Deployment Preparation
Understanding How to Deploy SUSE® Security
Deploy the SUSE® Security containers using Kubernetes, OpenShift, Rancher, Docker, or other platforms. Each type of SUSE® Security container has a unique purpose and may require special performance or node selection requirements for optimum operation.
The SUSE® Security open source images are hosted on Docker Hub at /neuvector/{image name}.
See the Onboarding/Best Practices section to download an on boarding guide.
Deploy using Kubernetes, OpenShift, Rancher, or other Kubernetes-based tools
To deploy SUSE® Security using Kubernetes, OpenShift, Rancher or other orchestration tools, see the preparation steps and sample files in the section Deploying SUSE® Security. This deploys manager, controller, scanner, and enforcer containers. For simple testing using the SUSE® Security Allinone container, see the section Special Use Cases with Allinone.
SUSE® Security supports Helm-based deployment with a Helm chart at https://github.com/neuvector/neuvector-helm.
Automated deployments are supported using Helm, Red Hat/Community Operators, the rest API, or a Kubernetes ConfigMap. See the section Deploy Using ConfigMap for more details on automating deployment.
Deploy using Docker Native
Before you deploy SUSE® Security with docker run or compose, you MUST set the CLUSTER_JOIN_ADDR to the appropriate IP address. Find the node IP address, node name (if using a name server, or node variable (if using orchestration tools) for the allinone (controller) to use for the “node IP” in the docker-compose files for both allinone and enforcer. For example:
- CLUSTER_JOIN_ADDR=192.168.33.10For Swarm-Based deployments, also add the following environment variable:
- NV_PLATFORM_INFO=platform=DockerSee the section Deploying SUSE® Security → Docker Production Deployment for instructions and examples.
Backing Up Configuration Files
By default SUSE® Security stores various config files in /var/neuvector/config/backup on the Controller or Allinone node.
This volume can be mapped to persistent storage to maintain configuration. Files in the folder may need to be deleted in order to start fresh.
Volume Mapping
Make sure volumes are mapped properly. SUSE® Security requires these to operate (/var/neuvector is only required on controller/allinone). For example:
volumes:
- /lib/modules:/lib/modules:ro
- /var/neuvector:/var/neuvector
- /var/run/docker.sock:/var/run/docker.sock:ro
- /proc:/host/proc:ro
- /sys/fs/cgroup:/host/cgroup:roAlso, you may need to ensure that other tools are not blocking access to the docker.sock interface.
Ports and Port Mapping
Make sure the required ports are mapped properly and open on the host. The Manager or Allinone requires 8443 (if using the console). The Allinone and Controller requires 18300, 18301, 18400, 18401 and optionally 10443, 11443, 20443, 30443. The Enforcer requires 18301 and 18401.
|
If deploying docker native (including SWARM) make sure there is not any host firewall blocking access to required ports such as firewalld. If enabled, the docker0 interface must be added as a trusted zone for the allinone/controller hosts. |
Port Summary
The following table lists communications from each SUSE® Security container. The Allinone container combines the Manager, Controller and Enforcer containers so requires the ports listed for those containers.
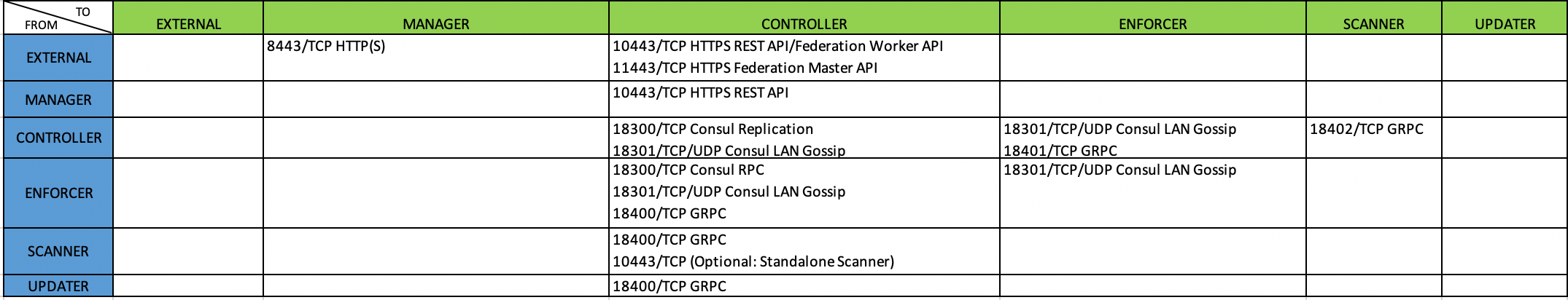
The following table summarizes the listening ports for each SUSE® Security container.

SUSE® Security images
SUSE® Security images are published to Docker Hub. Use a fixed version tag for core components and the latest tag for scanner and updater images.
Use the same version tag for the manager, controller, and enforcer images. Use latest for the scanner and updater images.
neuvector/manager:5.4.1
neuvector/controller:5.4.1
neuvector/enforcer:5.4.1
neuvector/scanner:latest
neuvector/updater:latestUpdate image references in your Kubernetes manifests or Helm values file to match the target NeuVector version.