30 Authentication with cephx #
To identify clients and protect against man-in-the-middle attacks, Ceph
provides its cephx authentication system. Clients in
this context are either human users—such as the admin user—or
Ceph-related services/daemons, for example OSDs, monitors, or Object Gateways.
The cephx protocol does not address data encryption in transport, such as
TLS/SSL.
30.1 Authentication architecture #
cephx uses shared secret keys for authentication, meaning both the client
and Ceph Monitors have a copy of the client’s secret key. The authentication
protocol enables both parties to prove to each other that they have a copy
of the key without actually revealing it. This provides mutual
authentication, which means the cluster is sure the user possesses the
secret key, and the user is sure that the cluster has a copy of the secret
key as well.
A key scalability feature of Ceph is to avoid a centralized interface to
the Ceph object store. This means that Ceph clients can interact with
OSDs directly. To protect data, Ceph provides its cephx authentication
system, which authenticates Ceph clients.
Each monitor can authenticate clients and distribute keys, so there is no
single point of failure or bottleneck when using cephx. The monitor
returns an authentication data structure that contains a session key for use
in obtaining Ceph services. This session key is itself encrypted with the
client’s permanent secret key, so that only the client can request services
from the Ceph monitors. The client then uses the session key to request
its desired services from the monitor, and the monitor provides the client
with a ticket that will authenticate the client to the OSDs that actually
handle data. Ceph monitors and OSDs share a secret, so the client can use
the ticket provided by the monitor with any OSD or metadata server in the
cluster. cephx tickets expire, so an attacker cannot use an expired ticket
or session key obtained wrongfully.
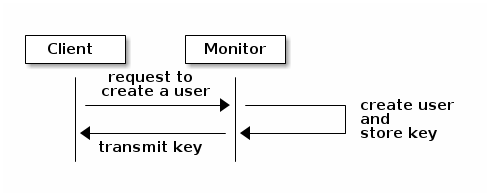
To use cephx, an administrator must setup clients/users first. In the
following diagram, the
client.admin user invokes
ceph auth get-or-create-key from the command line to
generate a user name and secret key. Ceph’s auth
subsystem generates the user name and key, stores a copy with the monitor(s)
and transmits the user’s secret back to the
client.admin user. This means that
the client and the monitor share a secret key.
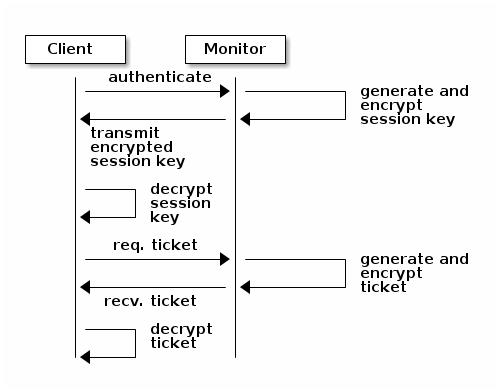
cephx authentication #To authenticate with the monitor, the client passes the user name to the monitor. The monitor generates a session key and encrypts it with the secret key associated with the user name and transmits the encrypted ticket back to the client. The client then decrypts the data with the shared secret key to retrieve the session key. The session key identifies the user for the current session. The client then requests a ticket related to the user, which is signed by the session key. The monitor generates a ticket, encrypts it with the user’s secret key and transmits it back to the client. The client decrypts the ticket and uses it to sign requests to OSDs and metadata servers throughout the cluster.
cephx authentication #
The cephx protocol authenticates ongoing communications between the client
machine and the Ceph servers. Each message sent between a client and a
server after the initial authentication is signed using a ticket that the
monitors, OSDs, and metadata servers can verify with their shared secret.
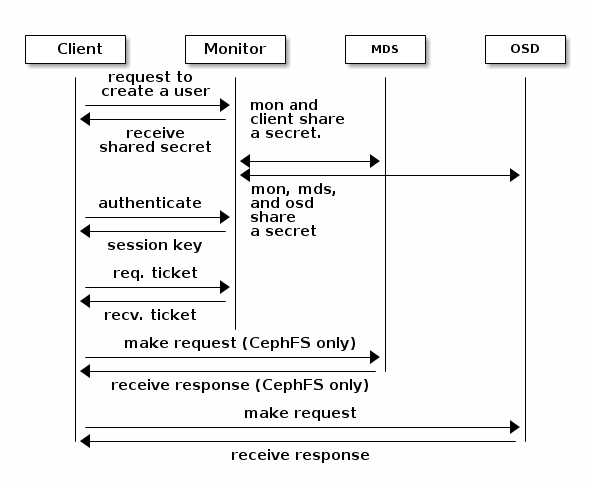
cephx authentication - MDS and OSD #The protection offered by this authentication is between the Ceph client and the Ceph cluster hosts. The authentication is not extended beyond the Ceph client. If the user accesses the Ceph client from a remote host, Ceph authentication is not applied to the connection between the user’s host and the client host.
30.2 Key management #
This section describes Ceph client users and their authentication and authorization with the Ceph storage cluster. Users are either individuals or system actors such as applications, which use Ceph clients to interact with the Ceph storage cluster daemons.
When Ceph runs with authentication and authorization enabled (enabled by
default), you must specify a user name and a keyring containing the secret
key of the specified user (usually via the command line). If you do not
specify a user name, Ceph will use
client.admin as the default user
name. If you do not specify a keyring, Ceph will look for a keyring via
the keyring setting in the Ceph configuration file. For example, if you
execute the ceph health command without specifying a user
name or keyring, Ceph interprets the command like this:
cephuser@adm > ceph -n client.admin --keyring=/etc/ceph/ceph.client.admin.keyring health
Alternatively, you may use the CEPH_ARGS environment
variable to avoid re-entering the user name and secret.
30.2.1 Background information #
Regardless of the type of Ceph client (for example, block device, object storage, file system, native API), Ceph stores all data as objects within pools. Ceph users need to have access to pools in order to read and write data. Additionally, Ceph users must have execute permissions to use Ceph's administrative commands. The following concepts will help you understand Ceph user management.
30.2.1.1 User #
A user is either an individual or a system actor such as an application. Creating users allows you to control who (or what) can access your Ceph storage cluster, its pools, and the data within pools.
Ceph uses types of users. For the purposes of user
management, the type will always be client. Ceph
identifies users in period (.) delimited form, consisting of the user type
and the user ID. For example, TYPE.ID,
client.admin, or client.user1. The
reason for user typing is that Ceph monitors, OSDs, and metadata servers
also use the cephx protocol, but they are not clients. Distinguishing the
user type helps to distinguish between client users and other users,
streamlining access control, user monitoring, and traceability.
Sometimes Ceph’s user type may seem confusing, because the Ceph
command line allows you to specify a user with or without the type,
depending upon your command line usage. If you specify
--user or --id, you can omit the type.
So client.user1 can be entered simply as
user1. If you specify --name or
-n, you must specify the type and name, such as
client.user1. We recommend using the type and name as a
best practice wherever possible.
A Ceph storage cluster user is not the same as a Ceph object storage user or a Ceph file system user. The Ceph Object Gateway uses a Ceph storage cluster user to communicate between the gateway daemon and the storage cluster, but the gateway has its own user management functionality for end users. The Ceph file system uses POSIX semantics. The user space associated with it is not the same as a Ceph storage cluster user.
30.2.1.2 Authorization and capabilities #
Ceph uses the term 'capabilities' (caps) to describe authorizing an authenticated user to exercise the functionality of the monitors, OSDs, and metadata servers. Capabilities can also restrict access to data within a pool or pool namespace. A Ceph administrative user sets a user's capabilities when creating or updating a user.
Capability syntax follows the form:
daemon-type 'allow capability' [...]
Following is a list of capabilities for each service type:
- Monitor capabilities
include
r,w,xandallow profile cap.mon 'allow rwx' mon 'allow profile osd'
- OSD capabilities
include
r,w,x,class-read,class-writeandprofile osd. Additionally, OSD capabilities also allow for pool and namespace settings.osd 'allow capability' [pool=poolname] [namespace=namespace-name]
- MDS capability
simply requires
allow, or blank.mds 'allow'
The following entries describe each capability:
- allow
Precedes access settings for a daemon. Implies
rwfor MDS only.- r
Gives the user read access. Required with monitors to retrieve the CRUSH map.
- w
Gives the user write access to objects.
- x
Gives the user the capability to call class methods (both read and write) and to conduct
authoperations on monitors.- class-read
Gives the user the capability to call class read methods. Subset of
x.- class-write
Gives the user the capability to call class write methods. Subset of
x.- *
Gives the user read, write, and execute permissions for a particular daemon/pool, and the ability to execute admin commands.
- profile osd
Gives a user permissions to connect as an OSD to other OSDs or monitors. Conferred on OSDs to enable OSDs to handle replication heartbeat traffic and status reporting.
- profile mds
Gives a user permissions to connect as an MDS to other MDSs or monitors.
- profile bootstrap-osd
Gives a user permissions to bootstrap an OSD. Delegated to deployment tools so that they have permissions to add keys when bootstrapping an OSD.
- profile bootstrap-mds
Gives a user permissions to bootstrap a metadata server. Delegated to deployment tools so they have permissions to add keys when bootstrapping a metadata server.
30.2.1.3 Pools #
A pool is a logical partition where users store data. In Ceph
deployments, it is common to create a pool as a logical partition for
similar types of data. For example, when deploying Ceph as a back-end
for OpenStack, a typical deployment would have pools for volumes, images,
backups and virtual machines, and users such as
client.glance or
client.cinder.
30.2.2 Managing users #
User management functionality provides Ceph cluster administrators with the ability to create, update, and delete users directly in the Ceph cluster.
When you create or delete users in the Ceph cluster, you may need to distribute keys to clients so that they can be added to keyrings. See Section 30.2.3, “Managing keyrings” for details.
30.2.2.1 Listing users #
To list the users in your cluster, execute the following:
cephuser@adm > ceph auth list
Ceph will list all users in your cluster. For example, in a cluster with
two nodes, ceph auth list output looks similar to this:
installed auth entries:
osd.0
key: AQCvCbtToC6MDhAATtuT70Sl+DymPCfDSsyV4w==
caps: [mon] allow profile osd
caps: [osd] allow *
osd.1
key: AQC4CbtTCFJBChAAVq5spj0ff4eHZICxIOVZeA==
caps: [mon] allow profile osd
caps: [osd] allow *
client.admin
key: AQBHCbtT6APDHhAA5W00cBchwkQjh3dkKsyPjw==
caps: [mds] allow
caps: [mon] allow *
caps: [osd] allow *
client.bootstrap-mds
key: AQBICbtTOK9uGBAAdbe5zcIGHZL3T/u2g6EBww==
caps: [mon] allow profile bootstrap-mds
client.bootstrap-osd
key: AQBHCbtT4GxqORAADE5u7RkpCN/oo4e5W0uBtw==
caps: [mon] allow profile bootstrap-osd
Note that the TYPE.ID notation for users applies such
that osd.0 specifies a user of type
osd and its ID is 0.
client.admin is a user of type
client and its ID is admin. Note
also that each entry has a key:
value entry, and one or more
caps: entries.
You may use the -o filename
option with ceph auth list to save the output to a
file.
30.2.2.2 Getting information about users #
To retrieve a specific user, key, and capabilities, execute the following:
cephuser@adm > ceph auth get TYPE.IDFor example:
cephuser@adm > ceph auth get client.admin
exported keyring for client.admin
[client.admin]
key = AQA19uZUqIwkHxAAFuUwvq0eJD4S173oFRxe0g==
caps mds = "allow"
caps mon = "allow *"
caps osd = "allow *"Developers may also execute the following:
cephuser@adm > ceph auth export TYPE.ID
The auth export command is identical to auth
get, but also prints the internal authentication ID.
30.2.2.3 Adding users #
Adding a user creates a user name (TYPE.ID), a secret
key, and any capabilities included in the command you use to create the
user.
A user's key enables the user to authenticate with the Ceph storage cluster. The user's capabilities authorize the user to read, write, or execute on Ceph monitors (mon), Ceph OSDs (osd), or Ceph metadata servers (mds).
There are a few commands available to add a user:
ceph auth addThis command is the canonical way to add a user. It will create the user, generate a key, and add any specified capabilities.
ceph auth get-or-createThis command is often the most convenient way to create a user, because it returns a keyfile format with the user name (in brackets) and the key. If the user already exists, this command simply returns the user name and key in the keyfile format. You may use the
-o filenameoption to save the output to a file.ceph auth get-or-create-keyThis command is a convenient way to create a user and return the user's key (only). This is useful for clients that need the key only (for example
libvirt). If the user already exists, this command simply returns the key. You may use the-o filenameoption to save the output to a file.
When creating client users, you may create a user with no capabilities. A
user with no capabilities can authenticate but nothing more. Such client
cannot retrieve the cluster map from the monitor. However, you can create
a user with no capabilities if you want to defer adding capabilities later
using the ceph auth caps command.
A typical user has at least read capabilities on the Ceph monitor and read and write capabilities on Ceph OSDs. Additionally, a user's OSD permissions are often restricted to accessing a particular pool.
cephuser@adm >ceph auth add client.john mon 'allow r' osd \ 'allow rw pool=liverpool'cephuser@adm >ceph auth get-or-create client.paul mon 'allow r' osd \ 'allow rw pool=liverpool'cephuser@adm >ceph auth get-or-create client.george mon 'allow r' osd \ 'allow rw pool=liverpool' -o george.keyringcephuser@adm >ceph auth get-or-create-key client.ringo mon 'allow r' osd \ 'allow rw pool=liverpool' -o ringo.key
If you provide a user with capabilities to OSDs, but you do not restrict access to particular pools, the user will have access to all pools in the cluster.
30.2.2.4 Modifying user capabilities #
The ceph auth caps command allows you to specify a user
and change the user's capabilities. Setting new capabilities will
overwrite current ones. To view current capabilities run ceph
auth get
USERTYPE.USERID.
To add capabilities, you also need to specify the existing capabilities
when using the following form:
cephuser@adm > ceph auth caps USERTYPE.USERID daemon 'allow [r|w|x|*|...] \
[pool=pool-name] [namespace=namespace-name]' [daemon 'allow [r|w|x|*|...] \
[pool=pool-name] [namespace=namespace-name]']For example:
cephuser@adm >ceph auth get client.johncephuser@adm >ceph auth caps client.john mon 'allow r' osd 'allow rw pool=prague'cephuser@adm >ceph auth caps client.paul mon 'allow rw' osd 'allow r pool=prague'cephuser@adm >ceph auth caps client.brian-manager mon 'allow *' osd 'allow *'
To remove a capability, you may reset the capability. If you want the user to have no access to a particular daemon that was previously set, specify an empty string:
cephuser@adm > ceph auth caps client.ringo mon ' ' osd ' '30.2.2.5 Deleting users #
To delete a user, use ceph auth del:
cephuser@adm > ceph auth del TYPE.ID
where TYPE is one of client,
osd, mon, or mds,
and ID is the user name or ID of the daemon.
If you created users with permissions strictly for a pool that no longer exists, you should consider deleting those users too.
30.2.2.6 Printing a user's key #
To print a user’s authentication key to standard output, execute the following:
cephuser@adm > ceph auth print-key TYPE.ID
where TYPE is one of client,
osd, mon, or mds,
and ID is the user name or ID of the daemon.
Printing a user's key is useful when you need to populate client software
with a user's key (such as libvirt), as in the following example:
# mount -t ceph host:/ mount_point \
-o name=client.user,secret=`ceph auth print-key client.user`30.2.2.7 Importing users #
To import one or more users, use ceph auth import and
specify a keyring:
cephuser@adm > ceph auth import -i /etc/ceph/ceph.keyringThe Ceph storage cluster will add new users, their keys and their capabilities and will update existing users, their keys and their capabilities.
30.2.3 Managing keyrings #
When you access Ceph via a Ceph client, the client will look for a local keyring. Ceph presets the keyring setting with the following four keyring names by default so you do not need to set them in your Ceph configuration file unless you want to override the defaults:
/etc/ceph/cluster.name.keyring /etc/ceph/cluster.keyring /etc/ceph/keyring /etc/ceph/keyring.bin
The cluster metavariable is your Ceph cluster
name as defined by the name of the Ceph configuration file.
ceph.conf means that the cluster name is
ceph, thus ceph.keyring. The
name metavariable is the user type and user ID,
for example client.admin, thus
ceph.client.admin.keyring.
After you create a user (for example
client.ringo), you must get the
key and add it to a keyring on a Ceph client so that the user can access
the Ceph storage cluster.
Section 30.2, “Key management” details how to list, get, add,
modify and delete users directly in the Ceph storage cluster. However,
Ceph also provides the ceph-authtool utility to allow
you to manage keyrings from a Ceph client.
30.2.3.1 Creating a keyring #
When you use the procedures in Section 30.2, “Key management” to create users, you need to provide user keys to the Ceph client(s) so that the client can retrieve the key for the specified user and authenticate with the Ceph storage cluster. Ceph clients access keyrings to look up a user name and retrieve the user's key:
cephuser@adm > ceph-authtool --create-keyring /path/to/keyring
When creating a keyring with multiple users, we recommend using the
cluster name (for example cluster.keyring) for
the keyring file name and saving it in the /etc/ceph
directory so that the keyring configuration default setting will pick up
the file name without requiring you to specify it in the local copy of
your Ceph configuration file. For example, create
ceph.keyring by executing the following:
cephuser@adm > ceph-authtool -C /etc/ceph/ceph.keyring
When creating a keyring with a single user, we recommend using the cluster
name, the user type and the user name and saving it in the
/etc/ceph directory. For example,
ceph.client.admin.keyring for the
client.admin user.
30.2.3.2 Adding a user to a keyring #
When you add a user to the Ceph storage cluster (see Section 30.2.2.3, “Adding users”), you can retrieve the user, key and capabilities, and save the user to a keyring.
If you only want to use one user per keyring, the ceph auth
get command with the -o option will save the
output in the keyring file format. For example, to create a keyring for
the client.admin user, execute
the following:
cephuser@adm > ceph auth get client.admin -o /etc/ceph/ceph.client.admin.keyring
When you want to import users to a keyring, you can use
ceph-authtool to specify the destination keyring and
the source keyring:
cephuser@adm > ceph-authtool /etc/ceph/ceph.keyring \
--import-keyring /etc/ceph/ceph.client.admin.keyring
If your keyring is compromised, delete your key from the
/etc/ceph directory and re-create a new key using
the same instructions from Section 30.2.3.1, “Creating a keyring”.
30.2.3.3 Creating a user #
Ceph provides the ceph auth add command to create a
user directly in the Ceph storage cluster. However, you can also create
a user, keys and capabilities directly on a Ceph client keyring. Then,
you can import the user to the Ceph storage cluster:
cephuser@adm > ceph-authtool -n client.ringo --cap osd 'allow rwx' \
--cap mon 'allow rwx' /etc/ceph/ceph.keyringYou can also create a keyring and add a new user to the keyring simultaneously:
cephuser@adm > ceph-authtool -C /etc/ceph/ceph.keyring -n client.ringo \
--cap osd 'allow rwx' --cap mon 'allow rwx' --gen-key
In the previous scenarios, the new user
client.ringo is only in the
keyring. To add the new user to the Ceph storage cluster, you must still
add the new user to the cluster:
cephuser@adm > ceph auth add client.ringo -i /etc/ceph/ceph.keyring30.2.3.4 Modifying users #
To modify the capabilities of a user record in a keyring, specify the keyring and the user followed by the capabilities:
cephuser@adm > ceph-authtool /etc/ceph/ceph.keyring -n client.ringo \
--cap osd 'allow rwx' --cap mon 'allow rwx'To update the modified user within the Ceph cluster environment, you must import the changes from the keyring to the user entry in the Ceph cluster:
cephuser@adm > ceph auth import -i /etc/ceph/ceph.keyringSee Section 30.2.2.7, “Importing users” for details on updating a Ceph storage cluster user from a keyring.
30.2.4 Commandline usage #
The ceph command supports the following options related
to the user name and secret manipulation:
--idor--userCeph identifies users with a type and an ID (TYPE.ID, such as
client.adminorclient.user1). Theid,nameand-noptions enable you to specify the ID portion of the user name (for exampleadminoruser1). You can specify the user with the --id and omit the type. For example, to specify user client.foo enter the following:cephuser@adm >ceph --id foo --keyring /path/to/keyring healthcephuser@adm >ceph --user foo --keyring /path/to/keyring health--nameor-nCeph identifies users with a type and an ID (TYPE.ID, such as
client.adminorclient.user1). The--nameand-noptions enable you to specify the fully qualified user name. You must specify the user type (typicallyclient) with the user ID:cephuser@adm >ceph --name client.foo --keyring /path/to/keyring healthcephuser@adm >ceph -n client.foo --keyring /path/to/keyring health--keyringThe path to the keyring containing one or more user name and secret. The
--secretoption provides the same functionality, but it does not work with Object Gateway, which uses--secretfor another purpose. You may retrieve a keyring withceph auth get-or-createand store it locally. This is a preferred approach, because you can switch user names without switching the keyring path:cephuser@adm >rbd map --id foo --keyring /path/to/keyring mypool/myimage