2 Public cloud images #
SUSE offers a variety of different product images for different use cases in partner cloud provider frameworks. Learn how to find the image that meets your use case.
2.1 Image lifecycle #
All SUSE public cloud images follow a refresh cycle up to the point of deletion. The refresh cycle follows a 'rolling' three month time frame. What this means:
Images in
activeandinactivestates are refreshed every three months. Replaced images are moved to thedeprecatedstate.If a critical security vulnerability occurs, images in
activeandinactivestates are updated as soon as possible once the fix for the affected code is available. For images inactiveandinactivestates the three month timer restarts with this forced replacement.SUSE is committed to address all security vulnerabilities disclosed through the
Common Vulnerabilities and Exposures process(CVE) and a score of 9.0 or greater in theCommon Vulnerability Scoring System(CVSS). For more information about the effects and rating of CVEs, refer to the SUSE CVE database.
The life cycle of an image consists of four different states:
- Active
Active images are fully supported and refreshed at least every three months. The duration lasts until the image is replaced by a newer image version.
- Inactive
Inactive images are supported following the rules of LTSS or ESPOS and will get refreshed at least every three months. The duration term is defined by the product. For more information, refer to https://www.suse.com/de-de/support/policy-products/#cloud
- Deprecated
Deprecated images may no longer be supported. The status of support depends on the support status of the product in the image. Deprecated images do not get refreshed and are not made available in regions added after an image has been set to
deprecated. At the end of the six month deprecation period, images are subject to deletion. It is strongly discouraged to use deprecated images to create new instances.- Deleted
Deleted images are no longer supported or available for instance creation.
active images for new instances
It is strongly recommended to only use active images to
launch instances for new deployments.
2.2 Naming scheme #
Names for SUSE's public cloud images consist of multiple parts that contain information about the product, its version, a time stamp indicating the release date of the image, and more. The general naming scheme for SUSE's public cloud images is as follows:
PRODUCT-FLAVOR-vVERSION-VIRTUALIZATION-STORAGE-ARCHITECTURE-TAXID-GEN
Not all components of this naming scheme are used in all frameworks.
PRODUCTAbbreviated name of the product in lower case letters, e.g.
suse-sles-15-sp3orsuse-manager-4-1-proxy. This part may also be “search-optimized” per cloud framework. For example the prefixsuse-helps when searching for SUSE in the general catalog in Amazon Web Services.FLAVORImages can have different flavors such as
chostorbyos. If it is the default image of a product, this part will be omitted. MultipleFLAVORattributes may be combined in an image name. For examplesles-15-sp3-chost-byosis an image build based on SUSE Linux Enterprise Server 15 SP3 build as a container host using a BYOS (Bring Your Own Subscription) billing model. Images withoutbyosin the name are set up the image is set up for PAYG (Pay As You Go) billing. For more information about the different billing models, refer to Section 1.3, “Plans”.SUSE Linux Enterprise flavors #byos: Bring your own subscription (BYOS) imagechost: Minimal container host imagehardened: Pre-hardened images, see Section 2.5, “Hardened Images”hpc: SUSE Linux Enterprise High Performance Computing imagesap: SUSE Linux Enterprise Server for SAP applications imagesapcal: SAP Cloud Application Library image
Not all flavors are available for all cloud frameworks; some are provider-specific.
Amazon Web Services flavors #ecs: Amazon Elastic Container Service image
Microsoft Azure flavors #basic: PAYG image that only includes updates but is not eligible for support (see Section 1.4, “Support”) or LTSS (see Section 3.3, “Enabling LTSS”).standard: Fully supported PAYG image
VERSIONUpload date of the image in the format
vYYYYMMDD(ISO 8601).VIRTUALIZATION(AWS-only)SUSE no longer supports or publishes para-virtualized images. The virtualization type was encoded as
pv(para-virtualized) orhvm(hardware-assisted virtual machine). Thehvmpart of the image name has been retained in an effort to not break backward compatibility.STORAGE(AWS-only)SUSE no longer publishes images that are based on hard disk (magnetic) backed storage. This used to be encoded as
mag. All published images are backed by SSD. Thessdpart of the image name has been retained in an effort to not break backward compatibility.ARCHITECTUREEither
x86_64orarm64. SUSE no longer supports or publishes 32 bitx86images. Images with thei386identifier are visible in Public Cloud Information Tracker data.TAXIDEither
llcorltd. Only for images with SUSE priority support. For more information, refer to Section 1.4, “Support”GENERATION(Microsoft Azure-only)appended as
gen2for 2nd Generation VMs.
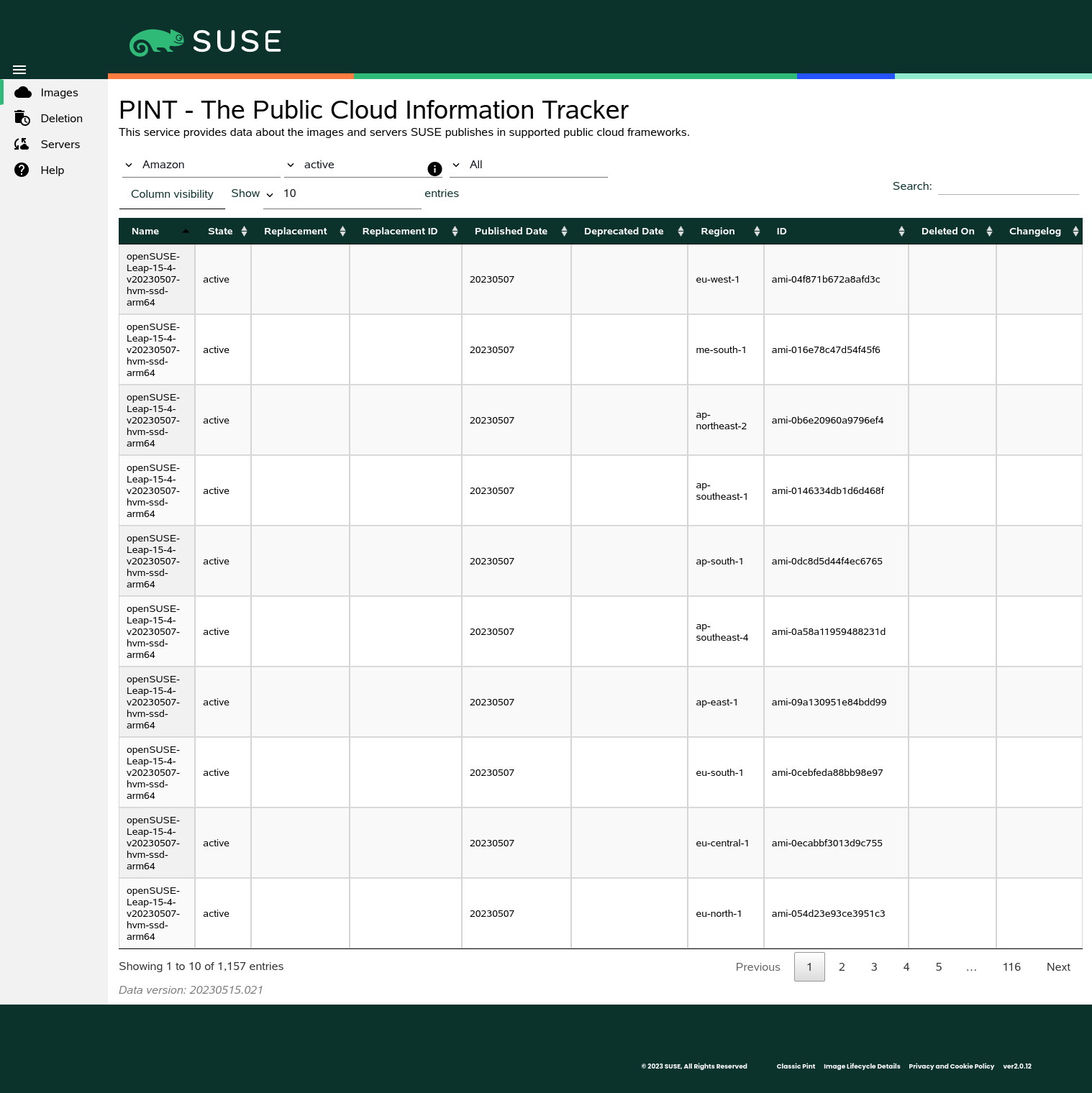
2.3 Public Cloud Information Tracker #
The Public Cloud Information Tracker (PINT) provides information about the images SUSE publishes
and servers that are part of the SUSE operated update infrastructure.
PINT is available at https://pint.suse.com/ and provided as an API
and command-line tool with the python3-susepubliccloudinfo
package from the Public Cloud Module repository.
Use the drop-down lists to view images, servers, or both, and filter by cloud framework, region, or image state. You can also search for strings and adjust the columns and the number of results per page.
2.3.1 Images view #
The following columns are shown in the Images view. Some columns depend on
the the cloud frameworks.
Images view #- Name
Name of the image. For more information about the image naming scheme, refer to Section 2.2, “Naming scheme”.
- State
State of the image. Can be one of
All states,active,inactive,deprecated, ordeleted. Note thatAll Statesexcludes images in thedeletedstate. Deleted images may be viewed by explicitly selectingdeletedas the image state. For more information information about image stated, refer to Section 2.1, “Image lifecycle”.- Replacement
Name of the image that replaces another.
- Replacement ID
ID of the image that replaces another. Only shown for Amazon, Oracle, and Alibaba; images on Google and Microsoft do not have IDs.
- Published Date
Publication date of the image. Displayed in the format
YYYYMMDD(ISO 8601).- Deprecated Date
Date the image was deprecated by a newer one. Displayed in the format
YYYYMMDD(ISO 8601). Only shown for deprecated or deleted images.- Project
Project of the image. Projects are used to organize Google Cloud Platform resources. Only shown for Google Cloud Platform.
- Region
Region of the image.
- Environment
Environment of the image. Only shown for Microsoft Azure.
- ID
Unique identifier of the image. While the
Nameof an image is the same across different regions, the is unique.- URN
Uniform Resource Name of an image. While the of an image is different across the environments, the
URNis the same. Only shown for Microsoft Azure.- Deleted on
Date the image was deleted in the format
YYYYMMDD(ISO 8601). Only shown for deleted images.- Changelog
Link to a detailed changelog and a software bill of materials (SBOM). For more information, refer to Section 2.4, “Change information”
Image changelogs are only available for images that replace others. For initial images of new product versions, refer to the product's release notes.
2.3.2 Servers view #
The following columns are shown in the Servers view:
Servers view #- Name
Host name of the server. Region servers do not have host names. Host names are not DNS resolvable.
- IP
IP address of the server.
- Region
Region of the server. For optimal performance SUSE provides servers in most regions of a cloud framework.
- Type
One of
regionserver-sles,regionserver-sap, orsmt. In every framework where SUSE operates an update infrastructure, theregionserversystems are randomly distributed across regions and thesmtservers are available in most regions. Every region hasupdateservers assigned.
2.4 Change information #
Whenever a new image gets released, you can review changes compared to the previously released image. Search for an image in PINT and click on its entry in the column.
Image change information is divided into different categories:
- Image configuration changes
This category describes changes in the image setup; for example, if a new service was enabled, kernel parameters were changed, or if packages were added or removed.
- CVE fixes
This category lists security fixes in the image. Entries are cross linked to the SUSE CVE database. For more information, refer to Section 2.1, “Image lifecycle”.
- Package version changes
This category lists all packages that had version changes compared to the previous image and the version in that image.
- Package change logs
This category shows a concatenated changelog of all packages that had changes.
- Software bill of materials (SPDX)
This category shows an SBOM in the
Software Package Data Exchangeformat.SPDXis an open standard backed by the Linux Foundation. For more information, refer to https://spdx.dev/.- Software bill of materials (CycloneDX)
This category shows an SBOM in the
CycloneDXformat. This format is backed by the Open Worldwide Application Security Project (OWASP) foundation. For more information, refer to https://cyclonedx.org/.
Please note that that image change information is only available for updated images, meaning for images that replace previous images of the same product version.
For initial images of new product versions, refer to the product's release notes at https://www.suse.com/releasenotes.
To allow for automatic retrieval of image change information, all URLs follow the schema:
https://publiccloudimagechangeinfo.suse.com/FRAMEWORK/IMAGE/CHANGES.html
FRAMEWORK is the cloud framework as used in the
pintcommand-line tool; i.e. one ofalibaba,amazon,google,microsoft, ororacle.IMAGE is the name of the image as shown by PINT, e.g.
suse-sles-15-sp3-byos-v20220127-hvm-ssd-x86_64.CHANGES is the category of the changes, i. e. one of
cve_fixes,image_changes,package_changelogs, orpackage_version_changes. Do not forget the.htmlextension to complete the URL.
2.5 Hardened Images #
To improve overall security, SUSE provides hardened images of some
products. The images are hardened using OpenSCAP, a collection of open source tools that
implement the Security Content Automation
Protocol (SCAP).
For more information and instructions on how to harden instances with OpenSCAP, refer to Section 3.4, “Hardening instances”.