Splunk
Integrating with Splunk with the SUSE® Security Splunk App
The SUSE® Security Splunk App can be found in the splunkbase catalog here or by searching for SUSE® Security.
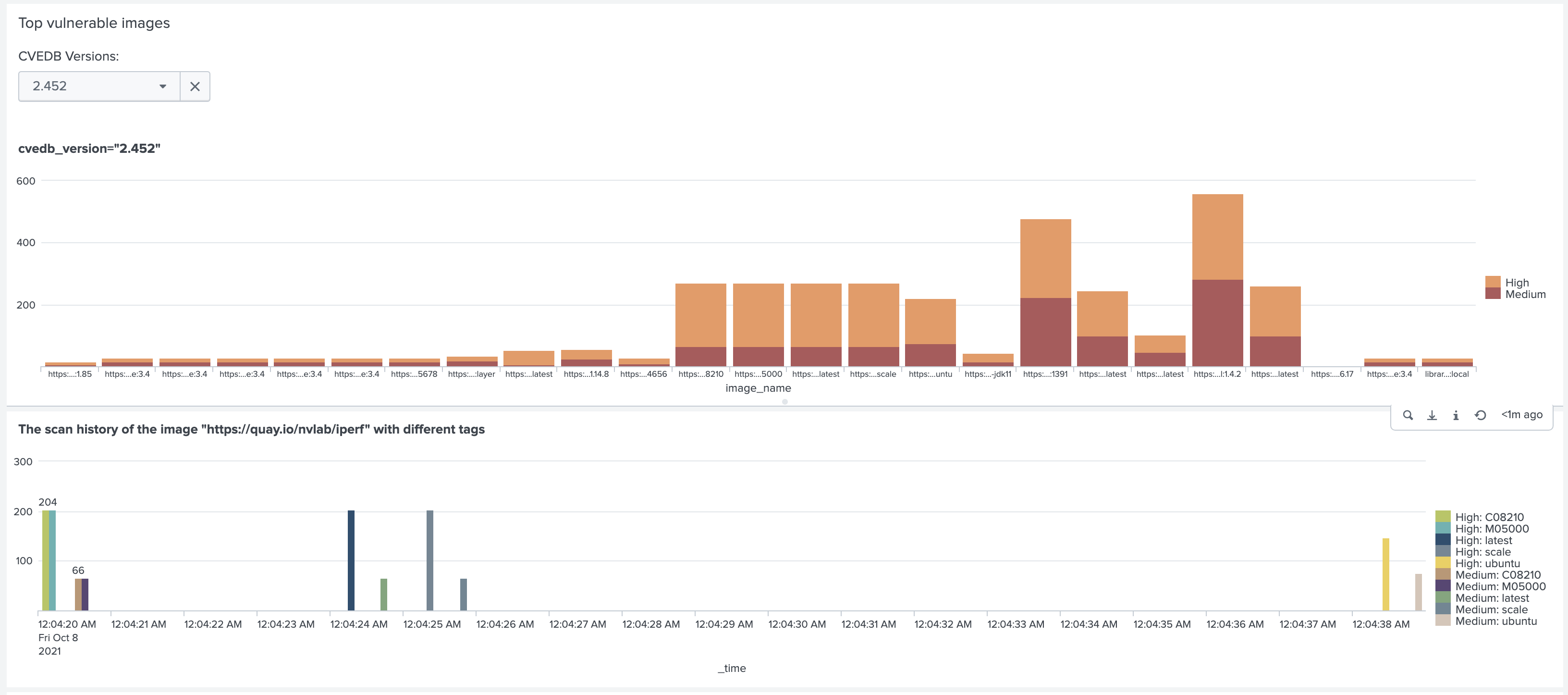
The SUSE® Security Security dashboard helps to identify security events such as suspicious login attempts, network violations and vulnerable images.
Below are sample screens displayed in the Splunk app.
Setup and Configuration
Getting the app
GitHub
Download the latest app tarball (neuvector_app.tar.gz) from the neuvector/neuvector-splunk-app repository.
Splunkbase
Download the latest app tarball from Splunkbase.
Installation and Setup
Install the app by either uploading the tarball or following the Splunkbase prompts.
Configure syslog in SUSE® Security console
Go to Settings → Configuration → Syslog
-
set the server value as the IP address that Splunk is running
-
choose TCP as the protocol
-
set port number as 10514
-
choose Info Level
-
click SUBMIT to save the setting.

You can configure multiple clusters to send syslog to your splunk instance and your splunk instance will receive these syslogs in real time.