Push via Salt SSH
Push via Salt SSH is used in environments where Salt clients cannot reach the SUSE Manager Server directly. In this environment, clients are located in a firewall-protected zone called a DMZ. No system within the DMZ is authorized to open a connection to the internal network, including the SUSE Manager Server.
The Push via Salt SSH method creates an encrypted tunnel from the SUSE Manager Server on the internal network to the clients located on the DMZ. After all actions and events are executed, the tunnel is closed.
The server uses the Salt SSH to contact the clients at regular intervals, checking in and performing scheduled actions and events. For more information about Salt SSH, see Salt SSH.
This contact method works for Salt clients only. For traditional clients, use Push via SSH.
This image demonstrates the Push via Salt SSH process path.
All items left of the Taskomatic block represent processes running on the SUSE Manager client.
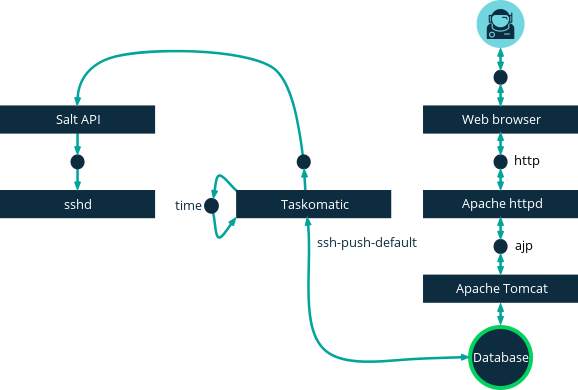
To use Push via Salt SSH, you must have the SSH daemon running on the client, and reachable by the salt-api daemon running on the SUSE Manager Server.
Additionally, Python must be available on the remote system, and be a version supported by Salt.
|
Red Hat Enterprise Linux 5, CentOS 5, and earlier are not supported, as they use unsupported versions of Python. |
-
In the SUSE Manager Web UI, navigate to and complete the appropriate fields.
-
Select an activation key with the Push via SSH contact method configured. For more information about activation keys, see Activation Keys.
-
Check the
Manage system completely via SSHcheckbox. -
Click Bootstrap to begin registration.
-
Confirm that the system has been registered correctly by navigating to .
1. Available Parameters
When you are configuring Push via Salt SSH, you can modify parameters that are used when a system is registered, including the host, activation key, and password. The password is used only for bootstrapping, it is not saved anywhere. All future SSH sessions are authorized via a key/certificate pair. These parameters are configured in .
You can also configure persistent parameters that are are used system-wide, including the sudo user. For more information on configuring the sudo user, see Push via SSH.
2. Action Execution
The Push via Salt SSH feature uses taskomatic to execute scheduled actions using salt-ssh.
The taskomatic job periodically checks for scheduled actions and executes them.
Unlike Push via SSH on traditional clients, the Push via Salt SSH feature executes a complete salt-ssh call based on the scheduled action.
By default, twenty Salt SSH actions can be executed at a time.
You can increase the number of actions that can be executed in parallel, by adding these lines to your configuration file, and adjusting the value of parallel_threads upwards.
We recommend you keep the number of parallel actions low, to avoid problems:
taskomatic.sshminion_action_executor.parallel_threads = <number> org.quartz.threadPool.threadCount = <value of parallel_threads + 20>
This adjusts the number of actions that can run in parallel on any one client and the total number of worker threads used by taskomatic. If actions needs to be run on multiple clients, actions are always executed sequentially on each client.
If the clients are connected through a proxy, you need to adjust the MaxSessions settings on the proxy.
In this case, set the number of parallel connections to be three times the total number of clients.
3. Future Features
There are some features that are not yet supported on Push via Salt SSH. These features do not work on Salt SSH clients:
-
OpenSCAP auditing
-
Beacons, resulting in:
-
Installing a package on a system using
zypperdoes not invoke the package refresh. -
Virtual Host functions (for example, a host to guests) does not work if the virtual host system is Salt SSH-based.
-
3.1. For more information
-
About Salt SSH in general, see Salt SSH and https://docs.saltproject.io/en/latest/topics/ssh/.
-
About SSH key rotation, see specialized-guides:salt/salt-ssh.adoc#salt.ssh.key_rotation.