39 The domain name system #
DNS (domain name system) is needed to resolve the domain names and host
names into IP addresses. In this way, the IP address 192.168.2.100 is assigned to
the host name jupiter, for example. Before setting up your
own name server, read the general information about DNS in
Section 23.3, “Name resolution”. The following configuration
examples refer to BIND, the default DNS server.
39.1 DNS terminology #
- Zone
The domain name space is divided into regions called zones. For example, if you have
example.com, you have theexamplesection (or zone) of thecomdomain.- DNS server
The DNS server is a server that maintains the name and IP information for a domain. You can have a primary DNS server for primary zone, a secondary server for secondary zone, or a secondary server without any zones for caching.
- Primary zone DNS server
The primary zone includes all hosts from your network and a DNS server primary zone stores up-to-date records for all the hosts in your domain.
- Secondary zone DNS server
A secondary zone is a copy of the primary zone. The secondary zone DNS server obtains its zone data with zone transfer operations from its primary server. The secondary zone DNS server responds authoritatively for the zone if it has valid (not expired) zone data. If the secondary server cannot obtain a new copy of the zone data, it stops responding for the zone.
- Forwarder
Forwarders are DNS servers to which your DNS server should send queries it cannot answer. To enable different configuration sources in one configuration,
netconfigis used (see alsoman 8 netconfig).- Record
The record is information about name and IP address. Supported records and their syntax are described in BIND documentation. Some special records are:
- NS record
An NS record tells name servers which machines are in charge of a given domain zone.
- MX record
The MX (mail exchange) records describe the machines to contact for directing mail across the Internet.
- SOA record
SOA (Start of Authority) record is the first record in a zone file. The SOA record is used when using DNS to synchronize data between multiple computers.
39.2 Installation #
To install a DNS server, start YaST and select › . Choose › and select . Confirm the installation of the dependent packages to finish the installation process.
Alternatively use the following command on the command line:
>sudozypper in -t pattern dhcp_dns_server
39.3 Configuration with YaST #
Use the YaST DNS module to configure a DNS server for the local network. When starting the module for the first time, a wizard starts, prompting you to make a few decisions concerning administration of the server. Completing this initial setup produces a basic server configuration. Use the expert mode to deal with more advanced configuration tasks, such as setting up ACLs, logging, TSIG keys, and other options.
39.3.1 Wizard configuration #
The wizard consists of three steps or dialogs. At the appropriate places in the dialogs, you can enter the expert configuration mode.
When starting the module for the first time, the dialog, shown in Figure 39.1, “DNS server installation: forwarder settings”, opens. The allows to set the following options:
—If is selected, can be specified; by default (with selected), is set to
auto, but here you can either set interface names or select from the two special policy namesSTATICandSTATIC_FALLBACK.
In , specify which service to use: , , or .
For more information about all these settings, see
man 8 netconfig.Figure 39.1: DNS server installation: forwarder settings #Forwarders are DNS servers to which your DNS server sends queries it cannot answer itself. Enter their IP address and click .
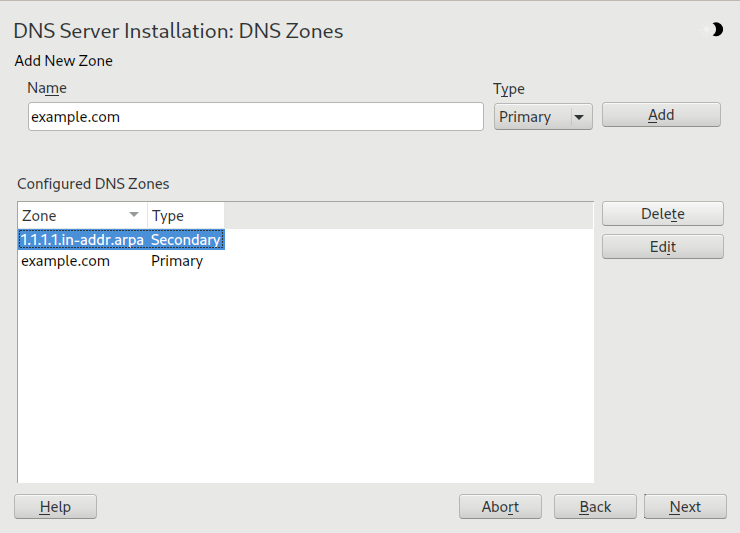
The dialog consists of several parts and is responsible for the management of zone files, described in Section 39.6, “Zone files”. For a new zone, provide a name for it in . To add a reverse zone, the name must end in
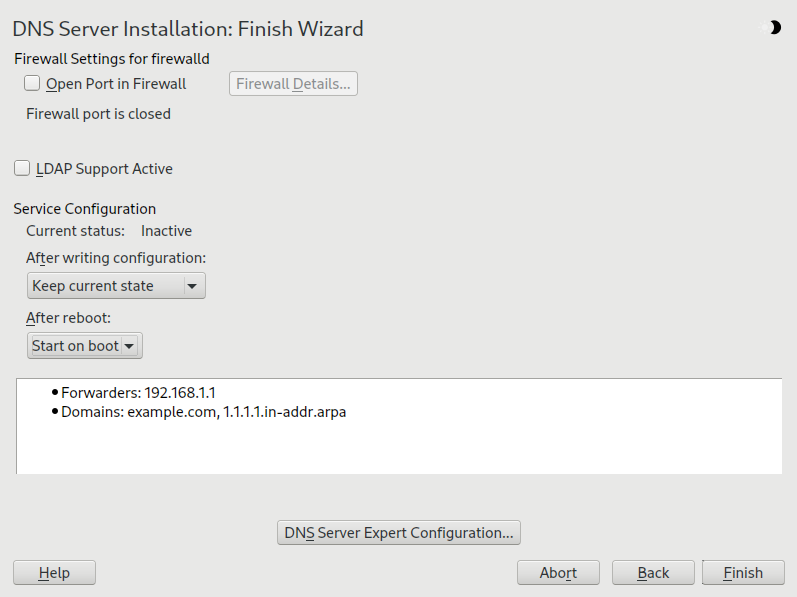
.in-addr.arpa. Finally, select the (primary, secondary, or forward). See Figure 39.2, “DNS server installation: DNS zones”. Click to configure other settings of an existing zone. To remove a zone, click .Figure 39.2: DNS server installation: DNS zones #In the final dialog, you can open the DNS port in the firewall by clicking . Then decide whether to start the DNS server when booting ( or ). You can also activate LDAP support. See Figure 39.3, “DNS server installation: finish wizard”.
Figure 39.3: DNS server installation: finish wizard #
39.3.2 Expert configuration #
After starting the module, YaST opens a window displaying several configuration options. Completing it results in a DNS server configuration with the basic functions in place:
39.3.2.1 Start-up #
Under , define whether the DNS server should be started when the booting the system or manually. To start the DNS server immediately, click . To stop the DNS server, click . To save the current settings, select . You can open the DNS port in the firewall with and modify the firewall settings with .
By selecting , the zone files are managed by an LDAP database. Any changes to zone data written to the LDAP database are picked up by the DNS server when it is restarted or prompted to reload its configuration.
39.3.2.2 Forwarders #
If your local DNS server cannot answer a request, it tries to forward the
request to a , if configured so. This
forwarder may be added manually to the .
If the forwarder is not static like in dial-up connections,
handles the configuration. For more
information about netconfig, see man 8 netconfig.
39.3.2.3 Basic options #
In this section, set basic server options. From the menu, select the desired item then specify the value in the corresponding text box. Include the new entry by selecting .
39.3.2.4 Logging #
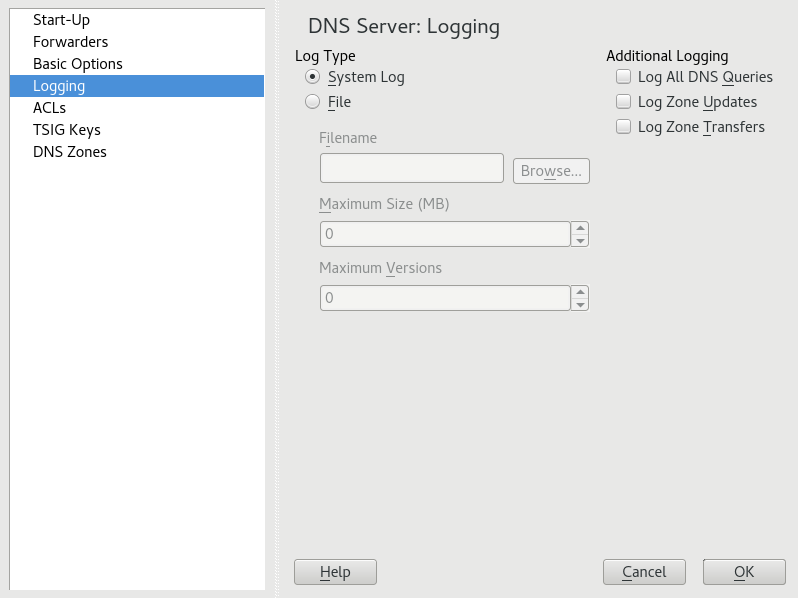
To set what the DNS server should log and how, select . Under , specify where the DNS server should write the log data. Use the system-wide log by selecting or specify a different file by selecting . In the latter case, additionally specify a name, the maximum file size in megabytes and the number of log file versions to store.
Further options are available under . Enabling causes every query to be logged, in which case the log file could grow extremely large. For this reason, it is not a good idea to enable this option for other than debugging purposes. To log the data traffic during zone updates between DHCP and DNS server, enable . To log the data traffic during a zone transfer from primary to secondary server, enable . See Figure 39.4, “DNS server: logging”.
39.3.2.5 ACLs #
Use this dialog to define ACLs (access control lists) to enforce access restrictions. After providing a distinct name under , specify an IP address (with or without netmask) under in the following fashion:
{ 192.168.1/24; }The syntax of the configuration file requires that the address ends with a semicolon and is put into curly braces.
39.3.2.6 TSIG keys #
The main purpose of TSIGs (transaction signatures) is to secure communications between DHCP and DNS servers. They are described in Section 39.8, “Secure transactions”.
To generate a TSIG key, enter a distinctive name in the field labeled and specify the file where the key should be stored (). Confirm your choices with .
To use a previously created key, leave the field blank and select the file where it is stored under . After that, confirm with .
39.3.2.7 DNS zones (adding a secondary zone) #
To add a secondary zone, select , choose the zone type , write the name of the new zone, and click .
In the sub-dialog under , specify the primary server from which the secondary server should pull its data. To limit access to the server, select one of the ACLs from the list.
39.3.2.8 DNS zones (adding a primary zone) #
To add a primary zone, select , choose the zone
type , write the name of the new zone, and click
. When adding a primary zone, a reverse zone is also
needed. For example, when adding the zone
example.com that points to hosts in a subnet
192.168.1.0/24, you should also add a reverse zone for
the IP-address range covered. By definition, this should be named
1.168.192.in-addr.arpa.
39.3.2.9 DNS zones (editing a primary zone) #
To edit a primary zone, select , select the primary zone from the table and click . The dialog consists of several pages: (the one opened first), , , , and .
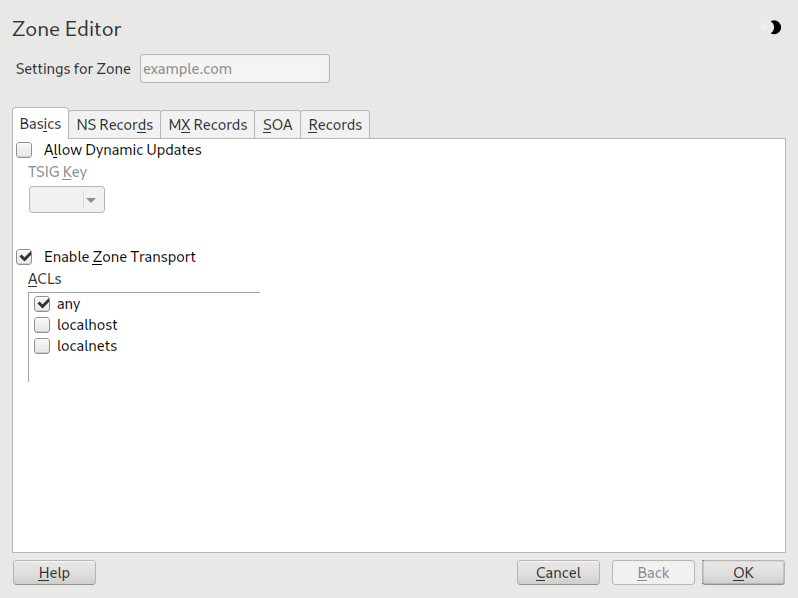
The basic dialog, shown in Figure 39.5, “DNS server: Zone Editor (Basics)”, lets you define settings for dynamic DNS and access options for zone transfers to clients and secondary name servers. To permit the dynamic updating of zones, select and the corresponding TSIG key. The key must have been defined before the update action starts. To enable zone transfers, select the corresponding ACLs. ACLs must have been defined already.
In the dialog, select whether to enable zone transfers. Use the listed ACLs to define who can download zones.
- Zone Editor (NS Records)
The dialog allows you to define alternative name servers for the zones specified. Make sure that your own name server is included in the list. To add a record, enter its name under then confirm with . See Figure 39.6, “DNS server: Zone Editor (NS Records)”.
Figure 39.6: DNS server: Zone Editor (NS Records) #- Zone Editor (MX Records)
To add a mail server for the current zone to the existing list, enter the corresponding address and priority value. After doing so, confirm by selecting . See Figure 39.7, “DNS server: Zone Editor (MX Records)”.
Figure 39.7: DNS server: Zone Editor (MX Records) #- Zone Editor (SOA)
This page allows you to create SOA (start of authority) records. For an explanation of the individual options, refer to Example 39.6, “The /var/lib/named/example.com.zone file”. Changing SOA records is not supported for dynamic zones managed via LDAP.
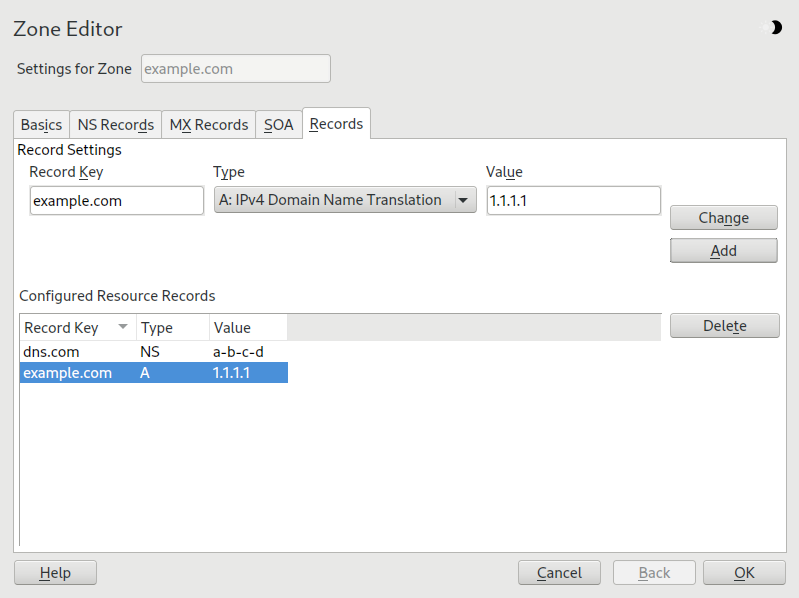
Figure 39.8: DNS server: Zone Editor (SOA) #- Zone Editor (Records)
This dialog manages name resolution. In , enter the host name then select its type. The type represents the main entry. The value for this should be an IP address (IPv4). Use for IPv6 addresses. is an alias. Use the types and for detailed or partial records that expand on the information provided in the and tabs. These three types resolve to an existing
Arecord. is for reverse zones. It is the opposite of anArecord, for example:hostname.example.com. IN A 192.168.0.1 1.0.168.192.in-addr.arpa IN PTR hostname.example.com.
39.3.2.9.1 Adding reverse zones #
To add a reverse zone, follow this procedure:
Start › › .
If you have not added a primary forward zone, add it and it.
In the tab, fill the corresponding and , then add the record with and confirm with . If YaST complains about a non-existing record for a name server, add it in the tab.
Figure 39.9: Adding a record for a primary zone #Back in the window, add a reverse primary zone.
Figure 39.10: Adding a reverse zone #the reverse zone, and in the tab, you can see the record type. Add the corresponding and , then click and confirm with .
Figure 39.11: Adding a reverse record #Add a name server record if needed.
After adding a forward zone, go back to the main menu and select the reverse zone for editing. There in the tab activate the check box and select your forward zone. That way, all changes to the forward zone are automatically updated in the reverse zone.
39.4 Starting the BIND name server #
On a SUSE® Linux Enterprise Server system, the name server BIND (Berkeley
Internet Name Domain) comes preconfigured, so it can be started
right after installation without any problems. Normally, if you already have an Internet connection and entered
127.0.0.1 as the name server
address for localhost in
/var/run/netconfig/resolv.conf, you already have a working
name resolution without needing to know the DNS of the provider. BIND
carries out name resolution via the root name server, a notably slower
process. Normally, the DNS of the provider should be entered with its IP
address in the configuration file /etc/named.conf under
forwarders to ensure effective and secure name
resolution. If this works so far, the name server runs as a pure
caching-only name server. Only when you configure its
own zones it becomes a proper DNS. Find a simple example documented in
/usr/share/doc/packages/bind/config.
Depending on the type of Internet connection or the network connection, the
name server information can automatically be adapted to the current
conditions. To do this, set the
NETCONFIG_DNS_POLICY variable in the
/etc/sysconfig/network/config file to
auto.
However, do not set up an official domain until one is assigned to you by the responsible institution. Even if you have your own domain and it is managed by the provider, you are better off not using it, because BIND would otherwise not forward requests for this domain. The Web server at the provider, for example, would not be accessible for this domain.
To start the name server, enter the command systemctl start
named as root. Check
with systemctl status named whether named (as the name
server process is called) has been started successfully. Test the name
server immediately on the local system with the host or
dig programs, which should return
localhost as the default server
with the address 127.0.0.1. If
this is not the case, /var/run/netconfig/resolv.conf probably
contains an incorrect name server entry or the file does not exist. For the
first test, enter host 127.0.0.1,
which should always work. If you get an error message, use
systemctl status named to see whether the server is
actually running. If the name server does not start or behaves unexpectedly,
check the output of journalctl -e.
To use the name server of the provider (or one already running on your
network) as the forwarder, enter the corresponding IP address or addresses
in the options section under
forwarders. The addresses included in
Example 39.1, “Forwarding options in named.conf” are examples only. Adjust these entries to your
own setup.
options {
directory "/var/lib/named";
forwarders { 10.11.12.13; 10.11.12.14; };
listen-on { 127.0.0.1; 192.168.1.116; };
allow-query { 127/8; 192.168/16 };
notify no;
};
The options entry is followed by entries for the
zone, localhost, and
0.0.127.in-addr.arpa. The type
hint entry under “.” should always be present. The
corresponding files do not need to be modified and should work as they are.
Also make sure that each entry is closed with a “;” and that
the curly braces are in the correct places. After changing the configuration
file /etc/named.conf or the zone files, tell BIND to
reread them with systemctl reload named. Achieve the same
by stopping and restarting the name server with systemctl restart
named. Stop the server at any time by entering systemctl
stop named.
39.5 The /etc/named.conf configuration file #
All the settings for the BIND name server itself are stored in the
/etc/named.conf file. However, the zone data for the
domains to handle (consisting of the host names, IP addresses, and so on)
are stored in separate files in the /var/lib/named
directory. The details of this are described later.
/etc/named.conf is roughly divided into two areas. One
is the options section for general settings and the
other consists of zone entries for the individual
domains. A logging section and
acl (access control list) entries are optional.
Comment lines begin with a # sign or
//. A minimal /etc/named.conf is
shown in Example 39.2, “A basic /etc/named.conf”.
options {
directory "/var/lib/named";
forwarders { 10.0.0.1; };
notify no;
};
zone "localhost" in {
type master;
file "localhost.zone";
};
zone "0.0.127.in-addr.arpa" in {
type master;
file "127.0.0.zone";
};
zone "." in {
type hint;
file "root.hint";
};39.5.1 Important configuration options #
- directory "FILENAME";
Specifies the directory in which BIND can find the files containing the zone data. Usually, this is
/var/lib/named.- forwarders { IP-ADDRESS; };
Specifies the name servers (mostly of the provider) to which DNS requests should be forwarded if they cannot be resolved directly. Replace IP-ADDRESS with an IP address like
192.168.1.116.- forward first;
Causes DNS requests to be forwarded before an attempt is made to resolve them via the root name servers. Instead of
forward first,forward onlycan be written to have all requests forwarded and none sent to the root name servers. This makes sense for firewall configurations.- listen-on port 53 { 127.0.0.1; IP-ADDRESS; };
Tells BIND on which network interfaces and port to accept client queries.
port 53does not need to be specified explicitly, because53is the default port. Enter127.0.0.1to permit requests from the local host. If you omit this entry entirely, all interfaces are used by default.- listen-on-v6 port 53 {any; };
Tells BIND on which port it should listen for IPv6 client requests. The only alternative to
anyisnone. As far as IPv6 is concerned, the server only accepts wild card addresses.- query-source address * port 53;
This entry is necessary if a firewall is blocking outgoing DNS requests. This tells BIND to post requests externally from port 53 and not from any of the high ports above 1024.
- query-source-v6 address * port 53;
Tells BIND which port to use for IPv6 queries.
- allow-query { 127.0.0.1; NET; };
Defines the networks from which clients can post DNS requests. Replace NET with address information like
192.168.2.0/24. The/24at the end is an abbreviated expression for the netmask (in this case255.255.255.0).- allow-transfer ! *;;
Controls which hosts can request zone transfers. In the example, such requests are completely denied with
! *. Without this entry, zone transfers can be requested from anywhere without restrictions.- statistics-interval 0;
In the absence of this entry, BIND generates several lines of statistical information per hour in the system's journal. Set it to 0 to suppress these statistics completely or set an interval in minutes.
- cleaning-interval 720;
This option defines at which time intervals BIND clears its cache. This triggers an entry in the system's journal each time it occurs. The time specification is in minutes. The default is 60 minutes.
- interface-interval 0;
BIND regularly searches the network interfaces for new or nonexistent interfaces. If this value is set to
0, this is not done and BIND only listens at the interfaces detected at start-up. Otherwise, the interval can be defined in minutes. The default is sixty minutes.- notify no;
noprevents other name servers from being informed when changes are made to the zone data or when the name server is restarted.
For a list of available options, read the manual page man 5
named.conf.
39.5.2 Logging #
What, how, and where logging takes place can be extensively configured in BIND. Normally, the default settings should be sufficient. Example 39.3, “Entry to disable logging”, shows the simplest form of such an entry and completely suppresses any logging.
logging {
category default { null; };
};39.5.3 Zone entries #
zone "example.com" in {
type master;
file "example.com.zone";
notify no;
};
After zone, specify the name of the domain to
administer (example.com)
followed by in and a block of relevant options
enclosed in curly braces, as shown in Example 39.4, “Zone entry for example.com”. To
define a secondary zone, switch the
type to secondary and specify a
name server that administers this zone as primary (which,
in turn, may be a secondary server of another primary server), as shown in
Example 39.5, “Zone entry for example.net”.
zone "example.net" in {
type secondary;
file "secondary/example.net.zone";
masters { 10.0.0.1; };
};The zone options:
- type primary;
By specifying
primary, tell BIND that the zone is handled by the local name server. This assumes that a zone file has been created in the correct format.- type secondary;
This zone is transferred from another name server. It must be used together with
primary_servers.- type hint;
The zone
.of thehinttype is used to set the root name servers. This zone definition can be left as is.- file
example.com.zoneor file “secondary/example.net.zone”; This entry specifies the file where zone data for the domain is located. This file is not required for a secondary server, because this data is pulled from another name server. To differentiate files of the primary and secondary server, use the directory
secondaryfor the secondary files.- primary_servers { SERVER_IP_ADDRESS; };
This entry is only needed for secondary zones. It specifies from which name server the zone file should be transferred.
- allow-update {! *; };
This option controls external write access, which would allow clients to make a DNS entry—something not normally desirable for security reasons. Without this entry, zone updates are not allowed. The above entry achieves the same because
! *effectively bans any such activity.
39.6 Zone files #
Two types of zone files are needed. One assigns IP addresses to host names and the other does the reverse: it supplies a host name for an IP address.
The "." has an important meaning in the zone files. If
host names are given without a final dot (.), the zone
is appended. Complete host names specified with a full domain name must end
with a dot (.) to avoid having the domain added to it
again. A missing or wrongly placed "." is probably the most frequent cause
of name server configuration errors.
The first case to consider is the zone file
example.com.zone, responsible for the domain
example.com, shown in
Example 39.6, “The /var/lib/named/example.com.zone file”.
$TTL 2D 1 example.com. IN SOA dns root.example.com. ( 2 2003072441 ; serial 3 1D ; refresh 4 2H ; retry 5 1W ; expiry 6 2D ) ; minimum 7 IN NS dns 8 IN MX 10 mail dns 9 gate IN A 192.168.5.1 10 IN A 10.0.0.1 dns IN A 192.168.1.116 mail IN A 192.168.3.108 jupiter IN A 192.168.2.100 venus IN A 192.168.2.101 saturn IN A 192.168.2.102 mercury IN A 192.168.2.103 ntp IN CNAME dns 11 dns6 IN A6 0 2002:c0a8:174::
| |
This is where the SOA (start of authority) control record begins:
| |
The | |
The | |
The | |
The | |
The last entry in the SOA record specifies the | |
The | |
The MX record specifies the mail server that accepts, processes, and
forwards e-mails for the domain | |
This and the following lines are the actual address records where one or more IP addresses are
assigned to host names. The names are listed here without a
Note: IPv6 syntax The IPv6 record has a slightly different syntax than IPv4. Because of the fragmentation possibility, it is necessary to provide information about missed bits before the address. To fill up the IPv6 address with the needed number of “0”, add two colons at the correct place in the address. pluto AAAA 2345:00C1:CA11::1234:5678:9ABC:DEF0 pluto AAAA 2345:00D2:DA11::1234:5678:9ABC:DEF0 | |
The alias |
The pseudo domain in-addr.arpa is used for the reverse
lookup of IP addresses into host names. It is appended to the network part
of the address in reverse notation. So
192.168 is resolved into
168.192.in-addr.arpa. See
Example 39.7, “Reverse lookup”.
$TTL 2D 1 168.192.in-addr.arpa. IN SOA dns.example.com. root.example.com. ( 2 2003072441 ; serial 1D ; refresh 2H ; retry 1W ; expiry 2D ) ; minimum IN NS dns.example.com. 3 1.5 IN PTR gate.example.com. 4 100.3 IN PTR www.example.com. 253.2 IN PTR cups.example.com.
$TTL defines the standard TTL that applies to all entries here. | |
The configuration file should activate reverse lookup for the network
See Example 39.6, “The /var/lib/named/example.com.zone file” for detail on the entries within this record. | |
This line specifies the name server responsible for this zone. This time,
however, the name is entered in its complete form with the domain and a
| |
This, and the following lines, are the pointer records hinting at the IP
addresses on the respective hosts. Only the last part of the IP address is
entered at the beginning of the line, without the |
Normally, zone transfers between different versions of BIND should be possible without any problems.
39.7 Dynamic update of zone data #
The term dynamic update refers to operations by which
entries in the zone files of a primary server are added, changed, or deleted.
This mechanism is described in RFC 2136. Dynamic update is configured
individually for each zone entry by adding an optional
allow-update or
update-policy rule. Zones to update dynamically
should not be edited by hand.
Transmit the entries to update to the server with the command
nsupdate. For the exact syntax of this command, check the
manual page for nsupdate (man 8
nsupdate). For security reasons, any such update should be
performed using TSIG keys as described in Section 39.8, “Secure transactions”.
39.8 Secure transactions #
Secure transactions can be made with transaction signatures (TSIGs) based on shared secret keys (also called TSIG keys). This section describes how to generate and use such keys.
Secure transactions are needed for communication between different servers and for the dynamic update of zone data. Making the access control dependent on keys is much more secure than merely relying on IP addresses.
Generate a TSIG key with the following command (for details, see
man tsig-keygen):
>sudotsig-keygen -a hmac-md5 host1-host2 > host1-host2.key
This creates a file with the name host1-host2.key with
contents that may look as follows:
key "host1-host2" { |
algorithm hmac-md5;
secret "oHpBLgtcZso6wxnRTWdJMA==";
};
The file must be transferred to the remote host, preferably in a secure way
(using scp, for example). To enable a secure communication between
host1 and host2, the key must be
included in the /etc/named.conf file on both the local
and the remote
server.
key host1-host2 {
algorithm hmac-md5;
secret "ejIkuCyyGJwwuN3xAteKgg==";
};/etc/named.conf
Make sure that the permissions of /etc/named.conf are
properly restricted. The default for this file is 0640,
with the owner being root and the
group named. As an alternative,
move the keys to an extra file with specially limited permissions, which is
then included from /etc/named.conf. To include an
external file, use:
include "filename"
Replace filename with an absolute path to your file with
keys.
To enable the server host1 to use the key for
host2 (which has the address 10.1.2.3
in this example), the server's /etc/named.conf must
include the following rule:
server 10.1.2.3 {
keys { host1-host2. ;};
};
Analogous entries must be included in the configuration files of
host2.
Add TSIG keys for any ACLs (access control lists, not to be confused with file system ACLs) that are defined for IP addresses and address ranges to enable transaction security. The corresponding entry could look like this:
allow-update { key host1-host2. ;};
This topic is discussed in more detail in the BIND Administrator
Reference Manual under update-policy.
39.9 DNS security #
DNSSEC, or DNS security, is described in RFC 2535. The tools available for DNSSEC are discussed in the BIND Manual.
A zone considered secure must have one or several zone keys associated with
it. These are generated with dnssec-keygen, as are the
host keys. The DSA encryption algorithm is currently used to generate these
keys. The public keys generated should be included in the corresponding zone
file with an $INCLUDE rule.
With the command dnssec-signzone, you can create sets of
generated keys (keyset- files), transfer them to the
parent zone in a secure manner, and sign them. This generates the files to
include for each zone in /etc/named.conf.
39.10 More information #
For more information, see the BIND Administrator Reference
Manual from the
bind-doc package, which is
installed under /usr/share/doc/packages/bind/arm.
Consider additionally consulting the RFCs referenced by the manual and the
manual pages included with BIND.
/usr/share/doc/packages/bind/README.SUSE contains
up-to-date information about BIND in SUSE Linux Enterprise Server.