four if edge high availability was set to true).
When that is verified, create a new compute instance either with the API, CLI, or within the cloud console GUI and log into the instance. From within the instance, using curl, grab the metadata instance-id from the metadata proxy address.
ardana > curl http://169.254.169.254/latest/meta-data/instance-id
i-0000000429 Installing Baremetal (Ironic) #
Bare Metal as a Service is enabled in this release for deployment of nova instances on bare metal nodes using flat networking.
29.1 Installation for SUSE OpenStack Cloud Entry-scale Cloud with Ironic Flat Network #
This page describes the installation step requirements for the SUSE OpenStack Cloud Entry-scale Cloud with ironic Flat Network.
29.1.1 Configure Your Environment #
Prior to deploying an operational environment with ironic, operators need to be aware of the nature of TLS certificate authentication. As pre-built deployment agent ramdisks images are supplied, these ramdisk images will only authenticate known third-party TLS Certificate Authorities in the interest of end-to-end security. As such, uses of self-signed certificates and private certificate authorities will be unable to leverage ironic without modifying the supplied ramdisk images.
Set up your configuration files, as follows:
See the sample sets of configuration files in the
~/openstack/examples/directory. Each set will have an accompanying README.md file that explains the contents of each of the configuration files.Copy the example configuration files into the required setup directory and edit them to contain the details of your environment:
cp -r ~/openstack/examples/entry-scale-ironic-flat-network/* \ ~/openstack/my_cloud/definition/
(Optional) You can use the
ardanaencrypt.pyscript to encrypt your IPMI passwords. This script uses OpenSSL.Change to the Ansible directory:
ardana >cd ~/openstack/ardana/ansiblePut the encryption key into the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Run the python script below and follow the instructions. Enter a password that you want to encrypt.
ardana >./ardanaencrypt.pyTake the string generated and place it in the
ilo-passwordfield in your~/openstack/my_cloud/definition/data/servers.ymlfile, remembering to enclose it in quotes.Repeat the above for each server.
NoteBefore you run any playbooks, remember that you need to export the encryption key in the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"ImportantThis step needs to be repeated any time you make changes to your configuration files before you move on to the following steps. See Chapter 22, Using Git for Configuration Management for more information.
29.1.2 Provisioning Your Baremetal Nodes #
To provision the baremetal nodes in your cloud deployment you can either use the automated operating system installation process provided by SUSE OpenStack Cloud or you can use the 3rd party installation tooling of your choice. We will outline both methods below:
29.1.2.1 Using Third Party Baremetal Installers #
If you do not wish to use the automated operating system installation tooling included with SUSE OpenStack Cloud then the requirements that have to be met using the installation tooling of your choice are:
The operating system must be installed via the SLES ISO provided on the SUSE Customer Center.
Each node must have SSH keys in place that allows the same user from the Cloud Lifecycle Manager node who will be doing the deployment to SSH to each node without a password.
Passwordless sudo needs to be enabled for the user.
There should be a LVM logical volume as
/rooton each node.If the LVM volume group name for the volume group holding the
rootLVM logical volume isardana-vg, then it will align with the disk input models in the examples.Ensure that
openssh-server,python,python-apt, andrsyncare installed.
If you chose this method for installing your baremetal hardware, skip forward to the step Running the Configuration Processor.
29.1.2.2 Using the Automated Operating System Installation Provided by SUSE OpenStack Cloud #
If you would like to use the automated operating system installation tools provided by SUSE OpenStack Cloud, complete the steps below.
29.1.2.2.1 Deploying Cobbler #
This phase of the install process takes the baremetal information that was
provided in servers.yml and installs the Cobbler
provisioning tool and loads this information into Cobbler. This sets each
node to netboot-enabled: true in Cobbler. Each node
will be automatically marked as netboot-enabled: false
when it completes its operating system install successfully. Even if the
node tries to PXE boot subsequently, Cobbler will not serve it. This is
deliberate so that you cannot reimage a live node by accident.
The cobbler-deploy.yml playbook prompts for a password
- this is the password that will be encrypted and stored in Cobbler, which
is associated with the user running the command on the Cloud Lifecycle Manager, that you
will use to log in to the nodes via their consoles after install. The
username is the same as the user set up in the initial dialogue when
installing the Cloud Lifecycle Manager from the ISO, and is the same user that is running
the cobbler-deploy play.
When imaging servers with your own tooling, it is still necessary to have
ILO/IPMI settings for all nodes. Even if you are not using Cobbler, the
username and password fields in servers.yml need to
be filled in with dummy settings. For example, add the following to
servers.yml:
ilo-user: manual ilo-password: deployment
Run the following playbook which confirms that there is IPMI connectivity for each of your nodes so that they are accessible to be re-imaged in a later step:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-power-status.ymlRun the following playbook to deploy Cobbler:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.yml
29.1.2.2.2 Imaging the Nodes #
This phase of the install process goes through a number of distinct steps:
Powers down the nodes to be installed
Sets the nodes hardware boot order so that the first option is a network boot.
Powers on the nodes. (The nodes will then boot from the network and be installed using infrastructure set up in the previous phase)
Waits for the nodes to power themselves down (this indicates a successful install). This can take some time.
Sets the boot order to hard disk and powers on the nodes.
Waits for the nodes to be reachable by SSH and verifies that they have the signature expected.
Deploying nodes has been automated in the Cloud Lifecycle Manager and requires the following:
All of your nodes using SLES must already be installed, either manually or via Cobbler.
Your input model should be configured for your SLES nodes.
You should have run the configuration processor and the
ready-deployment.ymlplaybook.
Execute the following steps to re-image one or more nodes after you have
run the ready-deployment.yml playbook.
Run the following playbook, specifying your SLES nodes using the nodelist. This playbook will reconfigure Cobbler for the nodes listed.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook prepare-sles-grub2.yml -e \ nodelist=node1[,node2,node3]Re-image the node(s) with the following command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml \ -e nodelist=node1[,node2,node3]
If a nodelist is not specified then the set of nodes in Cobbler with
netboot-enabled: True is selected. The playbook pauses
at the start to give you a chance to review the set of nodes that it is
targeting and to confirm that it is correct.
You can use the command below which will list all of your nodes with the
netboot-enabled: True flag set:
sudo cobbler system find --netboot-enabled=1
29.1.3 Running the Configuration Processor #
Once you have your configuration files setup, you need to run the configuration processor to complete your configuration.
When you run the configuration processor, you will be prompted for two
passwords. Enter the first password to make the configuration processor
encrypt its sensitive data, which consists of the random inter-service
passwords that it generates and the ansible group_vars
and host_vars that it produces for subsequent deploy
runs. You will need this password for subsequent Ansible deploy and
configuration processor runs. If you wish to change an encryption password
that you have already used when running the configuration processor then
enter the new password at the second prompt, otherwise just press
Enter to bypass this.
Run the configuration processor with this command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml
For automated installation (for example CI), you can specify the required passwords on the ansible command line. For example, the command below will disable encryption by the configuration processor:
ardana > ansible-playbook -i hosts/localhost config-processor-run.yml \
-e encrypt="" -e rekey=""If you receive an error during this step, there is probably an issue with one or more of your configuration files. Verify that all information in each of your configuration files is correct for your environment. Then commit those changes to Git using the instructions in the previous section before re-running the configuration processor again.
For any troubleshooting information regarding these steps, see Section 36.2, “Issues while Updating Configuration Files”.
29.1.4 Deploying the Cloud #
Use the playbook below to create a deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
[OPTIONAL] - Run the
wipe_disks.ymlplaybook to ensure all of your non-OS partitions on your nodes are completely wiped before continuing with the installation. Thewipe_disks.ymlplaybook is only meant to be run on systems immediately after runningbm-reimage.yml. If used for any other case, it may not wipe all of the expected partitions.If you are using fresh machines this step may not be necessary.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts wipe_disks.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts wipe_disks.yml --ask-vault-passRun the
site.ymlplaybook below:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts site.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts site.yml --ask-vault-passNoteThe step above runs
osconfigto configure the cloud andardana-deployto deploy the cloud. Therefore, this step may run for a while, perhaps 45 minutes or more, depending on the number of nodes in your environment.Verify that the network is working correctly. Ping each IP in the
/etc/hostsfile from one of the controller nodes.
For any troubleshooting information regarding these steps, see Section 36.3, “Issues while Deploying the Cloud”.
29.1.5 Ironic configuration #
Run the ironic-cloud-configure.yml playbook below:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ironic-cloud-configure.yml
This step configures ironic flat network, uploads glance images and sets the ironic configuration.
To see the images uploaded to glance, run:
$ source ~/service.osrc $ openstack image list
This will produce output like the following example, showing three images that have been added by ironic:
+--------------------------------------+--------------------------+ | ID | Name | +--------------------------------------+--------------------------+ | d4e2a0ff-9575-4bed-ac5e-5130a1553d93 | ir-deploy-iso-HOS3.0 | | b759a1f0-3b33-4173-a6cb-be5706032124 | ir-deploy-kernel-HOS3.0 | | ce5f4037-e368-46f2-941f-c01e9072676c | ir-deploy-ramdisk-HOS3.0 | +--------------------------------------+--------------------------+
To see the network created by ironic, run:
$ openstack network list
This returns details of the "flat-net" generated by the ironic install:
+---------------+----------+-------------------------------------------------------+ | id | name | subnets | +---------------+----------+-------------------------------------------------------+ | f9474...11010 | flat-net | ca8f8df8-12c8-4e58-b1eb-76844c4de7e8 192.168.245.0/24 | +---------------+----------+-------------------------------------------------------+
29.1.6 Node Configuration #
29.1.6.1 DHCP #
Once booted, nodes obtain network configuration via DHCP. If multiple interfaces are to be utilized, you may want to pre-build images with settings to execute DHCP on all interfaces. An easy way to build custom images is with KIWI, the command line utility to build Linux system appliances.
For information about building custom KIWI images, see Section 29.3.13, “Building glance Images Using KIWI”. For more information, see the KIWI documentation at https://osinside.github.io/kiwi/.
29.1.6.2 Configuration Drives #
Configuration Drives are stored unencrypted and should not include any sensitive data.
You can use Configuration Drives to store metadata for initial boot
setting customization. Configuration Drives are extremely useful for
initial machine configuration. However, as a general security practice,
they should not include any
sensitive data. Configuration Drives should only be trusted upon the initial
boot of an instance. cloud-init utilizes a lock file for
this purpose. Custom instance images should not rely upon the integrity of a
Configuration Drive beyond the initial boot of a host as an administrative
user within a deployed instance can potentially modify a configuration drive
once written to disk and released for use.
For more information about Configuration Drives, see http://docs.openstack.org/user-guide/cli_config_drive.html.
29.1.7 TLS Certificates with Ironic Python Agent (IPA) Images #
As part of SUSE OpenStack Cloud 9, ironic Python Agent, better known as IPA in the
OpenStack community, images are supplied and loaded into glance. Two types of
image exist. One is a traditional boot ramdisk which is used by the
agent_ipmitool, pxe_ipmitool, and
pxe_ilo drivers. The other is an ISO image that is
supplied as virtual media to the host when using the
agent_ilo driver.
As these images are built in advance, they are unaware of any private certificate authorities. Users attempting to utilize self-signed certificates or a private certificate authority will need to inject their signing certificate(s) into the image in order for IPA to be able to boot on a remote node, and ensure that the TLS endpoints being connected to in SUSE OpenStack Cloud can be trusted. This is not an issue with publicly signed certificates.
As two different types of images exist, below are instructions for
disassembling the image ramdisk file or the ISO image. Once this has been
done, you will need to re-upload the files to glance, and update any impacted
node's driver_info, for example, the
deploy_ramdisk and ilo_deploy_iso
settings that were set when the node was first defined. Respectively, this
can be done with the
ironic node-update <node> replace driver_info/deploy_ramdisk=<glance_id>
or
ironic node-update <node> replace driver_info/ilo_deploy_iso=<glance_id>
29.1.7.1 Add New Trusted CA Certificate Into Deploy Images #
Perform the following steps.
To upload your trusted CA certificate to the Cloud Lifecycle Manager, follow the directions in Section 41.7, “Upload to the Cloud Lifecycle Manager”.
Delete the deploy images.
ardana >openstack image delete ir-deploy-iso-ARDANA5.0ardana >openstack image delete ir-deploy-ramdisk-ARDANA5.0On the deployer, run
ironic-reconfigure.ymlplaybook to re-upload the images that include the new trusted CA bundle.ardana >cd /var/lib/ardana/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ironic-reconfigure.ymlUpdate the existing ironic nodes with the new image IDs accordingly. For example,
ardana >openstack baremetal node set --driver-info \ deploy_ramdisk=NEW_RAMDISK_ID NODE_ID
29.2 ironic in Multiple Control Plane #
SUSE OpenStack Cloud 9 introduces the concept of multiple control planes - see the Input Model documentation for the relevant Section 5.2.2.1, “Control Planes and Regions” and Section 6.2.3, “Multiple Control Planes”. This document covers the use of an ironic region in a multiple control plane cloud model in SUSE OpenStack Cloud.
29.2.1 Networking for Baremetal in Multiple Control Plane #
IRONIC-FLAT-NET is the network configuration for baremetal control plane.
You need to set the environment variable OS_REGION_NAME to the ironic region in baremetal control plane. This will set up the ironic flat networking in neutron.
export OS_REGION_NAME=<ironic_region>
To see details of the IRONIC-FLAT-NETWORK created during
configuration, use the following command:
openstack network list
Referring to the diagram below, the Cloud Lifecycle Manager is a shared service that runs in a Core API Controller in a Core API Cluster. ironic Python Agent (IPA) must be able to make REST API calls to the ironic API (the connection is represented by the green line to Internal routing). The IPA connect to swift to get user images (the gray line connecting to swift routing).
29.2.2 Handling Optional swift Service #
swift is resource-intensive and as a result, it is now optional in the SUSE OpenStack Cloud control plane. A number of services depend on swift, and if it is not present, they must provide a fallback strategy. For example, glance can use the filesystem in place of swift for its backend store.
In ironic, agent-based drivers require swift. If it is not present, it is
necessary to disable access to this ironic feature in the control plane. The
enable_agent_driver flag has been added to the ironic
configuration data and can have values of true or
false. Setting this flag to false will
disable swift configurations and the agent based drivers in the ironic
control plane.
29.2.3 Instance Provisioning #
In a multiple control plane cloud setup, changes for glance container name
in the swift namespace of ironic-conductor.conf
introduces a conflict with the one in glance-api.conf.
Provisioning with agent-based drivers requires the container name to be the
same in ironic and glance. Hence, on instance provisioning with agent-based
drivers (swift-enabled), the agent is not able to fetch the images from
glance store and fails at that point.
You can resolve this issue using the following steps:
Copy the value of
swift_store_containerfrom the file/opt/stack/service/glance-api/etc/glance-api.confLog in to the Cloud Lifecycle Manager and use the value for
swift_containerin glance namespace of~/scratch/ansible/next/ardana/ansible/roles/ironic-common/templates/ironic-conductor.conf.j2Run the following playbook:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
29.3 Provisioning Bare-Metal Nodes with Flat Network Model #
Providing bare-metal resources to an untrusted third party is not advised as a malicious user can potentially modify hardware firmware.
The steps outlined in Section 29.1.7, “TLS Certificates with Ironic Python Agent (IPA) Images” must be performed.
A number of drivers are available to provision and manage bare-metal machines. The drivers are named based on the deployment mode and the power management interface. SUSE OpenStack Cloud has been tested with the following drivers:
agent_ilo
agent_ipmi
pxe_ilo
pxe_ipmi
Redfish
Before you start, you should be aware that:
Node Cleaning is enabled for all the drivers in SUSE OpenStack Cloud 9.
Node parameter settings must have matching flavors in terms of
cpus,local_gb, andmemory_mb,boot_modeandcpu_arch.It is advisable that nodes enrolled for ipmitool drivers are pre-validated in terms of BIOS settings, in terms of boot mode, prior to setting capabilities.
Network cabling and interface layout should also be pre-validated in any given particular boot mode or configuration that is registered.
The use of
agent_drivers is predicated upon glance images being backed by a swift image store, specifically the need for the temporary file access features. Using the file system as a glance back-end image store means that theagent_drivers cannot be used.Manual Cleaning (RAID) and Node inspection is supported by ilo drivers (
agent_iloandpxe_ilo)
29.3.1 Redfish Protocol Support #
Redfish is a successor to the Intelligent Platform Management Interface (IPMI) with the ability to scale to larger and more diverse cloud deployments. It has an API that allows users to collect performance data from heterogeneous server installations and more data sources than could be handled previously. It is based on an industry standard protocol with a RESTful interface for managing cloud assets that are compliant with the Redfish protocol.
There are two known limitations to using Redfish.
RAID configuration does not work due to missing HPE Smart Storage Administrator CLI (HPE SSACLI) in the default deploy RAM disk. This is a licensing issue.
The ironic
inspectorinspect interface is not supported.
Enable the Redfish driver with the following steps:
Install the Sushy library on the ironic-conductor nodes. Sushy is a Python library for communicating with Redfish-based systems with ironic. More information is available at https://opendev.org/openstack/sushy/.
sudo pip install sushy
Add
redfishto the list ofenabled_hardware_types,enabled_power_interfacesandenabled_management_interfacesin/etc/ironic/ironic.confas shown below:[DEFAULT] ... enabled_hardware_types = ipmi,redfish enabled_power_interfaces = ipmitool,redfish enabled_management_interfaces = ipmitool,redfish
Restart the ironic-conductor service:
sudo systemctl restart openstack-ironic-conductor
To continue with Redfish, see Section 29.3.4, “Registering a Node with the Redfish Driver”.
29.3.2 Supplied Images #
As part of the SUSE OpenStack Cloud Entry-scale ironic Cloud installation, ironic Python Agent (IPA) images are supplied and loaded into glance. To see the images that have been loaded, execute the following commands on the deployer node:
$ source ~/service.osrc openstack image list
This will display three images that have been added by ironic:
Deploy_iso : openstack-ironic-image.x86_64-8.0.0.kernel.4.4.120-94.17-default Deploy_kernel : openstack-ironic-image.x86_64-8.0.0.xz Deploy_ramdisk : openstack-ironic-image.x86_64-8.0.0.iso
The ir-deploy-ramdisk image is a traditional boot ramdisk
used by the agent_ipmitool,
pxe_ipmitool, and pxe_ilo drivers
while ir-deploy-iso is an ISO image that is supplied as
virtual media to the host when using the agent_ilo
driver.
29.3.3 Provisioning a Node #
The information required to provision a node varies slightly depending on the driver used. In general the following details are required.
Network access information and credentials to connect to the management interface of the node.
Sufficient properties to allow for nova flavor matching.
A deployment image to perform the actual deployment of the guest operating system to the bare-metal node.
A combination of the ironic node-create and
ironic node-update commands are used for registering a
node's characteristics with the ironic service. In particular,
ironic node-update <nodeid>
add and ironic node-update
<nodeid> replace can be used to
modify the properties of a node after it has been created while
ironic node-update <nodeid>
remove will remove a property.
29.3.4 Registering a Node with the Redfish Driver #
Nodes configured to use the Redfish driver should have the driver property
set to redfish.
The following properties are specified in the driver_info
field of the node:
redfish_address(required)The URL address to the Redfish controller. It must include the authority portion of the URL, and can optionally include the scheme. If the scheme is missing, HTTPS is assumed.
redfish_system_id(required)The canonical path to the system resource that the driver interacts with. It should include the root service, version and the unique path to the system resource. For example,
/redfish/v1/Systems/1.redfish_username (recommended)User account with admin and server-profile access privilege.
redfish_password(recommended)User account password.
redfish_verify_ca(optional)If
redfish_addresshas the HTTPS scheme, the driver will use a secure (TLS) connection when talking to the Redfish controller. By default (if this is not set or set toTrue), the driver will try to verify the host certificates. This can be set to the path of a certificate file or directory with trusted certificates that the driver will use for verification. To disable verifying TLS, set this toFalse.
The openstack baremetal node create command is used
to enroll a node with the Redfish driver. For example:
openstack baremetal node create --driver redfish --driver-info \ redfish_address=https://example.com --driver-info \ redfish_system_id=/redfish/v1/Systems/CX34R87 --driver-info \ redfish_username=admin --driver-info redfish_password=password
29.3.5 Creating a Node Using agent_ilo #
If you want to use a boot mode of BIOS as opposed to UEFI, then you need to ensure that the boot mode has been set correctly on the IPMI:
While the iLO driver can automatically set a node to boot in UEFI mode via
the boot_mode defined capability, it cannot set BIOS boot
mode once UEFI mode has been set.
Use the ironic node-create command to specify the
agent_ilo driver, network access and credential
information for the IPMI, properties of the node and the glance ID of the
supplied ISO IPA image. Note that memory size is specified in megabytes while
disk size is specified in gigabytes.
ironic node-create -d agent_ilo -i ilo_address=IP_ADDRESS -i \ ilo_username=Administrator -i ilo_password=PASSWORD \ -p cpus=2 -p cpu_arch=x86_64 -p memory_mb=64000 -p local_gb=99 \ -i ilo_deploy_iso=DEPLOY_UUID
This will generate output similar to the following:
+--------------+---------------------------------------------------------------+
| Property | Value |
+--------------+---------------------------------------------------------------+
| uuid | NODE_UUID |
| driver_info | {u'ilo_address': u'IP_ADDRESS', u'ilo_password': u'******', |
| | u'ilo_deploy_iso': u'DEPLOY_UUID', |
| | u'ilo_username': u'Administrator'} |
| extra | {} |
| driver | agent_ilo |
| chassis_uuid | |
| properties | {u'memory_mb': 64000, u'local_gb': 99, u'cpus': 2, |
| | u'cpu_arch': u'x86_64'} |
| name | None |
+--------------+---------------------------------------------------------------+
Now update the node with boot_mode and
boot_option properties:
ironic node-update NODE_UUID add \ properties/capabilities="boot_mode:bios,boot_option:local"
The ironic node-update command returns details for all of
the node's characteristics.
+------------------------+------------------------------------------------------------------+
| Property | Value |
+------------------------+------------------------------------------------------------------+
| target_power_state | None |
| extra | {} |
| last_error | None |
| updated_at | None |
| maintenance_reason | None |
| provision_state | available |
| clean_step | {} |
| uuid | NODE_UUID |
| console_enabled | False |
| target_provision_state | None |
| provision_updated_at | None |
| maintenance | False |
| inspection_started_at | None |
| inspection_finished_at | None |
| power_state | None |
| driver | agent_ilo |
| reservation | None |
| properties | {u'memory_mb': 64000, u'cpu_arch': u'x86_64', u'local_gb': 99, |
| | u'cpus': 2, u'capabilities': u'boot_mode:bios,boot_option:local'}|
| instance_uuid | None |
| name | None |
| driver_info | {u'ilo_address': u'10.1.196.117', u'ilo_password': u'******', |
| | u'ilo_deploy_iso': u'DEPLOY_UUID', |
| | u'ilo_username': u'Administrator'} |
| created_at | 2016-03-11T10:17:10+00:00 |
| driver_internal_info | {} |
| chassis_uuid | |
| instance_info | {} |
+------------------------+------------------------------------------------------------------+29.3.6 Creating a Node Using agent_ipmi #
Use the ironic node-create command to specify the
agent_ipmi driver, network access and credential
information for the IPMI, properties of the node and the glance IDs of the
supplied kernel and ramdisk images. Note that memory size is specified in
megabytes while disk size is specified in gigabytes.
ironic node-create -d agent_ipmitool \
-i ipmi_address=IP_ADDRESS \
-i ipmi_username=Administrator -i ipmi_password=PASSWORD \
-p cpus=2 -p memory_mb=64000 -p local_gb=99 -p cpu_arch=x86_64 \
-i deploy_kernel=KERNEL_UUID \
-i deploy_ramdisk=RAMDISK_UUIDThis will generate output similar to the following:
+--------------+-----------------------------------------------------------------------+
| Property | Value |
+--------------+-----------------------------------------------------------------------+
| uuid | NODE2_UUID |
| driver_info | {u'deploy_kernel': u'KERNEL_UUID', |
| | u'ipmi_address': u'IP_ADDRESS', u'ipmi_username': u'Administrator', |
| | u'ipmi_password': u'******', |
| | u'deploy_ramdisk': u'RAMDISK_UUID'} |
| extra | {} |
| driver | agent_ipmitool |
| chassis_uuid | |
| properties | {u'memory_mb': 64000, u'cpu_arch': u'x86_64', u'local_gb': 99, |
| | u'cpus': 2} |
| name | None |
+--------------+-----------------------------------------------------------------------+
Now update the node with boot_mode and
boot_option properties:
ironic node-update NODE_UUID add \ properties/capabilities="boot_mode:bios,boot_option:local"
The ironic node-update command returns details for all of
the node's characteristics.
+------------------------+-----------------------------------------------------------------+
| Property | Value |
+------------------------+-----------------------------------------------------------------+
| target_power_state | None |
| extra | {} |
| last_error | None |
| updated_at | None |
| maintenance_reason | None |
| provision_state | available |
| clean_step | {} |
| uuid | NODE2_UUID |
| console_enabled | False |
| target_provision_state | None |
| provision_updated_at | None |
| maintenance | False |
| inspection_started_at | None |
| inspection_finished_at | None |
| power_state | None |
| driver | agent_ipmitool |
| reservation | None |
| properties | {u'memory_mb': 64000, u'cpu_arch': u'x86_64', |
| | u'local_gb': 99, u'cpus': 2, |
| | u'capabilities': u'boot_mode:bios,boot_option:local'} |
| instance_uuid | None |
| name | None |
| driver_info | {u'ipmi_password': u'******', u'ipmi_address': u'IP_ADDRESS', |
| | u'ipmi_username': u'Administrator', u'deploy_kernel': |
| | u'KERNEL_UUID', |
| | u'deploy_ramdisk': u'RAMDISK_UUID'} |
| created_at | 2016-03-11T14:19:18+00:00 |
| driver_internal_info | {} |
| chassis_uuid | |
| instance_info | {} |
+------------------------+-----------------------------------------------------------------+For more information on node enrollment, see the OpenStack documentation at http://docs.openstack.org/developer/ironic/deploy/install-guide.html#enrollment.
29.3.7 Creating a Flavor #
nova uses flavors when fulfilling requests for bare-metal nodes. The nova
scheduler attempts to match the requested flavor against the properties of
the created ironic nodes. So an administrator needs to set up flavors that
correspond to the available bare-metal nodes using the command
openstack flavor create:
openstack flavor create bmtest auto 64000 99 2 +----------------+--------+--------+------+-----------+------+-------+-------------+-----------+ | ID | Name | Mem_MB | Disk | Ephemeral | Swap | VCPUs | RXTX_Factor | Is_Public | +----------------+--------+--------+------+-----------+------+-------+-------------+-----------+ | 645de0...b1348 | bmtest | 64000 | 99 | 0 | | 2 | 1.0 | True | +----------------+--------+--------+------+-----------+------+-------+-------------+-----------+
To see a list of all the available flavors, run openstack flavor
list:
openstack flavor list +-------------+--------------+--------+------+-----------+------+-------+--------+-----------+ | ID | Name | Mem_MB | Disk | Ephemeral | Swap | VCPUs | RXTX | Is_Public | | | | | | | | | Factor | | +-------------+--------------+--------+------+-----------+------+-------+--------+-----------+ | 1 | m1.tiny | 512 | 1 | 0 | | 1 | 1.0 | True | | 2 | m1.small | 2048 | 20 | 0 | | 1 | 1.0 | True | | 3 | m1.medium | 4096 | 40 | 0 | | 2 | 1.0 | True | | 4 | m1.large | 8192 | 80 | 0 | | 4 | 1.0 | True | | 5 | m1.xlarge | 16384 | 160 | 0 | | 8 | 1.0 | True | | 6 | m1.baremetal | 4096 | 80 | 0 | | 2 | 1.0 | True | | 645d...1348 | bmtest | 64000 | 99 | 0 | | 2 | 1.0 | True | +-------------+--------------+--------+------+-----------+------+-------+--------+-----------+
Now set the CPU architecture and boot mode and boot option capabilities:
openstack flavor set 645de08d-2bc6-43f1-8a5f-2315a75b1348 set cpu_arch=x86_64 openstack flavor set 645de08d-2bc6-43f1-8a5f-2315a75b1348 set capabilities:boot_option="local" openstack flavor set 645de08d-2bc6-43f1-8a5f-2315a75b1348 set capabilities:boot_mode="bios"
For more information on flavor creation, see the OpenStack documentation at http://docs.openstack.org/developer/ironic/deploy/install-guide.html#flavor-creation.
29.3.8 Creating a Network Port #
Register the MAC addresses of all connected physical network interfaces intended for use with the bare-metal node.
ironic port-create -a 5c:b9:01:88:f0:a4 -n ea7246fd-e1d6-4637-9699-0b7c59c22e67
29.3.9 Creating a glance Image #
You can create a complete disk image using the instructions at Section 29.3.13, “Building glance Images Using KIWI”.
The image you create can then be loaded into glance:
openstack image create --name='leap' --disk-format=raw \
--container-format=bare \
--file /tmp/myimage/LimeJeOS-Leap-42.3.x86_64-1.42.3.raw
+------------------+--------------------------------------+
| Property | Value |
+------------------+--------------------------------------+
| checksum | 45a4a06997e64f7120795c68beeb0e3c |
| container_format | bare |
| created_at | 2018-02-17T10:42:14Z |
| disk_format | raw |
| id | 17e4915a-ada0-4b95-bacf-ba67133f39a7 |
| min_disk | 0 |
| min_ram | 0 |
| name | leap |
| owner | 821b7bb8148f439191d108764301af64 |
| protected | False |
| size | 372047872 |
| status | active |
| tags | [] |
| updated_at | 2018-02-17T10:42:23Z |
| virtual_size | None |
| visibility | private |
+------------------+--------------------------------------+This image will subsequently be used to boot the bare-metal node.
29.3.10 Generating a Key Pair #
Create a key pair that you will use when you login to the newly booted node:
openstack keypair create ironic_kp > ironic_kp.pem29.3.11 Determining the neutron Network ID #
openstack network list
+---------------+----------+----------------------------------------------------+
| id | name | subnets |
+---------------+----------+----------------------------------------------------+
| c0102...1ca8c | flat-net | 709ee2a1-4110-4b26-ba4d-deb74553adb9 192.3.15.0/24 |
+---------------+----------+----------------------------------------------------+29.3.12 Booting the Node #
Before booting, it is advisable to power down the node:
ironic node-set-power-state ea7246fd-e1d6-4637-9699-0b7c59c22e67 off
You can now boot the bare-metal node with the information compiled in the preceding steps, using the neutron network ID, the whole disk image ID, the matching flavor and the key name:
openstack server create --nic net-id=c010267c-9424-45be-8c05-99d68531ca8c \ --image 17e4915a-ada0-4b95-bacf-ba67133f39a7 \ --flavor 645de08d-2bc6-43f1-8a5f-2315a75b1348 \ --key-name ironic_kp leap
This command returns information about the state of the node that is booting:
+--------------------------------------+------------------------+
| Property | Value |
+--------------------------------------+------------------------+
| OS-EXT-AZ:availability_zone | |
| OS-EXT-SRV-ATTR:host | - |
| OS-EXT-SRV-ATTR:hypervisor_hostname | - |
| OS-EXT-SRV-ATTR:instance_name | instance-00000001 |
| OS-EXT-STS:power_state | 0 |
| OS-EXT-STS:task_state | scheduling |
| OS-EXT-STS:vm_state | building |
| OS-SRV-USG:launched_at | - |
| OS-SRV-USG:terminated_at | - |
| accessIPv4 | |
| accessIPv6 | |
| adminPass | adpHw3KKTjHk |
| config_drive | |
| created | 2018-03-11T11:00:28Z |
| flavor | bmtest (645de...b1348) |
| hostId | |
| id | a9012...3007e |
| image | leap (17e49...f39a7) |
| key_name | ironic_kp |
| metadata | {} |
| name | leap |
| os-extended-volumes:volumes_attached | [] |
| progress | 0 |
| security_groups | default |
| status | BUILD |
| tenant_id | d53bcaf...baa60dd |
| updated | 2016-03-11T11:00:28Z |
| user_id | e580c64...4aaf990 |
+--------------------------------------+------------------------+
The boot process can take up to 10 minutes. Monitor the progress with the
IPMI console or with openstack server list,
openstack server show
<nova_node_id>, and ironic node-show
<ironic_node_id> commands.
openstack server list +---------------+--------+--------+------------+-------------+----------------------+ | ID | Name | Status | Task State | Power State | Networks | +---------------+--------+--------+------------+-------------+----------------------+ | a9012...3007e | leap | BUILD | spawning | NOSTATE | flat-net=192.3.15.12 | +---------------+--------+--------+------------+-------------+----------------------+
During the boot procedure, a login prompt will appear for SLES:
Ignore this login screen and wait for the login screen of your target operating system to appear:
If you now run the command openstack server list, it should show the
node in the running state:
openstack server list
+---------------+--------+--------+------------+-------------+----------------------+
| ID | Name | Status | Task State | Power State | Networks |
+---------------+--------+--------+------------+-------------+----------------------+
| a9012...3007e | leap | ACTIVE | - | Running | flat-net=192.3.15.14 |
+---------------+--------+--------+------------+-------------+----------------------+You can now log in to the booted node using the key you generated earlier. (You may be prompted to change the permissions of your private key files, so that they are not accessible by others).
ssh leap@192.3.15.14 -i ironic_kp.pem
29.3.13 Building glance Images Using KIWI #
The following sections show you how to create your own images using KIWI, the command line utility to build Linux system appliances. For information on installing KIWI, see https://osinside.github.io/kiwi/installation.html.
KIWI creates images in a two-step process:
The
prepareoperation generates an unpacked image tree using the information provided in the image description.The
createoperation creates the packed image based on the unpacked image and the information provided in the configuration file (config.xml).
Instructions for installing KIWI are available at https://osinside.github.io/kiwi/installation.html.
Image creation with KIWI is automated and does not require any user interaction. The information required for the image creation process is provided by the image description.
To use and run KIWI requires:
A recent Linux distribution such as:
openSUSE Leap 42.3
SUSE Linux Enterprise 12 SP4
openSUSE Tumbleweed
Enough free disk space to build and store the image (a minimum of 10 GB is recommended).
Python version 2.7, 3.4 or higher. KIWI supports both Python 2 and 3 versions
Git (package git-core) to clone a repository.
Virtualization technology to start the image (QEMU is recommended).
29.3.14 Creating an openSUSE Image with KIWI #
The following example shows how to build an openSUSE Leap image that is ready to run in QEMU.
Retrieve the example image descriptions.
git clone https://github.com/SUSE/kiwi-descriptions
Build the image with KIWI:
sudo kiwi-ng --type vmx system build \ --description kiwi-descriptions/suse/x86_64/suse-leap-42.3-JeOS \ --target-dir /tmp/myimage
A
.rawimage will be built in the/tmp/myimagedirectory.Test the live image with QEMU:
qemu \ -drive file=LimeJeOS-Leap-42.3.x86_64-1.42.3.raw,format=raw,if=virtio \ -m 4096
With a successful test, the image is complete.
By default, KIWI generates a file in the .raw format.
The .raw file is a disk image with a structure
equivalent to a physical hard disk. .raw images are
supported by any hypervisor, but are not compressed and do not offer the
best performance.
Virtualization systems support their own formats (such as
qcow2 or vmdk) with compression and
improved I/O performance. To build an image in a format other than
.raw, add the format attribute to the type definition
in the preferences section of config.xml. Using
qcow2 for example:
<image ...>
<preferences>
<type format="qcow2" .../>
...
</preferences>
...
</imageMore information about KIWI is at https://osinside.github.io/kiwi/.
29.4 Provisioning Baremetal Nodes with Multi-Tenancy #
To enable ironic multi-tenancy, you must first manually install the
python-networking-generic-switch package along with all
its dependents on all neutron nodes.
To manually enable the genericswitch mechanism driver in
neutron, the networking-generic-switch package must be
installed first. Do the following steps in each of the controllers where
neutron is running.
Comment out the
multi_tenancy_switch_configsection in~/openstack/my_cloud/definition/data/ironic/ironic_config.yml.SSH into the controller node
Change to root
ardana >sudo -iActivate the neutron venv
tux >sudo . /opt/stack/venv/neutron-20180528T093206Z/bin/activateInstall netmiko package
tux >sudo pip install netmikoClone the
networking-generic-switchsource code into/tmptux >sudo cd /tmptux >sudo git clone https://github.com/openstack/networking-generic-switch.gitInstall
networking_generic_switchpackagetux >sudo python setup.py install
After the networking_generic_switch package is installed,
the genericswitch settings must be enabled in the input
model. The following process must be run again any time a maintenance update
is installed that updates the neutron venv.
SSH into the deployer node as the user
ardana.Edit the ironic configuration data in the input model
~/openstack/my_cloud/definition/data/ironic/ironic_config.yml. Make sure themulti_tenancy_switch_config:section is uncommented and has the appropriate settings.driver_typeshould begenericswitchanddevice_typeshould benetmiko_hp_comware.multi_tenancy_switch_config: - id: switch1 driver_type: genericswitch device_type: netmiko_hp_comware ip_address: 192.168.75.201 username: IRONICSHARE password: 'k27MwbEDGzTm'Run the configure process to generate the model
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun
neutron-reconfigure.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost neutron-reconfigure.ymlRun
neutron-status.ymlto make sure everything is OKardana >ansible-playbook -i hosts/verb_hosts neutron-status.yml
With the networking-generic-switch package installed and
enabled, you can proceed with provisioning baremetal nodes with multi-tenancy.
Create a network and a subnet:
$ openstack network create guest-net-1 Created a new network: +---------------------------+--------------------------------------+ | Field | Value | +---------------------------+--------------------------------------+ | admin_state_up | True | | availability_zone_hints | | | availability_zones | | | created_at | 2017-06-10T02:49:56Z | | description | | | id | 256d55a6-9430-4f49-8a4c-cc5192f5321e | | ipv4_address_scope | | | ipv6_address_scope | | | mtu | 1500 | | name | guest-net-1 | | project_id | 57b792cdcdd74d16a08fc7a396ee05b6 | | provider:network_type | vlan | | provider:physical_network | physnet1 | | provider:segmentation_id | 1152 | | revision_number | 2 | | router:external | False | | shared | False | | status | ACTIVE | | subnets | | | tags | | | tenant_id | 57b792cdcdd74d16a08fc7a396ee05b6 | | updated_at | 2017-06-10T02:49:57Z | +---------------------------+--------------------------------------+ $ openstack subnet create guest-net-1 200.0.0.0/24 Created a new subnet: +-------------------+----------------------------------------------+ | Field | Value | +-------------------+----------------------------------------------+ | allocation_pools | {"start": "200.0.0.2", "end": "200.0.0.254"} | | cidr | 200.0.0.0/24 | | created_at | 2017-06-10T02:53:08Z | | description | | | dns_nameservers | | | enable_dhcp | True | | gateway_ip | 200.0.0.1 | | host_routes | | | id | 53accf35-ae02-43ae-95d8-7b5efed18ae9 | | ip_version | 4 | | ipv6_address_mode | | | ipv6_ra_mode | | | name | | | network_id | 256d55a6-9430-4f49-8a4c-cc5192f5321e | | project_id | 57b792cdcdd74d16a08fc7a396ee05b6 | | revision_number | 2 | | service_types | | | subnetpool_id | | | tenant_id | 57b792cdcdd74d16a08fc7a396ee05b6 | | updated_at | 2017-06-10T02:53:08Z | +-------------------+----------------------------------------------+Review glance image list
$ openstack image list +--------------------------------------+--------------------------+ | ID | Name | +--------------------------------------+--------------------------+ | 0526d2d7-c196-4c62-bfe5-a13bce5c7f39 | cirros-0.4.0-x86_64 | +--------------------------------------+--------------------------+
Create ironic node
$ ironic --ironic-api-version 1.22 node-create -d agent_ipmitool \ -n test-node-1 -i ipmi_address=192.168.9.69 -i ipmi_username=ipmi_user \ -i ipmi_password=XXXXXXXX --network-interface neutron -p memory_mb=4096 \ -p cpu_arch=x86_64 -p local_gb=80 -p cpus=2 \ -p capabilities=boot_mode:bios,boot_option:local \ -p root_device='{"name":"/dev/sda"}' \ -i deploy_kernel=db3d131f-2fb0-4189-bb8d-424ee0886e4c \ -i deploy_ramdisk=304cae15-3fe5-4f1c-8478-c65da5092a2c +-------------------+-------------------------------------------------------------------+ | Property | Value | +-------------------+-------------------------------------------------------------------+ | chassis_uuid | | | driver | agent_ipmitool | | driver_info | {u'deploy_kernel': u'db3d131f-2fb0-4189-bb8d-424ee0886e4c', | | | u'ipmi_address': u'192.168.9.69', | | | u'ipmi_username': u'gozer', u'ipmi_password': u'******', | | | u'deploy_ramdisk': u'304cae15-3fe5-4f1c-8478-c65da5092a2c'} | | extra | {} | | name | test-node-1 | | network_interface | neutron | | properties | {u'cpu_arch': u'x86_64', u'root_device': {u'name': u'/dev/sda'}, | | | u'cpus': 2, u'capabilities': u'boot_mode:bios,boot_option:local', | | | u'memory_mb': 4096, u'local_gb': 80} | | resource_class | None | | uuid | cb4dda0d-f3b0-48b9-ac90-ba77b8c66162 | +-------------------+-------------------------------------------------------------------+ipmi_address, ipmi_username and ipmi_password are IPMI access parameters for baremetal ironic node. Adjust memory_mb, cpus, local_gb to your node size requirements. They also need to be reflected in flavor setting (see below). Use capabilities boot_mode:bios for baremetal nodes operating in Legacy BIOS mode. For UEFI baremetal nodes, use boot_mode:uefi lookup deploy_kernel and deploy_ramdisk in glance image list output above.
ImportantSince we are using ironic API version 1.22, node is created initial state enroll. It needs to be explicitly moved to available state. This behavior changed in API version 1.11
Create port
$ ironic --ironic-api-version 1.22 port-create --address f0:92:1c:05:6c:40 \ --node cb4dda0d-f3b0-48b9-ac90-ba77b8c66162 -l switch_id=e8:f7:24:bf:07:2e -l \ switch_info=hp59srv1-a-11b -l port_id="Ten-GigabitEthernet 1/0/34" \ --pxe-enabled true +-----------------------+--------------------------------------------+ | Property | Value | +-----------------------+--------------------------------------------+ | address | f0:92:1c:05:6c:40 | | extra | {} | | local_link_connection | {u'switch_info': u'hp59srv1-a-11b', | | | u'port_id': u'Ten-GigabitEthernet 1/0/34', | | | u'switch_id': u'e8:f7:24:bf:07:2e'} | | node_uuid | cb4dda0d-f3b0-48b9-ac90-ba77b8c66162 | | pxe_enabled | True | | uuid | a49491f3-5595-413b-b4a7-bb6f9abec212 | +-----------------------+--------------------------------------------+for
--address, use MAC of 1st NIC of ironic baremetal node, which will be used for PXE bootfor
--node, use ironic node uuid (see above)for
-l switch_id, use switch management interface MAC address. It can be retrieved by pinging switch management IP and looking up MAC address in 'arp -l -n' command output.for
-l switch_info, use switch_id fromdata/ironic/ironic_config.ymlfile. If you have several switch config definitions, use the right switch your baremetal node is connected to.for -l port_id, use port ID on the switch
Move ironic node to manage and then available state
$ ironic node-set-provision-state test-node-1 manage $ ironic node-set-provision-state test-node-1 provide
Once node is successfully moved to available state, its resources should be included into nova hypervisor statistics
$ openstack hypervisor stats show +----------------------+-------+ | Property | Value | +----------------------+-------+ | count | 1 | | current_workload | 0 | | disk_available_least | 80 | | free_disk_gb | 80 | | free_ram_mb | 4096 | | local_gb | 80 | | local_gb_used | 0 | | memory_mb | 4096 | | memory_mb_used | 0 | | running_vms | 0 | | vcpus | 2 | | vcpus_used | 0 | +----------------------+-------+
Prepare a keypair, which will be used for logging into the node
$ openstack keypair create ironic_kp > ironic_kp.pem
Obtain user image and upload it to glance. Please refer to OpenStack documentation on user image creation: https://docs.openstack.org/project-install-guide/baremetal/draft/configure-glance-images.html.
NoteDeployed images are already populated by SUSE OpenStack Cloud installer.
$ openstack image create --name='Ubuntu Trusty 14.04' --disk-format=qcow2 \ --container-format=bare --file ~/ubuntu-trusty.qcow2 +------------------+--------------------------------------+ | Property | Value | +------------------+--------------------------------------+ | checksum | d586d8d2107f328665760fee4c81caf0 | | container_format | bare | | created_at | 2017-06-13T22:38:45Z | | disk_format | qcow2 | | id | 9fdd54a3-ccf5-459c-a084-e50071d0aa39 | | min_disk | 0 | | min_ram | 0 | | name | Ubuntu Trusty 14.04 | | owner | 57b792cdcdd74d16a08fc7a396ee05b6 | | protected | False | | size | 371508736 | | status | active | | tags | [] | | updated_at | 2017-06-13T22:38:55Z | | virtual_size | None | | visibility | private | +------------------+--------------------------------------+ $ openstack image list +--------------------------------------+---------------------------+ | ID | Name | +--------------------------------------+---------------------------+ | 0526d2d7-c196-4c62-bfe5-a13bce5c7f39 | cirros-0.4.0-x86_64 | | 83eecf9c-d675-4bf9-a5d5-9cf1fe9ee9c2 | ir-deploy-iso-EXAMPLE | | db3d131f-2fb0-4189-bb8d-424ee0886e4c | ir-deploy-kernel-EXAMPLE | | 304cae15-3fe5-4f1c-8478-c65da5092a2c | ir-deploy-ramdisk- EXAMPLE | | 9fdd54a3-ccf5-459c-a084-e50071d0aa39 | Ubuntu Trusty 14.04 | +--------------------------------------+---------------------------+
Create a baremetal flavor and set flavor keys specifying requested node size, architecture and boot mode. A flavor can be re-used for several nodes having the same size, architecture and boot mode
$ openstack flavor create m1.ironic auto 4096 80 2 +-------------+-----------+--------+------+---------+------+-------+-------------+-----------+ | ID | Name | Mem_MB | Disk | Ephemrl | Swap | VCPUs | RXTX_Factor | Is_Public | +-------------+-----------+--------+------+---------+------+-------+-------------+-----------+ | ab69...87bf | m1.ironic | 4096 | 80 | 0 | | 2 | 1.0 | True | +-------------+-----------+--------+------+---------+------+-------+-------------+-----------+ $ openstack flavor set ab6988...e28694c87bf set cpu_arch=x86_64 $ openstack flavor set ab6988...e28694c87bf set capabilities:boot_option="local" $ openstack flavor set ab6988...e28694c87bf set capabilities:boot_mode="bios"
Parameters must match parameters of ironic node above. Use
capabilities:boot_mode="bios"for Legacy BIOS nodes. For UEFI nodes, usecapabilities:boot_mode="uefi"Boot the node
$ openstack server create --flavor m1.ironic --image 9fdd54a3-ccf5-459c-a084-e50071d0aa39 \ --key-name ironic_kp --nic net-id=256d55a6-9430-4f49-8a4c-cc5192f5321e \ test-node-1 +--------------------------------------+-------------------------------------------------+ | Property | Value | +--------------------------------------+-------------------------------------------------+ | OS-DCF:diskConfig | MANUAL | | OS-EXT-AZ:availability_zone | | | OS-EXT-SRV-ATTR:host | - | | OS-EXT-SRV-ATTR:hypervisor_hostname | - | | OS-EXT-SRV-ATTR:instance_name | | | OS-EXT-STS:power_state | 0 | | OS-EXT-STS:task_state | scheduling | | OS-EXT-STS:vm_state | building | | OS-SRV-USG:launched_at | - | | OS-SRV-USG:terminated_at | - | | accessIPv4 | | | accessIPv6 | | | adminPass | XXXXXXXXXXXX | | config_drive | | | created | 2017-06-14T21:25:18Z | | flavor | m1.ironic (ab69881...5a-497d-93ae-6e28694c87bf) | | hostId | | | id | f1a8c63e-da7b-4d9a-8648-b1baa6929682 | | image | Ubuntu Trusty 14.04 (9fdd54a3-ccf5-4a0...0aa39) | | key_name | ironic_kp | | metadata | {} | | name | test-node-1 | | os-extended-volumes:volumes_attached | [] | | progress | 0 | | security_groups | default | | status | BUILD | | tenant_id | 57b792cdcdd74d16a08fc7a396ee05b6 | | updated | 2017-06-14T21:25:17Z | | user_id | cc76d7469658401fbd4cf772278483d9 | +--------------------------------------+-------------------------------------------------+for
--image, use the ID of user image created at previous stepfor
--nic net-id, use ID of the tenant network created at the beginning
NoteDuring the node provisioning, the following is happening in the background:
neutron connects to switch management interfaces and assigns provisioning VLAN to baremetal node port on the switch. ironic powers up the node using IPMI interface. Node is booting IPA image via PXE. IPA image is writing provided user image onto specified root device (
/dev/sda) and powers node down. neutron connects to switch management interfaces and assigns tenant VLAN to baremetal node port on the switch. A VLAN ID is selected from provided range. ironic powers up the node using IPMI interface. Node is booting user image from disk.Once provisioned, node will join the private tenant network. Access to private network from other networks is defined by switch configuration.
29.5 View Ironic System Details #
29.5.1 View details about the server using openstack server show <nova-node-id> #
openstack server show a90122ce-bba8-496f-92a0-8a7cb143007e
+--------------------------------------+-----------------------------------------------+
| Property | Value |
+--------------------------------------+-----------------------------------------------+
| OS-EXT-AZ:availability_zone | nova |
| OS-EXT-SRV-ATTR:host | ardana-cp1-ir-compute0001-mgmt |
| OS-EXT-SRV-ATTR:hypervisor_hostname | ea7246fd-e1d6-4637-9699-0b7c59c22e67 |
| OS-EXT-SRV-ATTR:instance_name | instance-0000000a |
| OS-EXT-STS:power_state | 1 |
| OS-EXT-STS:task_state | - |
| OS-EXT-STS:vm_state | active |
| OS-SRV-USG:launched_at | 2016-03-11T12:26:25.000000 |
| OS-SRV-USG:terminated_at | - |
| accessIPv4 | |
| accessIPv6 | |
| config_drive | |
| created | 2016-03-11T12:17:54Z |
| flat-net network | 192.3.15.14 |
| flavor | bmtest (645de08d-2bc6-43f1-8a5f-2315a75b1348) |
| hostId | ecafa4f40eb5f72f7298...3bad47cbc01aa0a076114f |
| id | a90122ce-bba8-496f-92a0-8a7cb143007e |
| image | ubuntu (17e4915a-ada0-4b95-bacf-ba67133f39a7) |
| key_name | ironic_kp |
| metadata | {} |
| name | ubuntu |
| os-extended-volumes:volumes_attached | [] |
| progress | 0 |
| security_groups | default |
| status | ACTIVE |
| tenant_id | d53bcaf15afb4cb5aea3adaedbaa60dd |
| updated | 2016-03-11T12:26:26Z |
| user_id | e580c645bfec4faeadef7dbd24aaf990 |
+--------------------------------------+-----------------------------------------------+29.5.2 View detailed information about a node using ironic node-show <ironic-node-id> #
ironic node-show ea7246fd-e1d6-4637-9699-0b7c59c22e67
+------------------------+--------------------------------------------------------------------------+
| Property | Value |
+------------------------+--------------------------------------------------------------------------+
| target_power_state | None |
| extra | {} |
| last_error | None |
| updated_at | 2016-03-11T12:26:25+00:00 |
| maintenance_reason | None |
| provision_state | active |
| clean_step | {} |
| uuid | ea7246fd-e1d6-4637-9699-0b7c59c22e67 |
| console_enabled | False |
| target_provision_state | None |
| provision_updated_at | 2016-03-11T12:26:25+00:00 |
| maintenance | False |
| inspection_started_at | None |
| inspection_finished_at | None |
| power_state | power on |
| driver | agent_ilo |
| reservation | None |
| properties | {u'memory_mb': 64000, u'cpu_arch': u'x86_64', u'local_gb': 99, |
| | u'cpus': 2, u'capabilities': u'boot_mode:bios,boot_option:local'} |
| instance_uuid | a90122ce-bba8-496f-92a0-8a7cb143007e |
| name | None |
| driver_info | {u'ilo_address': u'10.1.196.117', u'ilo_password': u'******', |
| | u'ilo_deploy_iso': u'b9499494-7db3-4448-b67f-233b86489c1f', |
| | u'ilo_username': u'Administrator'} |
| created_at | 2016-03-11T10:17:10+00:00 |
| driver_internal_info | {u'agent_url': u'http://192.3.15.14:9999', |
| | u'is_whole_disk_image': True, u'agent_last_heartbeat': 1457699159} |
| chassis_uuid | |
| instance_info | {u'root_gb': u'99', u'display_name': u'ubuntu', u'image_source': u |
| | '17e4915a-ada0-4b95-bacf-ba67133f39a7', u'capabilities': u'{"boot_mode": |
| | "bios", "boot_option": "local"}', u'memory_mb': u'64000', u'vcpus': |
| | u'2', u'image_url': u'http://192.168.12.2:8080/v1/AUTH_ba121db7732f4ac3a |
| | 50cc4999a10d58d/glance/17e4915a-ada0-4b95-bacf-ba67133f39a7?temp_url_sig |
| | =ada691726337805981ac002c0fbfc905eb9783ea&temp_url_expires=1457699878', |
| | u'image_container_format': u'bare', u'local_gb': u'99', |
| | u'image_disk_format': u'qcow2', u'image_checksum': |
| | u'2d7bb1e78b26f32c50bd9da99102150b', u'swap_mb': u'0'} |
+------------------------+--------------------------------------------------------------------------+29.5.3 View detailed information about a port using ironic port-show <ironic-port-id> #
ironic port-show a17a4ef8-a711-40e2-aa27-2189c43f0b67
+------------+-----------------------------------------------------------+
| Property | Value |
+------------+-----------------------------------------------------------+
| node_uuid | ea7246fd-e1d6-4637-9699-0b7c59c22e67 |
| uuid | a17a4ef8-a711-40e2-aa27-2189c43f0b67 |
| extra | {u'vif_port_id': u'82a5ab28-76a8-4c9d-bfb4-624aeb9721ea'} |
| created_at | 2016-03-11T10:40:53+00:00 |
| updated_at | 2016-03-11T12:17:56+00:00 |
| address | 5c:b9:01:88:f0:a4 |
+------------+-----------------------------------------------------------+29.5.4 View detailed information about a hypervisor using openstack
hypervisor list and openstack hypervisor show #
openstack hypervisor list +-----+--------------------------------------+-------+---------+ | ID | Hypervisor hostname | State | Status | +-----+--------------------------------------+-------+---------+ | 541 | ea7246fd-e1d6-4637-9699-0b7c59c22e67 | up | enabled | +-----+--------------------------------------+-------+---------+
openstack hypervisor show ea7246fd-e1d6-4637-9699-0b7c59c22e67 +-------------------------+--------------------------------------+ | Property | Value | +-------------------------+--------------------------------------+ | cpu_info | | | current_workload | 0 | | disk_available_least | 0 | | free_disk_gb | 0 | | free_ram_mb | 0 | | host_ip | 192.168.12.6 | | hypervisor_hostname | ea7246fd-e1d6-4637-9699-0b7c59c22e67 | | hypervisor_type | ironic | | hypervisor_version | 1 | | id | 541 | | local_gb | 99 | | local_gb_used | 99 | | memory_mb | 64000 | | memory_mb_used | 64000 | | running_vms | 1 | | service_disabled_reason | None | | service_host | ardana-cp1-ir-compute0001-mgmt | | service_id | 25 | | state | up | | status | enabled | | vcpus | 2 | | vcpus_used | 2 | +-------------------------+--------------------------------------+
29.5.5 View a list of all running services using openstack compute
service list #
openstack compute service list +----+------------------+-----------------------+----------+---------+-------+------------+----------+ | Id | Binary | Host | Zone | Status | State | Updated_at | Disabled | | | | | | | | | Reason | +----+------------------+-----------------------+----------+---------+-------+------------+----------+ | 1 | nova-conductor | ardana-cp1-c1-m1-mgmt | internal | enabled | up | date:time | - | | 7 | nova-conductor | " -cp1-c1-m2-mgmt | internal | enabled | up | date:time | - | | 10 | nova-conductor | " -cp1-c1-m3-mgmt | internal | enabled | up | date:time | - | | 13 | nova-scheduler | " -cp1-c1-m1-mgmt | internal | enabled | up | date:time | - | | 16 | nova-scheduler | " -cp1-c1-m3-mgmt | internal | enabled | up | date:time | - | | 19 | nova-scheduler | " -cp1-c1-m2-mgmt | internal | enabled | up | date:time | - | | 25 | nova-compute | " -cp1-ir- | nova | | enabled | up | date:time | - | | | | compute0001-mgmt | | | | | | +----+------------------+-----------------------+----------+---------+-------+------------+----------+
29.6 Troubleshooting ironic Installation #
Sometimes the openstack server create command does not
succeed and when you do a openstack server list, you will see output
like the following:
ardana > openstack server list
+------------------+--------------+--------+------------+-------------+----------+
| ID | Name | Status | Task State | Power State | Networks |
+------------------+--------------+--------+------------+-------------+----------+
| ee08f82...624e5f | OpenSUSE42.3 | ERROR | - | NOSTATE | |
+------------------+--------------+--------+------------+-------------+----------+
You should execute the openstack server show <nova-node-id> and
ironic node-show <ironic-node-id> commands to get
more information about the error.
29.6.1 Error: No valid host was found. #
The error No valid host was found. There are not enough
hosts. is typically seen when performing the openstack
server create where there is a mismatch between the properties set
on the node and the flavor used. For example, the output from a
openstack server show command may look like this:
ardana > openstack server show ee08f82e-8920-4360-be51-a3f995624e5f
+------------------------+------------------------------------------------------------------------------+
| Property | Value |
+------------------------+------------------------------------------------------------------------------+
| OS-EXT-AZ: | |
| availability_zone | |
| OS-EXT-SRV-ATTR:host | - |
| OS-EXT-SRV-ATTR: | |
| hypervisor_hostname | - |
| OS-EXT-SRV-ATTR: | |
| instance_name | instance-00000001 |
| OS-EXT-STS:power_state | 0 |
| OS-EXT-STS:task_state | - |
| OS-EXT-STS:vm_state | error |
| OS-SRV-USG:launched_at | - |
| OS-SRV-USG: | |
| terminated_at | - |
| accessIPv4 | |
| accessIPv6 | |
| config_drive | |
| created | 2016-03-11T11:00:28Z |
| fault | {"message": "No valid host was found. There are not enough hosts |
| | available.", "code": 500, "details": " File \"/opt/stack/ |
| | venv/nova-20160308T002421Z/lib/python2.7/site-packages/nova/ |
| | conductor/manager.py\", line 739, in build_instances |
| | request_spec, filter_properties) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/nova/scheduler/utils.py\", line 343, in wrapped |
| | return func(*args, **kwargs) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/nova/scheduler/client/__init__.py\", line 52, |
| | in select_destinations context, request_spec, filter_properties) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/nova/scheduler/client/__init__.py\",line 37,in __run_method |
| | return getattr(self.instance, __name)(*args, **kwargs) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/nova/scheduler/client/query.py\", line 34, |
| | in select_destinations context, request_spec, filter_properties) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/nova/scheduler/rpcapi.py\", line 120, in select_destinations |
| | request_spec=request_spec, filter_properties=filter_properties) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/oslo_messaging/rpc/client.py\", line 158, in call |
| | retry=self.retry) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/oslo_messaging/transport.py\", line 90, in _send |
| | timeout=timeout, retry=retry) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/oslo_messaging/_drivers/amqpdriver.py\", line 462, in send |
| | retry=retry) |
| | File \"/opt/stack/venv/nova-20160308T002421Z/lib/python2.7/ |
| | site-packages/oslo_messaging/_drivers/amqpdriver.py\", line 453, in _send |
| | raise result |
| | ", "created": "2016-03-11T11:00:29Z"} |
| flavor | bmtest (645de08d-2bc6-43f1-8a5f-2315a75b1348) |
| hostId | |
| id | ee08f82e-8920-4360-be51-a3f995624e5f |
| image | opensuse (17e4915a-ada0-4b95-bacf-ba67133f39a7) |
| key_name | ironic_kp |
| metadata | {} |
| name | opensuse |
| os-extended-volumes: | |
| volumes_attached | [] |
| status | ERROR |
| tenant_id | d53bcaf15afb4cb5aea3adaedbaa60dd |
| updated | 2016-03-11T11:00:28Z |
| user_id | e580c645bfec4faeadef7dbd24aaf990 |
+------------------------+------------------------------------------------------------------------------+
You can find more information about the error by inspecting the log file at
/var/log/nova/nova-scheduler.log or alternatively by
viewing the error location in the source files listed in the stack-trace (in
bold above).
To find the mismatch, compare the properties of the ironic node:
+------------------------+---------------------------------------------------------------------+
| Property | Value |
+------------------------+---------------------------------------------------------------------+
| target_power_state | None |
| extra | {} |
| last_error | None |
| updated_at | None |
| maintenance_reason | None |
| provision_state | available |
| clean_step | {} |
| uuid | ea7246fd-e1d6-4637-9699-0b7c59c22e67 |
| console_enabled | False |
| target_provision_state | None |
| provision_updated_at | None |
| maintenance | False |
| inspection_started_at | None |
| inspection_finished_at | None |
| power_state | None |
| driver | agent_ilo |
| reservation | None |
| properties | {u'memory_mb': 64000, u'local_gb': 99, u'cpus': 2, u'capabilities': |
| | u'boot_mode:bios,boot_option:local'} |
| instance_uuid | None |
| name | None |
| driver_info | {u'ilo_address': u'10.1.196.117', u'ilo_password': u'******', |
| | u'ilo_deploy_iso': u'b9499494-7db3-4448-b67f-233b86489c1f', |
| | u'ilo_username': u'Administrator'} |
| created_at | 2016-03-11T10:17:10+00:00 |
| driver_internal_info | {} |
| chassis_uuid | |
| instance_info | {} |
+------------------------+---------------------------------------------------------------------+with the flavor characteristics:
ardana > openstack flavor show
+----------------------------+-------------------------------------------------------------------+
| Property | Value |
+----------------------------+-------------------------------------------------------------------+
| OS-FLV-DISABLED:disabled | False |
| OS-FLV-EXT-DATA:ephemeral | 0 |
| disk | 99 |
| extra_specs | {"capabilities:boot_option": "local", "cpu_arch": "x86_64", |
| | "capabilities:boot_mode": "bios"} |
| id | 645de08d-2bc6-43f1-8a5f-2315a75b1348 |
| name | bmtest |
| os-flavor-access:is_public | True |
| ram | 64000 |
| rxtx_factor | 1.0 |
| swap | |
| vcpus | 2 |
+----------------------------+-------------------------------------------------------------------+In this instance, the problem is caused by the absence of the "cpu_arch": "x86_64" property on the ironic node. This can be resolved by updating the ironic node, adding the missing property:
ardana > ironic node-update ea7246fd-e1d6-4637-9699-0b7c59c22e67 \
add properties/cpu_arch=x86_64
and then re-running the openstack server create command.
29.6.2 Node fails to deploy because it has timed out #
Possible cause: The neutron API session timed out before port creation was completed.
Resolution: Switch response time varies
by vendor; the value of url_timeout must be increased to
allow for switch response.
Check ironic Conductor logs
(/var/log/ironic/ironic-conductor.log) for
ConnectTimeout errors while connecting to neutron for
port creation. For example:
19-03-20 19:09:14.557 11556 ERROR ironic.conductor.utils [req-77f3a7b...1b10c5b - default default] Unexpected error while preparing to deploy to node 557316...84dbdfbe8b0: ConnectTimeout: Request to https://192.168.75.1:9696/v2.0/ports timed out
Use the following steps to increase the value of
url_timeout.
Log in to the deployer node.
Edit
./roles/ironic-common/defaults/main.yml, increasing the value ofurl_timeout.ardana >cd /var/lib/ardana/scratch/ansible/next/ardana/ansibleardana >vi ./roles/ironic-common/defaults/main.ymlIncrease the value of the
url_timeoutparameter in theironic_neutron:section. Increase the parameter from the default (60 seconds) to 120 and then in increments of 60 seconds until the node deploys successfully.Reconfigure ironic.
ardana >ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
29.6.3 Deployment to a node fails and in "ironic node-list" command, the power_state column for the node is shown as "None" #
Possible cause: The IPMI commands to the node take longer to change the power state of the server.
Resolution: Check if the node power state can be changed using the following command
ardana > ironic node-set-power-state $NODEUUID onIf the above command succeeds and the power_state column is updated correctly, then the following steps are required to increase the power sync interval time.
On the first controller, reconfigure ironic to increase the power sync interval time. In the example below, it is set to 120 seconds. This value may have to be tuned based on the setup.
Go to the
~/openstack/my_cloud/config/ironic/directory and editironic-conductor.conf.j2to set thesync_power_state_intervalvalue:[conductor] sync_power_state_interval = 120
Save the file and then run the following playbooks:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
29.6.4 Error Downloading Image #
If you encounter the error below during the deployment:
"u'message': u'Error downloading image: Download of image id 77700...96551 failed: Image download failed for all URLs.', u'code': 500, u'type': u'ImageDownloadError', u'details': u'Download of image id 77700b53-9e15-406c-b2d5-13e7d9b96551 failed: Image download failed for all URLs.'"
you should visit the Single Sign-On Settings in the Security page of IPMI and change the Single Sign-On Trust Mode setting from the default of "Trust None (SSO disabled)" to "Trust by Certificate".
29.6.5 Using node-inspection can cause temporary claim of IP addresses #
Possible cause: Running
node-inspection on a node discovers all the NIC ports
including the NICs that do not have any connectivity. This causes a
temporary consumption of the network IPs and increased usage of the
allocated quota. As a result, other nodes are deprived of IP addresses and
deployments can fail.
Resolution:You can add node properties manually added instead of using the inspection tool.
Note: Upgrade ipmitool to a version >= 1.8.15 or it
may not return detailed information about the NIC interface for
node-inspection.
29.6.6 Node permanently stuck in deploying state #
Possible causes:
ironic conductor service associated with the node could go down.
There might be a properties mismatch. MAC address registered for the node could be incorrect.
Resolution: To recover from this
condition, set the provision state of the node to Error
and maintenance to True. Delete the node and re-register
again.
29.6.7 The NICs in the baremetal node should come first in boot order #
Possible causes: By default, the boot order of baremetal node is set as NIC1, HDD and NIC2. If NIC1 fails, the nodes starts booting from HDD and the provisioning fails.
Resolution: Set boot order so that all the NICs appear before the hard disk of the baremetal as NIC1, NIC2…, HDD.
29.6.8 Increase in the number of nodes can cause power commands to fail #
Possible causes:ironic periodically performs a power state sync with all the baremetal nodes. When the number of nodes increase, ironic does not get sufficient time to perform power operations.
Resolution: The following procedure gives a
way to increase sync_power_state_interval:
Edit the file
~/openstack/my_cloud/config/ironic/ironic-conductor.conf.j2and navigate to the section for[conductor]Increase the
sync_power_state_interval. For example, for 100 nodes, setsync_power_state_interval = 90and save the file.Execute the following set of commands to reconfigure ironic:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
29.6.9 DHCP succeeds with PXE but times out with iPXE #
If you see DHCP error "No configuration methods succeeded" in iPXE right after successful DHCP performed by embedded NIC firmware, there may be an issue with Spanning Tree Protocol on the switch.
To avoid this error, Rapid Spanning Tree Protocol needs to be enabled on the switch. If this is not an option due to conservative loop detection strategies, use the steps outlined below to install the iPXE binary with increased DHCP timeouts.
Clone iPXE source code
tux >git clone git://git.ipxe.org/ipxe.gittux >cd ipxe/srcModify lines 22-25 in file
config/dhcp.h, which declare reduced DHCP timeouts (1-10 secs). Comment out lines with reduced timeouts and uncomment normal PXE timeouts (4-32)//#define DHCP_DISC_START_TIMEOUT_SEC 1 //#define DHCP_DISC_END_TIMEOUT_SEC 10 #define DHCP_DISC_START_TIMEOUT_SEC 4 /* as per PXE spec */ #define DHCP_DISC_END_TIMEOUT_SEC 32 /* as per PXE spec */
Make
undionly.kpxe(BIOS) andipxe.efi(UEFI) imagestux >make bin/undionly.kpxetux >make bin-x86_64-efi/ipxe.efiCopy iPXE images to Cloud Lifecycle Manager
tux >scp bin/undionly.kpxe bin-x86_64-efi/ipxe.efi stack@10.0.0.4: stack@10.0.0.4's password: undionly.kpxe 100% 66KB 65.6KB/s 00:00 ipxe.efi 100% 918KB 918.2KB/s 00:00From deployer, distribute image files onto all 3 controllers
stack@ardana-cp1-c1-m1-mgmt:
ardana >cd ~/scratch/ansible/next/ardana/ansible/ stack@ardana-cp1-c1-m1-mgmt:ardana >~/scratch/ansible/next/ardana/ansible$ ansible -i hosts/verb_hosts \ IRN-CND -m copy -b -a 'src=~/ipxe.efi dest=/tftpboot' ... stack@ardana-cp1-c1-m1-mgmt:ardana >~/scratch/ansible/next/ardana/ansible$ ansible -i hosts/verb_hosts \ IRN-CND -m copy -b -a 'src=~/undionly.kpxe dest=/tftpboot' ...
There is no need to restart services. With next PXE boot attempt, iPXE binary with the increased timeout will be downloaded to the target node via TFTP.
29.6.9.1 ironic Support and Limitations #
The following drivers are supported and tested:
pxe_ipmitool(UEFI and Legacy BIOS mode, flat-network)pxe_ipmitool(UEFI and Legacy BIOS mode, flat-network)pxe_ilo(UEFI and Legacy BIOS mode, flat-network)agent_ipmitool(UEFI and Legacy BIOS mode, flat-network)agent_ilo(UEFI and Legacy BIOS mode, flat-network)
ISO Image Exceeds Free Space
When using the agent_ilo driver, provisioning will
fail if the size of the user ISO image exceeds the free space available on
the ramdisk partition. This will produce an error in the ironic Conductor
logs that may look like as follows:
"ERROR root [-] Command failed: prepare_image, error: Error downloading image: Download of image id 0c4d74e4-58f1-4f8d-8c1d-8a49129a2163 failed: Unable to write image to /tmp/0c4d74e4-58f1-4f8d-8c1d-8a49129a2163. Error: [Errno 28] No space left on device: ImageDownloadError: Error downloading image: Download of image id 0c4d74e4-58f1-4f8d-8c1d-8a49129a2163 failed: Unable to write image to /tmp/0c4d74e4-58f1-4f8d-8c1d-8a49129a2163. Error: [Errno 28] No space left on device"
By default, the total amount of space allocated to ramdisk is 4GB. To increase the space allocated for the ramdisk, you can update the deploy ISO image using the following workaround.
Save the deploy ISO to a file:
tux >openstack image save --file deploy.isoIMAGE_IDReplace IMAGE_ID with the ID of the deploy ISO stored in glance. The ID can be obtained using the
openstack image list.Mount the saved ISO:
tux >mkdir /tmp/mnttux >sudo mount -t iso9660 -o loop deploy.iso /tmp/mntSince the mount directory is read-only, it is necessary to copy its content to be able to make modifications.
Copy the content of the mount directory to a custom directory:
tux >mkdir /tmp/customtux >cp -aRvf /tmp/mnt/* /tmp/custom/Modify the bootloader files to increase the size of the ramdisk:
/tmp/custom/boot/x86_64/loader/isolinux.cfg /tmp/custom/EFI/BOOT/grub.cfg /tmp/custom/boot/grub2/grub.cfg
Find the
openstack-ironic-imagelabel and modify theramdisk_sizeparameter in theappendproperty. Theramdisk_sizevalue must be specified in Kilobytes.label openstack-ironic-image kernel linux append initrd=initrd ramdisk_size=10485760 ramdisk_blocksize=4096 \ boot_method=vmedia showopts
Make sure that your baremetal node has the amount of RAM that equals or exceeds the
ramdisk_sizevalue.Repackage the ISO using the genisoimage tool:
tux >cd /tmp/customtux >genisoimage -b boot/x86_64/loader/isolinux.bin -R -J -pad -joliet-long \ -iso-level 4 -A '0xaa2dab53' -no-emul-boot -boot-info-table \ -boot-load-size 4 -c boot/x86_64/boot.catalog -hide boot/x86_64/boot.catalog \ -hide-joliet boot/x86_64/boot.catalog -eltorito-alt-boot -b boot/x86_64/efi \ -no-emul-boot -joliet-long -hide glump -hide-joliet glump -o /tmp/custom_deploy.iso ./ImportantWhen repackaging the ISO, make sure that you use the same label. You can find the label file in the
/tmp/custom/boot/directory. The label begins with0x. For example,0x51e568cb.Delete the existing deploy ISO in glance:
tux >openstack image delete IMAGE_IDCreate a new image with
custom_deploy.iso:tux >openstack image create --container-format bare \ --disk-format iso --public --file custom_deploy.iso ir-deploy-iso-ARDANA5.0Re-deploy the ironic node.
Partition Image Exceeds Free Space
The previous procedure applies to ISO images. It does not apply to
partition images, although there will be a similar error
in the ironic logs. However the resolution is different. An option must be
added to the PXE line in the
main.yml file to increase the /tmp
disk size with the following workaround:
Edit
/openstack/ardana/ansible/roles/ironic-common/defaults/main.yml.Add
suse.tmpsize=4Gtopxe_append_params. Adjust the size ofsuse.tmpsizeas needed for the partition image.pxe_append_params : "nofb nomodeset vga=normal elevator=deadline security=apparmor crashkernel=256M console=tty0 console=ttyS0 suse.tmpsize=4G"Update Git and run playbooks:
ardana >git add -Aardana >git commit -m "Add suse.tmpsize variable"ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd /var/lib/ardana/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ironic-reconfigure.ymlRe-deploy the ironic node.
29.7 Node Cleaning #
Cleaning is the process by which data is removed after a previous tenant has used the node. Cleaning requires use of ironic's agent_ drivers. It is extremely important to note that if the pxe_ drivers are utilized, no node cleaning operations will occur, and a previous tenant's data could be found on the node. The same risk of a previous tenant's data possibly can occur if cleaning is explicitly disabled as part of the installation.
By default, cleaning attempts to utilize ATA secure erase to wipe the contents of the disk. If secure erase is unavailable, the cleaning functionality built into the ironic Python Agent falls back to an operation referred to as "shred" where random data is written over the contents of the disk, and then followed up by writing "0"s across the disk. This can be a time-consuming process.
An additional feature of cleaning is the ability to update firmware or potentially assert new hardware configuration, however, this is an advanced feature that must be built into the ironic Python Agent image. Due to the complex nature of such operations, and the fact that no one size fits all, this requires a custom ironic Python Agent image to be constructed with an appropriate hardware manager. For more information on hardware managers, see http://docs.openstack.org/developer/ironic-python-agent/#hardware-managers
ironic's upstream documentation for cleaning may be found here: http://docs.openstack.org/developer/ironic/deploy/cleaning.html
29.7.1 Setup #
Cleaning is enabled by default in ironic when installed via the Cloud Lifecycle Manager. You can verify this by examining the ironic-conductor.conf file. Look for:
[conductor] clean_nodes=true
29.7.2 In use #
When enabled, cleaning will be run automatically when nodes go from active
to available state or from manageable to available. To monitor what step of
cleaning the node is in, run ironic node-show:
stack@ardana-cp1-c1-m1-mgmt:~$ ironic node-show 4e6d4273-2535-4830-a826-7f67e71783ed
+------------------------+-----------------------------------------------------------------------+
| Property | Value |
+------------------------+-----------------------------------------------------------------------+
| target_power_state | None |
| extra | {} |
| last_error | None |
| updated_at | 2016-04-15T09:33:16+00:00 |
| maintenance_reason | None |
| provision_state | cleaning |
| clean_step | {} |
| uuid | 4e6d4273-2535-4830-a826-7f67e71783ed |
| console_enabled | False |
| target_provision_state | available |
| provision_updated_at | 2016-04-15T09:33:16+00:00 |
| maintenance | False |
| inspection_started_at | None |
| inspection_finished_at | None |
| power_state | power off |
| driver | agent_ilo |
| reservation | ardana-cp1-c1-m1-mgmt |
| properties | {u'memory_mb': 4096, u'cpu_arch': u'amd64', u'local_gb': 80, |
| | u'cpus': 2, u'capabilities': u'boot_mode:uefi,boot_option:local'} |
| instance_uuid | None |
| name | None |
| driver_info | {u'ilo_deploy_iso': u'249bf095-e741-441d-bc28-0f44a9b8cd80', |
| | u'ipmi_username': u'Administrator', u'deploy_kernel': |
| | u'3a78c0a9-3d8d-4764-9300-3e9c00e167a1', u'ilo_address': |
| | u'10.1.196.113', u'ipmi_address': u'10.1.196.113', u'deploy_ramdisk': |
| | u'd02c811c-e521-4926-9f26-0c88bbd2ee6d', u'ipmi_password': u'******', |
| | u'ilo_password': u'******', u'ilo_username': u'Administrator'} |
| created_at | 2016-04-14T08:30:08+00:00 |
| driver_internal_info | {u'clean_steps': None, |
| | u'hardware_manager_version': {u'generic_hardware_manager': u'1.0'}, |
| | u'is_whole_disk_image': True, u'agent_erase_devices_iterations': 1, |
| | u'agent_url': u'http://192.168.246.245:9999', |
| | u'agent_last_heartbeat': 1460633166} |
| chassis_uuid | |
| instance_info | {} |
+------------------------+-----------------------------------------------------------------------+
The status will be in the driver_internal_info field. You
will also be able to see the clean_steps list there.
29.7.3 Troubleshooting #
If an error occurs during the cleaning process, the node will enter the clean failed state so that it is not deployed. The node remains powered on for debugging purposes. The node can be moved to the manageable state to attempt a fix using the following command:
ironic node-set-provision-state <node id> manage
Once you have identified and fixed the issue, you can return the node to available state by executing the following commands:
ironic node-set-maintenance <node id> false ironic node-set-provision-state <node id> provide
This will retry the cleaning steps and set the node to available state upon their successful completion.
29.7.4 Disabling Node Cleaning #
To disable node cleaning, edit
~/openstack/my_cloud/definition/data/ironic/ironic_config.yml
and set enable_node_cleaning to false.
Commit your changes:
cd ~/openstack/ardana/ansible git add -A git commit -m "disable node cleaning"
Deploy these changes by re-running the configuration processor and reconfigure the ironic installation:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml ansible-playbook -i hosts/localhost ready-deployment.yml cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
29.8 Ironic and HPE OneView #
29.8.1 Enabling Ironic HPE OneView driver in SUSE OpenStack Cloud #
Edit the file
~/openstack/my_cloud/definition/data/ironic/ironicconfig.yml
and set the value
enable_oneview: true
This will enable the HPE OneView driver for ironic in SUSE OpenStack Cloud.
29.8.2 Adding HPE OneView Appliance Credentials #
manage_url: https://<Onview appliance URL> oneview_username: "<Appliance username>" oneview_encrypted_password: "<Encrypted password>" oneview_allow_insecure_connections: <true/false> tls_cacert_file: <CA certificate for connection>
29.8.3 Encrypting the HPE OneView Password #
Encryption can be applied using ardanaencrypt.py or using
openssl. On the Cloud Lifecycle Manager node, export the key
used for encryption as environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY="ENCRYPTION_KEY"
And then execute the following commands:
cd ~/openstack/ardana/ansible python ardanaencrypt.py
Enter password to be encrypted when prompted. The script uses the key that
was exported in the ARDANA_USER_PASSWORD_ENCRYPT_KEY to do
the encryption.
For more information, see Book “Security Guide”, Chapter 10 “Encryption of Passwords and Sensitive Data”.
29.8.4 Decrypting the HPE OneView Password #
Before running the site.yml playbook, export the key used
for encryption as environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY="ENCRYPTION_KEY"
The decryption of the password is then automatically handled in ironic-ansible playbooks.
29.8.5 Registering Baremetal Node for HPE OneView Driver #
ironic node-create -d agent_pxe_oneview
Update node driver-info:
ironic node-update $NODE_UUID add driver_info/server_hardware_uri=$SH_URI
29.8.6 Updating Node Properties #
ironic node-update $NODE_UUID add \
properties/capabilities=server_hardware_type_uri:$SHT_URI,\
enclosure_group_uri:$EG_URI,server_profile_template_uri=$SPT_URI29.8.7 Creating Port for Driver #
ironic port-create -n $NODE_UUID -a $MAC_ADDRESS
29.8.8 Creating a Node #
Create Node:
ironic node-create -n ovbay7 -d agent_pxe_oneview
Update driver info:
ironic node-update $ID add driver_info/server_hardware_uri="/rest/server-hardware/3037...464B" \ driver_info/deploy_kernel="$KERNELDISK" driver_info/deploy_ramdisk="$RAMDISK"
Update node properties:
ironic node-update $ID add properties/local_gb=10 ironic node-update $ID add properties/cpus=24 properties/memory_mb=262144 \ properties/cpu_arch=x86_64
ironic node-update \ $ID add properties/capabilities=server_hardware_type_uri:'/rest/server-hardware-types/B31...F69E',\ enclosure_group_uri:'/rest/enclosure-groups/80efe...b79fa',\ server_profile_template_uri:'/rest/server-profile-templates/faafc3c0-6c81-47ca-a407-f67d11262da5'
29.8.9 Getting Data using REST API #
GET login session auth id:
curl -k https://ONEVIEW_MANAGER_URL/rest/login-sessions \
-H "content-type:application/json" \
-X POST \
-d '{"userName":"USER_NAME", "password":"PASSWORD"}'Get the complete node details in JSON format:
curl -k "https://ONEVIEW_MANAGER_URL;/rest/server-hardware/30373237-3132-4753-4835-32325652464B" -H "content-type:application/json" -H "Auth:<auth_session_id>"| python -m json.tool
29.8.10 Ironic HPE OneView CLI #
ironic-oneview-cli is already installed in
ironicclient venv with a symbolic link to it. To generate
an rc file for the HPE OneView CLI, follow these steps:
Run the following commands:
source ~/service.osrc openstack image list
Note the
deploy-kernelanddeploy-ramdiskUUID and then run the following command to generate thercfile:ironic-oneview genrc
You will be prompted to enter:
HPE OneView Manager URL
Username
deploy-kernel
deploy-ramdisk
allow_insecure_connection
cacert file
The
ironic-oneview.rcfile will be generated in the current directory, by default. It is possible to specify a different location.Source the generated file:
source ironic-oneview.rc
Now enter the password of the HPE OneView appliance.
You can now use the CLI for node and flavor creation as follows:
ironic-oneview node-create ironic-oneview flavor-create
29.9 RAID Configuration for Ironic #
Node Creation:
Check the raid capabilities of the driver:
ironic --ironic-api-version 1.15 driver-raid-logical-disk-properties pxe_ilo
This will generate output similar to the following:
+----------------------+-------------------------------------------------------------------------+ | Property | Description | +----------------------+-------------------------------------------------------------------------+ | controller | Controller to use for this logical disk. If not specified, the | | | driver will choose a suitable RAID controller on the bare metal node. | | | Optional. | | disk_type | The type of disk preferred. Valid values are 'hdd' and 'ssd'. If this | | | is not specified, disk type will not be a selection criterion for | | | choosing backing physical disks. Optional. | | interface_type | The interface type of disk. Valid values are 'sata', 'scsi' and 'sas'. | | | If this is not specified, interface type will not be a selection | | | criterion for choosing backing physical disks. Optional. | | is_root_volume | Specifies whether this disk is a root volume. By default, this is False.| | | Optional. | | #_of_physical_disks | Number of physical disks to use for this logical disk. By default, the | | | driver uses the minimum number of disks required for that RAID level. | | | Optional. | | physical_disks | The physical disks to use for this logical disk. If not specified, the | | | driver will choose suitable physical disks to use. Optional. | | raid_level | RAID level for the logical disk. Valid values are '0', '1', '2', '5', | | | '6', '1+0', '5+0' and '6+0'. Required. | | share_physical_disks | Specifies whether other logical disks can share physical disks with this| | | logical disk. By default, this is False. Optional. | | size_gb | Size in GiB (Integer) for the logical disk. Use 'MAX' as size_gb if | | | this logical disk is supposed to use the rest of | | | the space available. Required. | | volume_name | Name of the volume to be created. If this is not specified, it will be | | | auto-generated. Optional. | +----------------------+-------------------------------------------------------------------------+
Node State will be Available
ironic node-create -d pxe_ilo -i ilo_address=<ip_address> \ -i ilo_username=<username> -i ilo_password=<password> \ -i ilo_deploy_iso=<iso_id> -i deploy_kernel=<kernel_id> \ -i deploy_ramdisk=<ramdisk_id> -p cpus=2 -p memory_mb=4096 \ -p local_gb=80 -p cpu_arch=amd64 \ -p capabilities="boot_option:local,boot_mode:bios"
ironic port-create -a <port> -n <node-uuid>
Apply the target raid configuration on the node:
See the OpenStack documentation for RAID configuration at http://docs.openstack.org/developer/ironic/deploy/raid.html.
Set the target RAID configuration by editing the file
raid_conf.jsonand setting the appropriate values, for example:{ "logical_disks": [ {"size_gb": 5, "raid_level": "0", "is_root_volume": true} ] }and then run the following command:
ironic --ironic-api-version 1.15 node-set-target-raid-config <node-uuid> raid_conf.json
The output produced should be similar to the following:
+-----------------------+-------------------------------------------------------------------------+ | Property | Value | +-----------------------+-------------------------------------------------------------------------+ | chassis_uuid | | | clean_step | {} | | console_enabled | False | | created_at | 2016-06-14T14:58:07+00:00 | | driver | pxe_ilo | | driver_info | {u'ilo_deploy_iso': u'd43e589a-07db-4fce-a06e-98e2f38340b4', | | | u'deploy_kernel': u'915c5c74-1ceb-4f78-bdb4-8547a90ac9c0', | | | u'ilo_address': u'10.1.196.116', u'deploy_ramdisk': | | | u'154e7024-bf18-4ad2-95b0-726c09ce417a', u'ilo_password': u'******', | | | u'ilo_username': u'Administrator'} | | driver_internal_info | {u'agent_cached_clean_steps_refreshed': u'2016-06-15 07:16:08.264091', | | | u'agent_cached_clean_steps': {u'raid': [{u'interface': u'raid', | | | u'priority': 0, u'step': u'delete_configuration'}, {u'interface': | | | u'raid', u'priority': 0, u'step': u'create_configuration'}], u'deploy': | | | [{u'priority': 10, u'interface': u'deploy', u'reboot_requested': False, | | | u'abortable': True, u'step': u'erase_devices'}]}, u'clean_steps': None, | | | u'hardware_manager_version': {u'generic_hardware_manager': u'3'}, | | | u'agent_erase_devices_iterations': 1, u'agent_url': | | | u'http://192.168.245.143:9999', u'agent_last_heartbeat': 1465974974} | | extra | {} | | inspection_finished_at| None | | inspection_started_at | None | | instance_info | {u'deploy_key': u'XXN2ON0V9ER429MECETJMUG5YHTKOQOZ'} | | instance_uuid | None | | last_error | None | | maintenance | False | | maintenance_reason | None | | name | None | | power_state | power off | | properties | {u'cpu_arch': u'amd64', u'root_device': {u'wwn': u'0x600508b1001ce286'},| | | u'cpus': 2, u'capabilities': | | | u'boot_mode:bios,raid_level:6,boot_option:local', u'memory_mb': 4096, | | | u'local_gb': 4} | | provision_state | available | | provision_updated_at | 2016-06-15T07:16:27+00:00 | | reservation | padawan-ironic-cp1-c1-m2-mgmt | | target_power_state | power off | | target_provision_state| None | | target_raid_config | {u'logical_disks': [{u'size_gb': 5, u'raid_level': u'6', | | | u'is_root_volume': True}]} | | updated_at | 2016-06-15T07:44:22+00:00 | | uuid | 22ab9f85-71a1-4748-8d6b-f6411558127e | +-----------------------+-------------------------------------------------------------------------+Now set the state of the node to manageable:
ironic --ironic-api-version latest node-set-provision-state <node-uuid> manage
Manual cleaning steps:
Manual cleaning is enabled by default in production - the following are the steps to enable cleaning if the manual cleaning has been disabled.
Provide
cleaning_network_uuidinironic-conductor.confEdit the file
~/openstack/my_cloud/definition/data/ironic/ironic_config.ymland setenable_node_cleaningtotrue.Then run the following set of commands:
cd ~/openstack/ardana/ansible git add -A git commit -m "enabling node cleaning" cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml ansible-playbook -i hosts/localhost ready-deployment.yml cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml
After performing these steps, the state of the node will become Cleaning.
Run the following command:
ironic --ironic-api-version latest node-set-provision-state 2123254e-8b31...aa6fd \ clean --clean-steps '[{ "interface": "raid","step": "delete_configuration"}, \ { "interface": "raid" ,"step": "create_configuration"}]'Node-information after a Manual cleaning:
+-----------------------+-------------------------------------------------------------------------+ | Property | Value | +-----------------------+-------------------------------------------------------------------------+ | chassis_uuid | | | clean_step | {} | | console_enabled | False | | created_at | 2016-06-14T14:58:07+00:00 | | driver | pxe_ilo | | driver_info | {u'ilo_deploy_iso': u'd43e589a-07db-4fce-a06e-98e2f38340b4', | | | u'deploy_kernel': u'915c5c74-1ceb-4f78-bdb4-8547a90ac9c0', | | | u'ilo_address': u'10.1.196.116', u'deploy_ramdisk': | | | u'154e7024-bf18-4ad2-95b0-726c09ce417a', u'ilo_password': u'******', | | | u'ilo_username': u'Administrator'} | | driver_internal_info | {u'agent_cached_clean_steps_refreshed': u'2016-06-15 07:16:08.264091', | | | u'agent_cached_clean_steps': {u'raid': [{u'interface': u'raid', | | | u'priority': 0, u'step': u'delete_configuration'}, {u'interface': | | | u'raid', u'priority': 0, u'step': u'create_configuration'}], u'deploy': | | | [{u'priority': 10, u'interface': u'deploy', u'reboot_requested': False, | | | u'abortable': True, u'step': u'erase_devices'}]}, u'clean_steps': None, | | | u'hardware_manager_version': {u'generic_hardware_manager': u'3'}, | | | u'agent_erase_devices_iterations': 1, u'agent_url': | | | u'http://192.168.245.143:9999', u'agent_last_heartbeat': 1465974974} | | extra | {} | | inspection_finished_at| None | | inspection_started_at | None | | instance_info | {u'deploy_key': u'XXN2ON0V9ER429MECETJMUG5YHTKOQOZ'} | | instance_uuid | None | | last_error | None | | maintenance | False | | maintenance_reason | None | | name | None | | power_state | power off | | properties | {u'cpu_arch': u'amd64', u'root_device': {u'wwn': u'0x600508b1001ce286'},| | | u'cpus': 2, u'capabilities': | | | u'boot_mode:bios,raid_level:6,boot_option:local', u'memory_mb': 4096, | | | u'local_gb': 4} | | provision_state | manageable | | provision_updated_at | 2016-06-15T07:16:27+00:00 | | raid_config | {u'last_updated': u'2016-06-15 07:16:14.584014', u'physical_disks': | | | [{u'status': u'ready', u'size_gb': 1024, u'interface_type': u'sata', | | | u'firmware': u'HPGC', u'controller': u'Smart Array P440ar in Slot 0 | | | (Embedded)', u'model': u'ATA MM1000GBKAL', u'disk_type': u'hdd', | | | u'id': u'1I:3:3'}, {u'status': u'ready', u'size_gb': 1024, | | | u'interface_type': u'sata', u'firmware': u'HPGC', u'controller': u'Smart| | | Array P440ar in Slot 0 (Embedded)', u'model': u'ATA MM1000GBKAL', | | | u'disk_type': u'hdd', u'id': u'1I:3:1'}, {u'status': u'active', | | | u'size_gb': 1024, u'interface_type': u'sata', u'firmware': u'HPGC', | | | u'controller': u'Smart Array P440ar in Slot 0 (Embedded)', u'model': | | | u'ATA MM1000GBKAL', u'disk_type': u'hdd', u'id': u'1I:3:2'}, | | | {u'status': u'active', u'size_gb': 1024, u'interface_type': u'sata', | | | u'firmware': u'HPGC', u'controller': u'Smart Array P440ar in Slot 0 | | | (Embedded)', u'model': u'ATA MM1000GBKAL', u'disk_type': u'hdd', | | | u'id': u'2I:3:6'}, {u'status': u'active', u'size_gb': 1024, | | | u'interface_type': u'sata', u'firmware': u'HPGC', u'controller': u'Smart| | | Array P440ar in Slot 0 (Embedded)', u'model': u'ATA MM1000GBKAL', | | | u'disk_type': u'hdd', u'id': u'2I:3:5'}, {u'status': u'active', | | | u'size_gb': 1024, u'interface_type': u'sata', u'firmware': u'HPGC', | | | u'controller': u'Smart Array P440ar in Slot 0 (Embedded)', u'model': | | | u'ATA MM1000GBKAL', u'disk_type': u'hdd', u'id': u'1I:3:4'}], | | | u'logical_disks': [{u'size_gb': 4, u'physical_disks': [u'1I:3:2', | | | u'2I:3:6', u'2I:3:5', u'1I:3:4'], u'raid_level': u'6', | | | u'is_root_volume': True, u'root_device_hint': {u'wwn': | | | u'0x600508b1001ce286'}, u'controller': u'Smart Array P440ar in Slot 0 | | | (Embedded)', u'volume_name': u'015E795CPDNLH0BRH8N406AAB7'}]} | | reservation | padawan-ironic-cp1-c1-m2-mgmt | | target_power_state | power off | | target_provision_state| None | | target_raid_config | {u'logical_disks': [{u'size_gb': 5, u'raid_level': u'6', | | | u'is_root_volume': True}]} | | updated_at | 2016-06-15T07:44:22+00:00 | | uuid | 22ab9f85-71a1-4748-8d6b-f6411558127e | +-----------------------+-------------------------------------------------------------------------+After the manual cleaning, run the following command to change the state of a node to available:
ironic --ironic-api-version latest node-set-provision-state <node-uuid> \ provide
29.10 Audit Support for Ironic #
29.10.1 API Audit Logging #
Audit middleware supports delivery of CADF audit events via Oslo messaging
notifier capability. Based on notification_driver
configuration, audit events can be routed to messaging infrastructure
(notification_driver = messagingv2) or can be routed to a
log file (notification_driver = log).
Audit middleware creates two events per REST API interaction. The first event has information extracted from request data and the second one contains information on the request outcome (response).
29.10.2 Enabling API Audit Logging #
You can enable audit logging for ironic by changing the configuration in the
input model. Edit the file
~/openstack/my_cloud/definition/cloudConfig.yml and in the
audit-settings section, change the
default value to enabled. The
ironic-ansible playbooks will now enable audit support for ironic.
API audit events will be logged in the corresponding audit directory, for
example, /var/audit/ironic/ironic-api-audit.log. An audit
event will be logged in the log file for every request and response for an
API call.
29.10.3 Sample Audit Event #
The following output is an example of an audit event for an ironic
node-list command:
{
"event_type":"audit.http.request",
"timestamp":"2016-06-15 06:04:30.904397",
"payload":{
"typeURI":"http://schemas.dmtf.org/cloud/audit/1.0/event",
"eventTime":"2016-06-15T06:04:30.903071+0000",
"target":{
"id":"ironic",
"typeURI":"unknown",
"addresses":[
{
"url":"http://{ironic_admin_host}:6385",
"name":"admin"
},
{
"url":"http://{ironic_internal_host}:6385",
"name":"private"
},
{
"url":"http://{ironic_public_host}:6385",
"name":"public"
}
],
"name":"ironic"
},
"observer":{
"id":"target"
},
"tags":[
"correlation_id?value=685f1abb-620e-5d5d-b74a-b4135fb32373"
],
"eventType":"activity",
"initiator":{
"typeURI":"service/security/account/user",
"name":"admin",
"credential":{
"token":"***",
"identity_status":"Confirmed"
},
"host":{
"agent":"python-ironicclient",
"address":"10.1.200.129"
},
"project_id":"d8f52dd7d9e1475dbbf3ba47a4a83313",
"id":"8c1a948bad3948929aa5d5b50627a174"
},
"action":"read",
"outcome":"pending",
"id":"061b7aa7-5879-5225-a331-c002cf23cb6c",
"requestPath":"/v1/nodes/?associated=True"
},
"priority":"INFO",
"publisher_id":"ironic-api",
"message_id":"2f61ebaa-2d3e-4023-afba-f9fca6f21fc2"
}30 Installation for SUSE OpenStack Cloud Entry-scale Cloud with Swift Only #
This page describes the installation step requirements for the SUSE OpenStack Cloud Entry-scale Cloud with swift Only model.
30.1 Important Notes #
For information about when to use the GUI installer and when to use the command line (CLI), see Chapter 13, Overview.
Review the Chapter 2, Hardware and Software Support Matrix that we have listed.
Review the release notes to make yourself aware of any known issues and limitations.
The installation process can occur in different phases. For example, you can install the control plane only and then add Compute nodes afterwards if you would like.
If you run into issues during installation, we have put together a list of Chapter 36, Troubleshooting the Installation you can reference.
Make sure all disks on the system(s) are wiped before you begin the install. (For swift, refer to Section 11.6, “Swift Requirements for Device Group Drives”.)
There is no requirement to have a dedicated network for OS-install and system deployment, this can be shared with the management network. More information can be found in Chapter 9, Example Configurations.
The terms deployer and Cloud Lifecycle Manager are used interchangeably. They refer to the same nodes in your cloud environment.
When running the Ansible playbook in this installation guide, if a runbook fails you will see in the error response to use the
--limitswitch when retrying a playbook. This should be avoided. You can simply re-run any playbook without this switch.DVR is not supported with ESX compute.
When you attach a cinder volume to the VM running on the ESXi host, the volume will not get detected automatically. Make sure to set the image metadata vmware_adaptertype=lsiLogicsas for image before launching the instance. This will help to discover the volume change appropriately.
The installation process will create several OpenStack roles. Not all roles will be relevant for a cloud with swift only, but they will not cause problems.
30.2 Prepare for Cloud Installation #
Review the Chapter 14, Pre-Installation Checklist about recommended pre-installation tasks.
Prepare the Cloud Lifecycle Manager node. The Cloud Lifecycle Manager must be accessible either directly or via
ssh, and have SUSE Linux Enterprise Server 12 SP4 installed. All nodes must be accessible to the Cloud Lifecycle Manager. If the nodes do not have direct access to online Cloud subscription channels, the Cloud Lifecycle Manager node will need to host the Cloud repositories.If you followed the installation instructions for Cloud Lifecycle Manager server (see Chapter 15, Installing the Cloud Lifecycle Manager server), SUSE OpenStack Cloud software should already be installed. Double-check whether SUSE Linux Enterprise and SUSE OpenStack Cloud are properly registered at the SUSE Customer Center by starting YaST and running › .
If you have not yet installed SUSE OpenStack Cloud, do so by starting YaST and running › › . Choose and follow the on-screen instructions. Make sure to register SUSE OpenStack Cloud during the installation process and to install the software pattern
patterns-cloud-ardana.tux >sudo zypper -n in patterns-cloud-ardanaEnsure the SUSE OpenStack Cloud media repositories and updates repositories are made available to all nodes in your deployment. This can be accomplished either by configuring the Cloud Lifecycle Manager server as an SMT mirror as described in Chapter 16, Installing and Setting Up an SMT Server on the Cloud Lifecycle Manager server (Optional) or by syncing or mounting the Cloud and updates repositories to the Cloud Lifecycle Manager server as described in Chapter 17, Software Repository Setup.
Configure passwordless
sudofor the user created when setting up the node (as described in Section 15.4, “Creating a User”). Note that this is not the userardanathat will be used later in this procedure. In the following we assume you named the usercloud. Run the commandvisudoas userrootand add the following line to the end of the file:CLOUD ALL = (root) NOPASSWD:ALL
Make sure to replace CLOUD with your user name choice.
Set the password for the user
ardana:tux >sudo passwd ardanaBecome the user
ardana:tux >su - ardanaPlace a copy of the SUSE Linux Enterprise Server 12 SP4
.isoin theardanahome directory,var/lib/ardana, and rename it tosles12sp4.iso.Install the templates, examples, and working model directories:
ardana >/usr/bin/ardana-init
30.3 Configure Your Environment #
This part of the install is going to depend on the specific cloud configuration you are going to use.
Setup your configuration files, as follows:
See the sample sets of configuration files in the
~/openstack/examples/directory. Each set will have an accompanying README.md file that explains the contents of each of the configuration files.Copy the example configuration files into the required setup directory and edit them to contain the details of your environment:
cp -r ~/openstack/examples/entry-scale-swift/* \ ~/openstack/my_cloud/definition/
Begin inputting your environment information into the configuration files in the
~/openstack/my_cloud/definitiondirectory.Full details of how to do this can be found here: Section 11.10.1, “Ring Specifications in the Input Model”.
In many cases, the example models provide most of the data you need to create a valid input model. However, there are two important aspects you must plan and configure before starting a deploy as follows:
Check the disk model used by your nodes. Specifically, check that all disk drives are correctly named and used as described in Section 11.6, “Swift Requirements for Device Group Drives”.
Select an appropriate partition power for your rings. Detailed information about this is provided at Section 11.10, “Understanding Swift Ring Specifications”.
Optionally, you can use the ardanaencrypt.py script to
encrypt your IPMI passwords. This script uses OpenSSL.
Change to the Ansible directory:
cd ~/openstack/ardana/ansible
Put the encryption key into the following environment variable:
export ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Run the python script below and follow the instructions. Enter a password that you want to encrypt.
ardanaencrypt.py
Take the string generated and place it in the
"ilo_password"field in your~/openstack/my_cloud/definition/data/servers.ymlfile, remembering to enclose it in quotes.Repeat the above for each server.
Before you run any playbooks, remember that you need to export the
encryption key in the following environment variable: export
ARDANA_USER_PASSWORD_ENCRYPT_KEY=<encryption key>
Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
cd ~/openstack/ardana/ansible git add -A git commit -m "My config or other commit message"
This step needs to be repeated any time you make changes to your configuration files before you move onto the following steps. See Chapter 22, Using Git for Configuration Management for more information.
30.4 Provisioning Your Baremetal Nodes #
To provision the baremetal nodes in your cloud deployment you can either use the automated operating system installation process provided by SUSE OpenStack Cloud or you can use the 3rd party installation tooling of your choice. We will outline both methods below:
30.4.1 Using Third Party Baremetal Installers #
If you do not wish to use the automated operating system installation tooling included with SUSE OpenStack Cloud then the requirements that have to be met using the installation tooling of your choice are:
The operating system must be installed via the SLES ISO provided on the SUSE Customer Center.
Each node must have SSH keys in place that allows the same user from the Cloud Lifecycle Manager node who will be doing the deployment to SSH to each node without a password.
Passwordless sudo needs to be enabled for the user.
There should be a LVM logical volume as
/rooton each node.If the LVM volume group name for the volume group holding the
rootLVM logical volume isardana-vg, then it will align with the disk input models in the examples.Ensure that
openssh-server,python,python-apt, andrsyncare installed.
If you chose this method for installing your baremetal hardware, skip forward to the step Running the Configuration Processor.
30.4.2 Using the Automated Operating System Installation Provided by SUSE OpenStack Cloud #
If you would like to use the automated operating system installation tools provided by SUSE OpenStack Cloud, complete the steps below.
30.4.2.1 Deploying Cobbler #
This phase of the install process takes the baremetal information that was
provided in servers.yml and installs the Cobbler
provisioning tool and loads this information into Cobbler. This sets each
node to netboot-enabled: true in Cobbler. Each node
will be automatically marked as netboot-enabled: false
when it completes its operating system install successfully. Even if the
node tries to PXE boot subsequently, Cobbler will not serve it. This is
deliberate so that you cannot reimage a live node by accident.
The cobbler-deploy.yml playbook prompts for a password
- this is the password that will be encrypted and stored in Cobbler, which
is associated with the user running the command on the Cloud Lifecycle Manager, that you
will use to log in to the nodes via their consoles after install. The
username is the same as the user set up in the initial dialogue when
installing the Cloud Lifecycle Manager from the ISO, and is the same user that is running
the cobbler-deploy play.
When imaging servers with your own tooling, it is still necessary to have
ILO/IPMI settings for all nodes. Even if you are not using Cobbler, the
username and password fields in servers.yml need to
be filled in with dummy settings. For example, add the following to
servers.yml:
ilo-user: manual ilo-password: deployment
Run the following playbook which confirms that there is IPMI connectivity for each of your nodes so that they are accessible to be re-imaged in a later step:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-power-status.ymlRun the following playbook to deploy Cobbler:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.yml
30.4.2.2 Imaging the Nodes #
This phase of the install process goes through a number of distinct steps:
Powers down the nodes to be installed
Sets the nodes hardware boot order so that the first option is a network boot.
Powers on the nodes. (The nodes will then boot from the network and be installed using infrastructure set up in the previous phase)
Waits for the nodes to power themselves down (this indicates a successful install). This can take some time.
Sets the boot order to hard disk and powers on the nodes.
Waits for the nodes to be reachable by SSH and verifies that they have the signature expected.
Deploying nodes has been automated in the Cloud Lifecycle Manager and requires the following:
All of your nodes using SLES must already be installed, either manually or via Cobbler.
Your input model should be configured for your SLES nodes.
You should have run the configuration processor and the
ready-deployment.ymlplaybook.
Execute the following steps to re-image one or more nodes after you have
run the ready-deployment.yml playbook.
Run the following playbook, specifying your SLES nodes using the nodelist. This playbook will reconfigure Cobbler for the nodes listed.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook prepare-sles-grub2.yml -e \ nodelist=node1[,node2,node3]Re-image the node(s) with the following command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml \ -e nodelist=node1[,node2,node3]
If a nodelist is not specified then the set of nodes in Cobbler with
netboot-enabled: True is selected. The playbook pauses
at the start to give you a chance to review the set of nodes that it is
targeting and to confirm that it is correct.
You can use the command below which will list all of your nodes with the
netboot-enabled: True flag set:
sudo cobbler system find --netboot-enabled=1
30.5 Running the Configuration Processor #
Once you have your configuration files setup, you need to run the configuration processor to complete your configuration.
When you run the configuration processor, you will be prompted for two
passwords. Enter the first password to make the configuration processor
encrypt its sensitive data, which consists of the random inter-service
passwords that it generates and the ansible group_vars
and host_vars that it produces for subsequent deploy
runs. You will need this password for subsequent Ansible deploy and
configuration processor runs. If you wish to change an encryption password
that you have already used when running the configuration processor then
enter the new password at the second prompt, otherwise just press
Enter to bypass this.
Run the configuration processor with this command:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.yml
For automated installation (for example CI), you can specify the required passwords on the ansible command line. For example, the command below will disable encryption by the configuration processor:
ardana > ansible-playbook -i hosts/localhost config-processor-run.yml \
-e encrypt="" -e rekey=""If you receive an error during this step, there is probably an issue with one or more of your configuration files. Verify that all information in each of your configuration files is correct for your environment. Then commit those changes to Git using the instructions in the previous section before re-running the configuration processor again.
For any troubleshooting information regarding these steps, see Section 36.2, “Issues while Updating Configuration Files”.
30.6 Deploying the Cloud #
Use the playbook below to create a deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
[OPTIONAL] - Run the
wipe_disks.ymlplaybook to ensure all of your non-OS partitions on your nodes are completely wiped before continuing with the installation. Thewipe_disks.ymlplaybook is only meant to be run on systems immediately after runningbm-reimage.yml. If used for any other case, it may not wipe all of the expected partitions.If you are using fresh machines this step may not be necessary.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts wipe_disks.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts wipe_disks.yml --ask-vault-passRun the
site.ymlplaybook below:ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts site.ymlIf you have used an encryption password when running the configuration processor use the command below and enter the encryption password when prompted:
ardana >ansible-playbook -i hosts/verb_hosts site.yml --ask-vault-passNoteThe step above runs
osconfigto configure the cloud andardana-deployto deploy the cloud. Therefore, this step may run for a while, perhaps 45 minutes or more, depending on the number of nodes in your environment.Verify that the network is working correctly. Ping each IP in the
/etc/hostsfile from one of the controller nodes.
For any troubleshooting information regarding these steps, see Section 36.3, “Issues while Deploying the Cloud”.
30.7 Post-Installation Verification and Administration #
We recommend verifying the installation using the instructions in Chapter 38, Post Installation Tasks.
There are also a list of other common post-installation administrative tasks listed in the Chapter 44, Other Common Post-Installation Tasks list.
31 Installing SLES Compute #
31.1 SLES Compute Node Installation Overview #
SUSE OpenStack Cloud 9 supports SLES compute nodes, specifically SUSE Linux Enterprise Server 12 SP4. SUSE
does not ship a SLES ISO with SUSE OpenStack Cloud so you will need to download a copy of
the SLES ISO (SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.iso)
from SUSE. You can use the following
link to download the ISO. To do so, either log in or create a SUSE
account before downloading:
https://www.suse.com/products/server/download/.
There are two approaches for deploying SLES compute nodes in SUSE OpenStack Cloud:
Using the Cloud Lifecycle Manager to automatically deploy SLES Compute Nodes.
Provisioning SLES nodes yourself, either manually or using a third-party tool, and then providing the relevant information to the Cloud Lifecycle Manager.
These two approaches can be used whether you are installing a cloud for the first time or adding a compute node to an existing cloud. Regardless of your approach, you should be certain to register your SLES compute nodes in order to get product updates as they come available. For more information, see Chapter 1, Registering SLES.
31.2 SLES Support #
SUSE Linux Enterprise Server (SLES) Host OS KVM and/or supported SLES guests have been tested and qualified by SUSE to run on SUSE OpenStack Cloud.
31.3 Using the Cloud Lifecycle Manager to Deploy SLES Compute Nodes #
The method used for deploying SLES compute nodes using Cobbler on the Cloud Lifecycle Manager uses legacy BIOS.
31.3.1 Deploying legacy BIOS SLES Compute nodes #
The installation process for legacy BIOS SLES Compute nodes is similar to that described in Chapter 24, Installing Mid-scale and Entry-scale KVM with some additional requirements:
The standard SLES ISO (SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.iso) must be accessible as
~/sles12sp4.iso. Rename the ISO or create a symbolic link:mv SLE-12-SP4-Server-DVD-x86_64-GM-DVD1.iso ~/sles12sp4.iso
You must identify the node(s) on which you want to install SLES, by adding the key/value pair
distro-id: sles12sp4-x86_64to server details inservers.yml. If there are any network interface or disk layout differences in the new server compared to the servers already in the model, you may also need to updatenet_interfaces.yml,server_roles.yml,disk_compute.ymlandcontrol_plane.yml. For more information on configuration of the Input Model for SLES, see Section 10.1, “SLES Compute Nodes”.Run the playbook
config-processor-run.ymlto check for errors in the updated model.Run the
ready-deployment.ymlplaybook to build the newscratchdirectory.Record the management network IP address that is used for the new server. It will be used in the installation process.
31.3.2 Deploying UEFI SLES compute nodes #
Deploying UEFI nodes has been automated in the Cloud Lifecycle Manager and requires the following to be met:
All of your nodes using SLES must already be installed, either manually or via Cobbler.
Your input model should be configured for your SLES nodes, per the instructions at Section 10.1, “SLES Compute Nodes”.
You should have run the configuration processor and the
ready-deployment.ymlplaybook.
Execute the following steps to re-image one or more nodes after you have run
the ready-deployment.yml playbook.
Run the following playbook, ensuring that you specify only your UEFI SLES nodes using the nodelist. This playbook will reconfigure Cobbler for the nodes listed.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook prepare-sles-grub2.yml -e nodelist=node1[,node2,node3]Re-image the node(s), ensuring that you only specify your UEFI SLES nodes using the nodelist.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost bm-reimage.yml \ -e nodelist=node1[,node2,node3]Back up the
grub.cfg-*files in/srv/tftpboot/as they will be overwritten when running the cobbler-deploy playbook on the next step. You will need these files if you need to reimage the nodes in the future.Run the
cobbler-deploy.ymlplaybook, which will reset Cobbler back to the default values:ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost cobbler-deploy.yml
31.3.2.1 UEFI Secure Boot #
Secure Boot is a method used to restrict binary execution for booting the system. With this option enabled, system BIOS will only allow boot loaders with trusted cryptographic signatures to be executed, thus preventing malware from hiding embedded code in the boot chain. Each boot loader launched during the boot process is digitally signed and that signature is validated against a set of trusted certificates embedded in the UEFI BIOS. Secure Boot is completely implemented in the BIOS and does not require special hardware.
Thus Secure Boot is:
Intended to prevent boot-sector malware or kernel code injection.
Hardware-based code signing.
Extension of the UEFI BIOS architecture.
Optional with the ability to enable or disable it through the BIOS.
In Boot Options of RBSU, needs to be set to
UEFI Mode and
should be Enabled>.
Secure Boot is enabled at › › › › .
31.4 Provisioning SLES Yourself #
This section outlines the steps needed to manually provision a SLES node so that it can be added to a new or existing SUSE OpenStack Cloud 9 cloud.
31.4.1 Configure Cloud Lifecycle Manager to Enable SLES #
Take note of the IP address of the Cloud Lifecycle Manager node. It will be used below during Section 31.4.6, “Add zypper repository”.
Mount or copy the contents of
SLE-12-SP3-Server-DVD-x86_64-GM-DVD1.isoto/srv/www/suse-12.3/x86_64/repos/ardana/sles12/zypper/OS/
If you choose to mount an ISO, we recommend creating an /etc/fstab entry to
ensure the ISO is mounted after a reboot.
31.4.2 Install SUSE Linux Enterprise Server 12 SP4 #
Install SUSE Linux Enterprise Server 12 SP4 using the standard iso
(SLE-12-SP3-Server-DVD-x86_64-GM-DVD1.iso)
Boot the SUSE Linux Enterprise Server 12 SP4 ISO.
Agree to the license
Edit the network settings, enter the the management network IP address recorded earlier. It is not necessary to enter a /. For product registration to work correctly, you must provide a DNS server. Enter the IP address and the .
Additional
System Probingwill occur.On the
Registrationpage, you can skip registration if the database server does not have a external interface or if there is no SMT server on the MGMT LAN.No
Add On Productsare needed.For
System Role, select . Do not select .Partitioning
Select and to clear .
Delete all
Volume Groups.Under the root of the directory tree, delete
/dev/sda.Delete any other partitions on any other drives.
under
sda, calledardana, with a of 250MB.Add an . Partition should be formatted as
FATand mounted at .with all the remaining space (). The role for this partition is . It should not be mounted. It should not be formatted.
Select and add a volume group to
/dev/sda2calledardana-vg.Add an LV to
ardana-vgcalledroot,Typeof , of 50GB, . Format as and mount at/.Acknowledge the warning about having no swap partition.
Press on the
Suggested Partitioningpage.
Pick your and check
Hardware Clock Set to UTC.Create a user named
ardanaand a password forsystem administrator. Do not check .On the
Installation Settingspage:Disable firewall
Enable SSH service
Set
textas the .
Press and
Confirm Installationwith the button.Installation will begin and the system will reboot automatically when installation is complete.
When the system is booted, log in as
root, using the system administrator set during installation.Set up the
ardanauser and addardanato thesudoersgroup.root #useradd -s /bin/bash -d /var/lib/ardana -m ardanaroot #passwd ardanaEnter and retype the password for user
ardana.root #echo "ardana ALL=(ALL) NOPASSWD:ALL" | sudo tee -a \ /etc/sudoers.d/ardanaAdd an ardana group (id 1000) and change group owner to
ardana.root #groupadd --gid 1000 ardanaroot #chown -R ardana:ardana /var/lib/ardanaDisconnect the installation ISO. List repositories and remove the repository that was used for the installation.
root #zypper lrIdentify the
Nameof the repository to remove.root #zypper rr REPOSITORY_NAMECopy the SSH key from the Cloud Lifecycle Manager.
root #ssh-copy-id ardana@DEPLOYER_IP_ADDRESSLog in to the SLES via SSH.
Continue with the
site.ymlplaybook to scale out the node.
31.4.3 Assign a static IP #
Use the
ip addrcommand to find out what network devices are on your system:1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 ::1/128 scope host valid_lft forever preferred_lft forever 2: eno1: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000 link/ether f0:92:1c:05:89:70 brd ff:ff:ff:ff:ff:ff inet 10.13.111.178/26 brd 10.13.111.191 scope global eno1 valid_lft forever preferred_lft forever inet6 fe80::f292:1cff:fe05:8970/64 scope link valid_lft forever preferred_lft forever 3: eno2: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP qlen 1000 link/ether f0:92:1c:05:89:74 brd ff:ff:ff:ff:ff:ffIdentify the one that matches the MAC address of your server and edit the corresponding config file in
/etc/sysconfig/network-scripts.vi /etc/sysconfig/network-scripts/ifcfg-eno1Edit the
IPADDRandNETMASKvalues to match your environment. Note that theIPADDRis used in the corresponding stanza inservers.yml. You may also need to setBOOTPROTOtonone.TYPE=Ethernet BOOTPROTO=none DEFROUTE=yes PEERDNS=yes PEERROUTES=yes IPV4_FAILURE_FATAL=no IPV6INIT=yes IPV6_AUTOCONF=yes IPV6_DEFROUTE=yes IPV6_PEERDNS=yes IPV6_PEERROUTES=yes IPV6_FAILURE_FATAL=no NAME=eno1 UUID=36060f7a-12da-469b-a1da-ee730a3b1d7c DEVICE=eno1 ONBOOT=yes NETMASK=255.255.255.192 IPADDR=10.13.111.14
[OPTIONAL] Reboot your SLES node and ensure that it can be accessed from the Cloud Lifecycle Manager.
31.4.4 Add ardana user and home directory #
useradd -m ardana passwd ardana
31.4.5 Allow user ardana to sudo without password #
Setting up sudo on SLES is covered in the SLES Administration Guide at https://documentation.suse.com/sles/15-SP1/single-html/SLES-admin/#sec-sudo-conf.
The recommendation is to create user specific sudo config files under
/etc/sudoers.d, therefore creating an /etc/sudoers.d/ardana config file with
the following content will allow sudo commands without the requirement of a
password.
ardana ALL=(ALL) NOPASSWD:ALL
31.4.6 Add zypper repository #
Using the ISO-based repositories created above, add the zypper repositories.
Follow these steps. Update the value of deployer_ip as necessary.
deployer_ip=192.168.10.254tux >sudo zypper addrepo --no-gpgcheck --refresh http://$deployer_ip:79/ardana/sles12/zypper/OS SLES-OStux >sudo zypper addrepo --no-gpgcheck --refresh http://$deployer_ip:79/ardana/sles12/zypper/SDK SLES-SDK
To verify that the repositories have been added, run:
tux > sudo zypper repos --detailFor more information about Zypper, see the SLES Administration Guide at https://documentation.suse.com/sles/15-SP1/single-html/SLES-admin/#sec-zypper.
If you intend on attaching encrypted volumes to any of your SLES Compute nodes, install the cryptographic libraries through cryptsetup on each node. Run the following command to install the necessary cryptographic libraries:
tux > sudo zypper in cryptsetup31.4.7 Add Required Packages #
As documented in Section 24.4, “Provisioning Your Baremetal Nodes”,
you need to add extra packages.
Ensure that openssh-server,
python,
and rsync are installed.
31.4.8 Set up passwordless SSH access #
Once you have started your installation using the Cloud Lifecycle Manager, or if
you are adding a SLES node to an existing cloud, you need to copy the
Cloud Lifecycle Manager public key to the SLES node. One way of doing this is to
copy the /home/ardana/.ssh/authorized_keys from another
node in the cloud to the same location on the SLES node. If you are
installing a new cloud, this file will be available on the nodes after
running the bm-reimage.yml playbook.
Ensure that there is global read access to the file
/home/ardana/.ssh/authorized_keys.
Now test passwordless SSH from the deployer and check your ability to remotely execute sudo commands:
ssh ardana@IP_OF_SLES_NODE "sudo tail -5 /var/log/messages"
32 Installing manila and Creating manila Shares #
32.1 Installing manila #
The OpenStack Shared File Systems service (manila) provides file storage to a virtual machine. The Shared File Systems service provides a storage provisioning control plane for shared or distributed file systems. The service enables management of share types and share snapshots if you have a driver that supports them.
The manila service consists of the following components:
manila-api
manila-data
manila-scheduler
manila-share
messaging queue
These manila components are included in example SUSE OpenStack Cloud models
based on nova KVM, such as entry-scale-kvm,
entry-scale-kvm-mml, and
mid-scale-kvm. General installation instructions are
available at Chapter 24, Installing Mid-scale and Entry-scale KVM.
If you modify one of these cloud models to set up a dedicated Cloud Lifecycle Manager, add
manila-client item to the list of service components for
the Cloud Lifecycle Manager cluster.
The following steps install manila if it is not already present in your cloud data model:
Log in to the Cloud Lifecycle Manager.
Apply manila changes in
control_plane.yml.ardana >cd /var/lib/ardana/openstack/my_cloud/definition/data/Add
manila-clientto the list of service components for Cloud Lifecycle Manager, andmanila-apito the Control Node.Run the Configuration Processor.
ardana >cd ~/openstackardana >git add -Aardana >git commit -m "manila config"ardana >cd ~/openstack/ardana/ansible/ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlDeploy manila
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts percona-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts manila-deploy.ymlardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ardana-gen-hosts-file.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts clients-deploy.ymlIf manila has already been installed and is being reconfigured, run the following for the changes to take effect:
ardana >ansible-playbook -i hosts/verb_hosts manila-stop.ymlardana >ansible-playbook -i hosts/verb_hosts manila-start.ymlVerify the manila installation
ardana >cdardana >. manila.osrcardana >. service.osrcardana >manila api-versionardana >manila service-listThe manila CLI can be run from Cloud Lifecycle Manager or controller nodes.
The manila-share service component is not started by the
manila-deploy.yml playbook when run under default
conditions. This component requires that a valid backend be configured,
which is described in Section 32.3, “Configure manila Backend”.
32.2 Adding manila to an Existing SUSE OpenStack Cloud Environment #
Add manila to an existing SUSE OpenStack Cloud 9 installation or as part of an upgrade with the following steps:
Add the items listed below to the list of service components in
~/openstack/my_cloud/definition/data/control_plane.yml. Add them to clusters that haveserver-roleset toCONTROLLER-ROLE(applies to entry-scale models).manila-client
manila-api
If your environment uses a dedicated Cloud Lifecycle Manager, add
magnum-clientto the list of service components for the Cloud Lifecycle Manager in~/openstack/my_cloud/definition/data/control_plane.yml.Commit your configuration to the local git repo.
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"Run the configuration processor.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlUpdate deployment directory.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlDeploy manila.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts percona-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts manila-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-gen-hosts-file.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts clients-deploy.ymlVerify the manila installation.
ardana >cdardana >. manila.osrcardana >. service.osrcardana >manila api-versionardana >manila service-list
The manila CLI can be run from the Cloud Lifecycle Manager or controller nodes.
Proceed to Section 32.3, “Configure manila Backend”.
32.3 Configure manila Backend #
32.3.1 Configure NetaApp manila Back-end #
An account with cluster administrator privileges must be used with the
netapp_login option when using Share Server management.
Share Server management creates Storage Virtual Machines (SVM), thus SVM
administrator privileges are insufficient.
There are two modes for the NetApp manila back-end:
driver_handles_share_servers = Truedriver_handles_share_servers = FalseThis value must be set toFalseif you want the driver to operate without managing share servers.
More information is available from NetApp OpenStack
The steps to configure a NetApp manila back-end are:
Configure a back-end in the manila configuration file, following the directions and comments in the file.
ardana >cd ~/openstack/my_cloudardana >vi config/manila/manila.conf.j2Commit your configuration to the local Git repo.
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"Run the configuration processor.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlUpdate deployment directory.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun reconfiguration playbook.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts manila-reconfigure.ymlRestart manila services.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts manila-stop.ymlardana >ansible-playbook -i hosts/verb_hosts manila-start.yml
After the manila-share service has been initialized
with a backend, it can be controlled independently of
manila-api by using the playbooks
manila-share-start.yml,
manila-share-stop.yml, and
manila-share-status.yml.
32.3.2 Configure CephFS manila Backend #
Configure a back-end in the manila configuration file,
~/openstack/my_cloud vi config/manila/manila.conf.j2.
To define a CephFS native back-end, create a section like the following:
[cephfsnative1] driver_handles_share_servers = False share_backend_name = CEPHFSNATIVE1 share_driver = manila.share.drivers.cephfs.driver.CephFSDriver cephfs_conf_path = /etc/ceph/ceph.conf cephfs_protocol_helper_type = CEPHFS cephfs_auth_id = manila cephfs_cluster_name = ceph cephfs_enable_snapshots = False
Add CephFS to
enabled_share_protocols:enabled_share_protocols = NFS,CIFS,CEPHFS
Edit the
enabled_share_backendsoption in theDEFAULTsection to point to the driver’s back-end section name.According to the environment, modify back-end specific lines in
~/openstack/my_cloud vi config/manila/manila.conf.j2.Commit your configuration to the local Git repo.
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "My config or other commit message"Run the configuration processor.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlUpdate deployment directory.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun reconfiguration playbook.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts manila-reconfigure.ymlRestart manila services.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts manila-stop.ymlardana >ansible-playbook -i hosts/verb_hosts manila-start.yml
After the manila-share service has been initialized
with a back-end, it can be controlled independently of
manila-api by using the playbooks
manila-share-start.yml,
manila-share-stop.yml, and
manila-share-status.yml.
For more details of the CephFS manila back-end, see OpenStack CephFS driver.
32.4 Creating manila Shares #
manila can support two modes, with and without the handling of share servers. The mode depends on driver support.
Mode 1: The back-end is a generic driver,
driver_handles_share_servers = False (DHSS is disabled).
The following example creates a VM using manila share image.
ardana >wget http://tarballs.openstack.org/manila-image-elements/images/manila-service-image-master.qcow2ardana >. service.osrc;openstack image create --name "manila-service-image-new" \ --file manila-service-image-master.qcow2 --disk-format qcow2 \ --container-format bare --visibility public --progressardana >openstack image list (verify manila image)ardana >openstack security group create manila-security-group \ --description "Allows web and NFS traffic to manila server."ardana >openstack security group rule create manila-security-group \ --protocol tcp --dst-port 2049ardana >openstack security group rule create manila-security-group \ --protocol udp --dst-port 2049ardana >openstack security group rule create manila-security-group \ --protocol tcp --dst-port 22ardana >openstack security group rule create manila-security-group \ --protocol icmpardana >openstack security group rule list manila-security-group (verify manila security group)ardana >openstack keypair create --public-key ~/.ssh/id_rsa.pub mykeyardana >openstack network create n1ardana >openstack subnet create s1 --network n1 --subnet-range 11.11.11.0/24ardana >openstack router create r1ardana >openstack router add subnet r1 s1ardana >openstack router set r1 ext-netardana >openstack network listardana >openstack server create manila-vm --flavor m1.small \ --image IMAGE_ID --nic net-id=N1_ID --security-group manila-security-group \ --key-name myKeyardana >oenstack floating ip create EXT-NET_IDardana >openstack server add floating ip manila-vm EXT-NET_IDValidate your ability to ping or connect by SSH to
manila-vmwith credentialsmanila/manila.Modify the configuration:
ardana >vi /etc/manila/manila.conf.d/100-manila.confMake changes in [generic1] section
service_instance_name_or_id = MANILA_VM_ID service_net_name_or_ip = MANILA_VM_FLOATING_IP tenant_net_name_or_ip = MANILA_VM_FLOATING_IP
Create a share type. OpenStack docs has detailed instructions. Use the instructions for
manila type-create default_share_type FalseRestart manila services and verify they are up.
ardana >systemctl restart openstack-manila-api \ openstack-manila-share openstack-manila-schedulerardana >manila service-listContinue creating a share
ardana >manila create NFS 1 --name SHAREardana >manila list (status will change from creating to available)ardana >manila show share1ardana >manila access-allow SHARE ip INSTANCE_IPMount the share on a Compute instance
ardana >mkdir ~/test_directorytux >sudo mount -vt nfs EXT-NET_ID:/shares/SHARE-SHARE-ID ~/test_folder
Mode 2: The back-end is NetApp,
driver_handles_share_servers = True (DHSS is enabled).
Procedure for driver_handles_share_servers = False is similar to Mode 1.
Modify the configuration
ardana >vi /etc/manila/manila.conf.d/100-manila.confAdd a
backendNetAppsectionshare_driver = manila.share.drivers.netapp.common.NetAppDriver driver_handles_share_servers = True share_backend_name=backendNetApp netapp_login=NetApp_USERNAME netapp_password=NetApp_PASSWORD netapp_server_hostname=NETAPP_HOSTNAME netapp_root_volume_aggregate=AGGREGATE_NAME
Add to [DEFAULT] section
enabled_share_backends = backendNetApp default_share_type = default1
Create a manila share image and verify it
ardana >wget http://tarballs.openstack.org/manila-image-elements/images/manila-service-image-master.qcow2ardana >. service.osrc;openstack image createmanila-service-image-new\ --file manila-service-image-master.qcow2 --disk-format qcow2 \ --container-format bare --visibility public --progressardana >openstack image list (verify a manila image)Create a share type. OpenStack docs has detailed instructions. Use the instructions for
manila type-create default_share_type True.Restart services
ardana >systemctl restart openstack-manila-api openstack-manila-share \openstack-manila-schedulerardana >manila service-list (verify services are up)Continue creating a share.
OCTAVIA-MGMT-NETcan be used as PRIVATE_NETWORK in this example.ardana >manila share-network-create --name demo-share-network1 \ --neutron-net-id PRIVATE_NETWORK_ID --neutron-subnet-id PRIVATE_NETWORK_SUBNET_IDardana >manila create NFS 1 --name share2 --share-network demo-share-network1
32.5 Troubleshooting #
If manila-list shows share status in error, use storage aggregate
show to list available aggregates. Errors may be found in
/var/log/manila/manila-share.log
if the compute nodes do not have access to manila back-end server, use
the manila-share service on controller nodes instead. You
can do so by either running sudo systemctl stop
openstack-manila-share on compute to turn off its share service or
skipping adding "manila-share" to compute hosts in the input-model
(control_plane.yml in
/var/lib/ardana/openstack/my_cloud/definition/data).
33 Installing SUSE CaaS Platform heat Templates #
This chapter describes how to install SUSE CaaS Platform v3 using heat template on SUSE OpenStack Cloud.
33.1 SUSE CaaS Platform heat Installation Procedure #
Download the latest SUSE CaaS Platform for OpenStack image (for example,
SUSE-CaaS-Platform-3.0-OpenStack-Cloud.x86_64-1.0.0-GM.qcow2) from https://download.suse.com.Upload the image to glance:
openstack image create --public --disk-format qcow2 --container-format \ bare --file SUSE-CaaS-Platform-3.0-OpenStack-Cloud.x86_64-1.0.0-GM.qcow2 \ CaaSP-3
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
zypper in caasp-openstack-heat-templates
The installed templates are located in
/usr/share/caasp-openstack-heat-templates.Alternatively, you can get official heat templates by cloning the appropriate Git repository:
git clone https://github.com/SUSE/caasp-openstack-heat-templates
In horizon, go to › › .
Select from the drop-down box and upload the
caasp-stack.yamlfile.In the dialog, provide the required information (stack name, password, flavor size, external network of your environment, etc.).
Click to launch the stack. This creates all required resources for running SUSE CaaS Platform in an OpenStack environment. The stack creates one Admin Node, one Master Node, and server worker nodes as specified.
Specify the appropriate flavor and network settings in the
caasp-environment.yamlfile.Create a stack in heat by passing the template, environment file, and parameters:
openstack stack create -t caasp-stack.yaml -e caasp-environment.yaml \ --parameter image=CaaSP-3 caasp-stack
After the stack has been created, the Velum SUSE CaaS Platform dashboard runs on the Admin Node. You can access it using the Admin Node's floating IP address.
Create an account and follow the steps in the Velum SUSE CaaS Platform dashboard to complete the SUSE CaaS Platform installation.
When you have successfully accessed the admin node web interface via the floating IP, follow the instructions at https://documentation.suse.com/suse-caasp/4.1/single-html/caasp-deployment/ to continue the setup of SUSE CaaS Platform.
33.2 Installing SUSE CaaS Platform with Multiple Masters #
A heat stack with load balancing and multiple master nodes can only be created from the command line, because horizon does not have support for nested heat templates.
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
zypper in caasp-openstack-heat-templates
The installed templates are located in
/usr/share/caasp-openstack-heat-templates.
A working load balancer is needed in your SUSE OpenStack Cloud deployment. SUSE OpenStack Cloud uses HAProxy.
Verify that load balancing with HAProxy is working correctly
in your OpenStack installation by creating a load balancer manually and
checking that the provisioning_status changes to
Active.
ardana > openstack loadbalancer show
<LOAD_BALANCER_ID>HAProxy is the default load balancer provider in SUSE OpenStack Cloud.
The steps below can be used to set up a network, subnet, router, security
and IPs for a test lb_net1 network with
lb_subnet1 subnet.
ardana >openstack network create lb_net1ardana >openstack subnet create --name lb_subnet1 lb_net1 \ --subnet-range 172.29.0.0/24 --gateway 172.29.0.2ardana >openstack router create lb_router1ardana >openstack router add subnet lb_router1 lb_subnet1ardana >openstack router set lb_router1 --external-gateway ext-netardana >openstack network list
Specify the appropriate flavor and network settings in the
caasp-multi-master-environment.yamlfile.Set
master_countto the desired number in thecaasp-multi-master-environment.yamlfile. The master count must be set to an odd number of nodes.master_count: 3
Create a stack in heat by passing the template, environment file, and parameters:
ardana >openstack stack create -t caasp-multi-master-stack.yaml \ -e caasp-multi-master-environment.yaml --parameter image=CaaSP-3 caasp-multi-master-stackFind the floating IP address of the load balancer. This is necessary for accessing the Velum SUSE CaaS Platform dashboard.
ardana >openstack loadbalancer list --providerFrom the output, copy the
idand enter it in the following command as shown in the following example:ardana >openstack loadbalancer show id+---------------------+------------------------------------------------+ | Field | Value | +---------------------+------------------------------------------------+ | admin_state_up | True | | description | | | id | 0d973d80-1c79-40a4-881b-42d111ee9625 | | listeners | {"id": "c9a34b63-a1c8-4a57-be22-75264769132d"} | | | {"id": "4fa2dae0-126b-4eb0-899f-b2b6f5aab461"} | | name | caasp-stack-master_lb-bhr66gtrx3ue | | operating_status | ONLINE | | pools | {"id": "8c011309-150c-4252-bb04-6550920e0059"} | | | {"id": "c5f55af7-0a25-4dfa-a088-79e548041929"} | | provider | haproxy | | provisioning_status | ACTIVE | | tenant_id | fd7ffc07400642b1b05dbef647deb4c1 | | vip_address | 172.28.0.6 | | vip_port_id | 53ad27ba-1ae0-4cd7-b798-c96b53373e8b | | vip_subnet_id | 87d18a53-ad0c-4d71-b82a-050c229b710a | +---------------------+------------------------------------------------+Search the floating IP list for
vip_addressardana >openstack floating ip list | grep 172.28.0.6 | d636f3...481b0c | fd7ff...deb4c1 | 172.28.0.6 | 10.84.65.37 | 53ad2...373e8b |The load balancer floating ip address is 10.84.65.37
Accessing the Velum SUSE CaaS Platform Dashboard
After the stack has been created, the Velum SUSE CaaS Platform dashboard runs on the admin node. You can access it using the floating IP address of the admin node.
Create an account and follow the steps in the Velum SUSE CaaS Platform dashboard to complete the SUSE CaaS Platform installation.
SUSE CaaS Platform Admin Node Install: Screen 1
If you plan to manage your containers using Helm or Airship (this is common),
check the box labeled Install Tiller (Helm's server component).
SUSE CaaS Platform Admin Node Install: Screen 2
SUSE CaaS Platform Admin Node Install: Screen 3
SUSE CaaS Platform Admin Node Install: Screen 4
SUSE CaaS Platform Admin Node Install: Screen 5
Set External Kubernetes API to LOADBALANCER_FLOATING_IP, External Dashboard FQDN to ADMIN_NODE_FLOATING_IP
SUSE CaaS Platform Admin Node Install: Screen 6
SUSE CaaS Platform Admin Node Install: Screen 7
33.3 Deploy SUSE CaaS Platform Stack Using heat SUSE CaaS Platform Playbook #
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
ardana >zypper in caasp-openstack-heat-templatesThe installed templates are located in
/usr/share/caasp-openstack-heat-templates.Run
heat-caasp-deploy.ymlon the Cloud Lifecycle Manager to create a SUSE CaaS Platform cluster with heat templates from thecaasp-openstack-heat-templatespackage.ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.ymlIn a browser, navigate to the horizon UI to determine the floating IP address assigned to the admin node.
Go to http://ADMIN-NODE-FLOATING-IP/ to bring up the Velum dashboard.
Complete the web-based bootstrap process to bring up the SUSE CaaS Platform Kubernetes cluster. Refer to the SUSE CaaS Platform documentation for specifics.
When prompted, set the
Internal Dashboard Locationto the private network IP address (i.e. in the the 172.x.x.x subnet) of the SUSE CaaS Platform admin node created during theheat-caasp-deploy.ymlplaybook. Do not use the floating IP address which is also associated with the node.
33.4 Deploy SUSE CaaS Platform Cluster with Multiple Masters Using heat CaasP Playbook #
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
ardana >zypper in caasp-openstack-heat-templatesThe installed templates are located in
/usr/share/caasp-openstack-heat-templates.On the Cloud Lifecycle Manager, run the
heat-caasp-deploy.ymlplaybook and pass parameters forcaasp_stack_name,caasp_stack_yaml_fileandcaasp_stack_env_yaml_file.ardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_stack_name=caasp_multi-master caasp_stack_yaml_file=caasp-multi-master-stack.yaml caasp_stack_env_yaml_file=caasp-multi-master-environment.yaml"
33.5 SUSE CaaS Platform OpenStack Image for heat SUSE CaaS Platform Playbook #
By default the heat SUSE CaaS Platform playbook downloads the SUSE CaaS Platform image from http://download.suse.de/install/SUSE-CaaSP-3-GM/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2. If this URL is not accessible, the SUSE CaaS Platform image can be downloaded from https://download.suse.com/Download?buildid=z7ezhywXXRc and copied to the deployer.
To create a SUSE CaaS Platform cluster and pass the path to the downloaded image, run the following commands:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_image_tmp_path=~/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2"
To create a SUSE CaaS Platform cluster with multiple masters and pass the path to the downloaded image, run the following commands:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_image_tmp_path=caasp_image_tmp_path=~/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2 caasp_stack_name=caasp_multi-master caasp_stack_yaml_file=caasp-multi-master-stack.yaml caasp_stack_env_yaml_file=caasp-multi-master-environment.yaml"
33.6 Enabling the Cloud Provider Integration (CPI) Feature #
When deploying a CaaaSP cluster using SUSE CaaS Platform OpenStack heat
templates, the following CPI parameters can be set in
caasp-environment.yaml or
caasp-multi-master-environment.yaml.
- cpi_auth_url
The URL of the keystone API used to authenticate the user. This value can be found on OpenStack Dashboard under › › (for example, https://api.keystone.example.net:5000/)
- cpi_domain_name
Name of the domain the user belongs to.
- cpi_tenant_name
Name of the project the user belongs to. This is the project in which SUSE CaaS Platform resources are created.
- cpi_region
Name of the region to use when running a multi-region OpenStack cloud. The region is a general division of an OpenStack deployment.
- cpi_username
Username of a valid user that has been set in keystone. Default: admin
- cpi_password
Password of a valid user that has been set in keystone.
- cpi_monitor_max_retries
neutron load balancer monitoring max retries. Default: 3
- cpi_bs_version
cinder Block Storage API version. Possible values are v1, v2 , v3 or auto. Default:
auto- cpi_ignore_volume_az
Ignore cinder and nova availability zones. Default:
true- dns_nameserver
Set this to the IP address of a DNS nameserver accessible by the SUSE CaaS Platform cluster.
Immediately after the SUSE CaaS Platform cluster comes online, and before bootstrapping, install the latest SUSE CaaS Platform 3.0 Maintenance Update using the following steps.
Register the SUSE CaaS Platform nodes for Maintenance Updates by following the instructions in Section 33.7, “Register SUSE CaaS Platform Cluster for Software Updates”.
On each of the SUSE CaaS Platform nodes, install the latest Maintenance Update:
tux >sudo transactional-updateVerify that the Velum image packages were updated:
tux >sudo zypper se --detail velum-image i | sles12-velum-image | package | 3.1.7-3.27.3 | x86_64 | update_caaspReboot the node:
tux >sudo rebootFinally, when preparing to bootstrap using the SUSE CaaS Platform web interface, upload a valid trust certificate that can validate a certificate presented by keystone at the specified
keystone_auth_urlin theSystem-wide certificatesection of Velum. If the SSL certificate provided by keystone cannot be verified, bootstrapping fails with the errorx509: certificate signed by unknown authority.NoteIf your OpenStack endpoints operate on the Internet, or if the SSL certificates in use have been signed by a public authority, no action should be needed to enable secure communication with them.
If your OpenStack services operate in a private network using SSL certificates signed by an organizational certificate authority, provide that CA certificate as the system-wide certificate.
If your OpenStack service SSL infrastructure was self-signed during the installation of SUSE OpenStack Cloud 9 (as is done by default), its CA certificate can be retrieved from the Cloud Lifecycle Manager node in the
/etc/ssl/certs/directory. The filename should match the node name of your primary controller node. For example:/etc/ssl/certs/ardana-stack1-cp1-core-m1.pemDownload this file and provide it as the system-wide certificate.The CPI configuration settings match the values provided via the
caasp-environment.yamlorcaasp-multi-master-environment.yamlfiles. Verify that they are correct before proceeding.
33.7 Register SUSE CaaS Platform Cluster for Software Updates #
Software updates are published for all registered users of SUSE CaaS Platform, and should always be enabled upon deploying a new cluster.
These steps may be performed on cluster nodes one at a time, or in parallel,
making SSH connections as the root user with the password
that was established in your
/usr/share/caasp-openstack-heat-templates/caasp-environment.yaml file.
If using a private SMT server for registration, use its hostname or IP
address when running the commands below. Otherwise, use
scc.suse.com to connect to SUSE's public registration
server.
If this node was previously registered, deactivate its current registration:
tux >sudo SUSEConnect -dtux >sudo SUSEConnect --cleanupIf you are registering with a private SMT server, install its SSL certificate or the related organizational CA in order to perform SMT operations securely.
tux >sudo curl SMT_SERVER/smt.crt \ -o /etc/pki/trust/anchors/registration-server.pemtux >sudo update-ca-certificatesEstablish the new system registration:
tux >sudo SUSEConnect --write-config --url https://SMT_SERVER \ -r REGISTRATION_CODE -e EMAIL_ADDRESSThe same registration code may be used for all the nodes in your cluster.
Test the registration and look for a status of
Registered.tux >sudo SUSEConnect --status-text
34 Installing SUSE CaaS Platform v4 using terraform #
34.1 CaaSP v4 deployment on SOC using terraform. #
More information about the SUSE CaaS Platform v4 is available at https://documentation.suse.com/suse-caasp/4.0/html/caasp-deployment/_deployment_instructions.html#_deployment_on_suse_openstack_cloud
For SOC deployments that support Octavia, set export OS_USE_OCTAVIA=true in the downloaded openstack rc file in order for the load balancing API requests to the octavia service instead of the networking service.
35 Integrations #
Once you have completed your cloud installation, these are some of the common integrations you may want to perform.
35.1 Configuring for 3PAR Block Storage Backend #
This page describes how to configure your 3PAR backend for the SUSE OpenStack Cloud Entry-scale with KVM cloud model.
35.1.1 Prerequisites #
You must have the license for the following software before you start your 3PAR backend configuration for the SUSE OpenStack Cloud Entry-scale with KVM cloud model:
Thin Provisioning
Virtual Copy
System Reporter
Dynamic Optimization
Priority Optimization
Your SUSE OpenStack Cloud Entry-scale KVM Cloud should be up and running. Installation steps can be found in Chapter 24, Installing Mid-scale and Entry-scale KVM.
Your 3PAR Storage Array should be available in the cloud management network or routed to the cloud management network and the 3PAR FC and iSCSI ports configured.
The 3PAR management IP and iSCSI port IPs must have connectivity from the controller and compute nodes.
Please refer to the system requirements for 3PAR in the OpenStack configuration guide, which can be found here: 3PAR System Requirements.
35.1.2 Notes #
The cinder_admin role must be added in order to configure
3Par ICSI as a volume type in horizon.
ardana >source ~/service.osrcardana >openstack role add --user admin --project admin cinder_admin
Encrypted 3Par Volume: Attaching an
encrypted 3Par volume is possible after installation by setting
volume_use_multipath = true under the libvirt stanza in
the nova/kvm-hypervisor.conf.j2 file and reconfigure
nova.
Concerning using multiple backends: If you
are using multiple backend options, ensure that you specify each of the
backends you are using when configuring your
cinder.conf.j2 file using a comma-delimited list.
Also create multiple volume types so you can specify a backend to utilize
when creating volumes. Instructions are included below.
You can also read the OpenStack documentation about cinder
multiple storage backends.
Concerning iSCSI and Fiber Channel: You should not configure cinder backends so that multipath volumes are exported over both iSCSI and Fiber Channel from a 3PAR backend to the same nova compute server.
3PAR driver correct name: In a previous
release, the 3PAR driver used for SUSE OpenStack Cloud integration had its name
updated from HP3PARFCDriver and
HP3PARISCSIDriver to HPE3PARFCDriver
and HPE3PARISCSIDriver respectively
(HP changed to HPE). You may get a
warning or an error if the deprecated filenames are used. The correct values
are those in
~/openstack/my_cloud/config/cinder/cinder.conf.j2.
35.1.3 Multipath Support #
If multipath functionality is enabled, ensure that all 3PAR fibre channel ports are active and zoned correctly in the 3PAR storage.
We recommend setting up multipath support for 3PAR FC/iSCSI as a default
best practice. For instructions on this process, refer to the
~/openstack/ardana/ansible/roles/multipath/README.md
file on the Cloud Lifecycle Manager. The README.md file contains
detailed procedures for configuring multipath for 3PAR FC/iSCSI cinder
volumes.
The following steps are also required to enable 3PAR FC/iSCSI multipath support in the OpenStack configuration files:
Log in to the Cloud Lifecycle Manager.
Edit the
~/openstack/my_cloud/config/nova/kvm-hypervisor.conf.j2file and add this line under the[libvirt]section:Example:
[libvirt] ... iscsi_use_multipath=true
If you plan to attach encrypted 3PAR volumes, also set
volume_use_multipath=truein the same section.Edit the file
~/openstack/my_cloud/config/cinder/cinder.conf.j2and add the following lines in the[3par]section:Example:
[3par] ... enforce_multipath_for_image_xfer=True use_multipath_for_image_xfer=True
Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
cd ~/openstack/ardana/ansible git add -A git commit -m "My config or other commit message"
Run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
Use the playbook below to create a deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
Run the nova reconfigure playbook:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts nova-reconfigure.yml
35.1.4 Configure 3PAR FC as a Cinder Backend #
You must modify the cinder.conf.j2 file
to configure the FC details.
Perform the following steps to configure 3PAR FC as cinder backend:
Log in to Cloud Lifecycle Manager.
Make the following changes to the
~/openstack/my_cloud/config/cinder/cinder.conf.j2file:Add your 3PAR backend to the
enabled_backendssection:# Configure the enabled backends enabled_backends=3par_FC
If you are using multiple backend types, you can use a comma-delimited list.
- Important
A
default_volume_typeis required.Use one or the other of the following alternatives as the
volume typeto specify as thedefault_volume_type.Use a volume type (YOUR VOLUME TYPE) that has already been created to meet the needs of your environment (see Book “Operations Guide CLM”, Chapter 8 “Managing Block Storage”, Section 8.1 “Managing Block Storage using Cinder”, Section 8.1.2 “Creating a Volume Type for your Volumes”).
You can create an empty
volume typecalleddefault_typewith the following:ardana >openstack volume type create --is-public True \ --description "Default volume type" default_type
In
cinder.conf.j2, setdefault_volume_typewith one or the other of the following:[DEFAULT] # Set the default volume type default_volume_type = default_type
[DEFAULT] # Set the default volume type default_volume_type = YOUR VOLUME TYPE
Uncomment the
StoreServ (3par) iscsi clustersection and fill the values per your cluster information. Storage performance can be improved by enabling theImage-Volumecache. Here is an example:[3par_FC] san_ip: <3par-san-ipaddr> san_login: <3par-san-username> san_password: <3par-san-password> hpe3par_username: <3par-username> hpe3par_password: <hpe3par_password> hpe3par_api_url: https://<3par-san-ipaddr>:8080/api/v1 hpe3par_cpg: <3par-cpg-name-1>[,<3par-cpg-name-2>, ...] volume_backend_name: <3par-backend-name> volume_driver = cinder.volume.drivers.hpe.hpe_3par_iscsi.HPE3PARISCSIDriver image_volume_cache_enabled = True
ImportantDo not use
backend_hostvariable incinder.conf.j2file. Ifbackend_hostis set, it will override the [DEFAULT]/host value which SUSE OpenStack Cloud 9 is dependent on.Commit your configuration to the local git repo (Chapter 22, Using Git for Configuration Management), as follows:
cd ~/openstack/ardana/ansible git add -A git commit -m "My config or other commit message"
Run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
Update your deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
Run the following playbook to complete the configuration:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts cinder-reconfigure.yml
35.1.5 Configure 3PAR iSCSI as Cinder backend #
You must modify the cinder.conf.j2 to configure the iSCSI
details.
Perform the following steps to configure 3PAR iSCSI as cinder backend:
Log in to Cloud Lifecycle Manager.
Make the following changes to the
~/openstack/my_cloud/config/cinder/cinder.conf.j2file:Add your 3PAR backend to the
enabled_backendssection:# Configure the enabled backends enabled_backends=3par_iSCSI
Uncomment the
StoreServ (3par) iscsi clustersection and fill the values per your cluster information. Here is an example:[3par_iSCSI] san_ip: <3par-san-ipaddr> san_login: <3par-san-username> san_password: <3par-san-password> hpe3par_username: <3par-username> hpe3par_password: <hpe3par_password> hpe3par_api_url: https://<3par-san-ipaddr>:8080/api/v1 hpe3par_cpg: <3par-cpg-name-1>[,<3par-cpg-name-2>, ...] volume_backend_name: <3par-backend-name> volume_driver: cinder.volume.drivers.san.hp.hp_3par_iscsi.hpe3parISCSIDriver hpe3par_iscsi_ips: <3par-ip-address-1>[,<3par-ip-address-2>,<3par-ip-address-3>, ...] hpe3par_iscsi_chap_enabled=true
ImportantDo not use
backend_hostvariable incinder.conffile. Ifbackend_hostis set, it will override the [DEFAULT]/host value which SUSE OpenStack Cloud 9 is dependent on.
Commit your configuration your local git repository:
cd ~/openstack/ardana/ansible git add -A git commit -m "<commit message>"
Run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
When you run the configuration processor you will be prompted for two passwords. Enter the first password to make the configuration processor encrypt its sensitive data, which consists of the random inter-service passwords that it generates and the Ansible group_vars and host_vars that it produces for subsequent deploy runs. You will need this key for subsequent Ansible deploy runs and subsequent configuration processor runs. If you wish to change an encryption password that you have already used when running the configuration processor then enter the new password at the second prompt, otherwise press Enter.
For CI purposes you can specify the required passwords on the ansible command line. For example, the command below will disable encryption by the configuration processor
ansible-playbook -i hosts/localhost config-processor-run.yml \ -e encrypt="" -e rekey=""
If you receive an error during either of these steps then there is an issue with one or more of your configuration files. We recommend that you verify that all of the information in each of your configuration files is correct for your environment and then commit those changes to git using the instructions above.
Run the following command to create a deployment directory.
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
Run the following command to complete the configuration:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts cinder-reconfigure.yml
35.1.6 Post-Installation Tasks #
After configuring 3PAR as your Block Storage backend, perform the following tasks:
Book “Operations Guide CLM”, Chapter 8 “Managing Block Storage”, Section 8.1 “Managing Block Storage using Cinder”, Section 8.1.2 “Creating a Volume Type for your Volumes”
35.2 Ironic HPE OneView Integration #
SUSE OpenStack Cloud 9 supports integration of ironic (Baremetal) service with HPE OneView using agent_pxe_oneview driver. Please refer to OpenStack Documentation for more information.
35.2.1 Prerequisites #
Installed SUSE OpenStack Cloud 9 with entry-scale-ironic-flat-network or entry-scale-ironic-multi-tenancy model.
HPE OneView 3.0 instance is running and connected to management network.
HPE OneView configuration is set into
definition/data/ironic/ironic_config.yml(andironic-reconfigure.ymlplaybook ran if needed). This should enable agent_pxe_oneview driver in ironic conductor.Managed node(s) should support PXE booting in legacy BIOS mode.
Managed node(s) should have PXE boot NIC listed first. That is, embedded 1Gb NIC must be disabled (otherwise it always goes first).
35.2.2 Integrating with HPE OneView #
On the Cloud Lifecycle Manager, open the file
~/openstack/my_cloud/definition/data/ironic/ironic_config.yml~$ cd ~/openstack vi my_cloud/definition/data/ironic/ironic_config.yml
Modify the settings listed below:
enable_oneview: should be set to "true" for HPE OneView integrationoneview_manager_url: HTTPS endpoint of HPE OneView management interface, for example: https://10.0.0.10/oneview_username: HPE OneView username, for example: Administratoroneview_encrypted_password: HPE OneView password in encrypted or clear text form. The encrypted form is distinguished by presence of@ardana@at the beginning of the string. The encrypted form can be created by running theardanaencrypt.pyprogram. This program is shipped as part of SUSE OpenStack Cloud and can be found in~/openstack/ardana/ansibledirectory on Cloud Lifecycle Manager.oneview_allow_insecure_connections: should be set to "true" if HPE OneView is using self-generated certificate.
Once you have saved your changes and exited the editor, add files, commit changes to local git repository, and run
config-processor-run.ymlandready-deployment.ymlplaybooks, as described in Chapter 22, Using Git for Configuration Management.~/openstack$ git add my_cloud/definition/data/ironic/ironic_config.yml ~/openstack$ cd ardana/ansible ~/openstack/ardana/ansible$ ansible-playbook -i hosts/localhost \ config-processor-run.yml ... ~/openstack/ardana/ansible$ ansible-playbook -i hosts/localhost \ ready-deployment.yml
Run ironic-reconfigure.yml playbook.
$ cd ~/scratch/ansible/next/ardana/ansible/ # This is needed if password was encrypted in ironic_config.yml file ~/scratch/ansible/next/ardana/ansible$ export ARDANA_USER_PASSWORD_ENCRYPT_KEY=your_password_encrypt_key ~/scratch/ansible/next/ardana/ansible$ ansible-playbook -i hosts/verb_hosts ironic-reconfigure.yml ...
35.2.3 Registering Node in HPE OneView #
In the HPE OneView web interface:
Navigate to › . Add new item, using managed node IPMI IP and credentials. If this is the first node of this type being added, corresponding will be created automatically.
Navigate to › . Add . Use corresponding to node being registered. In section, set and options must be turned on:
Verify that node is powered off. Power the node off if needed.
35.2.4 Provisioning ironic Node #
Login to the Cloud Lifecycle Manager and source respective credentials file (for example
service.osrcfor admin account).Review glance images with
openstack image list$ openstack image list +--------------------------------------+--------------------------+ | ID | Name | +--------------------------------------+--------------------------+ | c61da588-622c-4285-878f-7b86d87772da | cirros-0.3.4-x86_64 | +--------------------------------------+--------------------------+
ironic deploy images (boot image,
ir-deploy-kernel,ir-deploy-ramdisk,ir-deploy-iso) are created automatically. Theagent_pxe_oneviewironic driver requiresir-deploy-kernelandir-deploy-ramdiskimages.Create node using
agent_pxe_oneviewdriver.$ ironic --ironic-api-version 1.22 node-create -d agent_pxe_oneview --name test-node-1 \ --network-interface neutron -p memory_mb=131072 -p cpu_arch=x86_64 -p local_gb=80 -p cpus=2 \ -p 'capabilities=boot_mode:bios,boot_option:local,server_hardware_type_uri:\ /rest/server-hardware-types/E5366BF8-7CBF-48DF-A752-8670CF780BB2,server_profile_template_uri:\ /rest/server-profile-templates/00614918-77f8-4146-a8b8-9fc276cd6ab2' \ -i 'server_hardware_uri=/rest/server-hardware/32353537-3835-584D-5135-313930373046' \ -i dynamic_allocation=True \ -i deploy_kernel=633d379d-e076-47e6-b56d-582b5b977683 \ -i deploy_ramdisk=d5828785-edf2-49fa-8de2-3ddb7f3270d5 +-------------------+--------------------------------------------------------------------------+ | Property | Value | +-------------------+--------------------------------------------------------------------------+ | chassis_uuid | | | driver | agent_pxe_oneview | | driver_info | {u'server_hardware_uri': u'/rest/server- | | | hardware/32353537-3835-584D-5135-313930373046', u'dynamic_allocation': | | | u'True', u'deploy_ramdisk': u'd5828785-edf2-49fa-8de2-3ddb7f3270d5', | | | u'deploy_kernel': u'633d379d-e076-47e6-b56d-582b5b977683'} | | extra | {} | | name | test-node-1 | | network_interface | neutron | | properties | {u'memory_mb': 131072, u'cpu_arch': u'x86_64', u'local_gb': 80, u'cpus': | | | 2, u'capabilities': | | | u'boot_mode:bios,boot_option:local,server_hardware_type_uri:/rest | | | /server-hardware-types/E5366BF8-7CBF- | | | 48DF-A752-8670CF780BB2,server_profile_template_uri:/rest/server-profile- | | | templates/00614918-77f8-4146-a8b8-9fc276cd6ab2'} | | resource_class | None | | uuid | c202309c-97e2-4c90-8ae3-d4c95afdaf06 | +-------------------+--------------------------------------------------------------------------+NoteFor deployments created via ironic/HPE OneView integration,
memory_mbproperty must reflect physical amount of RAM installed in the managed node. That is, for a server with 128 Gb of RAM it works out to 132*1024=13072.Boot mode in capabilities property must reflect boot mode used by the server, that is 'bios' for Legacy BIOS and 'uefi' for UEFI.
Values for
server_hardware_type_uri,server_profile_template_uriandserver_hardware_urican be grabbed from browser URL field while navigating to respective objects in HPE OneView UI. URI corresponds to the part of URL which starts form the token/rest. That is, the URLhttps://oneview.mycorp.net/#/profile-templates/show/overview/r/rest/server-profile-templates/12345678-90ab-cdef-0123-012345678901corresponds to the URI/rest/server-profile-templates/12345678-90ab-cdef-0123-012345678901.Grab IDs of
deploy_kernelanddeploy_ramdiskfrom openstack image list output above.
Create port.
$ ironic --ironic-api-version 1.22 port-create \ --address aa:bb:cc:dd:ee:ff \ --node c202309c-97e2-4c90-8ae3-d4c95afdaf06 \ -l switch_id=ff:ee:dd:cc:bb:aa \ -l switch_info=MY_SWITCH \ -l port_id="Ten-GigabitEthernet 1/0/1" \ --pxe-enabled true +-----------------------+----------------------------------------------------------------+ | Property | Value | +-----------------------+----------------------------------------------------------------+ | address | 8c:dc:d4:b5:7d:1c | | extra | {} | | local_link_connection | {u'switch_info': u'C20DATA', u'port_id': u'Ten-GigabitEthernet | | | 1/0/1', u'switch_id': u'ff:ee:dd:cc:bb:aa'} | | node_uuid | c202309c-97e2-4c90-8ae3-d4c95afdaf06 | | pxe_enabled | True | | uuid | 75b150ef-8220-4e97-ac62-d15548dc8ebe | +-----------------------+----------------------------------------------------------------+Warningironic Multi-Tenancy networking model is used in this example. Therefore, ironic port-create command contains information about the physical switch. HPE OneView integration can also be performed using the ironic Flat Networking model. For more information, see Section 9.6, “Ironic Examples”.
Move node to manageable provisioning state. The connectivity between ironic and HPE OneView will be verified, Server Hardware Template settings validated, and Server Hardware power status retrieved from HPE OneView and set into the ironic node.
$ ironic node-set-provision-state test-node-1 manage
Verify that node power status is populated.
$ ironic node-show test-node-1 +-----------------------+-----------------------------------------------------------------------+ | Property | Value | +-----------------------+-----------------------------------------------------------------------+ | chassis_uuid | | | clean_step | {} | | console_enabled | False | | created_at | 2017-06-30T21:00:26+00:00 | | driver | agent_pxe_oneview | | driver_info | {u'server_hardware_uri': u'/rest/server- | | | hardware/32353537-3835-584D-5135-313930373046', u'dynamic_allocation':| | | u'True', u'deploy_ramdisk': u'd5828785-edf2-49fa-8de2-3ddb7f3270d5', | | | u'deploy_kernel': u'633d379d-e076-47e6-b56d-582b5b977683'} | | driver_internal_info | {} | | extra | {} | | inspection_finished_at| None | | inspection_started_at | None | | instance_info | {} | | instance_uuid | None | | last_error | None | | maintenance | False | | maintenance_reason | None | | name | test-node-1 | | network_interface | | | power_state | power off | | properties | {u'memory_mb': 131072, u'cpu_arch': u'x86_64', u'local_gb': 80, | | | u'cpus': 2, u'capabilities': | | | u'boot_mode:bios,boot_option:local,server_hardware_type_uri:/rest | | | /server-hardware-types/E5366BF8-7CBF- | | | 48DF-A752-86...BB2,server_profile_template_uri:/rest/server-profile- | | | templates/00614918-77f8-4146-a8b8-9fc276cd6ab2'} | | provision_state | manageable | | provision_updated_at | 2017-06-30T21:04:43+00:00 | | raid_config | | | reservation | None | | resource_class | | | target_power_state | None | | target_provision_state| None | | target_raid_config | | | updated_at | 2017-06-30T21:04:43+00:00 | | uuid | c202309c-97e2-4c90-8ae3-d4c95afdaf06 | +-----------------------+-----------------------------------------------------------------------+Move node to available provisioning state. The ironic node will be reported to nova as available.
$ ironic node-set-provision-state test-node-1 provide
Verify that node resources were added to nova hypervisor stats.
$ openstack hypervisor stats show +----------------------+--------+ | Property | Value | +----------------------+--------+ | count | 1 | | current_workload | 0 | | disk_available_least | 80 | | free_disk_gb | 80 | | free_ram_mb | 131072 | | local_gb | 80 | | local_gb_used | 0 | | memory_mb | 131072 | | memory_mb_used | 0 | | running_vms | 0 | | vcpus | 2 | | vcpus_used | 0 | +----------------------+--------+
Create nova flavor.
$ openstack flavor create m1.ironic auto 131072 80 2 +-------------+-----------+--------+------+-----------+------+-------+-------------+-----------+ | ID | Name | Mem_MB | Disk | Ephemeral | Swap | VCPUs | RXTX_Factor | Is_Public | +-------------+-----------+--------+------+-----------+------+-------+-------------+-----------+ | 33c8...f8d8 | m1.ironic | 131072 | 80 | 0 | | 2 | 1.0 | True | +-------------+-----------+--------+------+-----------+------+-------+-------------+-----------+ $ openstack flavor set m1.ironic set capabilities:boot_mode="bios" $ openstack flavor set m1.ironic set capabilities:boot_option="local" $ openstack flavor set m1.ironic set cpu_arch=x86_64
NoteAll parameters (specifically, amount of RAM and boot mode) must correspond to ironic node parameters.
Create nova keypair if needed.
$ openstack keypair create ironic_kp --pub-key ~/.ssh/id_rsa.pub
Boot nova instance.
$ openstack server create --flavor m1.ironic --image d6b5...e942 --key-name ironic_kp \ --nic net-id=5f36...dcf3 test-node-1 +-------------------------------+-----------------------------------------------------+ | Property | Value | +-------------------------------+-----------------------------------------------------+ | OS-DCF:diskConfig | MANUAL | | OS-EXT-AZ:availability_zone | | | OS-EXT-SRV-ATTR:host | - | | OS-EXT-SRV-ATTR: | | | hypervisor_hostname | - | | OS-EXT-SRV-ATTR:instance_name | | | OS-EXT-STS:power_state | 0 | | OS-EXT-STS:task_state | scheduling | | OS-EXT-STS:vm_state | building | | OS-SRV-USG:launched_at | - | | OS-SRV-USG:terminated_at | - | | accessIPv4 | | | accessIPv6 | | | adminPass | pE3m7wRACvYy | | config_drive | | | created | 2017-06-30T21:08:42Z | | flavor | m1.ironic (33c81884-b8aa-46...3b72f8d8) | | hostId | | | id | b47c9f2a-e88e-411a-abcd-6172aea45397 | | image | Ubuntu Trusty 14.04 BIOS (d6b5d971-42...5f2d88e942) | | key_name | ironic_kp | | metadata | {} | | name | test-node-1 | | os-extended-volumes: | | | volumes_attached | [] | | progress | 0 | | security_groups | default | | status | BUILD | | tenant_id | c8573f7026d24093b40c769ca238fddc | | updated | 2017-06-30T21:08:42Z | | user_id | 2eae99221545466d8f175eeb566cc1b4 | +-------------------------------+-----------------------------------------------------+During nova instance boot, the following operations will be performed by ironic via HPE OneView REST API.
In HPE OneView, new Server Profile is generated for specified Server Hardware, using specified Server Profile Template. Boot order in Server Profile is set to list PXE as the first boot source.
The managed node is powered on and boots IPA image from PXE.
IPA image writes user image onto disk and reports success back to ironic.
ironic modifies Server Profile in HPE OneView to list 'Disk' as default boot option.
ironic reboots the node (via HPE OneView REST API call).
35.3 SUSE Enterprise Storage Integration #
The current version of SUSE OpenStack Cloud supports integration with SUSE Enterprise Storage (SES). Integrating SUSE Enterprise Storage enables Ceph to provide RADOS Block Device (RBD), block storage, image storage, object storage via RADOS Gateway (RGW), and CephFS (file storage) in SUSE OpenStack Cloud. The following documentation outlines integration for SUSE Enterprise Storage 5 , 5.5, 6.0, and 7.0.
Support for SUSE Enterprise Storage 5 and 5.5 is deprecated. The documentation for integrating these versions is included for customers who may not yet have upgraded to newer versions of SUSE Enterprise Storage . These versions are no longer officially supported.
Integration with SUSE Enterprise Storage 5.5 is configured using the same
steps as SUSE Enterprise Storage 6.0 except that salt-api queries authenticating with the
password= parameter should be updated to use
sharedsecret=
SUSE Enterprise Storage 6.0 uses a Salt runner that creates users and pools. Salt generates a yaml configuration that is needed to integrate with SUSE OpenStack Cloud. The integration runner creates separate users for cinder, cinder backup, and glance. Both the cinder and nova services have the same user, as cinder needs access to create objects that nova uses.
SUSE Enterprise Storage 5 uses a manual configuration that requires the creation of users and pools.
For more information on SUSE Enterprise Storage, see the https://documentation.suse.com/ses/6.
35.3.1 Enabling SUSE Enterprise Storage 7.0 Integration #
The following instructions detail integrating SUSE Enterprise Storage 7.0 with SUSE OpenStack Cloud.
Create the osd pools on the SUSE Enterprise Storage admin node (the names provided here are examples)
ceph osd pool create ses-cloud-volumes 16 && \ ceph osd pool create ses-cloud-backups 16 && \ ceph osd pool create ses-cloud-images 16 &&\ ceph osd pool create ses-cloud-vms 16
Enable the osd pools
ceph osd pool application enable ses-cloud-volumes rbd && \ ceph osd pool application enable ses-cloud-backups rbd && \ ceph osd pool application enable ses-cloud-images rbd && \ ceph osd pool application enable ses-cloud-vms rbd
Configure permissions on the SUSE OpenStack Cloud deployer
ceph-authtool -C /etc/ceph/ceph.client.ses-cinder.keyring --name client.ses-cinder --add-key $(ceph-authtool --gen-print-key) --cap mon "allow r" --cap osd "allow class-read object_prefix rbd_children, allow rwx pool=ses-cloud-volumes, allow rwx pool=ses-cloud-vms, allow rwx pool=ses-cloud-images" ceph-authtool -C /etc/ceph/ceph.client.ses-cinder-backup.keyring --name client.ses-cinder-backup --add-key $(ceph-authtool --gen-print-key) --cap mon "allow r" --cap osd "allow class-read object_prefix rbd_children, allow rwx pool=ses-cloud-cinder-backups" ceph-authtool -C /etc/ceph/ceph.client.ses-glance.keyring --name client.ses-glance --add-key $(ceph-authtool --gen-print-key) --cap mon "allow r" --cap osd "allow class-read object_prefix rbd_children, allow rwx pool=ses-cloud-images"
Import the updated keyrings into Ceph
ceph auth import -i /etc/ceph/ceph.client.ses-cinder-backup.keyring && \ ceph auth import -i /etc/ceph/ceph.client.ses-cinder.keyring && \ ceph auth import -i /etc/ceph/ceph.client.ses-glance.keyring
35.3.2 Enabling SUSE Enterprise Storage 6.0 Integration #
The following instructions detail integrating SUSE Enterprise Storage 6.0 & 5.5 with SUSE OpenStack Cloud.
Log in as root to run the SES 6 Salt runner on the salt admin host:
If no prefix is specified (as the below command shows), by default
pool names are prefixed with cloud- and are more
generic.
root # salt-run --out=yaml openstack.integrateceph_conf: cluster_network: 10.84.56.0/21 fsid: d5d7c7cb-5858-3218-a36f-d028df7b0673 mon_host: 10.84.56.8, 10.84.56.9, 10.84.56.7 mon_initial_members: ses-osd1, ses-osd2, ses-osd3 public_network: 10.84.56.0/21 cinder: key: AQBI5/xcAAAAABAAFP7ES4gl5tZ9qdLd611AmQ== rbd_store_pool: cloud-volumes rbd_store_user: cinder cinder-backup: key: AQBI5/xcAAAAABAAVSZmfeuPl3KFvJetCygUmA== rbd_store_pool: cloud-backups rbd_store_user: cinder-backup glance: key: AQBI5/xcAAAAABAALHgkBxARTZAeuoIWDsC0LA== rbd_store_pool: cloud-images rbd_store_user: glance nova: rbd_store_pool: cloud-vms radosgw_urls: - http://10.84.56.7:80/swift/v1 - http://10.84.56.8:80/swift/v1
If you perform the command with a prefix, the prefix is applied to pool names and to key names. This way, multiple cloud deployments can use different users and pools on the same SES deployment.
root # salt-run --out=yaml openstack.integrate prefix=mycloudceph_conf: cluster_network: 10.84.56.0/21 fsid: d5d7c7cb-5858-3218-a36f-d028df7b0673 mon_host: 10.84.56.8, 10.84.56.9, 10.84.56.7 mon_initial_members: ses-osd1, ses-osd2, ses-osd3 public_network: 10.84.56.0/21 cinder: key: AQAM5fxcAAAAABAAIyMeLwclr+5uegp33xdiIw== rbd_store_pool: mycloud-cloud-volumes rbd_store_user: mycloud-cinder cinder-backup: key: AQAM5fxcAAAAABAAq6ZqKuMNaaJgk6OtFHMnsQ== rbd_store_pool: mycloud-cloud-backups rbd_store_user: mycloud-cinder-backup glance: key: AQAM5fxcAAAAABAAvhJjxC81IePAtnkye+bLoQ== rbd_store_pool: mycloud-cloud-images rbd_store_user: mycloud-glance nova: rbd_store_pool: mycloud-cloud-vms radosgw_urls: - http://10.84.56.7:80/swift/v1 - http://10.84.56.8:80/swift/v1
35.3.3 Enabling SUSE Enterprise Storage 7, 6, 5 Integration #
The following instructions detail integrating SUSE Enterprise Storage 7, 6, 5 with SUSE OpenStack Cloud.
The SUSE Enterprise Storage integration is provided through the ardana-ses
RPM package. This package is included in the
patterns-cloud-ardana pattern and the installation is
covered in Chapter 15, Installing the Cloud Lifecycle Manager server. The update repositories and
the installation covered there are required to support SUSE Enterprise Storage
integration. The latest updates should be applied before proceeding.
After the SUSE Enterprise Storage integration package has been installed, it must be
configured. Files that contain relevant SUSE Enterprise Storage deployment information
must be placed into a directory on the deployer node. This includes the
configuration file that describes various aspects of the Ceph environment
as well as keyrings for each user and pool created in the Ceph
environment. In addition to that, you need to edit the
settings.yml file to enable the SUSE Enterprise Storage integration to
run and update all of the SUSE OpenStack Cloud service configuration files.
The settings.yml file must reside in the
~/openstack/my_cloud/config/ses/ directory. Open the
file for editing, uncomment the ses_config_path:
parameter, and specify the location on the deployer host containing the
ses_config.yml and keyring files as the parameter's
value. After you have done that, the site.yml and
ardana-reconfigure.yml playbooks activate and configure
the cinder, glance, and nova
services.
For security reasons, you should use a unique UUID in the
settings.yml file for
ses_secret_id, replacing the fixed, hard-coded UUID in
that file. You can generate a UUID that is unique to your deployment
using the command uuidgen.
After you have run the openstack.integrate runner, copy
the yaml into the ses_config.yml file on the deployer
node. Then edit the settings.yml file to enable SUSE Enterprise Storage
integration to run and update all of the SUSE OpenStack Cloud service configuration
files. The settings.yml file resides in the
~/openstack/my_cloud/config/ses directory. Open the
settings.yml file for editing, uncomment the
ses_config_path: parameter, and specify the location on
the deployer host containing the ses_config.yml file.
If you are integrating with SUSE Enterprise Storage and want to store nova images in Ceph, then set the following:
ses_nova_set_images_type: True
If you not want to store nova images in Ceph, the following setting is required:
ses_nova_set_images_type: False
Commit your configuration to your local git repo:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "add SES integration"Run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun a series of reconfiguration playbooks:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ses-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts cinder-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts glance-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts nova-reconfigure.ymlReconfigure the Cloud Lifecycle Manager to complete the deployment:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.yml
In the control_plane.yml file, the glance
default_store option must be adjusted.
- glance-api:
glance_default_store: 'rbd'The following content is only relevant if you are running a standalone Ceph cluster (not SUSE Enterprise Storage) or a SUSE Enterprise Storage cluster that is before version 5.5.
For Ceph, it is necessary to create pools and users to allow the SUSE OpenStack Cloud services to use the SUSE Enterprise Storage/Ceph cluster. Pools and users must be created for cinder, cinder backup, nova and glance. Instructions for creating and managing pools, users and keyrings is covered in the SUSE Enterprise Storage documentation under https://documentation.suse.com/en-us/ses/5.5/single-html/ses-admin/#storage-cephx-keymgmt.
After the required pools and users are set up on the Ceph
cluster, you have to create a ses_config.yml
configuration file (see the example below). This file is used during
deployment to configure all of the services. The
ses_config.yml and the keyring files should be placed
in a separate directory.
If you are integrating with SUSE Enterprise Storage and do not want to store nova images in Ceph, the following setting is required:
Edit settings.yml and change the line
ses_nova_set_images_type: True
to ses_nova_set_images_type: False
ses_cluster_configuration:
ses_cluster_name: ceph
ses_radosgw_url: "https://192.168.56.8:8080/swift/v1"
conf_options:
ses_fsid: d5d7c7cb-5858-3218-a36f-d028df7b1111
ses_mon_initial_members: ses-osd2, ses-osd3, ses-osd1
ses_mon_host: 192.168.56.8, 192.168.56.9, 192.168.56.7
ses_public_network: 192.168.56.0/21
ses_cluster_network: 192.168.56.0/21
cinder:
rbd_store_pool: cinder
rbd_store_pool_user: cinder
keyring_file_name: ceph.client.cinder.keyring
cinder-backup:
rbd_store_pool: backups
rbd_store_pool_user: cinder_backup
keyring_file_name: ceph.client.cinder-backup.keyring
# nova uses the cinder user to access the nova pool, cinder pool
# So all we need here is the nova pool name.
nova:
rbd_store_pool: nova
glance:
rbd_store_pool: glance
rbd_store_pool_user: glance
keyring_file_name: ceph.client.glance.keyring
The path to this directory must be specified in the
settings.yml file, as in the example below. After
making the changes, follow the steps to complete the configuration.
settings.yml ... ses_config_path: /var/lib/ardana/ses/ ses_config_file: ses_config.yml # The unique uuid for use with virsh for cinder and nova ses_secret_id: SES_SECRET_ID
After modifying these files, commit your configuration to the local git repo. For more information, see Chapter 22, Using Git for Configuration Management.
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "configure SES 5"Run the configuration processor:
ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory:
ardana >ansible-playbook -i hosts/localhost ready-deployment.ymlReconfigure Ardana:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.yml
When configuring SUSE Enterprise Storage integration, be aware of CVE-2021-20288 relating to Unauthorized global_id re-use.
35.3.4 Add Missing Swift Endpoints #
If you deployed Cloud Lifecycle Manager using the SUSE Enterprise Storage integration without swift, the integration will not be set up properly. Swift object endpoints will be missing. Use the following process to create the necessary endpoints.
Source the keystone
rcfile to have the correct permissions to create the swift service and endpoints.ardana >. ~/keystone.osrcCreate the swift service.
ardana >openstack service create --name swift object-store --enableRead the RADOS gateway URL from the
ses_config.ymlfile. For example:ardana >grep http ~/ses/ses_config.yml https://ses-osd3:8080/swift/v1Create the three swift endpoints.
ardana >openstack endpoint create --enable --region region1 swift \ admin https://ses-osd3:8080/swift/v1ardana >openstack endpoint create --enable --region region1 swift \ public https://ses-osd3:8080/swift/v1ardana >openstack endpoint create --enable --region region1 swift \ internal https://ses-osd3:8080/swift/v1Verify the objects in the endpoint list.
ardana >openstack endpoint list | grep object 5313b...e9412f region1 swift object-store True public https://ses-osd3:8080/swift/v1 83faf...1eb602 region1 swift object-store True internal https://ses-osd3:8080/swift/v1 dc698...715b8c region1 swift object-store True admin https://ses-osd3:8080/swift/v1
35.3.5 Configuring SUSE Enterprise Storage for Integration with RADOS Gateway #
RADOS gateway integration can be enabled (disabled) by adding (removing)
the following line in the ses_config.yml:
ses_radosgw_url: "https://192.168.56.8:8080/swift/v1"
If RADOS gateway integration is enabled, additional SUSE Enterprise Storage configuration is
needed. RADOS gateway must be configured to use keystone for
authentication. This is done by adding the configuration statements below
to the rados section of ceph.conf on the RADOS node.
[client.rgw.HOSTNAME] rgw frontends = "civetweb port=80+443s" rgw enable usage log = true rgw keystone url = KEYSTONE_ENDPOINT (for example: https://192.168.24.204:5000) rgw keystone admin user = KEYSTONE_ADMIN_USER rgw keystone admin password = KEYSTONE_ADMIN_PASSWORD rgw keystone admin project = KEYSTONE_ADMIN_PROJECT rgw keystone admin domain = KEYSTONE_ADMIN_DOMAIN rgw keystone api version = 3 rgw keystone accepted roles = admin,member rgw keystone accepted admin roles = admin rgw keystone revocation interval = 0 rgw keystone verify ssl = false # If keystone is using self-signed certificate
When integrating with SUSE Enterprise Storage 7, the ceph.conf file only contains the minimal setup, the remainder of the configuration data is stored in the Ceph database.
To update the configuration for SUSE Enterprise Storage 7 use the
ceph config CLI. It is possible to import a yaml
formatted configuration as follows
ceph config assimilate-conf -i configuration_file.yml
After making these changes to ceph.conf, (and in the case
of SUSE Enterprise Storage 7 importing the configuration) the RADOS
gateway service needs to be restarted.
Enabling RADOS gateway replaces the existing Object Storage endpoint with the RADOS gateway endpoint.
35.3.6 Enabling HTTPS, Creating and Importing a Certificate #
SUSE Enterprise Storage integration uses the HTTPS protocol to connect to the RADOS gateway. However, with SUSE Enterprise Storage 5, HTTPS is not enabled by default. To enable the gateway role to communicate securely using SSL, you need to either have a CA-issued certificate or create a self-signed one. Instructions for both are available in the SUSE Enterprise Storage documentation.
The certificate needs to be installed on your Cloud Lifecycle Manager. On the Cloud Lifecycle Manager, copy the
cert to /tmp/ardana_tls_cacerts. Then deploy it.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts tls-trust-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts tls-reconfigure.yml
When creating the certificate, the subjectAltName must
match the ses_radosgw_url entry in
ses_config.yml. Either an IP address or FQDN can be
used, but these values must be the same in both places.
35.3.7 Deploying SUSE Enterprise Storage Configuration for RADOS Integration #
The following steps deploy your configuration.
Commit your configuration to your local git repo.
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "add SES integration"Run the configuration processor.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlCreate a deployment directory.
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost ready-deployment.ymlRun a series of reconfiguration playbooks.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ses-deploy.ymlardana >ansible-playbook -i hosts/verb_hosts cinder-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts glance-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts nova-reconfigure.ymlReconfigure the Cloud Lifecycle Manager to complete the deployment.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.yml
35.3.8 Enable Copy-On-Write Cloning of Images #
Due to a security issue described in http://docs.ceph.com/docs/master/rbd/rbd-openstack/?highlight=uuid#enable-copy-on-write-cloning-of-images, we do not recommend the copy-on-write cloning of images when glance and cinder are both using a Ceph back-end. However, if you want to use this feature for faster operation, you can enable it as follows.
Open the
~/openstack/my_cloud/config/glance/glance-api.conf.j2file for editing and addshow_image_direct_url = Trueunder the[DEFAULT]section.Commit changes:
git add -A git commit -m "Enable Copy-on-Write Cloning"
Run the required playbooks:
ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.yml cd /var/lib/ardana/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts glance-reconfigure.yml
Note that this exposes the back-end location via glance's API, so the end-point should not be publicly accessible when Copy-On-Write image cloning is enabled.
35.3.9 Improve SUSE Enterprise Storage Storage Performance #
SUSE Enterprise Storage performance can be improved with Image-Volume cache. Be aware that Image-Volume cache and Copy-on-Write cloning cannot be used for the same storage back-end. For more information, see the OpenStack documentation.
Enable Image-Volume cache with the following steps:
Open the
~/openstack/my_cloud/config/cinder/cinder.conf.j2file for editing.Add
image_volume_cache_enabled = Trueoption under the[ses_ceph]section.Commit changes:
ardana >git add -Aardana >git commit -m "Enable Image-Volume cache"Run the required playbooks:
ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.ymlardana >cd /var/lib/ardana/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts cinder-reconfigure.yml
36 Troubleshooting the Installation #
We have gathered some of the common issues that occur during installation and organized them by when they occur during the installation. These sections will coincide with the steps labeled in the installation instructions.
36.1 Issues during Cloud Lifecycle Manager Setup #
Issue: Running the ardana-init.bash script when configuring your Cloud Lifecycle Manager does not complete#
Part of what the ardana-init.bash script does is
install Git. So if your DNS server(s) is/are not specified in your
/etc/resolv.conf file, is not valid, or is not
functioning properly on your Cloud Lifecycle Manager, it will not be able to
complete.
To resolve this issue, double check your nameserver in your
/etc/resolv.conf file and then re-run the script.
36.2 Issues while Updating Configuration Files #
Configuration Processor Fails Due to Wrong yml Format#
If you receive the error below when running the configuration processor then you may have a formatting error:
TASK: [fail msg="Configuration processor run failed, see log output above for details"]
First you should check the Ansible log in the location below for more details on which yml file in your input model has the error:
~/.ansible/ansible.log
Check the configuration file to locate and fix the error, keeping in mind the following tips below.
Check your files to ensure that they do not contain the following:
Non-ascii characters
Unneeded spaces
Once you have fixed the formatting error in your files, commit the changes with these steps:
Commit your changes to Git:
cd ~/openstack/ardana/ansible git add -A git commit -m "My config or other commit message"
Re-run the configuration processor playbook and confirm the error is not received again.
Configuration processor fails with provider network OCTAVIA-MGMT-NET error#
If you receive the error below when running the configuration processor then you have not correctly configured your VLAN settings for Octavia.
################################################################################, # The configuration processor failed. # config-data-2.0 ERR: Provider network OCTAVIA-MGMT-NET host_routes: # destination '192.168.10.0/24' is not defined as a Network in the input model. # Add 'external: True' to this host_route if this is for an external network. ################################################################################
To resolve the issue, ensure that your settings in
~/openstack/my_cloud/definition/data/neutron/neutron_config.yml
are correct for the VLAN setup for Octavia.
Changes Made to your Configuration Files#
If you have made corrections to your configuration files and need to re-run the Configuration Processor, the only thing you need to do is commit your changes to your local Git repository:
cd ~/openstack/ardana/ansible git add -A git commit -m "commit message"
You can then re-run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
Configuration Processor Fails Because Encryption Key Does Not Meet Requirements#
If you choose to set an encryption password when running the configuration processor, you may receive the following error if the chosen password does not meet the complexity requirements:
################################################################################ # The configuration processor failed. # encryption-key ERR: The Encryption Key does not meet the following requirement(s): # The Encryption Key must be at least 12 characters # The Encryption Key must contain at least 3 of following classes of characters: # Uppercase Letters, Lowercase Letters, Digits, Punctuation ################################################################################
If you receive the above error, run the configuration processor again and select a password that meets the complexity requirements detailed in the error message:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
36.3 Issues while Deploying the Cloud #
Issue: If the site.yml playbook fails, you can query the log for the reason#
Ansible is good about outputting the errors into the command line output, however if you would like to view the full log for any reason the location is:
~/.ansible/ansible.log
This log is updated real time as you run Ansible playbooks.
Use grep to parse through the log. Usage: grep <text>
~/.ansible/ansible.log
Issue: How to Wipe the Disks of your Machines#
If you have re-run the site.yml playbook, you may need to
wipe the disks of your nodes
You should run the wipe_disks.yml playbook only after
re-running the bm-reimage.yml playbook but before you
re-run the site.yml playbook.
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts wipe_disks.yml
The playbook will show you the disks to be wiped in the output and allow you
to confirm that you want to complete this action or abort it if you do not
want to proceed. You can optionally use the --limit
<NODE_NAME> switch on this playbook to restrict it to
specific nodes. This action will not affect the OS partitions on the servers.
If you receive an error stating that osconfig has already
run on your nodes then you will need to remove the
/etc/ardana/osconfig-ran file on each of the nodes you want
to wipe with this command:
sudo rm /etc/ardana/osconfig-ran
That will clear this flag and allow the disk to be wiped.
Error Received if Root Logical Volume is Too Small#
When running the site.yml playbook, you may receive a
message that includes the error below if your root logical volume is too
small. This error needs to be parsed out and resolved.
2015-09-29 15:54:03,022 p=26345 u=stack | stderr: New size given (7128 extents) not larger than existing size (7629 extents)
The error message may also reference the root volume:
"name": "root", "size": "10%"
The problem here is that the root logical volume, as specified in the
disks_controller.yml file, is set to
10% of the overall physical volume and this value is too
small.
To resolve this issue you need to ensure that the percentage is set properly for the size of your logical-volume. The default values in the configuration files is based on a 500 GB disk, so if your logical volumes are smaller you may need to increase the percentage so there is enough room.
Multiple Keystone Failures Received during site.yml#
If you receive the keystone error below during your
site.yml run then follow these steps:
TASK: [OPS-MON | _keystone_conf | Create Ops Console service in keystone] ***** failed: [...] msg: An unexpected error prevented the server from fulfilling your request. (HTTP 500) (Request-ID: req-23a09c72-5991-4685-b09f-df242028d742), failed FATAL: all hosts have already failed -- aborting
The most likely cause of this error is that the virtual IP address is having issues and the keystone API communication through the virtual IP address is not working properly. You will want to check the keystone log on the controller where you will likely see authorization failure errors.
Verify that your virtual IP address is active and listening on the proper port on all of your controllers using this command:
netstat -tplan | grep 35357
Ensure that your Cloud Lifecycle Manager did not pick the wrong (unusable) IP address from the list of IP addresses assigned to your Management network.
The Cloud Lifecycle Manager will take the first available IP address after the
gateway-ip defined in your
~/openstack/my_cloud/definition/data/networks.yml file.
This IP will be used as the virtual IP address for that particular network.
If this IP address is used and reserved for another purpose outside of your
SUSE OpenStack Cloud deployment then you will receive the error above.
To resolve this issue we recommend that you utilize the
start-address and possibly the
end-address (if needed) options in your
networks.yml file to further define which IP addresses
you want your cloud deployment to use. For more information, see
Section 6.14, “Networks”.
After you have made changes to your networks.yml file,
follow these steps to commit the changes:
Ensuring that you stay within the
~/openstackdirectory, commit the changes you just made:cd ~/openstack git commit -a -m "commit message"
Run the configuration processor:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml
Update your deployment directory:
cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost ready-deployment.yml
Re-run the site.yml playbook:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts site.yml
37 Troubleshooting the ESX #
This section contains troubleshooting tasks for your SUSE® OpenStack Cloud 9 for ESX.
37.1 Issue: ardana-service.service is not running #
If you perform any maintenance work or reboot the Cloud Lifecycle Manager/deployer node, make sure to restart the Cloud Lifecycle Manager API service for standalone deployer node and shared Cloud Lifecycle Manager/controller node based on your environment.
For standalone deployer node, execute ardana-start.yml
playbook to restart the Cloud Lifecycle Manager API service on the deployer node after a reboot.
For shared deployer/controller node, execute
ardana-start.yml playbook on all the controllers to
restart Cloud Lifecycle Manager API service.
For example:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ardana-start.yml --limit HOST_NAME
Replace HOST_NAME with the host name of the Cloud Lifecycle Manager node or the Cloud Lifecycle Manager Node/Shared Controller.
37.2 Issue: ESX Cluster shows UNKNOWN in Operations Console #
In the Operations Console Alarms dashboard, if all the alarms for ESX cluster are
showing UNKNOWN then restart the openstack-monasca-agent running in
ESX compute proxy.
SSH to the respective compute proxy. You can find the hostname of the proxy from the dimensions list shown against the respective alarm.
Restart the
openstack-monasca-agentservice.sudo systemctl restart openstack-monasca-agent
37.3 Issue: Unable to view the VM console in Horizon UI #
By default the gdbserver firewall is disabled in ESXi host which results in a Handshake error when accessing the VM instance console in the horizon UI.
Procedure to enable gdbserver
Login to vSphere Client.
Select the ESXi Host and click tab in the menu bar. You must perform the following actions on all the ESXi hosts in the compute clusters.
On the left hand side select Security Profile from the list of Software. Click Properties on the right hand side.
Firewall Properties box displays.
Select gdbserver checkbox and click OK.
Part V Post-Installation #
- 38 Post Installation Tasks
When you have completed your cloud deployment, these are some of the common post-installation tasks you may need to perform to verify your cloud installation.
- 39 UI Verification
Once you have completed your cloud deployment, these are some of the common post-installation tasks you may need to perform to verify your cloud installation.
- 40 Installing OpenStack Clients
If you have a standalone deployer, the OpenStack CLI and other clients will not be installed automatically on that node. If you require access to these clients, you will need to follow the procedure below to add the appropriate software.
- 41 Configuring Transport Layer Security (TLS)
TLS is enabled by default during the installation of SUSE OpenStack Cloud 9 and additional configuration options are available to secure your environment, as described below.
- 42 Configuring Availability Zones
The Cloud Lifecycle Manager only creates a default availability zone during installation. If your system has multiple failure/availability zones defined in your input model, these zones will not get created automatically.
- 43 Configuring Load Balancer as a Service
The SUSE OpenStack Cloud neutron LBaaS service supports several load balancing providers. By default, both Octavia and the namespace HAProxy driver are configured to be used.
- 44 Other Common Post-Installation Tasks
On your Cloud Lifecycle Manager, in the ~/scratch/ansible/next/ardana/ansible/group_vars/ directory you will find several files. In the one labeled as first control plane node you can locate the user credentials for both the Administrator user (admin) and your Demo user (demo) which you will use to …
38 Post Installation Tasks #
When you have completed your cloud deployment, these are some of the common post-installation tasks you may need to perform to verify your cloud installation.
Manually back up /etc/group on the Cloud Lifecycle Manager. It may be
useful for an emergency recovery.
38.1 API Verification #
SUSE OpenStack Cloud 9 provides a tool (Tempest) that you can use to verify that your cloud deployment completed successfully:
38.1.1 Prerequisites #
The verification tests rely on you having an external network setup and a cloud image in your image (glance) repository. Run the following playbook to configure your cloud:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts ardana-cloud-configure.yml
In SUSE OpenStack Cloud 9, the EXT_NET_CIDR setting for the external network is now specified in the input model - see Section 6.16.2.2, “neutron-external-networks”.
38.1.2 Tempest Integration Tests #
Tempest is a set of integration tests for OpenStack API validation, scenarios, and other specific tests to be run against a live OpenStack cluster. In SUSE OpenStack Cloud 9, Tempest has been modeled as a service and this gives you the ability to locate Tempest anywhere in the cloud. It is recommended that you install Tempest on your Cloud Lifecycle Manager node - that is where it resides by default in a new installation.
A version of the upstream Tempest integration tests is pre-deployed on the Cloud Lifecycle Manager node. For details on what Tempest is testing, you can check the contents of this file on your Cloud Lifecycle Manager:
/opt/stack/tempest/run_filters/ci.txt
You can use these embedded tests to verify if the deployed cloud is functional.
For more information on running Tempest tests, see Tempest - The OpenStack Integration Test Suite.
Running these tests requires access to the deployed cloud's identity admin credentials
Tempest creates and deletes test accounts and test resources for test purposes.
In certain cases Tempest might fail to clean-up some of test resources after a test is complete, for example in case of failed tests.
38.1.3 Running the Tests #
To run the default set of Tempest tests:
Log in to the Cloud Lifecycle Manager.
Ensure you can access your cloud:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts cloud-client-setup.yml source /etc/environment
Run the tests:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts tempest-run.yml
Optionally, you can Section 38.1.5, “Customizing the Test Run”.
38.1.4 Viewing Test Results #
Tempest is deployed under /opt/stack/tempest. Test
results are written in a log file in the following directory:
/opt/stack/tempest/logs
A detailed log file is written to:
/opt/stack/tempest/logs/testr_results_region1.log
If you encounter an error saying "local variable 'run_subunit_content'
referenced before assignment", you may need to log in as the
tempest user to run this command. This is due to a known
issue reported at
https://bugs.launchpad.net/testrepository/+bug/1348970.
See Test Repository Users Manual for more details on how to manage the test result repository.
38.1.5 Customizing the Test Run #
There are several ways available to customize which tests will be executed.
38.1.6 Run Tests for Specific Services and Exclude Specific Features #
Tempest allows you to test specific services and features using the
tempest.conf configuration file.
A working configuration file with inline documentation is deployed under
/opt/stack/tempest/configs/.
To use this, follow these steps:
Log in to the Cloud Lifecycle Manager.
Edit the
/opt/stack/tempest/configs/tempest_region1.conffile.To test specific service, edit the
[service_available]section and clear the comment character#and set a line totrueto test that service orfalseto not test that service.cinder = true neutron = false
To test specific features, edit any of the
*_feature_enabledsections to enable or disable tests on specific features of a service.[volume-feature-enabled] [compute-feature-enabled] [identity-feature-enabled] [image-feature-enabled] [network-feature-enabled] [object-storage-feature-enabled]
#Is the v2 identity API enabled (boolean value) api_v2 = true #Is the v3 identity API enabled (boolean value) api_v3 = false
Then run tests normally
38.1.7 Run Tests Matching a Series of White and Blacklists #
You can run tests against specific scenarios by editing or creating a run filter file.
Run filter files are deployed under
/opt/stack/tempest/run_filters.
Use run filters to whitelist or blacklist specific tests or groups of tests:
lines starting with # or empty are ignored
lines starting with
+are whitelistedlines starting with
-are blacklistedlines not matching any of the above conditions are blacklisted
If whitelist is empty, all available tests are fed to blacklist. If blacklist is empty, all tests from whitelist are returned.
Whitelist is applied first. The blacklist is executed against the set of tests returned by the whitelist.
To run whitelist and blacklist tests:
Log in to the Cloud Lifecycle Manager.
Make sure you can access the cloud:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts cloud-client-setup.yml source /etc/environment
Run the tests:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts tempest-run.yml -e run_filter <run_filter_name>
Note that the run_filter_name is the name of the run_filter file except for the extension. For instance, to run using the filter from the file /opt/stack/tempest/run_filters/ci.txt, use the following:
ansible-playbook -i hosts/verb_hosts tempest-run.yml -e run_filter=ci
Documentation on the format of white and black-lists is available at:
/opt/stack/tempest/bin/tests2skip.py
Example:
The following entries run API tests, exclude tests that are less relevant for deployment validation, such as negative, admin, cli and third-party (EC2) tests:
+tempest\.api\.* *[Aa]dmin.* *[Nn]egative.* - tempest\.cli.* - tempest\.thirdparty\.*
38.2 Verify the Object Storage (swift) Operations #
For information about verifying the operations, see Book “Operations Guide CLM”, Chapter 9 “Managing Object Storage”, Section 9.1 “Running the swift Dispersion Report”.
38.3 Uploading an Image for Use #
To create a Compute instance, you need to obtain an image that you can use. The Cloud Lifecycle Manager provides an Ansible playbook that will download a CirrOS Linux image, and then upload it as a public image to your image repository for use across your projects.
38.3.1 Running the Playbook #
Use the following command to run this playbook:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts glance-cloud-configure.yml -e proxy=<PROXY>
The table below shows the optional switch that you can use as part of this playbook to specify environment-specific information:
| Switch | Description |
|---|---|
|
|
Optional. If your environment requires a proxy for the internet, use this switch to specify the proxy information. |
38.3.2 How to Curate Your Own Images #
OpenStack has created a guide to show you how to obtain, create, and modify images that will be compatible with your cloud:
38.3.3 Using the python-glanceclient CLI to Create Images #
You can use the glanceClient on a machine accessible to your cloud or on your Cloud Lifecycle Manager where it is automatically installed.
The OpenStackClient allows you to create, update, list, and delete images as
well as manage your image member lists, which allows you to share access to
images across multiple tenants. As with most of the OpenStack CLI tools, you
can use the openstack help command to get a full list of
commands as well as their syntax.
If you would like to use the --copy-from option when
creating an image, you will need to have your Administrator enable the http
store in your environment using the instructions outlined at
Book “Operations Guide CLM”, Chapter 6 “Managing Compute”, Section 6.7 “Configuring the Image Service”, Section 6.7.2 “Allowing the glance copy-from option in your environment”.
38.4 Creating an External Network #
You must have an external network set up to allow your Compute instances to reach the internet. There are multiple methods you can use to create this external network and we provide two of them here. The SUSE OpenStack Cloud installer provides an Ansible playbook that will create this network for use across your projects. We also show you how to create this network via the command line tool from your Cloud Lifecycle Manager.
38.4.1 Using the Ansible Playbook #
This playbook will query the Networking service for an existing external
network, and then create a new one if you do not already have one. The
resulting external network will have the name ext-net
with a subnet matching the CIDR you specify in the command below.
If you need to specify more granularity, for example specifying an allocation pool for the subnet then you should utilize the Section 38.4.2, “Using the OpenStackClient CLI”.
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts neutron-cloud-configure.yml -e EXT_NET_CIDR=<CIDR>
The table below shows the optional switch that you can use as part of this playbook to specify environment-specific information:
| Switch | Description |
|---|---|
|
|
Optional. You can use this switch to specify the external network CIDR. If you do not use this switch, or use a wrong value, the VMs will not be accessible over the network.
This CIDR will be from the Note If this option is not defined the default value is "172.31.0.0/16" |
38.4.2 Using the OpenStackClient CLI #
For more granularity you can utilize the OpenStackClient to create your external network.
Log in to the Cloud Lifecycle Manager.
Source the Admin credentials:
source ~/service.osrc
Create the external network and then the subnet using these commands below.
Creating the network:
ardana >openstack network create --router:external <external-network-name>Creating the subnet:
ardana >openstack subnet create <external-network-name> <CIDR> --gateway <gateway> \ --allocation-pool start=<IP_start>,end=<IP_end> [--disable-dhcp]Where:
Value Description external-network-name This is the name given to your external network. This is a unique value that you will choose. The value
ext-netis usually used.CIDR You can use this switch to specify the external network CIDR. If you choose not to use this switch, or use a wrong value, the VMs will not be accessible over the network.
This CIDR will be from the EXTERNAL VM network.
--gateway Optional switch to specify the gateway IP for your subnet. If this is not included then it will choose the first available IP.
--allocation-pool start end Optional switch to specify start and end IP addresses to use as the allocation pool for this subnet.
--disable-dhcp Optional switch if you want to disable DHCP on this subnet. If this is not specified, DHCP will be enabled.
38.4.3 Next Steps #
Once the external network is created, users can create a Private Network to complete their networking setup.
39 UI Verification #
Once you have completed your cloud deployment, these are some of the common post-installation tasks you may need to perform to verify your cloud installation.
39.1 Verifying Your Block Storage Backend #
The sections below will show you the steps to verify that your Block Storage backend was setup properly.
39.1.1 Create a Volume #
Perform the following steps to create a volume using horizon dashboard.
Log into the horizon dashboard.
Choose › › .
On the tabs, click the button to create a volume.
In the options, enter the required details into the fields and then click the button:
Volume Name - This is the name you specify for your volume.
Description (optional) - This is an optional description for the volume.
Type - Select the volume type you have created for your volumes from the drop down.
Size (GB) - Enter the size, in GB, you would like the volume to be.
Availability Zone - You can either leave this at the default option of or select a specific zone from the drop-down box.
The dashboard will then show the volume you have just created.
39.1.2 Attach Volume to an Instance #
Perform the following steps to attach a volume to an instance:
Log into the horizon dashboard.
Choose › › .
In the column, choose the in the drop-down box next to the instance you want to attach the volume to.
In the drop-down, select the volume that you want to attach.
Edit the if necessary.
Click to complete the action.
On the screen, verify that the volume you attached is displayed in the columns.
39.1.3 Detach Volume from Instance #
Perform the following steps to detach the volume from instance:
Log into the horizon dashboard.
Choose › › .
Click the check box next to the name of the volume you want to detach.
In the column, choose the in the drop-down box next to the instance you want to attach the volume to.
Click . A confirmation dialog box appears.
Click to confirm the detachment of the volume from the associated instance.
39.1.4 Delete Volume #
Perform the following steps to delete a volume using horizon dashboard:
Log into the horizon dashboard.
Choose › › .
In the column, click next to the volume you would like to delete.
To confirm and delete the volume, click again.
Verify that the volume was removed from the screen.
39.1.5 Verifying Your Object Storage (swift) #
The following procedure shows how to validate that all servers have been added to the swift rings:
Run the swift-compare-model-rings.yml playbook as follows:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts swift-compare-model-rings.yml
Search for output similar to the following. Specifically, look at the number of drives that are proposed to be added.
TASK: [swiftlm-ring-supervisor | validate-input-model | Print report] ********* ok: [ardana-cp1-c1-m1-mgmt] => { "var": { "report.stdout_lines": [ "Rings:", " ACCOUNT:", " ring exists", " no device changes", " ring will be rebalanced", " CONTAINER:", " ring exists", " no device changes", " ring will be rebalanced", " OBJECT-0:", " ring exists", " no device changes", " ring will be rebalanced" ] } }If the text contains "no device changes" then the deploy was successful and no further action is needed.
If more drives need to be added, it indicates that the deploy failed on some nodes and that you restarted the deploy to include those nodes. However, the nodes are not in the swift rings because enough time has not elapsed to allow the rings to be rebuilt. You have two options to continue:
Repeat the deploy. There are two steps:
Delete the ring builder files as described in Book “Operations Guide CLM”, Chapter 18 “Troubleshooting Issues”, Section 18.6 “Storage Troubleshooting”, Section 18.6.2 “swift Storage Troubleshooting”, Section 18.6.2.8 “Restarting the Object Storage Deployment”.
Repeat the installation process starting by running the
site.ymlplaybook as described in Section 24.7, “Deploying the Cloud”.
Rebalance the rings several times until all drives are incorporated in the rings. This process may take several hours to complete (because you need to wait one hour between each rebalance). The steps are as follows:
Change the min-part-hours to 1 hour. See Book “Operations Guide CLM”, Chapter 9 “Managing Object Storage”, Section 9.5 “Managing swift Rings”, Section 9.5.7 “Changing min-part-hours in Swift”.
Use the "First phase of ring rebalance" and "Final rebalance phase" as described in Book “Operations Guide CLM”, Chapter 9 “Managing Object Storage”, Section 9.5 “Managing swift Rings”, Section 9.5.5 “Applying Input Model Changes to Existing Rings”. The “Weight change phase of ring rebalance” does not apply because you have not set the weight-step attribute at this stage.
Set the min-part-hours to the recommended 16 hours as described in Book “Operations Guide CLM”, Chapter 9 “Managing Object Storage”, Section 9.5 “Managing swift Rings”, Section 9.5.7 “Changing min-part-hours in Swift”.
If you receive errors during the validation, see Book “Operations Guide CLM”, Chapter 18 “Troubleshooting Issues”, Section 18.6 “Storage Troubleshooting”, Section 18.6.2 “swift Storage Troubleshooting”, Section 18.6.2.3 “Interpreting Swift Input Model Validation Errors”.
40 Installing OpenStack Clients #
If you have a standalone deployer, the OpenStack CLI and other clients will not be installed automatically on that node. If you require access to these clients, you will need to follow the procedure below to add the appropriate software.
[OPTIONAL] Connect to your standalone deployer and try to use the OpenStack CLI:
source ~/keystone.osrc openstack project list -bash: openstack: command not foundEdit the configuration file containing details of your Control Plane, typically
~/openstack/my_cloud/definition/data/control_plane.yml.Locate the stanza for the cluster where you want to install the client(s). For a standalone deployer, this will look like the following extract:
clusters: - name: cluster0 cluster-prefix: c0 server-role: LIFECYCLE-MANAGER-ROLE member-count: 1 allocation-policy: strict service-components: - ntp-server - lifecycle-managerChoose the client(s) you wish to install from the following list of available clients:
- barbican-client - ceilometer-client - cinder-client - designate-client - glance-client - heat-client - ironic-client - keystone-client - magnum-client - manila-client - monasca-client - neutron-client - nova-client - ntp-client - octavia-client - openstack-client - swift-client
Add the client(s) to the list of
service-components- in this example, we add theopenstack-clientto the standalone deployer:clusters: - name: cluster0 cluster-prefix: c0 server-role: LIFECYCLE-MANAGER-ROLE member-count: 1 allocation-policy: strict service-components: - ntp-server - lifecycle-manager - openstack-client - cinder-client - designate-client - glance-client - heat-client - ironic-client - keystone-client - neutron-client - nova-client - swift-client - monasca-client - barbican-clientCommit the configuration changes:
cd ~/openstack/ardana/ansible git add -A git commit -m "Add explicit client service deployment"
Run the configuration processor, followed by the
ready-deploymentplaybook:cd ~/openstack/ardana/ansible ansible-playbook -i hosts/localhost config-processor-run.yml -e encrypt="" \ -e rekey="" ansible-playbook -i hosts/localhost ready-deployment.yml
Add the software for the clients using the following command:
cd ~/scratch/ansible/next/ardana/ansible ansible-playbook -i hosts/verb_hosts clients-upgrade.yml
Check that the software has been installed correctly. In this instance, connect to your standalone deployer and try to use the OpenStack CLI:
source ~/keystone.osrc openstack project list
You should now see a list of projects returned:
stack@ardana-cp1-c0-m1-mgmt:~$ openstack project list +----------------------------------+------------------+ | ID | Name | +----------------------------------+------------------+ | 076b6e879f324183bbd28b46a7ee7826 | kronos | | 0b81c3a9e59c47cab0e208ea1bb7f827 | backup | | 143891c2a6094e2988358afc99043643 | octavia | | 1d3972a674434f3c95a1d5ed19e0008f | glance-swift | | 2e372dc57cac4915bf06bbee059fc547 | glance-check | | 383abda56aa2482b95fb9da0b9dd91f4 | monitor | | 606dd3b1fa6146668d468713413fb9a6 | swift-monitor | | 87db9d1b30044ea199f0293f63d84652 | admin | | 9fbb7494956a483ca731748126f50919 | demo | | a59d0c682474434a9ddc240ddfe71871 | services | | a69398f0f66a41b2872bcf45d55311a7 | swift-dispersion | | f5ec48d0328d400992c1c5fb44ec238f | cinderinternal | +----------------------------------+------------------+
41 Configuring Transport Layer Security (TLS) #
TLS is enabled by default during the installation of SUSE OpenStack Cloud 9 and additional configuration options are available to secure your environment, as described below.
In SUSE OpenStack Cloud 9, you can provide your own certificate authority and certificates for internal and public virtual IP addresses (VIPs), and you should do so for any production cloud. The certificates automatically generated by SUSE OpenStack Cloud are useful for testing and setup, but you should always install your own for production use. Certificate installation is discussed below.
Read the following if you are using the default cert-name:
my-public-cert in your model.
The bundled test certificate for public endpoints, located at
~/openstack/my_cloud/config/tls/certs/my-public-cert, is
now expired but was left in the product in case you changed the content with
your valid certificate. Please verify if the certificate is expired and
generate your own, as described in
Section 41.4, “Generate a self-signed CA”.
You can verify the expiry date by running this command:
ardana > openssl x509 -in ~/openstack/my_cloud/config/tls/certs/my-public-cert \
-noout -enddate
notAfter=Oct 8 09:01:58 2016 GMTBefore you begin, the following list of terms will be helpful when generating and installing certificates.
- SUSE OpenStack Cloud-generated public CA
A SUSE OpenStack Cloud-generated public CA (
openstack_frontend_cacert.crt) is available for you to use in/etc/pki/trust/anchors/ca-certificates.- Fully qualified domain name (FQDN) of the public VIP
The registered domain name. A FQDN is not mandatory. It is perfectly valid to have no FQDN and use IP addresses instead. Note that you can use FQDNs on public endpoints, and you may change them whenever the need arises.
- Certificate authority (CA) certificate
Your certificates must be signed by a CA, such as your internal IT department or a public certificate authority. For this example we will use a self-signed certificate.
- Server certificate
It is easy to confuse server certificates and CA certificates. Server certificates reside on the server and CA certificates reside on the client. A server certificate affirms that the server that sent it serves a set of IP addresses, domain names, and set of services. A CA certificate is used by the client to authenticate this claim.
- SAN (subject-alt-name)
The set of IP addresses and domain names in a server certificate request: A template for a server certificate.
- Certificate signing request (CSR)
A blob of data generated from a certificate request and sent to a CA, which would then sign it, produce a server certificate, and send it back.
- External VIP
External virtual IP address
- Internal VIP
Internal virtual IP address
The major difference between an external VIP certificate and an internal VIP certificate is that the internal VIP has approximately 40 domain names in the SAN. This is because each service has a different domain name in SUSE OpenStack Cloud 9. So it is unlikely that you can create an internal server certificate before running the configuration processor. But after a configuration processor run, a certificate request would be created for each of your cert-names.
41.1 Configuring TLS in the input model #
For this example certificate configuration, let us assume there is no FQDN for the external VIP and that you are going to use the default IP address provided by SUSE OpenStack Cloud 9. Let's also assume that for the internal VIP you will use the defaults as well. If you were to call your certificate authority "example-CA," the CA certificate would then be called "example-CA.crt" and the key would be called "example-CA.key." In the following examples, the external VIP certificate will be named "example-public-cert" and the internal VIP certificate will be named "example-internal-cert."
Cautions:
Any time you make a cert change when using your own CA:
You should use a distinct name from those already existing in
config/tls/cacerts. This also means that you should not reuse your CA names (and use unique and distinguishable names such as MyCompanyXYZ_PrivateRootCA.crt). A new name is what indicates that a file is new or changed, so reusing a name means that the file is not considered changed even its contents have changed.You should not remove any existing CA files from
config/tls/cacerts.If you want to remove an existing CA you must
First remove the file.
Then run:
ardana >ansible -i hosts/verb_hosts FND-STN -a 'sudo keytool -delete -alias \ debian:<filename to remove> \ -keystore /usr/lib/jvm/java-7-openjdk-amd64/jre/lib/security/cacerts \ -storepass changeit'
Be sure to install your own certificate for all production clouds after installing and testing your cloud. If you ever want to test or troubleshoot later, you will be able to revert to the sample certificate to get back to a stable state for testing.
Unless this is a new deployment, do not update both the certificate and the CA together. Add the CA first and then run a site deploy. Then update the certificate and run tls-reconfigure, FND-CLU-stop, FND-CLU-start and then ardana-reconfigure. If a playbook has failed, rerun it with -vv to get detailed error information. The configure, HAproxy restart, and reconfigure steps are included below. If this is a new deployment and you are adding your own certs/CA before running site.yml this caveat does not apply.
You can add your own certificate by following the instructions below. All
changes must go into the file
~/openstack/my_cloud/definition/data/network_groups.yml.
Below are the entries for TLS for the internal and admin load balancers:
- provider: ip-cluster
name: lb
tls-components:
- default
components:
# These services do not currently support TLS so they are not listed
# under tls-components
- nova-metadata
roles:
- internal
- admin
cert-file: openstack-internal-cert
# The openstack-internal-cert is a reserved name and
# this certificate will be autogenerated. You
# can bring in your own certificate with a different name
# cert-file: customer-provided-internal-cert
# replace this with name of file in "config/tls/certs/"
The configuration processor will also create a request template for each
named certificate under info/cert_reqs/ This will be of
the form:
info/cert_reqs/customer-provided-internal-cert
These request templates contain the subject Alt-names
that the certificates need. You can add to this template before generating
your certificate signing request .
You would then send the CSR to your CA to be signed, and once you receive
the certificate, place it in config/tls/certs.
When you bring in your own certificate, you may want to bring in the trust
chains (or CA certificate) for this certificate. This is usually not
required if the CA is a public signer that is typically bundled with the
operating system. However, we suggest you include it anyway by copying the
file into the directory config/cacerts/.
41.2 User-provided certificates and trust chains #
SUSE OpenStack Cloud generates its own internal certificates but is designed to allow you to bring in your own certificates for the VIPs. Here is the general process.
You must have a server certificate and a CA certificate to go with it (unless the signer is a public CA and it is already bundled with most distributions).
You must decide the names of the server certificates and configure the
network_groups.ymlfile in the input model such that each load balancer provider has at least one cert-name associated with it.Run the configuration processor. Note that you may or may not have the certificate file at this point. The configuration processor would create certificate request file artifacts under
info/cert_reqs/for each of the cert-name(s) in thenetwork_groups.ymlfile. While there is no special reason to use the request file created for an external endpoint VIP certificate, it is important to use the request files created for internal certificates since the canonical names for the internal VIP can be many and service specific and each of these need to be in the Subject Alt Names attribute of the certificate.Create a certificate signing request for this request file and send it to your internal CA or a public CA to get it certified and issued with a certificate. You will now have a server certificate and possibly a trust chain or CA certificate.
Next, upload it to the Cloud Lifecycle Manager. Server certificates should be added to
config/tls/certsand CA certificates should be added toconfig/tls/cacerts. The file extension should be CRT file for the CA certificate to be processed by SUSE OpenStack Cloud. Detailed steps are next.
41.3 Edit the input model to include your certificate files #
Edit the load balancer configuration in
~/openstack/my_cloud/definition/data/network_groups.yml:
load-balancers: - provider: ip-cluster name: lb tls-components: - default components: - nova-metadata roles: - internal - admin cert-file: example-internal-cert #<<<---- Certificate name for the internal VIP - provider: ip-cluster name: extlb external-name: myardana.test #<<<--- Use just IP for the external VIP in this example tls-components: - default roles: - public cert-file: example-public-cert #<<<---- Certificate name for the external VIP
Commit your changes to the local git repository and run the configuration processor:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "changed VIP certificates"ardana >ansible-playbook -i hosts/localhost config-processor-run.yml
Verify that certificate requests have been generated by the configuration
processor for every certificate file configured in the
networks_groups.yml file. In this example, there are two
files, as shown from the list command:
ardana > ls ~/openstack/my_cloud/info/cert_reqs
example-internal-cert
example-public-cert41.4 Generate a self-signed CA #
In a production setting you will not perform this step. You will use your company's CA or a valid public CA.
This section demonstrates to how you can create your own self-signed CA and then use this CA to sign server certificates. This CA can be your organization's IT internal CA that is self-signed and whose CA certificates are deployed on your organization's machines. This way the server certificate becomes legitimate.
Please use a unique CN for your example Certificate Authority and do not install multiple CA certificates with the same CN into your cloud.
Copy the commands below to the command line and execute. This will cause the
two files, example-CA.key and
example-CA.crt to be created:
ardana >export EXAMPLE_CA_KEY_FILE='example-CA.key'ardana >export EXAMPLE_CA_CERT_FILE='example-CA.crt'ardana >openssl req -x509 -batch -newkey rsa:2048 -nodes -out "${EXAMPLE_CA_CERT_FILE}" \ -keyout "${EXAMPLE_CA_KEY_FILE}" \ -subj "/C=UK/O=hp/CN=YourOwnUniqueCertAuthorityName" \ -days 365
You can tweak the subj and days settings above to meet your needs, or to
test. For instance, if you want to test what happens when a CA expires, you
can set 'days' to a very low value. Grab the configuration
processor-generated request file from info/cert_reqs/:
ardana > cat ~/openstack/my_cloud/info/cert_reqs/example-internal-cert
Now, copy this file to your working directory and append a
.req extension to it.
ardana > cp ~/openstack/my_cloud/info/cert_reqs/example-internal-cert \
example-internal-cert.req[req] distinguished_name = req_distinguished_name req_extensions = v3_req prompt = no [ req_distinguished_name ] CN = "openstack-vip" [ v3_req ] basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment subjectAltName = @alt_names [ alt_names ] DNS.1 = "deployerincloud-ccp-c0-m1-mgmt" DNS.2 = "deployerincloud-ccp-vip-CEI-API-mgmt" DNS.3 = "deployerincloud-ccp-vip-CND-API-mgmt" DNS.4 = "deployerincloud-ccp-vip-DES-API-mgmt" DNS.5 = "deployerincloud-ccp-vip-FND-MDB-mgmt" DNS.6 = "deployerincloud-ccp-vip-FND-RMQ-mgmt" DNS.7 = "deployerincloud-ccp-vip-FND-VDB-mgmt" DNS.8 = "deployerincloud-ccp-vip-FRE-API-mgmt" DNS.9 = "deployerincloud-ccp-vip-GLA-API-mgmt" DNS.10 = "deployerincloud-ccp-vip-GLA-REG-mgmt" DNS.11 = "deployerincloud-ccp-vip-HEA-ACF-mgmt" DNS.12 = "deployerincloud-ccp-vip-HEA-ACW-mgmt" DNS.13 = "deployerincloud-ccp-vip-HEA-API-mgmt" DNS.14 = "deployerincloud-ccp-vip-HUX-SVC-mgmt" DNS.15 = "deployerincloud-ccp-vip-HZN-WEB-mgmt" DNS.16 = "deployerincloud-ccp-vip-KEY-API-mgmt" DNS.17 = "deployerincloud-ccp-vip-KEYMGR-API-mgmt" DNS.18 = "deployerincloud-ccp-vip-LOG-API-mgmt" DNS.19 = "deployerincloud-ccp-vip-LOG-SVR-mgmt" DNS.20 = "deployerincloud-ccp-vip-MON-API-mgmt" DNS.21 = "deployerincloud-ccp-vip-NEU-SVR-mgmt" DNS.22 = "deployerincloud-ccp-vip-NOV-API-mgmt" DNS.23 = "deployerincloud-ccp-vip-NOV-MTD-mgmt" DNS.24 = "deployerincloud-ccp-vip-OCT-API-mgmt" DNS.25 = "deployerincloud-ccp-vip-OPS-WEB-mgmt" DNS.26 = "deployerincloud-ccp-vip-SHP-API-mgmt" DNS.27 = "deployerincloud-ccp-vip-SWF-PRX-mgmt" DNS.28 = "deployerincloud-ccp-vip-admin-CEI-API-mgmt" DNS.29 = "deployerincloud-ccp-vip-admin-CND-API-mgmt" DNS.30 = "deployerincloud-ccp-vip-admin-DES-API-mgmt" DNS.31 = "deployerincloud-ccp-vip-admin-FND-MDB-mgmt" DNS.32 = "deployerincloud-ccp-vip-admin-FRE-API-mgmt" DNS.33 = "deployerincloud-ccp-vip-admin-GLA-API-mgmt" DNS.34 = "deployerincloud-ccp-vip-admin-HEA-ACF-mgmt" DNS.35 = "deployerincloud-ccp-vip-admin-HEA-ACW-mgmt" DNS.36 = "deployerincloud-ccp-vip-admin-HEA-API-mgmt" DNS.37 = "deployerincloud-ccp-vip-admin-HUX-SVC-mgmt" DNS.38 = "deployerincloud-ccp-vip-admin-HZN-WEB-mgmt" DNS.39 = "deployerincloud-ccp-vip-admin-KEY-API-mgmt" DNS.40 = "deployerincloud-ccp-vip-admin-KEYMGR-API-mgmt" DNS.41 = "deployerincloud-ccp-vip-admin-MON-API-mgmt" DNS.42 = "deployerincloud-ccp-vip-admin-NEU-SVR-mgmt" DNS.43 = "deployerincloud-ccp-vip-admin-NOV-API-mgmt" DNS.44 = "deployerincloud-ccp-vip-admin-OPS-WEB-mgmt" DNS.45 = "deployerincloud-ccp-vip-admin-SHP-API-mgmt" DNS.46 = "deployerincloud-ccp-vip-admin-SWF-PRX-mgmt" DNS.47 = "192.168.245.5" IP.1 = "192.168.245.5" =============end of certificate request file.
In the case of a public VIP certificate, please add all the FQDNs you want
it to support Currently SUSE OpenStack Cloud does not add the hostname for the
external-name specified in network_groups.yml to the
certificate request file . However, you can add it to the certificate
request file manually. Here we assume that myardana.test
is your external-name. In that case you would add this line (to the
certificate request file that is shown above in
Example 41.1, “Certificate request file”):
DNS.48 = "myardana.test"
Any attempt to use IP addresses rather than FQDNs in certificates must use subject alternate name entries that list both the IP address (needed for Google) and DNS with an IP (needed for a Python bug workaround). Failure to create the certificates in this manner will cause future installations of Go-based tools (such as Cloud Foundry, Stackato and other PaaS components) to fail.
41.5 Generate a certificate signing request #
Now that you have a CA and a certificate request file, it is time to generate a CSR.
ardana >export EXAMPLE_SERVER_KEY_FILE='example-internal-cert.key'ardana >export EXAMPLE_SERVER_CSR_FILE='example-internal-cert.csr'ardana >export EXAMPLE_SERVER_REQ_FILE=example-internal-cert.reqardana >openssl req -newkey rsa:2048 -nodes -keyout "$EXAMPLE_SERVER_KEY_FILE" \ -out "$EXAMPLE_SERVER_CSR_FILE" -extensions v3_req -config "$EXAMPLE_SERVER_REQ_FILE"
Note that in production you would usually send the generated
example-internal-cert.csr file to your IT department. But
in this example you are your own CA, so sign and generate a server
certificate.
41.6 Generate a server certificate #
In a production setting you will not perform this step. You will send the CSR created in the previous section to your company CA or a to a valid public CA and have them sign and send you back the certificate.
This section demonstrates how you would use your own self-signed CA that your created earlier to sign and generate a server certificate. A server certificate is essentially a signed public key, the signer being a CA and trusted by a client. When you install this the signing CA's certificate (called CA certificate or trust chain) on the client machine, you are telling the client to trust this CA, and thereby implicitly trusting any server certificates that are signed by this CA, thus creating a trust anchor.
CA configuration file
When the CA signs the certificate, it uses a configuration file that tells it to verify the CSR. Note that in a production scenario the CA takes care of this for you.
Create a file called openssl.cnf and add the following
contents to it.
# Copyright 2010 United States Government as represented by the # Administrator of the National Aeronautics and Space Administration. # All Rights Reserved. #... # OpenSSL configuration file. # # Establish working directory. dir = . [ ca ] default_ca = CA_default [ CA_default ] serial = $dir/serial database = $dir/index.txt new_certs_dir = $dir/ certificate = $dir/cacert.pem private_key = $dir/cakey.pem unique_subject = no default_crl_days = 365 default_days = 365 default_md = md5 preserve = no email_in_dn = no nameopt = default_ca certopt = default_ca policy = policy_match copy_extensions = copy [ policy_match ] countryName = optional stateOrProvinceName = optional organizationName = optional organizationalUnitName = optional commonName = supplied emailAddress = optional [ req ] default_bits = 1024 # Size of keys default_keyfile = key.pem # name of generated keys default_md = md5 # message digest algorithm string_mask = nombstr # permitted characters distinguished_name = req_distinguished_name req_extensions = v3_req x509_extensions = v3_ca [ req_distinguished_name ] # Variable name Prompt string #---------------------- ---------------------------------- 0.organizationName = Organization Name (company) organizationalUnitName = Organizational Unit Name (department, division) emailAddress = Email Address emailAddress_max = 40 localityName = Locality Name (city, district) stateOrProvinceName = State or Province Name (full name) countryName = Country Name (2 letter code) countryName_min = 2 countryName_max = 2 commonName = Common Name (hostname, IP, or your name) commonName_max = 64 # Default values for the above, for consistency and less typing. # Variable name Value #------------------------------ ------------------------------ 0.organizationName_default = Exampleco PLC localityName_default = Anytown stateOrProvinceName_default = Anycounty countryName_default = UK commonName_default = my-CA [ v3_ca ] basicConstraints = CA:TRUE subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer:always subjectAltName = @alt_names [ v3_req ] basicConstraints = CA:FALSE subjectKeyIdentifier = hash [ alt_names ] ######### end of openssl.cnf #########
Sign and create a server certificate
Now you can sign the server certificate with your CA. Copy the commands below to the command line and execute. This will cause the one file, example-internal-cert.crt, to be created:
ardana >export EXAMPLE_SERVER_CERT_FILE='example-internal-cert.crt'ardana >export EXAMPLE_SERVER_CSR_FILE='example-internal-cert.csr'ardana >export EXAMPLE_CA_KEY_FILE='example-CA.key'ardana >export EXAMPLE_CA_CERT_FILE='example-CA.crt'ardana >touch index.txtardana >openssl rand -hex -out serial 6ardana >openssl ca -batch -notext -md sha256 -in "$EXAMPLE_SERVER_CSR_FILE" \ -cert "$EXAMPLE_CA_CERT_FILE" \ -keyfile "$EXAMPLE_CA_KEY_FILE" \ -out "$EXAMPLE_SERVER_CERT_FILE" \ -config openssl.cnf -extensions v3_req
Finally, concatenate both the server key and certificate in preparation for uploading to the Cloud Lifecycle Manager.
ardana > cat example-internal-cert.key example-internal-cert.crt > example-internal-certNote that you have only created the internal-cert in this example. Repeat the above sequence for example-public-cert. Make sure you use the appropriate certificate request generated by the configuration processor.
41.7 Upload to the Cloud Lifecycle Manager #
The following two files created from the example run above will need to be
uploaded to the Cloud Lifecycle Manager and copied into config/tls.
example-internal-cert
example-CA.crt
Once on the Cloud Lifecycle Manager, execute the following two copy commands to copy to their respective directories. Note if you had created an external cert, you can copy that in a similar manner, specifying its name using the copy command as well.
ardana >cp example-internal-cert ~/openstack/my_cloud/config/tls/certs/ardana >cp example-CA.crt ~/openstack/my_cloud/config/tls/cacerts/
Continue with the deployment
Next, log into the Cloud Lifecycle Manager node, and save and commit the changes to the local git repository:
ardana >cd ~/openstack/ardana/ansibleardana >git add -Aardana >git commit -m "updated certificate and CA"
Next, rerun the config-processor-run playbook, and run
ready-deployment.yml:
ardana >cd ~/openstack/ardana/ansibleardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.yml
If you receive any prompts, enter the required information.
For automated installation (for example CI) you can specify the required passwords on the Ansible command line. For example, the command below will disable encryption by the configuration processor:
ardana > ansible-playbook -i hosts/localhost config-processor-run.yml -e encrypt="" -e rekey=""Run this series of runbooks to complete the deployment:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts tls-reconfigure.ymlardana >ansible-playbook -i hosts/verb_hosts FND-CLU-stop.ymlardana >ansible-playbook -i hosts/verb_hosts FND-CLU-start.ymlardana >ansible-playbook -i hosts/verb_hosts monasca-stop.ymlardana >ansible-playbook -i hosts/verb_hosts monasca-start.ymlardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.yml
41.8 Configuring the cipher suite #
By default, the cipher suite is set to:
HIGH:!aNULL:!eNULL:!DES:!3DES. This setting is
recommended in the
OpenStack
documentation site. You may override this. To do so, open
config/haproxy/defaults.yml and edit it. The parameters
can be found under the haproxy_globals list.
- "ssl-default-bind-ciphers HIGH:!aNULL:!eNULL:!DES:!3DES" - "ssl-default-server-ciphers HIGH:!aNULL:!eNULL:!DES:!3DES"
Make the changes as needed. It is best to keep the two options identical.
41.9 Testing #
You can easily determine if an endpoint is behind TLS. To do so, run the following command, which probes a keystone identity service endpoint that is behind TLS:
ardana > echo | openssl s_client -connect 192.168.245.5:5000 | openssl x509 -fingerprint -noout
depth=0 CN = openstack-vip
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 CN = openstack-vip
verify error:num=27:certificate not trusted
verify return:1
depth=0 CN = openstack-vip
verify error:num=21:unable to verify the first certificate
verify return:1
DONE
SHA1 Fingerprint=C6:46:1E:59:C6:11:BF:72:5E:DD:FC:FF:B0:66:A7:A2:CC:32:1C:B8The next command probes a MariaDB endpoint that is not behind TLS:
ardana > echo | openssl s_client -connect 192.168.245.5:3306 | openssl x509 -fingerprint -noout
140448358213264:error:140770FC:SSL routines:SSL23_GET_SERVER_HELLO:unknown protocol:s23_clnt.c:795:
unable to load certificate
140454148159120:error:0906D06C:PEM routines:PEM_read_bio:no start line:pem_lib.c:703
:Expecting: TRUSTED CERTIFICATE41.10 Verifying that the trust chain is correctly deployed #
You can determine if the trust chain is correctly deployed by running the following commands:
ardana > echo | openssl s_client -connect 192.168.245.9:5000 2>/dev/null | grep code
Verify return code: 21 (unable to verify the first certificate)
echo | openssl s_client -connect 192.168.245.9:5000 \
-CAfile /etc/pki/trust/anchors/ca-certificates/openstack_frontend_cacert.crt 2>/dev/null | grep code
Verify return code: 0 (ok)Here, the first command produces error 21, which is then fixed by providing the CA certificate file. This verifies that the CA certificate matches the server certificate.
41.11 Turning TLS on or off #
You should leave TLS enabled in production. However, if you need to disable
it for any reason, you must change "tls-components" to "components" in
network_groups.yml (as shown earlier) and comment out the
cert-file. Additionally, if you have a network_groups.yml
file from a previous installation, you will not have TLS enabled unless you
change "components" to "tls-components" in that file. By default, horizon is
configured with TLS in the input model. Note that you should not disable TLS
in the input model for horizon as that is a public endpoint and is required.
Additionally, you should keep all services behind TLS, but using the input
model file network_groups.yml you may turn TLS off for a
service for troubleshooting or debugging. TLS should always be enabled for
production environments.
If you are using an example input model on a clean install, all supported TLS services will be enabled before deployment of your cloud. If you want to change this setting later, for example, when upgrading, you can change the input model and reconfigure the system. The process is as follows:
Edit the input model network_groups.yml file
appropriately, as described above. Then, commit the changes to the git
repository:
ardana >cd ~/openstack/ardana/ansible/ardana >git add -Aardana >git commit -m "TLS change"
Change directories again and run the configuration processor and ready deployment playbooks:
ardana >ansible-playbook -i hosts/localhost config-processor-run.ymlardana >ansible-playbook -i hosts/localhost ready-deployment.yml
Change directories again and run the reconfigure playbook:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts ardana-reconfigure.yml
42 Configuring Availability Zones #
The Cloud Lifecycle Manager only creates a default availability zone during installation. If your system has multiple failure/availability zones defined in your input model, these zones will not get created automatically.
Once the installation has finished, you can run the
nova-cloud-configure.yml playbook to configure
availability zones and assign compute nodes to those zones based on the
configuration specified in the model.
You can run the playbook nova-cloud-configure.yml any time
you make changes to the configuration of availability zones in your input
model. Alternatively, you can use horizon or the command line to perform the
configuration.
For more details, see the OpenStack Availability Zone documentation at https://docs.openstack.org/nova/rocky/user/aggregates.html.
43 Configuring Load Balancer as a Service #
The SUSE OpenStack Cloud neutron LBaaS service supports several load balancing providers. By default, both Octavia and the namespace HAProxy driver are configured to be used.
The SUSE OpenStack Cloud neutron LBaaS service supports several load balancing providers. By default, both Octavia and the namespace HAProxy driver are configured for use.
If you do not specify the --provider option it will
default to Octavia. The Octavia driver provides more functionality than the
HAProxy namespace driver which is deprecated. The HAProxy namespace driver
will be retired in a future version of SUSE OpenStack Cloud.
There are additional drivers for third-party hardware load balancers. Please
refer to the vendor directly. The openstack network service provider
list command displays the currently installed load balancer
drivers as well as other installed services such as VPN.
43.1 Summary #
The following procedure demonstrates how to setup a load balancer, and test that the round robin load balancing is successful between the two servers. For demonstration purposes, the security group rules and floating IPs are applied to the web servers. Adjust these configuration parameters if needed.
43.2 Prerequisites #
You need have an external network and a registered image to test LBaaS functionality.
Creating an external network: Section 38.4, “Creating an External Network”.
Creating and uploading a glance image: Section 38.3, “Uploading an Image for Use”.
43.3 Octavia Load Balancing Provider #
The Octavia Load balancing provider bundled with SUSE OpenStack Cloud 9 is an operator
grade load balancer for OpenStack. It is based on the OpenStack Rocky
version of Octavia. It differs from the namespace driver by starting a new
nova virtual machine (called an amphora) to house the
HAProxy load balancer software that provides the load balancer function. A
virtual machine for each load balancer requested provides a better
separation of load balancers between tenants, and simplifies increasing load
balancing capacity along with compute node growth. Additionally, if the
virtual machine fails for any reason, Octavia will replace it with a
replacement VM from a pool of spare VMs, assuming that the feature is
configured.
The Health Monitor will not create or replace failed amphoras. If the pool of spare VMs is exhausted there will be no additional virtual machines to handle load balancing requests.
Octavia uses two-way SSL encryption to communicate with amphoras. There
are demo Certificate Authority (CA) certificates included with SUSE OpenStack Cloud 9 in
~/scratch/ansible/next/ardana/ansible/roles/octavia-common/files
on the Cloud Lifecycle Manager. For additional security in production deployments, replace all
certificate authorities with ones you generate by running the following
commands:
ardana >openssl genrsa -passout pass:foobar -des3 -out cakey.pem 2048ardana >openssl req -x509 -passin pass:foobar -new -nodes -key cakey.pem -out ca_01.pemardana >openssl genrsa -passout pass:foobar -des3 -out servercakey.pem 2048ardana >openssl req -x509 -passin pass:foobar -new -nodes -key cakey.pem -out serverca_01.pem
For more details refer to the openssl man page.
If you change the certificate authority and have amphoras running with an old CA, you will not be able to control the amphoras. The amphoras will need to be failed over so they can utilize the new certificate. If you change the CA password for the server certificate, you need to change that in the Octavia configuration files as well. For more information, see Book “Operations Guide CLM”, Chapter 10 “Managing Networking”, Section 10.4 “Networking Service Overview”, Section 10.4.9 “Load Balancer: Octavia Driver Administration”, Section 10.4.9.2 “Tuning Octavia Installation”.
43.4 Prerequisite Setup #
Octavia Client Installation
The Octavia client must be installed in the control plane, see Chapter 40, Installing OpenStack Clients.
Octavia Network and Management Network Ports
The Octavia management network and Management network must have access to each other. If you have a configured firewall between the Octavia management network and Management network, you must open up the following ports to allow network traffic between the networks.
From Management network to Octavia network
TCP 9443 (amphora API)
From Octavia network to Management network
TCP 9876 (Octavia API)
UDP 5555 (Octavia Health Manager)
Optimizing the Octavia memory footprint
By default the Octavia health monitor will use up to 4.2GB of memory, this
can be safely reduced in entry scale environments by modifying
~/openstack/my_cloud/config/octavia/octavia-health-manager.conf.j2
to add the following lines in the [health manager] section:
health_update_threads = 2 stats_update_threads = 2
After editing the octavia-health-manager.conf.j2 file,
run the config-processor-run, ready-deployment and
octavia-reconfigure playbooks to apply these changes. This will limit
the number of processes providing updates for the amphora health and stats.
Installing the Amphora Image
Octavia uses nova VMs for its load balancing function; SUSE
provides images used to boot those VMs called
octavia-amphora.
Without these images the Octavia load balancer will not work.
Register the image. The OpenStack load balancing service (Octavia) does not automatically register the Amphora guest image.
The Amphora image is in an RPM package managed by zypper, display the full path to that file with the following command:
ardana >find /srv -type f -name "*amphora-image*"For example:
/srv/www/suse-12.4/x86_64/repos/Cloud/suse/noarch/openstack-octavia-amphora-image-x86_64-0.1.0-13.157.noarch.rpm. The Amphora image may be updated via maintenance updates, which will change the filename.Switch to the
ansibledirectory and register the image by giving the full path and name for the Amphora image as an argument toservice_package, replacing the filename as needed to reflect an updated amphora image rpm:ardana >cd ~/scratch/ansible/next/ardana/ansible/ardana >ansible-playbook -i hosts/verb_hosts service-guest-image.yml \ -e service_package=\ /srv/www/suse-12.4/x86_64/repos/Cloud/suse/noarch/openstack-octavia-amphora-image-x86_64-0.1.0-13.157.noarch.rpmSource the service user (this can be done on a different computer)
ardana >source service.osrcVerify that the image was registered (this can be done on a computer with access to the glance CLI client)
ardana >openstack image list +--------------------------------------+------------------------+--------- | ID | Name | Status | +--------------------------------------+------------------------+--------+ ... | 1d4dd309-8670-46b6-801d-3d6af849b6a9 | octavia-amphora-x86_64 | active | ...ImportantIn the example above, the status of the
octavia-amphora-x86_64image is active which means the image was successfully registered. If a status of the images is queued, you need to run the image registration again.If you run the registration by accident, the system will only upload a new image if the underlying image has been changed.
Ensure there are not multiple amphora images listed. Execute following command:
ardana >openstack image list --tag amphoraIf the above command returns more than one image, unset the old amphora image. To unset the image execute following command:
ardana >openstack image unset --tag amphora <oldimageid>If you have already created load balancers, they will not receive the new image. Only load balancers created after the image has been successfully installed will use the new image. If existing load balancers need to be switched to the new image, please follow the instructions in Book “Operations Guide CLM”, Chapter 10 “Managing Networking”, Section 10.4 “Networking Service Overview”, Section 10.4.9 “Load Balancer: Octavia Driver Administration”, Section 10.4.9.2 “Tuning Octavia Installation”.
Setup network, subnet, router, security and IP's
If you have already created a network, subnet, router, security settings and IPs you can skip the following steps and go directly to creating the load balancers. In this example we will boot two VMs running web servers and then use curl scripts to demonstrate load balancing between the two VMs. Along the way we will save important parameters to a bash variable and use them later in the process.
Make a tenant network for load balancer clients (the web servers):
ardana >openstack network create lb_net2 +---------------------------+--------------------------------------+ | Field | Value | +---------------------------+--------------------------------------+ | admin_state_up | UP | | availability_zone_hints | | | availability_zones | | | created_at | 2019-10-23T13:27:57Z | | description | | | dns_domain | | | id | 50a66468-084b-457f-88e4-2edb7b81851e | | ipv4_address_scope | None | | ipv6_address_scope | None | | is_default | False | | is_vlan_transparent | None | | mtu | 1450 | | name | lb_net2 | | port_security_enabled | False | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | provider:network_type | vxlan | | provider:physical_network | None | | provider:segmentation_id | 1080 | | qos_policy_id | None | | revision_number | 1 | | router:external | Internal | | segments | None | | shared | False | | status | ACTIVE | | subnets | | | tags | | | updated_at | 2019-10-23T13:27:57Z | +---------------------------+--------------------------------------+Create a subnet for the load balancing clients on the tenant network:
ardana >openstack subnet create --network lb_net2 --subnet-range 12.12.12.0/24 +-------------------+--------------------------------------+ | Field | Value | +-------------------+--------------------------------------+ | allocation_pools | 12.12.12.2-12.12.12.254 | | cidr | 12.12.12.0/24 | | created_at | 2019-10-23T13:29:45Z | | description | | | dns_nameservers | | | enable_dhcp | True | | gateway_ip | 12.12.12.1 | | host_routes | | | id | c141858a-a792-4c89-91f0-de4dc4694a7f | | ip_version | 4 | | ipv6_address_mode | None | | ipv6_ra_mode | None | | name | lb_subnet2 | | network_id | 50a66468-084b-457f-88e4-2edb7b81851e | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | revision_number | 0 | | segment_id | None | | service_types | | | subnetpool_id | None | | tags | | | updated_at | 2019-10-23T13:29:45Z | +-------------------+--------------------------------------+Save the ID of the tenant subnet. The load balancer will be attached to it later.
ardana >VIP_SUBNET="c141858a-a792-4c89-91f0-de4dc4694a7f"Create a router for client VMs:
ardana >openstack router create --centralized lb_router2 +-------------------------+--------------------------------------+ | Field | Value | +-------------------------+--------------------------------------+ | admin_state_up | UP | | availability_zone_hints | | | availability_zones | | | created_at | 2019-10-23T13:30:21Z | | description | | | distributed | False | | external_gateway_info | None | | flavor_id | None | | ha | False | | id | 1c9949fb-a500-475d-8694-346cf66ebf9a | | name | lb_router2 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | revision_number | 0 | | routes | | | status | ACTIVE | | tags | | | updated_at | 2019-10-23T13:30:21Z | +-------------------------+--------------------------------------+Add the subnet to the router and connect it to the external gateway:
ardana >openstack router add subnet lb_router2 lb_subnet2Set gateway for the router. The name of the external network is:
ardana >openstack network list +--------------------------------------+------------------+--------------------------------------+ | ID | Name | Subnets | +--------------------------------------+------------------+--------------------------------------+ | 2ed7deca-81ed-45ee-87ce-aeb4f565d3ad | ext-net | 45d31556-08b8-4b0e-98d8-c09dd986296a | | 50a66468-084b-457f-88e4-2edb7b81851e | lb_net2 | c141858a-a792-4c89-91f0-de4dc4694a7f | | 898975bd-e3cc-4afd-8605-3c5606fd5c54 | OCTAVIA-MGMT-NET | 68eed774-c07f-45bb-b37a-489515108acb | +--------------------------------------+------------------+--------------------------------------+ EXT_NET="ext-net" openstack router set --external-gateway $EXT_NET lb_router2Check the router:
ardana >openstack router show lb_router2 --fit-width +-------------------------+-------------------------------------------------------------------------------------------------------+ | Field | Value | +-------------------------+-------------------------------------------------------------------------------------------------------+ | admin_state_up | UP | | availability_zone_hints | | | availability_zones | nova | | created_at | 2019-10-23T13:30:21Z | | description | | | distributed | False | | external_gateway_info | {"network_id": "2ed7deca-81ed-45ee-87ce-aeb4f565d3ad", "enable_snat": true, "external_fixed_ips": | | | [{"subnet_id": "45d31556-08b8-4b0e-98d8-c09dd986296a", "ip_address": "10.84.57.38"}]} | | flavor_id | None | | ha | False | | id | 1c9949fb-a500-475d-8694-346cf66ebf9a | | interfaces_info | [{"subnet_id": "c141858a-a792-4c89-91f0-de4dc4694a7f", "ip_address": "12.12.12.1", "port_id": | | | "3d8a8605-dbe5-4fa6-87c3-b351763a9a63"}] | | name | lb_router2 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | revision_number | 3 | | routes | | | status | ACTIVE | | tags | | | updated_at | 2019-10-23T13:33:22Z | +-------------------------+-------------------------------------------------------------------------------------------------------+Create a security group for testing with unrestricted inbound and outbound traffic (you will have to restrict the traffic later):
ardana >openstack security group create letmein +-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+ | Field | Value | +-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+ | created_at | 2019-05-13T18:50:28Z | | description | letmein | | id | 1d136bc8-8186-4c08-88f4-fe83465f3c30 | | name | letmein | | project_id | 5bd04b76d1db42988612e5f27170a40a | | revision_number | 2 | | rules | created_at='2019-05-13T18:50:28Z', direction='egress', ethertype='IPv6', id='1f73b026-5f7e-4b2c-9a72-07c88d8ea82d', updated_at='2019-05-13T18:50:28Z' | | | created_at='2019-05-13T18:50:28Z', direction='egress', ethertype='IPv4', id='880a04ee-14b4-4d05-b038-6dd42005d3c0', updated_at='2019-05-13T18:50:28Z' | | updated_at | 2019-05-13T18:50:28Z | +-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+Create security rules for the VMs:
ardana >openstack security group rule create letmein --ingress --protocol tcp --dst-port 1:1024ardana >openstack security group rule create letmein --ingress --protocol icmpardana >openstack security group rule create letmein --egress --protocol tcp --dst-port 1:1024ardana >openstack security group rule create letmein --egress --protocol icmpIf you have not already created a keypair for the web servers, create one now with the
openstack keypair create. You will use the keypair to boot images.ardana >openstack keypair create lb_kp1 > lb_kp1.pem chmod 400 lb_kp1.pem ls -la lb* -r-------- 1 ardana ardana 1680 May 13 12:52 lb_kp1.pemVerify the keypair list:
ardana >openstack keypair list +---------------+-------------------------------------------------+ | Name | Fingerprint | +---------------+-------------------------------------------------+ | id_rsa2 | d3:82:4c:fc:80:79:db:94:b6:31:f1:15:8e:ba:35:0b | | lb_kp1 | 78:a8:0b:5b:2d:59:f4:68:4c:cb:49:c3:f8:81:3e:d8 | +---------------+-------------------------------------------------+List the image names available to boot and boot two VMs:
ardana >openstack image list | grep cirros | faa65f54-e38b-43dd-b0db-ae5f5e3d9b83 | cirros-0.4.0-x86_64 | active |Boot a VM that will host the pseudo web server:
ardana >openstack server create --flavor m1.tiny --image cirros-0.4.0-x86_64 \ --key-name id_rsa2 --security-group letmein --nic net-id=lb_net2 lb2_vm1 --wait +-------------------------------------+------------------------------------------------------------+ | Field | Value | +-------------------------------------+------------------------------------------------------------+ | OS-DCF:diskConfig | MANUAL | | OS-EXT-AZ:availability_zone | nova | | OS-EXT-SRV-ATTR:host | cjd9-cp1-comp0001-mgmt | | OS-EXT-SRV-ATTR:hypervisor_hostname | cjd9-cp1-comp0001-mgmt | | OS-EXT-SRV-ATTR:instance_name | instance-0000001f | | OS-EXT-STS:power_state | Running | | OS-EXT-STS:task_state | None | | OS-EXT-STS:vm_state | active | | OS-SRV-USG:launched_at | 2019-10-23T13:36:32.000000 | | OS-SRV-USG:terminated_at | None | | accessIPv4 | | | accessIPv6 | | | addresses | lb_net2=12.12.12.13 | | adminPass | 79GcsJQfNt3p | | config_drive | | | created | 2019-10-23T13:36:17Z | | flavor | m1.tiny (1) | | hostId | ed0511cb20d44f420e707fbc801643e0658eb2efbf980ef986aa45d0 | | id | 874e675b-727b-44a2-99a9-0ff178590f86 | | image | cirros-0.4.0-x86_64 (96e0df13-573f-4672-97b9-3fe67ff84d6a) | | key_name | id_rsa2 | | name | lb2_vm1 | | progress | 0 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | properties | | | security_groups | name='letmein' | | status | ACTIVE | | updated | 2019-10-23T13:36:32Z | | user_id | ec4d4dbf03be4bf09f105c06c7562ba7 | | volumes_attached | | +-------------------------------------+------------------------------------------------------------+Save the private IP of the first web server:
ardana >IP_LBVM1="12.12.12.13"Boot a second pseudo web server:
ardana >openstack server create --flavor m1.tiny --image cirros-0.4.0-x86_64 \ --key-name id_rsa2 --security-group letmein --nic net-id=lb_net2 lb2_vm2 --wait +-------------------------------------+------------------------------------------------------------+ | Field | Value | +-------------------------------------+------------------------------------------------------------+ | OS-DCF:diskConfig | MANUAL | | OS-EXT-AZ:availability_zone | nova | | OS-EXT-SRV-ATTR:host | cjd9-cp1-comp0002-mgmt | | OS-EXT-SRV-ATTR:hypervisor_hostname | cjd9-cp1-comp0002-mgmt | | OS-EXT-SRV-ATTR:instance_name | instance-00000022 | | OS-EXT-STS:power_state | Running | | OS-EXT-STS:task_state | None | | OS-EXT-STS:vm_state | active | | OS-SRV-USG:launched_at | 2019-10-23T13:38:09.000000 | | OS-SRV-USG:terminated_at | None | | accessIPv4 | | | accessIPv6 | | | addresses | lb_net2=12.12.12.5 | | adminPass | CGDs3mnHcnv8 | | config_drive | | | created | 2019-10-23T13:37:55Z | | flavor | m1.tiny (1) | | hostId | bf4424315eb006ccb91f80e1024b2617cbb86a2cc70cf912b6ca1f95 | | id | a60dfb93-255b-476d-bf28-2b4f0da285e0 | | image | cirros-0.4.0-x86_64 (96e0df13-573f-4672-97b9-3fe67ff84d6a) | | key_name | id_rsa2 | | name | lb2_vm2 | | progress | 0 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | properties | | | security_groups | name='letmein' | | status | ACTIVE | | updated | 2019-10-23T13:38:09Z | | user_id | ec4d4dbf03be4bf09f105c06c7562ba7 | | volumes_attached | | +-------------------------------------+------------------------------------------------------------+Save the private IP of the second web server:
ardana >IP_LBVM2="12.12.12.5"Verify that all the servers are running:
ardana >openstack server list +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+ | ID | Name | Status | Networks | Image | Flavor | +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+ | a60dfb93-255b-476d-bf28-2b4f0da285e0 | lb2_vm2 | ACTIVE | lb_net2=12.12.12.5 | cirros-0.4.0-x86_64 | m1.tiny | | 874e675b-727b-44a2-99a9-0ff178590f86 | lb2_vm1 | ACTIVE | lb_net2=12.12.12.13 | cirros-0.4.0-x86_64 | m1.tiny | +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+Check ports for the VMs first (.13 and .5):
ardana >openstack port list | grep -e $IP_LBVM2 -e $IP_LBVM1 | 42c356f1-8c49-469a-99c8-12c541378741 || fa:16:3e:2d:6b:be | ip_address='12.12.12.13', subnet_id='c141858a-a792-4c89-91f0-de4dc4694a7f' | ACTIVE | | fb7166c1-06f7-4457-bc0d-4692fc2c7fa2 || fa:16:3e:ac:5d:82 | ip_address='12.12.12.5', subnet_id='c141858a-a792-4c89-91f0-de4dc4694a7f' | ACTIVE |Create the floating IPs for the VMs:
ardana >openstack floating ip create $EXT_NET --port fb7166c1-06f7-4457-bc0d-4692fc2c7fa2 openstack floating ip create $EXT_NET --port 42c356f1-8c49-469a-99c8-12c541378741Verify the floating IP attachment:
ardana >openstack server list +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+ | ID | Name | Status | Networks | Image | Flavor | +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+ | a60dfb93-255b-476d-bf28-2b4f0da285e0 | lb2_vm2 | ACTIVE | lb_net2=12.12.12.5, 10.84.57.35 | cirros-0.4.0-x86_64 | m1.tiny | | 874e675b-727b-44a2-99a9-0ff178590f86 | lb2_vm1 | ACTIVE | lb_net2=12.12.12.13, 10.84.57.39 | cirros-0.4.0-x86_64 | m1.tiny | +--------------------------------------+---------+--------+----------------------------------+---------------------+---------+Save the floating IPs of the web server VMs:
ardana >LB_VM2_FIP="10.84.57.35"ardana >LB_VM1_FIP="10.84.57.39"Use the
pingcommand on the VMs to verify that they respond on their floating IPs:ardana >ping $LB_VM2_FIP PING 10.84.57.35 (10.84.57.35) 56(84) bytes of data. 64 bytes from 10.84.57.35: icmp_seq=1 ttl=62 time=2.09 ms 64 bytes from 10.84.57.35: icmp_seq=2 ttl=62 time=0.542 ms ^C ping $LB_VM1_FIP PING 10.84.57.39 (10.84.57.39) 56(84) bytes of data. 64 bytes from 10.84.57.39: icmp_seq=1 ttl=62 time=1.55 ms 64 bytes from 10.84.57.39: icmp_seq=2 ttl=62 time=0.552 ms ^C
43.5 Create Load Balancers #
The following steps will set up new Octavia Load Balancers.
The following examples assume names and values from the previous section.
Create the load balancer on the tenant network. Use the bash variable
VIP_SUBNETthat holds the ID of the subnet that was saved earlier, or the actual subnet ID:ardana >openstack loadbalancer create --name lb2 --vip-subnet-id $VIP_SUBNET +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | admin_state_up | True | | created_at | 2019-10-29T16:28:03 | | description | | | flavor | | | id | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | listeners | | | name | lb2 | | operating_status | OFFLINE | | pools | | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | provider | amphora | | provisioning_status | PENDING_CREATE | | updated_at | None | | vip_address | 12.12.12.6 | | vip_network_id | 50a66468-084b-457f-88e4-2edb7b81851e | | vip_port_id | 5122c1d0-2996-43d5-ad9b-7b3b2c5903d5 | | vip_qos_policy_id | None | | vip_subnet_id | c141858a-a792-4c89-91f0-de4dc4694a7f | +---------------------+--------------------------------------+Save the load balancer
vip_port_id. This is used when attaching a floating IP to the load balancer.LB_PORT="5122c1d0-2996-43d5-ad9b-7b3b2c5903d5"
List load balancers. You will need to wait until the load balancer
provisioning_statusisACTIVEbefore proceeding to the next step.ardana >openstack loadbalancer list +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+ | id | name | project_id | vip_address | provisioning_status | provider | +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+ | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | lb2 | de095070f242416cb3dc4cd00e3c79f7 | 12.12.12.6 | PENDING_CREATE | amphora | +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+After some time has passed, the status will change to
ACTIVE.ardana >openstack loadbalancer list +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+ | id | name | project_id | vip_address | provisioning_status | provider | +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+ | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | lb2 | de095070f242416cb3dc4cd00e3c79f7 | 12.12.12.6 | ACTIVE | amphora | +--------------------------------------+------+----------------------------------+-------------+---------------------+----------+Once the load balancer is created, create the listener. This may take some time.
ardana >openstack loadbalancer listener create --protocol HTTP \ --protocol-port=80 --name lb2_listener lb2 +---------------------------+--------------------------------------+ | Field | Value | +---------------------------+--------------------------------------+ | admin_state_up | True | | connection_limit | -1 | | created_at | 2019-10-29T16:32:26 | | default_pool_id | None | | default_tls_container_ref | None | | description | | | id | 65930b35-70bf-47d2-a135-aff49c219222 | | insert_headers | None | | l7policies | | | loadbalancers | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | name | lb2_listener | | operating_status | OFFLINE | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol | HTTP | | protocol_port | 80 | | provisioning_status | PENDING_CREATE | | sni_container_refs | [] | | timeout_client_data | 50000 | | timeout_member_connect | 5000 | | timeout_member_data | 50000 | | timeout_tcp_inspect | 0 | | updated_at | None | +---------------------------+--------------------------------------+Create the load balancing pool. During the creation of the load balancing pool, the status for the load balancer goes to
PENDING_UPDATE. Useopenstack loadbalancer pool showto watch for the change toACTIVE. Once the load balancer returns toACTIVE, proceed with the next step.ardana >openstack loadbalancer pool create --lb-algorithm ROUND_ROBIN \ --protocol HTTP --listener lb2_listener --name lb2_pool +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | admin_state_up | True | | created_at | 2019-10-29T16:35:06 | | description | | | healthmonitor_id | | | id | 75cd42fa-0525-421f-afaa-5de996267536 | | lb_algorithm | ROUND_ROBIN | | listeners | 65930b35-70bf-47d2-a135-aff49c219222 | | loadbalancers | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | members | | | name | lb2_pool | | operating_status | OFFLINE | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol | HTTP | | provisioning_status | PENDING_CREATE | | session_persistence | None | | updated_at | None | +---------------------+--------------------------------------+Wait for the status to change to
ACTIVE.ardana >openstack loadbalancer pool show lb2_pool +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | admin_state_up | True | | created_at | 2019-10-29T16:35:06 | | description | | | healthmonitor_id | | | id | 75cd42fa-0525-421f-afaa-5de996267536 | | lb_algorithm | ROUND_ROBIN | | listeners | 65930b35-70bf-47d2-a135-aff49c219222 | | loadbalancers | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | members | | | name | lb2_pool | | operating_status | ONLINE | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol | HTTP | | provisioning_status | ACTIVE | | session_persistence | None | | updated_at | 2019-10-29T16:35:10 | +---------------------+--------------------------------------+Add the private IPs of the tenant network for the first web server in the pool:
In the previous section the addresses for the VMs were saved in the
IP_LBVM1and IP_LBVM2 bash variables. Use those variables or the or the literal addresses of the VMs.ardana >openstack loadbalancer member create --subnet $VIP_SUBNET \ --address $IP_LBVM1 --protocol-port 80 lb2_pool +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | address | 12.12.12.13 | | admin_state_up | True | | created_at | 2019-10-29T16:39:02 | | id | 3012cfa2-359c-48c1-8b6f-c650a47c2b73 | | name | | | operating_status | NO_MONITOR | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol_port | 80 | | provisioning_status | PENDING_CREATE | | subnet_id | c141858a-a792-4c89-91f0-de4dc4694a7f | | updated_at | None | | weight | 1 | | monitor_port | None | | monitor_address | None | | backup | False | +---------------------+--------------------------------------+Put the addresses the VMs have on the tenant network into the load balancer pool:
ardana >openstack loadbalancer member create --subnet $VIP_SUBNET \ --address $IP_LBVM2 --protocol-port 80 lb2_pool +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | address | 12.12.12.5 | | admin_state_up | True | | created_at | 2019-10-29T16:39:59 | | id | 3dab546b-e3ea-46b3-96f2-a7463171c2b9 | | name | | | operating_status | NO_MONITOR | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol_port | 80 | | provisioning_status | PENDING_CREATE | | subnet_id | c141858a-a792-4c89-91f0-de4dc4694a7f | | updated_at | None | | weight | 1 | | monitor_port | None | | monitor_address | None | | backup | False | +---------------------+--------------------------------------+Verify the configuration:
ardana >openstack loadbalancer list --fit-width +---------------------------+------+---------------------------+-------------+---------------------+----------+ | id | name | project_id | vip_address | provisioning_status | provider | +---------------------------+------+---------------------------+-------------+---------------------+----------+ | 2b0660e1-2901-41ea- | lb2 | de095070f242416cb3dc4cd00 | 12.12.12.6 | ACTIVE | amphora | | 93d8-d1fa590b9cfd | | e3c79f7 | | | | +---------------------------+------+---------------------------+-------------+---------------------+----------+ardana >openstack loadbalancer show lb2 --fit-width +---------------------+--------------------------------------+ | Field | Value | +---------------------+--------------------------------------+ | admin_state_up | True | | created_at | 2019-10-29T16:28:03 | | description | | | flavor | | | id | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | listeners | 65930b35-70bf-47d2-a135-aff49c219222 | | name | lb2 | | operating_status | ONLINE | | pools | 75cd42fa-0525-421f-afaa-5de996267536 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | provider | amphora | | provisioning_status | ACTIVE | | updated_at | 2019-10-29T16:40:01 | | vip_address | 12.12.12.6 | | vip_network_id | 50a66468-084b-457f-88e4-2edb7b81851e | | vip_port_id | 5122c1d0-2996-43d5-ad9b-7b3b2c5903d5 | | vip_qos_policy_id | None | | vip_subnet_id | c141858a-a792-4c89-91f0-de4dc4694a7f | +---------------------+--------------------------------------+ardana >openstack loadbalancer listener list --fit-width +-----------------+-----------------+--------------+-----------------+----------+---------------+----------------+ | id | default_pool_id | name | project_id | protocol | protocol_port | admin_state_up | +-----------------+-----------------+--------------+-----------------+----------+---------------+----------------+ | 65930b35-70bf-4 | 75cd42fa-0525 | lb2_listener | de095070f242416 | HTTP | 80 | True | | 7d2-a135-aff49c | -421f-afaa- | | cb3dc4cd00e3c79 | | | | | 219222 | 5de996267536 | | f7 | | | | +-----------------+-----------------+--------------+-----------------+----------+---------------+----------------+ardana >openstack loadbalancer listener show lb2_listener --fit-width +---------------------------+--------------------------------------+ | Field | Value | +---------------------------+--------------------------------------+ | admin_state_up | True | | connection_limit | -1 | | created_at | 2019-10-29T16:32:26 | | default_pool_id | 75cd42fa-0525-421f-afaa-5de996267536 | | default_tls_container_ref | None | | description | | | id | 65930b35-70bf-47d2-a135-aff49c219222 | | insert_headers | None | | l7policies | | | loadbalancers | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd | | name | lb2_listener | | operating_status | ONLINE | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | protocol | HTTP | | protocol_port | 80 | | provisioning_status | ACTIVE | | sni_container_refs | [] | | timeout_client_data | 50000 | | timeout_member_connect | 5000 | | timeout_member_data | 50000 | | timeout_tcp_inspect | 0 | | updated_at | 2019-10-29T16:40:01 | +---------------------------+--------------------------------------+
43.6 Create Floating IPs for Load Balancer #
To create the floating IP's for the load balancer, you will need to list
the ports for the load balancer. Once you have the port ID, you can then
create the floating IP. Notice that the name has changed between the neutron
lbass-loadbalancer and openstack loadbalancer CLI. In this case, be sure
to pick the port associated with the name octavia-lb-
or use the port ID that was saved when the load balancer was created.
Search for the load balancers port, it will be used when the floating IP is created. Alternately, use the bash variable that contains the load balancer port from the previous section. Verify the port that has the address for the load balancer:
ardana >openstack port list --fit-width +----------------------------+----------------------------+-------------------+-----------------------------+--------+ | ID | Name | MAC Address | Fixed IP Addresses | Status | +----------------------------+----------------------------+-------------------+-----------------------------+--------+ | 5122c1d0-2996-43d5-ad9b- | octavia-lb-2b0660e1-2901 | fa:16:3e:6a:59:f3 | ip_address='12.12.12.6', su | DOWN | | 7b3b2c5903d5 | -41ea-93d8-d1fa590b9cfd | | bnet_id='c141858a-a792-4c89 | | | | | | -91f0-de4dc4694a7f' | |Create the floating IP for the load balancers port:
ardana >openstack floating ip create --port $LB_PORT $EXT_NET --fit-width +---------------------+-------------------------------------------------------------------------------------------------+ | Field | Value | +---------------------+-------------------------------------------------------------------------------------------------+ | created_at | 2019-10-29T16:59:43Z | | description | | | dns_domain | | | dns_name | | | fixed_ip_address | 12.12.12.6 | | floating_ip_address | 10.84.57.29 | | floating_network_id | 2ed7deca-81ed-45ee-87ce-aeb4f565d3ad | | id | f4f18854-9d92-4eb4-8c05-96ef059b4a41 | | name | 10.84.57.29 | | port_details | {u'status': u'DOWN', u'name': u'octavia-lb-2b0660e1-2901-41ea-93d8-d1fa590b9cfd', | | | u'admin_state_up': False, u'network_id': u'50a66468-084b-457f-88e4-2edb7b81851e', | | | u'device_owner': u'Octavia', u'mac_address': u'fa:16:3e:6a:59:f3', u'device_id': u'lb- | | | 2b0660e1-2901-41ea-93d8-d1fa590b9cfd'} | | port_id | 5122c1d0-2996-43d5-ad9b-7b3b2c5903d5 | | project_id | de095070f242416cb3dc4cd00e3c79f7 | | qos_policy_id | None | | revision_number | 0 | | router_id | 1c9949fb-a500-475d-8694-346cf66ebf9a | | status | DOWN | | subnet_id | None | | tags | [] | | updated_at | 2019-10-29T16:59:43Z | +---------------------+-------------------------------------------------------------------------------------------------+Save the floating IP for the load balancer for future use.
ardana >LB_FIP="10.84.57.29"
43.7 Testing the Octavia Load Balancer #
This is the web server code that runs on the VMs created earlier. In this example, the web server is on port 80.
echo <<EOF >webserver.sh
#!/bin/sh
MYIP=$(/sbin/ifconfig eth0|grep 'inet addr'|awk -F: '{print $2}'| awk '{print $1}');
while true; do
echo -e "HTTP/1.0 200 OK
Welcome to $MYIP" | sudo nc -l -p 80
done
EOFRemove any old floating IPs from
known_hosts:ardana >ssh-keygen -R $LB_VM1_FIPardana >ssh-keygen -R $LB_VM2_FIPDeploy the web server application:
ardana >scp -o StrictHostKeyChecking=no -i lb_kp1.pem webserver.sh cirros@$LB_VM1_FIP:webserver.sh ssh -o StrictHostKeyChecking=no -i lb_kp1.pem cirros@$LB_VM1_FIP 'chmod +x ./webserver.sh' ssh -o StrictHostKeyChecking=no -i lb_kp1.pem cirros@$LB_VM1_FIP '(./webserver.sh&)' scp -o StrictHostKeyChecking=no -i lb_kp1.pem webserver.sh cirros@$LB_VM2_FIP:webserver.sh ssh -o StrictHostKeyChecking=no -i lb_kp1.pem cirros@$LB_VM2_FIP 'chmod +x ./webserver.sh' ssh -o StrictHostKeyChecking=no -i lb_kp1.pem cirros@$LB_VM2_FIP '(./webserver.sh&)'Make sure the web servers respond with the correct IPs:
ardana >curl $LB_VM1_FIP Welcome to 12.12.12.5 curl $LB_VM2_FIP Welcome to 12.12.12.5Access the web servers through the Octavia load balancer using the floating IP:
ardana >curl $LB_FIP Welcome to 12.12.12.5ardana >curl $LB_FIP Welcome to 12.12.12.13ardana >curl $LB_FIP Welcome to 12.12.12.5ardana >curl $LB_FIP
44 Other Common Post-Installation Tasks #
44.1 Determining Your User Credentials #
On your Cloud Lifecycle Manager, in the
~/scratch/ansible/next/ardana/ansible/group_vars/ directory
you will find several files. In the one labeled as first control plane node
you can locate the user credentials for both the Administrator user
(admin) and your Demo user (demo)
which you will use to perform many other actions on your cloud.
For example, if you are using the Entry-scale KVM model and used
the default naming scheme given in the example configuration files, you can
use these commands on your Cloud Lifecycle Manager to grep for your user
credentials:
Administrator
ardana > grep keystone_admin_pwd entry-scale-kvm-control-plane-1Demo
ardana > grep keystone_demo_pwd entry-scale-kvm-control-plane-144.2 Configure your Cloud Lifecycle Manager to use the command-line tools #
This playbook will do a series of steps to update your environment variables for your cloud so you can use command-line clients.
Run the following command, which will replace /etc/hosts
on the Cloud Lifecycle Manager:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts cloud-client-setup.yml
As the /etc/hosts file no longer has entries for Cloud Lifecycle Manager,
sudo commands may become a bit slower. To fix this issue, once
this step is complete, add "ardana" after "127.0.0.1 localhost". The result
will look like this:
... # Localhost Information 127.0.0.1 localhost ardana
44.3 Protect home directory #
The home directory of the user that owns the SUSE OpenStack Cloud 9 scripts should not be world readable. Change the permissions so that they are only readable by the owner:
ardana > chmod 0700 ~44.4 Back up Your SSH Keys #
As part of the cloud deployment setup process, SSH keys to access the
systems are generated and stored in ~/.ssh on your
Cloud Lifecycle Manager.
These SSH keys allow access to the subsequently deployed systems and should be included in the list of content to be archived in any backup strategy.
44.5 Retrieving Service Endpoints #
Log in to your Cloud Lifecycle Manager.
Source the keystone admin credentials:
ardana >unset OS_TENANT_NAMEardana >source ~/keystone.osrcUsing the OpenStack command-line tool you can then query the keystone service for your endpoints:
ardana >openstack endpoint listTipYou can use
openstack -hto access the client help file and a full list of commands.
To learn more about keystone, see Book “Operations Guide CLM”, Chapter 5 “Managing Identity”, Section 5.1 “The Identity Service”.
44.6 Other Common Post-Installation Tasks #
Here are the links to other common post-installation tasks that either the Administrator or Demo users can perform:
Book “Operations Guide CLM”, Chapter 6 “Managing Compute”, Section 6.4 “Enabling the Nova Resize and Migrate Features”
Book “Operations Guide CLM”, Chapter 9 “Managing Object Storage”, Section 9.1 “Running the swift Dispersion Report”
Book “Security Guide”, Chapter 4 “Service Admin Role Segregation in the Identity Service”
Part VI Support #
- 45 FAQ
Find solutions for the most common pitfalls and technical details on how to create a support request for SUSE OpenStack Cloud here.
- 46 Support
Before contacting support to help you with a problem on your cloud, it is strongly recommended that you gather as much information about your system and the problem as possible. For this purpose, SUSE OpenStack Cloud ships with a tool called supportconfig. It gathers system information such as the c…
- 47 Applying PTFs (Program Temporary Fixes) Provided by SUSE L3 Support
Under certain circumstances, SUSE Support may provide temporary fixes (called PTFs, to customers with an L3 support contract. These PTFs are provided as RPM packages. To make them available on all nodes in SUSE OpenStack Cloud, proceed as follows. If you prefer to test them first on a single node, s…
- 48 Testing PTFs (Program Temporary Fixes) on a Single Node
If you want to test a PTF (Program Temporary Fix) before deploying it on all nodes to verify that it fixes a certain issue, you can manually install the PTF on a single node.
45 FAQ #
Find solutions for the most common pitfalls and technical details on how to create a support request for SUSE OpenStack Cloud here.
1. Node Deployment
- Q: How to Disable the YaST Installer Self-Update when deploying nodes?
Prior to starting an installation, the YaST installer can update itself if respective updates are available. By default this feature is enabled. In case of problems with this feature, disable it as follows:
Open
~/openstack/ardana/ansible/roles/cobbler/templates/sles.grub.j2with an editor and addself_update=0to the line starting withlinuxefi. The results needs to look like the following:linuxefi images/{{ sles_profile_name }}-x86_64/linux ifcfg={{ item[0] }}=dhcp install=http://{{ cobbler_server_ip_addr }}:79/cblr/ks_mirror/{{ sles_profile_name }} self_update=0 AutoYaST2=http://{{ cobbler_server_ip_addr }}:79/cblr/svc/op/ks/system/{{ item[1] }}Commit your changes:
ardana >git commit -m "Disable Yast Self Update feature" \ ~/openstack/ardana/ansible/roles/cobbler/templates/sles.grub.j2If you need to reenable the installer self-update, remove
self_update=0and commit the changes.
46 Support #
Before contacting support to help you with a problem on your cloud, it is
strongly recommended that you gather as much information about your
system and the problem as possible. For this purpose, SUSE OpenStack Cloud
ships with a tool called supportconfig. It gathers
system information such as the current kernel version being used, the
hardware, RPM database, partitions, and other items.
supportconfig also collects the most important log
files, making it easier for the supporters to identify and solve your
problem.
It is recommended to always run supportconfig on the
CLM Server and on the Control Node(s). If a Compute Node or a
Storage Node is part of the problem, run
supportconfig on the affected node as well. For
details on how to run supportconfig, see
https://documentation.suse.com/sles/15-SP1/single-html/SLES-admin/#cha-adm-support.
47 Applying PTFs (Program Temporary Fixes) Provided by SUSE L3 Support #
Under certain circumstances, SUSE Support may provide temporary fixes (called PTFs, to customers with an L3 support contract. These PTFs are provided as RPM packages. To make them available on all nodes in SUSE OpenStack Cloud, proceed as follows. If you prefer to test them first on a single node, see Chapter 48, Testing PTFs (Program Temporary Fixes) on a Single Node .
Download the packages from the location provided by SUSE L3 Support to a temporary location on the CLM Server.
Move the packages from the temporary download location to the following directories on the CLM Server:
-
“noarch” packages (
*.noarch.rpm): /srv/www/suse-12.4/x86_64/repos/PTF/rpm/noarch/-
“x86_64” packages (
*.x86_64.rpm) /srv/www/suse-12.4/x86_64/repos/PTF/rpm/x86_64/
-
“noarch” packages (
Create or update the repository metadata:
ardana >sudo /usr/local/sbin/createrepo-cloud-ptfTo deploy the updates, proceed as described in Book “Operations Guide CLM”, Chapter 15 “System Maintenance”, Section 15.3 “Cloud Lifecycle Manager Maintenance Update Procedure” and refresh the PTF repository before installing package updates on a node:
ardana >sudo zypper refresh -fr PTF
48 Testing PTFs (Program Temporary Fixes) on a Single Node #
If you want to test a PTF (Program Temporary Fix) before deploying it on all nodes to verify that it fixes a certain issue, you can manually install the PTF on a single node.
In the following procedure, a PTF named
venv-openstack-nova-x86_64-ptf.rpm, containing a fix
for nova, is installed on the Compute Node 01.
Check the version number of the package(s) that will be upgraded with the PTF. Run the following command on the deployer node:
ardana >rpm -q venv-openstack-nova-x86_64Install the PTF on the deployer node:
tux >sudo zypper up ./venv-openstack-nova-x86_64-ptf.rpmThis will install a new TAR archive in
/opt/ardana_packager/ardana-8/sles_venv/x86_64/.Register the TAR archive with the indexer:
tux >sudo create_index --dir \ /opt/ardana_packager/ardana-8/sles_venv/x86_64This will update the indexer
/opt/ardana_packager/ardana-8/sles_venv/x86_64/packages.Deploy the fix on Compute Node 01:
Check whether the fix can be deployed on a single Compute Node without updating the Control Nodes:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts nova-upgrade.yml \ --limit=inputmodel-ccp-compute0001-mgmt --list-hostsIf the previous test passes, install the fix:
ardana >ansible-playbook -i hosts/verb_hosts nova-upgrade.yml \ --limit=inputmodel-ccp-compute0001-mgmt
Validate the fix, for example by logging in to the Compute Node to check the log files:
ardana >ssh ardana@inputmodel-ccp-compute0001-mgmtIn case your tests are positive, install the PTF on all nodes as described in Chapter 47, Applying PTFs (Program Temporary Fixes) Provided by SUSE L3 Support .
In case the test are negative uninstall the fix and restore the previous state of the Compute Node by running the following commands on the deployer node;
tux >sudo zypper install --force venv-openstack-nova-x86_64-OLD-VERSIONardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/verb_hosts nova-upgrade.yml \ --limit=inputmodel-ccp-compute0001-mgmtMake sure to replace OLD-VERSION with the version number you checked in the first step.