4 Component model #
This section describes the various components being used to create a Rancher Kubernetes Engine Government solution deployment, in the perspective of top to bottom ordering. When completed, the Rancher Kubernetes Engine Government instance can be used as the application infrastructure for cloud-native workloads and can be imported into SUSE Rancher for management.
4.1 Component overview #
By using:
Kubernetes Platform - Rancher Kubernetes Engine Government
Operating System - SUSE Linux Enterprise Server
Compute Platform
you can create the necessary infrastructure and services. Further details for these components are described in the following sections.
4.2 Software - Rancher Kubernetes Engine Government #
Rancher Kubernetes Engine Government also known as RKE2, is Rancher’s next-generation Kubernetes distribution. It is a fully conformant Kubernetes distribution that focuses on security and compliance within the U.S. Federal Government sector. It solves the common frustration of installation complexity with Kubernetes by removing most host dependencies and presenting a stable path for deployment, upgrades, and rollbacks.
To meet these goals, Rancher Kubernetes Engine Government does the following:
launches control plane components as static pods, managed by the kubelet. The embedded container runtime is containerd.
provides defaults and configuration options that allow clusters to pass the CIS Kubernetes Benchmark v1.5 or v1.6 with minimal operator intervention
enables FIPS 140-2 compliance
regularly scans components for CVEs using trivy in our build pipeline
With Rancher Kubernetes Engine Government we take lessons learned from developing and maintaining our lightweight Kubernetes distribution, K3s, and apply them to build an enterprise-ready distribution with K3s ease-of-use. What this means is that Rancher Kubernetes Engine Government is, at its simplest, a single binary to be installed and configured on all nodes expected to participate in the Kubernetes cluster. When started, Rancher Kubernetes Engine Government is then able to bootstrap and supervise role-appropriate agents per node while sourcing needed content from the network.
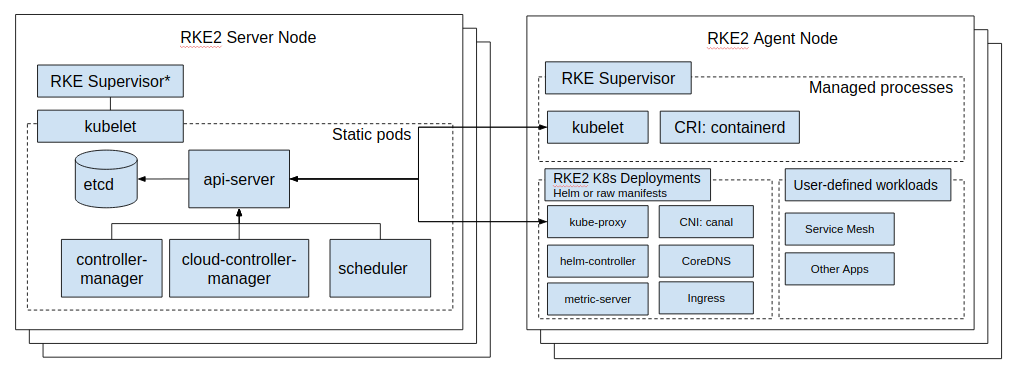
The fundamental roles for the nodes and core functionality of Rancher Kubernetes Engine Government are represented in the following figure:
Rancher Kubernetes Engine Government brings together several open source technologies to make this all work:
K3s - Helm Controller
Kubernetes
API Server
Controller Manager
Kubelet
Scheduler
Proxy
etcd
Container Runtime - runc, containerd/cri
CoreDNS
NGINX Ingress Controller
Metrics Server
Helm
All of these, except the NGINX Ingress Controller, are compiled and statically linked with [4]
While all Rancher Kubernetes Engine Government roles can be installed on a single system, for the best availability, performance and security, the recommended deployment of a Rancher Kubernetes Engine Government cluster is a pair of nodes for the control plane role, at least three etcd role-based nodes and three or more worker nodes.
Rancher Kubernetes Engine Government can run as a complete cluster on a single node or can be expanded into a multi-node cluster. Besides the core Kubernetes components, these are also configurable and included:
Multiple Kubernetes versions
CoreDNS, Metrics, Ingress controller
CNI: Canal (Calico & Flannel), Cilium or Calico
Fleet Agent : for GitOps deployment of cloud-native applications
All of these components are configurable and can be swapped out for your implementation of choice. With these included components, you get a fully functional and CNCF-conformant cluster so you can start running apps right away.
Learn more information about Rancher Kubernetes Engine Government at https://documentation.suse.com/cloudnative/rke2/.
While all Rancher Kubernetes Engine Government roles can be installed on a single system, a multi-node cluster, is a more production-like approach and will be described in the deployment section.
To improve availability, performance and security, the recommended deployment of a Rancher Kubernetes Engine Government cluster is a pair of nodes for the control plane role, at least three etcd role-based nodes and three or more worker nodes.
4.3 Software - SUSE Linux Enterprise Server #
SUSE Linux Enterprise Server (SLES) is an adaptable and easy-to-manage platform that allows developers and administrators to deploy business-critical workloads on-premises, in the cloud and at the edge. It is a Linux operating system that is adaptable to any environment – optimized for performance, security and reliability. As a multimodal operating system that paves the way for IT transformation in the software-defined era, this simplifies multimodal IT, makes traditional IT infrastructure efficient and provides an engaging platform for developers. As a result, one can easily deploy and transition business-critical workloads across on-premises and public cloud environments.
Designed for interoperability, SUSE Linux Enterprise Server integrates into classical Unix and Windows environments, supports open standard interfaces for systems management, and has been certified for IPv6 compatibility. This modular, general purpose operating system runs on four processor architectures and is available with optional extensions that provide advanced capabilities for tasks such as real time computing and high availability clustering. SUSE Linux Enterprise Server is optimized to run as a high performing guest on leading hypervisors and supports an unlimited number of virtual machines per physical system with a single subscription. This makes it the perfect guest operating system for virtual computing.
4.4 Compute Platform #
Leveraging the enterprise grade functionality of the operating system mentioned in the previous section, many compute platforms can be the foundation of the deployment:
Virtual machines on supported hypervisors or hosted on cloud service providers
Physical, baremetal or single-board computers, either on-premises or hosted by cloud service providers
To complete self-testing of hardware with SUSE YES Certified Process, you can download and install the respective SUSE operating system support-pack version of SUSE Linux Enterprise Server and the YES test suite. Then run the tests per the instructions in the test kit, fixing any problems encountered and when corrected, re-run all tests to obtain clean test results. Submit the test results into the SUSE Bulletin System (SBS) for audit, review and validation.
Certified systems and hypervisors can be verified via SUSE YES Certified Bulletins and then can be leveraged as supported nodes for this deployment, as long as the certification refers to the respective version of the underlying SUSE operating system required.