4 Component model #
This section describes the various components being used to create a Rancher Kubernetes Engine solution deployment, in the perspective of top to bottom ordering. When completed, the Rancher Kubernetes Engine instance can be used as the application infrastructure for cloud-native workloads and can be imported into SUSE Rancher for management.
4.1 Component overview #
By using:
Kubernetes Platform - Rancher Kubernetes Engine
Operating System - SUSE Linux Enterprise Server
Compute Platform
Supermicro Supermicro SuperServer
you can create the necessary infrastructure and services. Further details for these components are described in the following sections.
4.2 Software - Rancher Kubernetes Engine #
Rancher Kubernetes Engine is a CNCF-certified Kubernetes distribution that runs entirely within Docker containers. It solves the common frustration of installation complexity with Kubernetes by removing most host dependencies and presenting a stable path for deployment, upgrades, and rollbacks.
With Rancher Kubernetes Engine [RKE], the operation of Kubernetes is easily automated and entirely independent of the operating system and platform you are running. As long as you can run a supported version of Docker, you can deploy and run Kubernetes with RKE. It builds a cluster from a single command in a few minutes, and its declarative configuration makes Kubernetes upgrades atomic and safe.
- What is provided with Rancher Kubernetes Engine
CNCF Certification
Rancher Kubernetes Engine CNCF certification means that every release supports the same APIs as upstream Kubernetes. This gives enterprises the confidence that their Kubernetes resources are portable between RKE and other CNCF-certified Kubernetes distributions.
Simplified installation
Installation is via a single binary and it uses a single YAML file, meaning that even non-experts can deploy Kubernetes with a single command. The command connects to remote hosts via SSH, so Rancher or any staff member with SSH access can deploy and manage RKE instances anywhere in the world.
Automated Operation
When used with SUSE Rancher, operators can perform automated installation and upgrades of RKE clusters with a few clicks.
Vendor Independence
RKE is not locked into a specific vendor operating system, Kubernetes Management Platform or proprietary tooling.
Safe, Atomic Upgrades
Since RKE is built using containers, it does not have any touch points with the underlying operating system beyond the container engine. Containers make it easy to upgrade to a new version and to roll back to the previous version if necessary.
24x7 Enterprise-level Support
Ensures around-the-clock support from technical experts when you need it.
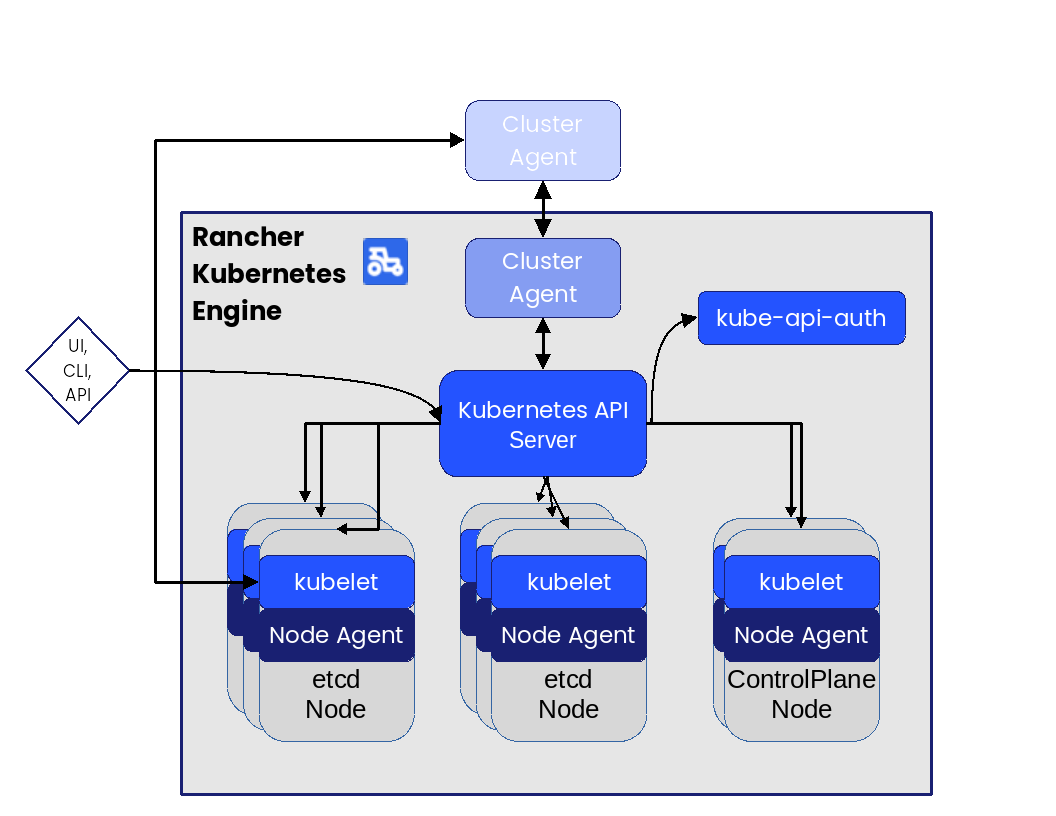
The fundamental roles for the nodes and core functionality of Rancher Kubernetes Engine are represented in the following figure:
Kubernetes API Server,
interacts with kubelet on all the nodes, plus addresses authentication, user interface (UI), command line interface (CLI) and API for external access and cluster management via SUSE Rancher cluster controller to agent
While all Rancher Kubernetes Engine roles can be installed on a single system, for the best availability, performance and security, the recommended deployment of a Rancher Kubernetes Engine cluster is a pair of nodes for the control plane role, at least three etcd role-based nodes and three or more worker nodes.
Rancher Kubernetes Engine can run as a complete cluster on a single node or can be expanded into a multi-node cluster. Besides the core Kubernetes components, these are also configurable and included:
Multiple Kubernetes versions
CoreDNS, Metrics, Ingress controller
CNI : Canal, Calico, Flannel, Weave
Support for a Windows worker agent node (only with Flannel)
Fleet Agent : for GitOps deployment of cloud-native applications
All of these components are configurable and can be swapped out for your implementation of choice. With these included components, you get a fully functional and CNCF-conformant cluster so you can start running apps right away.
Learn more information about Rancher Kubernetes Engine at https://rancher.com/docs/rke/latest/en/.
While all Rancher Kubernetes Engine roles can be installed on a single system, a multi-node cluster, is a more production-like approach and will be described in the deployment section.
To improve availability, performance and security, the recommended deployment of a Rancher Kubernetes Engine cluster is a pair of nodes for the control plane role, at least three etcd role-based nodes and three or more worker nodes.
4.3 Software - SUSE Linux Enterprise Server #
SUSE Linux Enterprise Server (SLES) is an adaptable and easy-to-manage platform that allows developers and administrators to deploy business-critical workloads on-premises, in the cloud and at the edge. It is a Linux operating system that is adaptable to any environment – optimized for performance, security and reliability. As a multimodal operating system that paves the way for IT transformation in the software-defined era, this simplifies multimodal IT, makes traditional IT infrastructure efficient and provides an engaging platform for developers. As a result, one can easily deploy and transition business-critical workloads across on-premises and public cloud environments.
Designed for interoperability, SUSE Linux Enterprise Server integrates into classical Unix and Windows environments, supports open standard interfaces for systems management, and has been certified for IPv6 compatibility. This modular, general purpose operating system runs on four processor architectures and is available with optional extensions that provide advanced capabilities for tasks such as real time computing and high availability clustering. SUSE Linux Enterprise Server is optimized to run as a high performing guest on leading hypervisors and supports an unlimited number of virtual machines per physical system with a single subscription. This makes it the perfect guest operating system for virtual computing.
4.4 Compute Platform #
Leveraging the enterprise grade functionality of the operating system mentioned in the previous section, many compute platforms can be the foundation of the deployment:
Virtual machines on supported hypervisors or hosted on cloud service providers
Physical, baremetal or single-board computers, either on-premises or hosted by cloud service providers
To complete self-testing of hardware with SUSE YES Certified Process, you can download and install the respective SUSE operating system support-pack version of SUSE Linux Enterprise Server and the YES test suite. Then run the tests per the instructions in the test kit, fixing any problems encountered and when corrected, re-run all tests to obtain clean test results. Submit the test results into the SUSE Bulletin System (SBS) for audit, review and validation.
Certified systems and hypervisors can be verified via SUSE YES Certified Bulletins and then can be leveraged as supported nodes for this deployment, as long as the certification refers to the respective version of the underlying SUSE operating system required.
Supermicro servers take advantage of the latest CPU technologies available. The new servers have been shown to produce more work per watt than ever before. Thus, additional workloads can not only be performed in less time, but at a lower cost as well. Supermicro systems can support up to 6TB of memory per socket.
4.4.1 SYS-120C-TN10R Rack Servers #
The Supermicro SYS-120C-TN10R is SUSE YES Certified Hardware.
The SYS-120C-TN10R Rack Servers provide the following attributes:
CPU: Up to 270W and 40 cores
Memory: 4TB DDR4-3200 memory in 16 DIMM slots w/ support of Intel Optane PMEM 200 series
Storage: Up to 10x all hybrid drive bays (NVMe/SAS/SATA) + Flexible internal storage options (dual NVMe M.2 / SATADOM)
Expansion: Up to 2 standard PCIe 4.0 FHHL expansion slots + 2 AIOM for OCP 3.0 NIC; Building block solution for different applications and environment
860W Platinum level redundant PWS
Cost optimized for large volume deployment
Tool-less mechanical design for rapid deployment
Hot-swap storage and PWS for easy maintenance.
IPMI, serial port and service tag for easy management
Compact system design makes no waste of internal space
< 600mm chassis depth
Fully utilized system resource with 12 NVMe, 4 PCIe 4.0 x16 + 2 PCIe 4.0 x8 expansion
Security is top priority
TPM 1.2/2.0, signed firmware, Silicon Root of Trust
Secure Boot, System Erase
FIPS Compliance, Trusted Execution Environment
Balanced architecture between CPUs and optimized for scalable compute, database, GPU, tiered storage and I/O intensive applications
Support open standards like OpenBMC and OCP 3.0
Optimized thermal design
High efficiency Platinum level PWS (AC/DC)
Reduced waste with bulk packaging and customizable accessories
4.4.2 SYS-620C-TN12R Rack Servers #
The Supermicro SYS-620C-TN12R is SUSE YES Certified Hardware.
The SYS-620C-TN12R Rack Servers provide the following attributes:
CPU: Up to 270W and 40 cores
Memory: 4TB DDR4-3200 memory in 16 DIMM slots w/ support of Intel Optane PMEM 200 series
Storage: Up to 12 all hybrid drive bays (NVMe/SAS/SATA) + Flexible internal storage options (dual NVMe M.2 / SATADOM)
Expansion: Up to 6 standard PCIe 4.0 expansion slots + 2 AIOM for OCP 3.0 NIC; Up to 2 FHFL DW GPUs or 6 LP GPUs
Building block solution for different applications and environment
1200W Titanium level redundant PWS
Cost optimized for large volume deployment
Tool-less mechanical design for rapid deployment
Hot-swap storage and PWS for easy maintenance.
IPMI, serial port and service tag for easy management
Compact system design makes no waste of internal space
< 650mm chassis depth
Fully utilized system resource with 12 NVMe, 4 PCIe 4.0 x16 + 2 PCIe 4.0 x8 expansion
Security is top priority
TPM 1.2/2.0, signed firmware, Silicon Root of Trust
Secure Boot, System Erase
FIPS Compliance, Trusted Execution Environment
Balanced architecture between CPUs and optimized for scalable compute, database, GPU, tiered storage and I/O intensive applications
Cost and performance optimized down to component level
Support open standards like OpenBMC and OCP 3.0
Optimized thermal design
High efficiency Titanium level PWS (AC/DC)
Reduced waste with bulk packaging and customizable accessories
A sample bill of materials, in the Chapter 9, Appendix, cites the necessary quantities of all components, along with a reference to the minimum resource requirements needed by the software components.