17 Managing Users with YaST #
During installation, you could have created a local user for your system. With the YaST module you can add more users or edit existing ones. It also lets you configure your system to authenticate users with a network server.
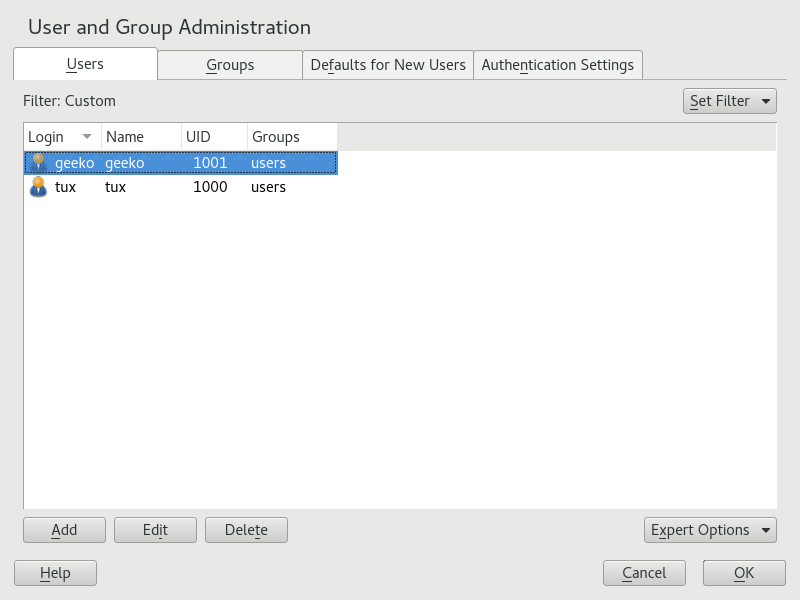
17.1 User and Group Administration Dialog #
To administer users or groups, start YaST and click › . Alternatively, start the dialog directly by running sudo
yast2 users & from a command line.
Every user is assigned a system-wide user ID (UID). Apart from the users which can log in to your machine, there are also several system users for internal use only. Each user is assigned to one or more groups. Similar to system users, there are also system groups for internal use.
Depending on the set of users you choose to view and modify with, the dialog (local users, network users, system users), the main window shows several tabs. These allow you to execute the following tasks:
- Managing User Accounts
From the tab create, modify, delete or temporarily disable user accounts as described in Section 17.2, “Managing User Accounts”. Learn about advanced options like enforcing password policies, using encrypted home directories, or managing disk quotas in Section 17.3, “Additional Options for User Accounts”.
- Changing Default Settings
Local users accounts are created according to the settings defined on the tab. Learn how to change the default group assignment, or the default path and access permissions for home directories in Section 17.4, “Changing Default Settings for Local Users”.
- Assigning Users to Groups
Learn how to change the group assignment for individual users in Section 17.5, “Assigning Users to Groups”.
- Managing Groups
From the tab, you can add, modify or delete existing groups. Refer to Section 17.6, “Managing Groups” for information on how to do this.
- Changing the User Authentication Method
When your machine is connected to a network that provides user authentication methods like NIS or LDAP, you can choose between several authentication methods on the tab. For more information, refer to Section 17.7, “Changing the User Authentication Method”.
For user and group management, the dialog provides similar functionality. You can easily switch between the user and group administration view by choosing the appropriate tab at the top of the dialog.
Filter options allow you to define the set of users or groups you want to modify: On the or tab, click to view and edit users or groups according to certain categories, such as or , for example (if you are part of a network which uses LDAP). With › you can also set up and use a custom filter.
Depending on the filter you choose, not all of the following options and functions will be available from the dialog.
17.2 Managing User Accounts #
YaST offers to create, modify, delete or temporarily disable user accounts. Do not modify user accounts unless you are an experienced user or administrator.
File ownership is bound to the user ID, not to the user name. After a user ID change, the files in the user's home directory are automatically adjusted to reflect this change. However, after an ID change, the user no longer owns the files they created elsewhere in the file system unless the file ownership for those files is manually modified.
In the following, learn how to set up default user accounts. For further options, refer to Section 17.3, “Additional Options for User Accounts”.
Open the YaST dialog and click the tab.
With define the set of users you want to manage. The dialog lists users in the system and the groups the users belong to.
To modify options for an existing user, select an entry and click .
To create a new user account, click .
Enter the appropriate user data on the first tab, such as (which is used for login) and . This data is sufficient to create a new user. If you click now, the system will automatically assign a user ID and set all other values according to the default.
Activate if you want any kind of system notifications to be delivered to this user's mailbox. This creates a mail alias for
rootand the user can read the system mail without having to first log in asroot.The mails sent by system services are stored in the local mailbox
/var/spool/mail/USERNAME, where USERNAME is the login name of the selected user. To read e-mails, you can use themailcommand.To adjust further details such as the user ID or the path to the user's home directory, do so on the tab.
If you need to relocate the home directory of an existing user, enter the path to the new home directory there and move the contents of the current home directory with . Otherwise, a new home directory is created without any of the existing data.
To force users to regularly change their password or set other password options, switch to and adjust the options. For more details, refer to Section 17.3.2, “Enforcing Password Policies”.
If all options are set according to your wishes, click .
Click to close the administration dialog and to save the changes. A newly added user can now log in to the system using the login name and password you created.
Alternatively, to save all changes without exiting the dialog, click › .
root Account
While it is technically possible to rename the root account, certain applications,
scripts or third-party products may rely on the existence of a user called root. While
such a configuration always targets individual environments, necessary adjustments could be
overwritten by vendor updates, so this becomes an ongoing task, not a one-time setting.
This is especially true in very complex setups involving third-party applications, where it
needs to be verified with every involved vendor whether a rename of the root account is
supported.
As the implications for renaming the root account cannot be foreseen, SUSE does not
support renaming the root account.
Usually, the idea behind renaming the root account is to hide it or make it unpredictable.
However, /etc/passwd requires 644 permissions for
regular users, so any user of the system can retrieve the login name for the
user ID 0.
For better ways to secure the root account, refer to
Section 2.30, “Restricting root Logins” and
Section 2.30.3, “Restricting SSH Logins”.
For a new (local) user on a laptop which also needs to integrate into a network environment where this user already has a user ID, it is useful to match the (local) user ID to the ID in the network. This ensures that the file ownership of the files the user creates “offline” is the same as if he had created them directly on the network.
Open the YaST dialog and click the tab.
To temporarily disable a user account without deleting it, select the user from the list and click . Activate . The user cannot log in to your machine until you enable the account again.
To delete a user account, select the user from the list and click . Choose if you also want to delete the user's home directory or if you want to retain the data.
17.3 Additional Options for User Accounts #
In addition to the settings for a default user account, SUSE® Linux Enterprise Server offers further options, such as options to enforce password policies, use encrypted home directories or define disk quotas for users and groups.
17.3.1 Automatic Login and Passwordless Login #
If you use the GNOME desktop environment you can configure Auto Login for a certain user and Passwordless Login for all users. Auto login causes a user to become automatically logged in to the desktop environment on boot. This functionality can only be activated for one user at a time. Login without password allows all users to log in to the system after they have entered their user name in the login manager.
Enabling Auto Login or Passwordless Login on a machine that can be accessed by more than one person is a security risk. Without the need to authenticate, any user can gain access to your system and your data. If your system contains confidential data, do not use this functionality.
to activate auto login or login without password, access these functions in the YaST with › .
17.3.2 Enforcing Password Policies #
On any system with multiple users, it is a good idea to enforce at least basic password security policies. Users should change their passwords regularly and use strong passwords that cannot easily be exploited. For local users, proceed as follows:
Open the YaST dialog and select the tab.
Select the user for which to change the password options and click .
Switch to the tab. The user's last password change is displayed on the tab.
To make the user change his password at next login, activate .
To enforce password rotation, set a and a .
To remind the user to change his password before it expires, set the number of .
To restrict the period of time the user can log in after his password has expired, change the value in .
You can also specify a certain expiration date for the complete account. Enter the in YYYY-MM-DD format. Note that this setting is not password-related but rather applies to the account itself.
For more information about the options and about the default values, click .
Apply your changes with .
17.3.3 Managing Encrypted Home Directories #
To protect data in home directories against theft and hard disk removal, you can create encrypted home directories for users. These are encrypted with LUKS (Linux Unified Key Setup), which results in an image and an image key being generated for the user. The image key is protected with the user's login password. When the user logs in to the system, the encrypted home directory is mounted and the contents are made available to the user.
With YaST, you can create encrypted home directories for new or existing users. To encrypt or modify encrypted home directories of already existing users, you need to know the user's current login password. By default, all existing user data is copied to the new encrypted home directory, but it is not deleted from the unencrypted directory.
Encrypting a user's home directory does not provide strong security from other users. If strong security is required, the system should not be physically shared.
Find background information about encrypted home directories and which actions to take for stronger security in Section 12.2, “Using Encrypted Home Directories”.
Open the YaST dialog and click the tab.
To encrypt the home directory of an existing user, select the user and click .
Otherwise, click to create a new user account and enter the appropriate user data on the first tab.
In the tab, activate . With , specify the size of the encrypted image file to be created for this user.
Apply your settings with .
Enter the user's current login password to proceed if YaST prompts for it.
Click to close the administration dialog and save the changes.
Alternatively, to save all changes without exiting the dialog, click › .
Of course, you can also disable the encryption of a home directory or change the size of the image file at any time.
Open the YaST dialog in the view.
Select a user from the list and click .
to disable the encryption, switch to the tab and disable .
If you need to enlarge or reduce the size of the encrypted image file for this user, change the .
Apply your settings with .
Enter the user's current login password to proceed if YaST prompts for it.
Click to close the administration dialog and save the changes.
Alternatively, to save all changes without exiting the dialog, click › .
17.3.4 Managing Quotas #
To prevent system capacities from being exhausted without notification, system administrators can set up quotas for users or groups. Quotas can be defined for one or more file systems and restrict the amount of disk space that can be used and the number of inodes (index nodes) that can be created there. Inodes are data structures on a file system that store basic information about a regular file, directory, or other file system object. They store all attributes of a file system object (like user and group ownership, read, write, or execute permissions), except file name and contents.
SUSE Linux Enterprise Server allows usage of soft and
hard quotas. Additionally, grace intervals can be
defined that allow users or groups to temporarily violate their quotas by
certain amounts.
- Soft Quota
Defines a warning level at which users are informed that they are nearing their limit. Administrators will urge the users to clean up and reduce their data on the partition. The soft quota limit is usually lower than the hard quota limit.
- Hard Quota
Defines the limit at which write requests are denied. When the hard quota is reached, no more data can be stored and applications may crash.
- Grace Period
Defines the time between the overflow of the soft quota and a warning being issued. Usually set to a rather low value of one or several hours.
To configure quotas for certain users and groups, you need to enable quota support for the respective partition in the YaST Expert Partitioner first.
Quotas for Btrfs partitions are handled differently. For more information, see Section 1.2.5, “Btrfs Quota Support for Subvolumes”.
In YaST, select › and click to proceed.
In the , select the partition for which to enable quotas and click .
Click and activate . If the
quotapackage is not already installed, it will be installed once you confirm the respective message with .Confirm your changes and leave the .
Make sure the service
quotaonis running by entering the following command:systemctl status quotaon
It should be marked as being
active. If this is not the case, start it with the commandsystemctl start quotaon.
Now you can define soft or hard quotas for specific users or groups and set time periods as grace intervals.
In the YaST , select the user or the group you want to set the quotas for and click .
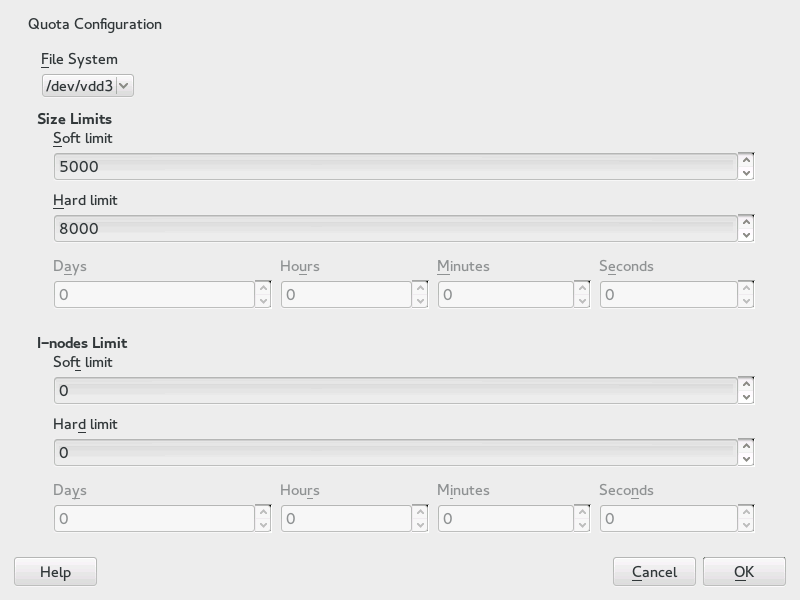
On the tab, select the entry and click to open the dialog.
From , select the partition to which the quota should apply.
Below , restrict the amount of disk space. Enter the number of 1 KB blocks the user or group may have on this partition. Specify a and a value.
Additionally, you can restrict the number of inodes the user or group may have on the partition. Below , enter a and .
You can only define grace intervals if the user or group has already exceeded the soft limit specified for size or inodes. Otherwise, the time-related text boxes are not activated. Specify the time period for which the user or group is allowed to exceed the limits set above.
Confirm your settings with .
Click to close the administration dialog and save the changes.
Alternatively, to save all changes without exiting the dialog, click › .
SUSE Linux Enterprise Server also ships command-line tools like
repquota or warnquota. System
administrators can use these tools to control the disk usage or send e-mail
notifications to users exceeding their quota. Using
quota_nld, administrators can also forward kernel
messages about exceeded quotas to D-BUS. For more information, refer to the
repquota, the warnquota
and the quota_nld man page.
17.4 Changing Default Settings for Local Users #
When creating new local users, several default settings are used by YaST. These include, for example, the primary group and the secondary groups the user belongs to, or the access permissions of the user's home directory. You can change these default settings to meet your requirements:
Open the YaST dialog and select the tab.
To change the primary group the new users should automatically belong to, select another group from .
To modify the secondary groups for new users, add or change groups in . The group names must be separated by commas.
If you do not want to use
/home/USERNAMEas default path for new users' home directories, modify the .To change the default permission modes for newly created home directories, adjust the umask value in . For more information about umask, refer to Chapter 11, Access Control Lists in Linux and to the
umaskman page.For information about the individual options, click .
Apply your changes with .
17.5 Assigning Users to Groups #
Local users are assigned to several groups according to the default settings which you can access from the dialog on the tab. In the following, learn how to modify an individual user's group assignment. If you need to change the default group assignments for new users, refer to Section 17.4, “Changing Default Settings for Local Users”.
Open the YaST dialog and click the tab. It lists users and the groups the users belong to.
Click and switch to the tab.
To change the primary group the user belongs to, click and select the group from the list.
To assign the user additional secondary groups, activate the corresponding check boxes in the list.
Click to apply your changes.
Click to close the administration dialog and save the changes.
Alternatively, to save all changes without exiting the dialog, click › .
17.6 Managing Groups #
With YaST you can also easily add, modify or delete groups.
Open the YaST dialog and click the tab.
With define the set of groups you want to manage. The dialog lists groups in the system.
To create a new group, click .
To modify an existing group, select the group and click .
In the following dialog, enter or change the data. The list on the right shows an overview of all available users and system users which can be members of the group.
To add existing users to a new group select them from the list of possible by checking the corresponding box. To remove them from the group deactivate the box.
Click to apply your changes.
Click to close the administration dialog and save the changes.
Alternatively, to save all changes without exiting the dialog, click › .
To delete a group, it must not contain any group members. To delete a group, select it from the list and click . Click to close the administration dialog and save the changes. Alternatively, to save all changes without exiting the dialog, click › .
17.7 Changing the User Authentication Method #
When your machine is connected to a network, you can change the authentication method. The following options are available:
- NIS
Users are administered centrally on a NIS server for all systems in the network. For details, see Chapter 3, Using NIS.
- SSSD
The System Security Services Daemon (SSSD) can locally cache user data and then allow users to use the data, even if the real directory service is (temporarily) unreachable. For details, see Section 4.3, “SSSD”.
- Samba
SMB authentication is often used in mixed Linux and Windows networks. For details, see Chapter 30, Samba and Chapter 7, Active Directory Support.
To change the authentication method, proceed as follows:
Open the dialog in YaST.
Click the tab to show an overview of the available authentication methods and the current settings.
To change the authentication method, click and select the authentication method you want to modify. This takes you directly to the client configuration modules in YaST. For information about the configuration of the appropriate client, refer to the following sections:
NIS: Section 3.2, “Configuring NIS Clients”
LDAP: Section 4.2, “Configuring an Authentication Client with YaST”
Samba: Section 30.5.1, “Configuring a Samba Client with YaST”
After accepting the configuration, return to the overview.
Click to close the administration dialog.