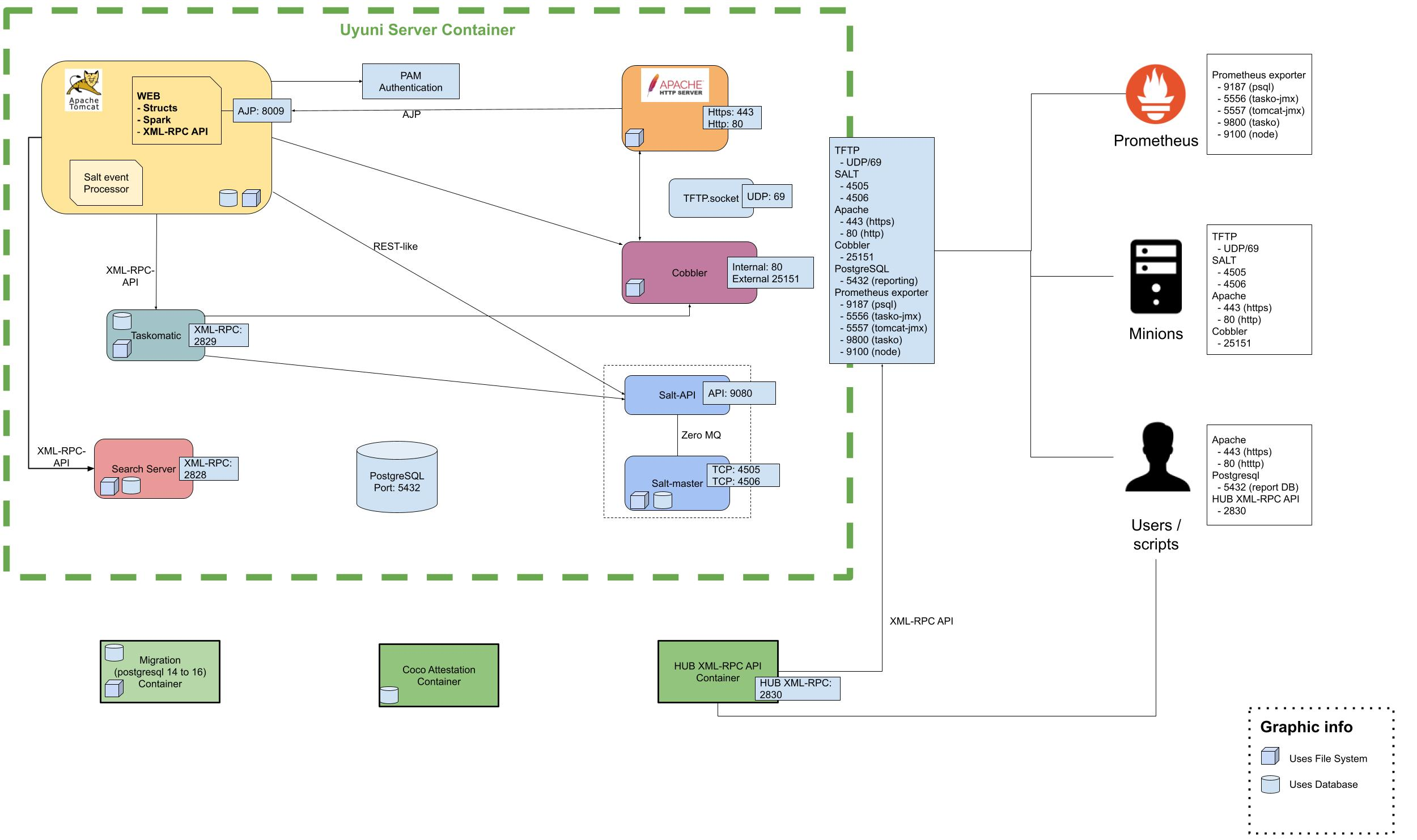
网络要求
本节详细说明 SUSE Multi-Linux Manager 的网络和端口要求。
|
IP 转发将通过容器化安装来实现。这意味着 SUSE Multi-Linux Manager 服务器和代理将充当路由器。此行为由 podman 直接完成。如果禁用 IP 转发,podman 容器将不会运行。 您可以考虑根据您的策略实现 SUSE Multi-Linux Manager 环境的网络隔离。 |
1. 完全限定的域名 (FQDN)
SUSE Multi-Linux Manager 服务器必须正确解析其 FQDN。如果无法解析 FQDN,可能会导致许多不同的组件出现严重问题。
2. 主机名和 IP 地址
为确保 SUSE Multi-Linux Manager 域名可由其客户端解析,服务器和客户端计算机都必须连接到一台正常工作的 DNS 服务器。还需要确保正确配置反向查找。
有关设置 DNS 服务器的详细信息,请参见 https://documentation.suse.com/sles/15-SP6/html/SLES-all/cha-dns.html。
3. 重新启用路由器通告
当使用 mgradm install podman 或 mgrpxy install podman 安装 SUSE Multi-Linux Manager 时,系统会设置 Podman,后者会启用 IPv4 和 IPv6 转发。这是容器与外部通信的必要条件。
然而,如果系统此前将 /proc/sys/net/ipv6/conf/eth0/accept_ra 设置为 1,则会停止使用路由器通告 (RA)。这将导致路由无法再通过 RA 获取,且默认 IPv6 路由将会缺失。
要恢复 IPv6 路由的正常功能,请执行以下步骤:
-
在
/etc/sysctl.d中创建文件,例如99-ipv6-ras.conf。 -
向文件中添加以下参数和值:
net.ipv6.conf.eth0.accept_ra = 2
-
重引导。
4. 在 HTTP 或 HTTPS OSI 七层代理后部署
有些环境强制要求通过 HTTP 或 HTTPS 代理(如 Squid 服务器或类似服务器)访问互联网。要在此类配置下允许 SUSE Multi-Linux Manager 服务器访问互联网,需进行以下配置。
-
要进行操作系统互联网访问配置,请根据需求修改
/etc/sysconfig/proxy:PROXY_ENABLED="no" HTTP_PROXY="" HTTPS_PROXY="" NO_PROXY="localhost, 127.0.0.1" -
要进行 podman 容器互联网访问配置,请根据需求修改
/etc/systemd/system/uyuni-server.service.d/custom.conf。例如,设置以下内容:[Service] Environment=TZ=Europe/Berlin Environment="PODMAN_EXTRA_ARGS=" Environment="https_proxy=user:password@http://192.168.10.1:3128" -
要进行 Java 应用程序互联网访问配置,请根据需求修改
/etc/rhn/rhn.conf。在容器主机上,执行mgrctl term以打开服务器容器内的命令行:-
修改
/etc/rhn/rhn.conf。例如,设置以下内容:# 使用代理 FQDN 或 FQDN:端口 server.satellite.http_proxy = server.satellite.http_proxy_username = server.satellite.http_proxy_password = # no_proxy 为逗号分隔的列表 server.satellite.no_proxy =
-
-
在容器主机上,重启服务器以强制应用新配置:
systemctl restart uyuni-server.service
6. 所需的网络端口
本节提供了 SUSE Multi-Linux Manager 中各种通信使用的端口的综合列表。
您不需要打开所有这些端口。某些端口只有在您使用需要这些端口的服务时才需打开。
6.2. 外部入站服务器端口
必须打开外部入站端口,以在 SUSE Multi-Linux Manager 服务器上配置防火墙用于防范未经授权访问服务器。
打开这些端口将允许外部网络流量访问 SUSE Multi-Linux Manager 服务器。
| 端口号 | 协议 | 使用方 | 备注 |
|---|---|---|---|
67 |
TCP/UDP |
DHCP |
仅当客户端向服务器请求 IP 地址时才需要此端口。 |
69 |
TCP/UDP |
TFTP |
将服务器用作 PXE 服务器进行自动化客户端安装时需要此端口。 |
80 |
TCP |
HTTP |
某些引导储存库以及进行自动化安装时需要临时使用此端口。 |
443 |
TCP |
HTTPS |
处理 Web UI、客户端、服务器和代理 ( |
4505 |
TCP |
salt |
接受来自客户端的通信请求时需要此端口。 客户端会发起连接,且该连接将保持开启状态以接收 Salt 主控端发出的命令。 |
4506 |
TCP |
salt |
接受来自客户端的通信请求时需要此端口。 客户端会发起连接,且该连接将保持开启状态以向 Salt 主控端报告结果。 |
5432 |
TCP |
PostgreSQL |
访问报告数据库时需要此端口。 |
5556 |
TCP |
Prometheus |
抓取 Taskomatic JMX 指标时需要此端口。 |
5557 |
TCP |
Prometheus |
抓取 Tomcat JMX 指标时需要此端口。 |
9100 |
TCP |
Prometheus |
抓取 节点导出器指标时需要此端口。 |
9187 |
TCP |
Prometheus |
抓取 PostgreSQL 指标时需要此端口。 |
9800 |
TCP |
Prometheus |
抓取 Taskomatic 指标时需要此端口。 |
25151 |
TCP |
Cobbler |
6.3. 外部出站服务器端口
必须打开外部出站端口,以在 SUSE Multi-Linux Manager 服务器上配置防火墙用于限制服务器可访问的内容。
打开这些端口将允许来自 SUSE Multi-Linux Manager 服务器的网络流量与外部服务通信。
| 端口号 | 协议 | 使用方 | 备注 |
|---|---|---|---|
80 |
TCP |
HTTP |
SUSE Customer Center 需要此端口。 端口 80 不用于为 Web UI 传递数据。 |
443 |
TCP |
HTTPS |
SUSE Customer Center 需要此端口。 |
25151 |
TCP |
Cobbler |
6.4. 内部服务器端口
内部端口由 SUSE Multi-Linux Manager 服务器在内部使用。只能从 localhost 访问内部端口。
大多数情况下无需调整这些端口。
| 端口号 | 备注 |
|---|---|
2828 |
Satellite-search API,由 Tomcat 和 Taskomatic 中的 RHN 应用程序使用。 |
2829 |
Taskomatic API,由 Tomcat 中的 RHN 应用程序使用。 |
8005 |
Tomcat 关机端口。 |
8009 |
Tomcat 到 Apache HTTPD (AJP)。 |
8080 |
Tomcat 到 Apache HTTPD (HTTP)。 |
9080 |
Salt-API,由 Tomcat 和 Taskomatic 中的 RHN 应用程序使用。 |
25151 |
Cobbler 的 XMLRPC API |
32000 |
与运行 Taskomatic 和 satellite-search 的 Java 虚拟机 (JVM) 建立 TCP 连接时使用此端口。 |
32768 和更高的端口用作临时端口。这些端口往往用于接收 TCP 连接。收到 TCP 连接请求后,发送方将选择其中一个临时端口号来与目标端口进行匹配。
可使用以下命令来确定哪些端口是临时端口:
cat /proc/sys/net/ipv4/ip_local_port_range
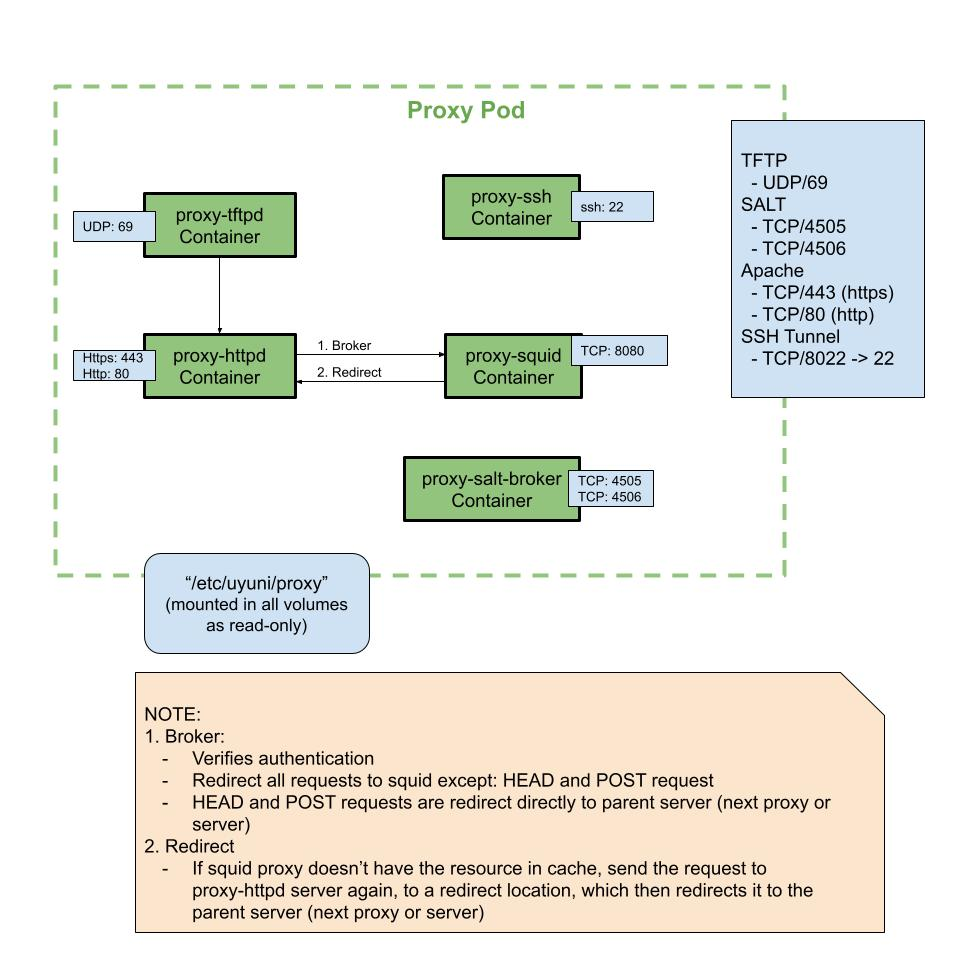
6.5. 外部入站代理端口
必须打开外部入站端口,以在 SUSE Multi-Linux Manager Proxy 上配置防火墙用于防范未经授权访问代理。
打开这些端口将允许外部网络流量访问 SUSE Multi-Linux Manager Proxy。
| 端口号 | 协议 | 使用方 | 备注 |
|---|---|---|---|
22 |
仅当用户需要通过 Salt SSH 管理代理主机时才需要此端口。 |
||
67 |
TCP/UDP |
DHCP |
仅当客户端向服务器请求 IP 地址时才需要此端口。 |
69 |
TCP/UDP |
TFTP |
将服务器用作 PXE 服务器进行自动化客户端安装时需要此端口。 |
443 |
TCP |
HTTPS |
Web UI、客户端、服务器和代理 ( |
4505 |
TCP |
salt |
接受来自客户端的通信请求时需要此端口。 客户端会发起连接,且该连接将保持开启状态以接收 Salt 主控端发出的命令。 |
4506 |
TCP |
salt |
接受来自客户端的通信请求时需要此端口。 客户端会发起连接,且该连接将保持开启状态以向 Salt 主控端报告结果。 |
8022 |
使用 ssh-push 和 ssh-push-tunnel 联系方法时需要此端口。连接至代理的客户端会主动向服务器发起签入请求,并通过该端口跳转至目标客户端。 |
6.6. 外部出站代理端口
必须打开外部出站端口,以在 SUSE Multi-Linux Manager Proxy 上配置防火墙用于限制代理可访问的内容。
打开这些端口将允许来自 SUSE Multi-Linux Manager Proxy 的网络流量与外部服务通信。
| 端口号 | 协议 | 使用方 | 备注 |
|---|---|---|---|
80 |
用于访问服务器。 |
||
443 |
TCP |
HTTPS |
SUSE Customer Center 需要此端口。 |
4505 |
TCP |
Salt |
直接或通过代理连接到 Salt 主控端时需要此端口。 |
4506 |
TCP |
Salt |
直接或通过代理连接到 Salt 主控端时需要此端口。 |
6.7. 外部客户端端口
必须打开外部客户端端口,以在 SUSE Multi-Linux Manager 服务器及其客户端之间配置防火墙。
大多数情况下无需调整这些端口。
| 端口号 | 方向 | 协议 | 备注 |
|---|---|---|---|
22 |
入站 |
SSH |
使用 ssh-push 和 ssh-push-tunnel 联系方法时需要此端口。 |
80 |
出站 |
用于访问服务器或代理。 |
|
443 |
出站 |
用于访问服务器或代理。 |
|
4505 |
出站 |
TCP |
直接或通过代理连接到 Salt 主控端时需要此端口。 |
4506 |
出站 |
TCP |
直接或通过代理连接到 Salt 主控端时需要此端口。 |
9090 |
出站 |
TCP |
Prometheus 用户界面需要此端口。 |
9093 |
出站 |
TCP |
Prometheus 警报管理器需要此端口。 |
9100 |
出站 |
TCP |
Prometheus 节点导出器需要此端口。 |
9117 |
出站 |
TCP |
Prometheus Apache 导出器需要此端口。 |
9187 |
出站 |
TCP |
Prometheus PostgreSQL 需要此端口。 |
6.8. 所需的 URL
SUSE Multi-Linux Manager 必须能够访问某些 URL 才能注册客户端和执行更新。大多数情况下,允许访问以下 URL 便已足够:
-
scc.suse.com -
updates.suse.com -
installer-updates.suse.com -
registry.suse.com -
registry-storage.suse.com -
opensuse.org
此外,您可能需要访问以下非 SUSE 产品的 URL:
-
download.nvidia.com -
public.dhe.ibm.com -
nu.novell.com
您可以在以下文章中找到有关将指定 URL 及其关联 IP 地址列入白名单的更多详细信息:访问受防火墙和/或代理保护的 SUSE Customer Center 和 SUSE 仓库。
如果您正在使用非 SUSE 客户端,则还可能需要允许访问为这些操作系统提供特定软件包的其他服务器。例如,如果您使用的是 Ubuntu 客户端,则需要能够访问 Ubuntu 服务器。
有关为非 SUSE 客户端排查防火墙访问权限问题的详细信息,请参见 防火墙查错。