39 Gathering system information for support #
For a quick overview of all relevant system information of a machine,
SUSE Linux Enterprise Server offers the
hostinfo package. It also helps
system administrators to check for tainted kernels (that are not supported)
or any third-party packages installed on a machine.
In case of problems, a detailed system report may be created with either
the supportconfig command line tool or the YaST
module. Both will collect information about the
system such as: current kernel version, hardware, installed packages,
partition setup, and much more. The result is a TAR archive of files. After
opening a Service Request (SR), you can upload the TAR archive to Global
Technical Support. It will help to locate the issue you reported and to
assist you in solving the problem.
Additionally, you can analyze the supportconfig output
for known issues to help resolve problems faster. For this purpose,
SUSE Linux Enterprise Server provides both an appliance and a command line tool for
Supportconfig Analysis (SCA).
39.1 Displaying current system information #
For a quick and easy overview of all relevant system information when
logging in to a server, use the package
hostinfo. After it has been
installed on a machine, the console displays the following information to
any root user that logs in to this machine:
hostinfo when logging in as root #Welcome to SUSE Linux Enterprise Server 15 SP2 Snapshot8 (x86_64) - Kernel \r (\l). Distribution: SUSE Linux Enterprise Server 15 SP2 Current As Of: Wed 25 Mar 2020 12:09:20 PM PDT Hostname: localhost Kernel Version: 5.3.18-8-default Architecture: x86_64 Installed: Thu 19 Mar 2020 11:25:13 AM PDT Status: Not Tainted Last Installed Package: Wed 25 Mar 2020 11:42:24 AM PDT Patches Needed: 0 Security: 0 3rd Party Packages: 219 Network Interfaces eth0: 192.168.2/24 2002:c0a8:20a::/64 Memory Total/Free/Avail: 7.4Gi/6.4Gi/6.8Gi (91% Avail) CPU Load Average: 7 (3%) with 2 CPUs
In case the output shows a tainted kernel status, see
Section 39.6, “Support of kernel modules” for more details.
39.2 Collecting system information with supportconfig #
To create a TAR archive with detailed system information that you can hand over to Global Technical Support, use either:
the command
supportconfigor,the YaST module.
The command line tool is provided by the
package supportutils which is installed by default.
The YaST module is also based on the command
line tool.
Depending on which packages are installed on your system, some of these
packages integrate Supportconfig plug-ins. When Supportconfig is executed,
all plug-ins are executed as well and create one or more result files for
the archive. That has the benefit that the only topics checked are those
that contain a specific plug-in for them. Supportconfig plug-ins are stored
in the directory /usr/lib/supportconfig/plugins/.
39.2.1 Creating a service request number #
Supportconfig archives can be generated at any time. However, for handing over the Supportconfig data to Global Technical Support, you need to generate a service request number first. You will need it to upload the archive to support.
To create a service request, go to https://scc.suse.com/support/requests and follow the instructions on the screen. Write down the service request number.
SUSE treats system reports as confidential data. For details about our privacy commitment, see https://www.suse.com/company/policies/privacy/.
39.2.2 Upload targets #
After having created a service request number, you can upload your Supportconfig archives to Global Technical Support as described in Procedure 39.1, “Submitting information to support with YaST” or Procedure 39.2, “Submitting information to support from command line”. Use one of the following upload targets:
North America: FTP ftp://support-ftp.us.suse.com/incoming/, FTPS ftps://support-ftp.us.suse.com/incoming/
EMEA, Europe, the Middle East, and Africa: FTP ftp://support-ftp.emea.suse.com/incoming, FTPS ftps://support-ftp.emea.suse.com/incoming
Alternatively, you can manually attach the TAR archive to your service request using the service request URL: https://scc.suse.com/support/requests.
39.2.3 Creating a supportconfig archive with YaST #
To use YaST to gather your system information, proceed as follows:
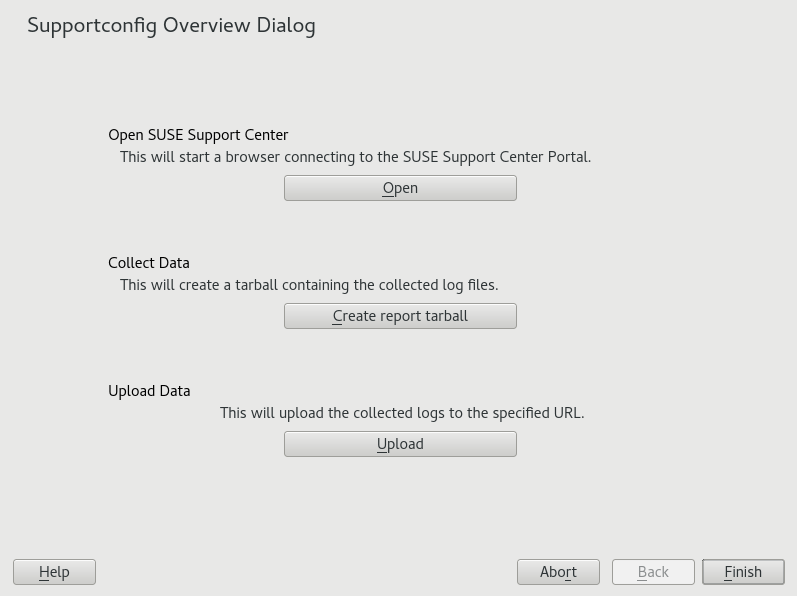
Start YaST and open the module.
Click .
In the next window, select one of the Supportconfig options from the radio button list. is preselected by default. If you want to test the report function first, use . For additional information on the other options, refer to the
supportconfigman page.Press .
Enter your contact information. It is saved in the
basic-environment.txtfile and included in the created archive.To submit the archive to Global Technical Support, provide the required . YaST automatically suggests an upload server. To modify it, refer to Section 39.2.2, “Upload targets” for details of which upload servers are available.
To submit the archive later, leave the empty.
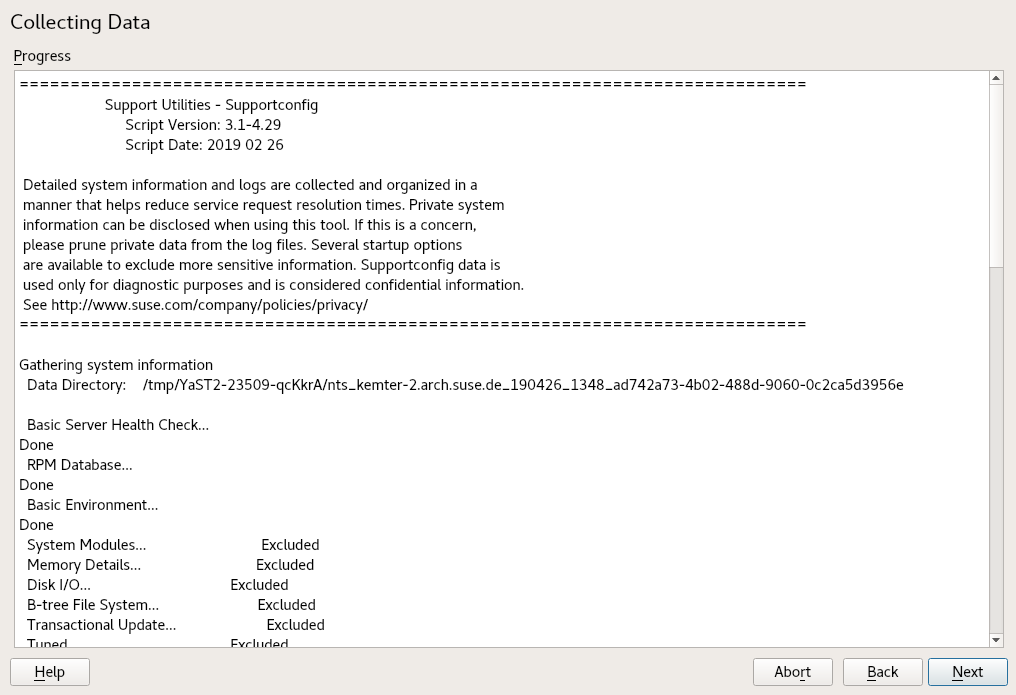
Press to start the information collection process.
After the process is finished, press .
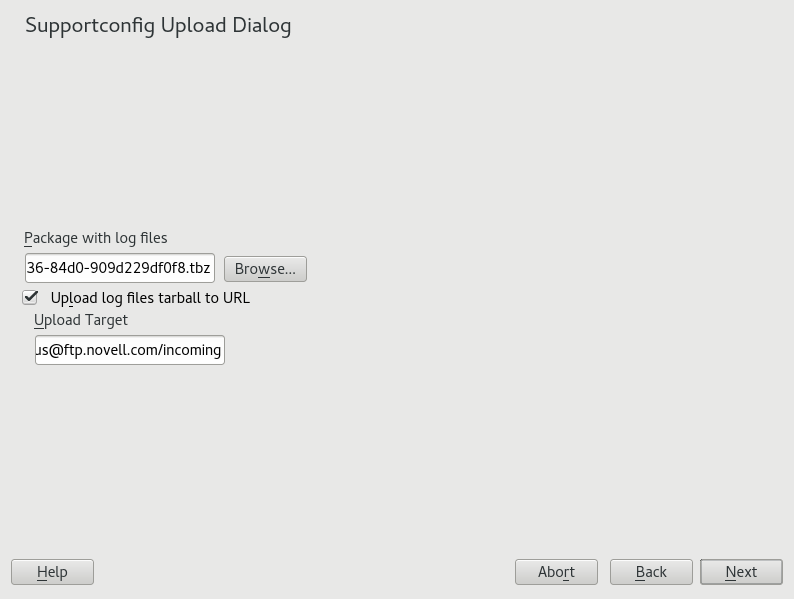
To review the collected data, select the desired file from to view its contents in YaST. To remove a file from the TAR archive before submitting it to support, use . Press .
Save the TAR archive. If you started the YaST module as
rootuser, YaST prompts to save the archive to/var/log(otherwise, to your home directory). The file name format isscc_HOST_DATE_TIME.tbz.To upload the archive to support directly, make sure is activated. The shown here is the one that YaST suggests in Step 5. To modify the upload target, check which upload servers are available in Section 39.2.2, “Upload targets”.
To skip the upload, deactivate .
Confirm the changes to close the YaST module.
39.2.4 Creating a supportconfig archive from command line #
The following procedure shows how to create a Supportconfig archive, but without submitting it to support directly. For uploading it, you need to run the command with certain options as described in Procedure 39.2, “Submitting information to support from command line”.
Open a shell and become
root.Run
supportconfig. Usually, it is enough to run this tool without any options. Some options are very common and are displayed in the following list:-E MAIL,-N NAME,-O COMPANY,-P PHONESets your contact data: e-mail address (
-E), company name (-O), your name (-N), and your phone number (-P).-i KEYWORDS,-FLimits the features to check. The placeholder KEYWORDS is a comma separated list of case-sensitive keywords. Get a list of all keywords with
supportconfig -F.-r SRNUMBERDefines your service request number when uploading the generated TAR archive.
Wait for the tool to complete the operation.
The default archive location is
/var/log, with the file name format beingscc_HOST_DATE_TIME.tbz
39.2.5 Understanding the output of supportconfig #
Whether you run supportconfig through YaST or directly,
the script gives you a summary of what it did.
Support Utilities - Supportconfig
Script Version: 3.0-98
Script Date: 2017 06 01
[...]
Gathering system information
Data Directory: /var/log/scc_d251_180201_1525 1
Basic Server Health Check... Done 2
RPM Database... Done 2
Basic Environment... Done 2
System Modules... Done 2
[...]
File System List... Skipped 3
[...]
Command History... Excluded 4
[...]
Supportconfig Plugins: 1 5
Plugin: pstree... Done
[...]
Creating Tar Ball
==[ DONE ]===================================================================
Log file tar ball: /var/log/scc_d251_180201_1525.txz 6
Log file size: 732K
Log file md5sum: bf23e0e15e9382c49f92cbce46000d8b
=============================================================================The temporary data directory to store the results. This directory is archived as tar file, see 6. | |
The feature was enabled (either by default or selected manually) and executed successfully. The result is stored in a file (see Table 39.1, “Comparison of features and file names in the TAR archive”). | |
The feature was skipped because some files of one or more RPM packages were changed. | |
The feature was excluded because it was deselected via the | |
The script found one plug-in and executes the plug-in
| |
The tar file name of the archive, by default compressed with |
39.2.6 Common supportconfig options #
The supportconfig utility is usually called without any
options. Display a list of all options with
supportconfig -h or refer to the man
page. The following list gives a brief overview of some common use cases:
- Reducing the size of the information being gathered
Use the minimal option (
-m):>sudosupportconfig -m- Limiting the information to a specific topic
If you have already localized a problem that relates to a specific area or feature set only, you should limit the collected information to the specific area for the next
supportconfigrun. For example, if you detected problems with LVM and want to test a recent change that you did to the LVM configuration. In that case it makes sense to gather the minimum Supportconfig information around LVM only:>sudosupportconfig -i LVMAdditional keywords can be separated through commas. For example, an additional disk test:
>sudosupportconfig -i LVM,DISKFor a complete list of feature keywords that you can use for limiting the collected information to a specific area, run:
>sudosupportconfig -F- Including additional contact information in the output:
>sudosupportconfig -E tux@example.org -N "Tux Penguin" -O "Penguin Inc." ...(all in one line)
- Collecting already rotated log files
>sudosupportconfig -lThis is especially useful in high logging environments or after a kernel crash when syslog rotates the log files after a reboot.
39.2.7 Overview of the archive content #
The TAR archive contains all the results from the features. Depending on
what you have selected (all or only a small set), the archive can contain
more or less files.
The set of features can be limited through the -i
option (see Section 39.2.6, “Common supportconfig options”).
To list the content of the archive, use the following tar
command:
#tarxf /var/log/scc_earth_180131_1545.tbz
The following file names are always available inside the TAR archive:
basic-environment.txtContains the date when this script was executed and system information like version of the distribution, hypervisor information, and more.
basic-health-check.txtContains some basic health checks like uptime, virtual memory statistics, free memory and hard disk, checks for zombie processes, and more.
hardware.txtContains basic hardware checks like information about the CPU architecture, list of all connected hardware, interrupts, I/O ports, kernel boot messages, and more.
messages.txtContains log messages from the system journal.
rpm.txtContains a list of all installed RPM packages, the name, where they are coming from, and their versions.
summary.xmlContains some information in XML format like distribution, the version, and product specific fragments.
supportconfig.txtContains information about the
supportconfigscript itself.y2log.txtContains YaST specific information like specific packages, configuration files, and log files.
Table 39.1, “Comparison of features and file names in the TAR archive” lists all available features and their file names. Further service packs can extend the list, as can plug-ins.
| Feature | File name |
|---|---|
| APPARMOR | security-apparmor.txt |
| AUDIT | security-audit.txt |
| AUTOFS | fs-autofs.txt |
| BOOT | boot.txt |
| BTRFS | fs-btrfs.txt |
| DAEMONS | systemd.txt |
| CIMOM | cimom.txt |
| CRASH | crash.txt |
| CRON | cron.txt |
| DHCP | dhcp.txt |
| DISK | fs-diskio.txt |
| DNS | dns.txt |
| DOCKER | docker.txt |
| DRBD | drbd.txt |
| ENV | env.txt |
| ETC | etc.txt |
| HA | ha.txt |
| HAPROXY | haproxy.txt |
| HISTORY | shell_history.txt |
| IB | ib.txt |
| IMAN | novell-iman.txt |
| ISCSI | fs-iscsi.txt |
| LDAP | ldap.txt |
| LIVEPATCH | kernel-livepatch.txt |
| LVM | lvm.txt |
| MEM | memory.txt |
| MOD | modules.txt |
| MPIO | mpio.txt |
| NET | network-*.txt |
| NFS | nfs.txt |
| NTP | ntp.txt |
| NVME | nvme.txt |
| OCFS2 | ocfs2.txt |
| OFILES | open-files.txt |
print.txt | |
| PROC | proc.txt |
| SAR | sar.txt |
| SLERT | slert.txt |
| SLP | slp.txt |
| SMT | smt.txt |
| SMART | fs-smartmon.txt |
| SMB | samba.txt |
| SRAID | fs-softraid.txt |
| SSH | ssh.txt |
| SSSD | sssd.txt |
| SYSCONFIG | sysconfig.txt |
| SYSFS | sysfs.txt |
| TRANSACTIONAL | transactional-update.txt |
| TUNED | tuned.txt |
| UDEV | udev.txt |
| UFILES | fs-files-additional.txt |
| UP | updates.txt |
| WEB | web.txt |
| X | x.txt |
39.3 Submitting information to Global Technical Support #
Use the YaST module or the
supportconfig command line utility to submit system
information to the Global Technical Support. When you experience a server
issue and want the support's assistance, you will need to open a service
request first. For details, see
Section 39.2.1, “Creating a service request number”.
The following examples use 12345678901 as a placeholder for your service request number. Replace 12345678901 with the service request number you created in Section 39.2.1, “Creating a service request number”.
The following procedure assumes that you have already created a Supportconfig archive, but have not uploaded it yet. Make sure to have included your contact information in the archive as described in Section 39.2.3, “Creating a supportconfig archive with YaST”, Step 4. For instructions on how to generate and submit a Supportconfig archive in one go, see Section 39.2.3, “Creating a supportconfig archive with YaST”.
Start YaST and open the module.
Click .
In specify the path to the existing Supportconfig archive or for it.
YaST automatically proposes an upload server. If you want to modify it, refer to Section 39.2.2, “Upload targets” for details of which upload servers are available.
Proceed with .
Click .
The following procedure assumes that you have already created a Supportconfig archive, but have not uploaded it yet. For instructions on how to generate and submit a Supportconfig archive in one go, see Section 39.2.3, “Creating a supportconfig archive with YaST”.
Servers with Internet connectivity:
To use the default upload target, run:
>sudosupportconfig -ur 12345678901For the secure upload target, use the following:
>sudosupportconfig -ar 12345678901
Servers without Internet connectivity
Run the following:
>sudosupportconfig -r 12345678901Manually upload the
/var/log/scc_SR12345678901*tbzarchive to one of our FTP servers. Which one to use depends on your location in the world. For an overview, see Section 39.2.2, “Upload targets”.
After the TAR archive arrives in the incoming directory of our FTP server, it becomes automatically attached to your service request.
39.4 Analyzing system information #
System reports created with supportconfig can be analyzed
for known issues to help resolve problems faster. For this purpose,
SUSE Linux Enterprise Server provides both an appliance and a command line tool for
Supportconfig Analysis (SCA). The SCA appliance is a
server-side tool which is non-interactive. The SCA tool
(scatool provided by the package
sca-server-report) runs on the client-side and is
executed from command line. Both tools analyze Supportconfig archives from
affected servers. The initial server analysis takes place on the SCA
appliance or the workstation on which scatool is
running. No analysis cycles happen on the production server.
Both the appliance and the command line tool additionally need product-specific patterns that enable them to analyze the Supportconfig output for the associated products. Each pattern is a script that parses and evaluates a Supportconfig archive for one known issue. The patterns are available as RPM packages.
You can also develop your own patterns as briefly described in Section 39.4.3, “Developing custom analysis patterns”.
39.4.1 SCA command line tool #
The SCA command line tool lets you analyze a local machine using both
supportconfig and the analysis patterns for the specific
product that is installed on the local machine. The tool creates an HTML
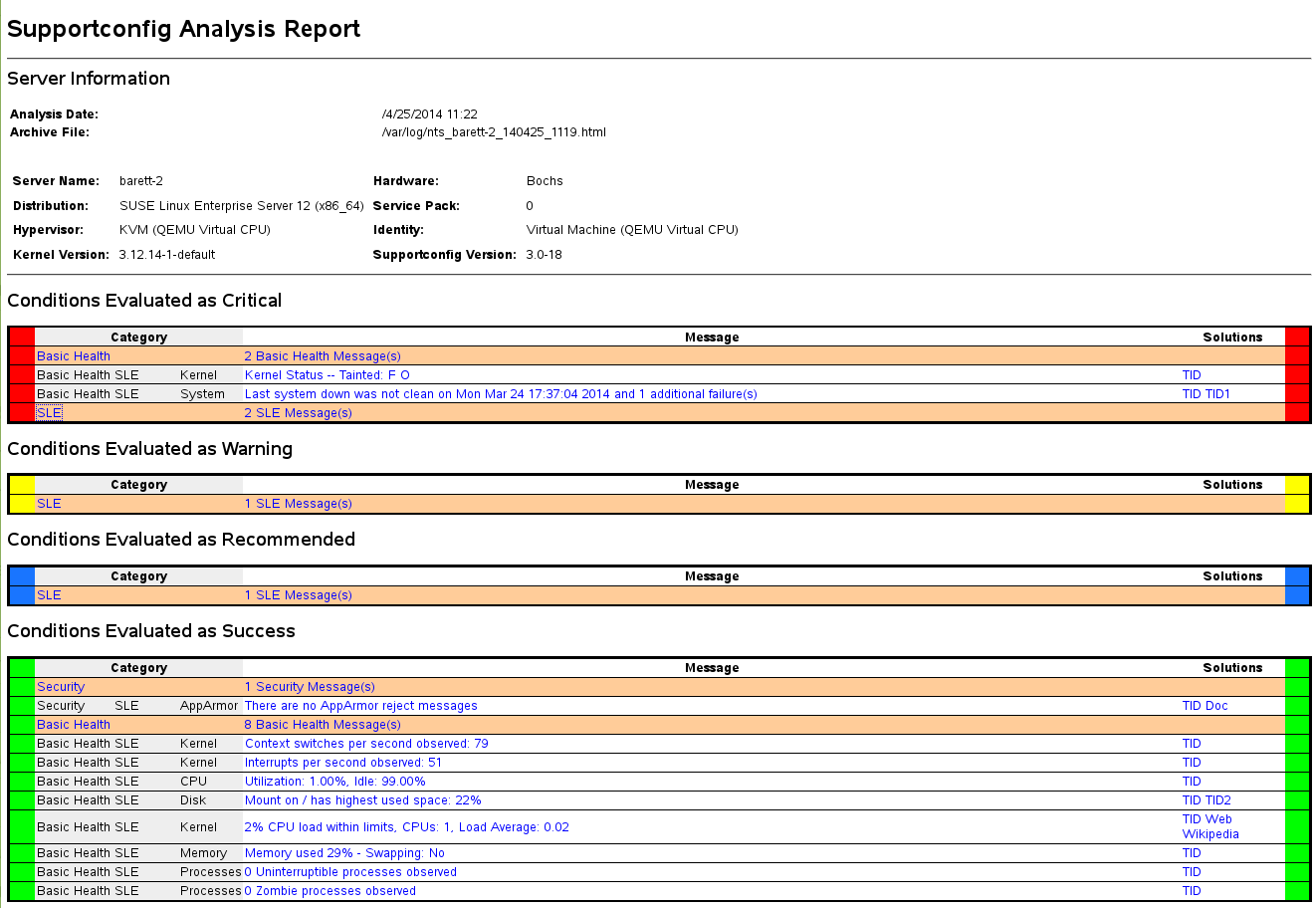
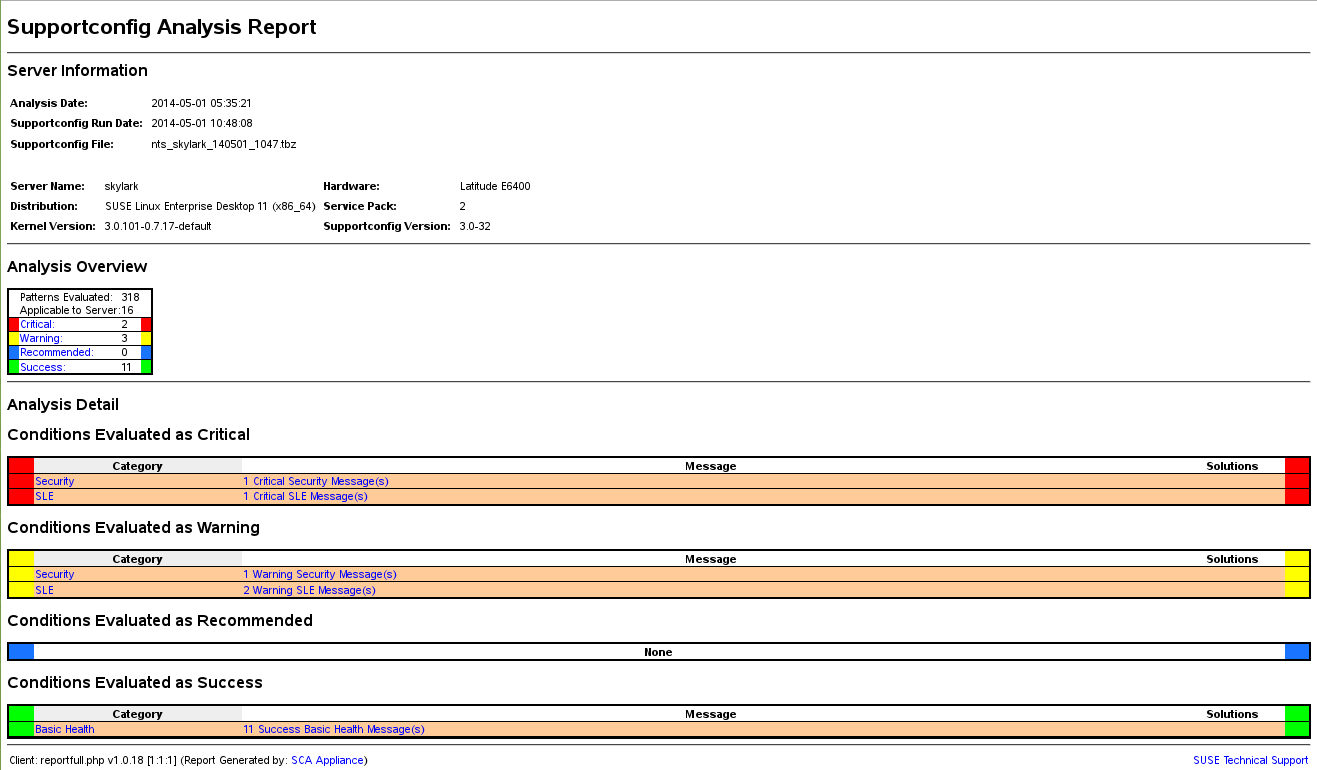
report showing its analysis results. For an example, see
Figure 39.1, “HTML report generated by SCA tool”.
The scatool command is provided by the
sca-server-report package. It is
not installed by default. Additionally, you need the
sca-patterns-base package and any
of the product-specific
sca-patterns-* packages that
matches the product installed on the machine where you want to run the
scatool command.
Execute the scatool command either as root user or
with sudo. When calling the SCA tool, either
analyze an existing supportconfig TAR archive or
let it generate and analyze a new archive in one go. The tool also provides
an interactive console with tab completion. It is possible to run
supportconfig on an external machine and to execute the
subsequent analysis on the local machine.
Find some example commands below:
sudo scatool-sCalls
supportconfigand generates a new Supportconfig archive on the local machine. Analyzes the archive for known issues by applying the SCA analysis patterns that match the installed product. Displays the path to the HTML report that is generated from the results of the analysis. It is usually written to the same directory where the Supportconfig archive can be found.sudo scatool-s-o/opt/sca/reports/Same as
sudo scatool-s, only that the HTML report is written to the path specified with-o.sudo scatool-aPATH_TO_TARBALL_OR_DIRAnalyzes the specified Supportconfig archive file (or the specified directory to where the Supportconfig archive has been extracted). The generated HTML report is saved in the same location as the Supportconfig archive or directory.
sudo scatool-aSLES_SERVER.COMPANY.COMEstablishes an SSH connection to an external server SLES_SERVER.COMPANY.COM and runs
supportconfigon the server. The Supportconfig archive is then copied back to the local machine and is analyzed there. The generated HTML report is saved to the default/var/logdirectory. (Only the Supportconfig archive is created on SLES_SERVER.COMPANY.COM).sudo scatool-cStarts the interactive console for
scatool. Press →| twice to see the available commands.
For further options and information, run sudo scatool -h
or see the scatool man page.
39.4.2 SCA appliance #
If you decide to use the SCA appliance for analyzing the Supportconfig archives, configure a dedicated server (or virtual machine) as the SCA appliance server. The SCA appliance server can then be used to analyze Supportconfig archives from all machines in your enterprise running SUSE Linux Enterprise Server or SUSE Linux Enterprise Desktop. You can simply upload Supportconfig archives to the appliance server for analysis. Interaction is not required. In a MariaDB database, the SCA appliance keeps track of all Supportconfig archives that have been analyzed . You can read the SCA reports directly from the appliance Web interface. Alternatively, you can have the appliance send the HTML report to any administrative user via e-mail. For details, see Section 39.4.2.5.4, “Sending SCA reports via e-mail”.
39.4.2.1 Installation quick start #
To install and set up the SCA appliance in a very fast way from the command line, follow the instructions here. The procedure is intended for experts and focuses on the bare installation and setup commands. For more information, refer to the more detailed description in Section 39.4.2.2, “Prerequisites” to Section 39.4.2.3, “Installation and basic setup”.
Web and LAMP Pattern
Web and Scripting Module (you must register the machine to be able to select this module).
root privileges required
All commands in the following procedure must be run as root.
After the appliance is set up and running, no more manual interaction is required. This way of setting up the appliance is therefore ideal for using cron jobs to create and upload Supportconfig archives.
On the machine on which to install the appliance, log in to a console and execute the following commands (make sure to accept the recommended packages):
>sudozypper install sca-appliance-* sca-patterns-* \ vsftpd yast2 yast2-ftp-server>sudosystemctl enable apache2>sudosystemctl start apache2>sudosystemctl enable vsftpd>sudosystemctl start vsftpd>sudoyast ftp-serverIn YaST FTP Server, select › › › › to .
Execute the following commands:
>sudosystemctl enable mysql>sudosystemctl start mysql>sudomysql_secure_installation>sudosetup-sca -fThe mysql_secure_installation will create a MariaDB
rootpassword.
This way of setting up the appliance requires manual interaction when typing the SSH password.
On the machine on which to install the appliance, log in to a console.
Execute the following commands:
>sudozypper install sca-appliance-* sca-patterns-*>sudosystemctl enable apache2>sudosystemctl start apache2>sudosudo systemctl enable mysql>sudosystemctl start mysql>sudomysql_secure_installation>sudosetup-sca
39.4.2.2 Prerequisites #
To run an SCA appliance server, you need the following prerequisites:
All
sca-appliance-*packages.The
sca-patterns-basepackage. Additionally, any of the product-specificsca-patterns-*for the type of Supportconfig archives that you want to analyze with the appliance.Apache
PHP
MariaDB
anonymous FTP server (optional)
39.4.2.3 Installation and basic setup #
As listed in Section 39.4.2.2, “Prerequisites”, the SCA appliance has several dependencies on other packages. Therefore you need do so some preparations before installing and setting up the SCA appliance server:
For Apache and MariaDB, install the
WebandLAMPinstallation patterns.Set up Apache, MariaDB, and optionally an anonymous FTP server. For more information, see Chapter 34, The Apache HTTP server and Chapter 35, Setting up an FTP server with YaST.
Configure Apache and MariaDB to start at boot time:
>sudosystemctl enable apache2 mysqlStart both services:
>sudosystemctl start apache2 mysql
Now you can install the SCA appliance and set it up as described in Procedure 39.5, “Installing and configuring the SCA appliance”.
After installing the packages, use the setup-sca
script for the basic configuration of the MariaDB administration and
report database that is used by the SCA appliance.
It can be used to configure the following options you have for uploading the Supportconfig archives from your machines to the SCA appliance:
scpanonymous FTP server
Install the appliance and the SCA base-pattern library:
>sudozypper install sca-appliance-* sca-patterns-baseAdditionally, install the pattern packages for the types of Supportconfig archives you want to analyze. For example, if you have SUSE Linux Enterprise Server 12 and SUSE Linux Enterprise Server 15 servers in your environment, install both the
sca-patterns-sle12andsca-patterns-sle15packages.To install all available patterns:
>sudozypper install sca-patterns-*For basic setup of the SCA appliance, use the
setup-scascript. How to call it depends on how you want to upload the Supportconfig archives to the SCA appliance server:If you have configured an anonymous FTP server that uses the
/srv/ftp/uploaddirectory, execute the setup script with the-foption. Follow the instructions on the screen:>sudosetup-sca -fNote: FTP server using another directoryIf your FTP server uses another directory than
/srv/ftp/upload, adjust the following configuration files first to make them point to the correct directory:/etc/sca/sdagent.confand/etc/sca/sdbroker.conf.If you want to upload Supportconfig files to the
/tmpdirectory of the SCA appliance server viascp, call the setup script without any parameters. Follow the instructions on the screen:>sudosetup-sca
The setup script runs a few checks regarding its requirements and configures the needed components. It will prompt you for two passwords: the MySQL
rootpassword of the MariaDB that you have set up, and a Web user password with which to log in to the Web interface of the SCA appliance.Enter the existing MariaDB
rootpassword. It will allow the SCA appliance to connect to the MariaDB.Define a password for the Web user. It will be written to
/srv/www/htdocs/sca/web-config.phpand will be set as the password for the userscdiag. Both user name and password can be changed at any time later, see Section 39.4.2.5.1, “Password for the Web interface”.
After successful installation and setup, the SCA appliance is ready for use, see Section 39.4.2.4, “Using the SCA appliance”. However, you should modify some options such as changing the password for the Web interface, changing the source for the SCA pattern updates, enabling archiving mode or configuring e-mail notifications. For details on that, see Section 39.4.2.5, “Customizing the SCA appliance”.
As the reports on the SCA appliance server contain security-relevant information, make sure to protect the data on the SCA appliance server against unauthorized access.
39.4.2.4 Using the SCA appliance #
You can upload existing Supportconfig archives to the SCA appliance manually or create new Supportconfig archives and upload them to the SCA appliance in one step. Uploading can be done via FTP or SCP. For both, you need to know the URL where the SCA appliance can be reached. For upload via FTP, an FTP server needs to be configured for the SCA appliance, see Procedure 39.5, “Installing and configuring the SCA appliance”.
39.4.2.4.1 Uploading supportconfig archives to the SCA appliance #
For creating a Supportconfig archive and uploading it via (anonymous) FTP:
>sudosupportconfig -U “ftp://SCA-APPLIANCE.COMPANY.COM/upload”For creating a Supportconfig archive and uploading it via SCP:
>sudosupportconfig -U “scp://SCA-APPLIANCE.COMPANY.COM/tmp”You will be prompted for the
rootuser password of the server running the SCA appliance.If you want to manually upload one or multiple archives, copy the existing archive files (usually located at
/var/log/scc_*.tbz) to the SCA appliance. As target, use either the appliance server's/tmpdirectory or the/srv/ftp/uploaddirectory (if FTP is configured for the SCA appliance server).
39.4.2.4.2 Viewing SCA reports #
SCA reports can be viewed from any machine that has a browser installed and can access the report index page of the SCA appliance.
Start a Web browser and make sure that JavaScript and cookies are enabled.
As a URL, enter the report index page of the SCA appliance.
https://sca-appliance.company.com/sca
If in doubt, ask your system administrator.
You will be prompted for a user name and a password to log in.
Figure 39.2: HTML report generated by SCA appliance #After logging in, click the date of the report you want to read.
Click the category first to expand it.
In the column, click an individual entry. This opens the corresponding article in the SUSE Knowledge base. Read the proposed solution and follow the instructions.
If the column of the shows any additional entries, click them. Read the proposed solution and follow the instructions.
Check the SUSE Knowledge base (https://www.suse.com/support/kb/) for results that directly relate to the problem identified by SCA. Work at resolving them.
Check for results that can be addressed proactively to avoid future problems.
39.4.2.5 Customizing the SCA appliance #
The following sections show how to change the password for the Web interface, how to change the source for the SCA pattern updates, how to enable archiving mode, and how to configure e-mail notifications.
39.4.2.5.1 Password for the Web interface #
The SCA Appliance Web interface requires a user name and password for
logging in. The default user name is scdiag and the
default password is linux (if not specified otherwise,
see Procedure 39.5, “Installing and configuring the SCA appliance”). Change the default password
to a secure password at the earliest possibility. You can also modify the
user name.
Log in as
rootuser at the system console of the SCA appliance server.Open
/srv/www/htdocs/sca/web-config.phpin an editor.Change the values of
$usernameand$passwordas desired.Save the file and exit.
39.4.2.5.2 Updates of SCA patterns #
By default, all sca-patterns-*
packages are updated regularly by a root cron job that executes the
sdagent-patterns script nightly, which in turn runs
zypper update sca-patterns-*. A regular system update
will update all SCA appliance and pattern packages. To update the SCA
appliance and patterns manually, run:
>sudozypper update sca-*
The updates are installed from the SUSE Linux Enterprise 15 SP3 update
repository by default. You can change the source for the updates to an
RMT server, if desired. When sdagent-patterns runs
zypper update sca-patterns-*, it gets the updates from
the currently configured update channel. If that channel is located on an
RMT server, the packages will be pulled from there.
Log in as
rootuser at the system console of the SCA appliance server.Open
/etc/sca/sdagent-patterns.confin an editor.Change the entry
UPDATE_FROM_PATTERN_REPO=1
to
UPDATE_FROM_PATTERN_REPO=0
Save the file and exit. The machine does not require any restart to apply the change.
39.4.2.5.3 Archiving mode #
All Supportconfig archives are deleted from the SCA appliance after they have been analyzed and their results have been stored in the MariaDB database. However, for troubleshooting purposes it can be useful to keep copies of Supportconfig archives from a machine. By default, archiving mode is disabled.
Log in as
rootuser at the system console of the SCA appliance server.Open
/etc/sca/sdagent.confin an editor.Change the entry
ARCHIVE_MODE=0
to
ARCHIVE_MODE=1
Save the file and exit. The machine does not require any restart to apply the change.
After having enabled archive mode, the SCA appliance will save the
Supportconfig files to the /var/log/archives/saved
directory, instead of deleting them.
39.4.2.5.4 Sending SCA reports via e-mail #
The SCA appliance can e-mail a report HTML file for each Supportconfig
analyzed. This feature is disabled by default. When enabling it, you can
define a list of e-mail addresses to which the reports should be sent.
Define a level of status messages that trigger the sending of reports
(STATUS_NOTIFY_LEVEL).
STATUS_NOTIFY_LEVEL #- $STATUS_OFF
Deactivate sending of HTML reports.
- $STATUS_CRITICAL
Send only SCA reports that include a CRITICAL.
- $STATUS_WARNING
Send only SCA reports that include a WARNING or CRITICAL.
- $STATUS_RECOMMEND
Send only SCA reports that include a RECOMMEND, WARNING or CRITICAL.
- $STATUS_SUCCESS
Send SCA reports that include a SUCCESS, RECOMMEND, WARNING or CRITICAL.
Log in as
rootuser at the system console of the SCA appliance server.Open
/etc/sca/sdagent.confin an editor.Search for the entry
STATUS_NOTIFY_LEVEL. By default, it is set to$STATUS_OFF(e-mail notifications are disabled).To enable e-mail notifications, change
$STATUS_OFFto the level of status messages that you want to have e-mail reports for, for example:STATUS_NOTIFY_LEVEL=$STATUS_SUCCESS
For details, see Possible values for
STATUS_NOTIFY_LEVEL.To define the list of recipients to which the reports should be sent:
Search for the entry
EMAIL_REPORT='root'.Replace
rootwith a list of e-mail addresses to which SCA reports should be sent. The e-mail addresses must be separated by spaces. For example:EMAIL_REPORT='tux@my.company.com wilber@your.company.com'
Save the file and exit. The machine does not require any restart to apply the changes. All future SCA reports will be e-mailed to the specified addresses.
39.4.2.6 Backing up and restoring the database #
To back up and restore the MariaDB database that stores the SCA reports,
use the scadb command as described
below. scadb is provided by the package
sca-appliance-broker.
Log in as
rootuser at the system console of the server running the SCA appliance.Put the appliance into maintenance mode by executing:
#scadb maintStart the backup with:
#scadb backupThe data is saved to a TAR archive:
sca-backup-*sql.gz.If you are using the pattern creation database to develop your own patterns (see Section 39.4.3, “Developing custom analysis patterns”), back up this data, too:
#sdpdb backupThe data is saved to a TAR archive:
sdp-backup-*sql.gz.Copy the following data to another machine or an external storage medium:
sca-backup-*sql.gzsdp-backup-*sql.gz/usr/lib/sca/patterns/local(only needed if you have created custom patterns)
Reactivate the SCA appliance with:
#scadb reset agents
To restore the database from your backup, proceed as follows:
Log in as
rootuser at the system console of the server running the SCA appliance.Copy the newest
sca-backup-*sql.gzandsdp-backup-*sql.gzTAR archives to the SCA appliance server.To decompress the files, run:
#gzip -d *-backup-*sql.gzTo import the data into the database, execute:
#scadb import sca-backup-*sqlIf you are using the pattern creation database to create your own patterns, also import the following data with:
#sdpdb import sdp-backup-*sqlIf you are using custom patterns, also restore
/usr/lib/sca/patterns/localfrom your backup data.Reactivate the SCA appliance with:
#scadb reset agentsUpdate the pattern modules in the database with:
#sdagent-patterns -u
39.4.3 Developing custom analysis patterns #
The SCA appliance comes with a complete pattern development environment
(the SCA Pattern Database) that enables you to develop your own, custom
patterns. Patterns can be written in any programming language. To make them
available for the Supportconfig analysis process, they need to be saved to
/usr/lib/sca/patterns/local and to be made executable.
Both the SCA appliance and the SCA tool will then run the custom patterns
against new Supportconfig archives as part of the analysis report. For
detailed instructions on how to create (and test) your own patterns, see
https://www.suse.com/c/blog/sca-pattern-development/.
39.5 Gathering information during the installation #
During the installation, supportconfig is not available.
However, you can collect log files from YaST by using
save_y2logs. This command will create a
.tar.xz archive in the directory
/tmp.
If issues appear very early during installation, you may be able to gather
information from the log file created by
linuxrc. linuxrc is a small command
that runs before YaST starts. This log file is available at
/var/log/linuxrc.log.
The log files available during the installation are not available in the installed system anymore. Properly save the installation log files while the installer is still running.
39.6 Support of kernel modules #
An important requirement for every enterprise operating system is the level
of support you receive for your environment. Kernel modules are the most
relevant connector between hardware (“controllers”) and the
operating system. Every kernel module in SUSE Linux Enterprise has a
supported flag that can take three possible values:
“yes”, thus
supported“external”, thus
supported“(empty, not set)”, thus
unsupported
The following rules apply:
All modules of a self-recompiled kernel are by default marked as unsupported.
Kernel modules supported by SUSE partners and delivered using
SUSE SolidDriver Programare marked “external”.If the
supportedflag is not set, loading this module will taint the kernel. Tainted kernels are not supported. Unsupported Kernel modules are included in an extra RPM package (kernel-FLAVOR-extra). That package is only available for SUSE Linux Enterprise Desktop and the SUSE Linux Enterprise Workstation Extension. Those kernels will not be loaded by default (FLAVOR=default|xen|...). In addition, these unsupported modules are not available in the installer, and thekernel-FLAVOR-extrapackage is not part of the SUSE Linux Enterprise media.Kernel modules not provided under a license compatible to the license of the Linux kernel also taint the kernel. For details, see the state of
/proc/sys/kernel/tainted.
39.6.1 Technical background #
Linux kernel: The value of
/proc/sys/kernel/unsupporteddefaults to2on SUSE Linux Enterprise 15 SP3 (do not warn in syslog when loading unsupported modules). This default is used in the installer and in the installed system.modprobe: Themodprobeutility for checking module dependencies and loading modules appropriately checks for the value of thesupportedflag. If the value is “yes” or “external” the module will be loaded, otherwise it will not. For information on how to override this behavior, see Section 39.6.2, “Working with unsupported modules”.Note: SupportSUSE does not generally support the removal of storage modules via
modprobe -r.
39.6.2 Working with unsupported modules #
While general supportability is important, situations can occur where loading an unsupported module is required. For example, for testing or debugging purposes, or if your hardware vendor provides a hotfix.
To override the default, edit
/etc/modprobe.d/10-unsupported-modules.confand change the value of the variableallow_unsupported_modulesto1. If an unsupported module is needed in the initrd, do not forget to rundracut-fto update the initrd.If you only want to try loading a module once, you can use the
--allow-unsupported-modulesoption withmodprobe. For more information, see themodprobeman page.During installation, unsupported modules may be added through driver update disks, and they will be loaded. To enforce loading of unsupported modules during boot and afterward, use the kernel command line option
oem-modules. While installing and initializing thesuse-module-toolspackage, the kernel flagTAINT_NO_SUPPORT(/proc/sys/kernel/tainted) will be evaluated. If the kernel is already tainted,allow_unsupported_moduleswill be enabled. This will prevent unsupported modules from failing in the system being installed. If no unsupported modules are present during installation and the other special kernel command line option (oem-modules=1) is not used, the default still is to disallow unsupported modules.
Remember that loading and running unsupported modules will make the kernel and the whole system unsupported by SUSE.
39.7 More information #
man supportconfig—Thesupportconfigman page.man supportconfig.conf—The man page of the Supportconfig configuration file.man scatool—Thescatoolman page.man scadb—Thescadbman page.man setup-sca—Thesetup-scaman page.https://mariadb.com/kb/en/—The MariaDB documentation.
http://httpd.apache.org/docs/ and Chapter 34, The Apache HTTP server—Documentation about the Apache Web server.
Chapter 35, Setting up an FTP server with YaST—Documentation of how to set up an FTP server.
https://www.suse.com/c/blog/sca-pattern-development/—Instructions on how to create (and test) your own SCA patterns.
https://www.suse.com/c/blog/basic-server-health-check-supportconfig/—A Basic Server Health Check with Supportconfig.
https://community.microfocus.com/img/gw/groupwise/w/groupwise/34308/create-your-own-supportconfig-plugin—Create Your Own Supportconfig Plugin.
https://www.suse.com/c/blog/creating-a-central-supportconfig-repository/—Creating a Central Supportconfig Repository.