13 Managing Networks #
This chapter describes common network configurations for a VM Host Server,
including those supported natively by the VM Host Server and libvirt. The
configurations are valid for all hypervisors supported by SUSE Linux Enterprise Server,
such as KVM or Xen.
There are two common network configurations to provide a VM Guest with a network connection:
A network bridge acting as a Layer 2 switch
A virtual network managed by
libvirtwith Layer 3 forwarding enabled
13.1 Network Bridge #
The network bridge configuration provides a Layer 2 switch for VM Guests, switching Layer 2 Ethernet packets between ports on the bridge based on MAC addresses associated with the ports. This gives the VM Guest Layer 2 access to the VM Host Server's network. This configuration is analogous to connecting the VM Guest's virtual Ethernet cable into a hub that is shared with the host and other VM Guests running on the host. The configuration is often referred to as shared physical device.
The network bridge configuration is the default configuration of SUSE Linux Enterprise Server when configured as a KVM or Xen hypervisor. It is the preferred configuration when you simply want to connect VM Guests to the VM Host Server's LAN.
13.1.1 Managing Network Bridges with YaST #
This section includes procedures to add or remove network bridges with YaST.
13.1.1.1 Adding a Network Bridge #
To add a network bridge on VM Host Server, follow these steps:
Start › › .
Activate the tab and click .
Select from the list and enter the bridge device interface name in the entry. Press the button to proceed.
In the tab, specify networking details such as DHCP/static IP address, subnet mask or host name.
Using is only useful when also assigning a device to a bridge that is connected to a DHCP server.
If you intend to create a virtual bridge that has no connection to a real Ethernet device, use . In this case, it is a good idea to use addresses from the private IP address ranges, for example,
192.168.0.0/16,172.16.0.0/12, or10.0.0.0/8.To create a bridge that should only serve as a connection between the different guests without connection to the host system, set the IP address to
0.0.0.0and the subnet mask to255.255.255.255. The network scripts handle this special address as an unset IP address.Activate the tab and activate the network devices you want to include in the network bridge.
Click to return to the tab and confirm with . The new network bridge should now be active on VM Host Server.
13.1.1.2 Deleting a Network Bridge #
To delete an existing network bridge, follow these steps:
Start › › .
Select the bridge device you want to delete from the list in the tab.
Delete the bridge with and confirm with .
13.1.2 Managing Network Bridges from the Command Line #
This section includes procedures to add or remove network bridges using the command line.
13.1.2.1 Adding a Network Bridge #
To add a new network bridge device on VM Host Server, follow these steps:
Log in as
rooton the VM Host Server where you want to create a new network bridge.Choose a name for the new bridge—virbr_test in our example—and run
tux >sudoip link add name VIRBR_TEST type bridgeCheck if the bridge was created on VM Host Server:
tux >sudobridge vlan [...] virbr_test 1 PVID Egress Untaggedvirbr_testis present, but is not associated with any physical network interface.Bring the network bridge up and add a network interface to the bridge:
tux >sudoip link set virbr_test uptux >sudoip link set eth1 master virbr_testImportant: Network Interface Must Be UnusedYou can only assign a network interface that is not yet used by other network bridge.
Optionally, enable STP (see Spanning Tree Protocol):
tux >sudobridge link set dev virbr_test cost 4
13.1.2.2 Deleting a Network Bridge #
To delete an existing network bridge device on VM Host Server from the command line, follow these steps:
Log in as
rooton the VM Host Server where you want to delete an existing network bridge.List existing network bridges to identify the name of the bridge to remove:
tux >sudobridge vlan [...] virbr_test 1 PVID Egress UntaggedDelete the bridge:
tux >sudoip link delete dev virbr_test
13.1.3 Using VLAN Interfaces #
Sometimes, it is necessary to create a private connection either between two VM Host Servers or between VM Guest systems. For example, to migrate VM Guest to hosts in a different network segment, or to create a private bridge that only VM Guest systems may connect to (even when running on different VM Host Server systems). An easy way to build such connections is to set up VLAN networks.
VLAN interfaces are commonly set up on the VM Host Server. They either interconnect the different VM Host Server systems, or they may be set up as a physical interface to an otherwise virtual-only bridge. It is even possible to create a bridge with a VLAN as a physical interface that has no IP address in the VM Host Server. That way, the guest systems have no possibility to access the host over this network.
Run the YaST module › . Follow this procedure to set up the VLAN device:
Click to create a new network interface.
In the , select .
Change the value of to the ID of your VLAN. Note that VLAN ID
1is commonly used for management purposes.Click .
Select the interface that the VLAN device should connect to below . If the desired interface does not appear in the list, first set up this interface without an IP address.
Select the desired method for assigning an IP address to the VLAN device.
Click to finish the configuration.
It is also possible to use the VLAN interface as a physical interface of a bridge. This makes it possible to connect several VM Host Server-only networks and allows live migration of VM Guest systems that are connected to such a network.
YaST does not always allow setting no IP address. However, this may be a
desired feature, especially if VM Host Server-only networks should be connected.
In this case, use the special address 0.0.0.0 with
netmask 255.255.255.255. The system scripts handle this
address as no IP address set.
13.2 Virtual Networks #
libvirt-managed virtual networks are similar to bridged networks, but
typically have no Layer 2 connection to the VM Host Server. Connectivity to the
VM Host Server's physical network is accomplished with Layer 3 forwarding, which
introduces additional packet processing on the VM Host Server as compared to a
Layer 2 bridged network. Virtual networks also provide DHCP and DNS services
for VM Guests. For more information on libvirts virtual networks see the
Network XML format documentation at
https://libvirt.org/formatnetwork.html.
A standard libvirt installation on SUSE Linux Enterprise Server already comes with a
predefined virtual network named default that provides
DHCP and DNS services for the network, along with connectivity to the
VM Host Server's physical network using the network address translation (NAT)
forwarding mode. Although it is predefined, the default
virtual network must be explicitly enabled by the administrator. For more
information on the forwarding modes supported by libvirt see the
Connectivity section of the Network XML
format documentation at
https://libvirt.org/formatnetwork.html#elementsConnect.
libvirt-managed virtual networks can be used to satisfy a wide range of
use-cases, but are commonly used on VM Host Servers that have a wireless
connection or dynamic/sporadic network connectivity such as laptops. Virtual
networks are also useful when the VM Host Server's network has limited IP
addresses, allowing forwarding of packets between the virtual network and
the VM Host Server's network. However, most server use-cases are better suited for
the network bridge configuration, where VM Guests are connected to the
VM Host Server's LAN.
Enabling forwarding mode in a libvirt virtual network enables forwarding
in the VM Host Server by setting
/proc/sys/net/ipv4/ip_forward and
/proc/sys/net/ipv6/conf/all/forwarding to 1, which
essentially turns the VM Host Server into a router. Restarting the VM Host Server's
network may reset the values and disable forwarding. To avoid this
behavior, explicitly enable forwarding in the VM Host Server by editing the
/etc/sysctl.conf file and adding:
net.ipv4.ip_forward = 1
net.ipv6.conf.all.forwarding = 1
13.2.1 Managing Virtual Networks with Virtual Machine Manager #
You can define, configure, and operate virtual networks with Virtual Machine Manager.
13.2.1.1 Defining Virtual Networks #
Start Virtual Machine Manager. In the list of available connections, right-click the name of the connection for which you need to configure the virtual network, and then select .
In the window, click the tab. You can see the list of all virtual networks available for the current connection. On the right, there are details of the selected virtual network.
Figure 13.1: Connection Details #To add a new virtual network, click .
Specify a name for the new virtual network and click .
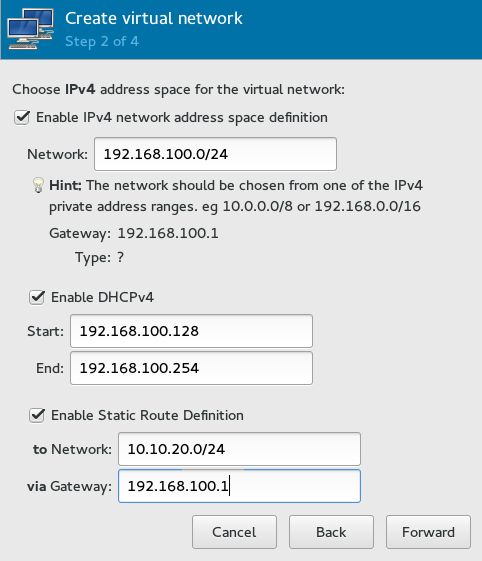
Figure 13.2: Create virtual network #To specify an IPv4 network address space definition, activate the relevant option and type it into the text entry.
Figure 13.3: Create virtual network #libvirtcan provide your virtual network with a DHCP server. If you need it, activate , then type the start and end IP address range of assignable addresses.To enable static routing for the new virtual network, activate the relevant option and type the network and gateway addresses.
Click to proceed.
To specify IPv6-related options—network address space, DHCPv6 server, or static route—activate and activate the relevant options and fill in the relevant boxes.
Click to proceed.
Select whether you want an isolated or forwarded virtual network.
Figure 13.4: Create virtual network #For forwarded networks, specify the network interface to which the requests will be forwarded, and one of the forwarding modes: While (network address translation) remaps the virtual network address space and allows sharing a single IP address, forwards packets from the virtual network to the VM Host Server's physical network with no translation.
If you did not specify an IPv6 network address space definition earlier, you can enable IPv6 internal routing between virtual machines.
(Optional) Optionally, change the DNS domain name.
Click to create the new virtual network. On the VM Host Server, a new virtual network bridge
virbrXis available, which corresponds to the newly-created virtual network. You can check withbridge link.libvirtautomatically adds iptables rules to allow traffic to/from guests attached to the new virbrX device.
13.2.1.2 Starting Virtual Networks #
To start a virtual network that is temporarily stopped, follow these steps:
Start Virtual Machine Manager. In the list of available connections, right-click the name of the connection for which you need to configure the virtual network, and then select .
In the window, click the tab. You can see the list of all virtual networks available for the current connection.
To start the virtual network, click .
13.2.1.3 Stopping Virtual Networks #
To stop an active virtual network, follow these steps:
Start Virtual Machine Manager. In the list of available connections, right-click the name of the connection for which you need to configure the virtual network, and then select .
In the window, click the tab. You can see the list of all virtual networks available for the current connection.
Select the virtual network to be stopped, then click .
13.2.1.4 Deleting Virtual Networks #
To delete a virtual network from VM Host Server, follow these steps:
Start Virtual Machine Manager. In the list of available connections, right-click the name of the connection for which you need to configure the virtual network, and then select .
In the window, click the tab. You can see the list of all virtual networks available for the current connection.
Select the virtual network to be deleted, then click .
13.2.1.5 Obtaining IP Addresses with nsswitch for NAT Networks (in KVM) #
On VM Host Server, install libvirt-nss, which provides NSS support for libvirt:
tux >sudozypper in libvirt-nssAdd
libvirtto/etc/nsswitch.conf:... hosts: files libvirt mdns_minimal [NOTFOUND=return] dns ...
If NSCD is running, restart it:
tux >sudosystemctl restart nscd
Now you can reach the guest system by name from the host.
The NSS module has limited functionality. It reads
/var/lib/libvirt/dnsmasq/*.status files to find the
host name and corresponding IP addresses in a JSON record describing each
lease provided by dnsmasq. Host name translation can
only be done on those VM Host Servers using a libvirt-managed bridged network
backed by dnsmasq.
For more information, see http://wiki.libvirt.org/page/NSS_module.
13.2.2 Managing Virtual Networks with virsh #
You can manage libvirt-provided virtual networks with the
virsh command line tool. To view all network related
virsh commands, run
tux >sudovirsh help network Networking (help keyword 'network'): net-autostart autostart a network net-create create a network from an XML file net-define define (but don't start) a network from an XML file net-destroy destroy (stop) a network net-dumpxml network information in XML net-edit edit XML configuration for a network net-event Network Events net-info network information net-list list networks net-name convert a network UUID to network name net-start start a (previously defined) inactive network net-undefine undefine an inactive network net-update update parts of an existing network's configuration net-uuid convert a network name to network UUID
To view brief help information for a specific virsh
command, run virsh help
VIRSH_COMMAND:
tux >sudovirsh help net-create NAME net-create - create a network from an XML file SYNOPSIS net-create <file> DESCRIPTION Create a network. OPTIONS [--file] <string> file containing an XML network description
13.2.2.1 Creating a Network #
To create a new running virtual network, run
tux >sudovirsh net-create VNET_DEFINITION.xml
The VNET_DEFINITION.xml XML file includes the
definition of the virtual network that libvirt accepts.
To define a new virtual network without activating it, run
tux >sudovirsh net-define VNET_DEFINITION.xml
The following examples illustrate definitions of different types of virtual networks.
The following configuration allows VM Guests outgoing connectivity if it is available on VM Host Server. In the absence of VM Host Server networking, it allows guests to talk directly to each other.
<network> <name>vnet_nated</name>1 <bridge name="virbr1"/>2 <forward mode="nat"/>3 <ip address="192.168.122.1" netmask="255.255.255.0">4 <dhcp> <range start="192.168.122.2" end="192.168.122.254"/>5 <host mac="52:54:00:c7:92:da" name="host1.testing.com" \ ip="192.168.1.23.101"/>6 <host mac="52:54:00:c7:92:db" name="host2.testing.com" \ ip="192.168.1.23.102"/> <host mac="52:54:00:c7:92:dc" name="host3.testing.com" \ ip="192.168.1.23.103"/> </dhcp> </ip> </network>
The name of the new virtual network. | |
The name of the bridge device used to construct the virtual network.
When defining a new network with a <forward> mode of "nat" or
"route" (or an isolated network with no <forward> element),
| |
Inclusion of the <forward> element indicates that the virtual
network will be connected to the physical LAN. The
| |
The IP address and netmask for the network bridge. | |
Enable DHCP server for the virtual network, offering IP addresses
ranging from the specified | |
The optional <host> elements specify hosts that will be given
names and predefined IP addresses by the built-in DHCP server. Any IPv4
host element must specify the following: the MAC address of the host to
be assigned a given name, the IP to be assigned to that host, and the
name to be given to that host by the DHCP server. An IPv6 host element
differs slightly from that for IPv4: there is no |
The following configuration routes traffic from the virtual network to the LAN without applying any NAT. The IP address range must be preconfigured in the routing tables of the router on the VM Host Server network.
<network>
<name>vnet_routed</name>
<bridge name="virbr1"/>
<forward mode="route" dev="eth1"/>1
<ip address="192.168.122.1" netmask="255.255.255.0">
<dhcp>
<range start="192.168.122.2" end="192.168.122.254"/>
</dhcp>
</ip>
</network>
The guest traffic may only go out via the |
This configuration provides a completely isolated private network. The guests can talk to each other, and to VM Host Server, but cannot reach any other machines on the LAN, as the <forward> element is missing in the XML description.
<network> <name>vnet_isolated</name> <bridge name="virbr3"/> <ip address="192.168.152.1" netmask="255.255.255.0"> <dhcp> <range start="192.168.152.2" end="192.168.152.254"/> </dhcp> </ip> </network>
This configuration shows how to use an existing VM Host Server's network bridge
br0. VM Guests are directly connected to the physical
network. Their IP addresses will all be on the subnet of the physical
network, and there will be no restrictions on incoming or outgoing
connections.
<network>
<name>host-bridge</name>
<forward mode="bridge"/>
<bridge name="br0"/>
</network>13.2.2.2 Listing Networks #
To list all virtual networks available to libvirt, run:
tux >sudovirsh net-list --all Name State Autostart Persistent ---------------------------------------------------------- crowbar active yes yes vnet_nated active yes yes vnet_routed active yes yes vnet_isolated inactive yes yes
To list available domains, run:
tux >sudovirsh list Id Name State ---------------------------------------------------- 1 nated_sles12sp5 running ...
To get a list of interfaces of a running domain, run domifaddr
DOMAIN, or optionally specify the
interface to limit the output to this interface. By default, it
additionally outputs their IP and MAC addresses:
tux >sudovirsh domifaddr nated_sles12sp5 --interface vnet0 --source lease Name MAC address Protocol Address ------------------------------------------------------------------------------- vnet0 52:54:00:9e:0d:2b ipv6 fd00:dead:beef:55::140/64 - - ipv4 192.168.100.168/24
To print brief information of all virtual interfaces associated with the specified domain, run:
tux >sudovirsh domiflist nated_sles12sp5 Interface Type Source Model MAC --------------------------------------------------------- vnet0 network vnet_nated virtio 52:54:00:9e:0d:2b
13.2.2.3 Getting Details about a Network #
To get detailed information about a network, run:
tux >sudovirsh net-info vnet_routed Name: vnet_routed UUID: 756b48ff-d0c6-4c0a-804c-86c4c832a498 Active: yes Persistent: yes Autostart: yes Bridge: virbr5
13.2.2.4 Starting a Network #
To start an inactive network that was already defined, find its name (or unique identifier, UUID) with:
tux >sudovirsh net-list --inactive Name State Autostart Persistent ---------------------------------------------------------- vnet_isolated inactive yes yes
Then run:
tux >sudovirsh net-start vnet_isolated Network vnet_isolated started
13.2.2.5 Stopping a Network #
To stop an active network, find its name (or unique identifier, UUID) with:
tux >sudovirsh net-list --inactive Name State Autostart Persistent ---------------------------------------------------------- vnet_isolated active yes yes
Then run:
tux >sudovirsh net-destroy vnet_isolated Network vnet_isolated destroyed
13.2.2.6 Removing a Network #
To remove the definition of an inactive network from VM Host Server permanently, run:
tux >sudovirsh net-undefine vnet_isolated Network vnet_isolated has been undefined