Improve Security Risk Score
Improving the Security Risk Score
The Security Risk Score in the Dashboard provides a score between 0 and 100.
-
0-20 Good
-
21-50 Fair
-
51-100 Poor
The score is the sum of following metrics, each shown as a maximum value, with a max 100:
-
SUSE® Security Protection Mode - 30
-
Ingress/Egress Risk - 42
-
Privileged Containers - 4
-
Root Containers - 4
-
Admission Controls - 4
-
Vulnerabilities - 16 (Containers - 8, Host - 6, orchestrator Platform - 2)
By default, SUSE® Security includes all containers, including system containers, in the risk score. This can be customized for each learned container Group to disable certain containers from being included in the risk score calculation, as shown below.
How to Improve the Score
SUSE® Security Protection Mode
-
Change the New Service Protection Mode in Settings → Configuration to Monitor or Protect
-
Change all ‘learned’ Groups in Policy → Groups to Monitor or Protect
Or
-
Click the Tool icon to follow the Wizard to perform the above steps
Ingress/Egress Risk
-
Click the Tool icon to follow the Wizard to review Ingress and Egress
-
Review all Ingress and Egress Connections to make sure they should be allowed
-
Switch all services that are still in Discover mode to Monitor or Protect
-
Review and Clear all threats, violations and session history by clicking the Delete/Trash icon for each one
Privileged and/or Root Containers
-
Remove privileged containers
-
Remove Root Containers
|
This may not be possible due to your required containers, however each of these only account for 4 points. |
How to Customize Which Container Groups Are Included in the Score
To enable or disable which container Groups are included in the Security Risk Score, go to the Policy → Groups menu, and select the Group to modify. The summary column on the right has a 'Scorable' icon which indicates which groups are used for scoring.
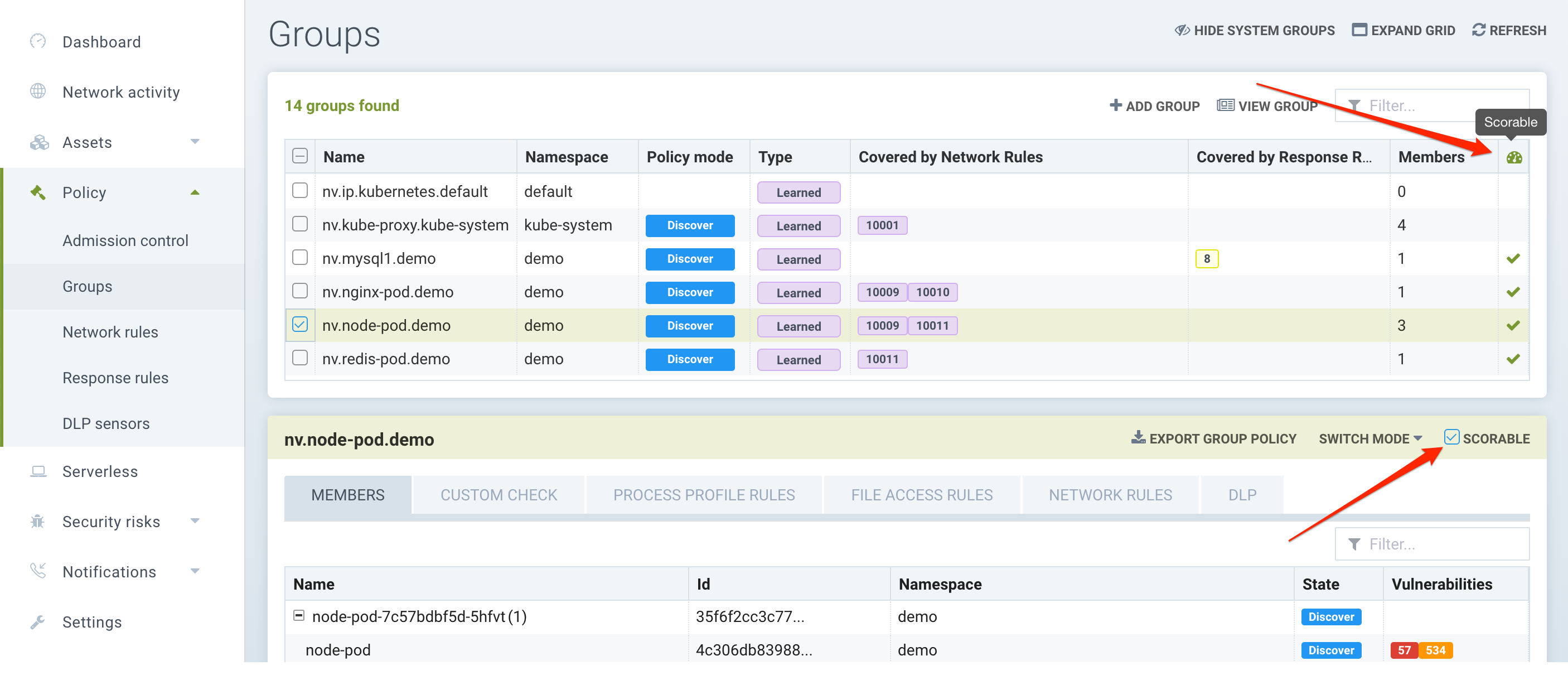
Select or deselect the Scorable check box in the upper right for the selected Group.
|
Only 'learned Groups' (e.g. those that begin with 'nv.') can be edited, not reserved groups or custom groups. |