33 Installing SUSE CaaS Platform heat Templates #
This chapter describes how to install SUSE CaaS Platform v3 using heat template on SUSE OpenStack Cloud.
33.1 SUSE CaaS Platform heat Installation Procedure #
Download the latest SUSE CaaS Platform for OpenStack image (for example,
SUSE-CaaS-Platform-3.0-OpenStack-Cloud.x86_64-1.0.0-GM.qcow2) from https://download.suse.com.Upload the image to glance:
openstack image create --public --disk-format qcow2 --container-format \ bare --file SUSE-CaaS-Platform-3.0-OpenStack-Cloud.x86_64-1.0.0-GM.qcow2 \ CaaSP-3
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
zypper in caasp-openstack-heat-templates
The installed templates are located in
/usr/share/caasp-openstack-heat-templates.Alternatively, you can get official heat templates by cloning the appropriate Git repository:
git clone https://github.com/SUSE/caasp-openstack-heat-templates
In horizon, go to › › .
Select from the drop-down box and upload the
caasp-stack.yamlfile.In the dialog, provide the required information (stack name, password, flavor size, external network of your environment, etc.).
Click to launch the stack. This creates all required resources for running SUSE CaaS Platform in an OpenStack environment. The stack creates one Admin Node, one Master Node, and server worker nodes as specified.
Specify the appropriate flavor and network settings in the
caasp-environment.yamlfile.Create a stack in heat by passing the template, environment file, and parameters:
openstack stack create -t caasp-stack.yaml -e caasp-environment.yaml \ --parameter image=CaaSP-3 caasp-stack
After the stack has been created, the Velum SUSE CaaS Platform dashboard runs on the Admin Node. You can access it using the Admin Node's floating IP address.
Create an account and follow the steps in the Velum SUSE CaaS Platform dashboard to complete the SUSE CaaS Platform installation.
When you have successfully accessed the admin node web interface via the floating IP, follow the instructions at https://documentation.suse.com/suse-caasp/4.1/single-html/caasp-deployment/ to continue the setup of SUSE CaaS Platform.
33.2 Installing SUSE CaaS Platform with Multiple Masters #
A heat stack with load balancing and multiple master nodes can only be created from the command line, because horizon does not have support for nested heat templates.
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
zypper in caasp-openstack-heat-templates
The installed templates are located in
/usr/share/caasp-openstack-heat-templates.
A working load balancer is needed in your SUSE OpenStack Cloud deployment. SUSE OpenStack Cloud uses HAProxy.
Verify that load balancing with HAProxy is working correctly
in your OpenStack installation by creating a load balancer manually and
checking that the provisioning_status changes to
Active.
ardana > openstack loadbalancer show
<LOAD_BALANCER_ID>HAProxy is the default load balancer provider in SUSE OpenStack Cloud.
The steps below can be used to set up a network, subnet, router, security
and IPs for a test lb_net1 network with
lb_subnet1 subnet.
ardana >openstack network create lb_net1ardana >openstack subnet create --name lb_subnet1 lb_net1 \ --subnet-range 172.29.0.0/24 --gateway 172.29.0.2ardana >openstack router create lb_router1ardana >openstack router add subnet lb_router1 lb_subnet1ardana >openstack router set lb_router1 --external-gateway ext-netardana >openstack network list
Specify the appropriate flavor and network settings in the
caasp-multi-master-environment.yamlfile.Set
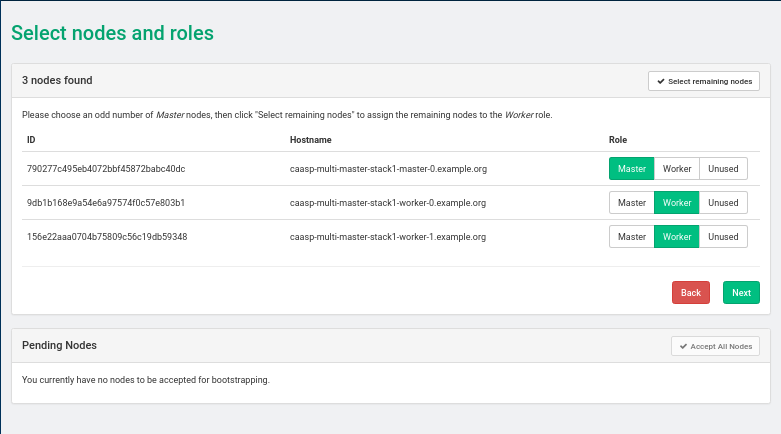
master_countto the desired number in thecaasp-multi-master-environment.yamlfile. The master count must be set to an odd number of nodes.master_count: 3
Create a stack in heat by passing the template, environment file, and parameters:
ardana >openstack stack create -t caasp-multi-master-stack.yaml \ -e caasp-multi-master-environment.yaml --parameter image=CaaSP-3 caasp-multi-master-stackFind the floating IP address of the load balancer. This is necessary for accessing the Velum SUSE CaaS Platform dashboard.
ardana >openstack loadbalancer list --providerFrom the output, copy the
idand enter it in the following command as shown in the following example:ardana >openstack loadbalancer show id+---------------------+------------------------------------------------+ | Field | Value | +---------------------+------------------------------------------------+ | admin_state_up | True | | description | | | id | 0d973d80-1c79-40a4-881b-42d111ee9625 | | listeners | {"id": "c9a34b63-a1c8-4a57-be22-75264769132d"} | | | {"id": "4fa2dae0-126b-4eb0-899f-b2b6f5aab461"} | | name | caasp-stack-master_lb-bhr66gtrx3ue | | operating_status | ONLINE | | pools | {"id": "8c011309-150c-4252-bb04-6550920e0059"} | | | {"id": "c5f55af7-0a25-4dfa-a088-79e548041929"} | | provider | haproxy | | provisioning_status | ACTIVE | | tenant_id | fd7ffc07400642b1b05dbef647deb4c1 | | vip_address | 172.28.0.6 | | vip_port_id | 53ad27ba-1ae0-4cd7-b798-c96b53373e8b | | vip_subnet_id | 87d18a53-ad0c-4d71-b82a-050c229b710a | +---------------------+------------------------------------------------+Search the floating IP list for
vip_addressardana >openstack floating ip list | grep 172.28.0.6 | d636f3...481b0c | fd7ff...deb4c1 | 172.28.0.6 | 10.84.65.37 | 53ad2...373e8b |The load balancer floating ip address is 10.84.65.37
Accessing the Velum SUSE CaaS Platform Dashboard
After the stack has been created, the Velum SUSE CaaS Platform dashboard runs on the admin node. You can access it using the floating IP address of the admin node.
Create an account and follow the steps in the Velum SUSE CaaS Platform dashboard to complete the SUSE CaaS Platform installation.
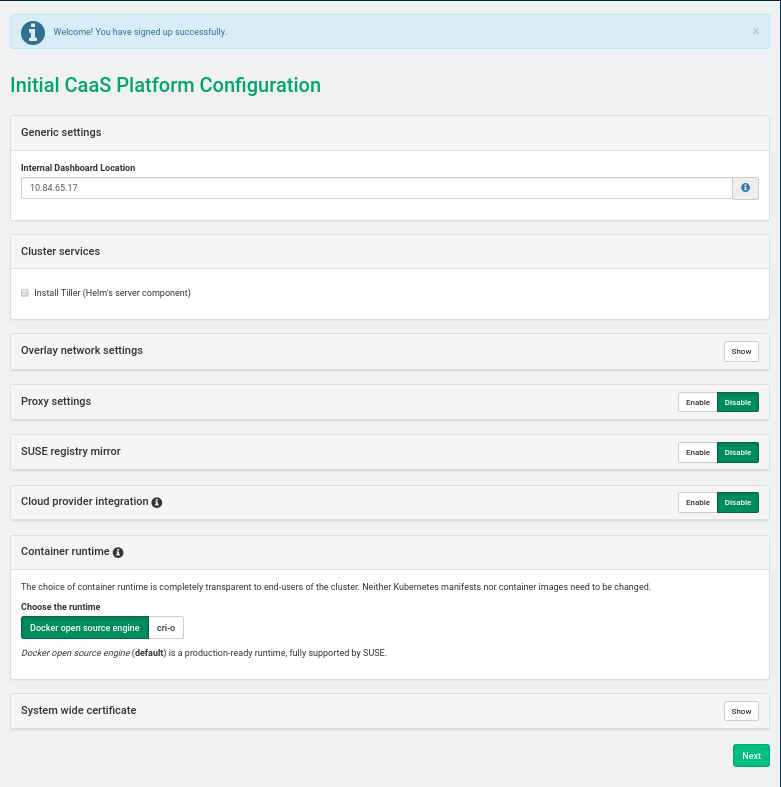
SUSE CaaS Platform Admin Node Install: Screen 1
If you plan to manage your containers using Helm or Airship (this is common),
check the box labeled Install Tiller (Helm's server component).
SUSE CaaS Platform Admin Node Install: Screen 2
SUSE CaaS Platform Admin Node Install: Screen 3
SUSE CaaS Platform Admin Node Install: Screen 4
SUSE CaaS Platform Admin Node Install: Screen 5
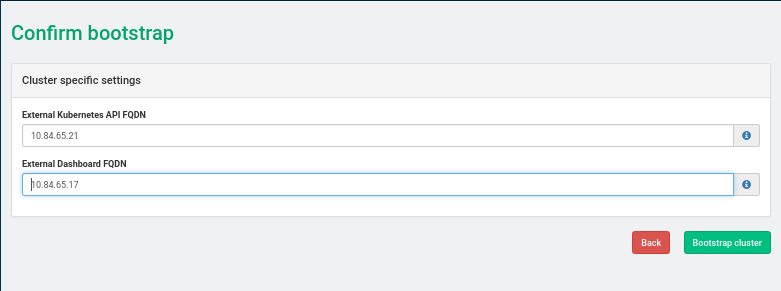
Set External Kubernetes API to LOADBALANCER_FLOATING_IP, External Dashboard FQDN to ADMIN_NODE_FLOATING_IP
SUSE CaaS Platform Admin Node Install: Screen 6
SUSE CaaS Platform Admin Node Install: Screen 7
33.3 Deploy SUSE CaaS Platform Stack Using heat SUSE CaaS Platform Playbook #
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
ardana >zypper in caasp-openstack-heat-templatesThe installed templates are located in
/usr/share/caasp-openstack-heat-templates.Run
heat-caasp-deploy.ymlon the Cloud Lifecycle Manager to create a SUSE CaaS Platform cluster with heat templates from thecaasp-openstack-heat-templatespackage.ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.ymlIn a browser, navigate to the horizon UI to determine the floating IP address assigned to the admin node.
Go to http://ADMIN-NODE-FLOATING-IP/ to bring up the Velum dashboard.
Complete the web-based bootstrap process to bring up the SUSE CaaS Platform Kubernetes cluster. Refer to the SUSE CaaS Platform documentation for specifics.
When prompted, set the
Internal Dashboard Locationto the private network IP address (i.e. in the the 172.x.x.x subnet) of the SUSE CaaS Platform admin node created during theheat-caasp-deploy.ymlplaybook. Do not use the floating IP address which is also associated with the node.
33.4 Deploy SUSE CaaS Platform Cluster with Multiple Masters Using heat CaasP Playbook #
Install the caasp-openstack-heat-templates package on a machine with SUSE OpenStack Cloud repositories:
ardana >zypper in caasp-openstack-heat-templatesThe installed templates are located in
/usr/share/caasp-openstack-heat-templates.On the Cloud Lifecycle Manager, run the
heat-caasp-deploy.ymlplaybook and pass parameters forcaasp_stack_name,caasp_stack_yaml_fileandcaasp_stack_env_yaml_file.ardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_stack_name=caasp_multi-master caasp_stack_yaml_file=caasp-multi-master-stack.yaml caasp_stack_env_yaml_file=caasp-multi-master-environment.yaml"
33.5 SUSE CaaS Platform OpenStack Image for heat SUSE CaaS Platform Playbook #
By default the heat SUSE CaaS Platform playbook downloads the SUSE CaaS Platform image from http://download.suse.de/install/SUSE-CaaSP-3-GM/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2. If this URL is not accessible, the SUSE CaaS Platform image can be downloaded from https://download.suse.com/Download?buildid=z7ezhywXXRc and copied to the deployer.
To create a SUSE CaaS Platform cluster and pass the path to the downloaded image, run the following commands:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_image_tmp_path=~/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2"
To create a SUSE CaaS Platform cluster with multiple masters and pass the path to the downloaded image, run the following commands:
ardana >cd ~/scratch/ansible/next/ardana/ansibleardana >ansible-playbook -i hosts/localhost heat-caasp-deploy.yml -e "caasp_image_tmp_path=caasp_image_tmp_path=~/SUSE-CaaS-Platform-3.0-for-OpenStack-Cloud.x86_64-3.0.0-GM.qcow2 caasp_stack_name=caasp_multi-master caasp_stack_yaml_file=caasp-multi-master-stack.yaml caasp_stack_env_yaml_file=caasp-multi-master-environment.yaml"
33.6 Enabling the Cloud Provider Integration (CPI) Feature #
When deploying a CaaaSP cluster using SUSE CaaS Platform OpenStack heat
templates, the following CPI parameters can be set in
caasp-environment.yaml or
caasp-multi-master-environment.yaml.
- cpi_auth_url
The URL of the keystone API used to authenticate the user. This value can be found on OpenStack Dashboard under › › (for example, https://api.keystone.example.net:5000/)
- cpi_domain_name
Name of the domain the user belongs to.
- cpi_tenant_name
Name of the project the user belongs to. This is the project in which SUSE CaaS Platform resources are created.
- cpi_region
Name of the region to use when running a multi-region OpenStack cloud. The region is a general division of an OpenStack deployment.
- cpi_username
Username of a valid user that has been set in keystone. Default: admin
- cpi_password
Password of a valid user that has been set in keystone.
- cpi_monitor_max_retries
neutron load balancer monitoring max retries. Default: 3
- cpi_bs_version
cinder Block Storage API version. Possible values are v1, v2 , v3 or auto. Default:
auto- cpi_ignore_volume_az
Ignore cinder and nova availability zones. Default:
true- dns_nameserver
Set this to the IP address of a DNS nameserver accessible by the SUSE CaaS Platform cluster.
Immediately after the SUSE CaaS Platform cluster comes online, and before bootstrapping, install the latest SUSE CaaS Platform 3.0 Maintenance Update using the following steps.
Register the SUSE CaaS Platform nodes for Maintenance Updates by following the instructions in Section 33.7, “Register SUSE CaaS Platform Cluster for Software Updates”.
On each of the SUSE CaaS Platform nodes, install the latest Maintenance Update:
tux >sudo transactional-updateVerify that the Velum image packages were updated:
tux >sudo zypper se --detail velum-image i | sles12-velum-image | package | 3.1.7-3.27.3 | x86_64 | update_caaspReboot the node:
tux >sudo rebootFinally, when preparing to bootstrap using the SUSE CaaS Platform web interface, upload a valid trust certificate that can validate a certificate presented by keystone at the specified
keystone_auth_urlin theSystem-wide certificatesection of Velum. If the SSL certificate provided by keystone cannot be verified, bootstrapping fails with the errorx509: certificate signed by unknown authority.NoteIf your OpenStack endpoints operate on the Internet, or if the SSL certificates in use have been signed by a public authority, no action should be needed to enable secure communication with them.
If your OpenStack services operate in a private network using SSL certificates signed by an organizational certificate authority, provide that CA certificate as the system-wide certificate.
If your OpenStack service SSL infrastructure was self-signed during the installation of SUSE OpenStack Cloud 9 (as is done by default), its CA certificate can be retrieved from the Cloud Lifecycle Manager node in the
/etc/ssl/certs/directory. The filename should match the node name of your primary controller node. For example:/etc/ssl/certs/ardana-stack1-cp1-core-m1.pemDownload this file and provide it as the system-wide certificate.The CPI configuration settings match the values provided via the
caasp-environment.yamlorcaasp-multi-master-environment.yamlfiles. Verify that they are correct before proceeding.
33.7 Register SUSE CaaS Platform Cluster for Software Updates #
Software updates are published for all registered users of SUSE CaaS Platform, and should always be enabled upon deploying a new cluster.
These steps may be performed on cluster nodes one at a time, or in parallel,
making SSH connections as the root user with the password
that was established in your
/usr/share/caasp-openstack-heat-templates/caasp-environment.yaml file.
If using a private SMT server for registration, use its hostname or IP
address when running the commands below. Otherwise, use
scc.suse.com to connect to SUSE's public registration
server.
If this node was previously registered, deactivate its current registration:
tux >sudo SUSEConnect -dtux >sudo SUSEConnect --cleanupIf you are registering with a private SMT server, install its SSL certificate or the related organizational CA in order to perform SMT operations securely.
tux >sudo curl SMT_SERVER/smt.crt \ -o /etc/pki/trust/anchors/registration-server.pemtux >sudo update-ca-certificatesEstablish the new system registration:
tux >sudo SUSEConnect --write-config --url https://SMT_SERVER \ -r REGISTRATION_CODE -e EMAIL_ADDRESSThe same registration code may be used for all the nodes in your cluster.
Test the registration and look for a status of
Registered.tux >sudo SUSEConnect --status-text