8 Deploying a SUSE Linux Enterprise Server instance to support RMT in the public cloud #
You can deploy a SUSE Linux Enterprise Server instance to support RMT in Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure. RMT is included in SLES starting with version 15.
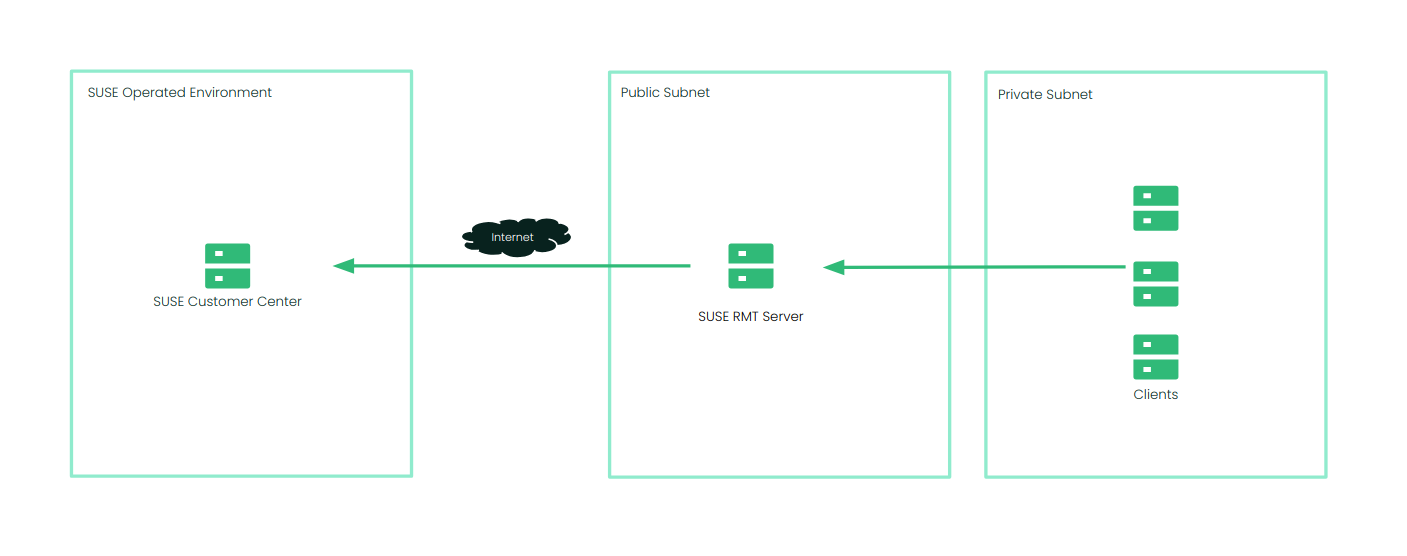
The following example shows a generic cloud architecture for the RMT deployment. Your deployment may look different based on your networking requirements.
8.1 Using a bring-your-own-subscription image #
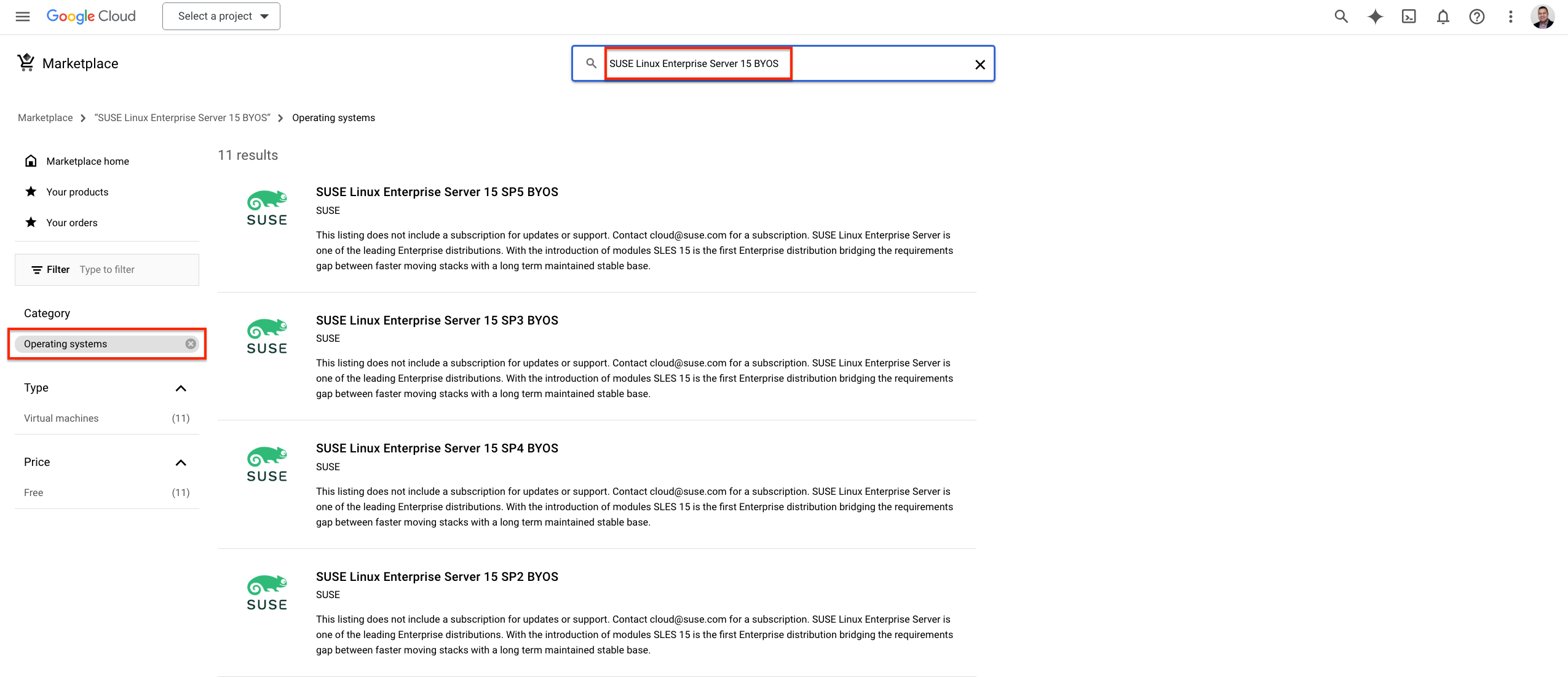
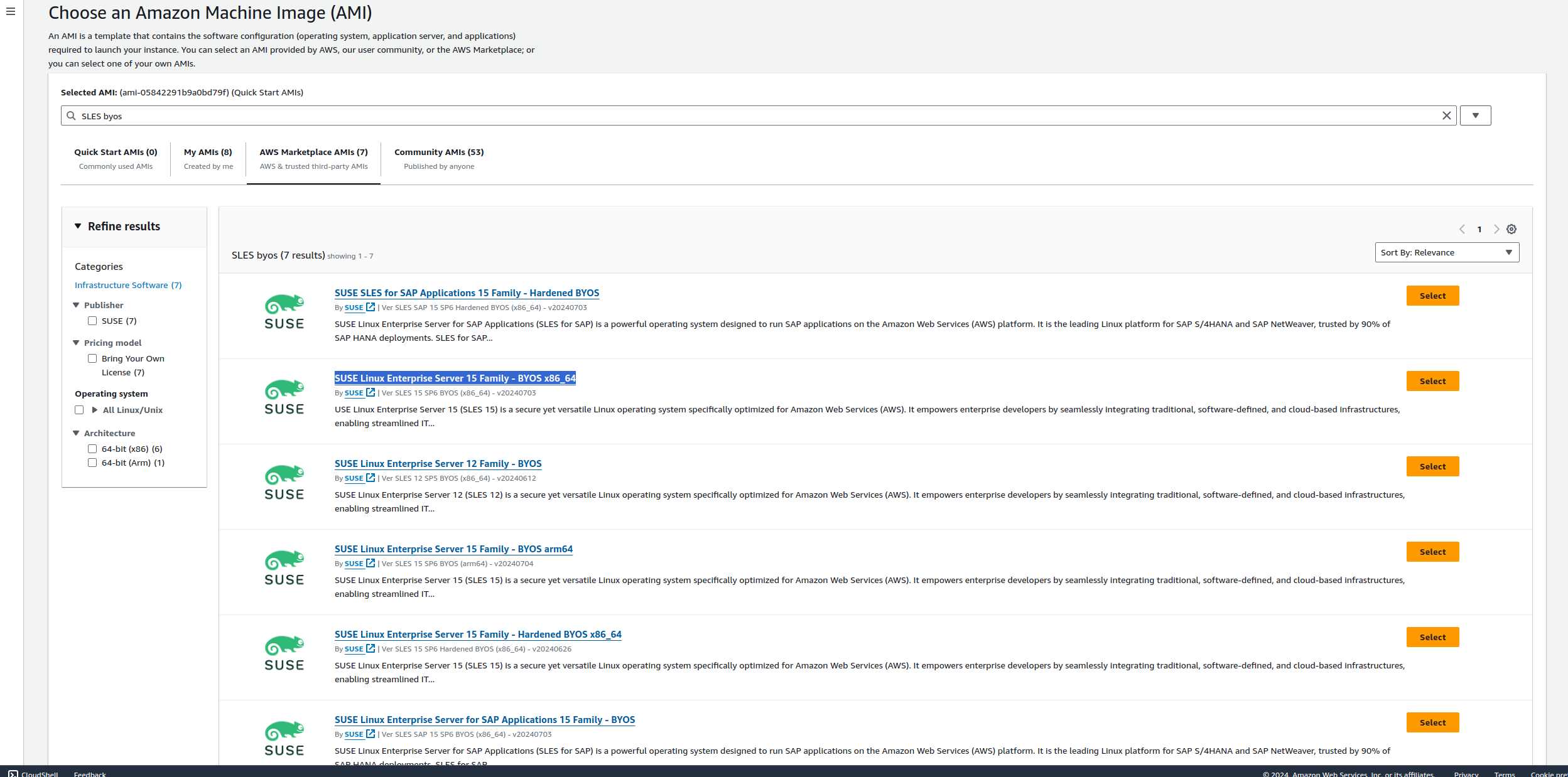
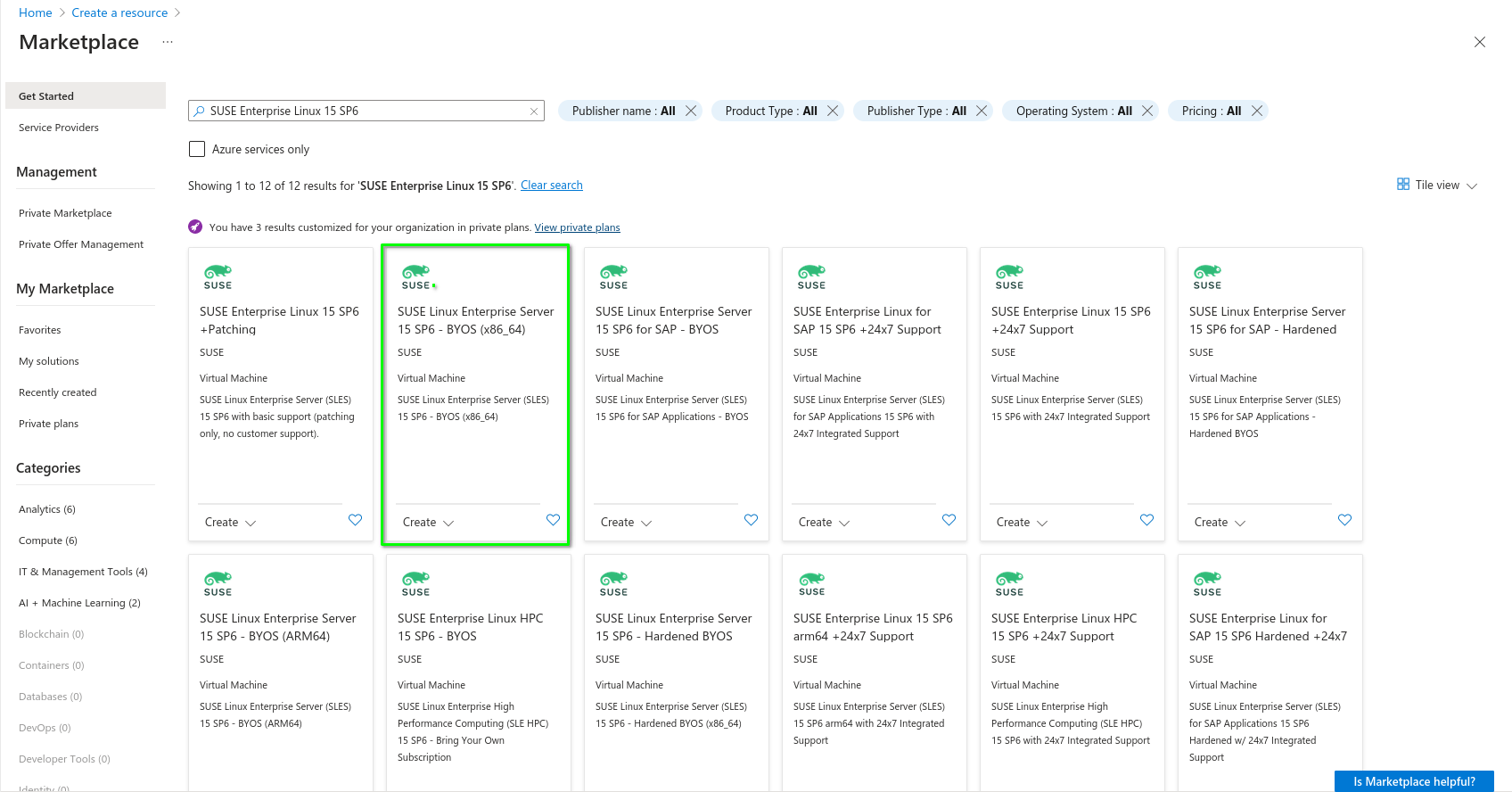
SUSE provides images for SLES in Amazon Web Services, Google Cloud and Microsoft Azure. There are two types of images available: PAYG (Pay-As-You-Go) and BYOS (Bring-Your-Own-Subscription). These images are updated at regular intervals and it is suggested that you deploy new instances from the latest version of the image to ensure the most recent security updates are in place. To support RMT deployment, we recommend deploying an RMT instance from a BYOS image.
8.1.1 Finding images in the cloud marketplace #
The location of the relevant image in each of the cloud provider is shown below:
It is recommended to start with an instance type that has at least
two vCPUs and a minimum of 8 GB RAM to support the RMT deployment.
For example, on Amazon EC2, this could be a t3.large
instance type, and in Microsoft Azure, it could be a B2as_v2
The instance can be rightsized as needed and depends on the number of clients being managed and updated by the RMT server.
8.1.2 Registering the SLES instance #
After the SLES instance deployment, you must register the instance with the SUSE Customer Center.
Registering with the SUSE Customer Center requires a SUSE account. If you do not have a SUSE account yet, go to the SUSE Customer Center home page (https://scc.suse.com/) to create one.
To connect your instance:
AWS:
>ssh -i SSH_KEY EC2_USER_ID@SERVER_IP
Google Cloud:
>gcloud compute ssh GCE_INSTANCE_IP
Azure:
>ssh AZURE_USER_ID@SERVER_IP
To register the SLES instance with SCC:
>sudoSUSEConnect -e EMAIL_ADDRESS -r REGISTRATION_CODE
The registration code is available once you log in to SCC.
8.2 Considerations when using RMT #
You must consider the following requirements when you use RMT:
- Disk space
The RMT server requires sufficient disk space to mirror the repositories. Downloaded packages are available in
/var/lib/rmt/public/repo/. Disk space is dependent on the number of repositories you mirror. We recommend a minimum of 1.5 times the total size of all enabled repositories. It is a best practice to provision an additional disk volume to support this requirement. You can either mount the volume to/var/lib/rmt/public/repo/on instance creation or immediately after the launch. For Azure, this is an additional disk volume. For AWS, it is an Amazon EBS volume and for GCP, it is a persistent disk volume .- IP or DNS resolution
A static IP address or a DNS name is required in order for clients to connect to the RMT server. In Azure, AWS and GCP, a DNS provided by the Cloud Service Provider (CSP) is assigned when the instance is launched. This IP or DNS may change if the instance is re-created. For Azure, consider using a static IP address to provide a consistent connection point for your clients. In AWS, this would be an elastic IP or Route53. In GCP, this would be a cloud DNS record that uses a static IP address.
- Connectivity for the RMT server
The RMT server can connect to SCC on ports 80 and 443. There are many ways to provide connectivity. For example, in AWS, connectivity to SCC can be provided via an AWS Internet Gateway, an AWS NAT Gateway, or via a local data center (VPN/DX Connection) but this is depends on whether the RMT instance is in a public or private subnet. GCP provides direct access to the Internet via the VPC routes or Cloud NAT services. Azure offers similar services.
- Connectivity for clients
Clients can connect to RMT on ports 80 and 443. When launching the SLES instance to support RMT, check if network connectivity allows inbound access to the RMT server from your clients (HTTP/HTTPS). For AWS, when a SLES instance is launched to support RMT, it is possible to use an existing AWS security group or a new one. The security group must be configured to allow inbound access to the RMT server from your clients. For GCP, the firewall rules must be configured to allow inbound access to the RMT server from your clients.
8.3 More information #
https://documentation.suse.com/sles/15-SP6/html/SLES-all/cha-rmt-mirroring.html#sec-rmt-mirroring-credentials Organization credentials to create a local mirror of the SUSE Linux Enterprise repositories.
https://documentation.suse.com/sles/15-SP6/html/SLES-all/cha-register-sle.html#sec-register-sle-installation Register and activate SUSE Linux Enterprise Server with the SUSE Customer Center.