Synchronizing Time Using NTP/NTS
- WHAT?
This article describes what time synchronization is and how to configure it.
- WHY?
Keeping the system time synchronized is crucial when sharing tasks and resources with other team members over the network.
- EFFORT
Up to 60 minutes to read this article and perform a basic configuration of time synchronization on your computer.
- REQUIREMENTS
A basic knowledge of Linux system administration is required. Specific tasks require
rootprivileges.Working network connection to the internal network or Internet to reach the source time server.
To configure
chronydusing YaST, the YaST NTP module included in the yast2-ntp-client package must be available.
1 Introduction #
Maintaining an accurate and synchronized system time on the computer is vital for teamwork. Planning and calendaring applications rely on it to track time correctly and notify users about appointments on time. For clustered applications, individual host machines often require synchronized system time for mutual communication.
The built-in hardware clock is not a reliable time source. A manual correction of the system time may cause malfunction of critical applications due to sudden time leaps. Therefore, the system time needs to be synchronized against an external reliable time source over the network.
1.1 What is NTP? #
The Network Time Protocol (NTP) is designed to synchronize the system time over the network. Its goal is to maintain the absolute time and use it to synchronize the system time of all machines within a network.
1.2 What is NTS? #
Network Time Security (NTS) is a security extension of NTP. NTS provides mechanisms to authenticate NTP messages and encrypt them, ensuring that the time data received is both secure and authentic. NTS is designed to be backward compatible with existing NTP infrastructure. This allows for gradual deployment without requiring changes to existing NTP servers that do not support NTS.
1.3 How does NTP work? #
When the NTP service is properly configured, it continuously queries and adjusts the system time with reliable time servers. Typically, home computers and other devices connected to the internet are configured to query a public time server on the Internet.
Conversely, desktop computers and servers that reside inside a corporate subnet are configured to query a dedicated time server within the local network. The time server itself synchronizes its time with a public time server.
1.3.1 Implementation #
chrony is the default implementation of NTP in SUSE Linux Enterprise Server.
chrony includes two parts:
chronydis asystemdservice that can be started at boot time.chronycis a command-line interface program to monitor the performance ofchronydand to change specific operating parameters at runtime.
1.4 Benefits #
Using NTP to maintain the accurate time has the following benefits:
People can rely on their clocks when following a planned schedule.
Applications can trigger scheduled desktop or system actions accurately.
Cluster nodes can keep their data synchronized and up to date.
Using an internal time server helps maintain synchronized system time in networks with restricted access to the Internet.
By integrating security measures into NTP through NTS, the protocol enhances its robustness and addresses the vulnerabilities associated with unsecured time synchronization.
2 Configuring NTP using YaST #
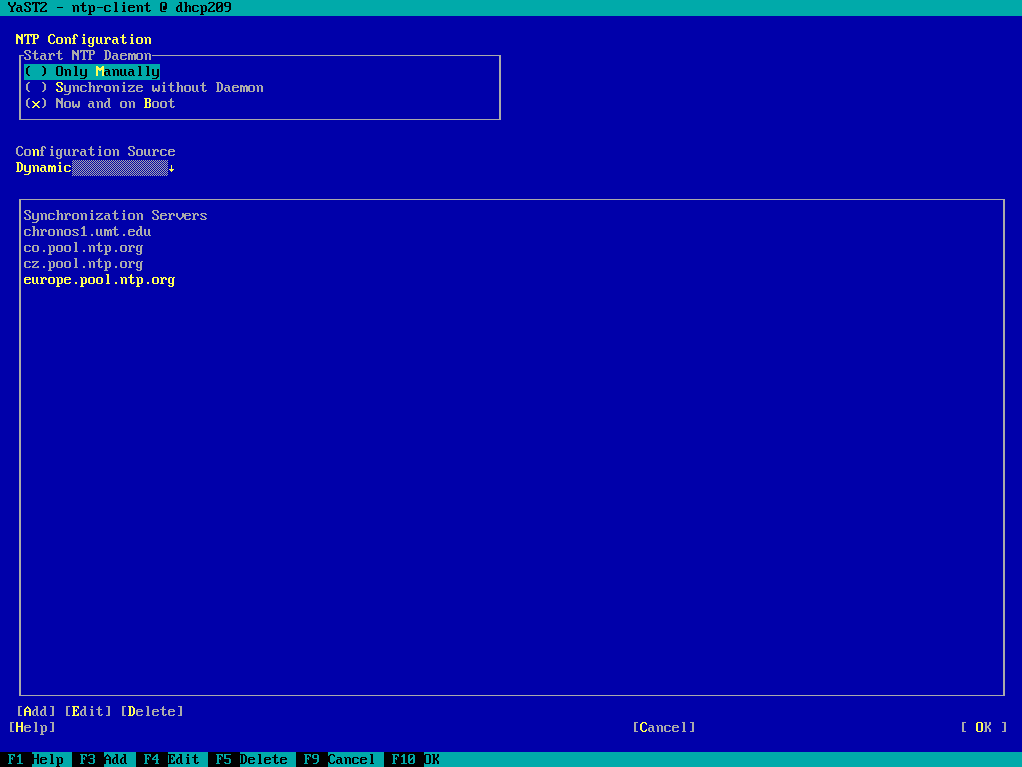
Open the YaST NTP module. Start › › .
Figure 3: NTP configuration window #Specify when to start the NTP service:
Start the NTP service manually.
Set the system time periodically without a permanently running NTP service. You can set the .
Start the NTP service automatically when the system is booting. This setting is recommended.
Specify the type of configuration source. In the drop-down box, select either or . Set if your server uses only a fixed set of (public) NTP servers. If your internal network offers NTP servers via DHCP, pick .
Configure time servers. Time servers for the client to query are listed in the lower part of the window. Modify this list as needed by clicking , , and .
Click to add a new time server:
Figure 4: Adding a time server #In the field, type the URL of the time server or pool of time servers with which you want to synchronize the machine time. After the URL is complete, click to verify that it points to a valid time source.
Activate to speed up the time synchronization by sending more requests at the NTP service start.
Activate to speed up the boot time on systems that start the NTP service automatically and may not have an Internet connection at boot time. This option is useful, for example, for laptops with network connections managed by NetworkManager.
Confirm with .
3 Configuring NTP by adjusting /etc/chrony.conf #
When chronyd starts, it reads its configuration from the
/etc/chrony.conf file. The following sections
list important parameters that can affect chronyd behavior.
3.1 Specifying time sources #
To keep the computer clock synchronized, you need to tell chronyd what
time sources to use. For this purpose, use server,
pool and peer directives. You can
use each of them multiple times.
The server directive tells chronyd to use a specific
host as a time server by its name or IP address.
server 0.europe.pool.ntp.org offline1 server 1.europe.pool.ntp.org offline prefer2 server 192.168.2.254
The | |
The |
The pool directive lets you specify a network name that
resolves to multiple IP addresses that may change over time.
pool pool.ntp.org iburst1 maxsources 32
The | |
The |
The peer directive specifies an NTP peer host instead
of a time server. System time synchronization among
peers uses a symmetric architecture instead of the
client/server mode invoked by server and
pool options. You can use peer
multiple times to specify more than one peer.
peer 192.168.1.116 peer ntp.example.com
3.2 Running chronyd as an NTP server #
By default, chronyd works as a client to specified NTP servers. To make
it operate as an NTP server as well, add the allow
directive to the /etc/chrony.conf file. It opens the
NTP server port (123 by default) and responds to client requests.
You can either specify a single IP of an NTP client, or a subnet to
include multiple clients. You can use the allow
directive multiple times:
allow 1.2.3.4 allow 3.4.5.0/24
If you do not specify an IP address or a subnet, the stand-alone
allow directive allows access from all IPv4 and IPv6
addresses.
To limit the access of the previous allow directive,
use the deny directive:
allow 1.2.3.4 deny 1.2.3.0/24 allow 1.2.0.0/16
In the above example, the effect is the same regardless of the order of
the three directives. The 1.2.0.0/16 subnet is allowed
access except for the 1.2.3.0/24 subnet, which is
denied access. However, the host 1.2.3.4 is allowed
access.
3.3 Configuring a local reference clock #
chronyd relies on other programs (such as gpsd)
to access the timing data via a specific driver. Use the
refclock directive in
/etc/chrony.conf to specify a hardware reference
clock to be used as a time source. It has two mandatory parameters: a
driver name and a driver-specific parameter. The two parameters are
followed by zero or more refclock options. chronyd
includes the following drivers:
- PPS
Driver for the kernel pulse per second API. For example:
refclock PPS /dev/pps0 lock NMEA refid GPS
- SHM
NTP shared memory driver. For example:
refclock SHM 0 poll 3 refid GPS1 refclock SHM 1:perm=0644 refid GPS2
- SOCK
Unix domain socket driver. For example:
refclock SOCK /var/run/chrony.ttyS0.sock
- PHC
PTP hardware clock driver. For example:
refclock PHC /dev/ptp0 poll 0 dpoll -2 offset -37 refclock PHC /dev/ptp1:nocrossts poll 3 pps
For more information on individual drivers' options, see man 8
chrony.conf.
3.4 Activating offline time sources #
Although chronyd starts up normally on a system that boots without a
network connection, it cannot access the time servers specified in
/etc/chrony.conf. To prevent chronyd from trying to
query inaccessible time servers, use the offline option
next to the time source directive, for example:
server ntp.example.org offline
chronyd then does not try to poll the server until it is enabled using
the following command:
# chronyc online ntp.example.org
When the auto_offline option is set instead of the
offline option, chronyd assumes that the time server
has gone offline when two requests have been sent to it without
receiving a response. This option avoids the need to run the
offline command from chronyc when disconnecting the
network link.
4 Managing chronyd at runtime #
4.1 What is chronyc? #
chronyc is the client part of the chrony NTP implementation. You can
use the chronyc command to change the behavior of the chronyd service
at runtime. It also generates status reports about the operation of
chronyd.
Changes made using chronyc are not permanent. They are lost after the
next chronyd restart. For permanent changes, modify
/etc/chrony.conf as described in
Section 3, “Configuring NTP by adjusting /etc/chrony.conf”.
4.2 How does chronyc work? #
You can run chronyc either in an interactive or non-interactive mode.
To run chronyc interactively, enter chronyc on the command line and
press Enter. It displays a prompt and waits for your
command input. For example, to check how many NTP sources are online or
offline, run the activity command:
#chronycchronyc> activity 200 OK 4 sources online 2 sources offline 1 sources doing burst (return to online) 1 sources doing burst (return to offline) 0 sources with unknown address
To exit chronyc's prompt, enter quit or
exit.
If you do not need to use the interactive prompt, enter the command directly, for example:
#chronycactivity
5 Configuring NTS #
NTP protocol does not introduce security mechanism to make the communication
between the time server and client authenticated and encrypted. Network Time Security (NTS)
is an extension that improves the security of NTP. chrony supports NTS and
can authenticate time sources and protect against certain network attacks.
The following procedures outline how to configure the time server and client machine for secure time synchronization.
(Optional) It is a good idea to configure the time server to update its time via NTS. This ensures secure time synchronization from the very beginning of the synchronization chain. Comment out any existing time sources in
/etc/chrony.confthat do not support NTS and add at least one that supports NTS, for example:server time.cloudflare.com iburst nts
TipThe
ntsoption requests NTS connection if it is available, otherwise it falls back to NTP if NTS is not available.Restart the
chronydservice.>sudosystemctl restart chronyd.srviceVerify the configured time sources.
>chronyc sources -vMS Name/IP address Stratum Poll Reach LastRx Last sample =============================================================================== ^? time.cloudflare.com 3 6 1 2 -947ms[ -947ms] +/- 12ms ^? pyrrha.fi.muni.cz 2 6 1 1 -948ms[ -948ms] +/- 39ms ^* whitesoft-intex16.c.cbsn> 1 6 1 2 -948ms[ -948ms] +/- 5444us ^? mail.combatostrich.dev 2 6 1 1 -948ms[ -948ms] +/- 28msNoteThe line that starts with
^*includes the time source that was selected as best.Verify that the configured time source uses the NTS mode.
>chronyc -N authdataName/IP address Mode KeyID Type KLen Last Atmp NAK Cook CLen ========================================================================= [...] time.cloudflare.com NTS 1 15 256 3 0 0 8 96Verify that the server configuration includes the
allowoption that specifies which clients can synchronize time with the time server, for example:allow 192.168.1.0/24
(Optional) If the time server is running behind a firewall, allow communication on ports for both NTP and NTS. They are 123 and 4460 by default.
Obtain a TLS certificate and a corresponding private key and copy them to
/var/lib/chrony/. Verify that they are readable bychrony, for example:>sudoinstall -m 0440 -o chrony -g chrony nts.key /var/lib/chrony/>sudoinstall -m 0440 -o chrony -g chrony nts.crt /var/lib/chrony/Edit
/etc/chrony.confand verify that thentsdumpdir /var/lib/chronyoption is active. Then append the paths to the TLS key and certificate.ntsdumpdir /var/lib/chrony ntsserverkey /var/lib/chrony/nts.key ntsservercert /var/lib/chrony/nts.crt
Restart the
chronydservice.>sudosystemctl restart chronyd.service
Disable existing NTP sources, for example:
#server 192.168.1.1 iburst
The sources configurations are included in
/etc/chrony.confor in files under/etc/chrony.d/.The client host needs to trust the Root CA that signed the TLS certificate. Find details on how to manage the CA certificate store in a dedicated article.
Add the NTS time server source that you configured in Procedure 1, “Configuring NTS time server” to the client
chronyconfiguration in/etc/chrony.conf, for example:server nts1.example.com iburst nts
Restart the
chronydservice.>sudosystemctl restart chronyd.serviceVerify configured time sources on the client and confirm that the connection is authenticated.
>sudochronyc sources -v>sudochronyc -N authdataOn the NTS time server, verify per client statistics about NTS connections.
>sudochronyc -N clients -k
6 The chronyd systemd service #
The main part of chrony is the chronyd systemd service that runs
in the background and synchronizes system time with selected time
servers. You can use the following systemd commands to operate the
chronyd service:
systemctl status chronyd.servicePrints extended information about the current status of the
chronydservice.systemctl is-enabled chronyd.serviceChecks whether the automatic start of the
chronydservice at system boot is enabled.systemctl enabled chronyd.serviceEnables the automatic start of the
chronydservice at system boot.systemctl disable chronyd.serviceDisables the automatic start of the
chronydservice at system boot.systemctl is-active chronyd.serviceChecks whether the
chronydservice was started and is running.systemctl start chronyd.serviceStarts the
chronydservice.systemctl stop chronyd.serviceStops the
chronydservice.systemctl restart chronyd.serviceRestarts the
chronydservice and reloads/etc/chronyd.conf.
7 Troubleshooting #
In case of errors, check the following.
Verify that your computer is connected to a network and that the network is configured correctly:
>sudosystemctl status network.service ● NetworkManager.service - Network Manager Loaded: loaded (/usr/lib/systemd/system/NetworkManager.service; enabled; vendor preset: disabled) Active: active (running) since Sat 2021-08-07 20:09:44 CEST; 4 days ago [...]Verify that the time servers that you entered as a time source exist and are reachable over the network. For example:
>ping pool.ntp.org PING pool.ntp.org (85.199.214.101) 56(84) bytes of data. 64 bytes from 85.199.214.101 (85.199.214.101): icmp_seq=1 ttl=37 time=29.9 ms [...]If the
firewalldservice is active on your computer, verify that the NTP service is allowed.Verify that the
chronydservice is running:>sudosystemctl status chronyd.service ● chronyd.service - NTP client/server Loaded: loaded (/usr/lib/systemd/system/chronyd.service; enabled; vendor preset: disabled) Active: active (running) since Sat 2021-08-07 20:09:44 CEST; 4 days ago [...]If the system time on a virtualized guest diverges from the exact time, make sure that the VM Host Server system time is synchronized with a valid time server and that the guest is synchronized with the same time source as the host.
If the NTP service fails to start properly during system boot, it can be caused by network switches configured to use the
Spanning Tree Protocolwhile ports are not configured asEdge PortsbutPortfast. In this case, it can take up to a minute until the network connectivity is established.If the NTP service fails to start during system boot when the NetworkManager is used, edit the
/etc/sysconfig/network/configfile and change the value ofNM_ONLINE_TIMEOUTvalue to 30. If the problem persists, increase the timeout value by 15 and try again.If NTP sources cannot be reached, identify them with the following command:
>chronyc sources -v [...] MS Name/IP address Stratum Poll Reach LastRx Last sample =============================================================================== ^* time.mydomain.com 3 10 377 81 -5354us[-8257us] +/- 191ms ^? ntp1.example.com 0 10 0 - +0ns[ +0ns] +/- 0ns ^? 77.177.77.177 0 10 0 - +0ns[ +0ns] +/- 0ns ^? ntp3.example.com 0 10 0 - +0ns[ +0ns] +/- 0ns ^? ntp4.example.net 0 10 0 - +0ns[ +0ns] +/- 0ns ^? 2a02:3d8:1::1:1 0 6 0 - +0ns[ +0ns] +/- 0ns ^? ntp2.example.org 0 10 0 - +0ns[ +0ns] +/- 0nsIn this case, the only server that is really serving time is
time.mydomain.com. It is necessary to generally troubleshoot the network connection to the failing remote NTP time sources.
8 For more information #
Securing your computer with
firewalldis described in https://documentation.suse.com/sles/html/SLES-all/cha-security-firewall.html#sec-security-firewall-firewalld.Commands for operating
systemdservices are listed in https://susedoc.github.io/doc-modular/main/html/reference-systemctl-enable-disable-services/.For a complete reference, see related manual pages:
For a complete list of configuration directives, run
man 1 chrony.conf.For a complete list of
chronyccommands, runman 1 chronyc.For a complete list of
chronydcommand-line options, runman 8 chronyd.
9 Legal Notice #
Copyright© 2006–2026 SUSE LLC and contributors. All rights reserved.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”.
For SUSE trademarks, see https://www.suse.com/company/legal/. All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors, nor the translators shall be held liable for possible errors or the consequences thereof.