Securing Communication with TLS Certificates
- WHAT?
TLS certificates are key elements when establishing secure network communication.
- WHY?
You want to learn how to generate and sign TLS certificates to establish secured network communication.
- EFFORT
One hour is enough to learn how to manage TLS certificates and create a certificate signed by a private CA for a trusted network environment.
- GOAL
You can generate, sign and manage TLS certificates, and include them in the system-wide certificate store.
- REQUIREMENTS
To perform selected tasks, you need
rootorsudoprivileges.
1 Introduction #
Two systems, such as client and server hosts, communicate by exchanging data over the network. To avoid exposing such communication and possibly sensitive data, you can configure the systems to encrypt the mutual communication using TLS certificate.
This topic introduces basic theory behind establishing encrypted communication.
1.1 How is secure communication established? #
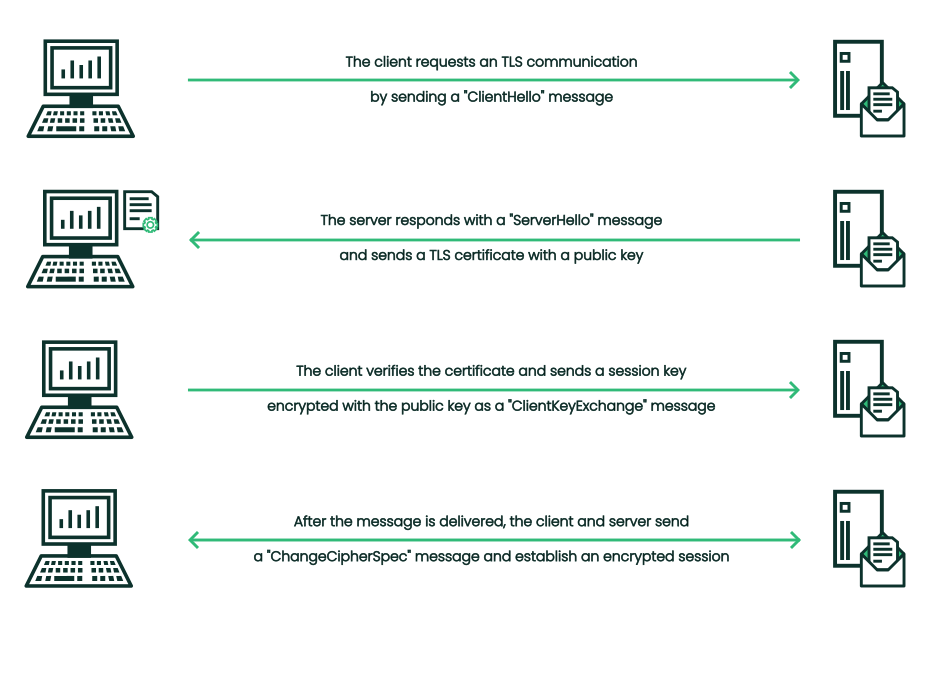
The following steps illustrate the process of establishing secure communication between the client and the server. The process is often referred to as a TLS handshake.
Client “hello”. The TLS handshake is started by the client sending a
ClientHellomessage to the server. Such message includes information about the TLS protocol versions and cryptographic algorithms supported by the client, as well as a random value used for generating session keys.Server “hello”. When the server receives the
ClientHellomessage, it responds with aServerHellomessage. Such a message includes the TLS protocol version selected by the server, the selected cryptographic algorithm, and a random value. The server also sends its digital certificate that includes the public key.Certificate verification. After the client receives the server's certificate, the client verifies that it is signed by a trusted CA and that the server's domain name matches the one in the certificate.
Key exchange. After the server's certificate is successfully verified, the client generates a secret and encrypts it with the server's public key from the certificate. This encrypted secret is sent to the server in a
ClientKeyExchangemessage.Session key generation. Both the client and the server use the exchanged data—client and server random values and the generated secret—to generate a shared session key. This key will be used to encrypt and decrypt data transmitted during the TLS session. Both parties confirm that subsequent messages will be encrypted by sending a
ChangeCipherSpecmessage.Finished. Finally, both the client and the server send a
Finishedmessage to confirm that the TLS handshake is complete. These messages contain a hash of all preceding TLS handshake messages, encrypted with the shared session key. If the hashes match on both sides, the TLS handshake is successful and the secure TLS connection is established.
1.2 Benefits of using secure communication #
Several key benefits of secure communication are:
Confidentiality: Secure communication ensures that sensitive information remains confidential and cannot be accessed by unauthorized parties. This is particularly important for protecting personal data and financial information.
Integrity: Secure communication guarantees the integrity of transmitted data and ensures that it remains unchanged during transmission. This helps prevent unauthorized modification of data and maintain its accuracy and reliability.
Authentication: Secure communication allows parties to authenticate each other's identities, verifying that they are who they claim to be. This helps prevent impersonation and ensures that communication is conducted securely between trusted parties.
Compliance: Secure communication helps organizations follow regulatory requirements and industry standards related to data protection and privacy. Compliance with regulations such as GDPR often requires the implementation of secure communication protocols and practices.
2 Issuing and installing TLS certificates #
The following procedures outline the TLS certificate issuance and installation process using both trusted and private CAs.
2.1 Using a trusted CA #
Generate a private key. A private key is required on the server—such as a Web server—that will use the certificate. The key is kept secure and used to sign messages and decrypt data.
Create a certificate signing request (CSR). Generate a CSR using the private key. The CSR contains information about the entity requesting the certificate and the public key that will be included in the certificate.
Submit the CSR to a CA signing. The CA verifies the information in the CSR and issues a signed certificate if the request is approved. This step may involve validation of the domain ownership or organization identity, depending on the type of certificate requested.
Receive the signed certificate. After the CA approves the CSR, it issues a signed certificate. The certificate includes the digital signature of the CA, the public key of the server, and additional information about the server, such as the domain name or organization.
Install the certificate on the server. Install the signed certificate on the server that will use it. This typically involves configuring the server software—such as the Apache Web server—to use the certificate for securing communication.
Configure the server and client for secure communication. After the certificate is installed on the server, configure the server and client software to use secure communication protocols, for example, HTTPS that uses the certificate for encryption and authentication.
Regular maintenance and renewal. Regularly monitor the validity of the certificate and renew it before it expires. Keep the private key secure and ensure that certificates are properly configured and updated as needed.
2.2 Using a private CA #
Create a private certificate authority (CA). A private CA is only needed to sign the server certificate yourself and not have it signed by a trusted CA.
Generate a private key. A private key is required on the server—such as a Web server—that will use the certificate. The key is kept secure and used to sign messages and decrypt data.
Create a certificate signing request (CSR). Generate a CSR using the private key. The CSR contains information about the entity requesting the certificate and the public key that will be included in the certificate.
Sign the CSR with your private CA. If you intend to use the TLS certificate for testing or internal purposes, you can sign the CSR yourself by your private CA instead of a publicly trusted CA.
Install the certificate on the server. Install the signed certificate on the server that will use it. This typically involves configuring the server software—such as the Apache Web server—to use the certificate for securing communication.
Configure the server and client for secure communication. After the certificate is installed on the server, configure the server and client software to use secure communication protocols, for example, HTTPS that uses the certificate for encryption and authentication.
Regular maintenance and renewal. Regularly monitor the validity of the certificate and renew it before it expires. Keep the private key secure and ensure that certificates are properly configured and updated as needed.
3 Creating a private CA #
If you do not plan to get the server certificate signed by a trusted CA, create your private CA. Such an approach is fine for testing and internal scenarios, but not for production network applications.
To perform selected tasks, you need
rootorsudoprivileges.
Generate a private key and a certificate for your private CA. The following command creates a new 2048 bit-long RSA key using the SHA-256 hash algorithm. During its creation, you will be asked for an encryption passphrase. Remember the passphrase because you will need it when signing the server CSR with your private CA in Section 6, “Signing a CSR”.
>openssl req -x509 -sha256 -days 3650 -newkey rsa:2048 \ -subj "/CN=myRootCA/C=CZ/L=Prague" -keyout myRootCA.key -out myRootCA.crtReplace the
-subjvalue with your suitable string.Secure the private key by restricting its permissions and ownership so that only the
rootcan read it.>sudochownroot:rootmyRootCA.key>sudochmod 600 myRootCA.key(Optional) Verify the validity of the CA private key.
>openssl pkey -check -in myRootCA.key Enter pass phrase for myRootCA.key: Key is valid -----BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQCq/oAhZ0VGSsGb [...] 8q3vKA+KRtxhMgW1f50U2qo= -----END PRIVATE KEY-----(Optional) Verify your private CA by displaying its basic data. It must include the
CA:TRUEflag.>openssl x509 -in myRootCA.crt -text -noout Certificate: [...] Signature Algorithm: sha256WithRSAEncryption Issuer: CN = myRootCA, C = CZ, L = Prague Validity Not Before: Apr 23 14:41:53 2024 GMT Not After : Apr 17 14:41:53 2029 GMT Subject: CN = myRootCA, C = CZ, L = Prague X509v3 extensions: [...] X509v3 Basic Constraints: critical CA:TRUE [...]
To trust the server certificate, client machines need to know the private CA certificate with which the server's private certificate was signed. Refer to Section 7.3, “Adding new CA certificates” for details about storing CA certificates in a system-wide certificate store on the client.
Create a server private TLS key as described in Section 4, “Creating a server private key”.
4 Creating a server private key #
A server needs a private TLS key to encrypt data required by a client. The following procedure describes how to generate it.
To perform selected tasks, you need
rootorsudoprivileges.
Generate a private TLS key. The following example generates an unencrypted 256-bit ECDSA key.
TipYou can verify if ECDSA keys are supported by listing its available elliptic curves with the
openssl ecparam -list_curvescommand.>openssl ecparam -name prime256v1 -genkey -out server.keyThe speed of generating the key depends on the hardware, the selected encryption algorithm, and the length of the key.
Move the generated private key to a safe location on the server and secure it by restricting its permissions and ownership so that only the
rootcan read it.>sudochownroot:rootserver.key>sudochmod 600 server.key(Optional) Verify the consistency of the private key.
>sudoopenssl pkey -check -in server.key Key is valid -----BEGIN PRIVATE KEY----- MIGHAgEAMBMGByqGSM49AgEGCCqGSM49AwEHBG0wawIBAQQgUnW551Qru4+pbWqu JRXQVFi45N1j+qmx7dEnr+8eox+hRANCAAR+rRLHBGjq2H2jOq09efVt99JB/R7h QkDLjVMa9jemVH1g3YiVIEAHyCVjms2rC06lkU1S+z8WsRjh6A/ev8// -----END PRIVATE KEY-----
Create a certificate signing request (CSR) so that your preferred CA can sign and validate it. Find more details in Section 5, “Creating a CSR”.
5 Creating a CSR #
Establishing TLS encrypted communication requires a valid TLS certificate signed by a CA. To obtain such a certificate, you need to create a certificate signing request (CSR).
You have previously created a private TLS key as described in Section 4, “Creating a server private key”.
(Optional) Prepare a configuration template that simplifies the process of creating your CSR, for example:
>cat example_csr.cnf [req] prompt = no distinguished_name = dn req_extensions = re [dn] countryName = CZ localityName = Prague organizationName = Example organization commonName = www.example.org emailAddress =wilber@example.org [re] extendedKeyUsage = serverAuth,clientAuth [alt_names] DNS.1 = example.org DNS.2 = www.example.org IP.1 = 10.0.0.5 IP.2 = 10.0.0.6Important: Exact request matchesThe
[alt_names]section can list domain names and IP addresses that must match the URL that the client will request. In the above example, while the following requests will be accepted:https://example.org/ https://www.example.org/ https://10.0.0.5/ https://10.0.0.6/
the request for
https://www2.example.org/will be refused.If you previously prepared a CSR template, create the CSR using the template and the private key.
>openssl req -new -key server.key \ -config example_csr.cnf \ -out server.csrIf you did not prepare the CSR template, omit the
-configoption from the command above.>openssl req -new -key server.key -out server.csrYou will be prompted for additional information about the certificate. When asked for a
challenge passwordand anoptional company name, leave it blank.Important: Common NameThe
Common Name (CN)value must be the fully qualified host name of the server host.You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:CZ State or Province Name (full name) [Some-State]: Czech Republic Locality Name (eg, city) []:Prague Organization Name (eg, company) [Internet Widgits Pty Ltd]:Example organization Organizational Unit Name (eg, section) []: Common Name (e.g. server FQDN or YOUR name) []:www.example.org Email Address []:wilber@example.org Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
Submit the CSR to a CA of your choice. If you want to use the certificate inside a trusted network, you can sign the certificate with your private CA as described in Section 6, “Signing a CSR”.
6 Signing a CSR #
Establishing TLS encrypted communication requires that a certificate authority (CA) signs the certificate signing request (CSR). For testing or internal purposes, you can sign the CSR yourself by a private CA.
You created a private TLS key as described in Section 4, “Creating a server private key”.
You created a CSR file as described in Section 5, “Creating a CSR”.
(Optional) Prepare an optional configuration file that specifies additional server and client extensions, for example:
>cat example_ssl_ext.cnf [ server-cert ] keyUsage = digitalSignature, keyEncipherment extendedKeyUsage = serverAuth basicConstraints=CA:FALSE [ client-cert ] keyUsage = digitalSignature extendedKeyUsage = clientAuth basicConstraints=CA:FALSESign the CSR with your private CA, optionally using the extension configuration file. You will be asked for your private CA passphrase that you entered per Section 3, “Creating a private CA”.
openssl x509 -req -days 730 -in server.csr -out server.crt \ -CA myRootCA.crt -CAkey myRootCA.key -CAcreateserial \ -extfile example_ssl_ext.cnf -extensions server-cert
The certificate remains valid for two years. Adjust the value to your needs. After this period, you must create a new CSR and have a CA sign the certificate.
The
server.crtfile will be created that includes the signed certificate.(Optional) Verify that the data included in the resulting certificate matches your requirements.
>openssl x509 -text -noout -in server.crt [...] Issuer: C = CZ, ST = Some-State, L = Prague, O = Example organization, CN = www.example.org, emailAddress =wilber@example.org Validity Not Before: Apr 15 09:18:11 2024 GMT Not After : Apr 15 09:18:11 2026 GMT Subject: C = CZ, ST = Some-State, L = Prague, O = Example organization, CN = www.example.org, emailAddress =wilber@example.org Subject Public Key Info: Public Key Algorithm: id-ecPublicKey[...] X509v3 extensions: X509v3 Key Usage: Digital Signature, Key Encipherment X509v3 Extended Key Usage: TLS Web Server Authentication [...]
Install the certificate on the server that will use it for providing encrypted content.
7 System-wide CA certificate store #
A shared system-wide CA store is a centralized repository for storing trusted root certificates and user-specific certificates on a system. This store is used by software applications and components within the operating system to establish secure connections, validate the authenticity of TLS certificates presented by servers, and verify the identity of individuals or entities. By default, the store contains the Mozilla CA certificate list included in the ca-certificates-mozilla package. You can either update this list or select another certificate list.
By default, there are two different CA certificate stores in SLES: the OpenSSL-based store and the NSS (Network Security System)-based store. Many GUI-based Web browsers—such as Firefox—use the NSS certificate store. To avoid installing CA certificates in both certificate stores, install the plug-in package p11-kit-nss-trust that makes the NSS store look up certificates in the OpenSSL store automatically.
7.1 Where is the CA certificate store on the file system? #
In SLES, the shared system-wide certificate store is located in the following directories:
- /usr/share/pki/trust/anchors
CA certificates trust anchors provided by the system.
- /usr/share/pki/trust/blacklist
Distrusted CA certificates provided by the system.
- /etc/pki/trust/anchors
CA certificates trust anchors provided by the system administrators.
- /etc/pki/trust/blacklist
Distrusted CA certificates provided by the system administrators.
7.2 Benefits of using a system-wide CA certificate store #
Some of the key benefits of using a shared certificate store are:
Security: Centralizing trusted certificates helps ensure that all applications and services use a consistent set of trusted certificates to verify the authenticity of TLS connections.
Simplified management: Instead of each application or service maintaining its own list of trusted certificates, they can rely on the system-wide certificate store.
Ease of update: System administrators can update the trusted certificates in the system-wide store as needed, either manually or through automated mechanisms such as operating system updates. This ensures that systems remain up to date with the latest trusted certificates and security standards.
7.3 Adding new CA certificates #
To let applications know about a new private CA certificate on the system,
add it to a system-wide certificate store on the client and use
the update-ca-certificates command to update the store.
The ca-certificate package is installed on the system.
You created a CA certificate as described in Section 3, “Creating a private CA”.
To perform selected tasks, you need
rootorsudoprivileges.
Copy the certificate file to the
/etc/pki/trust/anchorsdirectory.>sudocp myRootCA.crt /etc/pki/trust/anchors/Update the system-wide certificate store.
>sudoupdate-ca-certificates
The
man 8 update-ca-certificatesmanual page.
8 Troubleshooting #
This topic describes how to examine TLS certificates.
8.1 How do I examine a TLS certificate? #
To review a server certificate that is available locally as a file, use the following command:
> openssl x509 -in server.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
6a:43:f5:55:ef:03:ee:0e:23:c8:99:82:71:39:f2:22:1a:da:53:db
Signature Algorithm: ecdsa-with-SHA256
Issuer:1 C = CZ, ST = Some-State, L = Prague, O = Example organization, CN = www.example.org, emailAddress = wilber@example.org
Validity2
Not Before: Apr 15 09:30:31 2024 GMT
Not After : May 15 09:30:31 2024 GMT
Subject:3 C = CZ, ST = Some-State, L = Prague, O = Example organization, CN = www.example.org, emailAddress = wilber@example.org
Subject Public Key Info:
Public Key Algorithm: id-ecPublicKey
Public-Key: (256 bit)
pub:
04:7e:ad:12:c7:04:68:ea:d8:7d:a3:3a:ad:3d:79:
[...]
ASN1 OID: prime256v1
NIST CURVE: P-256
X509v3 extensions:
X509v3 Subject Alternative Name:4
DNS:*.example.org, DNS:example.org
X509v3 Key Usage:5
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
Signature Algorithm: ecdsa-with-SHA256
30:46:02:21:00:a8:4f:7d:16:f2:93:01:b9:3d:31:e3:c6:6c:
[...]Describes who issued the certificate. It shows only the parent-level issuer, not the top-level issuer from the certificate chain. | |
Displays certificate validity time. | |
Describes the server that uses the certificate. The most important
attribute is | |
When used, it overrides the subject's | |
Specifies purposes for which the certificate can be used. |
8.2 How do I download server TLS certificate files? #
The following command downloads just the server certificate from the example server suse.com. Replace it with the domain name of the server you want to examine.
> echo | openssl s_client -showcerts -connect suse.com:443 2>/dev/null \
| openssl x509 -out 1.pemMost public servers use several subordinate CAs in the certificate chain. To download the whole certificate chain into individual files, use the following command:
> echo | openssl s_client -showcerts -connect suse.com:443 2>/dev/null \
| awk -v RS="-----BEGIN CERTIFICATE-----" \
'NR>1{sub(/-----END CERTIFICATE-----.*/,"-----END CERTIFICATE-----"); \
print RS$0>NR-1".pem"}'
The command writes all certificate files named increasingly
1.pem, 2.pem and so on, up to
the last certificate in the chain.
8.3 How do I verify the whole TLS certificate chain? #
The client host normally has a collection of root CAs and verifies the
server certificates against them. But the certificate that the server
provides can be a subordinate CA. To trust the server's certificate, the
client needs to verify its complete
TLS certificate chain. The server sends all
certificates as part of its Server Hello message and
you can download them as described in
Section 8.2, “How do I download server TLS certificate files?”.
The openssl command uses the -subject_hash
and -issuer_hash options to retrieve the
subject and issuer hashes from a certificate, for example:
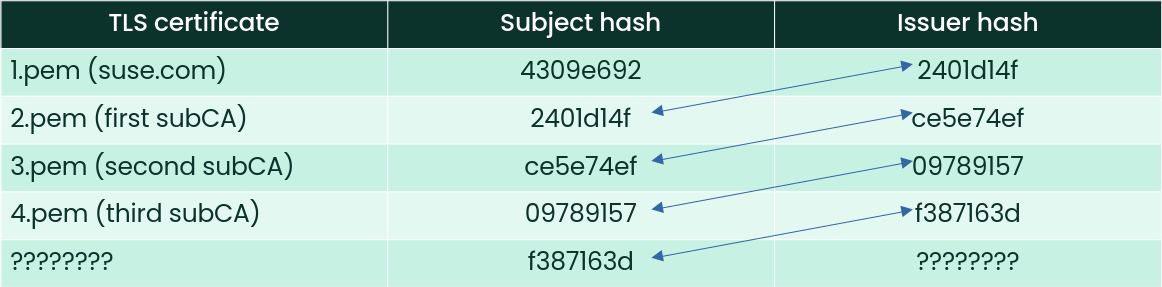
> openssl x509 -in 1.pem -noout -issuer_hash
2401d14f
The client compares the issuer hash 2401d14f with the
issuer hashes of its collection of root CAs. In this case, no root CA has
an issuer hash of 2401d14f. As the client cannot trust
the server yet, it has to verify the other certificates from the chain as
well. Notice that the next certificate in the chain has the
-subject_hash identical to the
-issuer_hash from the server certificate.
> openssl x509 -in 2.pem -noout -subject_hash
2401d14fDisplay the issuer hash of this certificate.
> openssl x509 -in 2.pem -noout -issuer_hash
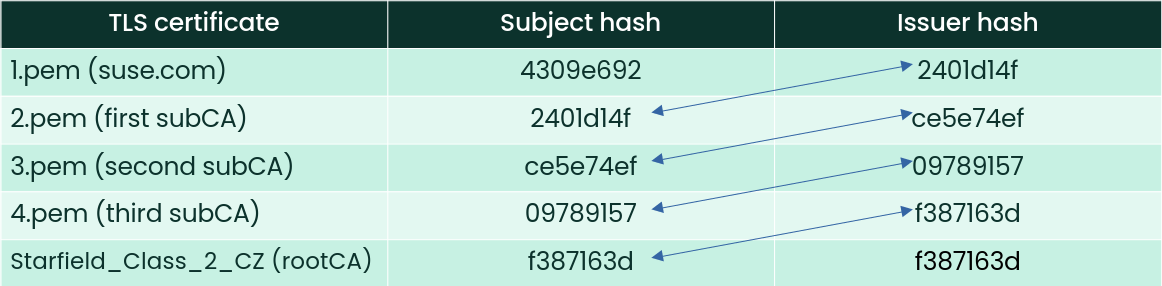
ce5e74efAgain, this issuer hash cannot be found among the client's root CAs. Continue with checking the issuer and subject hashes of the next certificates in the chain until you reach the last one. The results are summarized in the following table:
The last issuer hash f387163d finally has a matching
CA:
> ls -l /etc/ssl/certs/f387163d*
lrwxrwxrwx 1 root root 24 Oct 4 09:55 /etc/ssl/certs/f387163d.0 -> Starfield_Class_2_CA.pemIf the discovered issuer certificate is valid, you can trust the server as much as you trust the root CAs in your client certificate store.
> openssl x509 -in /etc/ssl/certs/Starfield_Class_2_CA.pem -noout -dates
notBefore=Jun 29 17:39:16 2004 GMT
notAfter=Jun 29 17:39:16 2034 GMTTo confirm that the certificate is a root CA, check its subject and issuer hashes. Because root CA certificates are self-signed, they have both hashes identical.
> openssl x509 -in /etc/ssl/certs/Starfield_Class_2_CA.pem -noout -issuer_hash -subject_hash
f387163d
f387163dThe complete certificate chain then looks as follows:
9 Legal Notice #
Copyright© 2006–2026 SUSE LLC and contributors. All rights reserved.
Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”.
For SUSE trademarks, see https://www.suse.com/company/legal/. All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its affiliates. Asterisks (*) denote third-party trademarks.
All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its affiliates, the authors, nor the translators shall be held liable for possible errors or the consequences thereof.