SAML (Azure AD)
Integrate with Azure AD SAML authentication
-
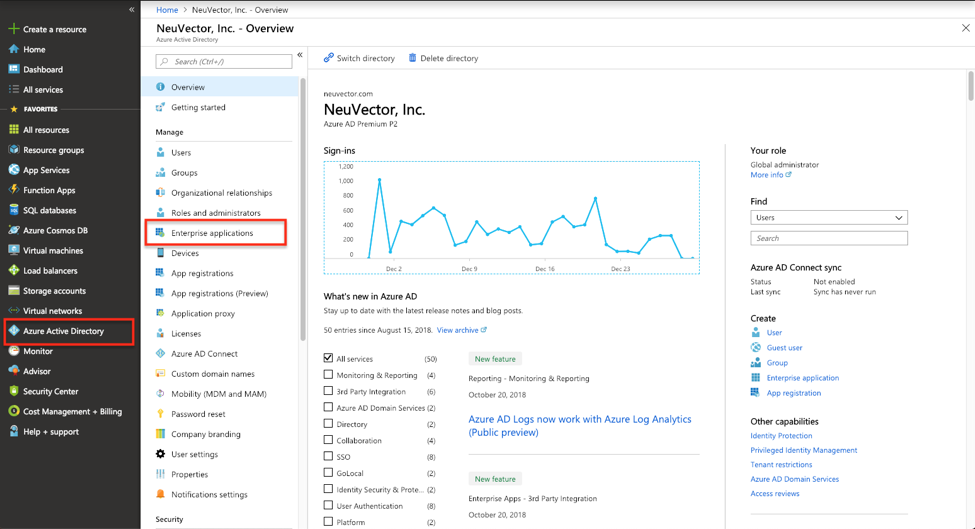
In the Azure management console, select the `"Enterprise applications" menu item in Azure Active Directory
-
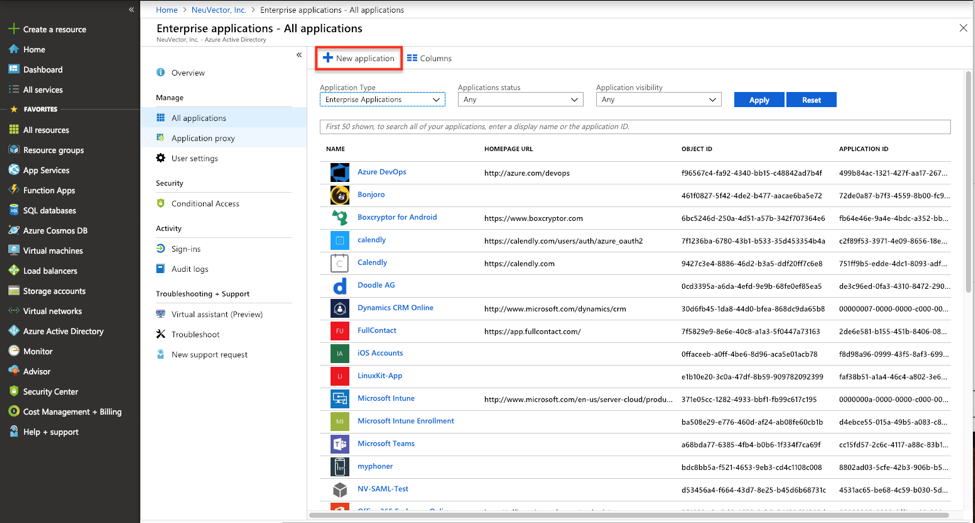
Select “New Application”
-
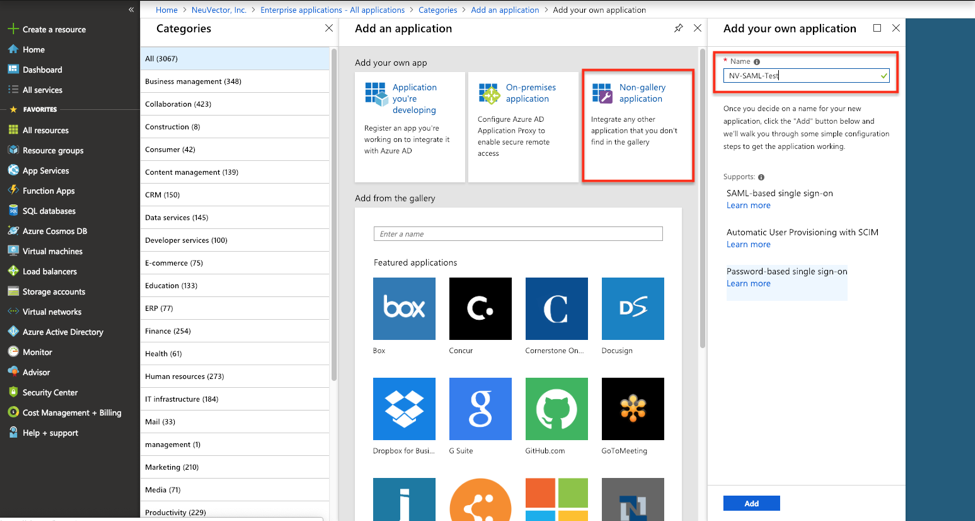
Create a Non-gallery application and give it a unique name
-
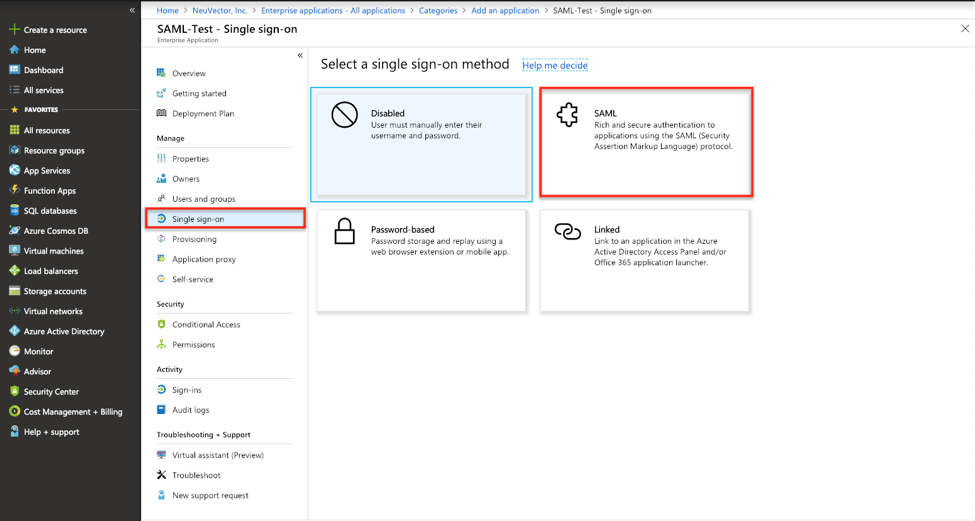
In the application’s configuration page, select "Single sign-on" in the left-side panel and choose the SAML-based sign-on
-
Download the certificate in the base64 format and note the application’s Login URL and Azure AD Identifier
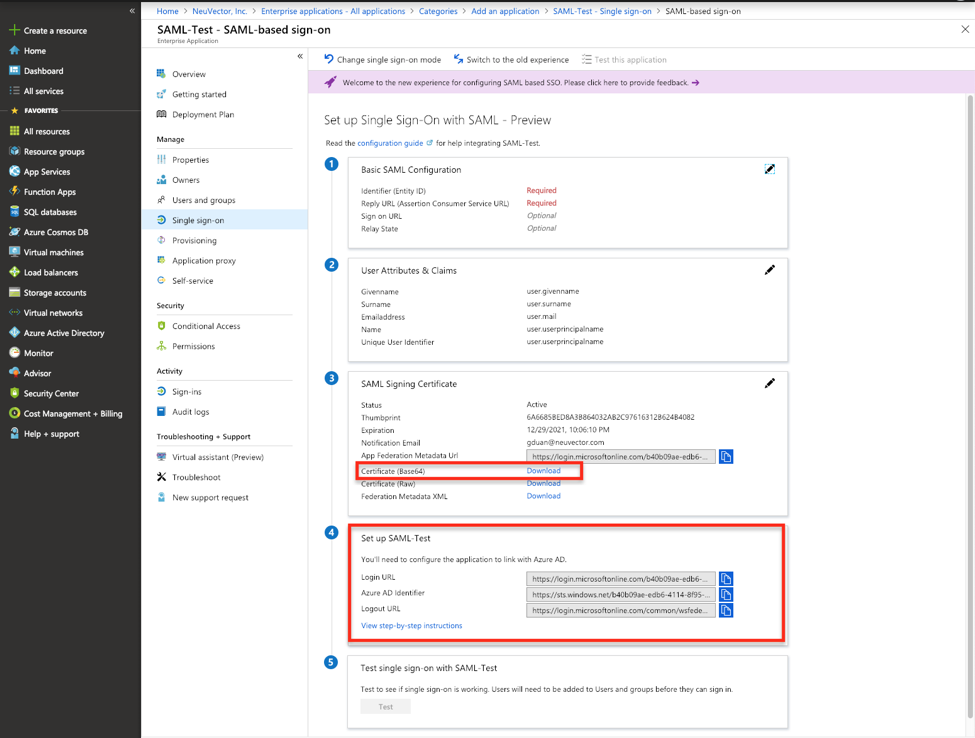
-
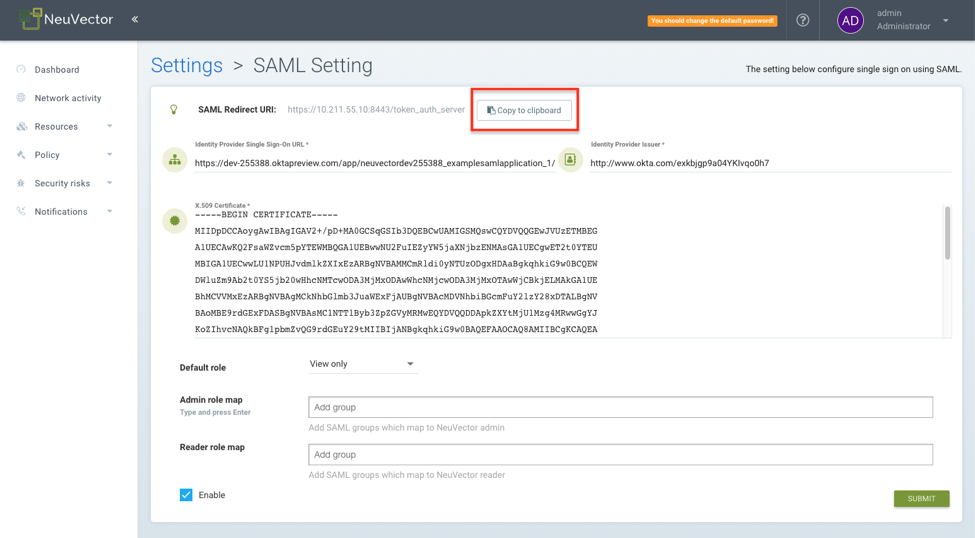
In the SUSE® Security management console, login as an administrator. Select "`Settings" in the administrator dropdown menu at the top-right corner. Click SAML settings
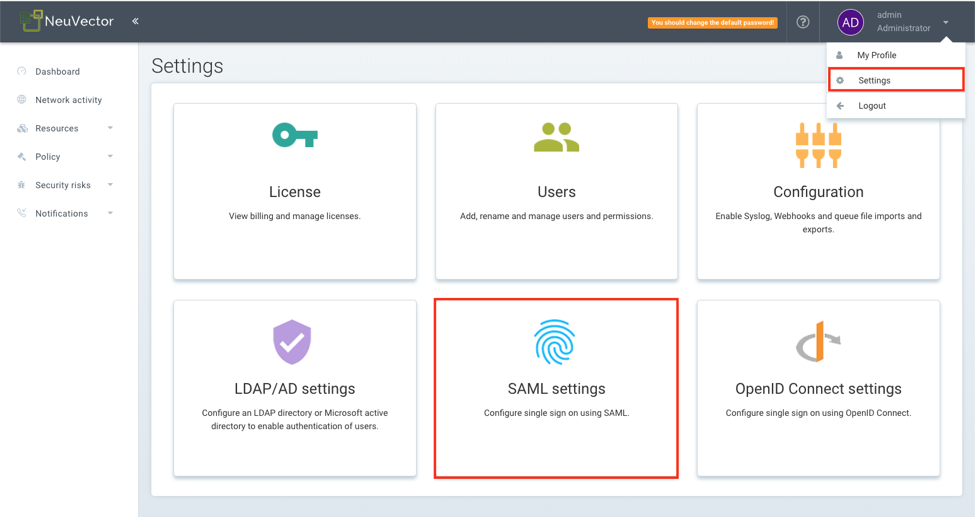
-
Configure the SAML server as follows:
-
Copy application’s "Login URL" as the Single Sign-On URL.
-
Copy "Azure AD Identifier" as the Issuer.
-
Open downloaded the certificate and copy the text to X.509 Certificate box.
-
Set a default role.
-
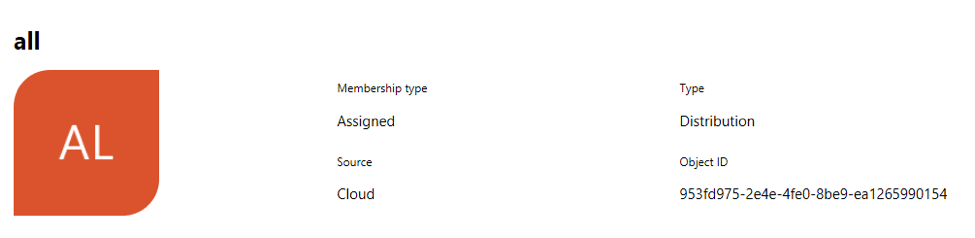
Enter the group name for role mapping. The group claim returned by Azure are identified by the "Object ID" instead of the name. The group’s object ID can be located in menu:Azure Active Directory[Groups > Group name Page]. You should use this value to configure group-based role mapping in SUSE® Security.
Then Enable the SAML server.
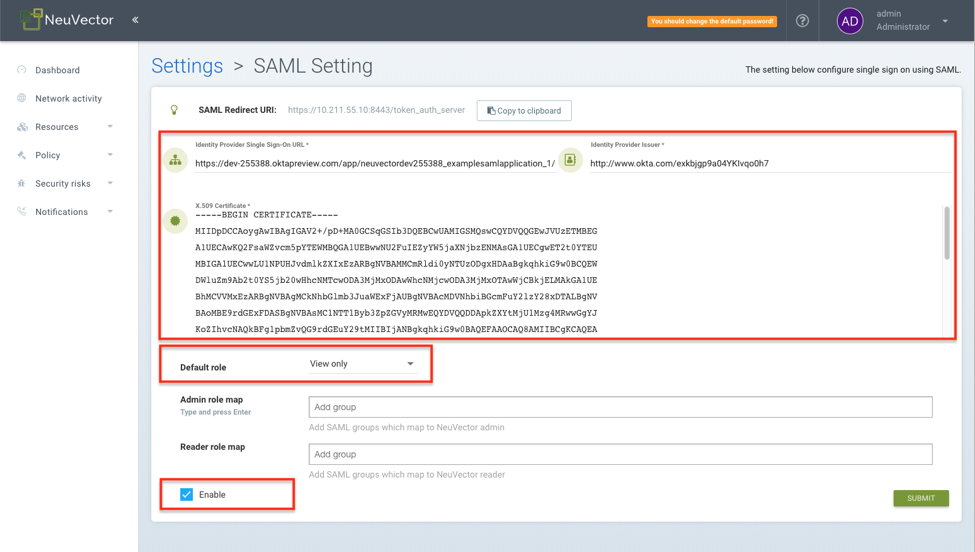
-
-
Copy the Redirect URL
-
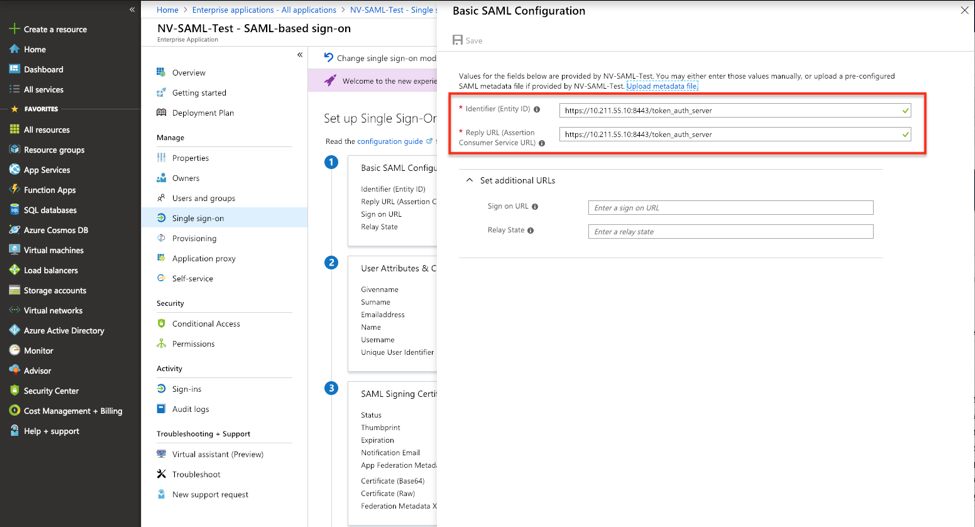
Return to the Azure management console to setup "Basic SAML Configuration". Copy SUSE® Security console’s Redirect URL to both "Identifier" and "Reply URL" boxes
-
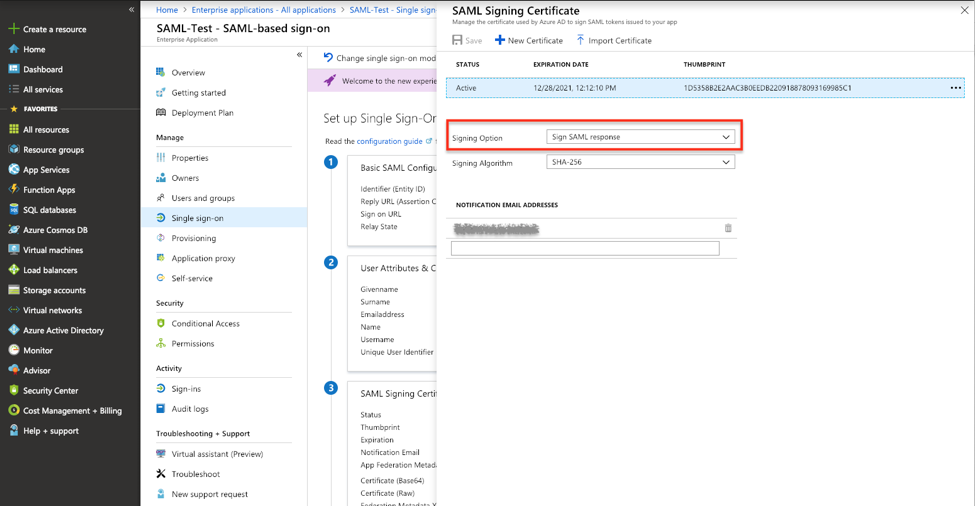
Edit "SAML Signing Certificate", changing the Signing Option to "Sign SAML response"
-
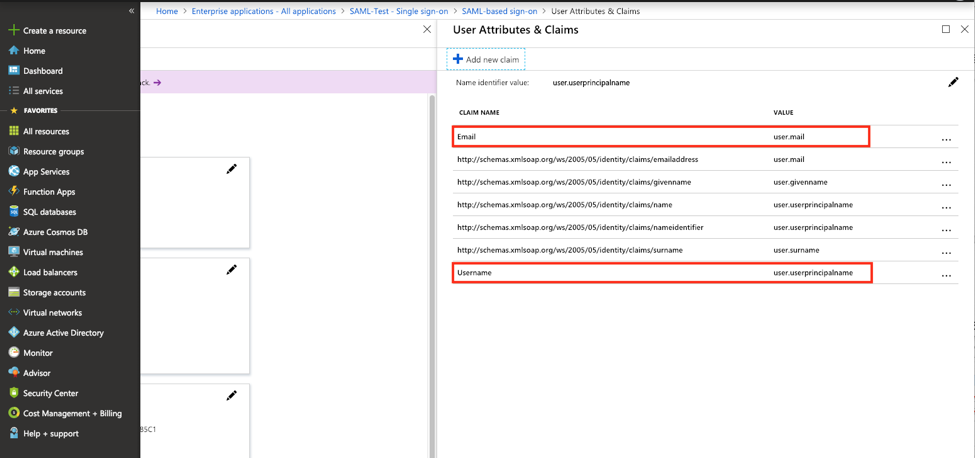
Edit "User Attributes & Claims" so the response can carry the login user’s attributes back to SUSE® Security. Click "Add new claim" to add "Username" and "Email" claims with "user.userprincipalname" and "user.mail" respectively.
-
If the users are assigned to the groups in the active directory, their group membership can be added to the claim. Find the application in "App registrations" and edit the manifest. Modify the value of "groupMembershipClaims" to "All".
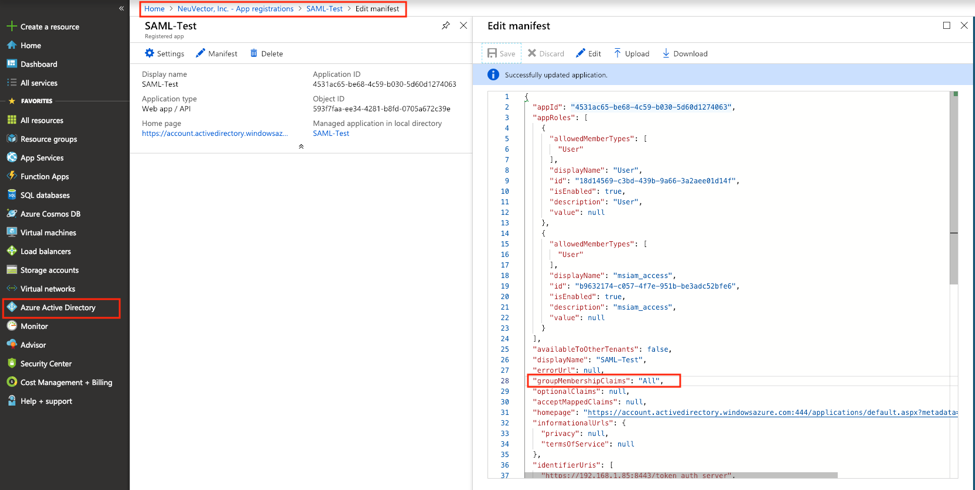
-
Authorize users and groups to access the application so they can login SUSE® Security console with Azure AD SAML SSO
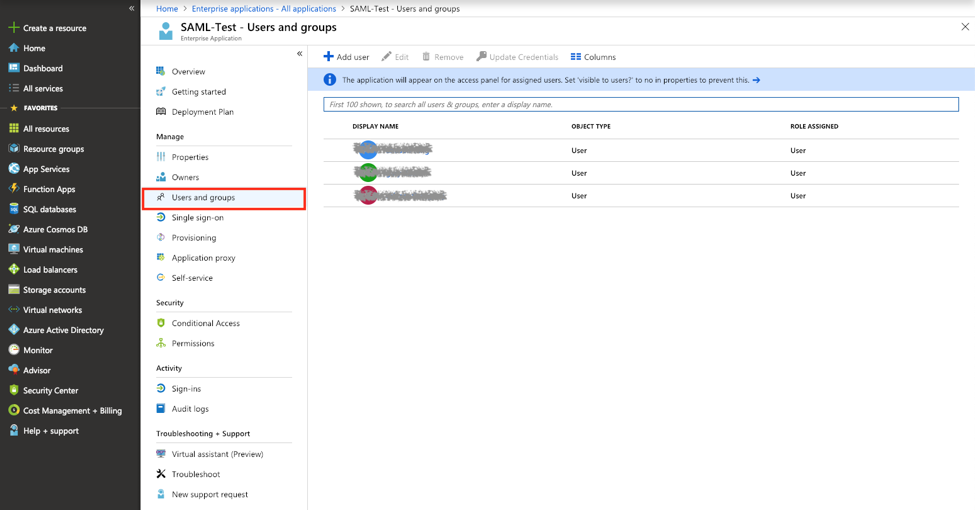
Mapping Groups to Roles and Namespaces
Please see the Users and Roles section for how to map groups to preset and custom roles as well as namespaces in SUSE® Security.