11 #
Sophisticated system configurations require specific disk setups. You can perform all common partitioning tasks during the installation.
To get persistent device naming with block devices, use the block devices
below /dev/disk/by-id or
/dev/disk/by-uuid.
Logical Volume Management (LVM) is a disk partitioning scheme that is designed to be much more flexible than the physical partitioning used in standard setups. Its snapshot functionality enables easy creation of data backups. Redundant Array of Independent Disks (RAID) offers increased data integrity, performance, and fault tolerance. SUSE Linux Enterprise Server also supports multipath I/O (see Chapter 18, Managing multipath I/O for devices for details). There is also the option to use iSCSI as a networked disk (read more about iSCSI in Chapter 15, Mass storage over IP networks: iSCSI).
Note that for partitioning purposes, disk space is measured in binary
units, rather than in decimal units. For example, if you enter sizes of
1GB, 1GiB or 1G,
they all signify 1 GiB (Gibibyte), as opposed to 1 GB (Gigabyte).
- Binary
1 GiB = 1 073 741 824 bytes.
- Decimal
1 GB = 1 000 000 000 bytes.
- Difference
1 GiB ≈ 1.07 GB.
11.1 Using the #
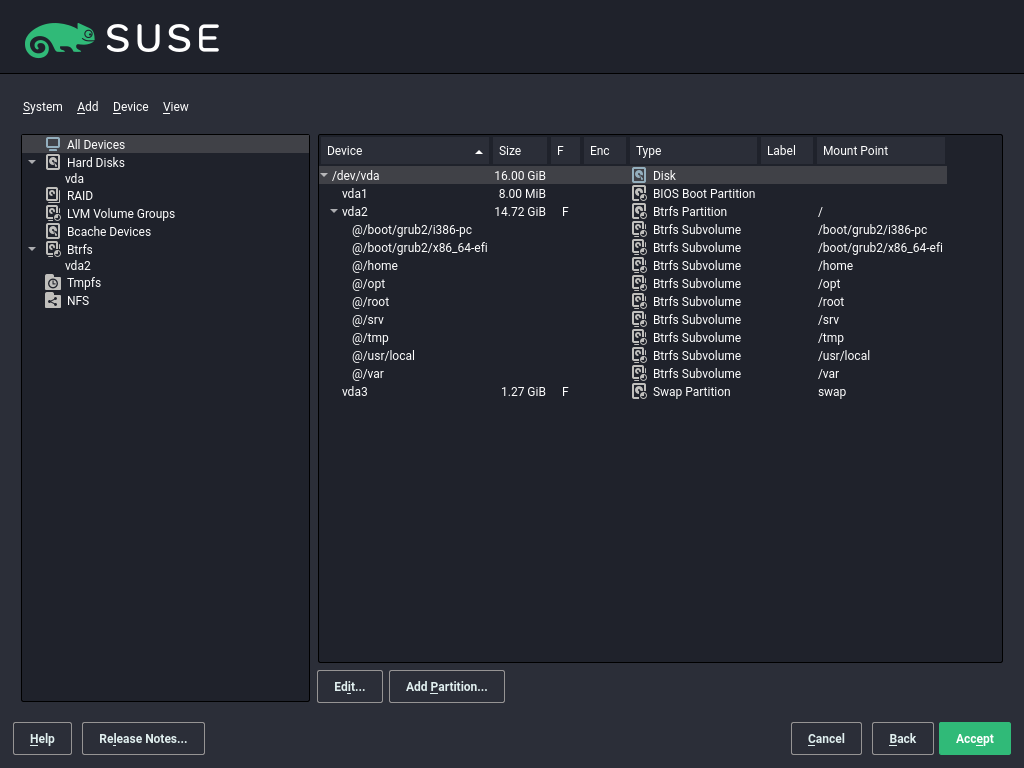
Using the (Figure 11.1, “The YaST partitioner”), you can add, delete, resize, and edit partitions, as well as access the soft RAID, and LVM configuration.
Although it is possible to repartition your system while it is running, the risk of making a mistake that causes data loss is very high. Try to avoid repartitioning your installed system and always create a complete backup of your data before attempting to do so.
IBM Z recognizes only DASD, zFCP and SCSI hard disks. IDE hard disks are
not supported. This is why these devices appear in the partition table as
dasda or sda for the first
recognized device.
All existing or suggested partitions on all connected hard disks are
displayed in the list of in the YaST
dialog. Entire hard disks are listed as
devices without numbers, such as
/dev/sda (or
/dev/dasda). Partitions are listed as parts of
these devices, such as
/dev/sda1 (or
/dev/dasda1, respectively). The size, type,
encryption status, file system, and mount point of the hard disks and their
partitions are also displayed. The mount point describes where the partition
appears in the Linux file system tree.
Several functional views are available on the left hand . These views can be used to collect information about
existing storage configurations, configure functions (like
RAID, Volume Management,
Crypt Files), and view file systems with additional
features, such as Btrfs, NFS, or TMPFS.
If you run the expert dialog during installation, any free hard disk space is also listed and automatically selected. To provide more disk space to SUSE Linux Enterprise Server, free the needed space by going from the bottom toward the top in the list of partitions.
11.1.1 Partition tables #
SUSE Linux Enterprise Server allows to use and create different partition tables. In some cases the partition table is called disk label. The partition table is important to the boot process of your computer. To boot your machine from a partition in a newly created partition table, make sure that the table format is supported by the firmware.
To change the partition table, click the relevant disk name in the and choose › .
11.1.1.1 Master boot record #
The master boot record (MBR) is the legacy partition table used on IBM PCs. It is sometimes also called an MS-DOS partition table. The MBR only supports four primary partitions. If the disk already has an MBR, SUSE Linux Enterprise Server allows you to create additional partitions in it which can be used as the installation target.
The limit of four partitions can be overcome by creating an extended partition. The extended partition itself is a primary partition and can contain more logical partitions.
UEFI firmware usually supports booting from MBR in the legacy mode.
11.1.1.2 GPT partition table #
UEFI computers use a GUID Partition Table (GPT) by default. SUSE Linux Enterprise Server will create a GPT on a disk if no other partition table exists.
Old BIOS firmware does not support booting from GPT partitions.
You need a GPT partition table to use one of the following features:
More than four primary partitions
UEFI Secure Boot
Use disks larger than 2 TB
GPT partitions created with Parted 3.1 or earlier versions use the
Microsoft Basic Data partition type instead of the newer Linux-specific GPT
GUID. Newer versions of Parted set the misleading flag
msftdata on such partitions. This causes various
disk tools to label the partition as a Windows Data
Partition or similar.
To remove the flag, run:
# parted DEVICE set PARTITION_NUMBER msftdata off11.1.1.3 Partition tables on IBM Z #
On IBM Z platforms, SUSE Linux Enterprise Server supports SCSI hard disks and direct access storage devices (DASD). While SCSI disks can be partitioned as described above, DASDs can have no more than three partition entries in their partition tables.
11.1.2 Partitions #
The YaST Partitioner can create and format partitions with several
file systems. The default file system used by SUSE Linux Enterprise Server is
Btrfs. For details, see
Section 11.1.2.2, “Btrfs partitioning”.
Other commonly used file systems are available:
Ext2, Ext3,
Ext4, FAT,
XFS, Swap, and UDF.
11.1.2.1 Creating a partition #
To create a partition, select and then a hard disk with free space:
Click to create a new partition. When using MBR, specify to create a primary or extended partition. Within the extended partition, you can create several logical partitions. For details, see Section 11.1.1, “Partition tables”.
Specify the size of the new partition. You can either choose to occupy all the free unpartitioned space, or enter a custom size.
Select the file system to use and a mount point. YaST suggests a mount point for each partition created. To use a different mount method, like mount by label, select .
Specify additional file system options if your setup requires them. This is necessary, for example, if you need persistent device names. For details on the available options, refer to Section 11.1.3, “Editing a partition”.
Click to apply your partitioning setup and leave the partitioning module.
If you created the partition during installation, you are returned to the installation overview screen.
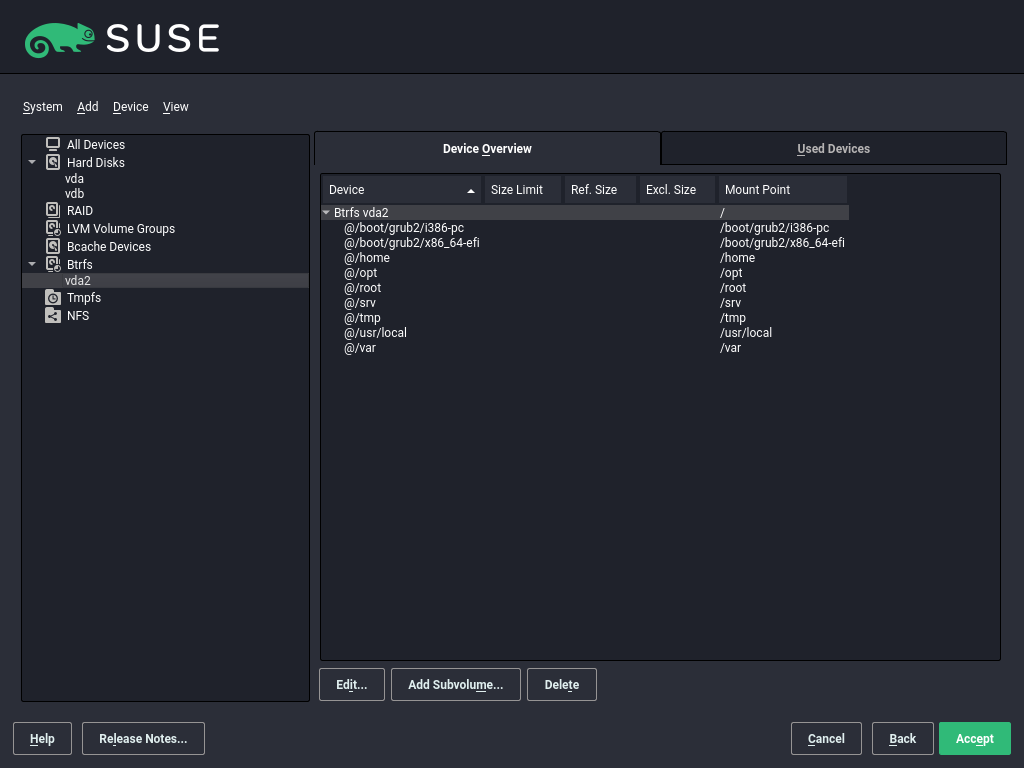
11.1.2.2 Btrfs partitioning #
The default file system for the root partition is Btrfs. For details, see Chapter 10, System recovery and snapshot management with Snapper and Chapter 1, Overview of file systems in Linux. The root file system is the default subvolume and it is not listed in the list of created subvolumes. As a default Btrfs subvolume, it can be mounted as a normal file system.
The default partitioning setup suggests the root partition as
Btrfs with /boot being a directory. To
encrypt the root partition, make sure to use the GPT partition
table type instead of the default MSDOS type. Otherwise the GRUB2
boot loader may not have enough space for the second stage loader.
It is possible to create snapshots of Btrfs subvolumes—either
manually, or automatically based on system events. For example when
making changes to the file system, zypper
invokes the snapper command to create snapshots
before and after the change. This is useful if you are not
satisfied with the change zypper made and want
to restore the previous state. As snapper
invoked by zypper creates snapshots of the
root file system by default, it makes sense to
exclude specific directories from snapshots. This is the reason
YaST suggests creating the following separate subvolumes:
/boot/grub2/i386-pc,/boot/grub2/x86_64-efi,/boot/grub2/powerpc-ieee1275,/boot/grub2/s390x-emuA rollback of the boot loader configuration is not supported. The directories listed above are architecture-specific. The first two directories are present on AMD64/Intel 64 machines, the latter two on IBM POWER and on IBM Z, respectively.
/homeIf
/homedoes not reside on a separate partition, it is excluded to avoid data loss on rollbacks./optThird-party products usually get installed to
/opt. It is excluded to avoid uninstalling these applications on rollbacks./srvContains data for Web and FTP servers. It is excluded to avoid data loss on rollbacks.
/tmpAll directories containing temporary files and caches are excluded from snapshots.
/usr/localThis directory is used when manually installing software. It is excluded to avoid uninstalling these installations on rollbacks.
/varThis directory contains many variable files, including logs, temporary caches, third party products in
/var/opt, and is the default location for virtual machine images and databases. Therefore this subvolume is created to exclude all of this variable data from snapshots and has Copy-On-Write disabled.
Since saved snapshots require more disk space, it is recommended to
reserve enough space for Btrfs. While the minimum size for a root Btrfs
partition with snapshots and default subvolumes is 16 GB, SUSE
recommends at least 32 GB, or more if /home
does not reside on a separate partition.
11.1.2.3 Managing Btrfs subvolumes using YaST #
Subvolumes of a Btrfs partition can be now managed with the YaST module. You can add new or delete existing subvolumes.
Choose in the left side pane.
Select the Btrfs partition whose subvolumes you need to manage.
Depending on whether you want to edit, add, or delete subvolumes, do the following:
To edit a subvolume, select it from the list and click . You can then disable
copy-on-write(check ) for the volume or limit its size. Click to finish.To add a new subvolume, click , and enter its path. Optionally, you can disable
copy-on-write(check ) for the volume or limit its size. Click to finish.To delete a subvolume, select it from the list and click . Confirm the deletion by clicking .
- Figure 11.2: Btrfs subvolumes in YaST partitioner #
Leave the partitioner with .
11.1.3 Editing a partition #
When you create a new partition or modify an existing partition, you can set various parameters. For new partitions, the default parameters set by YaST are usually sufficient and do not require any modification. To edit your partition setup manually, proceed as follows:
Select the partition.
Click to edit the partition and set the parameters:
- File system ID
Even if you do not want to format the partition at this stage, assign it a file system ID to ensure that the partition is registered correctly. Typical values are , , , and .
- File System
To change the partition file system, click and select file system type in the list.
SUSE Linux Enterprise Server supports several types of file systems. Btrfs is the Linux file system of choice for the root partition because of its advanced features. It supports copy-on-write functionality, creating snapshots, multi-device spanning, subvolumes, and other useful techniques. XFS, Ext3, and Ext4 are journaling file systems. These file systems can restore the system very quickly after a system crash, using write processes logged during the operation. Ext2 is not a journaling file system, but it is adequate for smaller partitions because it does not require much disk space for management.
The default file system for the root partition is Btrfs. The default file system for additional partitions is XFS.
The UDF file system can be used on optical rewritable and non-rewritable media, USB flash drives and hard disks. It is supported by multiple operating systems.
Swap is a special format that allows the partition to be used as a virtual memory. Create a swap partition of at least 256 MB. However, if you use up your swap space, consider adding memory to your system instead of adding swap space.
Warning: Changing the file systemChanging the file system and reformatting partitions irreversibly deletes all data from the partition.
For details on the various file systems, refer to Storage Administration Guide.
- Encrypt Device
If you activate the encryption, all data is written to the hard disk in encrypted form. This increases the security of sensitive data, but reduces the system speed, as the encryption takes some time to process. More information about the encryption of file systems is provided in Section 11.2, “Device encryption” and Chapter 12, Encrypting partitions and files.
- Mount Point
Specify the directory where the partition should be mounted in the file system tree. Select from YaST suggestions or enter any other name.
- Fstab Options
Specify various parameters contained in the global file system administration file (
/etc/fstab). The default settings should suffice for most setups. You can, for example, change the file system identification from the device name to a volume label. In the volume label, use all characters except/and space.To get persistent devices names, use the mount option , or . In SUSE Linux Enterprise Server, persistent device names are enabled by default.
Note: IBM Z: Mounting by pathSince mounting by ID causes problems on IBM Z when using disk-to-disk copying for cloning purposes, devices are mounted by path in
/etc/fstabon IBM Z by default.If you prefer to mount the partition by its label, you need to define one in the text entry. For example, you could use the partition label
HOMEfor a partition intended to mount to/home.If you intend to use quotas on the file system, use the mount option . This must be done before you can define quotas for users in the YaST module. For further information on how to configure user quota, refer to Section 6.3.3, “Managing quotas”.
If you intend to specify quotas for Btrfs subvolumes, refer to Section 1.2.5, “Btrfs quota support for subvolumes”.
Select to save the changes.
To resize an existing file system, select the partition and use . Note, that it is not possible to resize partitions while mounted. To resize partitions, unmount the relevant partition before running the partitioner.
11.1.4 Expert options #
After you select a hard disk device (like ) in the pane, you can access the menu in the lower right part of the window. The menu contains the following commands:
- Create new partition table
This option helps you create a new partition table on the selected device.
Warning: Creating a new partition tableCreating a new partition table on a device irreversibly deletes all partitions and their data from that device.
- Clone this disk
This option helps you clone the device partition layout (but not the data) to other available disk devices.
11.1.5 #
tmpfs is a RAM-based virtual memory file system. It offers very fast file access and supports Transparent HugePage Support (THP). The file system is temporary, which means files are not stored on the hard disk but the kernel internal cache. When the file system is unmounted, all data is discarded.
To add a tmpfs file system, click , select the mount point and optionally configure custom mount options.
11.1.6 #
bcache is a Linux kernel block layer cache. It allows one or more fast disk drives (such as
SSDs) to act as a cache for one or more slower hard disks. bcache supports write-through and
write-back, and is independent of the file system used. By default it caches random reads and
writes only, which SSDs excel at. It is suitable for desktops, servers, and high end storage
arrays as well.
To set up bcache, select the (the slow hard drive), the
(typically a SSD) and the .
Then click to apply the changes.
For information about the different cache modes, refer to
Section 4.3, “bcache”.
11.1.7 Advanced options #
After you select the host name of the computer (the top-level of the tree in the pane), you can access the menu in the lower right part of the window. The menu contains the following commands:
- Configure iSCSI
To access SCSI over IP block devices, you first need to configure iSCSI. This results in additionally available devices in the main partition list.
- Configure multipath
Selecting this option helps you configure the multipath enhancement to the supported mass storage devices.
11.1.8 More partitioning tips #
The following section includes a few hints and tips on partitioning that should help you make the right decisions when setting up your system.
11.1.8.1 Cylinder numbers #
Note, that different partitioning tools may start counting the cylinders of
a partition with 0 or with 1. When
calculating the number of cylinders, you should always use the difference
between the last and the first cylinder number and add one.
11.1.8.2 Using swap #
Swap is used to extend the available physical memory. It is then possible to use more memory than physical RAM available. The memory management system of kernels before 2.4.10 needed swap as a safety measure. Then, if you did not have twice the size of your RAM in swap, the performance of the system suffered. These limitations no longer exist.
Linux uses a page called “Least Recently Used” (LRU) to select pages that might be moved from memory to disk. Therefore, running applications have more memory available and caching works more smoothly.
If an application tries to allocate the maximum allowed memory, problems with swap can arise. There are three major scenarios to look at:
- System with no swap
The application gets the maximum allowed memory. All caches are freed, and thus all other running applications are slowed. After a few minutes, the kernel's out-of-memory kill mechanism activates and kills the process.
- System with medium sized swap (128 MB–512 MB)
At first, the system slows like a system without swap. After all physical RAM has been allocated, swap space is used as well. At this point, the system becomes very slow and it becomes impossible to run commands from remote. Depending on the speed of the hard disks that run the swap space, the system stays in this condition for about 10 to 15 minutes until the out-of-memory kill mechanism resolves the issue. Note that you will need a certain amount of swap if the computer needs to perform a “suspend to disk”. In that case, the swap size should be large enough to contain the necessary data from memory (512 MB–1GB).
- System with lots of swap (several GB)
It is better to not have an application that is out of control and swapping excessively in this case. If you use such application, the system will need many hours to recover. In the process, it is likely that other processes get timeouts and faults, leaving the system in an undefined state, even after terminating the faulty process. In this case, do a hard machine reboot and try to get it running again. Lots of swap is only useful if you have an application that relies on this feature. Such applications (like databases or graphics manipulation programs) often have an option to directly use hard disk space for their needs. It is advisable to use this option instead of using lots of swap space.
If your system is not out of control, but needs more swap after some time, it is possible to extend the swap space online. If you prepared a partition for swap space, add this partition with YaST. If you do not have a partition available, you can also use a swap file to extend the swap. Swap files are generally slower than partitions, but compared to physical RAM, both are extremely slow so the actual difference is negligible.
To add a swap file in the running system, proceed as follows:
Create an empty file in your system. For example, to add a swap file with 128 MB swap at
/var/lib/swap/swapfile, use the commands:>sudomkdir -p /var/lib/swap>sudodd if=/dev/zero of=/var/lib/swap/swapfile bs=1M count=128Initialize this swap file with the command
>sudomkswap /var/lib/swap/swapfileNote: Changed UUID for swap partitions when formatting viamkswapDo not reformat existing swap partitions with
mkswapif possible. Reformatting withmkswapwill change the UUID value of the swap partition. Either reformat via YaST (which will update/etc/fstab) or adjust/etc/fstabmanually.Activate the swap with the command
>sudoswapon /var/lib/swap/swapfileTo disable this swap file, use the command
>sudoswapoff /var/lib/swap/swapfileCheck the current available swap spaces with the command
>cat /proc/swapsNote that at this point, it is only temporary swap space. After the next reboot, it is no longer used.
To enable this swap file permanently, add the following line to
/etc/fstab:/var/lib/swap/swapfile swap swap defaults 0 0
11.1.9 Partitioning and LVM #
From the , access the LVM configuration by clicking the item in the pane. However, if a working LVM configuration already exists on your system, it is automatically activated upon entering the initial LVM configuration of a session. In this case, all disks containing a partition (belonging to an activated volume group) cannot be repartitioned. The Linux kernel cannot reread the modified partition table of a hard disk when any partition on this disk is in use. If you already have a working LVM configuration on your system, physical repartitioning should not be necessary. Instead, change the configuration of the logical volumes.
At the beginning of the physical volumes (PVs), information about the volume
is written to the partition. To reuse such a partition for other non-LVM
purposes, it is advisable to delete the beginning of this volume. For
example, in the VG system and PV
/dev/sda2, do this with the command:
ddif=/dev/zero of=/dev/sda2 bs=512 count=1
For more details about LVM, see Storage Administration Guide.
11.2 Device encryption #
Linux Unified Key Setup (LUKS) is the standard for Linux disk encryption. It provides a standardized on-disk format and enables users to transport or migrate data seamlessly.
LUKS is used to encrypt block devices. The contents of the encrypted device are arbitrary, and therefore any file system can be encrypted, including swap partitions. All necessary setup information, like encryption keys and parameters, such as cipher type and key size, is stored in the partition header.
Encryption is done with a multi-layer approach. First, the block device is encrypted using a master key. Then, this master key is encrypted with each active user keys. User keys are derived from passphrases, FIDO2 security keys, TPMs or smart cards. This multi-layer approach allows users to change their passphrase without re-encrypting the whole block device.
For more information about LUKS, refer to Chapter 13, Storage encryption for hosted applications with cryptctl.
11.2.1 Encryption methods #
To encrypt a device, follow the instructions in Section 11.1.3, “Editing a partition”.
LUKS2 encryption is supported by the YaST Partitioner as of SUSE Linux Enterprise 15 SP4, but needs to be enabled explicitly. There are two ways to do this:
At boot time, by adding the parameter to
YAST_LUKS2_AVAILABLEto the kernel command line. For information about boot parameters, refer to Chapter 8, Boot parameters.During installation in the YaST configuration:
In the graphical interface, press Ctrl–Alt–Shift–C.
In the text interface, press Ctrl–D and then Shift–C.
Check and exit the configuration screen with .
If you do not enable LUKS2 support, the selection is not visible and you only need to enter the encryption password.
This method allows to encrypt the device using LUKS1. You have to provide the encryption password. Additional passwords—up to eight in total—can be added later with
cryptsetup luksAddKey.LUKS2 uses a newer version of the header format, which is resilient to corruption, and supports up to 32 user keys and device labels. You have to provide the encryption password and the password-based key derivation function (PBKDF) that will be used to protect that passphrase (see Section 11.2.2, “Password-based key derivation functions”).
- (only on IBM Z)
This method allows to encrypt the device using LUKS2 with a master secure key processed by a Crypto Express cryptographic coprocessor configured in CCA mode. If the cryptographic system already contains a secure key associated to this volume, that key will be used. Otherwise, a new secure key will be generated and registered in the system. You need to provide an encryption password that will be used to protect the access to that master key. Moreover, when there are several APQNs in the system, you can select which ones to use.
For more information about pervasive encryption, refer to https://www.ibm.com/docs/en/linux-on-systems?topic=security-pervasive-encryption.
- (only for swap devices)
This method encrypts a swap device with a randomly generated key at boot and therefore does not support hibernation to hard disk. The swap device is re-encrypted on every boot, and its previous content is destroyed. To avoid data loss, disable hibernation and configure your system to shut down instead.
In addition to the encryption key, the device label and the UUID change every time the swap is re-encrypted, so neither is a valid option to mount a randomly encrypted swap device. Make sure the swap device is referenced by a stable name that is not subject to change on every reboot in the
/etc/crypttabfile. For example, for a swap partition it is safer to use the udev device id or path instead of the partition device name, since that device name may be assigned to a different partition during the next boot. If that happens, a wrong device could be encrypted instead of your swap!YaST tries to use stable names in
/etc/crypttab, unless it is configured to always use device names (see the section of the partitioner). But for some devices, finding a fully stable name may not be possible. Only use encryption with volatile keys if you are sure about the implications.- (only for swap devices)
This method encrypts a swap device with a volatile protected AES key without requiring a cryptographic coprocessor. It is an improvement over the
Encryption with Volatile Random Keymethod and all considerations for that method still apply.- (only for swap devices)
This method encrypts a swap device with a volatile secure AES key generated from a cryptographic coprocessor. It is an improvement over the
Encryption with Volatile Random Keymethod and all considerations for that method still apply.
11.2.2 Password-based key derivation functions #
The password-based key derivation function (PBKDF) to use depends on the context, the hardware capabilities and the needed level of compatibility with other system components:
- PBKDF2
PBKDF2is the function that LUKS1 uses. It is defined in RFC 2898.- Argon2i
Argon2 is a function designed to be more secure and to require a lot of memory to be computed. It is defined in RFC 9106. Argon2i is a variant of Argon2 optimized to resist side-channel attacks by accessing the memory array in a password-independent order.
- Argon2id
Argon2id is a hybrid version of Argon2. It follows the Argon2i approach for the first half pass over memory and the Argon2d (not supported by YaST) approach to limit GPU cracking attacks for subsequent passes. RFC 9106 recommends using Argon2id if you do not know the difference between the types or you consider side-channel attacks to be a viable threat.
While Argon2 is more secure, there are still use cases for
PBKDF2:
As an intentional security feature, Argon2 requires a lot more memory to be computed. This may result in problems on some systems. If the strength of the password can be fully assured, then using PBKDF2 may still be secure and save memory.
grub2offers limited support to boot from devices encrypted with LUKS2, but only if PBKDF2 is used. This means you cannot use Argon2 for a file system that contains the/bootdirectory. Note that even if PBKDF2 is used, some manualgrub2configuration may be needed to boot from a LUKS2 device.
For more information on configuring device encryption with LUKS, use the
Help button in the installer and refer to
Chapter 13, Storage encryption for hosted applications with cryptctl.
11.3 LVM configuration #
This section explains specific steps to take when configuring LVM. If you need information about the Logical Volume Manager in general, refer to the Section 5.1, “Understanding the logical volume manager”.
Using LVM is sometimes associated with increased risk such as data loss. Risks also include application crashes, power failures, and faulty commands. Save your data before implementing LVM or reconfiguring volumes. Never work without a backup.
The YaST LVM configuration can be reached from the YaST Expert Partitioner (see Section 11.1, “Using the ”) within the item in the pane. The allows you to manage hard disks and partitions, as well as setting up RAID and LVM configurations.
11.3.1 Create physical volume #
The first task is to create physical volumes that provide space to a volume group:
Select a hard disk from .
Change to the tab.
Click and enter the desired size of the PV on this disk.
Use and change the to . Do not mount this partition.
Repeat this procedure until you have defined all the desired physical volumes on the available disks.
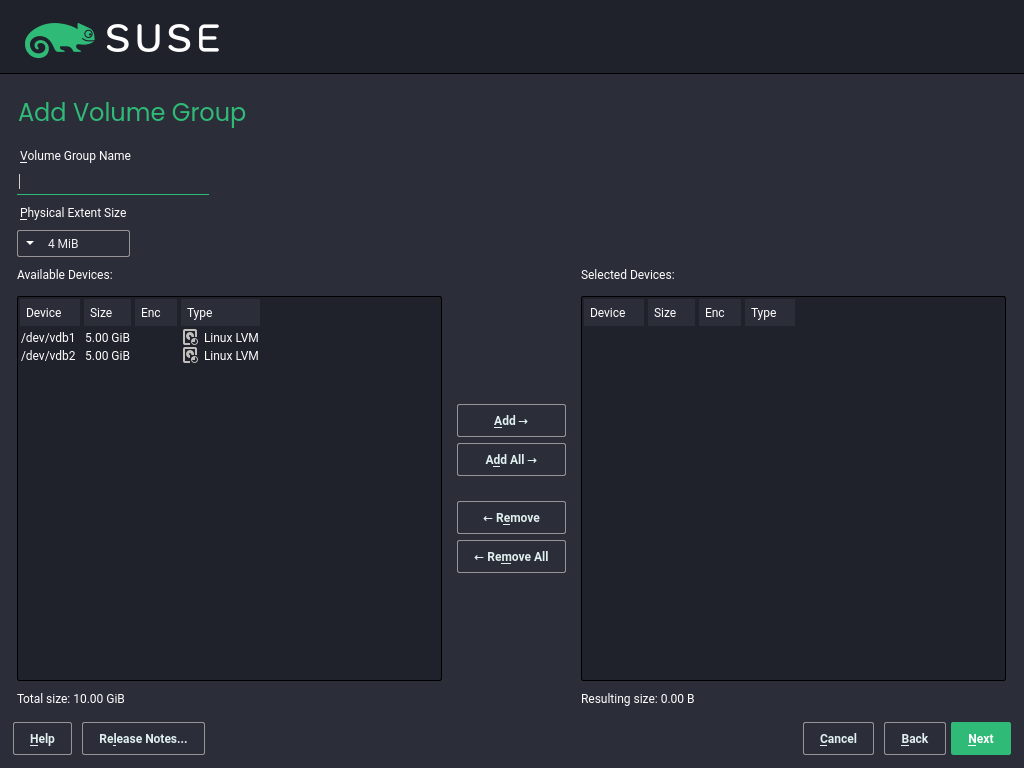
11.3.2 Creating volume groups #
If no volume group exists on your system, you must add one (see Figure 11.3, “Creating a volume group”). It is possible to create additional groups by clicking in the pane, and then on . One single volume group is usually sufficient.
Enter a name for the VG, for example,
system.Select the desired . This value defines the size of a physical block in the volume group. All the disk space in a volume group is handled in blocks of this size.
Add the prepared PVs to the VG by selecting the device and clicking . Selecting several devices is possible by holding Ctrl while selecting the devices.
Select to make the VG available to further configuration steps.
If you have multiple volume groups defined and want to add or remove PVs, select the volume group in the list and click . In the following window, you can add PVs to or remove them from the selected volume group.
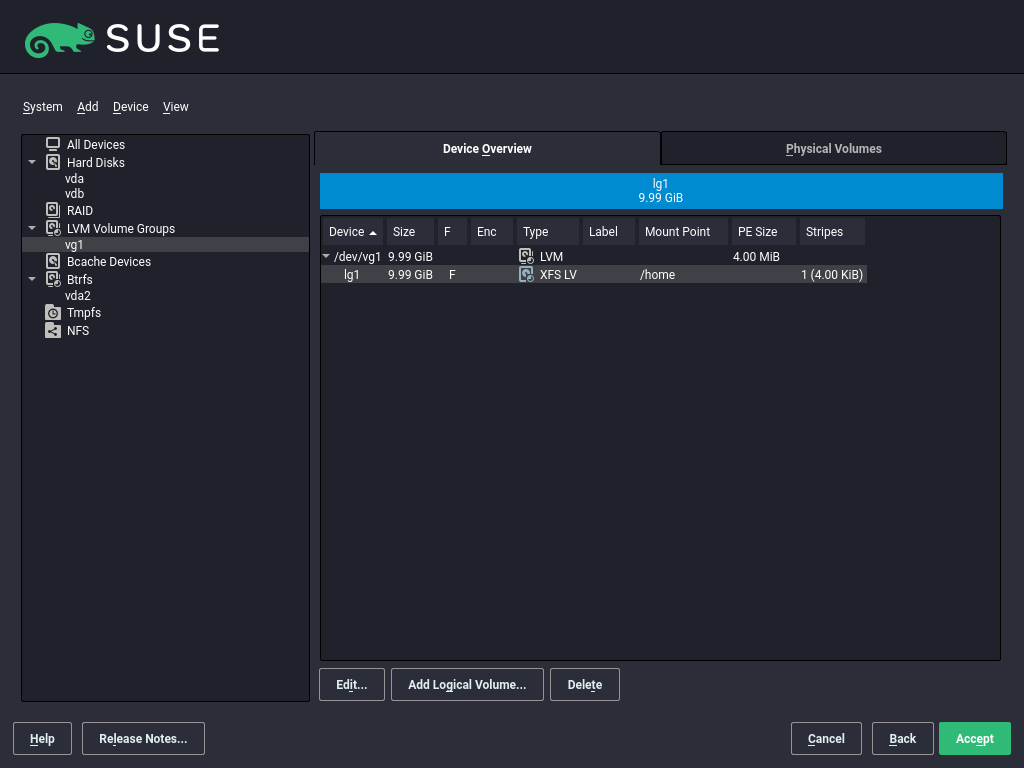
11.3.3 Configuring logical volumes #
After the volume group has been filled with PVs, define the LVs which the operating system should use in the next dialog. Choose the current volume group and change to the tab. , , , and LVs as needed until all space in the volume group has been occupied. Assign at least one LV to each volume group.
Click and go through the wizard-like pop-up that opens:
Enter the name of the LV. For a partition that should be mounted to
/home, a name likeHOMEcould be used.Select the type of the LV. It can be either , , or . Note that you need to create a thin pool first, which can store individual thin volumes. The big advantage of thin provisioning is that the total sum of all thin volumes stored in a thin pool can exceed the size of the pool itself.
Select the size and the number of stripes of the LV. If you have only one PV, selecting more than one stripe is not useful.
Choose the file system to use on the LV and the mount point.
By using stripes it is possible to distribute the data stream in the LV among several PVs (striping). However, striping a volume can only be done over different PVs, each providing at least the amount of space of the volume. The maximum number of stripes equals to the number of PVs, where Stripe "1" means "no striping". Striping only makes sense with PVs on different hard disks, otherwise performance will decrease.
YaST cannot verify your entries concerning striping at this point. Mistakes made here will show later when the LVM is implemented on disk.
If you have already configured LVM on your system, the existing logical volumes can also be used. Before continuing, assign appropriate mount points to these LVs. With , return to the YaST and finish your work there.
11.4 Soft RAID #
This section describes actions required to create and configure various types of RAID. In case you need background information about RAID, refer to Section 7.1, “Understanding RAID levels”.
11.4.1 Soft RAID configuration #
The YaST configuration can be reached from the YaST , described in Section 11.1, “Using the ”. This partitioning tool enables you to edit and delete existing partitions and create new ones to be used with soft RAID:
Select a hard disk from .
Change to the tab.
Click and enter the desired size of the raid partition on this disk.
Use and change the to . Do not mount this partition.
Repeat this procedure until you have defined all the desired physical volumes on the available disks.
For RAID 0 and RAID 1, at least two partitions are needed—for RAID 1, usually exactly two and no more. If RAID 5 is used, at least three partitions are required, RAID 6 and RAID 10 require at least four partitions. It is recommended to use partitions of the same size only. The RAID partitions should be located on different hard disks to decrease the risk of losing data if one is defective (RAID 1 and 5) and to optimize the performance of RAID 0. After creating all the partitions to use with RAID, click › to start the RAID configuration.
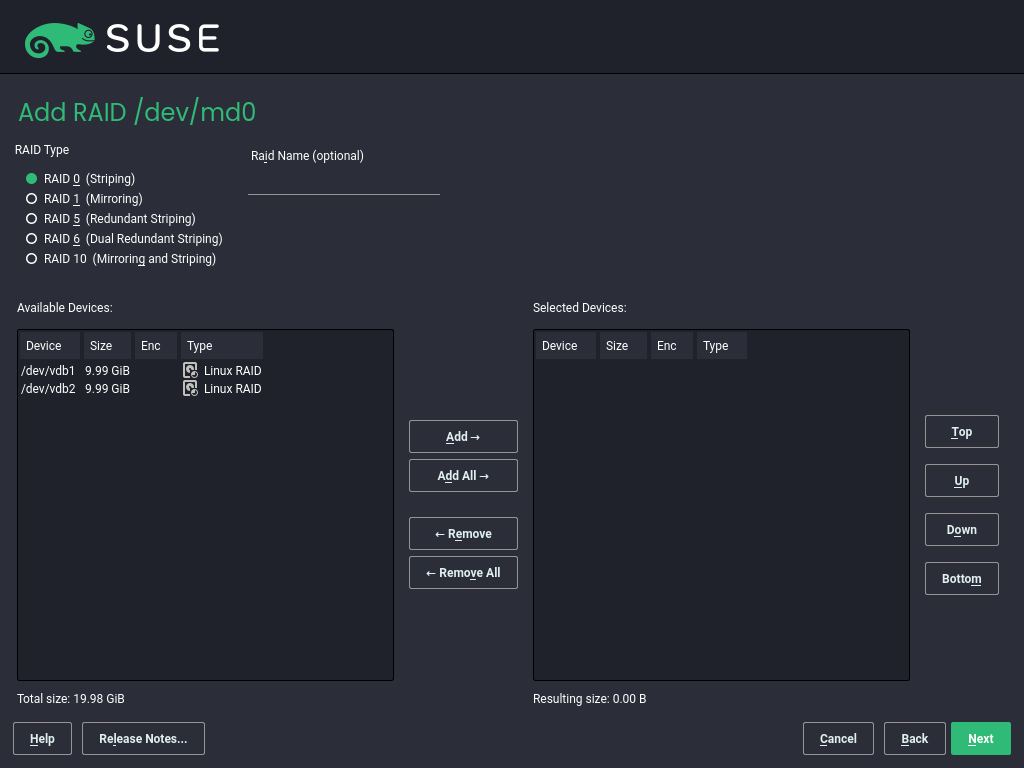
In the next dialog, choose between RAID levels 0, 1, 5, 6 and 10. Then, select all partitions with either the “Linux RAID” or “Linux native” type that should be used by the RAID system. No swap or DOS partitions are shown.
To add a previously unassigned partition to the selected RAID volume, first click the partition then . Assign all partitions reserved for RAID. Otherwise, the space on the partition remains unused. After assigning all partitions, click to select the available .
In this last step, set the file system to use, encryption and the mount
point for the RAID volume. After completing the configuration with
, see the /dev/md0 device and
others indicated with RAID in the .
11.4.2 Troubleshooting #
Check the file /proc/mdstat to find out whether a RAID
partition is damaged. If the system fails, shut down the machine and replace
the defective hard disk with a new one partitioned the same way. Then
restart your system and run mdadm
/dev/mdX --add
/dev/sdX. Replace 'X' with your
particular device identifiers. This integrates the hard disk automatically
into the RAID system and fully reconstructs it.
Note that although you can access all data during the rebuild, you may encounter some performance issues until the RAID has been fully rebuilt.
11.4.3 More information #
Configuration instructions and more details for soft RAID can be found at:
Linux RAID mailing lists are available, such as https://marc.info/?l=linux-raid.